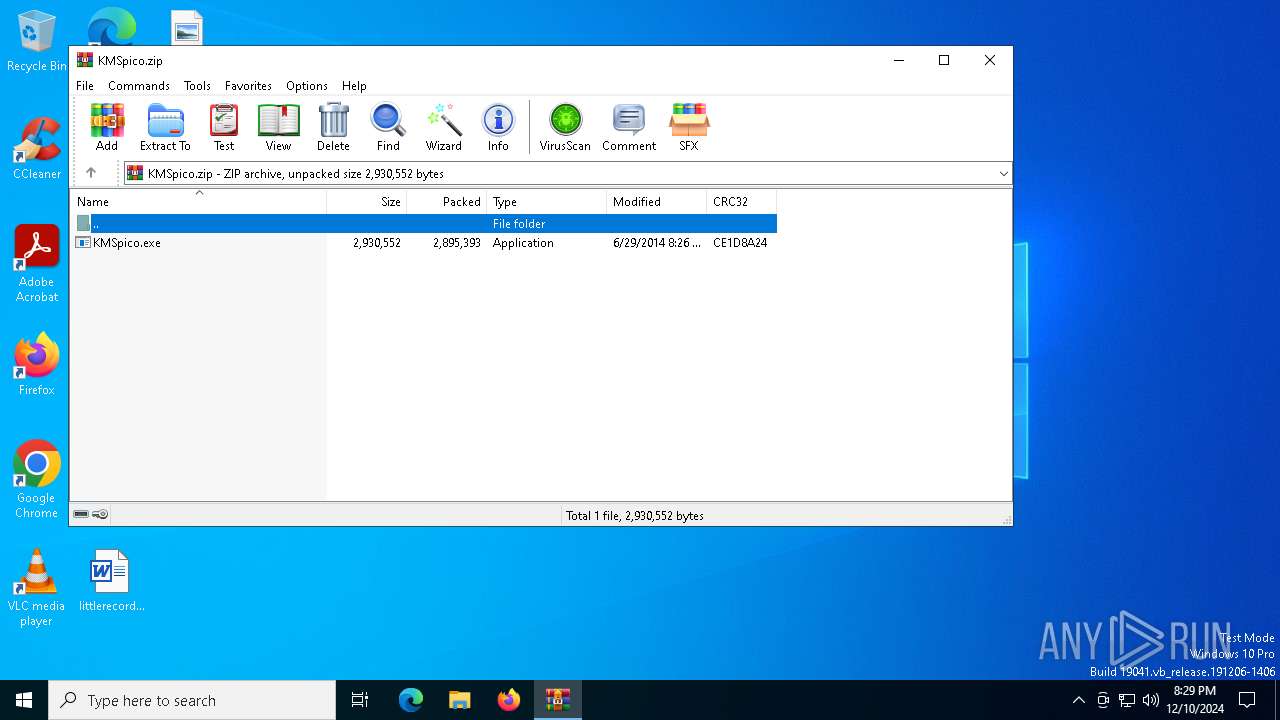
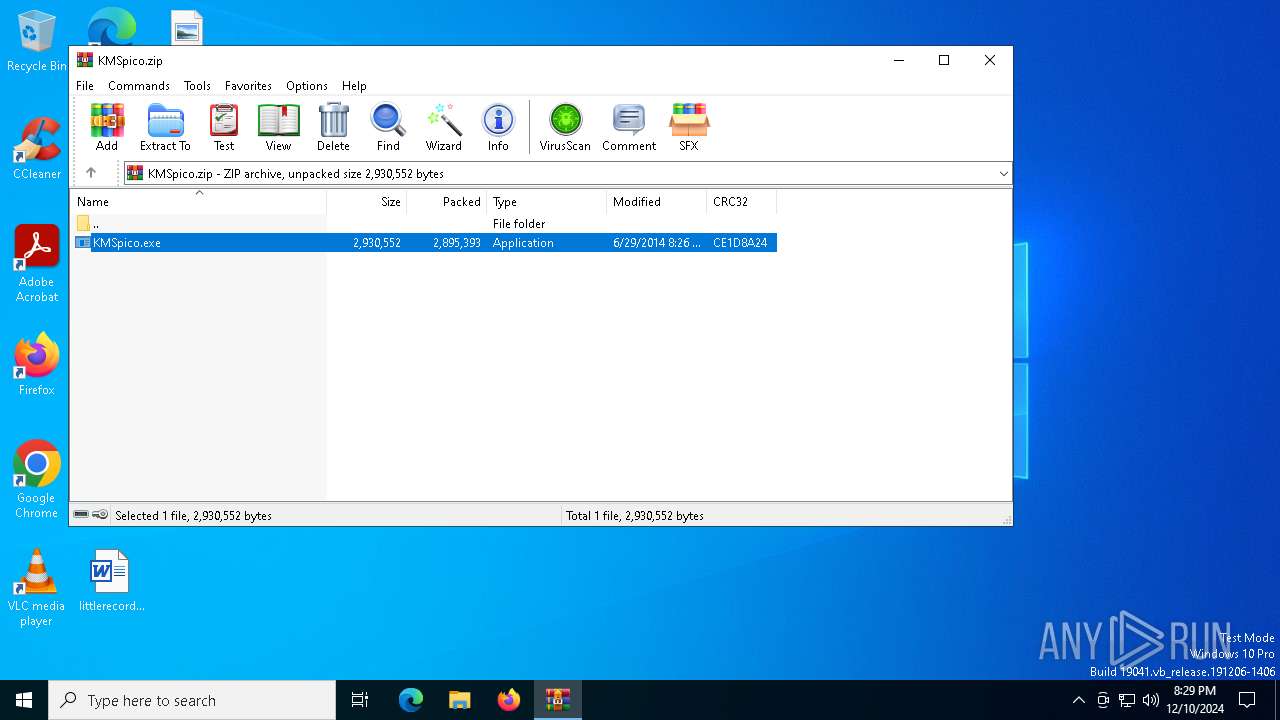
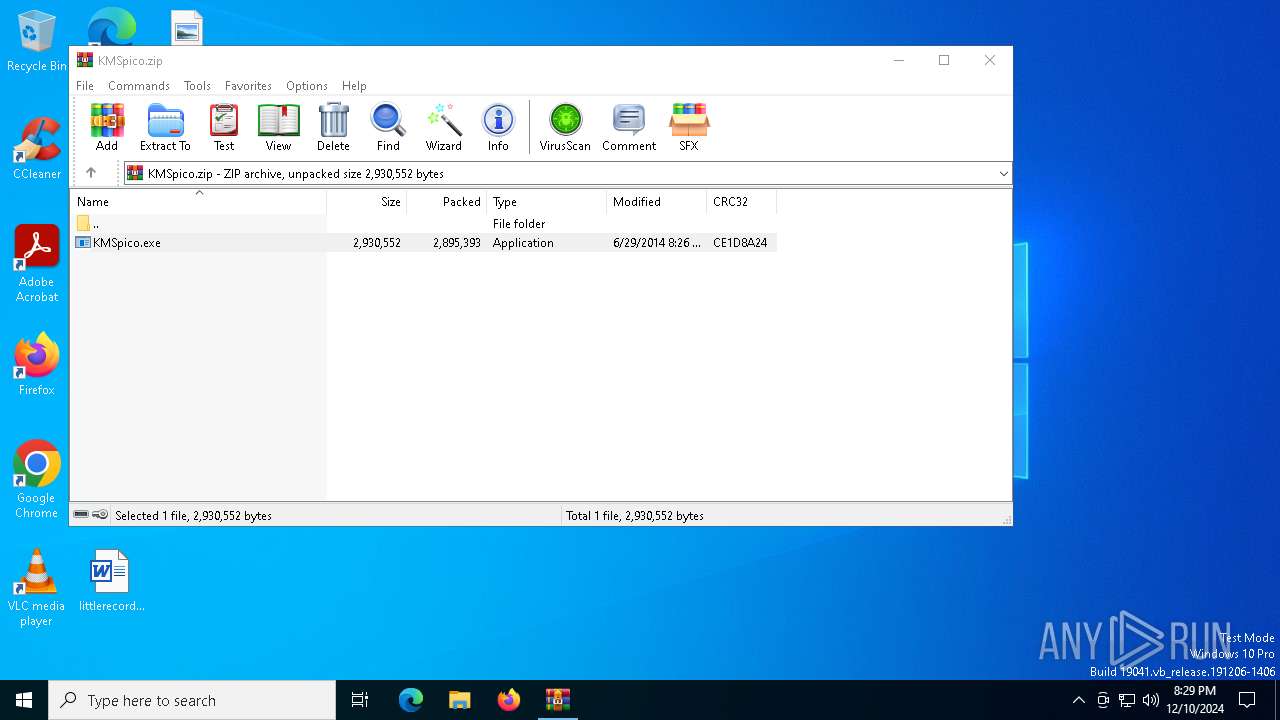
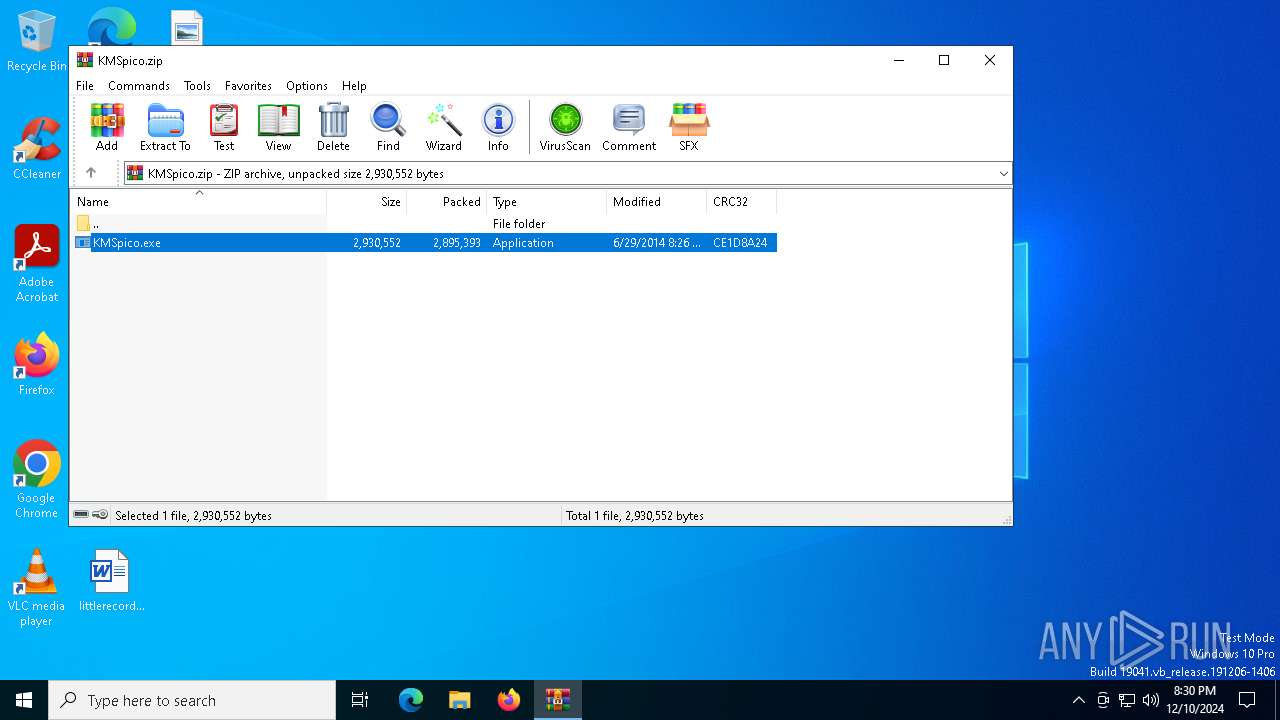
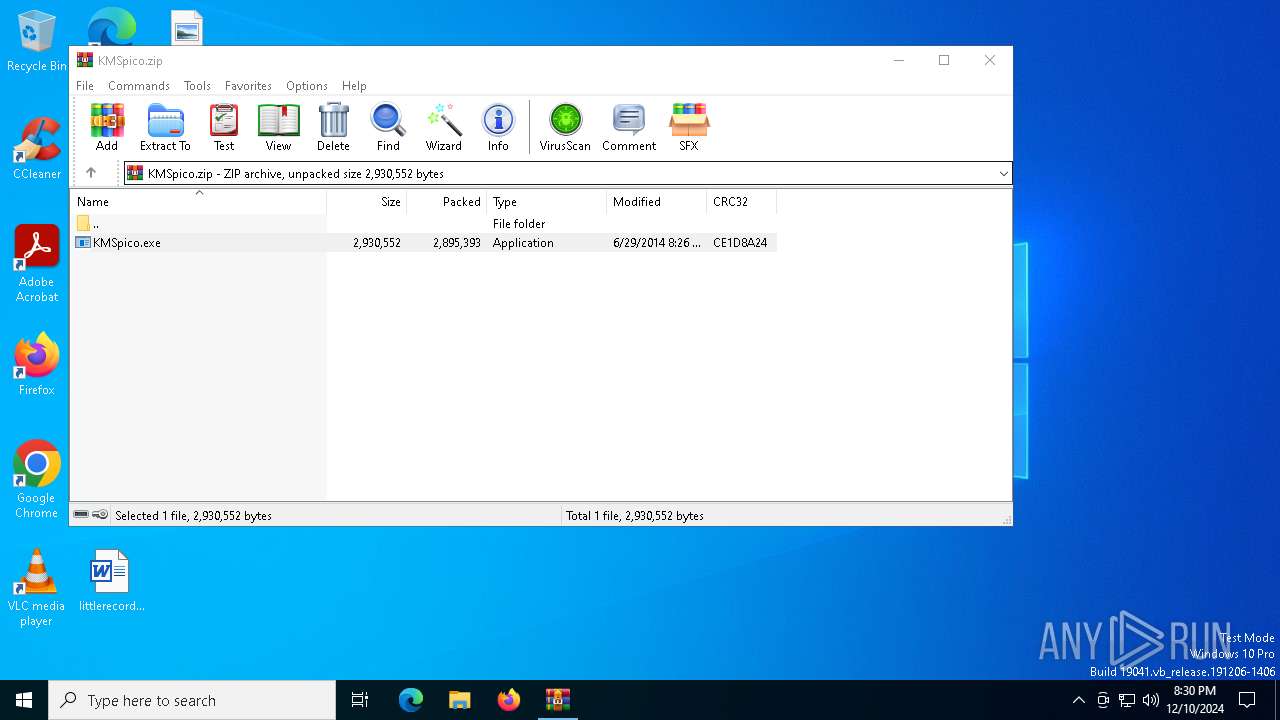
| File name: | KMSpico.zip |
| Full analysis: | https://app.any.run/tasks/5b5dc92b-94f9-4d66-b47c-62f512aad8e2 |
| Verdict: | Malicious activity |
| Analysis date: | December 10, 2024, 20:29:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D34E6F0A86C9EA7ACAA05869DF52045B |
| SHA1: | 08D45A80E4BC9F6B089F4546319FD3579FEF93F0 |
| SHA256: | E79A55C17A8D838EAD3CDE1630848FE2EDDC611E3D0742F47E8BDFAAE4279F8B |
| SSDEEP: | 98304:7/do1NRCYJM2bDKekRYf2EIsMjNFMu3dFBAo1nB0VR9qQAGDw6U0xRJVCcp50WXX:2rn88 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6220)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6188)
Executing a file with an untrusted certificate
- KMSELDI.exe (PID: 4076)
- AutoPico.exe (PID: 6792)
Changes image file execution options
- KMSELDI.exe (PID: 4076)
- AutoPico.exe (PID: 6792)
- KMSELDI.exe (PID: 1616)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6220)
- KMSpico.tmp (PID: 6512)
Executable content was dropped or overwritten
- KMSpico.exe (PID: 6484)
- KMSpico.exe (PID: 6652)
- KMSpico.tmp (PID: 6680)
- KMSELDI.exe (PID: 4076)
- KMSELDI.exe (PID: 1616)
- AutoPico.exe (PID: 6792)
Reads the Windows owner or organization settings
- KMSpico.tmp (PID: 6680)
Process drops legitimate windows executable
- KMSpico.tmp (PID: 6680)
Executing commands from ".cmd" file
- KMSpico.tmp (PID: 6680)
Starts SC.EXE for service management
- cmd.exe (PID: 4052)
Starts CMD.EXE for commands execution
- KMSpico.tmp (PID: 6680)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6220)
Create files in a temporary directory
- KMSpico.exe (PID: 6484)
- KMSpico.exe (PID: 6652)
Checks supported languages
- KMSpico.exe (PID: 6484)
- KMSpico.tmp (PID: 6512)
- KMSpico.tmp (PID: 6680)
- KMSpico.exe (PID: 6652)
- KMSELDI.exe (PID: 4076)
- OEM-DM.exe (PID: 1804)
- AutoPico.exe (PID: 6792)
- KMSELDI.exe (PID: 1616)
- OEM-DM.exe (PID: 6964)
Reads the computer name
- KMSpico.tmp (PID: 6512)
- KMSpico.tmp (PID: 6680)
- OEM-DM.exe (PID: 1804)
- AutoPico.exe (PID: 6792)
- OEM-DM.exe (PID: 1016)
- OEM-DM.exe (PID: 6964)
Process checks computer location settings
- KMSpico.tmp (PID: 6512)
The sample compiled with english language support
- KMSpico.tmp (PID: 6680)
Creates files in the program directory
- KMSpico.tmp (PID: 6680)
- KMSELDI.exe (PID: 4076)
- KMSELDI.exe (PID: 1616)
Reads Microsoft Office registry keys
- KMSELDI.exe (PID: 4076)
Reads the machine GUID from the registry
- KMSELDI.exe (PID: 4076)
- KMSELDI.exe (PID: 1616)
Reads product name
- AutoPico.exe (PID: 6792)
- KMSELDI.exe (PID: 1616)
Manual execution by a user
- KMSELDI.exe (PID: 4504)
- KMSELDI.exe (PID: 1616)
Reads Environment values
- KMSELDI.exe (PID: 1616)
- AutoPico.exe (PID: 6792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2014:06:29 20:26:32 |
| ZipCRC: | 0xce1d8a24 |
| ZipCompressedSize: | 2895393 |
| ZipUncompressedSize: | 2930552 |
| ZipFileName: | KMSpico.exe |
Total processes
152
Monitored processes
23
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1016 | "C:\Program Files\KMSpico\OEM-DM.exe" | C:\Program Files\KMSpico\OEM-DM.exe | — | AutoPico.exe | |||||||||||
User: admin Integrity Level: HIGH Description: MSDM Key Dump Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
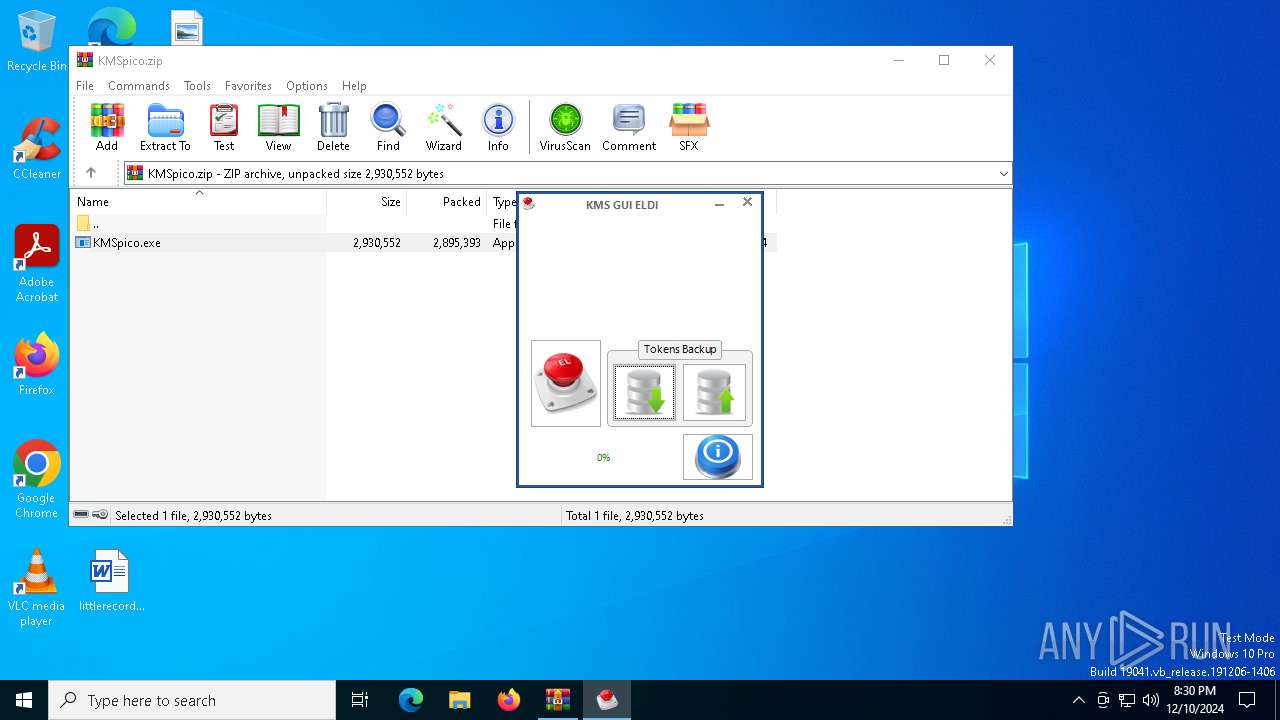
| 1616 | "C:\Program Files\KMSpico\KMSELDI.exe" | C:\Program Files\KMSpico\KMSELDI.exe | explorer.exe | ||||||||||||
User: admin Company: @ByELDI Integrity Level: HIGH Description: KMS GUI ELDI Version: 33.3.0.0 Modules
| |||||||||||||||
| 1804 | "C:\Program Files\KMSpico\OEM-DM.exe" | C:\Program Files\KMSpico\OEM-DM.exe | — | KMSELDI.exe | |||||||||||
User: admin Integrity Level: HIGH Description: MSDM Key Dump Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | OEM-DM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2436 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3564 | SCHTASKS /Create /TN "Service KMSELDI" /TR "sc.exe start "Service KMSELDI"" /SC DAILY /ST 04:59:59 /RI 330 /DU 12:00 /RU SYSTEM /RL Highest /F | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 2147500037 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3724 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4052 | "C:\WINDOWS\system32\cmd.exe" /C ""C:\Program Files\KMSpico\scripts\Install_Service.cmd"" | C:\Windows\System32\cmd.exe | — | KMSpico.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4076 | "C:\Program Files\KMSpico\KMSELDI.exe" /backup /silent | C:\Program Files\KMSpico\KMSELDI.exe | KMSpico.tmp | ||||||||||||
User: admin Company: @ByELDI Integrity Level: HIGH Description: KMS GUI ELDI Exit code: 0 Version: 33.3.0.0 Modules
| |||||||||||||||
| 4504 | "C:\Program Files\KMSpico\KMSELDI.exe" | C:\Program Files\KMSpico\KMSELDI.exe | — | explorer.exe | |||||||||||
User: admin Company: @ByELDI Integrity Level: MEDIUM Description: KMS GUI ELDI Exit code: 3221226540 Version: 33.3.0.0 Modules
| |||||||||||||||
Total events
8 177
Read events
8 081
Write events
89
Delete events
7
Modification events
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMSpico.zip | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6680) KMSpico.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | delete value | Name: | EnableSmartScreen |
Value: | |||
| (PID) Process: | (6680) KMSpico.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | write | Name: | EnableSmartScreen |
Value: 0 | |||
Executable files
22
Suspicious files
11
Text files
877
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6680 | KMSpico.tmp | C:\Users\admin\AppData\Local\Temp\is-94CJ6.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 6680 | KMSpico.tmp | C:\Users\admin\AppData\Local\Temp\is-94CJ6.tmp\_isetup\_setup64.tmp | executable | |
MD5:C8871EFD8AF2CF4D9D42D1FF8FADBF89 | SHA256:E4FC574A01B272C2D0AED0EC813F6D75212E2A15A5F5C417129DD65D69768F40 | |||
| 6484 | KMSpico.exe | C:\Users\admin\AppData\Local\Temp\is-8KHQP.tmp\KMSpico.tmp | executable | |
MD5:7060027EB4044B1D80C19F47CC87CDC7 | SHA256:383D09D76BDFE36C4CD700A70D985D568BE66C54C3B15E53670CD646074F2383 | |||
| 6220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6220.39184\KMSpico.exe | executable | |
MD5:EED1A4AF9D7080B2283BF50F551DDE72 | SHA256:38AF4D0ABB7D92A528BD05A3561DFE288CEC9388B3EF6066B4AF8E6AB91304D0 | |||
| 6680 | KMSpico.tmp | C:\Program Files\KMSpico\is-PGK6I.tmp | executable | |
MD5:EE81C6A4186274E057ADC1EE623137A5 | SHA256:5DE1745C9B3B32EE1FC264B77BED27944EDBFEFF5A4B1B9B765F6BB30A9CB647 | |||
| 6680 | KMSpico.tmp | C:\Program Files\KMSpico\is-HSLSE.tmp | binary | |
MD5:67115DFDA5935F743CBF81F85C5E763C | SHA256:BE090348B66D8B4A478DB2C958AF92A04A4BEA631E346323E0A5B355CD80C0E7 | |||
| 6680 | KMSpico.tmp | C:\Program Files\KMSpico\DevComponents.DotNetBar2.dll | binary | |
MD5:67115DFDA5935F743CBF81F85C5E763C | SHA256:BE090348B66D8B4A478DB2C958AF92A04A4BEA631E346323E0A5B355CD80C0E7 | |||
| 6680 | KMSpico.tmp | C:\Program Files\KMSpico\AutoPico.exe | executable | |
MD5:EE81C6A4186274E057ADC1EE623137A5 | SHA256:5DE1745C9B3B32EE1FC264B77BED27944EDBFEFF5A4B1B9B765F6BB30A9CB647 | |||
| 6680 | KMSpico.tmp | C:\Program Files\KMSpico\is-UIU14.tmp | executable | |
MD5:8F36A9E4D7A4E51AC41CFA85E01A4294 | SHA256:7A6BC0AE4129F80C321DD2500A974A6B1E77829F76FDDB57F36CBB886E6C295F | |||
| 6680 | KMSpico.tmp | C:\Program Files\KMSpico\is-73DCS.tmp | executable | |
MD5:2166FCBDD90C8514504CF69683F5C9BB | SHA256:304D70AA483359DCCDEBA954B2B6D444D50FC92EF1E1F8BA808181FD1C247029 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
49
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7064 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7064 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3080 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.137:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.137:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 92.123.104.30:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |