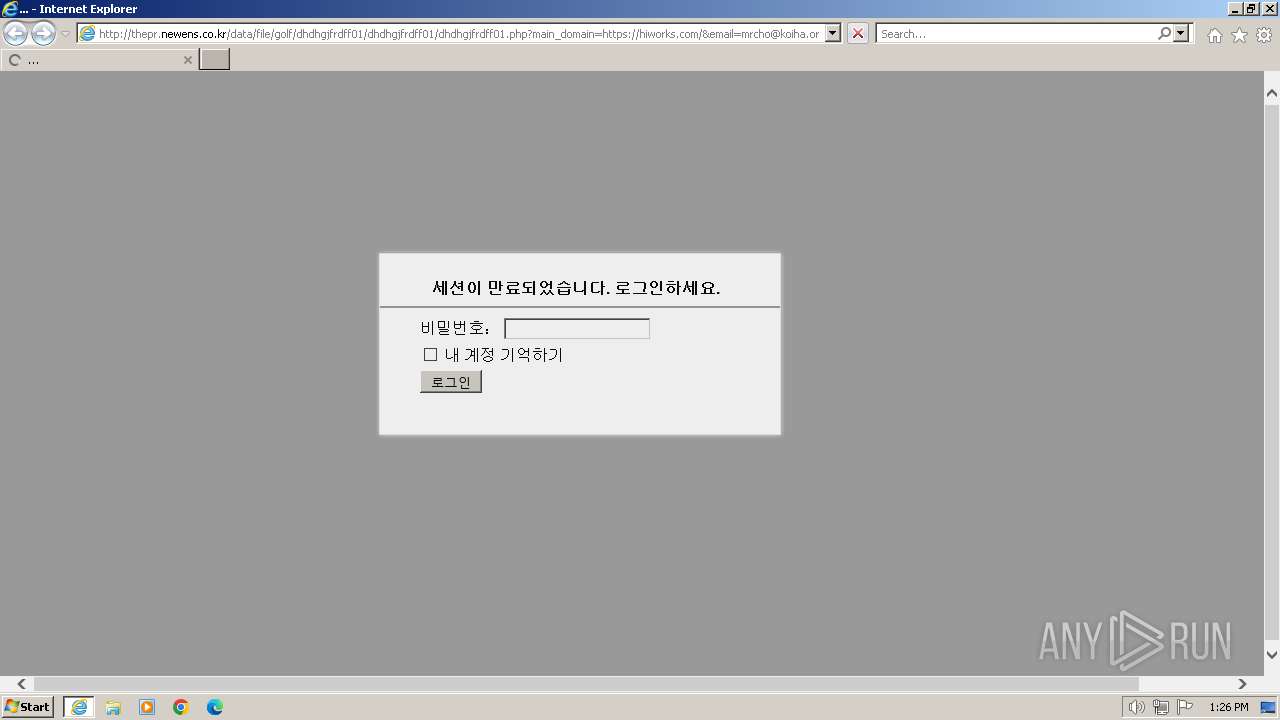
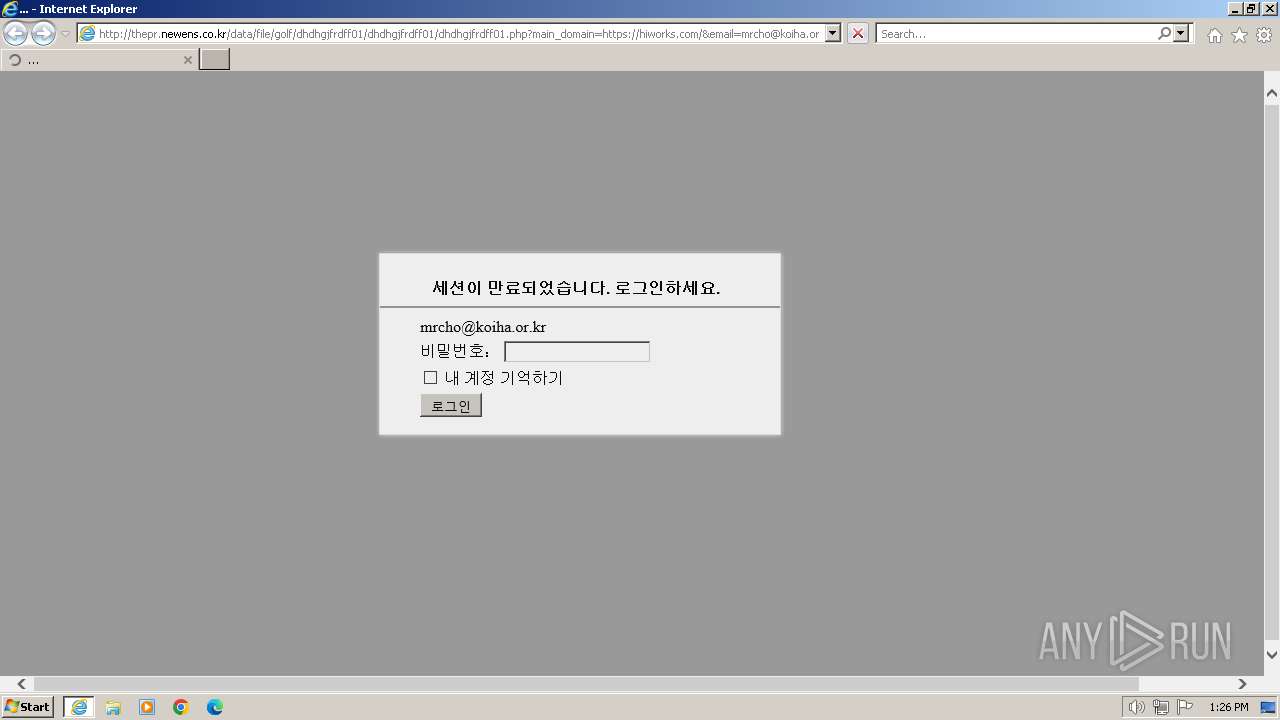
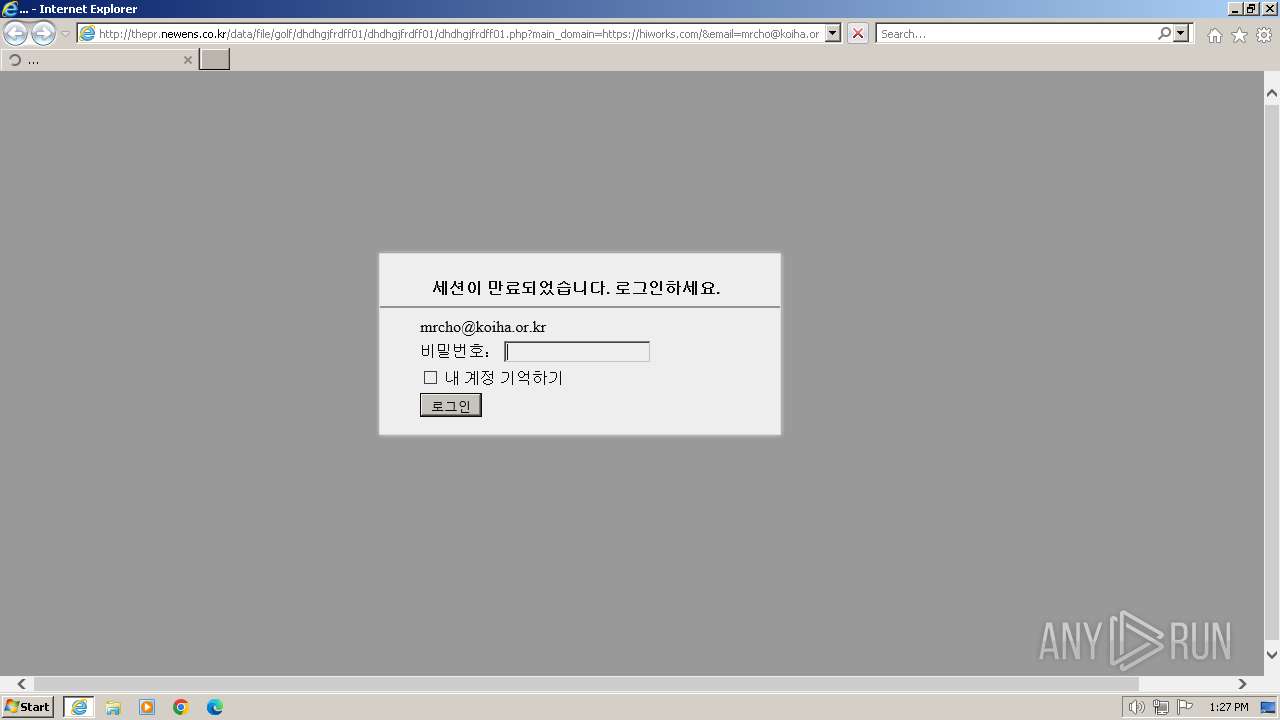
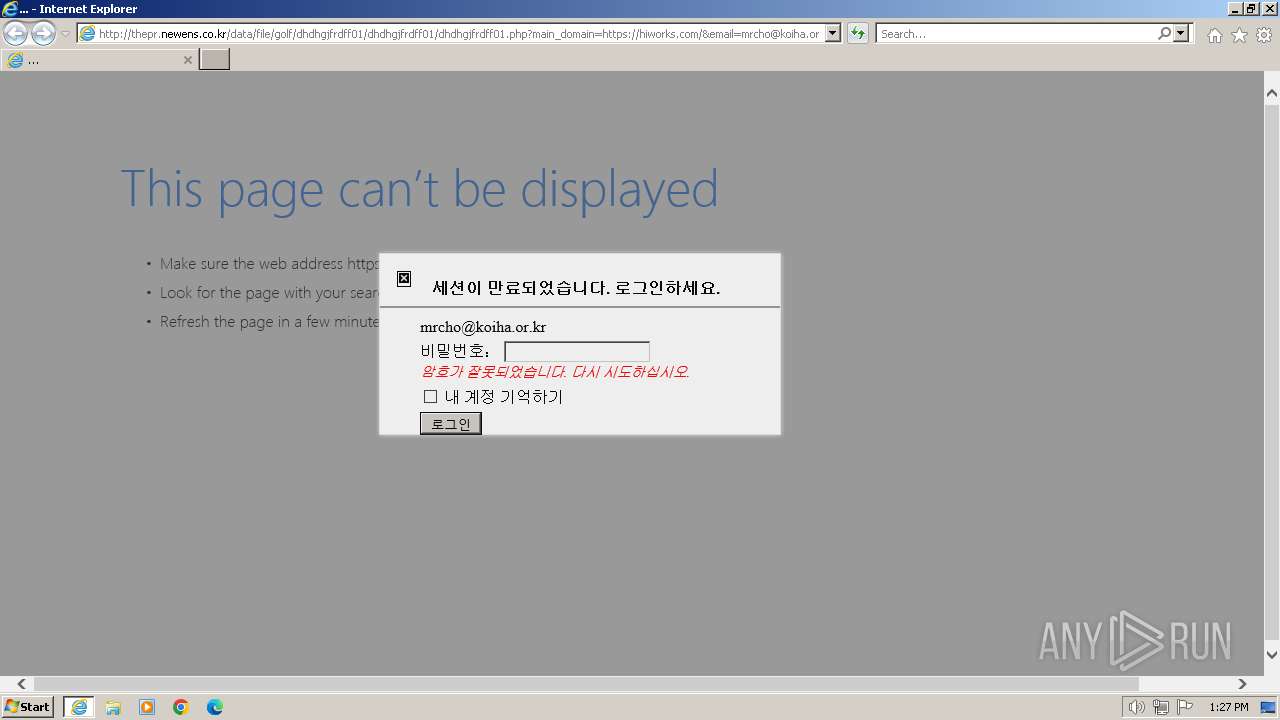
| URL: | http://thepr.newens.co.kr/data/file/golf/dhdhgjfrdff01/dhdhgjfrdff01/dhdhgjfrdff01.php?main_domain=https://hiworks.com/&email=mrcho@koiha.or.kr&subdomain=https://hiworks.com |
| Full analysis: | https://app.any.run/tasks/c71a4a7d-3292-4307-88db-ce43d545bbc4 |
| Verdict: | Malicious activity |
| Analysis date: | March 18, 2024, 13:26:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 211AA589AAD92CEEAAAB045A27789C82 |
| SHA1: | D7D6F83CE76C58E5B8B1DC3D533BE487C73ECA24 |
| SHA256: | E79D9D3272AE5B7A9FA7517779914806778EC2305D3A6954B6F9DC6BEEE6972E |
| SSDEEP: | 3:N1KKNwb0KBJfAKjZsaTNNaTNNxaM5EY5XVGK3aSRoVsrY5XVGKI:CKNotJ+aTNNaTNN0Y5XsKqB4Y5XsKI |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 4008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3276 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:4008 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4008 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://thepr.newens.co.kr/data/file/golf/dhdhgjfrdff01/dhdhgjfrdff01/dhdhgjfrdff01.php?main_domain=https://hiworks.com/&email=mrcho@koiha.or.kr&subdomain=https://hiworks.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
11 734
Read events
11 635
Write events
71
Delete events
28
Modification events
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31095095 | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31095095 | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
4
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3276 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\jquery-3.2.1.min[1].js | text | |
MD5:C9F5AEECA3AD37BF2AA006139B935F0A | SHA256:87083882CC6015984EB0411A99D3981817F5DC5C90BA24F0940420C5548D82DE | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:CF4942AC94675EBE5342E96ED7FFA41F | SHA256:041CB8183FC1B5358A9C2670B27287E1778531102979B19FFDE21671F8CB0099 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:94C20CE605229FE43B3B3589432E48F0 | SHA256:5DCC71E9B3FAD70B52F7270C105535D82B475773BE2B0DC10DA3BD704436E807 | |||
| 4008 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicons[1].htm | html | |
MD5:BB694C18DC8EE0738B445E7754C235E5 | SHA256:DE0A0DA411D90902630E599BE445FE084E8343CADE3CF727EE497CC68841E579 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\favicons[1].htm | html | |
MD5:BB694C18DC8EE0738B445E7754C235E5 | SHA256:DE0A0DA411D90902630E599BE445FE084E8343CADE3CF727EE497CC68841E579 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:2BE527BAFD97039C169D707C0869C375 | SHA256:DD22D139587FFDC5FE685EB59EE52070487BCCCA0684550B4FF14852EFA1D250 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:08073685D4B92DF6F34BA023FBAF5D0F | SHA256:C5A48925D552D47F9428BAADF724482753D80E83EB5A470EEC43D0A10D5B32FD | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\dhdhgjfrdff01[1].htm | html | |
MD5:C0820D082667F18369C45193321526C9 | SHA256:D12C81913D4414DEFE55B70C56A264386EC76BCD6D59DA97D1A286A09A199193 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | der | |
MD5:C4589D928BDE093A8B3C4AC1B2E9A472 | SHA256:C04B0BCC650D2A58D5F3846C775FDD29C4257063540FC79AC1C5043AEEE22FE1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
45
DNS requests
22
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3276 | iexplore.exe | GET | 200 | 175.126.77.143:80 | http://thepr.newens.co.kr/data/file/golf/dhdhgjfrdff01/dhdhgjfrdff01/dhdhgjfrdff01.php?main_domain=https://hiworks.com/&email=mrcho@koiha.or.kr&subdomain=https://hiworks.com | unknown | html | 5.67 Kb | unknown |
3276 | iexplore.exe | GET | 304 | 23.65.29.16:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9df0723acf4b4299 | unknown | — | — | unknown |
3276 | iexplore.exe | GET | 301 | 172.217.18.4:80 | http://www.google.com/s2/favicons?domain=https://hiworks.com/ | unknown | html | 333 b | unknown |
3276 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
3276 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | binary | 2.18 Kb | unknown |
4008 | iexplore.exe | GET | 301 | 172.217.18.4:80 | http://www.google.com/s2/favicons?domain=https://hiworks.com/ | unknown | html | 333 b | unknown |
1080 | svchost.exe | GET | 200 | 95.100.155.18:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?4f071b604691de88 | unknown | compressed | 67.5 Kb | unknown |
1080 | svchost.exe | GET | 304 | 95.100.155.18:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c14a917a25499794 | unknown | compressed | 67.5 Kb | unknown |
4008 | iexplore.exe | GET | 404 | 175.126.77.143:80 | http://thepr.newens.co.kr/favicon.ico | unknown | html | 209 b | unknown |
3276 | iexplore.exe | POST | 200 | 175.126.77.143:80 | http://thepr.newens.co.kr/data/file/golf/dhdhgjfrdff01/dhdhgjfrdff01/trytti.php | unknown | binary | 1 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3276 | iexplore.exe | 175.126.77.143:80 | thepr.newens.co.kr | SK Broadband Co Ltd | KR | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3276 | iexplore.exe | 172.217.18.4:80 | www.google.com | GOOGLE | US | whitelisted |
3276 | iexplore.exe | 151.101.66.137:443 | code.jquery.com | FASTLY | US | unknown |
3276 | iexplore.exe | 121.254.216.63:443 | hiworks.com | LG DACOM Corporation | KR | unknown |
3276 | iexplore.exe | 172.217.16.196:443 | t1.gstatic.com | GOOGLE | US | whitelisted |
3276 | iexplore.exe | 23.65.29.16:80 | ctldl.windowsupdate.com | Akamai International B.V. | DK | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
thepr.newens.co.kr |
| unknown |
www.google.com |
| whitelisted |
code.jquery.com |
| whitelisted |
hiworks.com |
| whitelisted |
t1.gstatic.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3276 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
3276 | iexplore.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspicious sending of an email address as an unencrypted POST request |