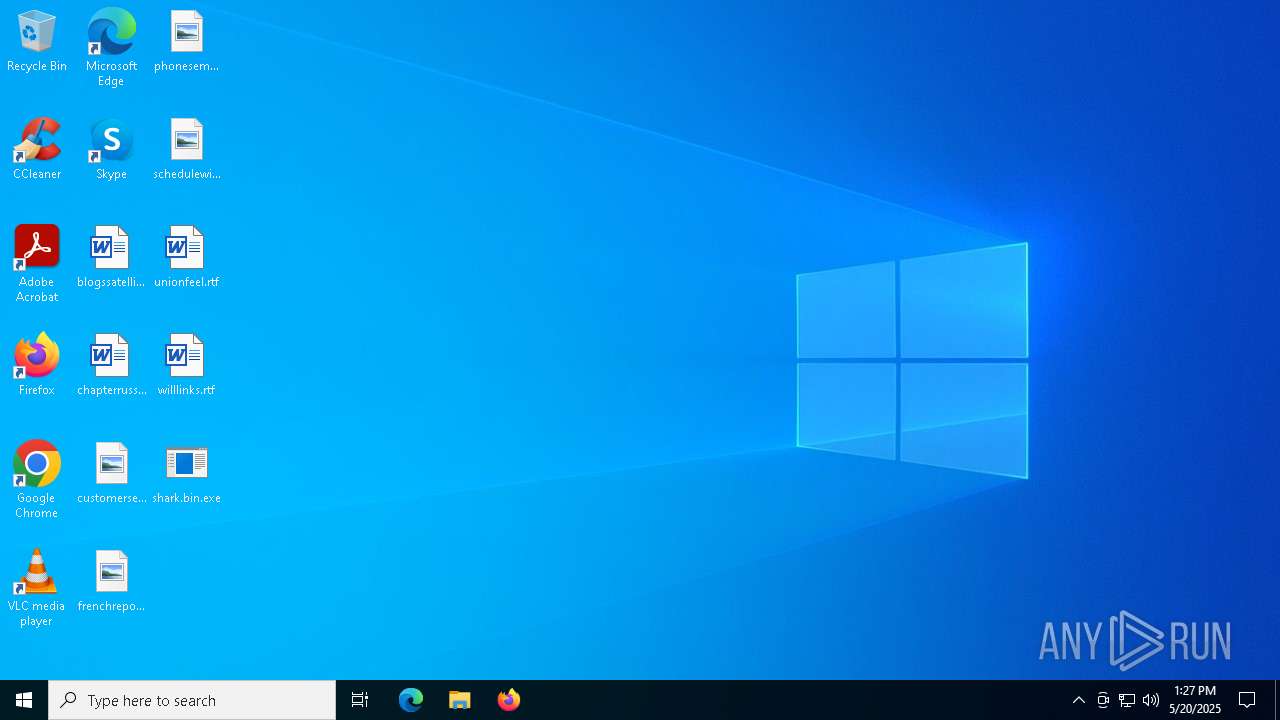
| File name: | shark.bin |
| Full analysis: | https://app.any.run/tasks/f264f6f5-4f4b-4149-a4cd-ee85c0554b8a |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2025, 13:25:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 1C34124D40BD086CBC058267BDA5D76F |
| SHA1: | 465EE2C0EDD007DFA01D38123620D808ACDFE4B6 |
| SHA256: | E882A6BC39D1EEF27CC0F7B15E649002AF592A90903C8E80164C049365B2268E |
| SSDEEP: | 98304:EoiwjIbFzw5R3Q/GzWFNk7WYa53NTjIrh4UqqCmbW8mrl5D9sgiOdtxdqoTrT+6T:a+BQVnAA |
MALICIOUS
Executing a file with an untrusted certificate
- shark.bin.exe (PID: 3020)
- shark.exe (PID: 768)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6388)
SUSPICIOUS
Executes application which crashes
- shark.bin.exe (PID: 3020)
- shark.exe (PID: 768)
Detected use of alternative data streams (AltDS)
- svchost.exe (PID: 3060)
Executable content was dropped or overwritten
- shark.bin.exe (PID: 3020)
Starts CMD.EXE for commands execution
- shark.bin.exe (PID: 3020)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4180)
- shark.exe (PID: 768)
Starts POWERSHELL.EXE for commands execution
- shark.exe (PID: 768)
Connects to unusual port
- shark.exe (PID: 768)
INFO
Application based on Golang
- shark.bin.exe (PID: 3020)
Checks supported languages
- shark.bin.exe (PID: 3020)
- OfficeClickToRun.exe (PID: 2896)
Drops encrypted JS script (Microsoft Script Encoder)
- shark.bin.exe (PID: 3020)
Manual execution by a user
- svchost.exe (PID: 3256)
- svchost.exe (PID: 3312)
- svchost.exe (PID: 2872)
- svchost.exe (PID: 2780)
- OfficeClickToRun.exe (PID: 2896)
- svchost.exe (PID: 3060)
- svchost.exe (PID: 3032)
- svchost.exe (PID: 2932)
- svchost.exe (PID: 2916)
- svchost.exe (PID: 2688)
- svchost.exe (PID: 3008)
- svchost.exe (PID: 3900)
- svchost.exe (PID: 3864)
- sppsvc.exe (PID: 3884)
- svchost.exe (PID: 4124)
- svchost.exe (PID: 3916)
- svchost.exe (PID: 3216)
- svchost.exe (PID: 2256)
- svchost.exe (PID: 3448)
- svchost.exe (PID: 876)
- svchost.exe (PID: 2136)
- svchost.exe (PID: 4848)
- svchost.exe (PID: 4264)
- svchost.exe (PID: 4384)
- svchost.exe (PID: 4536)
- svchost.exe (PID: 3324)
- TrustedInstaller.exe (PID: 5048)
- svchost.exe (PID: 5672)
- svchost.exe (PID: 5156)
- svchost.exe (PID: 5980)
- svchost.exe (PID: 5792)
- svchost.exe (PID: 6656)
- svchost.exe (PID: 6340)
- svchost.exe (PID: 6124)
- svchost.exe (PID: 6184)
- svchost.exe (PID: 2096)
- uhssvc.exe (PID: 188)
- svchost.exe (PID: 1180)
- svchost.exe (PID: 1528)
- svchost.exe (PID: 1916)
- svchost.exe (PID: 2912)
Creates files in the program directory
- shark.bin.exe (PID: 3020)
- PLUGScheduler.exe (PID: 4180)
Detects GO elliptic curve encryption (YARA)
- shark.bin.exe (PID: 3020)
Disables trace logs
- svchost.exe (PID: 3312)
Checks proxy server information
- svchost.exe (PID: 2136)
Reads the computer name
- PLUGScheduler.exe (PID: 4180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (37.4) |
|---|---|---|
| .scr | | | Windows screen saver (34.5) |
| .exe | | | Win32 Executable (generic) (11.9) |
| .exe | | | Win16/32 Executable Delphi generic (5.4) |
| .exe | | | Generic Win/DOS Executable (5.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 351232 |
| InitializedDataSize: | 5707776 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x56a64 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
319
Monitored processes
77
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Microsoft Update Health Tools\uhssvc.exe" | C:\Program Files\Microsoft Update Health Tools\uhssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Update Health Service Version: 10.0.19041.3626 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | "C:\ProgramData\shark.exe" | C:\ProgramData\shark.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 876 | C:\WINDOWS\System32\svchost.exe -k LocalServiceNetworkRestricted -s RmSvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1180 | C:\WINDOWS\System32\svchost.exe -k NetworkService -p -s WinRM | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 3020 -s 620 | C:\Windows\SysWOW64\WerFault.exe | — | shark.bin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1528 | C:\WINDOWS\System32\svchost.exe -k LocalServiceNetworkRestricted -p -s wscsvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1912 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 3020 -s 156 | C:\Windows\SysWOW64\WerFault.exe | — | shark.bin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1916 | C:\WINDOWS\system32\svchost.exe -k UnistackSvcGroup | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s StorSvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | C:\WINDOWS\system32\svchost.exe -k UnistackSvcGroup -s CDPUserSvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
40 995
Read events
40 764
Write events
192
Delete events
39
Modification events
| (PID) Process: | (2932) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\WDI\Config |
| Operation: | write | Name: | ServerName |
Value: \BaseNamedObjects\WDI_{cd9f5bca-ce95-4428-bfb3-4ef65341f42f} | |||
| (PID) Process: | (2780) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Winmgmt\Parameters |
| Operation: | write | Name: | ServiceDllUnloadOnStop |
Value: 1 | |||
| (PID) Process: | (3020) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\LanmanServer\Parameters |
| Operation: | delete value | Name: | Guid |
Value: 蘆땛箒䗲ᢌ嬷�꽮 | |||
| (PID) Process: | (3020) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\LanmanServer\Parameters |
| Operation: | write | Name: | Guid |
Value: 938B9D6BC7464A45938F9541D39C6FC8 | |||
| (PID) Process: | (3008) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\iphlpsvc\DaMultisite |
| Operation: | delete value | Name: | SelectedSite |
Value: | |||
| (PID) Process: | (3008) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\iphlpsvc\DaMultisite |
| Operation: | delete value | Name: | SelectionMethod |
Value: | |||
| (PID) Process: | (3312) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RasMan\Parameters |
| Operation: | delete value | Name: | AllocatedLuids |
Value: | |||
| (PID) Process: | (5156) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Orchestrator |
| Operation: | write | Name: | MostackEnabled |
Value: 1 | |||
| (PID) Process: | (5156) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Orchestrator |
| Operation: | write | Name: | MoStack |
Value: 1 | |||
| (PID) Process: | (5156) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Orchestrator\Scheduler |
| Operation: | write | Name: | Checking to see if mostack override has changed |
Value: 60A627FF8AC9DB01 | |||
Executable files
1
Suspicious files
99
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2932 | svchost.exe | C:\Windows\System32\sru\SRUDB.dat | — | |
MD5:— | SHA256:— | |||
| 3020 | shark.bin.exe | C:\ProgramData\shark.exe | executable | |
MD5:1C34124D40BD086CBC058267BDA5D76F | SHA256:E882A6BC39D1EEF27CC0F7B15E649002AF592A90903C8E80164C049365B2268E | |||
| 2932 | svchost.exe | C:\Windows\System32\sru\SRU00274.log | binary | |
MD5:7AD6E1F17A45EADBA8347F9B79E1E034 | SHA256:01E126E0C9854760E26774EAD65F1E36825F8531D5FDDF56381FDB52ED6EABBC | |||
| 3884 | sppsvc.exe | C:\Windows\System32\spp\store\2.0\data.dat.bak | binary | |
MD5:C7C6D58F9E2A32CE16ECAE42BC951434 | SHA256:A8717B0BCEBF96616226B212641F2EC46F66989F35F8C112BD785EEAB4FE318F | |||
| 2932 | svchost.exe | C:\Windows\System32\sru\SRU.log | binary | |
MD5:2B83A22EB7169A51F444328AB6999F2F | SHA256:9C0A52F420EEB3D75FED078075025D7B4C543F24C3E6431C78948912EB2CA5A4 | |||
| 4180 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.050.etl | binary | |
MD5:C8834D365FAE073DEDE1F1620454CE71 | SHA256:C6DD793EEE1D5551CA507A3C5BFFECA82DD3E29C63C2C6DD218A7D4BFB37046B | |||
| 3884 | sppsvc.exe | C:\Windows\System32\spp\store\2.0\data.dat | binary | |
MD5:C7C6D58F9E2A32CE16ECAE42BC951434 | SHA256:A8717B0BCEBF96616226B212641F2EC46F66989F35F8C112BD785EEAB4FE318F | |||
| 2896 | OfficeClickToRun.exe | C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\27EFE683-F590-4309-BDF5-E3CBB7CC6C78 | xml | |
MD5:39A133BB25EC9A977418E12E4AF70F91 | SHA256:61D5BBDA8F855EBCD1A177A465A0804D1386C87BC75342B0D027EA47DA4D4561 | |||
| 3448 | svchost.exe | C:\ProgramData\regid.1991-06.com.microsoft\regid.1991-06.com.microsoft_Windows-10-Pro.swidtag | xml | |
MD5:CAB432C4918E1CFF493C9668B2338104 | SHA256:2CE9E3A7CF26A6706D8078C732D8211AEB76E9FAA5C6D3A026E32B077EDF23DF | |||
| 3884 | sppsvc.exe | C:\Windows\System32\spp\store\2.0\data.dat.tmp | binary | |
MD5:C7C6D58F9E2A32CE16ECAE42BC951434 | SHA256:A8717B0BCEBF96616226B212641F2EC46F66989F35F8C112BD785EEAB4FE318F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
71
DNS requests
31
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5260 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5260 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5296 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3432 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5736 | BackgroundTransferHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6684 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.25:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET TA_ABUSED_SERVICES DNS Query to Commonly Actor Abused Online Service (data-seed-prebsc-2-s1 .binance .org) |
768 | shark.exe | Misc activity | ET TA_ABUSED_SERVICES Observed Commonly Actor Abused Online Service Domain (data-seed-prebsc-2-s1 .binance .org in TLS SNI) |