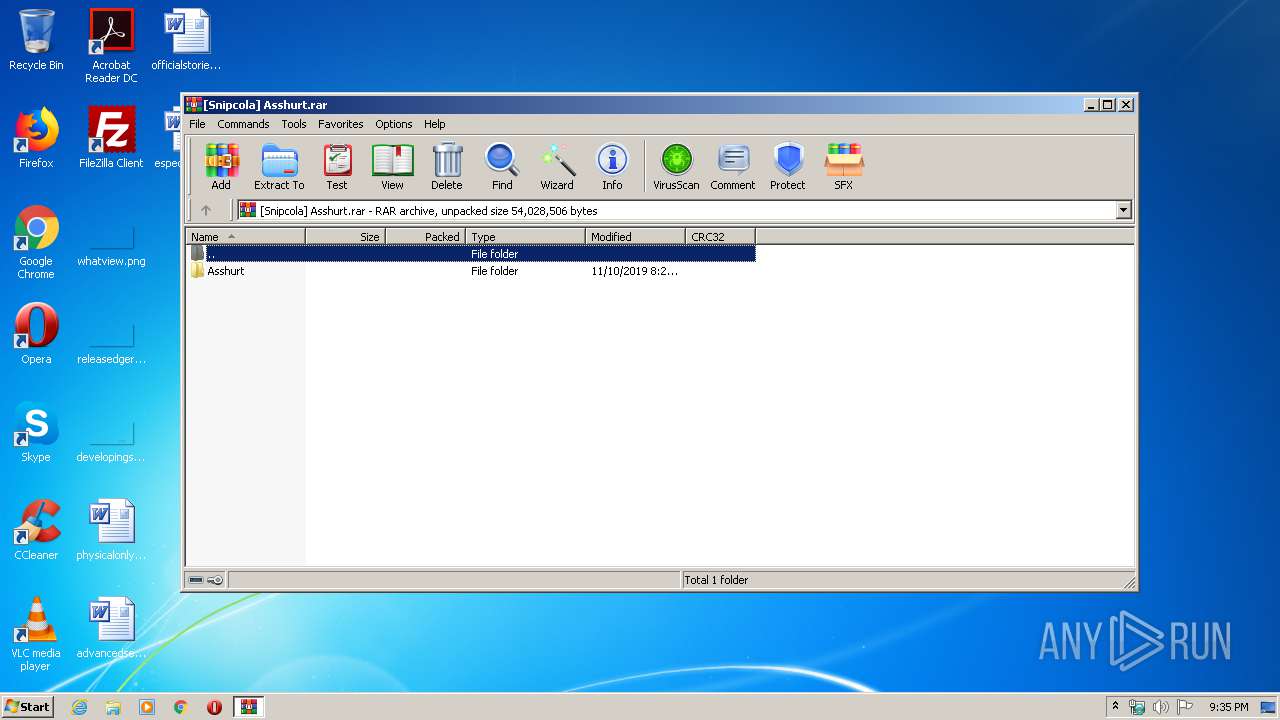
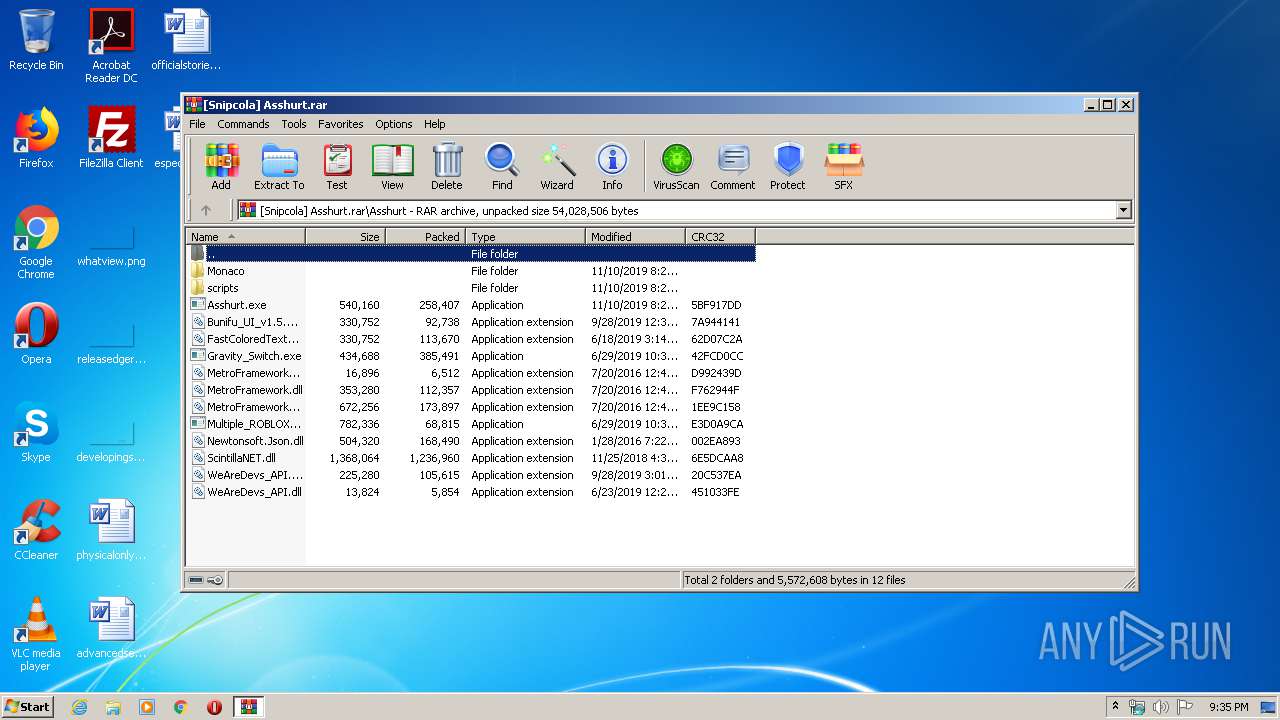
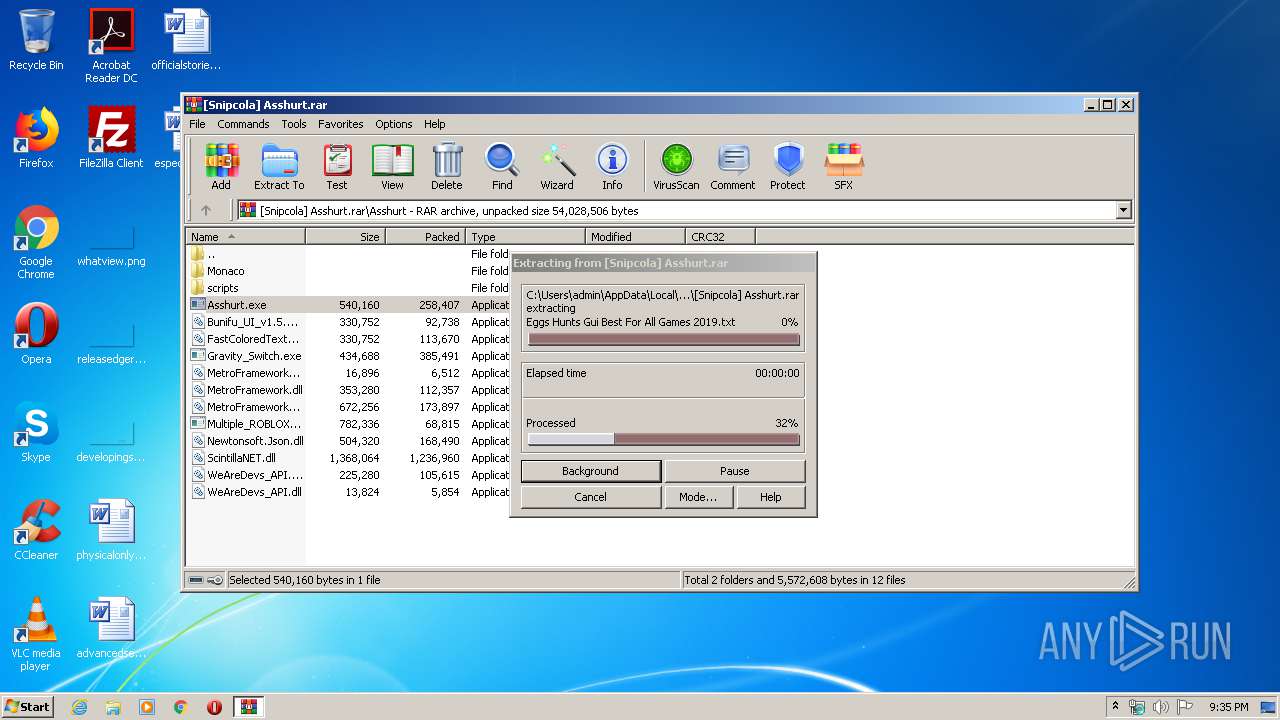
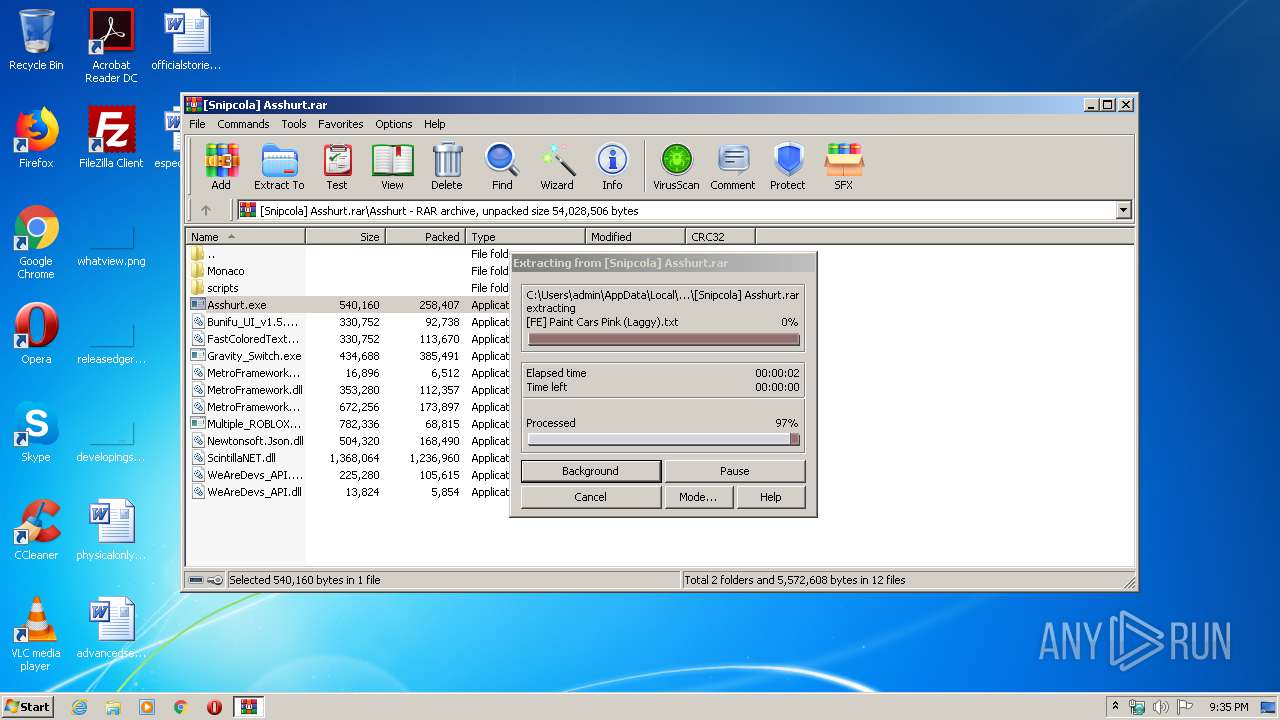
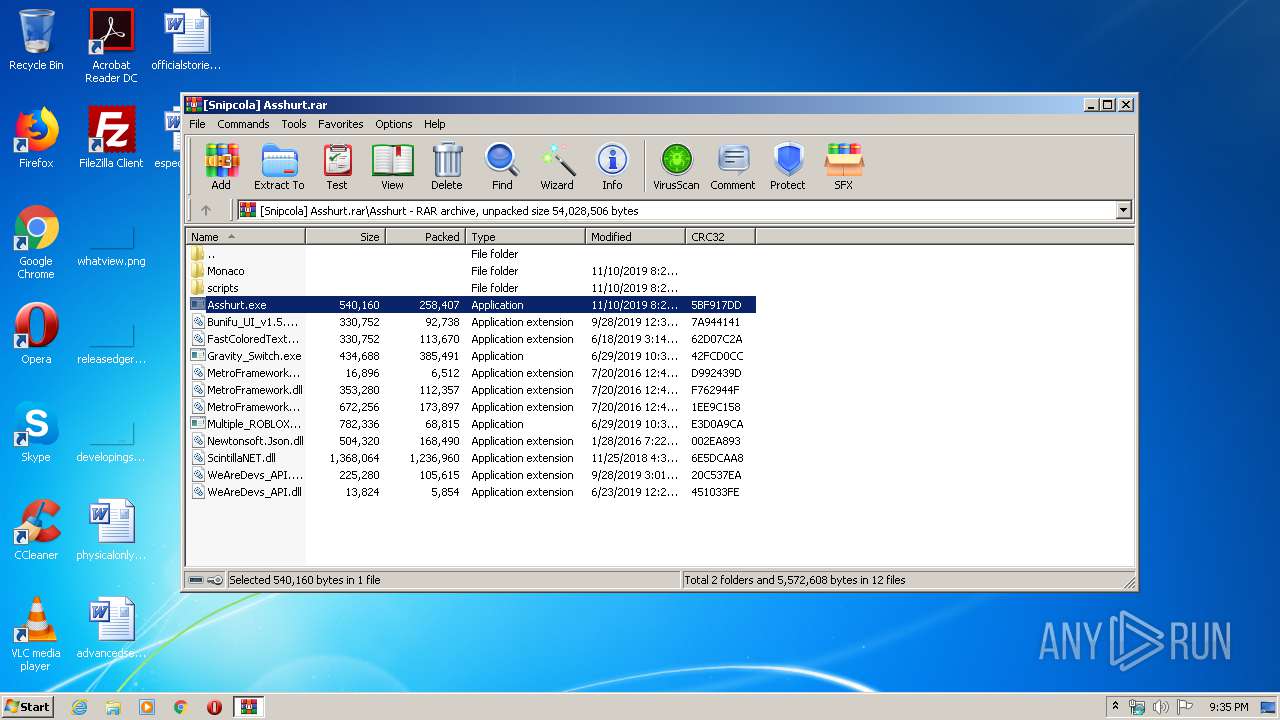
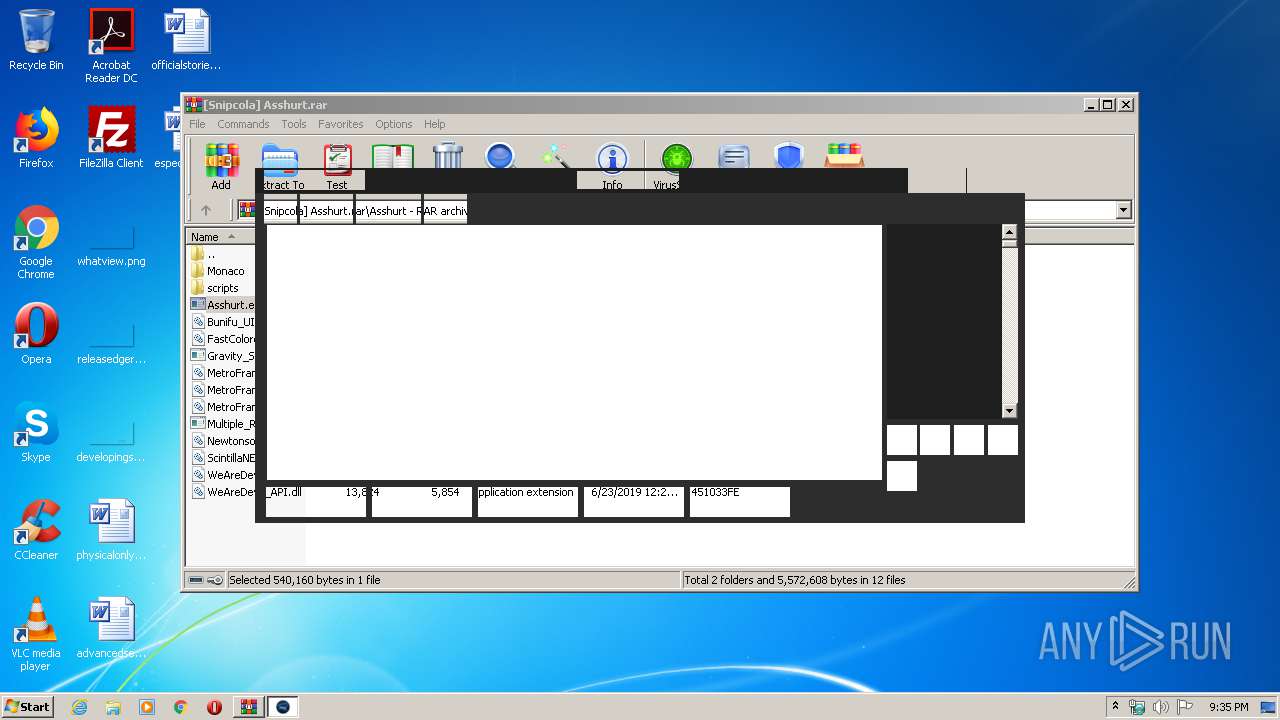
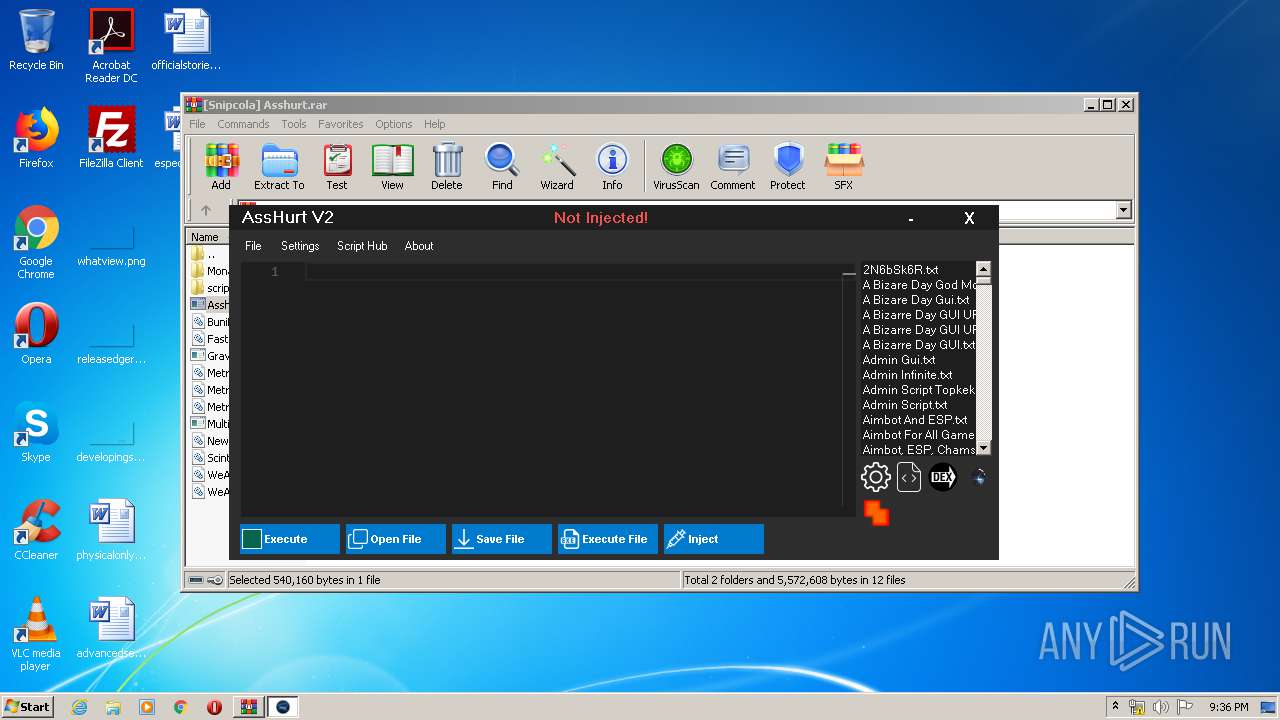
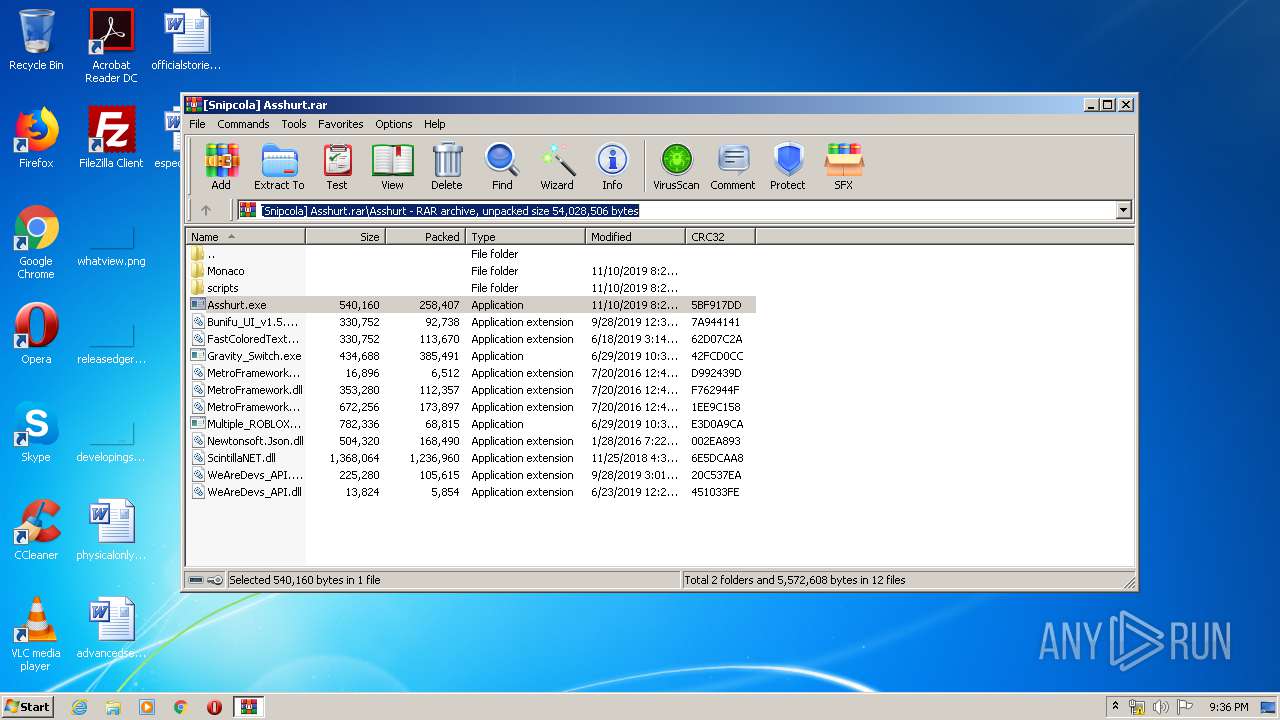
| File name: | [Snipcola] Asshurt.rar |
| Full analysis: | https://app.any.run/tasks/60444abd-17d8-42c2-bd8b-b643b464f61c |
| Verdict: | Malicious activity |
| Analysis date: | March 14, 2020, 21:34:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A7C000EA7C4EE80888EC8C9A3C5F8BEF |
| SHA1: | 073BAFD906161B35D39777B122D7874288EDF895 |
| SHA256: | E852C2FEB1CDED5D8CF161BF3530E1DED83661841BACB85ABF7011ECDC8F3FB8 |
| SSDEEP: | 393216:Vth8C7sZoTrefEP+GfvKiNi1Gm9GmxDpIm4NoyNHBHF4nCIto:f6o7+iKiNixDpt4NFNHBHSnCIm |
MALICIOUS
Loads dropped or rewritten executable
- Asshurt.exe (PID: 3336)
Application was dropped or rewritten from another process
- Asshurt.exe (PID: 3336)
SUSPICIOUS
Reads Internet Cache Settings
- Asshurt.exe (PID: 3336)
Reads internet explorer settings
- Asshurt.exe (PID: 3336)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 3408)
Changes IE settings (feature browser emulation)
- Asshurt.exe (PID: 3336)
Creates files in the user directory
- Asshurt.exe (PID: 3336)
Executable content was dropped or overwritten
- Asshurt.exe (PID: 3336)
- WinRAR.exe (PID: 3408)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3408)
Reads settings of System Certificates
- Asshurt.exe (PID: 3336)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
35
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 880 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIa3408.10321\FastColoredTextBox.dll | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
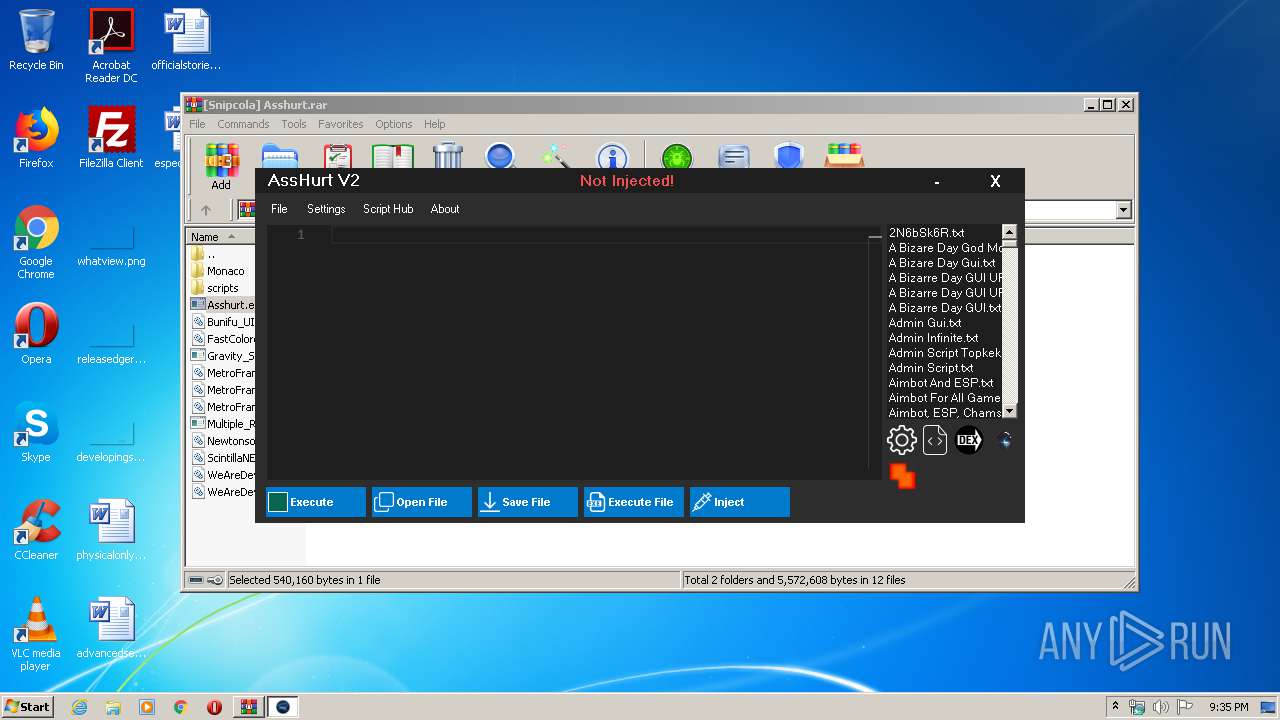
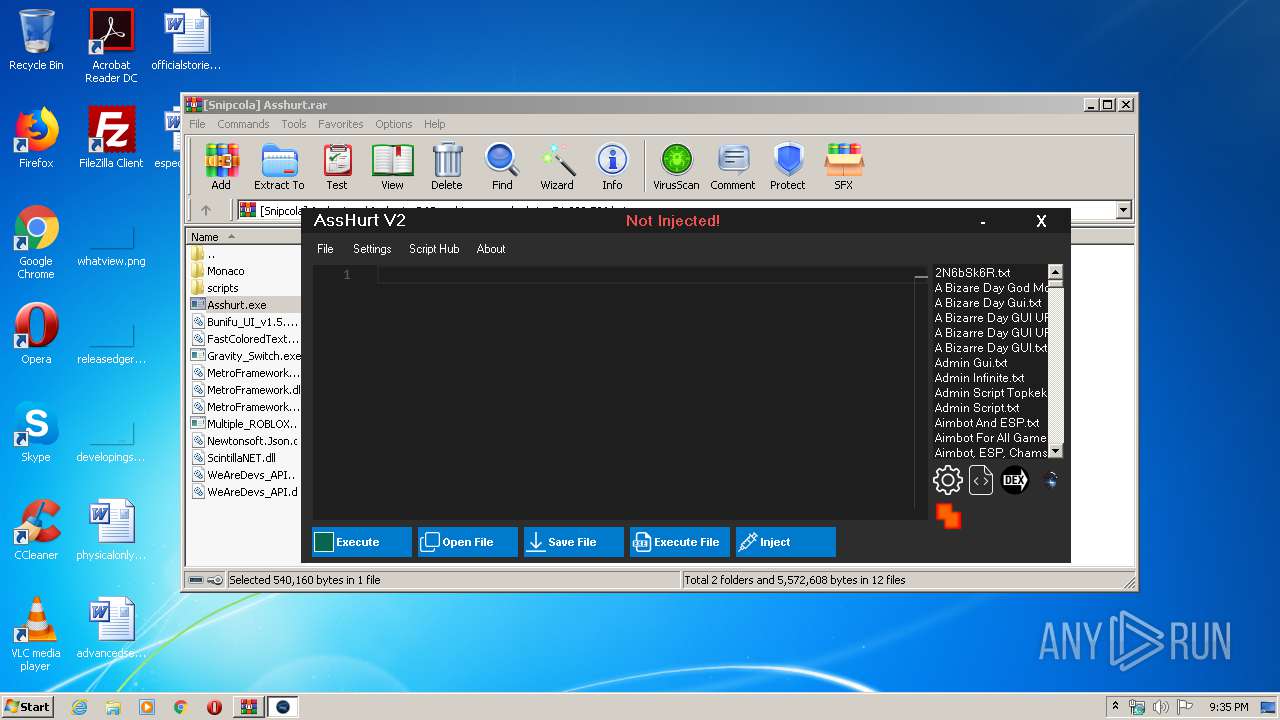
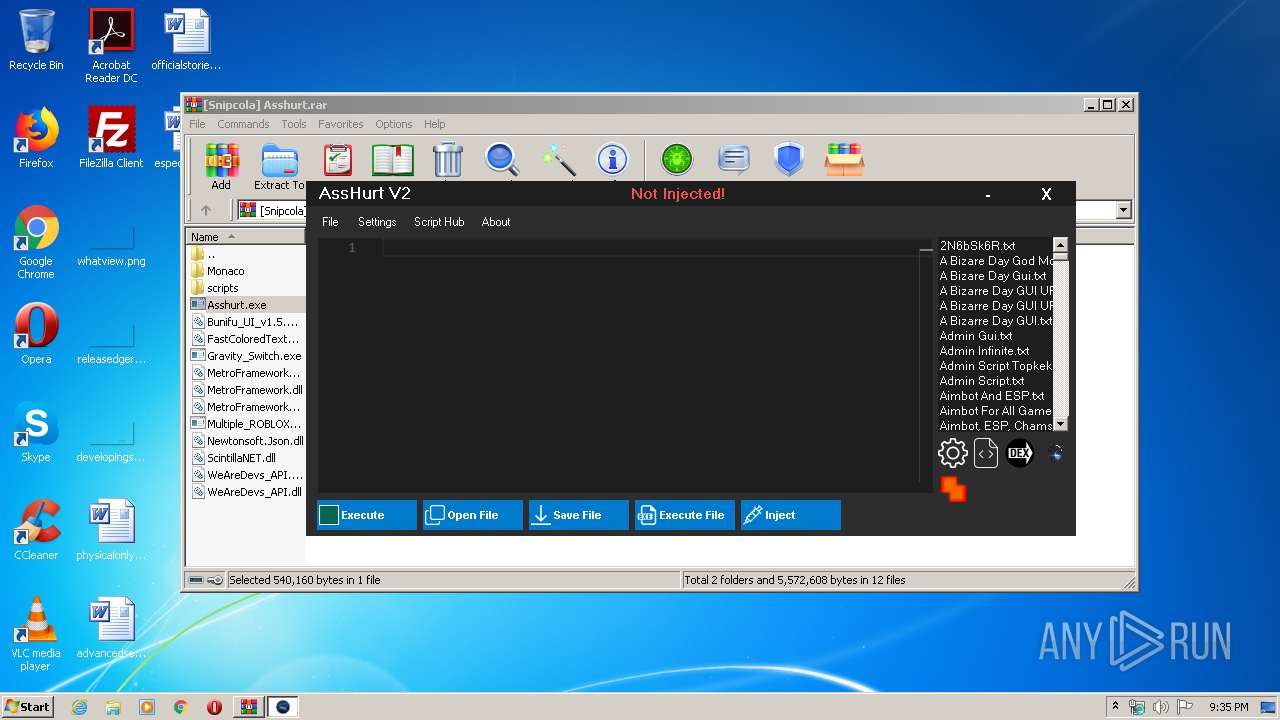
| 3336 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3408.6032\Asshurt\Asshurt.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3408.6032\Asshurt\Asshurt.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: AssHurt Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3408 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\[Snipcola] Asshurt.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
933
Read events
900
Write events
33
Delete events
0
Modification events
| (PID) Process: | (3408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3408) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\[Snipcola] Asshurt.rar | |||
| (PID) Process: | (3408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
15
Suspicious files
10
Text files
1 190
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3408.6032\Asshurt\FastColoredTextBox.dll | executable | |
MD5:8610F4D3CDC6CC50022FEDDCED9FDAEB | SHA256:AC926C92CCFC3789A5AE571CC4415EB1897D500A79604D8495241C19ACDF01B9 | |||
| 3408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3408.6032\Asshurt\Asshurt.exe | executable | |
MD5:5F2630506F57B492AA0FEA7B8B752337 | SHA256:297D0B5D8102C5B6646D48688D928031D4CCC8E4400434638406383ADB7E78BB | |||
| 3408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3408.6032\Asshurt\MetroFramework.dll | executable | |
MD5:34EA7F7D66563F724318E322FF08F4DB | SHA256:C2C12D31B4844E29DE31594FC9632A372A553631DE0A0A04C8AF91668E37CF49 | |||
| 3408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3408.6032\Asshurt\MetroFramework.Fonts.dll | executable | |
MD5:65EF4B23060128743CEF937A43B82AA3 | SHA256:C843869AACA5135C2D47296985F35C71CA8AF4431288D04D481C4E46CC93EE26 | |||
| 3408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3408.6032\Asshurt\Gravity_Switch.exe | executable | |
MD5:A6CEAF8E4B44B37A7487A9152B9514C3 | SHA256:3C9DD88809C6BFD1FB9439DBB4C5859DCA2A50918695443A85D3E118705ADB47 | |||
| 3408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3408.6032\Asshurt\Bunifu_UI_v1.5.3.dll | executable | |
MD5:E0EF2817EE5A7C8CD1EB837195768BD2 | SHA256:76E1D3EC95FDEF74ABAF90392DD6F4AA5E344922ABF11E572707287D467F2930 | |||
| 3408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3408.6032\Asshurt\MetroFramework.Design.dll | executable | |
MD5:AB4C3529694FC8D2427434825F71B2B8 | SHA256:0A4A96082E25767E4697033649B16C76A652E120757A2CECAB8092AD0D716B65 | |||
| 3408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3408.6032\Asshurt\Monaco\Monaco.html | html | |
MD5:999896134BD43CEFA865F37E514BA62F | SHA256:1ECDD9529EF5487F92736894D94FF680F6C32EE821615D29C0FC814F3A310B4A | |||
| 3408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3408.6032\Asshurt\Monaco\vs\basic-languages\csharp\csharp.js | text | |
MD5:F8F841D13C9220E15DCD6BC386B37BA2 | SHA256:6B3BE9A86EE8E3202F51745D94D24CC1EEFBCF7D9E6D94FBAF70146B084E835F | |||
| 3408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3408.6032\Asshurt\Monaco\vs\basic-languages\cpp\cpp.js | text | |
MD5:0A16509E6CD0155FB622E785CFE976C7 | SHA256:A7C2BEA7CA3D9E203A3A286735945FE010C8F4F8D46620386EE8BEFC6A78B32B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
6
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3336 | Asshurt.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
3336 | Asshurt.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrJdiQ%2Ficg9B19asFe73bPYs%2BreAQUdXGnGUgZvJ2d6kFH35TESHeZ03kCEFslzmkHxCZVZtM5DJmpVK0%3D | US | der | 313 b | whitelisted |
3336 | Asshurt.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.trust-provider.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEENSAj%2F6qJAfE5%2Fj9OXBRE4%3D | US | der | 471 b | whitelisted |
3336 | Asshurt.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrBBNpPfHTPX6Jy6BVzyBPnBWMnQQUPnQtH89FdQR%2BP8Cihz5MQ4NRE8YCEA6m%2Bvqf2Tko8%2BzIIJ9atpw%3D | US | der | 279 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3336 | Asshurt.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3336 | Asshurt.exe | 104.26.7.147:443 | wearedevs.net | Cloudflare Inc | US | suspicious |
3336 | Asshurt.exe | 104.26.6.147:443 | wearedevs.net | Cloudflare Inc | US | suspicious |
3336 | Asshurt.exe | 162.159.130.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
3336 | Asshurt.exe | 151.139.128.14:80 | ocsp.trust-provider.com | Highwinds Network Group, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wearedevs.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cdn.wearedevs.net |
| whitelisted |
cdn.discordapp.com |
| shared |
ocsp.trust-provider.com |
| whitelisted |
ocsp.comodoca4.com |
| whitelisted |