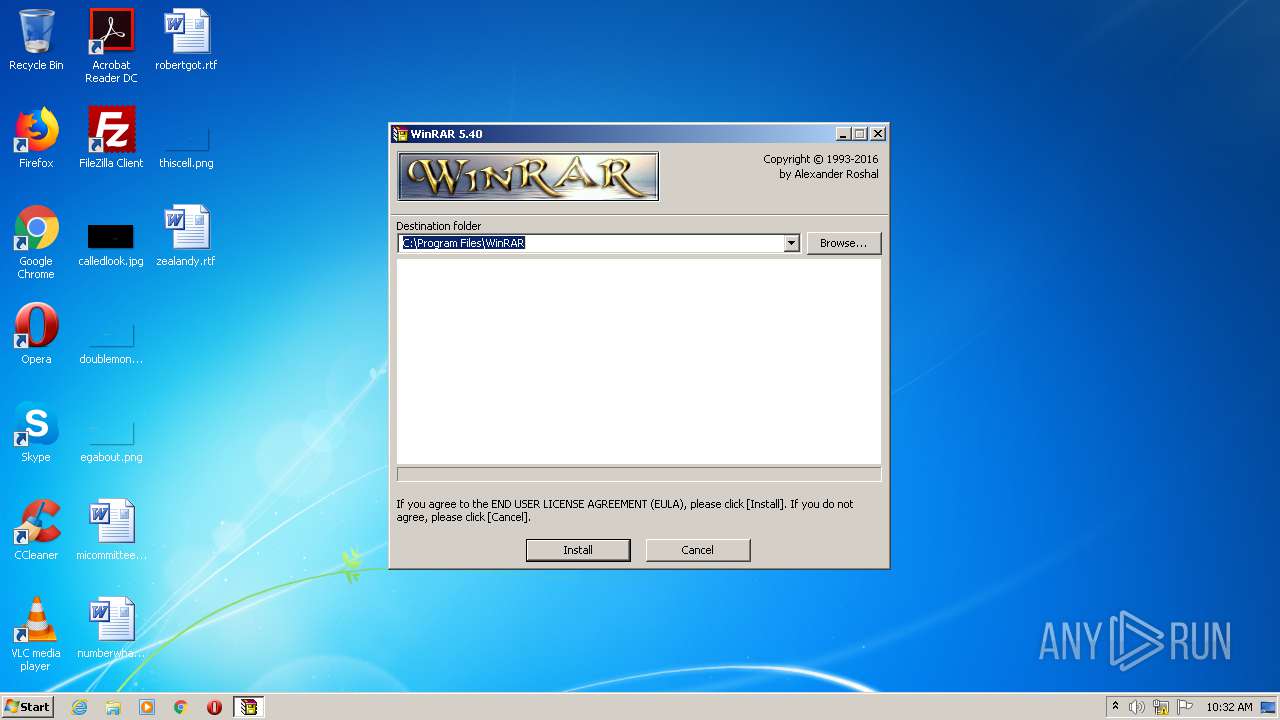
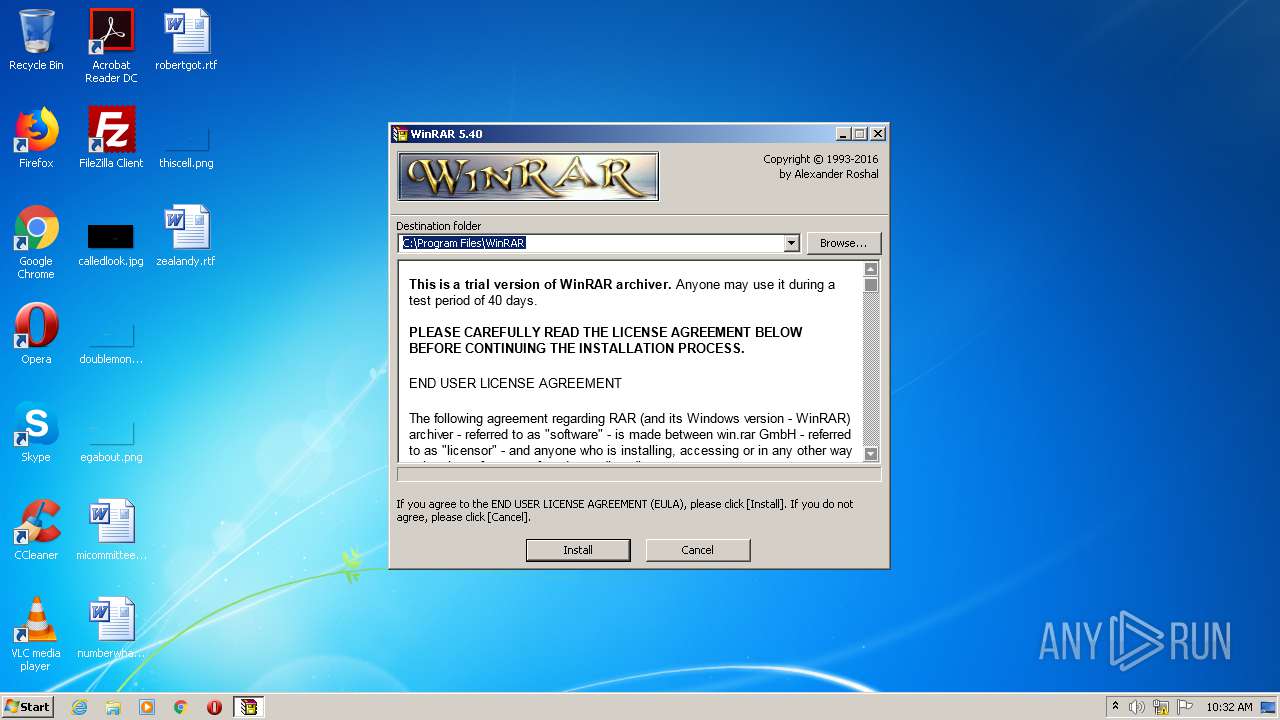
| File name: | wrar540.exe |
| Full analysis: | https://app.any.run/tasks/799e0a1e-4658-4839-8ba2-230f293b7795 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 09:32:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 5D930FA790EED4B6C7DD22262A015723 |
| SHA1: | 211A19CA4EC3C7562C9844FE6C42E66A521B8BD4 |
| SHA256: | E81BAA5C2D2771CBAD2D168ECF278F865DC2DE38983C6A169D583949375EA735 |
| SSDEEP: | 49152:/Dkie7RK2bx22GpCmYEtmE9T8RtiwcwBbo28T9holoPAGP:r87RK2b3G5YEtmE9T+UwcUq9h/AK |
MALICIOUS
Loads the Task Scheduler COM API
- CCleaner.exe (PID: 2264)
Actions looks like stealing of personal data
- CCleaner.exe (PID: 3896)
SUSPICIOUS
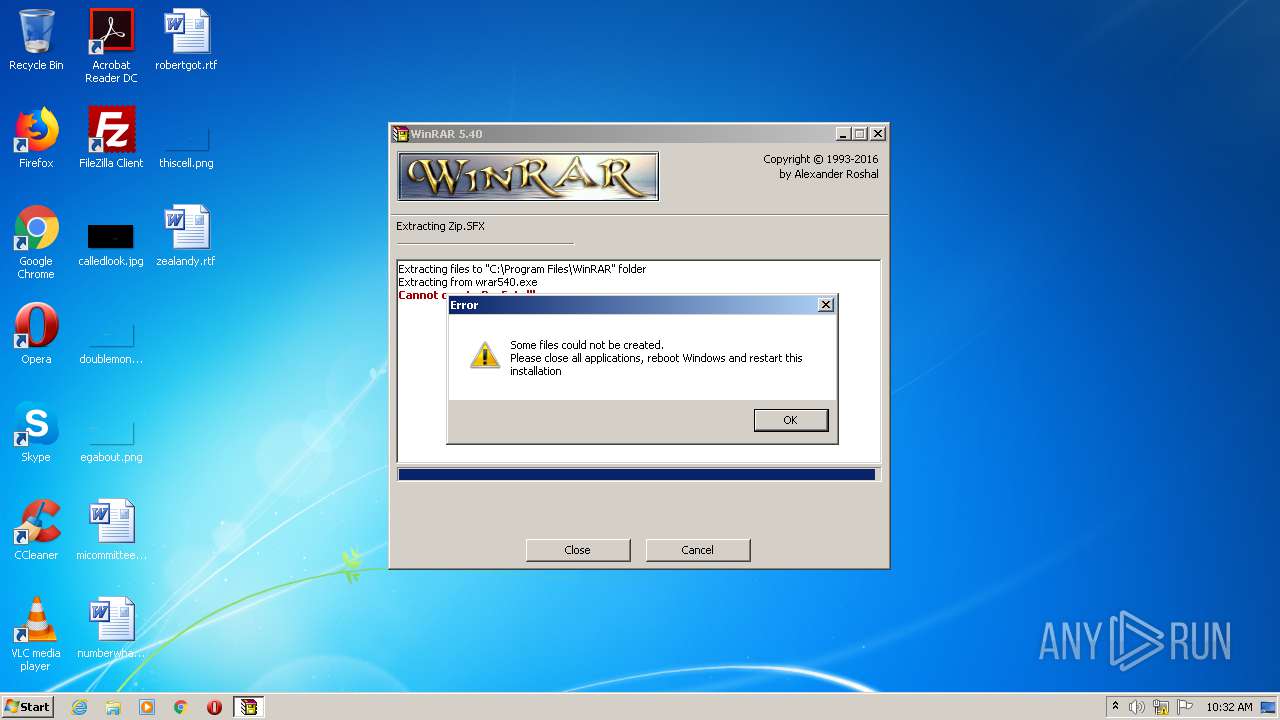
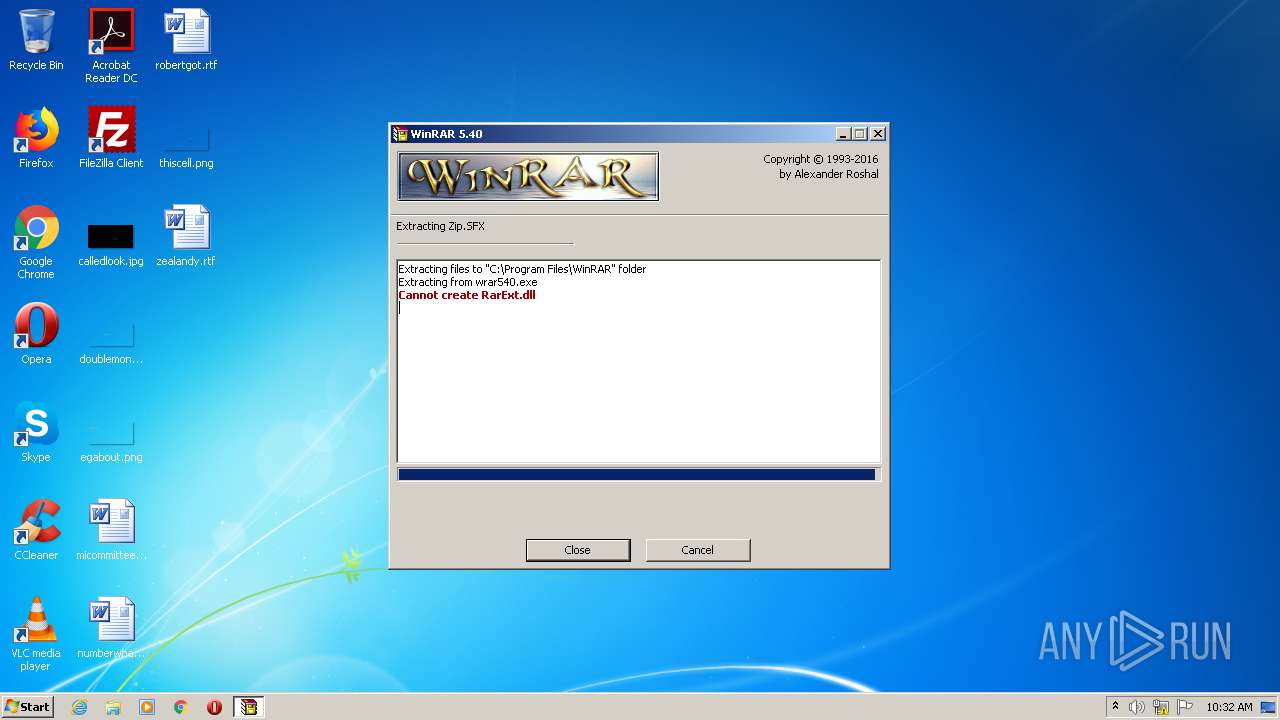
Creates files in the program directory
- wrar540.exe (PID: 3892)
Reads Internet Cache Settings
- wrar540.exe (PID: 3892)
- CCleaner.exe (PID: 3896)
Executable content was dropped or overwritten
- wrar540.exe (PID: 3892)
Reads internet explorer settings
- wrar540.exe (PID: 3892)
- CCleaner.exe (PID: 3896)
Executed via Task Scheduler
- CCleaner.exe (PID: 3896)
Low-level read access rights to disk partition
- CCleaner.exe (PID: 3896)
Creates files in the user directory
- CCleaner.exe (PID: 3896)
Starts Internet Explorer
- CCleaner.exe (PID: 3896)
INFO
Manual execution by user
- CCleaner.exe (PID: 2264)
Reads settings of System Certificates
- CCleaner.exe (PID: 3896)
- iexplore.exe (PID: 3380)
Reads Internet Cache Settings
- iexplore.exe (PID: 3512)
- iexplore.exe (PID: 3380)
Application launched itself
- iexplore.exe (PID: 3512)
Changes internet zones settings
- iexplore.exe (PID: 3512)
Reads internet explorer settings
- iexplore.exe (PID: 3380)
Creates files in the user directory
- iexplore.exe (PID: 3380)
Changes settings of System certificates
- iexplore.exe (PID: 3380)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:08:14 21:15:59+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 186880 |
| InitializedDataSize: | 204800 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1c445 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 14-Aug-2016 19:15:59 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 14-Aug-2016 19:15:59 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0002D988 | 0x0002DA00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.70795 |
.rdata | 0x0002F000 | 0x00009930 | 0x00009A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.13601 |
.data | 0x00039000 | 0x0001F8A0 | 0x00000C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.26031 |
.gfids | 0x00059000 | 0x000000F0 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.13823 |
.rsrc | 0x0005A000 | 0x000068A0 | 0x00006A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.62086 |
.reloc | 0x00061000 | 0x00001F48 | 0x00002000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.63002 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.26297 | 1872 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 4.38314 | 1384 | UNKNOWN | English - United States | RT_ICON |
3 | 3.38848 | 744 | UNKNOWN | English - United States | RT_ICON |
4 | 3.48636 | 296 | UNKNOWN | English - United States | RT_ICON |
7 | 3.11482 | 376 | UNKNOWN | English - United States | RT_STRING |
8 | 3.14988 | 436 | UNKNOWN | English - United States | RT_STRING |
9 | 3.16863 | 434 | UNKNOWN | English - United States | RT_STRING |
10 | 2.99727 | 326 | UNKNOWN | English - United States | RT_STRING |
11 | 3.06856 | 470 | UNKNOWN | English - United States | RT_STRING |
12 | 2.86396 | 214 | UNKNOWN | English - United States | RT_STRING |
Imports
COMCTL32.dll (delay-loaded) |
KERNEL32.dll |
Total processes
47
Monitored processes
6
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2264 | "C:\Program Files\CCleaner\CCleaner.exe" | C:\Program Files\CCleaner\CCleaner.exe | — | explorer.exe | |||||||||||
User: admin Company: Piriform Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
| 3228 | "C:\Users\admin\AppData\Local\Temp\wrar540.exe" | C:\Users\admin\AppData\Local\Temp\wrar540.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3380 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3512 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3512 | "C:\Program Files\Internet Explorer\iexplore.exe" http://www.piriform.com/ccleaner/update?a=0&v=5.35.6210&l=1033&o=6.1W3&t=4&au=1 | C:\Program Files\Internet Explorer\iexplore.exe | — | CCleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3892 | "C:\Users\admin\AppData\Local\Temp\wrar540.exe" | C:\Users\admin\AppData\Local\Temp\wrar540.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 9 Modules
| |||||||||||||||
| 3896 | "C:\Program Files\CCleaner\CCleaner.exe" /uac | C:\Program Files\CCleaner\CCleaner.exe | taskeng.exe | ||||||||||||
User: admin Company: Piriform Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
Total events
1 177
Read events
881
Write events
296
Delete events
0
Modification events
| (PID) Process: | (3892) wrar540.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3892) wrar540.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3892) wrar540.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3892) wrar540.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3892) wrar540.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3892) wrar540.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR SFX |
| Operation: | write | Name: | C%%Program Files%WinRAR |
Value: C:\Program Files\WinRAR | |||
| (PID) Process: | (3896) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | NewVersion |
Value: | |||
| (PID) Process: | (3896) CCleaner.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3896) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3896) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
Executable files
10
Suspicious files
92
Text files
81
Unknown types
45
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3896 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\0Y4H3EDYEBN1ZEOB5MTP.temp | — | |
MD5:— | SHA256:— | |||
| 3896 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ed7a5cc3cca8d52a.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3892 | wrar540.exe | C:\Program Files\WinRAR\Descript.ion | text | |
MD5:73E2E911B7730A92C04298EC770B0AB6 | SHA256:29BF0E22BA729921958BBE4DC42D8BF688CCCFBFEAC6EF68B79674023B05D01F | |||
| 3892 | wrar540.exe | C:\Program Files\WinRAR\Rar.txt | text | |
MD5:AF65D295F498939287D335875661E38C | SHA256:C8E739A280ED99A2031EF532663471F1F74408E915A24A7F867284F178097108 | |||
| 3892 | wrar540.exe | C:\Program Files\WinRAR\ReadMe.txt | text | |
MD5:6A697FE386885EA78AB05AD1BD4A96EB | SHA256:25C6C5F336B404579889549B10A45F5E32CE5844A5A5A29075168D460D025BD2 | |||
| 3892 | wrar540.exe | C:\Program Files\WinRAR\Uninstall.lst | text | |
MD5:DC20A41DD5976945AD2FF6A742BC26DD | SHA256:548291EC78A04CB9B1606858A6913ECCF215C5B57F05E510EC82B4A1BDCFEF8C | |||
| 3892 | wrar540.exe | C:\Program Files\WinRAR\License.txt | text | |
MD5:672064CF19DB0B083B981CF0BE7662B0 | SHA256:9FC8AA33CCAFA04C1CE4C0A61047B341297D720ADAB1B77F67B5FE59F43BB59F | |||
| 3896 | CCleaner.exe | C:\Users\admin\AppData\Local\Temp\Tar9D9D.tmp | — | |
MD5:— | SHA256:— | |||
| 3892 | wrar540.exe | C:\Program Files\WinRAR\WhatsNew.txt | text | |
MD5:9F49544A844B7652D5765EEF0A6028AE | SHA256:0D35A441F492BD5FC5A216B475DFF0193DA933E946E984E5D53649A12D215CA2 | |||
| 3892 | wrar540.exe | C:\Program Files\WinRAR\7zxa.dll | executable | |
MD5:9DF6E520FA019FD34F92F3F769910756 | SHA256:C4932C914FC979C1614E39D9D514357BDED665F24F491D3FE8C07B0160E08C04 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
97
DNS requests
38
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3896 | CCleaner.exe | GET | 301 | 151.101.0.64:80 | http://www.piriform.com/auto?a=0&p=cc&v=5.35.6210&l=1033&lk=&mk=IJR6-W5SV-5KYR-QBZD-6BY4-RN5Z-WAV9-RVK2-HZ8S&o=6.1W3&au=1&mx=97B7721C4994E2556FF6A439510F665DB45337A341A47E15F4997584423BF714&gu=00000000-0000-4000-8000-d6f7f2be5127 | US | — | — | whitelisted |
3380 | iexplore.exe | GET | 301 | 151.101.0.64:80 | http://www.piriform.com/ccleaner/update?a=0&v=5.35.6210&l=1033&o=6.1W3&t=4&au=1 | US | — | — | whitelisted |
3896 | CCleaner.exe | GET | 200 | 151.101.2.109:80 | http://license.piriform.com/verify/?p=ccpro&c=cc&cv=5.35.6210&l=1033&lk=CJ9T-J7CU-SPNV-GWMB-WBEC&mk=IJR6-W5SV-5KYR-QBZD-6BY4-RN5Z-WAV9-RVK2-HZ8S&mx=97B7721C4994E2556FF6A439510F665DB45337A341A47E15F4997584423BF714&gu=00000000-0000-4000-8000-d6f7f2be5127 | US | text | 14 b | whitelisted |
3896 | CCleaner.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/ME8wTTBLMEkwRzAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDkbwjNvPLFRm7zMB3V80 | US | der | 1.49 Kb | whitelisted |
3380 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
3896 | CCleaner.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/MEwwSjBIMEYwRDAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCCwQAAAAAAURO8EJH | US | der | 1.49 Kb | whitelisted |
3380 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
3380 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCECiWpPQxRDpPAgAAAAB8NWE%3D | US | der | 471 b | whitelisted |
3380 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
3380 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAtb9ltrp%2FvQiykNkEU33uA%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3380 | iexplore.exe | 104.75.88.112:443 | s7.addthis.com | Akamai Technologies, Inc. | NL | suspicious |
3380 | iexplore.exe | 216.58.208.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3380 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3380 | iexplore.exe | 142.250.74.195:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3896 | CCleaner.exe | 151.101.0.64:80 | www.piriform.com | Fastly | US | whitelisted |
3896 | CCleaner.exe | 151.101.0.64:443 | www.piriform.com | Fastly | US | whitelisted |
3896 | CCleaner.exe | 151.101.2.202:443 | www.ccleaner.com | Fastly | US | suspicious |
3896 | CCleaner.exe | 104.18.21.226:80 | ocsp.globalsign.com | Cloudflare Inc | US | shared |
3896 | CCleaner.exe | 104.18.20.226:80 | ocsp.globalsign.com | Cloudflare Inc | US | shared |
3896 | CCleaner.exe | 151.101.2.109:443 | license.piriform.com | Fastly | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.piriform.com |
| whitelisted |
www.ccleaner.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
license.piriform.com |
| whitelisted |
s1.pir.fm |
| suspicious |
www.google.com |
| malicious |
s7.addthis.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3380 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3380 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |