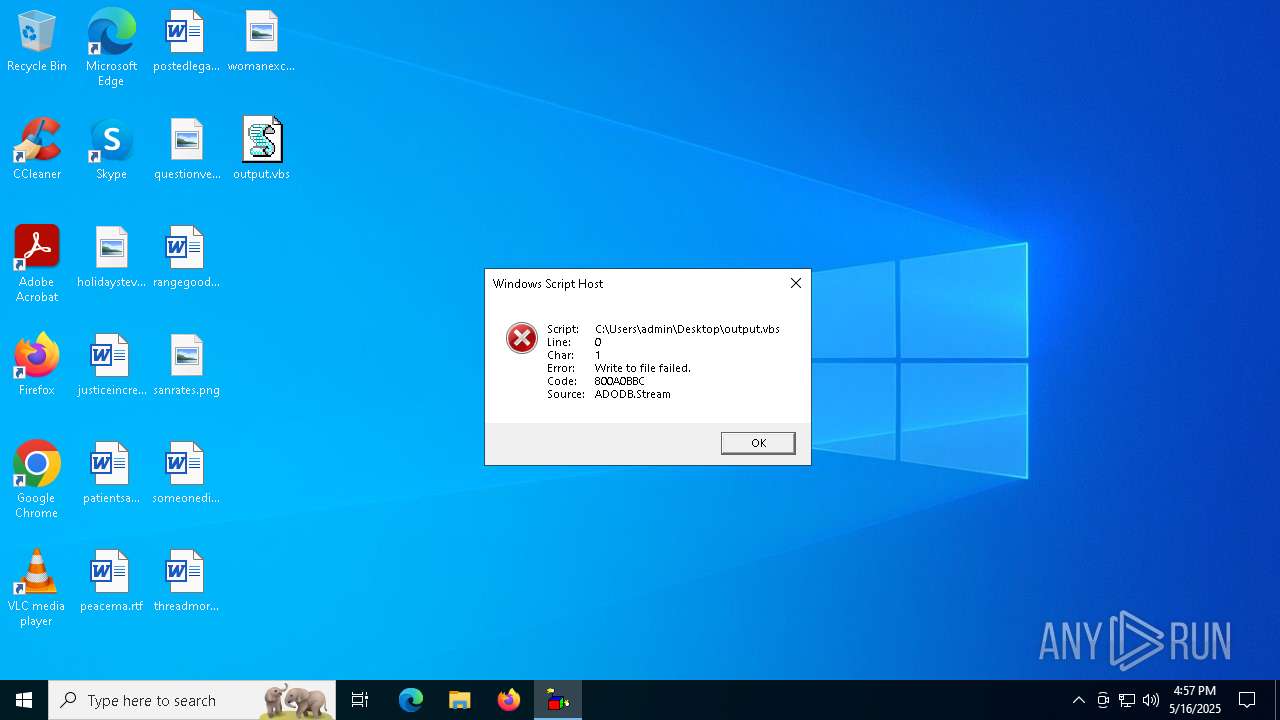
| File name: | output.vbs |
| Full analysis: | https://app.any.run/tasks/27429802-4957-4522-b36b-fff93023704c |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 16:56:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | EEC5F3AB050EDDE074CEA53CB0A54247 |
| SHA1: | A351A62C87FCE95B2A694ED10C29F51D78B044B7 |
| SHA256: | E81F6D232E4E4185B4228896799096CCBA533D4358A0FBE981FD140FA48BC47E |
| SSDEEP: | 12288:f/reZGLqKiw9/8ZYrZpSxbFDYju93jjzsBQ+KzGhNv:6sqjo5ZIVyyjYQ5Gr |
MALICIOUS
Detects the decoding of a binary file from Base64 (SCRIPT)
- wscript.exe (PID: 5072)
- wscript.exe (PID: 5176)
Uses base64 encoding (SCRIPT)
- wscript.exe (PID: 5072)
- wscript.exe (PID: 5176)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 5072)
- wscript.exe (PID: 5176)
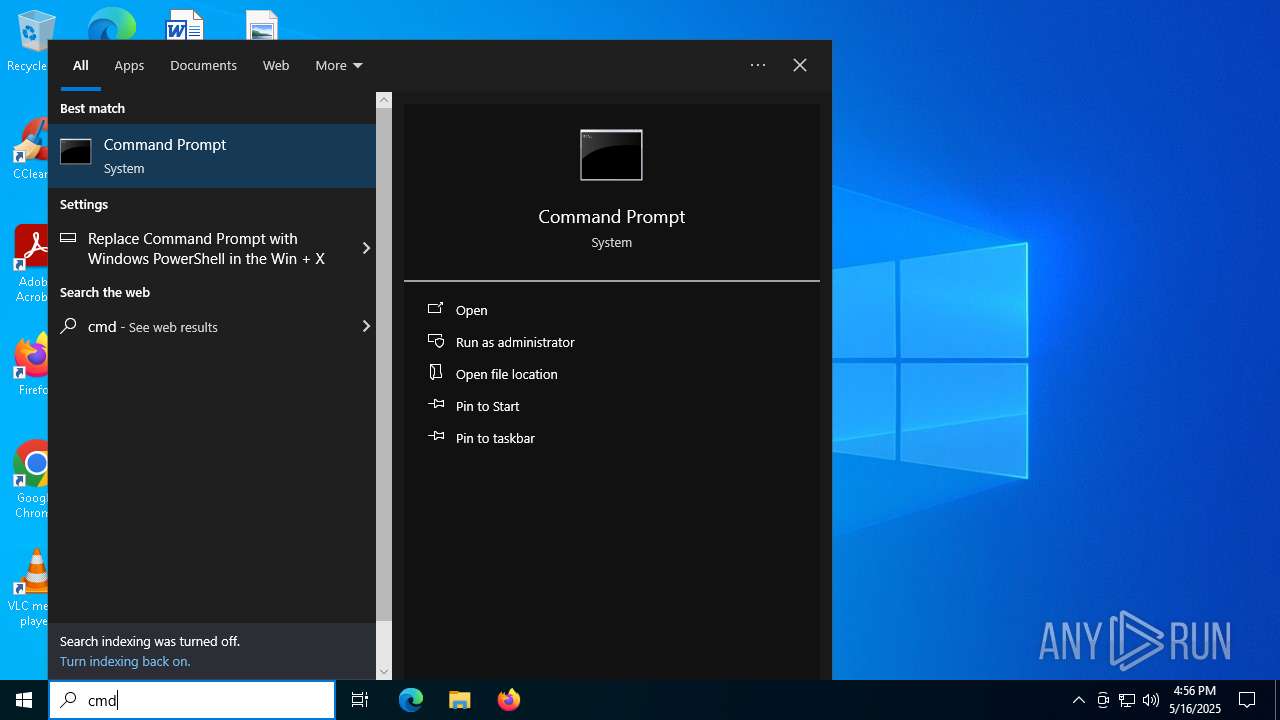
Runs shell command (SCRIPT)
- wscript.exe (PID: 5072)
- wscript.exe (PID: 5176)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 5072)
- wscript.exe (PID: 5176)
Starts a Microsoft application from unusual location
- cmd.exe (PID: 5548)
Saves data to a binary file (SCRIPT)
- wscript.exe (PID: 5072)
- wscript.exe (PID: 5176)
The process creates files with name similar to system file names
- wscript.exe (PID: 5072)
Executable content was dropped or overwritten
- wscript.exe (PID: 5072)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 5176)
- wscript.exe (PID: 5072)
Sets XML DOM element text (SCRIPT)
- wscript.exe (PID: 5176)
- wscript.exe (PID: 5072)
Process drops legitimate windows executable
- wscript.exe (PID: 5072)
INFO
Potential library load (Base64 Encoded 'LoadLibrary')
- wscript.exe (PID: 5072)
Potential access to remote process (Base64 Encoded 'OpenProcess')
- wscript.exe (PID: 5072)
Manual execution by a user
- wscript.exe (PID: 5176)
- cmd.exe (PID: 5176)
Checks supported languages
- cmd.exe (PID: 5548)
The sample compiled with english language support
- wscript.exe (PID: 5072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
136
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4756 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5072 | "C:\WINDOWS\System32\WScript.exe" C:\Users\admin\Desktop\output.vbs | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5176 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5176 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\output.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5548 | "C:\Users\admin\AppData\Local\Temp\cmd.exe" | C:\Users\admin\AppData\Local\Temp\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6028 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6044 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6372 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 043
Read events
2 033
Write events
10
Delete events
0
Modification events
| (PID) Process: | (5072) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A7803901000062B06A59D2B415429F74E9109B0A8153BB000000 | |||
| (PID) Process: | (5072) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E232827701000060B81DB4E464D2119906E49FADC173CABC0000006078A409B011A54DAFA526D86198A7803901000010901EF8A46ECE11A7FF00AA003CA9F696010000 | |||
| (PID) Process: | (5072) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E232827701000060B81DB4E464D2119906E49FADC173CABC0000006078A409B011A54DAFA526D86198A7803901000062B06A59D2B415429F74E9109B0A8153BB000000 | |||
| (PID) Process: | (5072) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D56040000BD0E0C47735D584D9CEDE91E22E232827701000060B81DB4E464D2119906E49FADC173CABC0000006078A409B011A54DAFA526D86198A7803901000010901EF8A46ECE11A7FF00AA003CA9F696010000 | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5072 | wscript.exe | C:\Users\admin\AppData\Local\Temp\cmd.exe | executable | |
MD5:2B40C98ED0F7A1D3B091A3E8353132DC | SHA256:BADF4752413CB0CBDC03FB95820CA167F0CDC63B597CCDB5EF43111180E088B0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
24
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4608 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4608 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |