| File name: | vmcheck.exe |
| Full analysis: | https://app.any.run/tasks/2d7862ec-4cc3-4cd4-b20b-ef31374d7293 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 18:34:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64 (stripped to external PDB), for MS Windows, 9 sections |
| MD5: | A8F15780B1B6F9716938D85A8E3569EF |
| SHA1: | 25DA6E9B509B9F4E1A890EE3A4555727A6C71CA4 |
| SHA256: | E7C2EAD5E48926CABAA25888E54722D656C14DC876B65BCE214086FB30425587 |
| SSDEEP: | 768:IN7+hNkQOmpRFuh31IFYkM2Ng97vyO/r46hK:2AROaRFuh31IFxMugJvyO/r46h |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process checks if it is being run in the virtual environment
- vmcheck.exe (PID: 7588)
Reads security settings of Internet Explorer
- vmcheck.exe (PID: 7588)
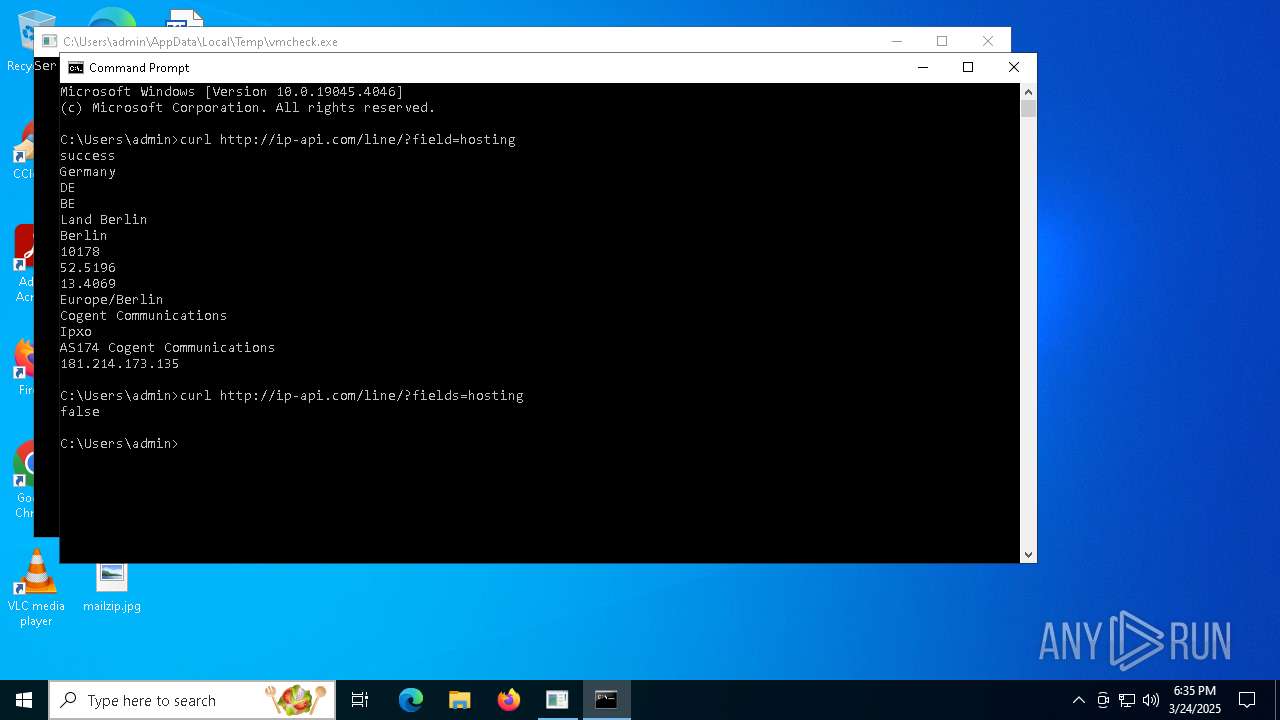
Checks for external IP
- curl.exe (PID: 7984)
- curl.exe (PID: 8000)
- svchost.exe (PID: 2196)
- vmcheck.exe (PID: 7588)
There is functionality for VM detection VMWare (YARA)
- vmcheck.exe (PID: 7588)
There is functionality for VM detection VirtualBox (YARA)
- vmcheck.exe (PID: 7588)
INFO
Checks proxy server information
- vmcheck.exe (PID: 7588)
Reads the computer name
- vmcheck.exe (PID: 7588)
- curl.exe (PID: 7984)
- curl.exe (PID: 8000)
Checks supported languages
- vmcheck.exe (PID: 7588)
Reads the machine GUID from the registry
- vmcheck.exe (PID: 7588)
Manual execution by a user
- cmd.exe (PID: 6044)
Execution of CURL command
- cmd.exe (PID: 6044)
Creates files or folders in the user directory
- vmcheck.exe (PID: 7588)
Reads the software policy settings
- vmcheck.exe (PID: 7588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.2) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:03:24 18:32:21+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 2.34 |
| CodeSize: | 31744 |
| InitializedDataSize: | 53248 |
| UninitializedDataSize: | 5120 |
| EntryPoint: | 0x14f0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
139
Monitored processes
9
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5936 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6044 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7588 | "C:\Users\admin\AppData\Local\Temp\vmcheck.exe" | C:\Users\admin\AppData\Local\Temp\vmcheck.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7596 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | vmcheck.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7748 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7780 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7984 | curl http://ip-api.com/line/?fields=hosting | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 8000 | curl http://ip-api.com/line/?field=hosting | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
Total events
1 586
Read events
1 583
Write events
3
Delete events
0
Modification events
| (PID) Process: | (7588) vmcheck.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7588) vmcheck.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7588) vmcheck.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
4
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7588 | vmcheck.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\line[1].txt | text | |
MD5:D42F2DA1DF5ECDF29BE4AC27EDDA0C12 | SHA256:2ED27C1421E6928DBE13DBFDB5C59E1045B30341FE7EBE05700006BC5AC572C0 | |||
| 7588 | vmcheck.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:E192462F281446B5D1500D474FBACC4B | SHA256:F1BA9F1B63C447682EBF9DE956D0DA2A027B1B779ABEF9522D347D3479139A60 | |||
| 7588 | vmcheck.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\803449686E38E932B196DD1051D4F513 | binary | |
MD5:EEE5943BCD9E3AE4806C4809C0E4DF76 | SHA256:EA5011993260351172E22C6DE35C5BF9A0550EF5241053D4C1D7EBBECC23D130 | |||
| 7588 | vmcheck.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:4D8FECB88FA2D781E21314844FAF20F2 | SHA256:E6A6DE98FE1181CAC980C7FCD67BAB90052D4704CA59F1CB28011850336B9FC2 | |||
| 7588 | vmcheck.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\803449686E38E932B196DD1051D4F513 | binary | |
MD5:5237E939FE4413AF44A9DDA667623539 | SHA256:0BD849E9E316BC3317611A20B9A97B2505163C822F16A12E490CCE27C1DD0AB8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
43
DNS requests
23
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7588 | vmcheck.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
7588 | vmcheck.exe | GET | 200 | 2.16.202.121:80 | http://e6.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBTUejiAQejpjQc4fOz2ttjyD6VkMQQUDcXM%2FZvuFAWhTDCCpT5eisNYCdICEgQn2hyQgJMBE5DOD2g%2B3iQvig%3D%3D | unknown | — | — | whitelisted |
7588 | vmcheck.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
7244 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6108 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6108 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
8000 | curl.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?field=hosting | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.48.23.193:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.159.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7588 | vmcheck.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | whitelisted |
7588 | vmcheck.exe | 35.173.69.207:443 | vtendpoint.pythonanywhere.com | AMAZON-AES | US | whitelisted |
7588 | vmcheck.exe | 23.209.209.135:80 | x1.c.lencr.org | PT. Telekomunikasi Selular | ID | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ip-api.com |
| whitelisted |
vtendpoint.pythonanywhere.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
e6.o.lencr.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7588 | vmcheck.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
7588 | vmcheck.exe | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
8000 | curl.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7984 | curl.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |