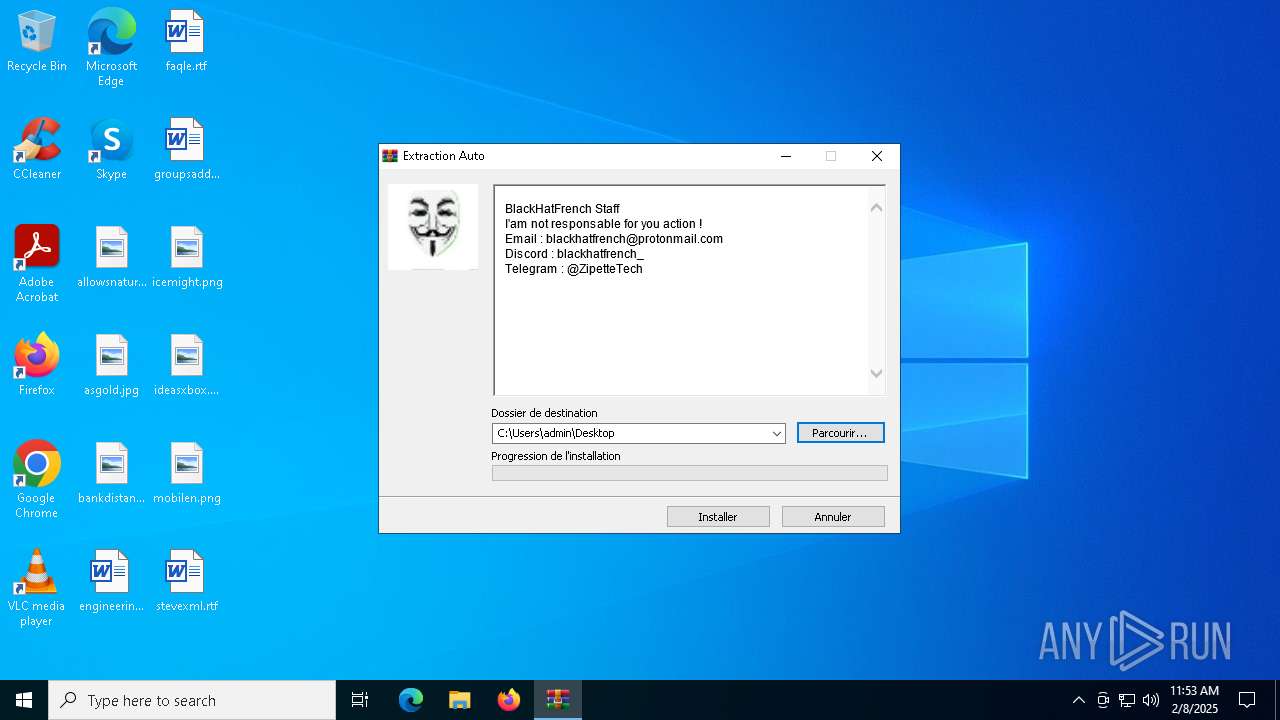
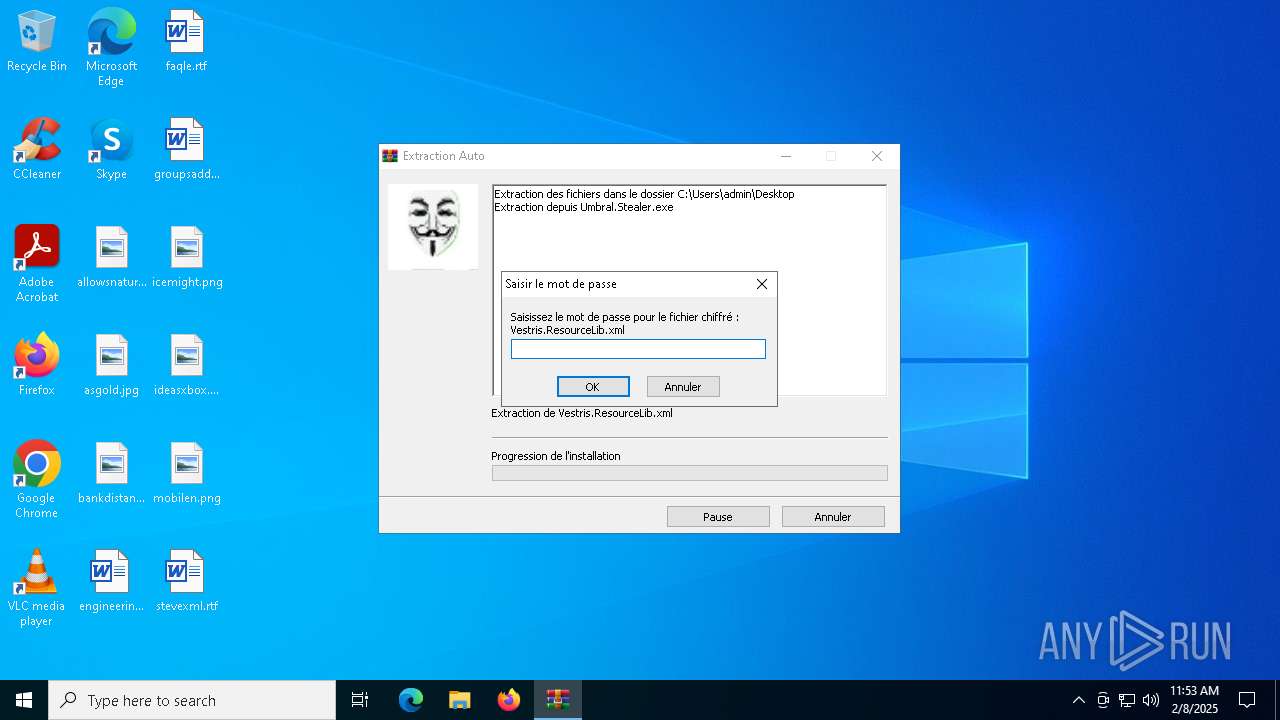
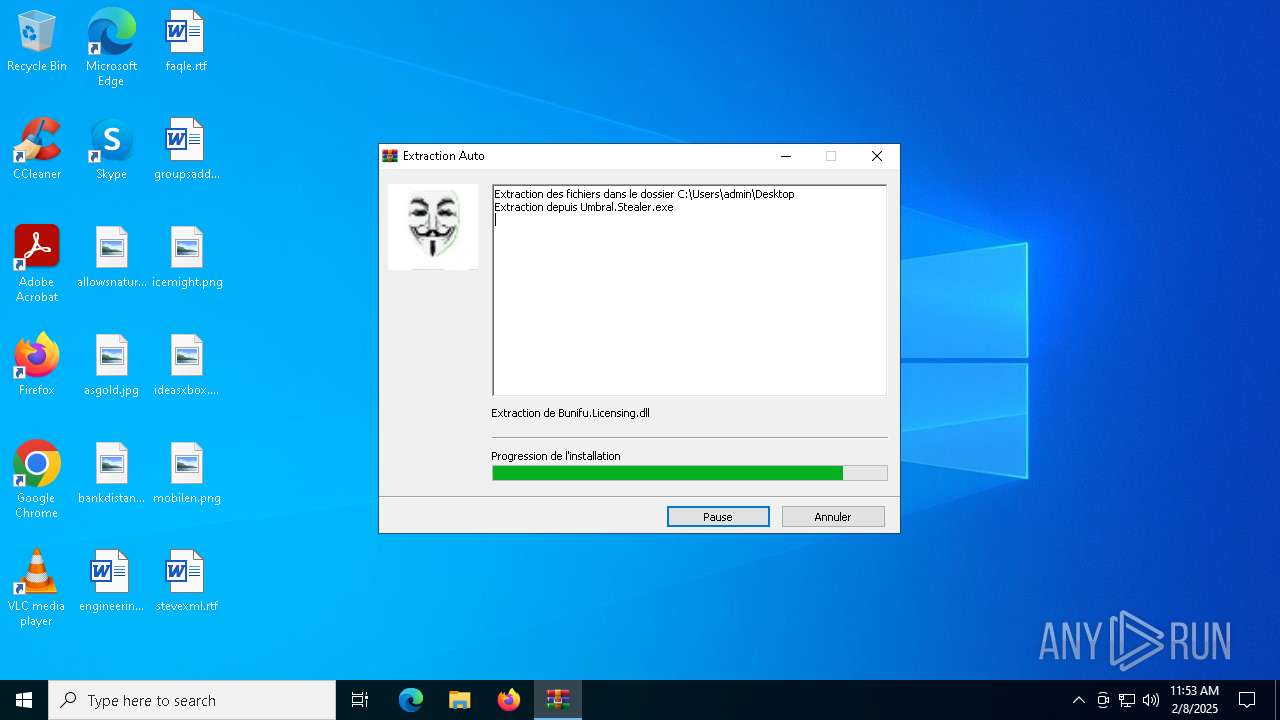
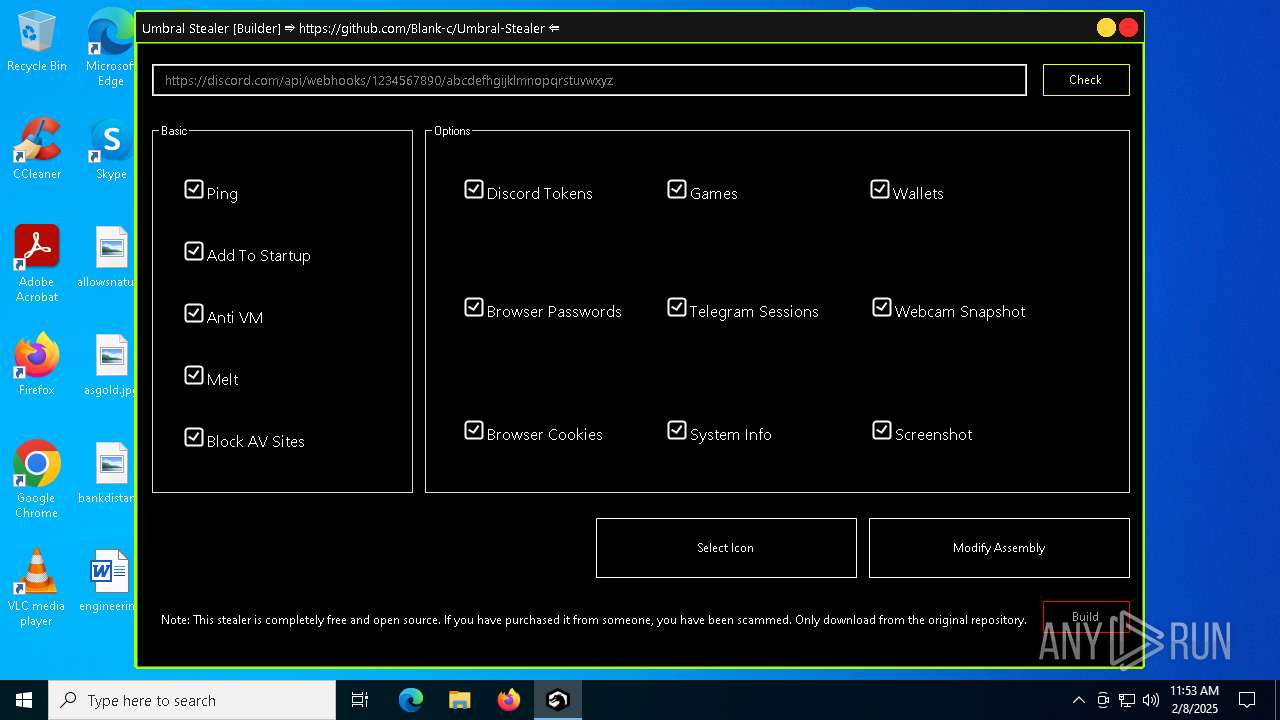
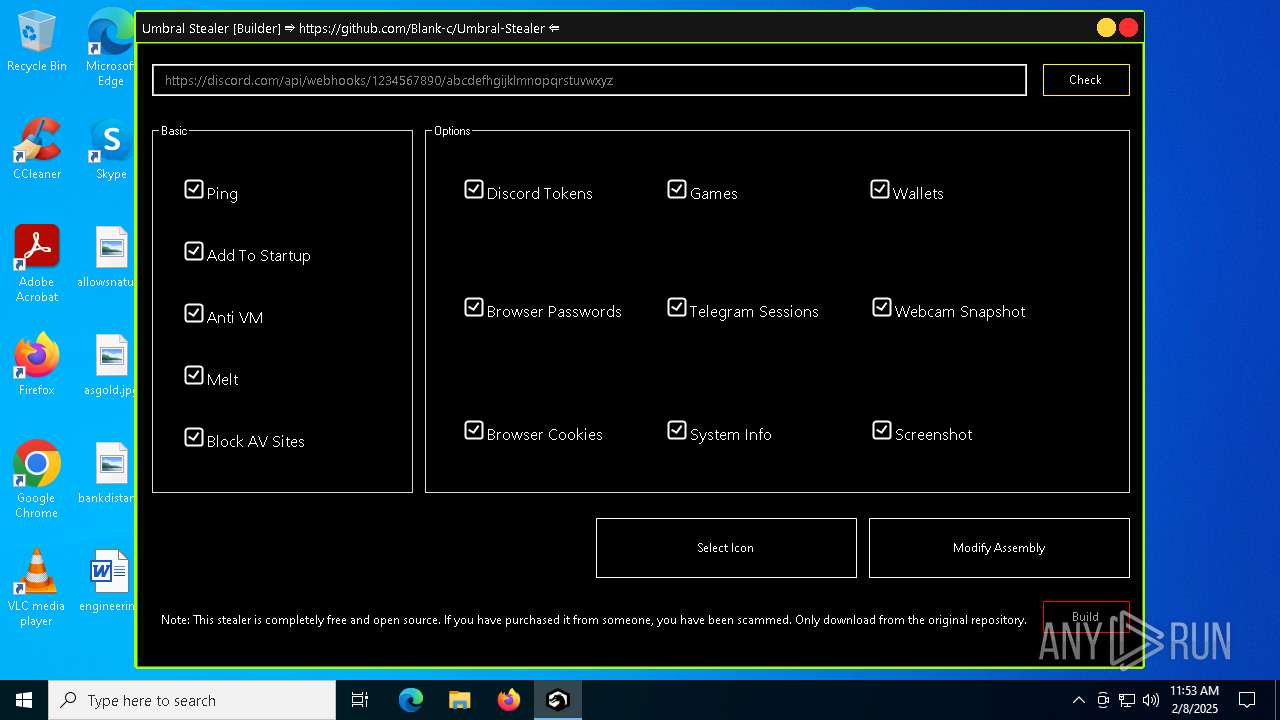
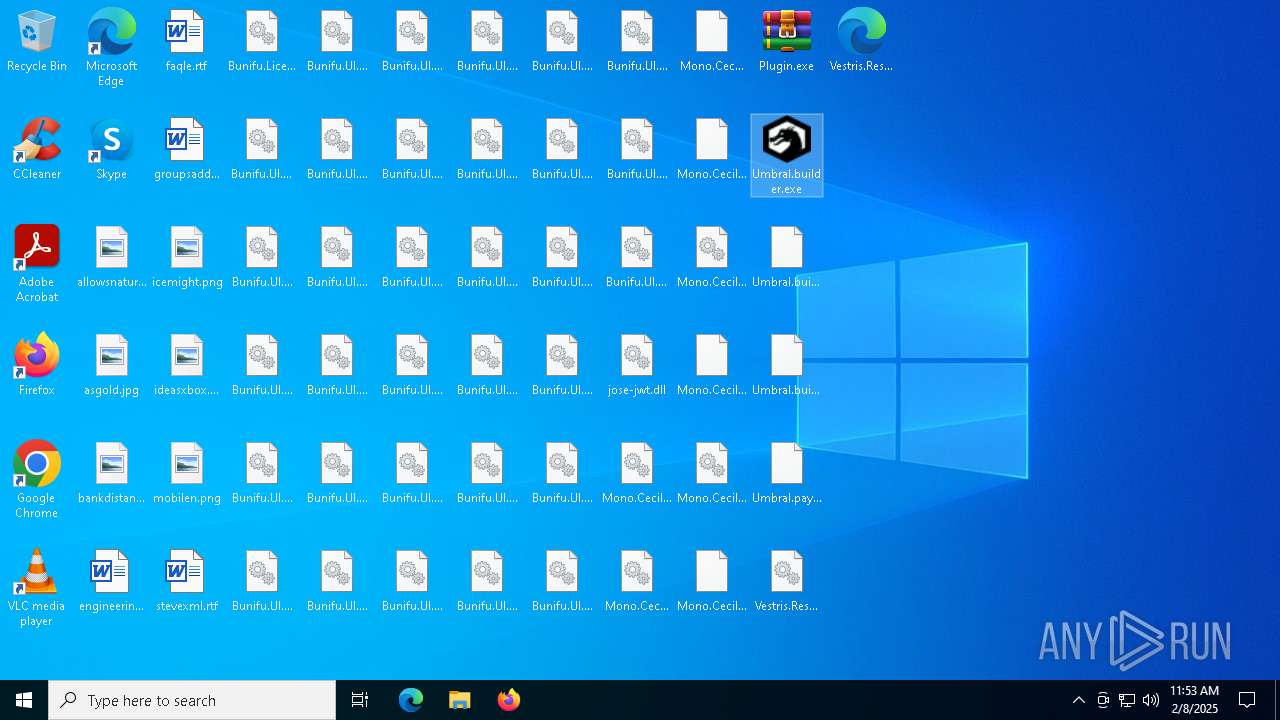
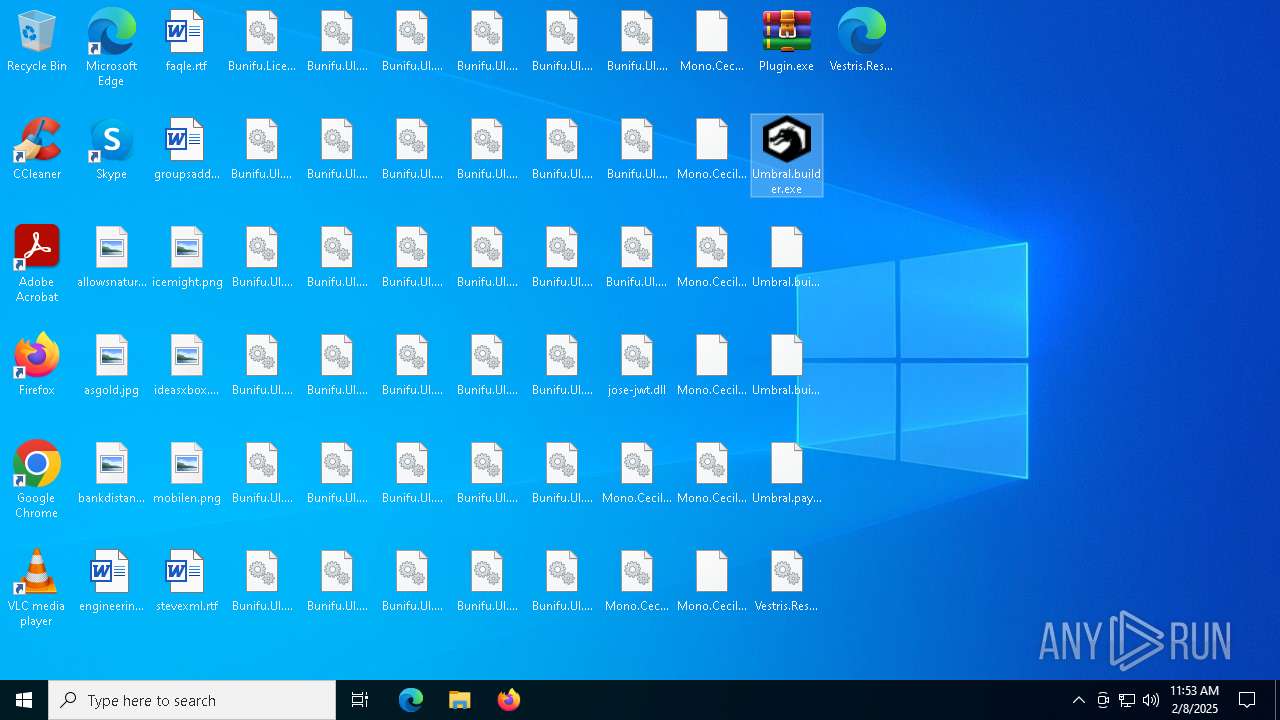
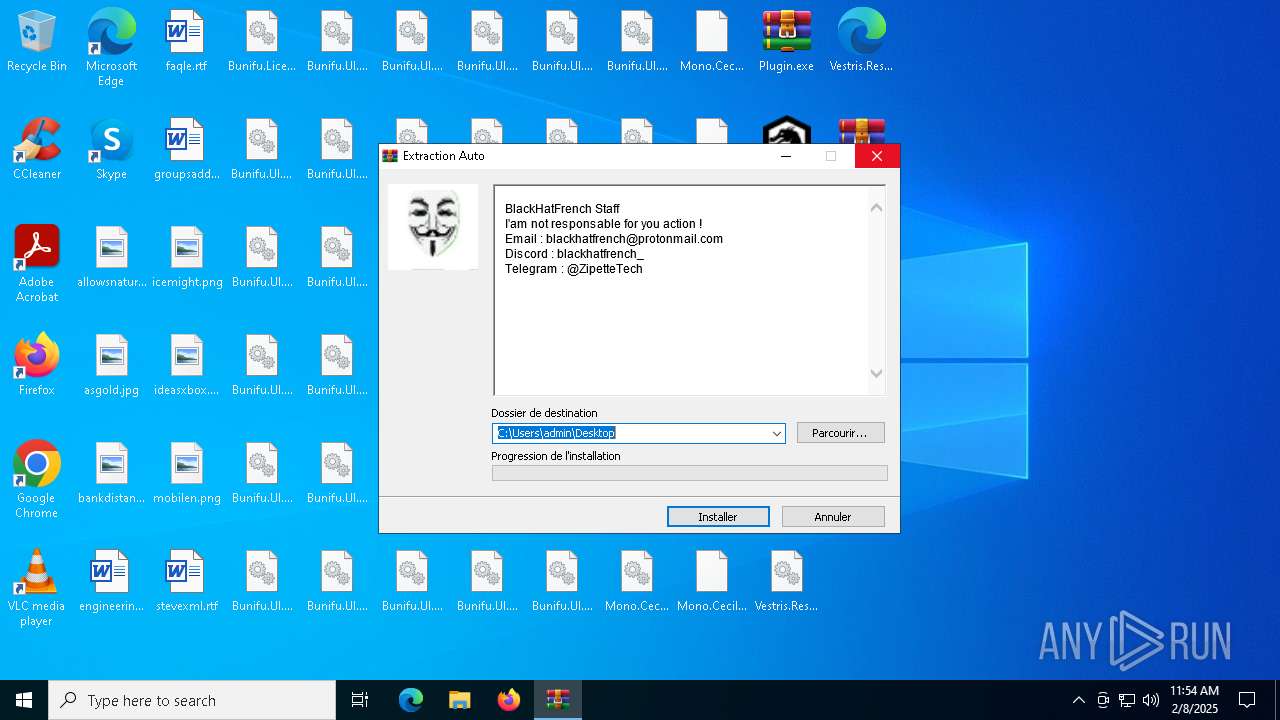
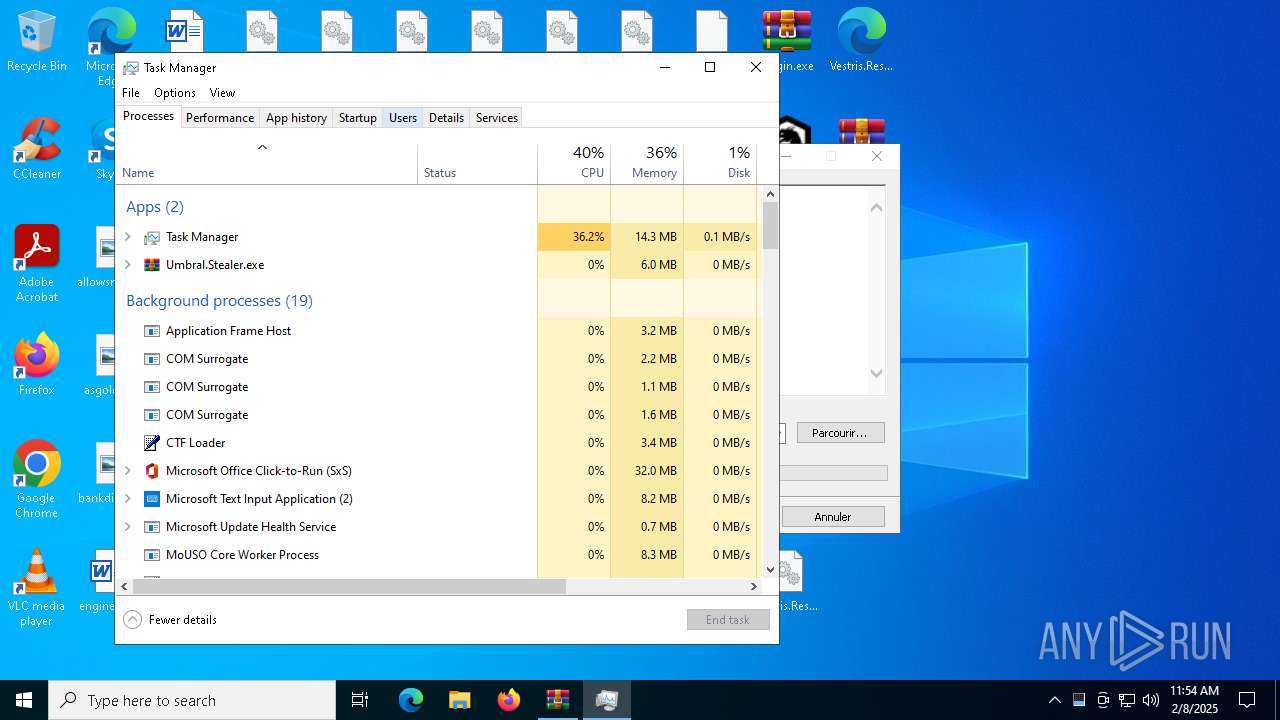
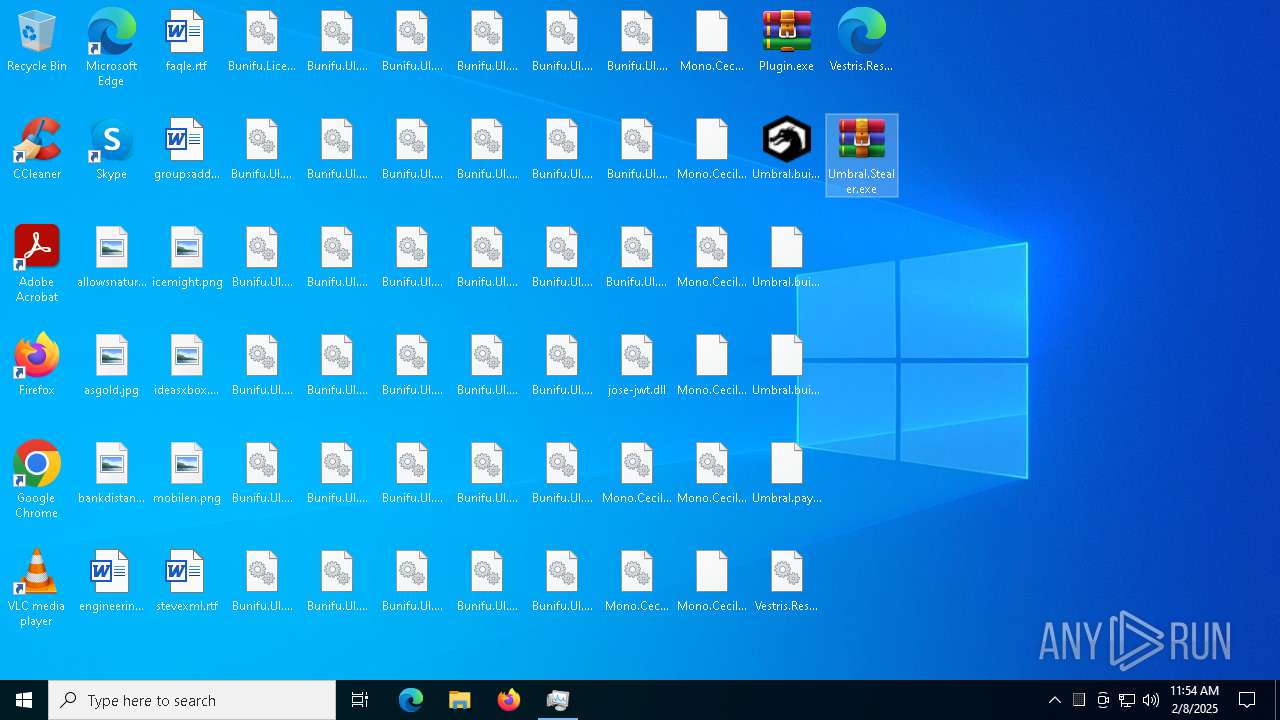
| File name: | Umbral.Stealer.exe |
| Full analysis: | https://app.any.run/tasks/6253775d-70ef-453c-81a9-e66565d3d708 |
| Verdict: | Malicious activity |
| Analysis date: | February 08, 2025, 11:52:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 8 sections |
| MD5: | 471B38A445EB6833E40C0DAF289CD630 |
| SHA1: | D46E034C5C02725A66980F00537B4358685A454F |
| SHA256: | E79FFE8F53A0216A0264C0A8FE465A77A85CC390FDCB2B75BF7AFBAAED058DE5 |
| SSDEEP: | 196608:6zUEn+nTljDo1Z7XBf0X5500F257dL6X/33uEGl:KUEKTl3qXB612dL6f3LGl |
MALICIOUS
No malicious indicators.SUSPICIOUS
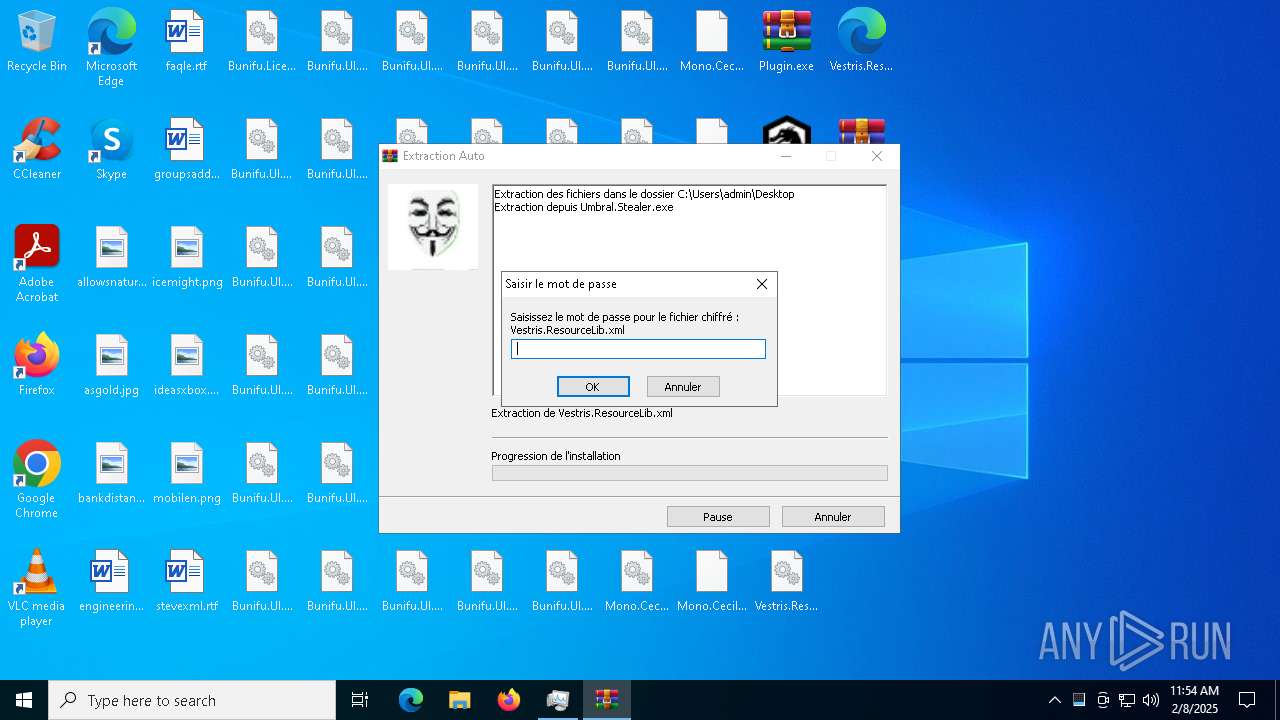
Executable content was dropped or overwritten
- Umbral.Stealer.exe (PID: 6696)
Reads security settings of Internet Explorer
- Umbral.Stealer.exe (PID: 6696)
- Umbral.Stealer.exe (PID: 7044)
Reads Internet Explorer settings
- Umbral.Stealer.exe (PID: 6696)
- Umbral.Stealer.exe (PID: 7044)
Reads Microsoft Outlook installation path
- Umbral.Stealer.exe (PID: 6696)
- Umbral.Stealer.exe (PID: 7044)
There is functionality for taking screenshot (YARA)
- Umbral.Stealer.exe (PID: 6696)
- Umbral.Stealer.exe (PID: 7044)
Reads the date of Windows installation
- Umbral.Stealer.exe (PID: 6696)
- Umbral.Stealer.exe (PID: 7044)
Executes application which crashes
- Plugin.exe (PID: 3188)
- Plugin.exe (PID: 6204)
- Plugin.exe (PID: 4932)
- Plugin.exe (PID: 6540)
Checks for external IP
- Plugin.exe (PID: 3188)
- svchost.exe (PID: 2192)
- Plugin.exe (PID: 6204)
- Plugin.exe (PID: 4932)
- Plugin.exe (PID: 6540)
INFO
Checks supported languages
- Umbral.Stealer.exe (PID: 6696)
- Plugin.exe (PID: 3188)
- Plugin.exe (PID: 6204)
- Umbral.builder.exe (PID: 7068)
- Plugin.exe (PID: 4932)
- Umbral.Stealer.exe (PID: 7044)
- identity_helper.exe (PID: 4876)
- Plugin.exe (PID: 6540)
- identity_helper.exe (PID: 900)
Checks proxy server information
- Umbral.Stealer.exe (PID: 6696)
- Plugin.exe (PID: 3188)
- WerFault.exe (PID: 2464)
- Plugin.exe (PID: 6204)
- WerFault.exe (PID: 6720)
- Umbral.Stealer.exe (PID: 7044)
- Plugin.exe (PID: 4932)
- WerFault.exe (PID: 3992)
- Plugin.exe (PID: 6540)
- WerFault.exe (PID: 7136)
Reads the computer name
- Umbral.Stealer.exe (PID: 6696)
- Plugin.exe (PID: 3188)
- Plugin.exe (PID: 6204)
- Umbral.builder.exe (PID: 7068)
- Plugin.exe (PID: 4932)
- Umbral.Stealer.exe (PID: 7044)
- identity_helper.exe (PID: 4876)
- Plugin.exe (PID: 6540)
- identity_helper.exe (PID: 900)
Process checks computer location settings
- Umbral.Stealer.exe (PID: 6696)
- Umbral.Stealer.exe (PID: 7044)
Reads the machine GUID from the registry
- Plugin.exe (PID: 3188)
- Plugin.exe (PID: 6204)
- Umbral.builder.exe (PID: 7068)
- Plugin.exe (PID: 4932)
- Plugin.exe (PID: 6540)
Reads Environment values
- Plugin.exe (PID: 3188)
- Plugin.exe (PID: 6204)
- Plugin.exe (PID: 4932)
- identity_helper.exe (PID: 4876)
- Plugin.exe (PID: 6540)
- identity_helper.exe (PID: 900)
Disables trace logs
- Plugin.exe (PID: 3188)
- Plugin.exe (PID: 6204)
- Plugin.exe (PID: 4932)
- Plugin.exe (PID: 6540)
Reads the software policy settings
- WerFault.exe (PID: 2464)
- WerFault.exe (PID: 6720)
- WerFault.exe (PID: 3992)
- WerFault.exe (PID: 7136)
Manual execution by a user
- Plugin.exe (PID: 6204)
- Umbral.builder.exe (PID: 7068)
- Taskmgr.exe (PID: 628)
- Taskmgr.exe (PID: 2776)
- Umbral.Stealer.exe (PID: 7044)
- msedge.exe (PID: 4536)
- Plugin.exe (PID: 6540)
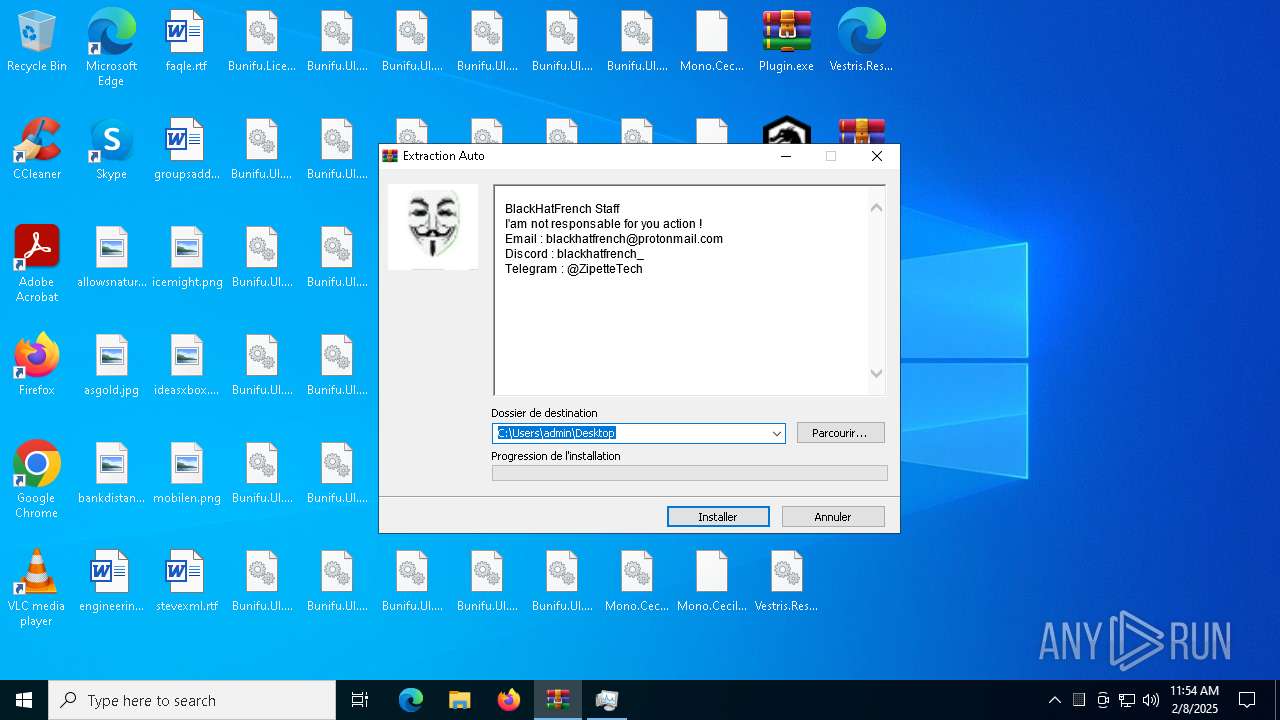
- WinRAR.exe (PID: 6488)
Creates files or folders in the user directory
- WerFault.exe (PID: 6720)
- WerFault.exe (PID: 2464)
- WerFault.exe (PID: 3992)
- WerFault.exe (PID: 7136)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 628)
Application launched itself
- msedge.exe (PID: 4128)
- msedge.exe (PID: 4536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:05:12 10:17:07+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.33 |
| CodeSize: | 288768 |
| InitializedDataSize: | 294912 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x32ee0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
218
Monitored processes
81
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 488 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8508 --field-trial-handle=2424,i,11978401152325539739,1706654038104579703,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 540 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=21 --mojo-platform-channel-handle=5524 --field-trial-handle=2424,i,11978401152325539739,1706654038104579703,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 556 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --mojo-platform-channel-handle=5724 --field-trial-handle=2424,i,11978401152325539739,1706654038104579703,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 628 | "C:\WINDOWS\system32\taskmgr.exe" /0 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 880 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6892 --field-trial-handle=2424,i,11978401152325539739,1706654038104579703,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 900 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8188 --field-trial-handle=2424,i,11978401152325539739,1706654038104579703,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 900 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=3384 --field-trial-handle=2120,i,3235996338614596179,15946405259923892475,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1216 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --mojo-platform-channel-handle=5604 --field-trial-handle=2120,i,3235996338614596179,15946405259923892475,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1344 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7032 --field-trial-handle=2424,i,11978401152325539739,1706654038104579703,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1344 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2208 --field-trial-handle=2120,i,3235996338614596179,15946405259923892475,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
30 754
Read events
30 664
Write events
85
Delete events
5
Modification events
| (PID) Process: | (6696) Umbral.Stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6696) Umbral.Stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6696) Umbral.Stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6696) Umbral.Stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 105 | |||
| (PID) Process: | (6696) Umbral.Stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 9B45A76700000000 | |||
| (PID) Process: | (6696) Umbral.Stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Width |
Value: 318 | |||
| (PID) Process: | (6696) Umbral.Stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Height |
Value: 288 | |||
| (PID) Process: | (6696) Umbral.Stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (6696) Umbral.Stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (3188) Plugin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Plugin_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
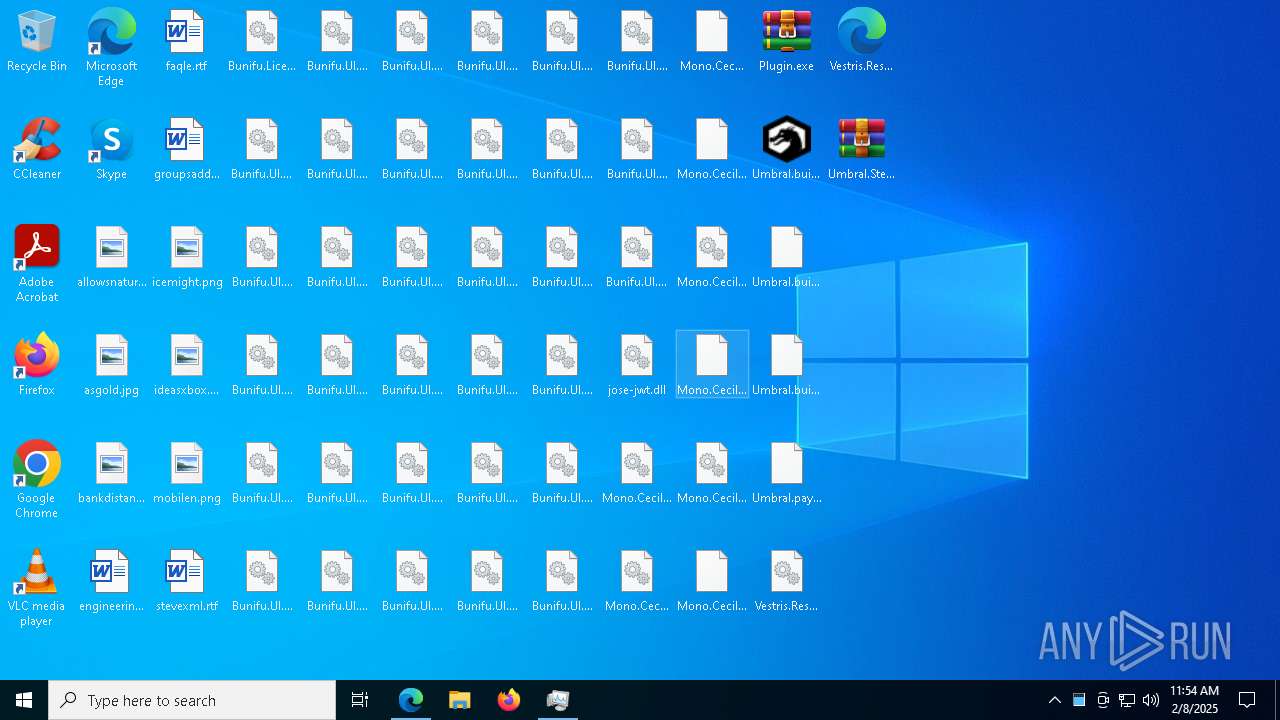
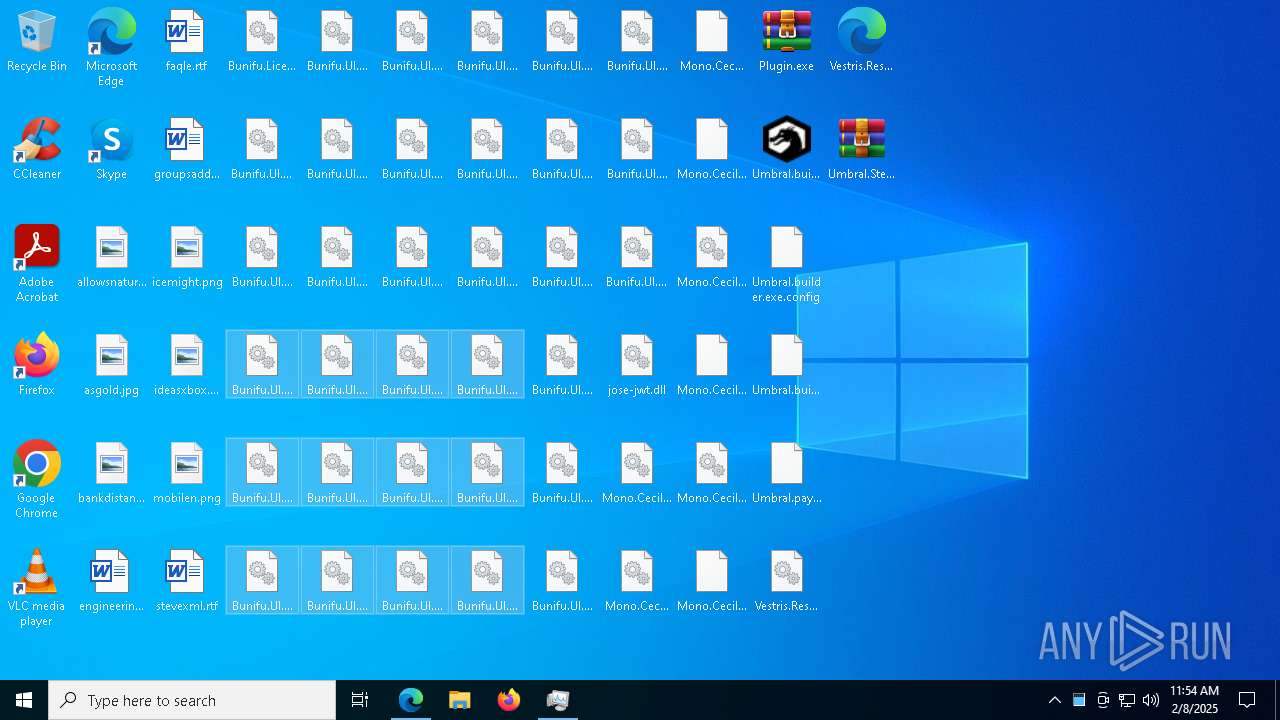
Executable files
110
Suspicious files
910
Text files
168
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6696 | Umbral.Stealer.exe | C:\Users\admin\Desktop\Bunifu.UI.WinForms.BunifuImageButton.dll | executable | |
MD5:7D68B8AF58C87EE29ECA74FE8EF2F093 | SHA256:32B8EB2FAE4A14E8319448CD173B73A8E63234B3816D6407EF95BE204CEC226D | |||
| 6696 | Umbral.Stealer.exe | C:\Users\admin\Desktop\Bunifu.UI.WinForms.BunifuDatePicker.dll | executable | |
MD5:A05882BAC172C61B5B1BD3F4A56B4320 | SHA256:3C1AC3E39665E49327B64887131A53C63379DE884B3A6F9A0AB96A36E882CEB7 | |||
| 6696 | Umbral.Stealer.exe | C:\Users\admin\Desktop\Bunifu.UI.WinForms.BunifuLabel.dll | executable | |
MD5:73CA0338C9C3B7901D3621B346C76A7A | SHA256:A505193910F7B8FD6123C00BB437BFF3D2A4F28C970E24207D395554765E6AD4 | |||
| 6696 | Umbral.Stealer.exe | C:\Users\admin\Desktop\Bunifu.UI.WinForms.BunifuGroupBox.dll | executable | |
MD5:E86AAFA7C25A2F1654CF95657CACC39C | SHA256:637B5CAC86E245C53AF91E41E6479DE42DF1B5FA5A524F931E034F5B5EE1F259 | |||
| 6696 | Umbral.Stealer.exe | C:\Users\admin\Desktop\Bunifu.UI.WinForms.BunifuDataGridView.dll | executable | |
MD5:53765AD5B31FD87986A569BBB79F402C | SHA256:9E61BD6DBCC8D5866BF3A139EA12F453EF4CA8BAB28C08329CBC5F0BF13950DF | |||
| 6696 | Umbral.Stealer.exe | C:\Users\admin\Desktop\Bunifu.UI.WinForms.BunifuButton.dll | executable | |
MD5:21F999E5AC72A16077511D41590822DE | SHA256:2A62C78F1F0DB2E3258135B50F7885E6734C31C74A8F2F5782F285AA268C2F71 | |||
| 6696 | Umbral.Stealer.exe | C:\Users\admin\Desktop\Bunifu.UI.WinForms.BunifuCheckBox.dll | executable | |
MD5:EF11F59A9381DF17D7AB94434F79F260 | SHA256:390252AEB6FD76A954A03853C3D883E0360DC8B3F2CF8CFED5BA94E4E5A24DA4 | |||
| 6696 | Umbral.Stealer.exe | C:\Users\admin\Desktop\Bunifu.UI.WinForms.BunifuCircleProgress.dll | executable | |
MD5:BC930A050CA23EA75DBD9DEADE4189BB | SHA256:D5ED95667AA44A80278B80A90413C0DE9D85EEB3CA1FA24A40AE71C3AD88D837 | |||
| 6696 | Umbral.Stealer.exe | C:\Users\admin\Desktop\Bunifu.UI.WinForms.1.5.3.dll | executable | |
MD5:41C216D27C71A227774E680E95E99F31 | SHA256:012D717B4AC00C3686A772757F49C1908E223624E3974314CDB9FC9291073305 | |||
| 6696 | Umbral.Stealer.exe | C:\Users\admin\Desktop\Bunifu.Licensing.dll | executable | |
MD5:2B2740E0C34A46DE31CF9DA8A75D77CF | SHA256:A9BE91CAE167702885A5CA74273DB779E3E391E2E604CC03779ED403C53EBE43 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
229
DNS requests
265
Threats
25
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6432 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6612 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6432 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2464 | WerFault.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6204 | Plugin.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
2464 | WerFault.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3188 | Plugin.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
6236 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e30939f9-8764-4977-9b5d-f865df373b71?P1=1739232052&P2=404&P3=2&P4=g18QMiEcDnwyj57wYJPOibuVQbsNDbSKaDqV8GNoStf%2fYEB11%2bVvtRC%2fXdPTqr4UkqH59gUC6ji6RqWvRdzSKw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5064 | SearchApp.exe | 92.123.104.12:443 | — | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.31.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3416 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
3188 | Plugin.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
3188 | Plugin.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2192 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2192 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2192 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
6204 | Plugin.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
6204 | Plugin.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
4932 | Plugin.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
4932 | Plugin.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
Process | Message |
|---|---|
Plugin.exe | CLR: Managed code called FailFast without specifying a reason.
|
Plugin.exe | CLR: Managed code called FailFast without specifying a reason.
|
Plugin.exe | CLR: Managed code called FailFast without specifying a reason.
|
Plugin.exe | CLR: Managed code called FailFast without specifying a reason.
|