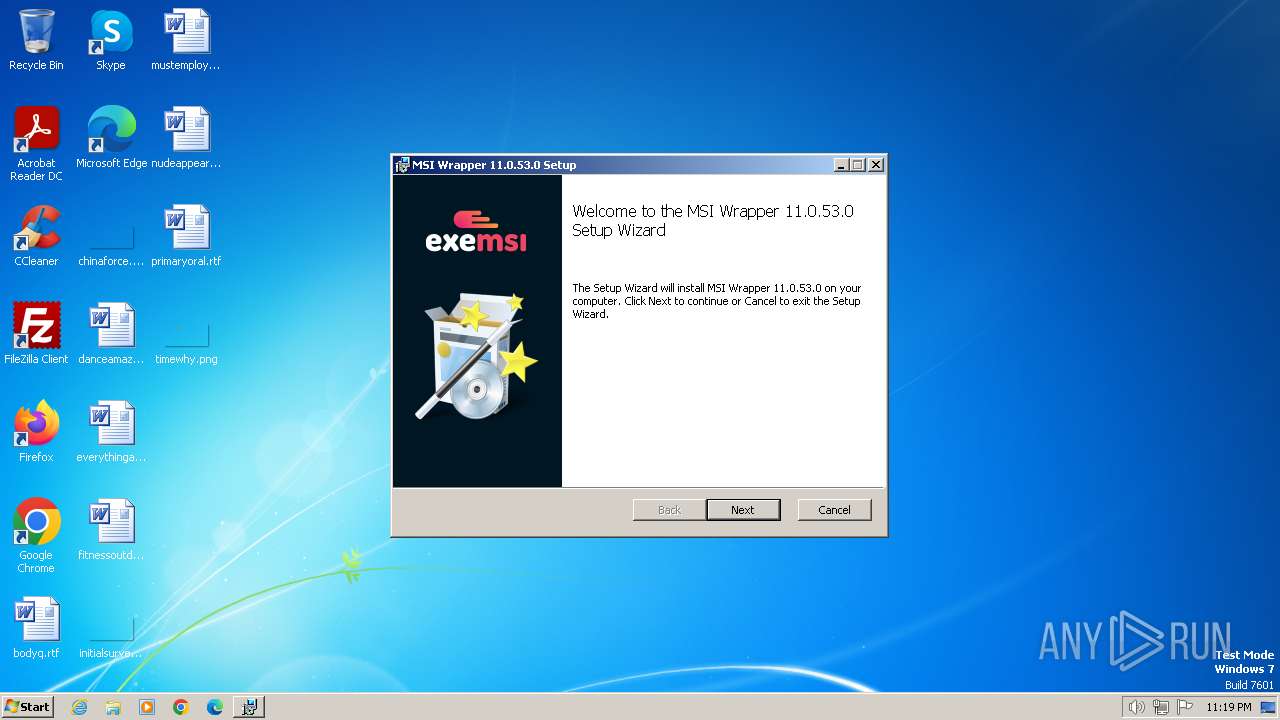
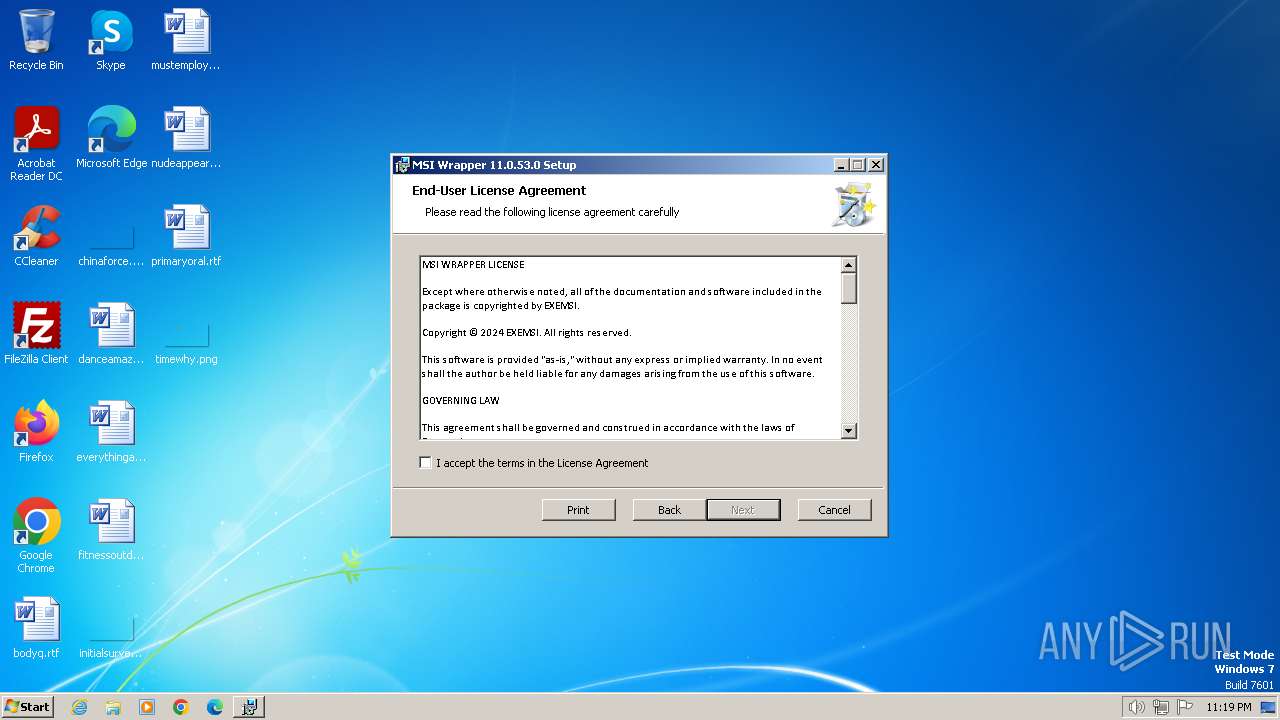
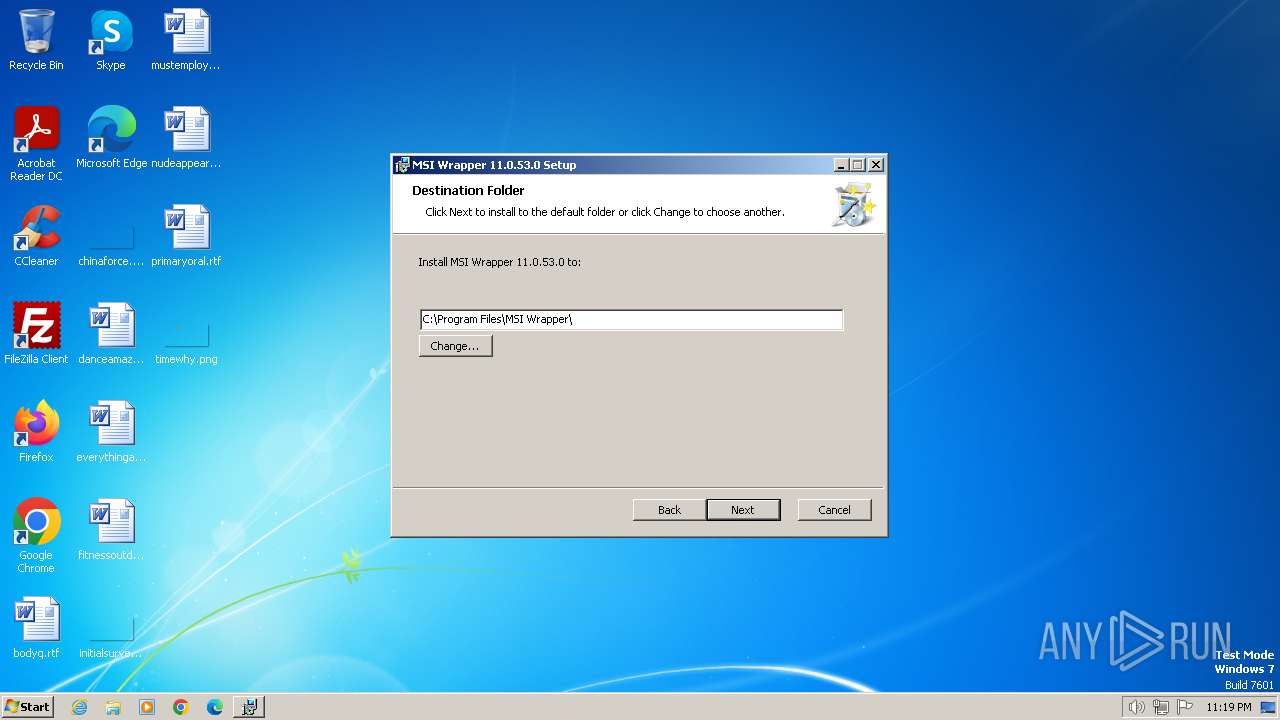
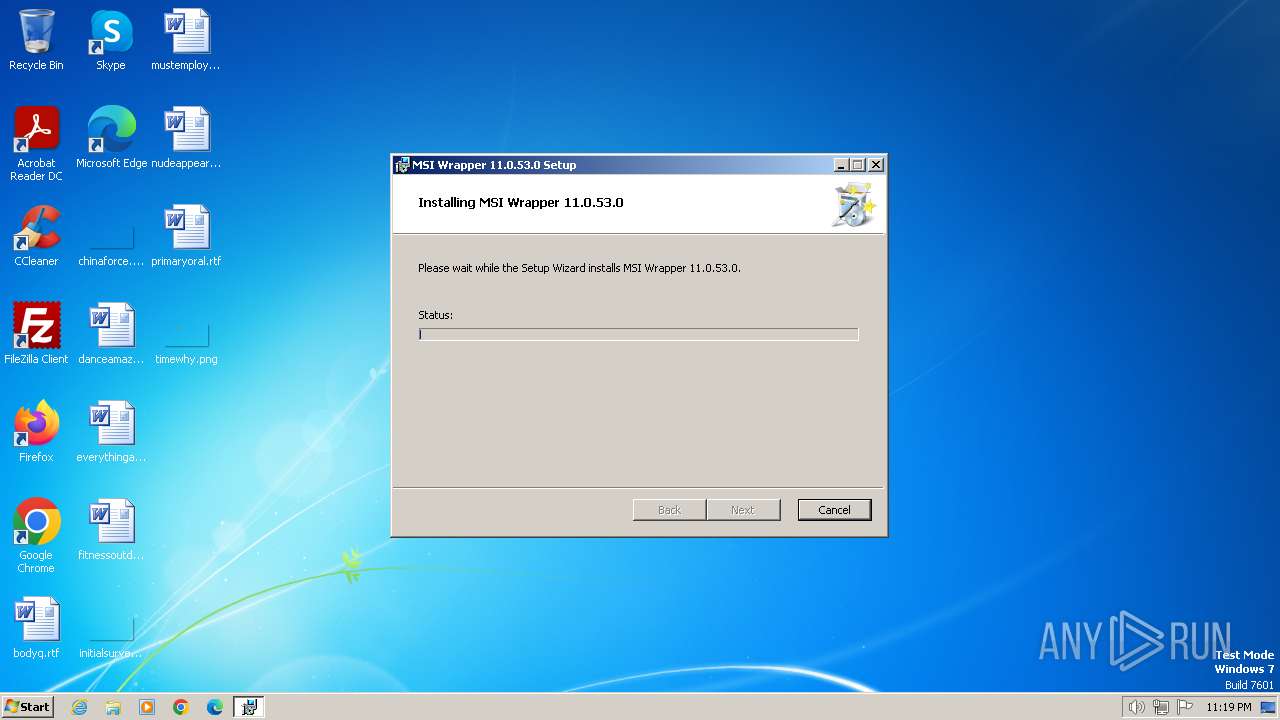
| File name: | MSI_Wrapper_11_0_53_0.msi |
| Full analysis: | https://app.any.run/tasks/a5ca90e0-b2d2-4e54-9d6c-141e3eb45e53 |
| Verdict: | Malicious activity |
| Analysis date: | February 11, 2024, 23:19:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: MSI Wrapper 11.0.53.0, Author: exemsi.com, Keywords: Installer, Comments: This installer database contains the logic and data required to install MSI Wrapper 11.0.53.0., Template: Intel;1033, Revision Number: {53F180E7-C069-41DE-8B16-13236ABB46BF}, Create Time/Date: Thu Jan 11 15:03:18 2024, Last Saved Time/Date: Thu Jan 11 15:03:18 2024, Number of Pages: 200, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | EC0025B211E98CE1444836BA6925CD69 |
| SHA1: | 59E2CB20348F29D4AEC0F4C6F2DC60A07F8A1ECF |
| SHA256: | E844501CEE4F76B4D6028C740650B33C56C120F79230FE60ED571C44D4E45756 |
| SSDEEP: | 98304:JF1KJizSgh6/nGVSLTt8H+uZ/gfQmFjggzahskl6dujA/8dzAzPyjnjsDSHJzYSX:m8c9b |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 2472)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 3708)
Reads the Internet Settings
- MsiWrapper.exe (PID: 584)
Reads settings of System Certificates
- MsiWrapper.exe (PID: 584)
INFO
Reads the software policy settings
- msiexec.exe (PID: 2472)
- MsiWrapper.exe (PID: 584)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2472)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2472)
Create files in a temporary directory
- MsiWrapper.exe (PID: 584)
Checks supported languages
- MsiWrapper.exe (PID: 584)
Reads the computer name
- MsiWrapper.exe (PID: 584)
Reads Environment values
- MsiWrapper.exe (PID: 584)
Reads the machine GUID from the registry
- MsiWrapper.exe (PID: 584)
Manual execution by a user
- MsiWrapper.exe (PID: 584)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | MSI Wrapper 11.0.53.0 |
| Author: | exemsi.com |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install MSI Wrapper 11.0.53.0. |
| Template: | Intel;1033 |
| RevisionNumber: | {53F180E7-C069-41DE-8B16-13236ABB46BF} |
| CreateDate: | 2024:01:11 15:03:18 |
| ModifyDate: | 2024:01:11 15:03:18 |
| Pages: | 200 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
54
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 584 | "C:\Program Files\MSI Wrapper\MsiWrapper.exe" | C:\Program Files\MSI Wrapper\MsiWrapper.exe | explorer.exe | ||||||||||||
User: admin Company: EXEMSI.COM Integrity Level: MEDIUM Description: MSI Wrapper Exit code: 0 Version: 11.0.53.0 Modules
| |||||||||||||||
| 2472 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\MSI_Wrapper_11_0_53_0.msi" | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3708 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
9 715
Read events
9 549
Write events
166
Delete events
0
Modification events
| (PID) Process: | (2472) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3708) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000004CDDCBE405DDA017C0E00006C0F0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3708) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000004CDDCBE405DDA017C0E0000F4070000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3708) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000004CDDCBE405DDA017C0E0000880D0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3708) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000004CDDCBE405DDA017C0E0000900C0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3708) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 40000000000000005E2FDFBE405DDA017C0E0000880D0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3708) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 40000000000000005E2FDFBE405DDA017C0E0000F4070000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3708) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000B891E1BE405DDA017C0E0000900C0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3708) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000B891E1BE405DDA017C0E00006C0F0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3708) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SwProvider_{b5946137-7b9f-4925-af80-51abd60b20d5} |
| Operation: | write | Name: | PROVIDER_BEGINPREPARE (Enter) |
Value: 40000000000000002E6F23C0405DDA017C0E00006C0F000001040000010000000000000000000000E4D1214AD09A1C45BF392B3D1C5433FB0000000000000000 | |||
Executable files
1
Suspicious files
3
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 584 | MsiWrapper.exe | C:\Users\admin\AppData\Local\Temp\Tar589B.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 2472 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI673.tmp | executable | |
MD5:4FDD16752561CF585FED1506914D73E0 | SHA256:AECD2D2FE766F6D439ACC2BBF1346930ECC535012CF5AD7B3273D2875237B7E7 | |||
| 584 | MsiWrapper.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:7D0ED13065A48B7A6F08591FADC2D8FA | SHA256:5759E345BD0531723B976964B49833EE797CEA3D266D4118B74CB181D58C2564 | |||
| 584 | MsiWrapper.exe | C:\Users\admin\AppData\Local\Temp\Cab589A.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 584 | MsiWrapper.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
34
DNS requests
38
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
584 | MsiWrapper.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1b2c67b9db6f7f0d | unknown | compressed | 65.2 Kb | unknown |
1352 | msedge.exe | GET | 301 | 77.111.240.51:80 | http://www.exemsi.com/dispatch/?action=GettingStarted | unknown | html | 262 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2364 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
1352 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1352 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1352 | msedge.exe | 77.111.240.51:80 | www.exemsi.com | One.com A/S | DK | unknown |
1352 | msedge.exe | 77.111.240.51:443 | www.exemsi.com | One.com A/S | DK | unknown |
1352 | msedge.exe | 142.250.186.138:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.exemsi.com |
| unknown |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.youtube.com |
| whitelisted |
i.ytimg.com |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |
static.doubleclick.net |
| whitelisted |