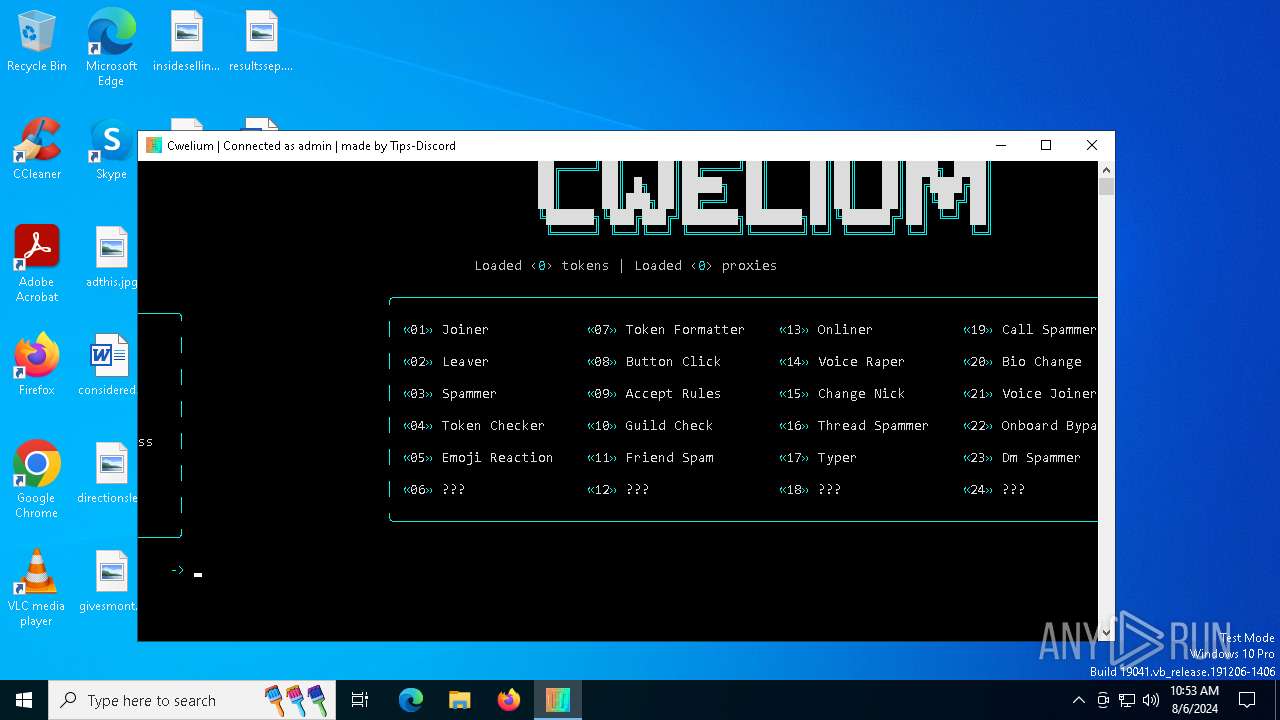
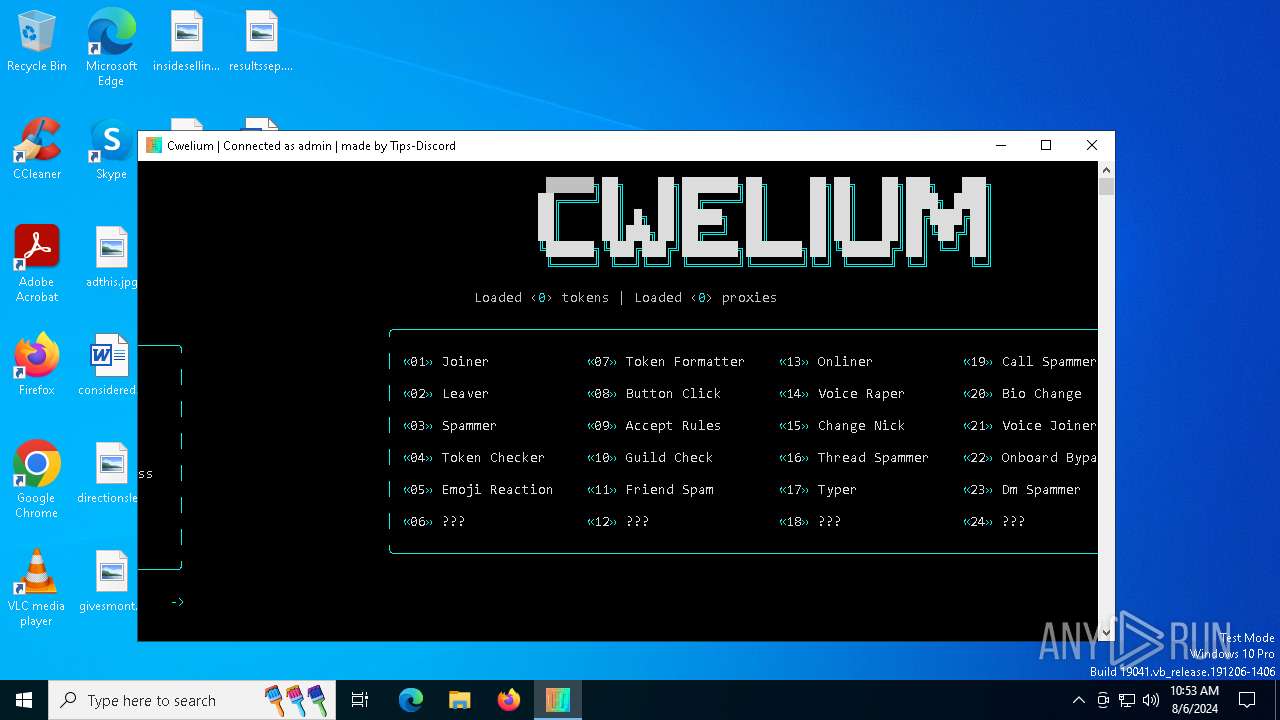
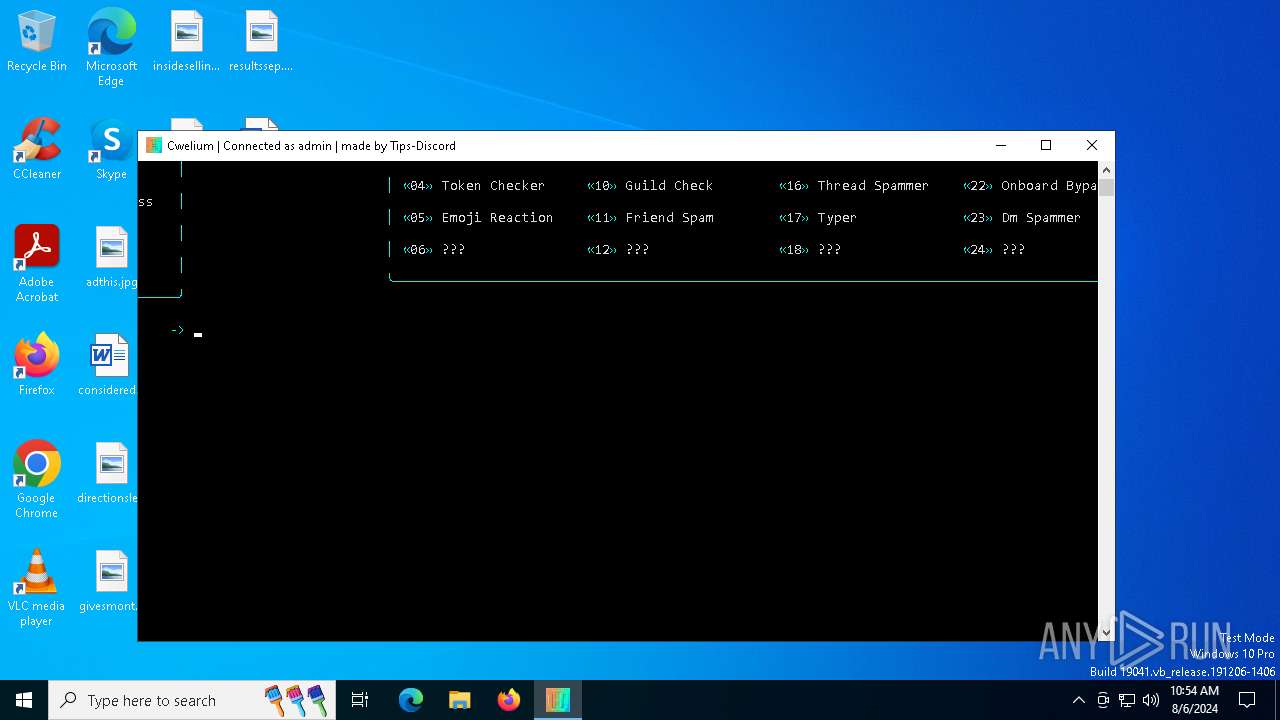
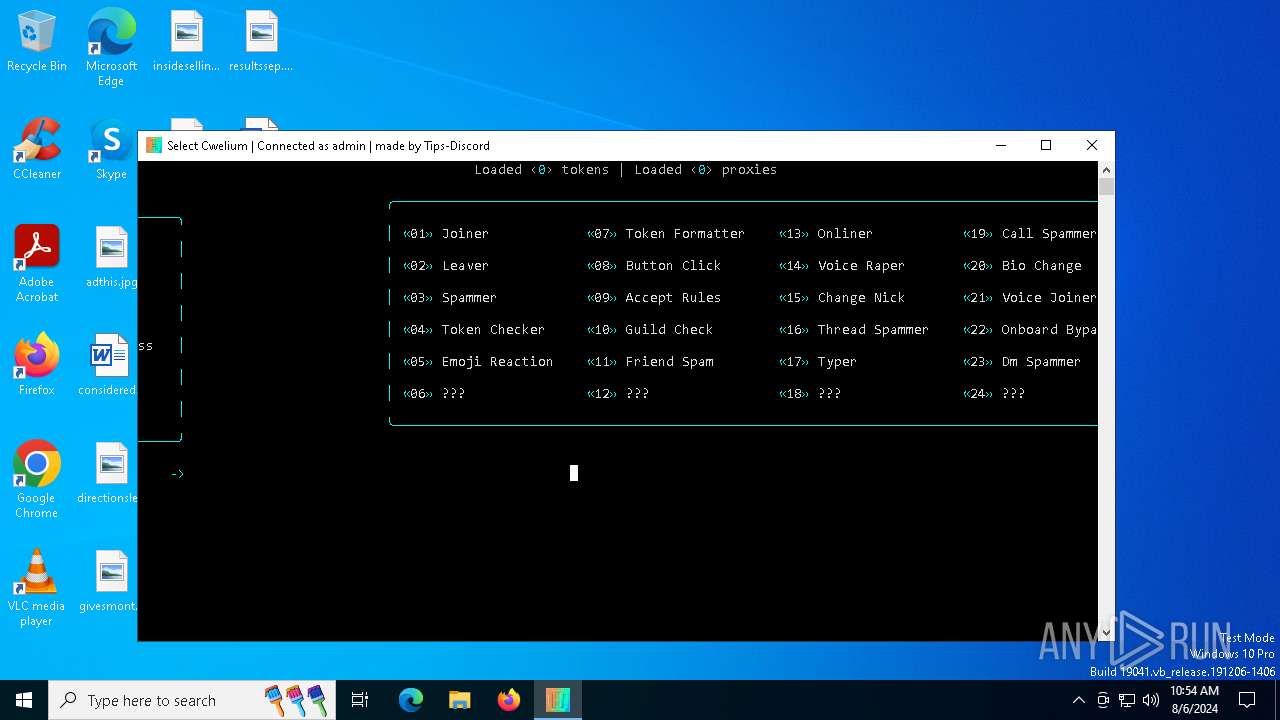
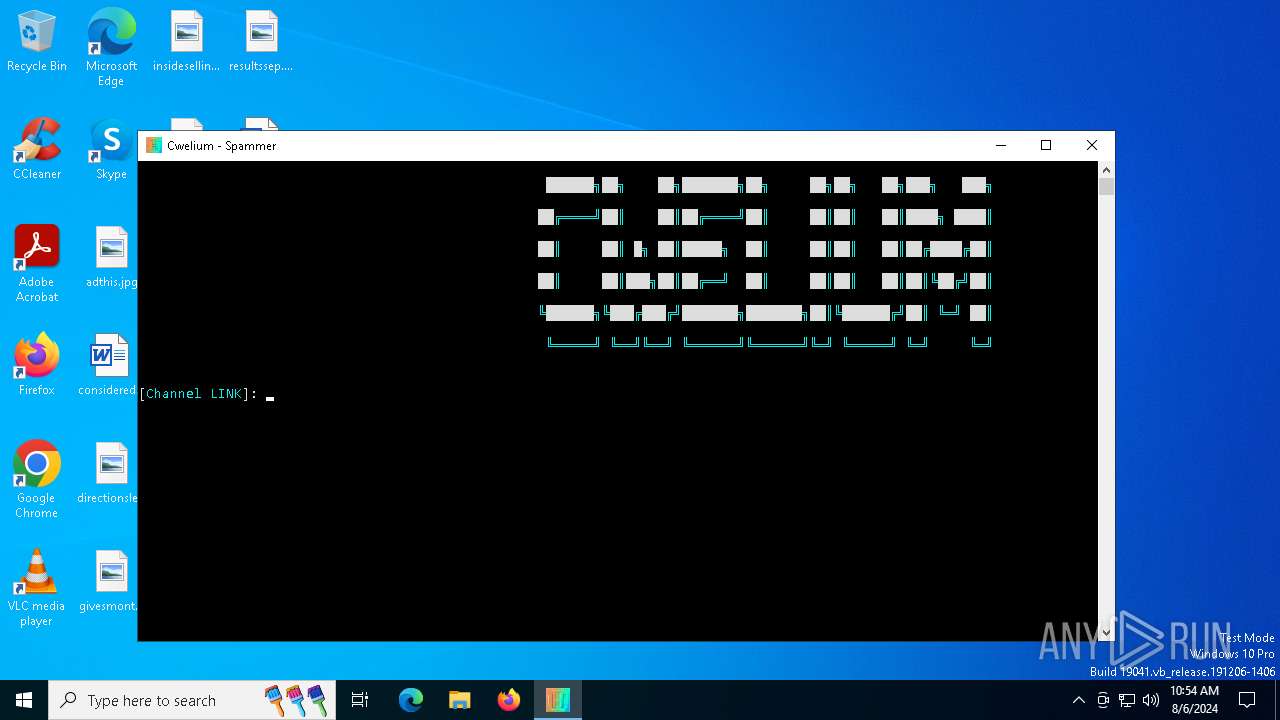
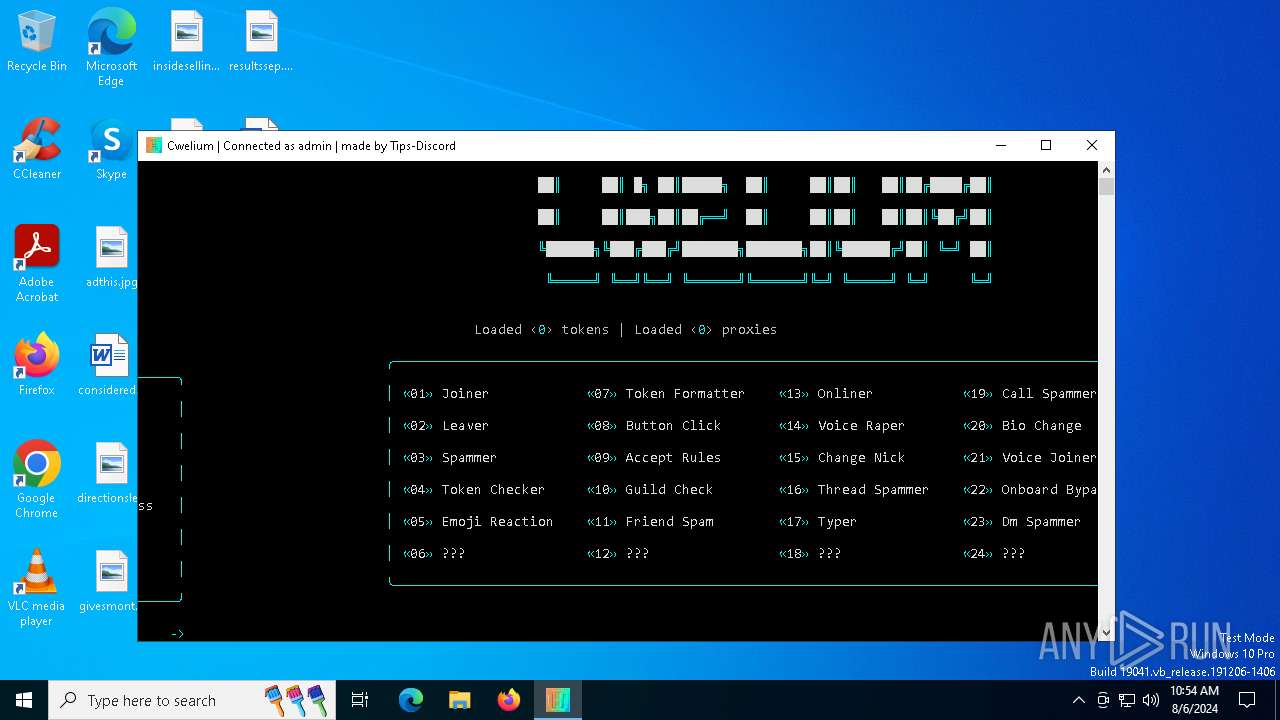
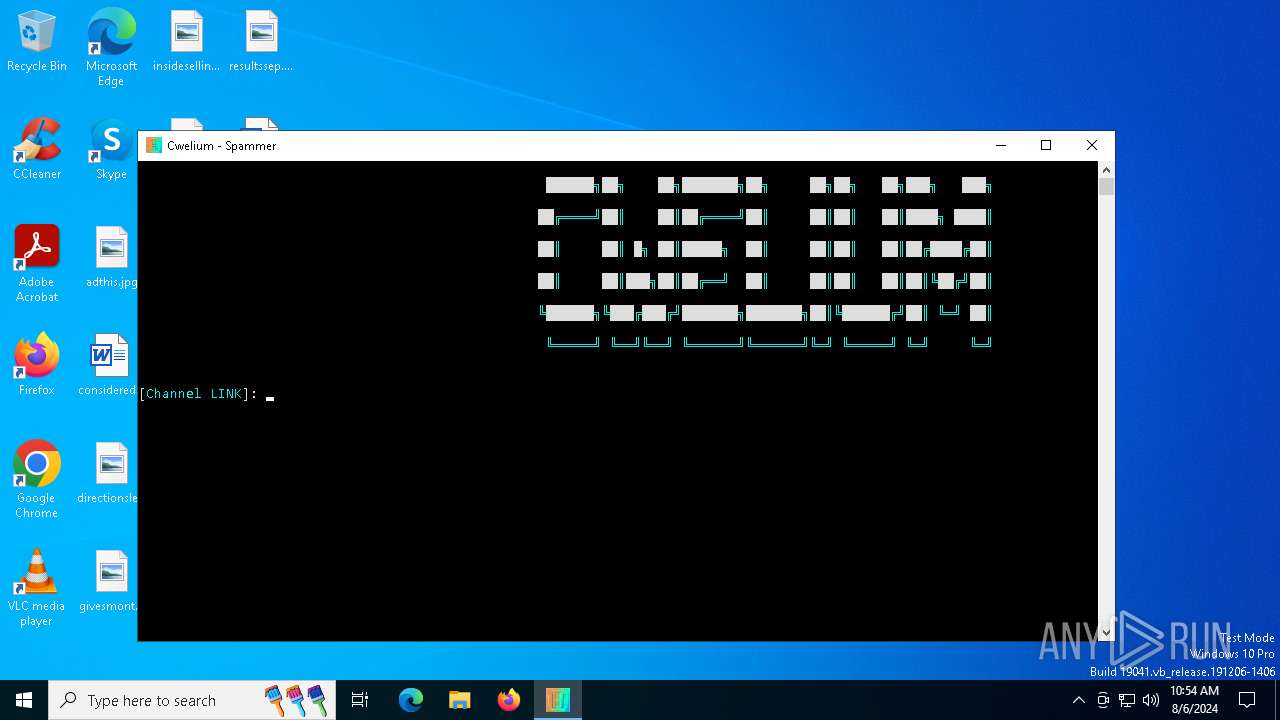
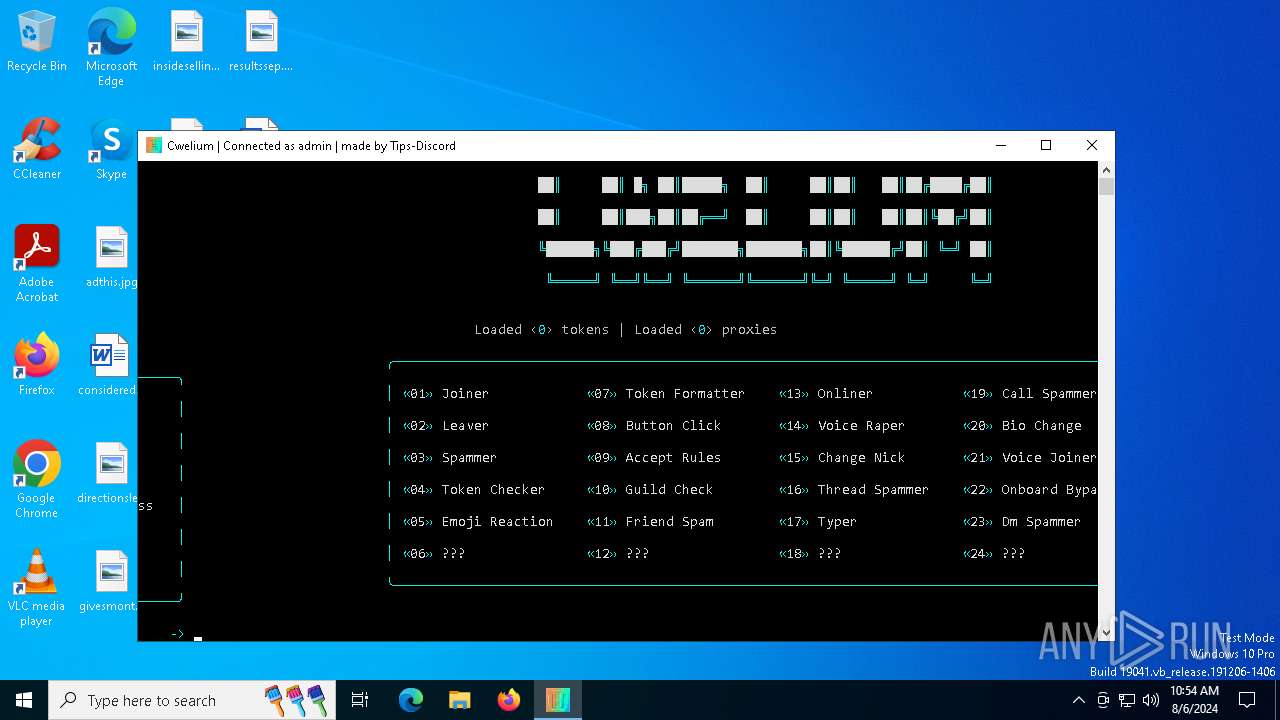
| File name: | Cwelium.exe |
| Full analysis: | https://app.any.run/tasks/bc0dde0b-5def-45cb-ba8c-af6511cff30f |
| Verdict: | Malicious activity |
| Analysis date: | August 06, 2024, 10:53:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64 (stripped to external PDB), for MS Windows |
| MD5: | 546F3E40437F8F71E1D3F872C65F1AD5 |
| SHA1: | 8803B0C94BF73E165BEE35C6443FDAFBACBD86CC |
| SHA256: | E85F26BEB6DC9095A46375FBB3D662CD7E270125EA4702CC9FCE7A962EA4305D |
| SSDEEP: | 196608:Bsx4kJua9a980xs/PIZEc4halNmehVjTHshRQSh:yxLwEahxs/P3PevHVs |
MALICIOUS
Drops the executable file immediately after the start
- Cwelium.exe (PID: 7020)
SUSPICIOUS
Process drops python dynamic module
- Cwelium.exe (PID: 7020)
The process drops C-runtime libraries
- Cwelium.exe (PID: 7020)
Executable content was dropped or overwritten
- Cwelium.exe (PID: 7020)
Process drops legitimate windows executable
- Cwelium.exe (PID: 7020)
Loads Python modules
- Cwelium.exe (PID: 7100)
Starts CMD.EXE for commands execution
- Cwelium.exe (PID: 7100)
INFO
Create files in a temporary directory
- Cwelium.exe (PID: 7020)
- Cwelium.exe (PID: 7100)
Checks supported languages
- Cwelium.exe (PID: 7020)
- Cwelium.exe (PID: 7100)
Reads the computer name
- Cwelium.exe (PID: 7100)
Reads the software policy settings
- Cwelium.exe (PID: 7100)
Reads the machine GUID from the registry
- Cwelium.exe (PID: 7100)
Attempting to use instant messaging service
- Cwelium.exe (PID: 7100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:08:06 10:51:16+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 2.41 |
| CodeSize: | 110080 |
| InitializedDataSize: | 13413888 |
| UninitializedDataSize: | 73216 |
| EntryPoint: | 0x1125 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.8.0 |
| ProductVersionNumber: | 1.1.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Cwelium inc. |
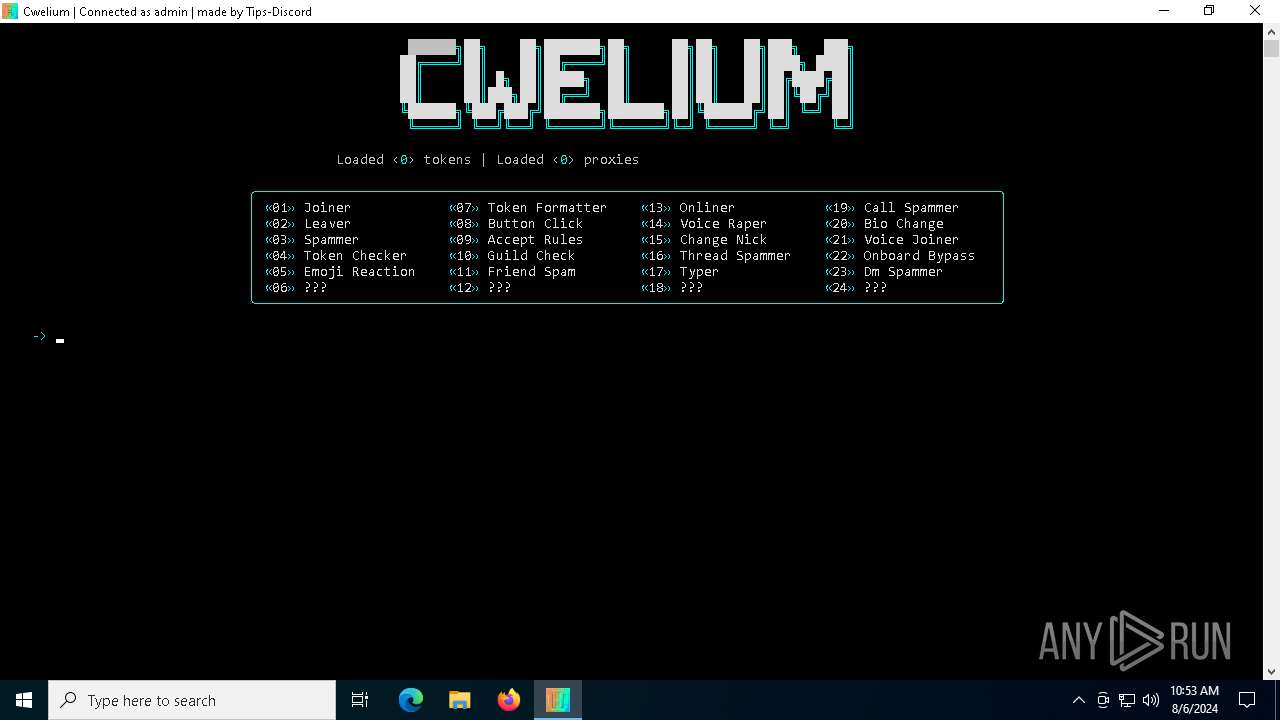
| FileDescription: | Cwelium Discord Raider |
| LegalCopyright: | Copyright (c) 2024 Cwelium Inc. All rights reserved. |
| ProductVersion: | 1.1.0.0 |
| FileVersion: | 1.0.8.0 |
| OriginalFileName: | Cwelium.exe |
| InternalName: | Cwelium |
| ProductName: | Cwelium |
Total processes
140
Monitored processes
15
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1568 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 3276 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 3520 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 3980 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 4604 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 4844 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 5468 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 5984 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 6476 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 6572 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
Total events
5 465
Read events
5 219
Write events
246
Delete events
0
Modification events
| (PID) Process: | (7100) Cwelium.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-462 |
Value: Afghanistan Standard Time | |||
| (PID) Process: | (7100) Cwelium.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-461 |
Value: Afghanistan Daylight Time | |||
| (PID) Process: | (7100) Cwelium.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-222 |
Value: Alaskan Standard Time | |||
| (PID) Process: | (7100) Cwelium.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-221 |
Value: Alaskan Daylight Time | |||
| (PID) Process: | (7100) Cwelium.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-2392 |
Value: Aleutian Standard Time | |||
| (PID) Process: | (7100) Cwelium.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-2391 |
Value: Aleutian Daylight Time | |||
| (PID) Process: | (7100) Cwelium.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-2162 |
Value: Altai Standard Time | |||
| (PID) Process: | (7100) Cwelium.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-2161 |
Value: Altai Daylight Time | |||
| (PID) Process: | (7100) Cwelium.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-392 |
Value: Arab Standard Time | |||
| (PID) Process: | (7100) Cwelium.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-391 |
Value: Arab Daylight Time | |||
Executable files
23
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7020 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_7020_133674152206396212\Cwelium.exe | executable | |
MD5:3A1C1D4C60D40FEB32EEF4D9269AE0E0 | SHA256:920009C5E37D334AF7D2B284F6DB158CA81DCB63C8F3C1ED08513FDD403D5A6D | |||
| 7020 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_7020_133674152206396212\_lzma.pyd | executable | |
MD5:E5ABC3A72996F8FDE0BCF709E6577D9D | SHA256:1796038480754A680F33A4E37C8B5673CC86C49281A287DC0C5CAE984D0CB4BB | |||
| 7020 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_7020_133674152206396212\_decimal.pyd | executable | |
MD5:65B4AB77D6C6231C145D3E20E7073F51 | SHA256:93EB9D1859EDCA1C29594491863BF3D72AF70B9A4240E0D9DD171F668F4F8614 | |||
| 7020 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_7020_133674152206396212\_ctypes.pyd | executable | |
MD5:BD36F7D64660D120C6FB98C8F536D369 | SHA256:EE543453AC1A2B9B52E80DC66207D3767012CA24CE2B44206804767F37443902 | |||
| 7020 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_7020_133674152206396212\libcrypto-1_1.dll | executable | |
MD5:E94733523BCD9A1FB6AC47E10A267287 | SHA256:F20EB4EFD8647B5273FDAAFCEB8CCB2B8BA5329665878E01986CBFC1E6832C44 | |||
| 7020 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_7020_133674152206396212\_socket.pyd | executable | |
MD5:1EEA9568D6FDEF29B9963783827F5867 | SHA256:74181072392A3727049EA3681FE9E59516373809CED53E08F6DA7C496B76E117 | |||
| 7020 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_7020_133674152206396212\_uuid.pyd | executable | |
MD5:46E9D7B5D9668C9DB5CAA48782CA71BA | SHA256:F6063622C0A0A34468679413D1B18D1F3BE67E747696AB972361FAED4B8D6735 | |||
| 7020 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_7020_133674152206396212\libffi-8.dll | executable | |
MD5:0F8E4992CA92BAAF54CC0B43AACCCE21 | SHA256:EFF52743773EB550FCC6CE3EFC37C85724502233B6B002A35496D828BD7B280A | |||
| 7020 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_7020_133674152206396212\python3.dll | executable | |
MD5:B711598FC3ED0FE4CF2C7F3E0877979E | SHA256:520169AA6CF49D7EE724D1178DE1BE0E809E4BDCF671E06F3D422A0DD5FD294A | |||
| 7020 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_7020_133674152206396212\python311.dll | executable | |
MD5:5A5DD7CAD8028097842B0AFEF45BFBCF | SHA256:A811C7516F531F1515D10743AE78004DD627EBA0DC2D3BC0D2E033B2722043CE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
37
DNS requests
16
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6708 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6764 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1120 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 104.126.37.137:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6680 | backgroundTaskHost.exe | 104.126.37.137:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
discord.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
7100 | Cwelium.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |