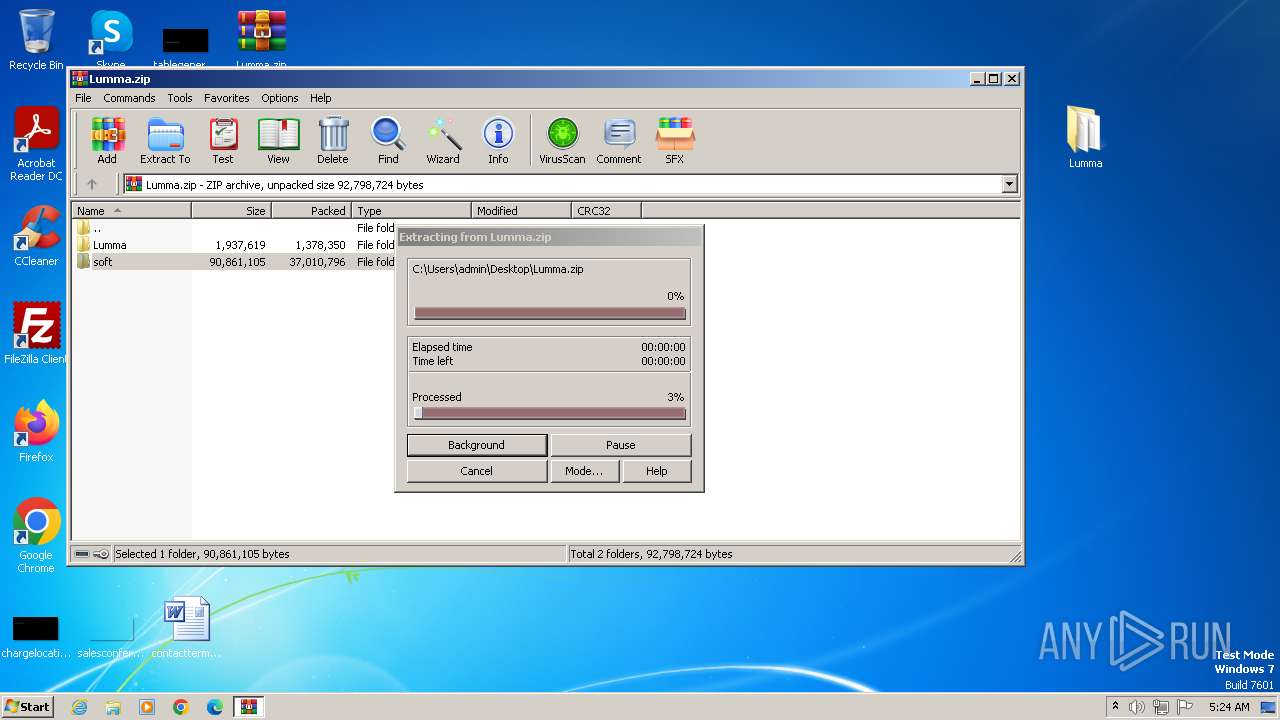
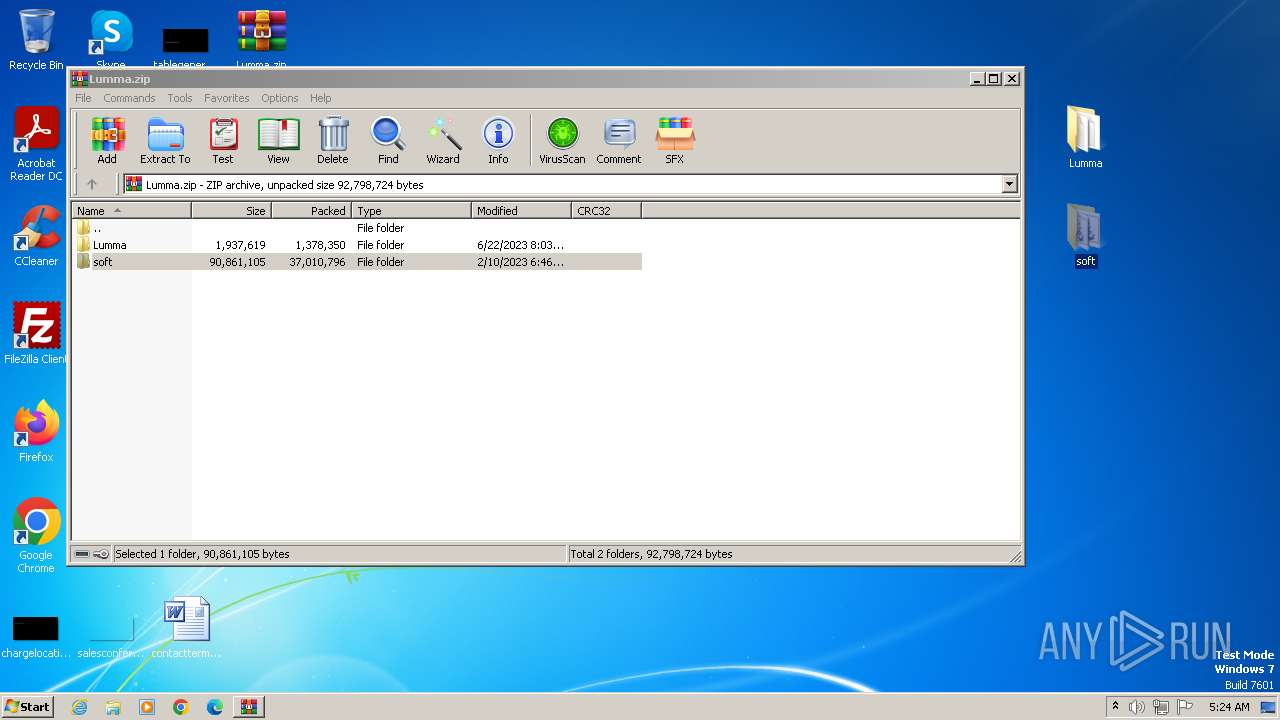
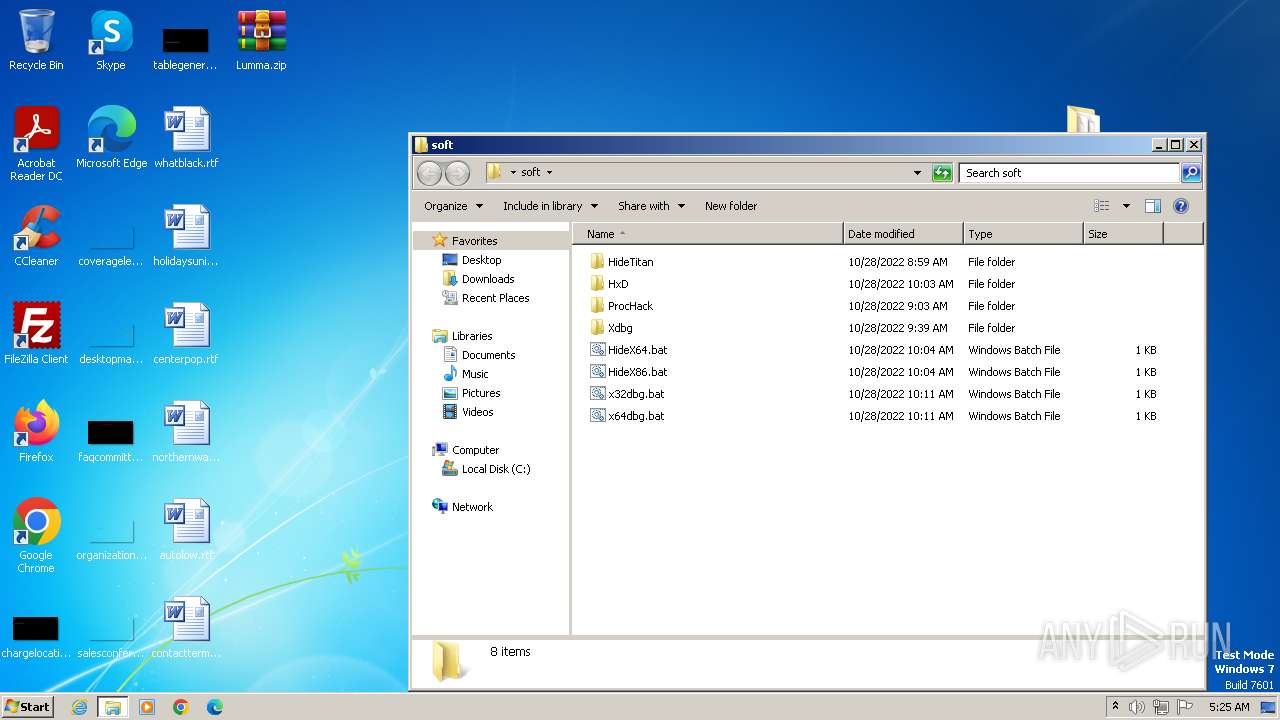
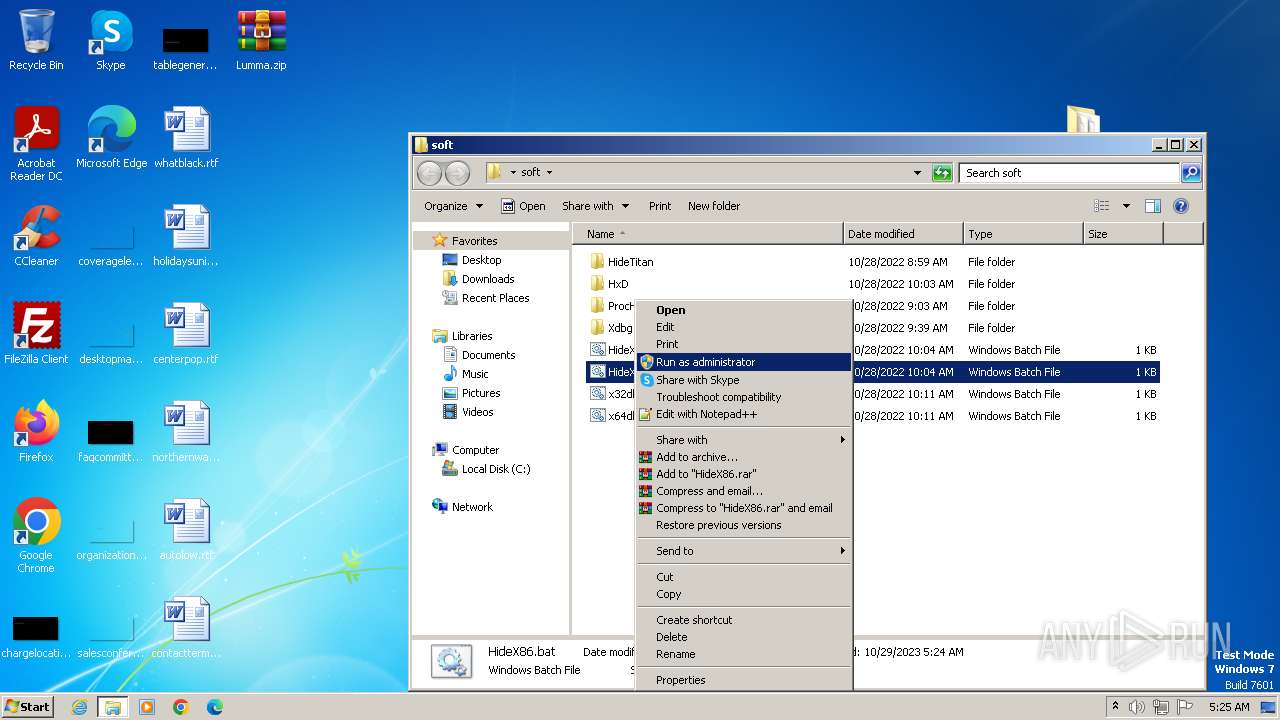
| File name: | Lumma.zip |
| Full analysis: | https://app.any.run/tasks/d61d67d7-2728-4952-86a8-8136375d3c37 |
| Verdict: | Malicious activity |
| Analysis date: | October 29, 2023, 05:24:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | B07F5045C85F1E546645AE049E78F5DB |
| SHA1: | CB4F4BA7E622E253ABB637065C80544B4320F7F6 |
| SHA256: | E7AC75DD061665BDB28BDC5A890877ECAF38388AB56DBDE3922898D4A7D1053E |
| SSDEEP: | 786432:NgLcTr3A15h5X5eGA/S5xAaodcLCWDDRPF7H60m80bfbSIEn5vfo2W6OxvZ:uLqr3A1z5AcKBetBa0m80pE5vVOxx |
MALICIOUS
Application was dropped or rewritten from another process
- dbg32x.exe (PID: 1848)
- 45f00d2a6b59b6669c108b460fccde6a.bin (PID: 316)
- dbg32x.exe (PID: 3820)
- 45f00d2a6b59b6669c108b460fccde6a.bin (PID: 3456)
Loads dropped or rewritten executable
- dbg32x.exe (PID: 1848)
- dbg32x.exe (PID: 3820)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 1248)
Starts CMD.EXE for commands execution
- runas.exe (PID: 2204)
- runas.exe (PID: 560)
Starts SC.EXE for service management
- cmd.exe (PID: 1868)
- cmd.exe (PID: 548)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 1248)
Reads the Internet Settings
- dbg32x.exe (PID: 1848)
Starts application with an unusual extension
- dbg32x.exe (PID: 3820)
- dbg32x.exe (PID: 1848)
Application launched itself
- dbg32x.exe (PID: 1848)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 2368)
- dbg32x.exe (PID: 1848)
- dbg32x.exe (PID: 3820)
- 45f00d2a6b59b6669c108b460fccde6a.bin (PID: 3456)
Reads the computer name
- wmpnscfg.exe (PID: 2368)
- dbg32x.exe (PID: 1848)
- dbg32x.exe (PID: 3820)
Manual execution by a user
- WinRAR.exe (PID: 1248)
- cmd.exe (PID: 3800)
- cmd.exe (PID: 568)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 2368)
- dbg32x.exe (PID: 1848)
- dbg32x.exe (PID: 3820)
Create files in a temporary directory
- dbg32x.exe (PID: 1848)
- dbg32x.exe (PID: 3820)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1248)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:06:23 01:03:14 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Lumma/ |
Total processes
62
Monitored processes
16
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Users\admin\Desktop\Lumma\45f00d2a6b59b6669c108b460fccde6a.bin" | C:\Users\admin\Desktop\Lumma\45f00d2a6b59b6669c108b460fccde6a.bin | — | dbg32x.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
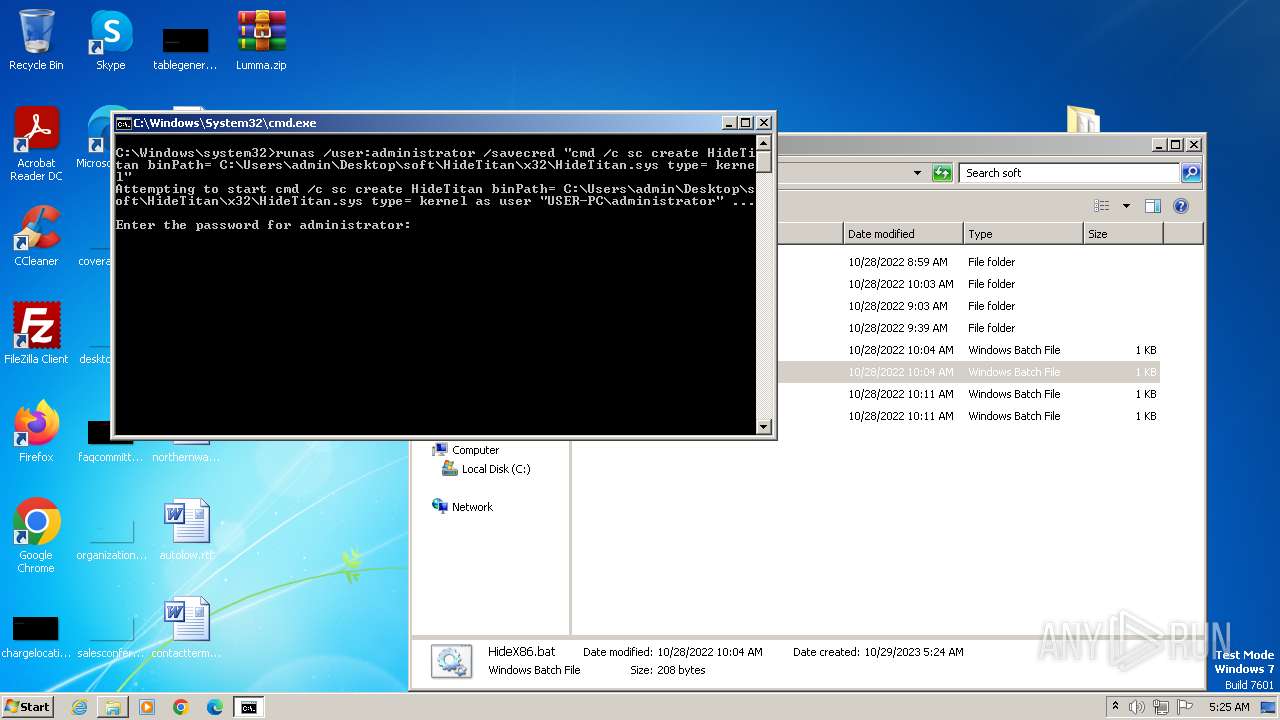
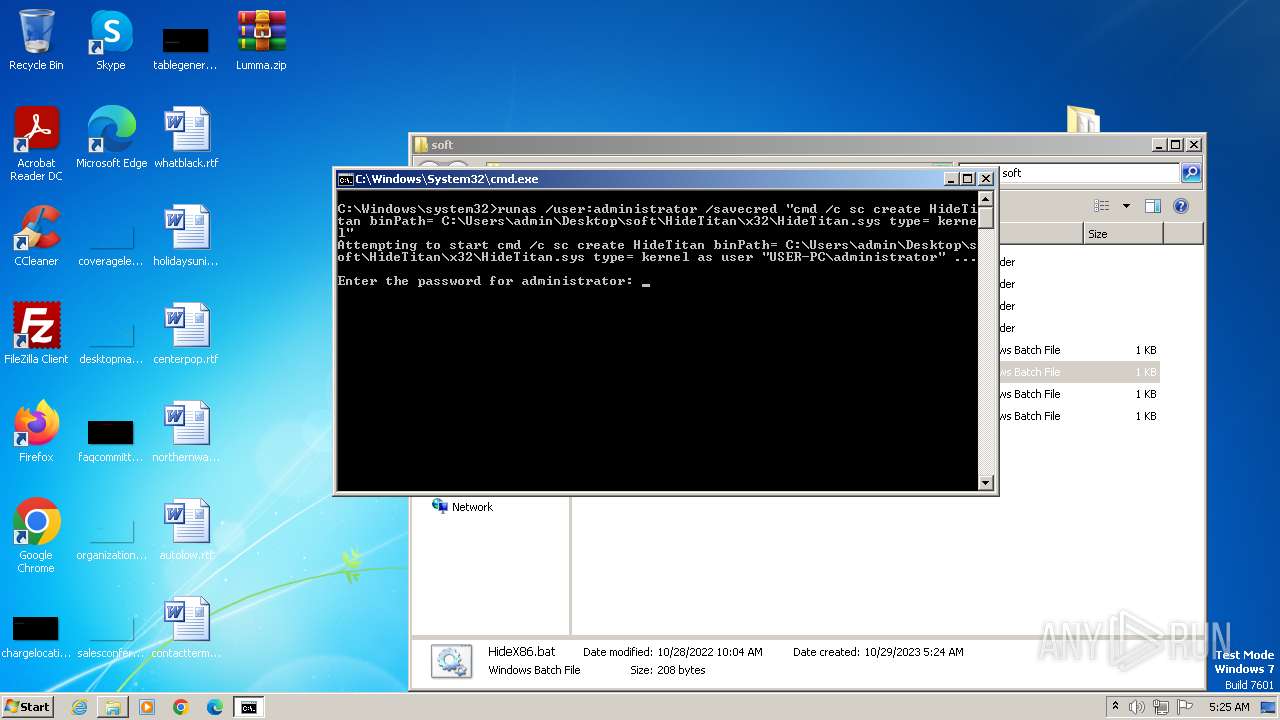
| 548 | cmd /c sc create HideTitan binPath= C:\Users\admin\Desktop\soft\HideTitan\x32\HideTitan.sys type= kernel | C:\Windows\System32\cmd.exe | — | runas.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 560 | runas /user:administrator /savecred "cmd /c sc start HideTitan" | C:\Windows\System32\runas.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run As Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\soft\x32dbg.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 844 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 1248 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Lumma.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1280 | sc create HideTitan binPath= C:\Users\admin\Desktop\soft\HideTitan\x32\HideTitan.sys type= kernel | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1848 | Xdbg\x32\dbg32x.exe | C:\Users\admin\Desktop\soft\Xdbg\x32\dbg32x.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: x64dbg Exit code: 0 Version: 0.0.2.5 Modules
| |||||||||||||||
| 1868 | cmd /c sc start HideTitan | C:\Windows\System32\cmd.exe | — | runas.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2204 | runas /user:administrator /savecred "cmd /c sc create HideTitan binPath= C:\Users\admin\Desktop\soft\HideTitan\x32\HideTitan.sys type= kernel" | C:\Windows\System32\runas.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run As Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 887
Read events
1 856
Write events
28
Delete events
3
Modification events
| (PID) Process: | (2368) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{51131184-60BC-4A38-BAB0-97B33B9589C3}\{D716EF08-2EFC-4F4A-9F8A-D449D2FAE55F} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2368) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{51131184-60BC-4A38-BAB0-97B33B9589C3} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2368) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{B44CBD19-CDBF-45A1-929D-29909BC8E041} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
99
Suspicious files
3
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1248 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1248.7765\soft\HideTitan\x64\HideTitan.sys | executable | |
MD5:7298D6D5A8DB2D3E06D60C0BB4D03E46 | SHA256:2B024DEE2A639C4795DB859DD6FD85657DBB7FDD652D1A5B904A908A0EC25053 | |||
| 1248 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1248.7573\Lumma\45f00d2a6b59b6669c108b460fccde6a.bin | executable | |
MD5:45F00D2A6B59B6669C108B460FCCDE6A | SHA256:B57CC512C2E7990AFD0E29FBFCFA9D53DF8AD37E08E8C13BAB2D9AAFCF2FA34E | |||
| 1248 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1248.7765\soft\HideTitan\x32\TitanHideTest.exe | executable | |
MD5:6868E084AFF0A611B6C8AD4078D579FF | SHA256:BF404240A4DE80CF716B608C2E91B04906D7ED7CE82B76491215BCC7BC73204E | |||
| 1248 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1248.7765\soft\x64dbg.bat | text | |
MD5:AF47A9EC391EDFAC880052942215DF80 | SHA256:ADB8DDBFB263EB3E23FC5DEE0867946FA2D150DB26F3BBB4EC61A390324A647D | |||
| 1248 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1248.7573\Lumma\c2conf | text | |
MD5:4C55078DA7F0D632B0AF29DFA23E0DB7 | SHA256:533A6854EFE4F57824AD9E8154D448D22EAB66AF085E377E190B648F2363ECEF | |||
| 1248 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1248.7765\soft\HideTitan\x32\HideTitan.sys | executable | |
MD5:8F1255AFBE54B08852CA6805F5B23741 | SHA256:30F9D0756D65808B05BB3E165DD2AC4C7630A28533219EA7E971896A6F9F5C15 | |||
| 1248 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1248.7765\soft\Xdbg\x64\platforms\qwindows.dll | executable | |
MD5:0CDAC0E449902682182F78A552C35DE2 | SHA256:85DBCAF6965FB146CDE7825465ADD3E890E13D2C67390B8B3C6FBCAECD503C68 | |||
| 1248 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1248.7765\soft\Xdbg\x64\msdia140.dll | executable | |
MD5:73E0349829750676B7791AC210E304E8 | SHA256:46351BD350799DC196481CBE2B26F628B489A280A9E2F49BACE71930F3DC80D3 | |||
| 1248 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1248.7765\soft\HideX86.bat | text | |
MD5:E3AD7885D913A8C605ACDDF66F0F414D | SHA256:377DB35772EE0D41B9B8376F75808E3DDF116F534EAA8BB611BAD513BEC99C4C | |||
| 1248 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1248.7765\soft\Xdbg\x64\Qt5WinExtras.dll | executable | |
MD5:DE7154814975F02E171F637F8222F8B1 | SHA256:8DC1C6AD37A164639EF75093D8A0179F6F8EFDF1A22877C59BAC745968738E6D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |