| File name: | Here.zip |
| Full analysis: | https://app.any.run/tasks/a9d3c4ef-e787-4589-961b-35c9e7b02962 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2020, 18:19:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 433D2BA266B252EE7169C1332EA3C70D |
| SHA1: | DA2574BAA71AE19B63BD74FD004D416AAFDA0917 |
| SHA256: | E7EBCDB71B394BBEB7C7E57AE45CFEF5E6CE37FCCA9E38CF94CBF11B12EF9938 |
| SSDEEP: | 6:5jq9hnRsPs6PoyhRzvHpoDjQB2Vd2hwh97yVZKhxxBzxq918n5jQBZ/z7tz:5jqXWwyhR9skB2ehQ9yVZKhxzM386Bjz |
MALICIOUS
No malicious indicators.SUSPICIOUS
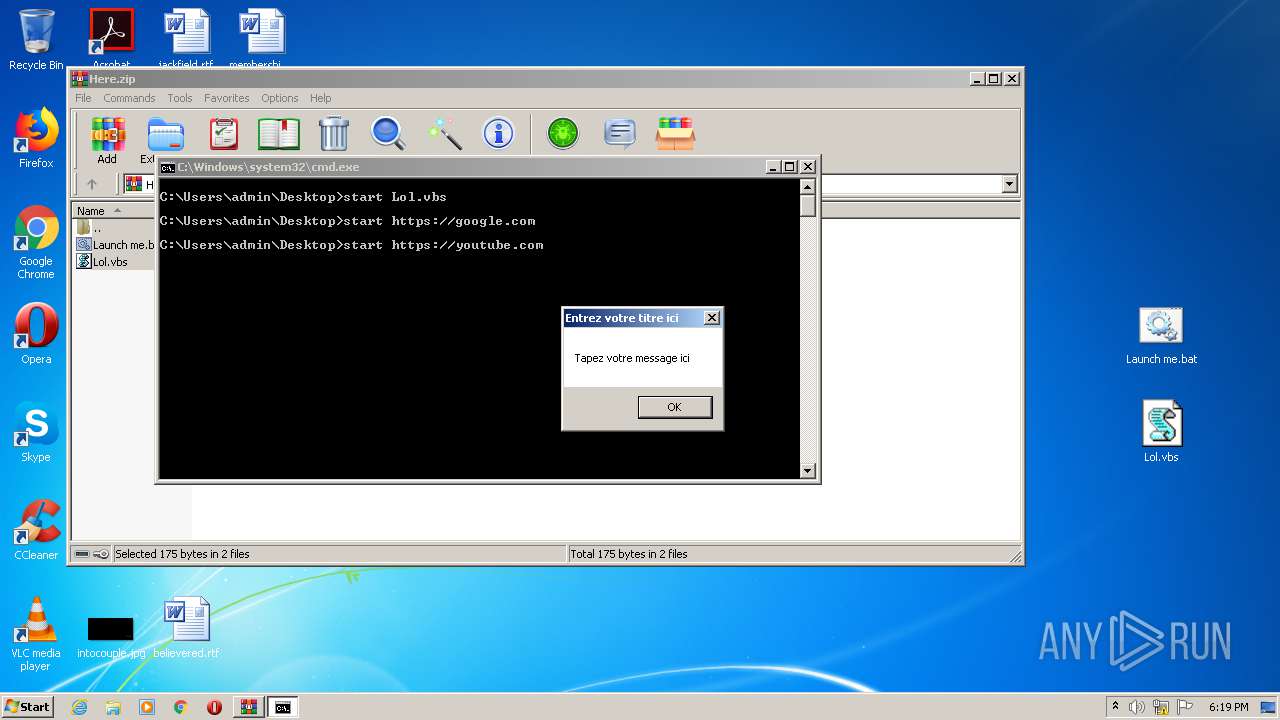
Starts Internet Explorer
- cmd.exe (PID: 2848)
Executes scripts
- cmd.exe (PID: 2848)
INFO
Manual execution by user
- cmd.exe (PID: 2848)
Changes internet zones settings
- iexplore.exe (PID: 3636)
- iexplore.exe (PID: 1852)
- iexplore.exe (PID: 4072)
- iexplore.exe (PID: 1516)
- iexplore.exe (PID: 2148)
- iexplore.exe (PID: 2660)
- iexplore.exe (PID: 756)
Application launched itself
- iexplore.exe (PID: 2148)
- iexplore.exe (PID: 3636)
- iexplore.exe (PID: 2660)
- iexplore.exe (PID: 1852)
- iexplore.exe (PID: 1516)
- iexplore.exe (PID: 4072)
- iexplore.exe (PID: 756)
Reads settings of System Certificates
- iexplore.exe (PID: 3128)
- iexplore.exe (PID: 1484)
- iexplore.exe (PID: 2464)
- iexplore.exe (PID: 2672)
- iexplore.exe (PID: 3692)
- iexplore.exe (PID: 2484)
- iexplore.exe (PID: 3636)
- iexplore.exe (PID: 556)
- iexplore.exe (PID: 3660)
- iexplore.exe (PID: 756)
- iexplore.exe (PID: 4588)
- iexplore.exe (PID: 2660)
- iexplore.exe (PID: 1516)
- iexplore.exe (PID: 4784)
- iexplore.exe (PID: 2348)
- iexplore.exe (PID: 1852)
- iexplore.exe (PID: 6092)
- iexplore.exe (PID: 4072)
- iexplore.exe (PID: 2148)
Reads internet explorer settings
- iexplore.exe (PID: 1484)
- iexplore.exe (PID: 2672)
- iexplore.exe (PID: 3612)
- iexplore.exe (PID: 2484)
- iexplore.exe (PID: 1652)
- iexplore.exe (PID: 2508)
- iexplore.exe (PID: 2572)
- iexplore.exe (PID: 2056)
- iexplore.exe (PID: 3660)
- iexplore.exe (PID: 556)
- iexplore.exe (PID: 4784)
- iexplore.exe (PID: 5780)
- iexplore.exe (PID: 4864)
- iexplore.exe (PID: 4588)
- iexplore.exe (PID: 1392)
- iexplore.exe (PID: 3692)
Creates files in the user directory
- iexplore.exe (PID: 2464)
- iexplore.exe (PID: 3128)
- iexplore.exe (PID: 1484)
- iexplore.exe (PID: 2484)
- iexplore.exe (PID: 2508)
Changes settings of System certificates
- iexplore.exe (PID: 3636)
- iexplore.exe (PID: 2148)
- iexplore.exe (PID: 1516)
- iexplore.exe (PID: 756)
- iexplore.exe (PID: 2660)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2148)
- iexplore.exe (PID: 3636)
- iexplore.exe (PID: 1516)
- iexplore.exe (PID: 756)
- iexplore.exe (PID: 2660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
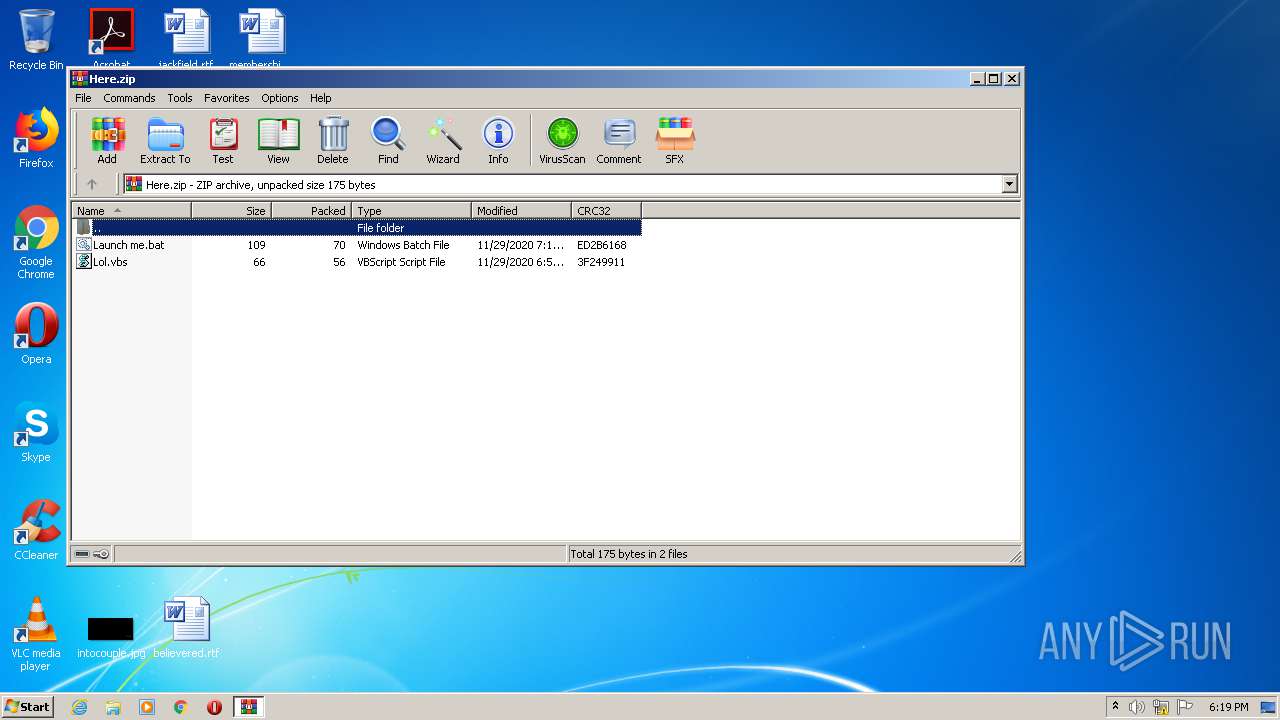
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:11:29 19:19:00 |
| ZipCRC: | 0xed2b6168 |
| ZipCompressedSize: | 70 |
| ZipUncompressedSize: | 109 |
| ZipFileName: | Launch me.bat |
Total processes
103
Monitored processes
67
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1516 CREDAT:2692382 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 584 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\Lol.vbs" | C:\Windows\System32\WScript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 756 | "C:\Program Files\Internet Explorer\iexplore.exe" https://google.com/ | C:\Program Files\Internet Explorer\iexplore.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 852 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\Lol.vbs" | C:\Windows\System32\WScript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1516 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1484 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3636 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1516 | "C:\Program Files\Internet Explorer\iexplore.exe" https://youtube.com/ | C:\Program Files\Internet Explorer\iexplore.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1652 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1516 CREDAT:3216647 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1708 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\Lol.vbs" | C:\Windows\System32\WScript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\Internet Explorer\iexplore.exe" https://youtube.com/ | C:\Program Files\Internet Explorer\iexplore.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
10 353
Read events
8 528
Write events
1 817
Delete events
8
Modification events
| (PID) Process: | (2476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2476) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Here.zip | |||
| (PID) Process: | (2476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2476) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (2476) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\wshext.dll,-4802 |
Value: VBScript Script File | |||
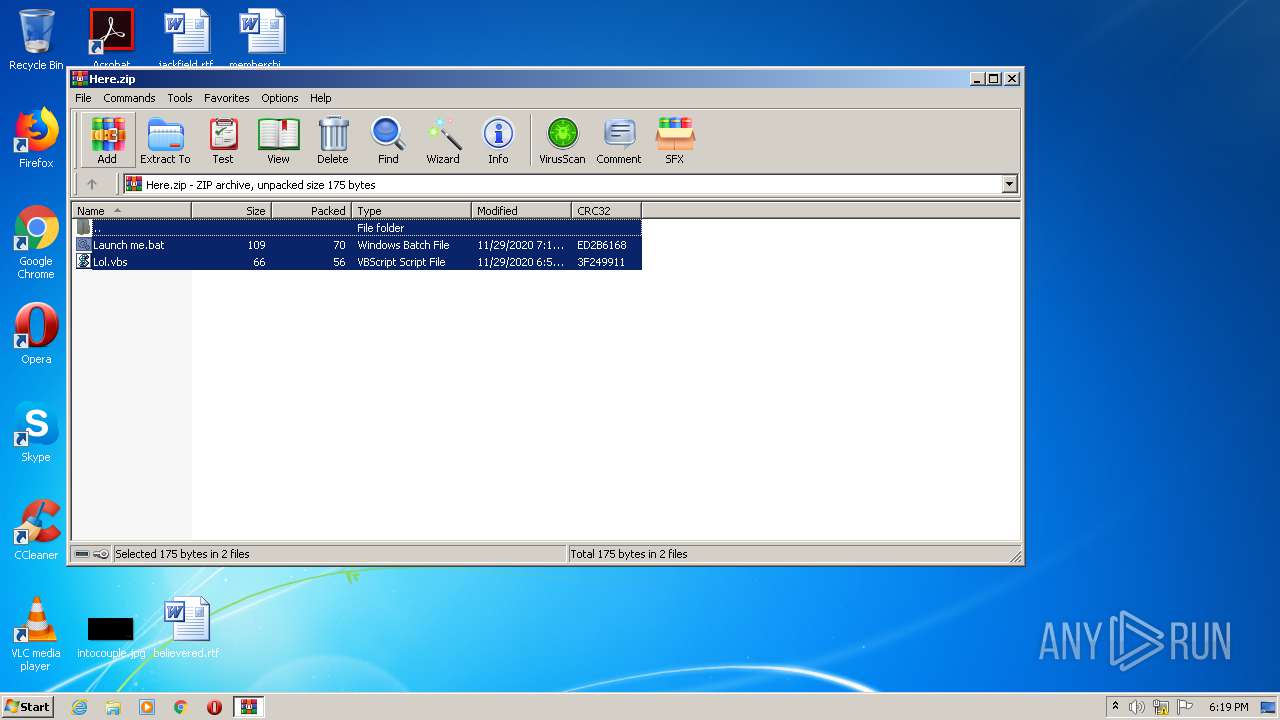
Executable files
0
Suspicious files
50
Text files
285
Unknown types
36
Dropped files
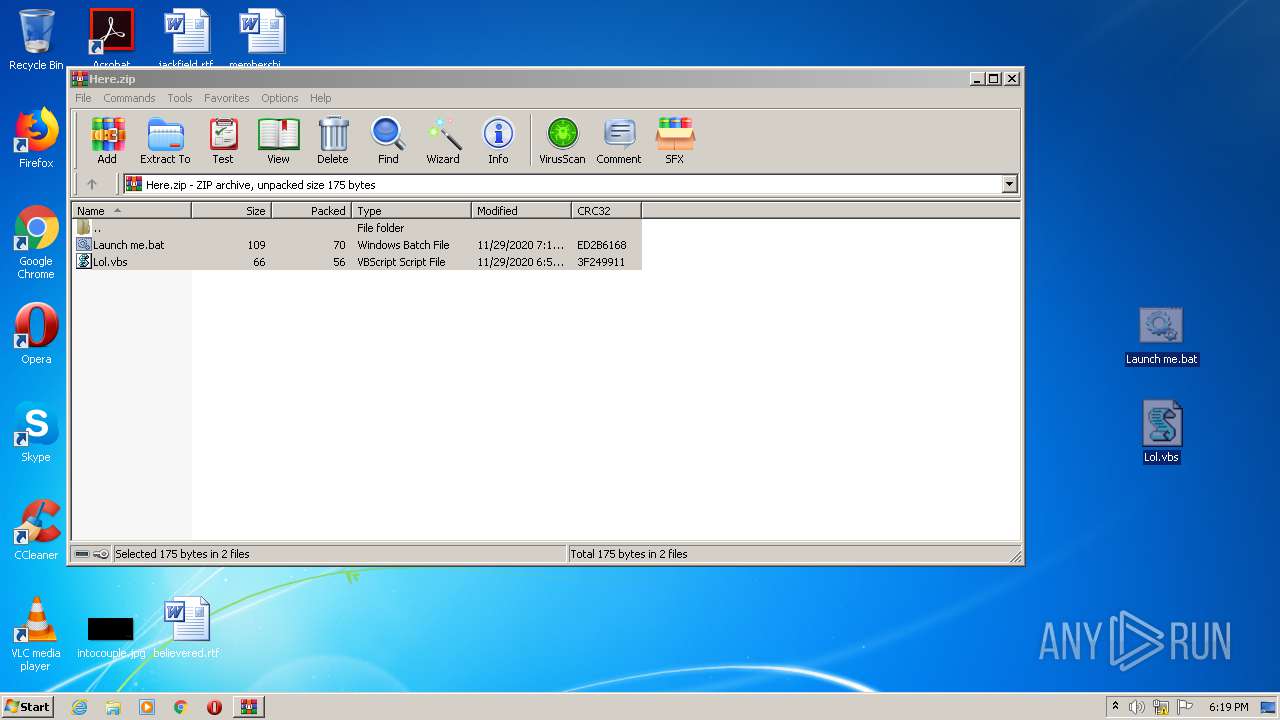
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2476 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2476.31585\Launch me.bat | — | |
MD5:— | SHA256:— | |||
| 2476 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2476.31585\Lol.vbs | — | |
MD5:— | SHA256:— | |||
| 3636 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 1852 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[3].ico | — | |
MD5:— | SHA256:— | |||
| 1852 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2148 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3128 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab355A.tmp | — | |
MD5:— | SHA256:— | |||
| 3128 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar355B.tmp | — | |
MD5:— | SHA256:— | |||
| 2464 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab3673.tmp | — | |
MD5:— | SHA256:— | |||
| 2464 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar3674.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
303
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2464 | iexplore.exe | GET | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQD76E8xQFZstgIAAAAAgFWS | US | der | 472 b | whitelisted |
3128 | iexplore.exe | GET | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQD76E8xQFZstgIAAAAAgFWS | US | der | 472 b | whitelisted |
2464 | iexplore.exe | GET | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDliVAU%2F6ZWzwIAAAAAgFX%2B | US | der | 472 b | whitelisted |
2508 | iexplore.exe | GET | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDa2MTpyZrzlQgAAAAAYth4 | US | der | 472 b | whitelisted |
2464 | iexplore.exe | GET | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQD76E8xQFZstgIAAAAAgFWS | US | der | 472 b | whitelisted |
1484 | iexplore.exe | GET | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDgM%2F2Oalb9SggAAAAAYth0 | US | der | 472 b | whitelisted |
1484 | iexplore.exe | GET | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDgM%2F2Oalb9SggAAAAAYth0 | US | der | 472 b | whitelisted |
2464 | iexplore.exe | GET | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQD76E8xQFZstgIAAAAAgFWS | US | der | 472 b | whitelisted |
2464 | iexplore.exe | GET | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDliVAU%2F6ZWzwIAAAAAgFX%2B | US | der | 472 b | whitelisted |
1852 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3636 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2464 | iexplore.exe | 172.217.23.142:443 | youtube.com | Google Inc. | US | whitelisted |
3128 | iexplore.exe | 172.217.23.142:443 | youtube.com | Google Inc. | US | whitelisted |
1484 | iexplore.exe | 172.217.12.142:443 | google.com | Google Inc. | US | whitelisted |
— | — | 172.217.12.142:443 | google.com | Google Inc. | US | whitelisted |
2672 | iexplore.exe | 172.217.12.142:443 | google.com | Google Inc. | US | whitelisted |
3128 | iexplore.exe | 64.233.160.136:443 | www.youtube.com | Google Inc. | US | unknown |
2464 | iexplore.exe | 172.217.165.132:443 | www.google.com | Google Inc. | US | whitelisted |
1392 | iexplore.exe | 172.217.12.142:443 | google.com | Google Inc. | US | whitelisted |
2464 | iexplore.exe | 172.217.21.195:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
youtube.com |
| whitelisted |
google.com |
| malicious |
nintendo.co.jp |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.youtube.com |
| whitelisted |
www.google.com |
| malicious |
ssl.gstatic.com |
| whitelisted |
consent.google.com |
| shared |