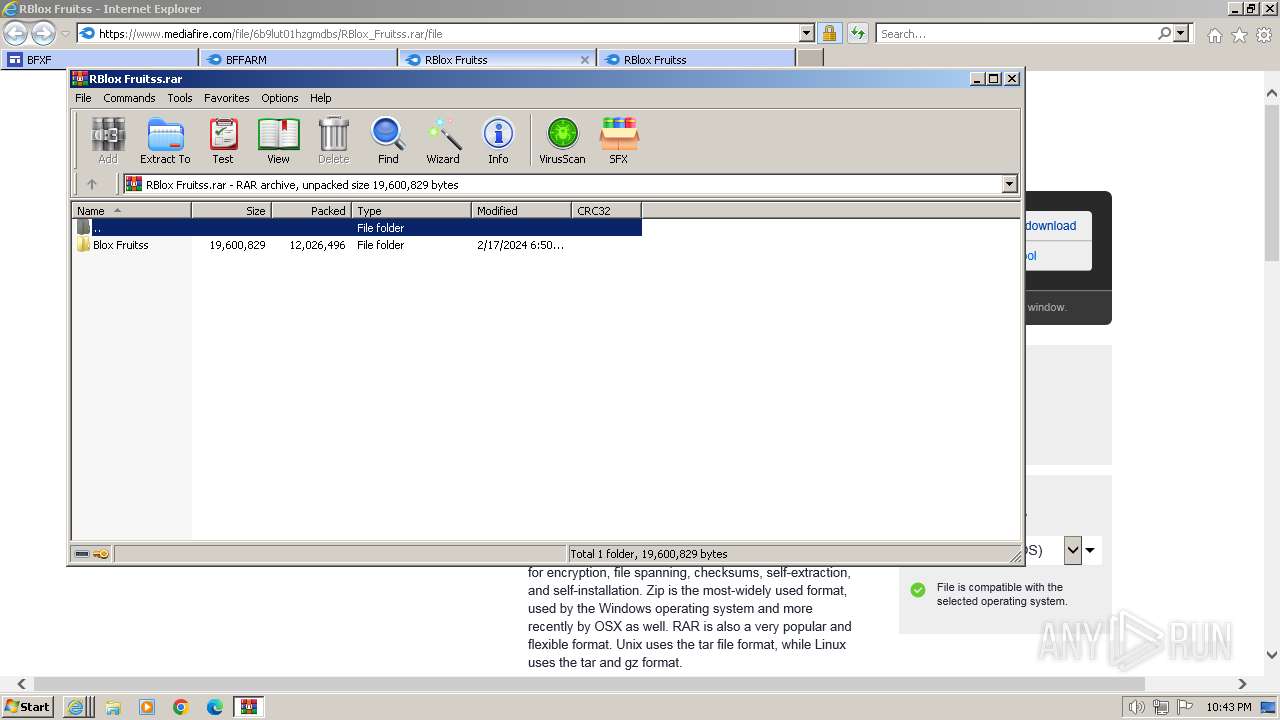
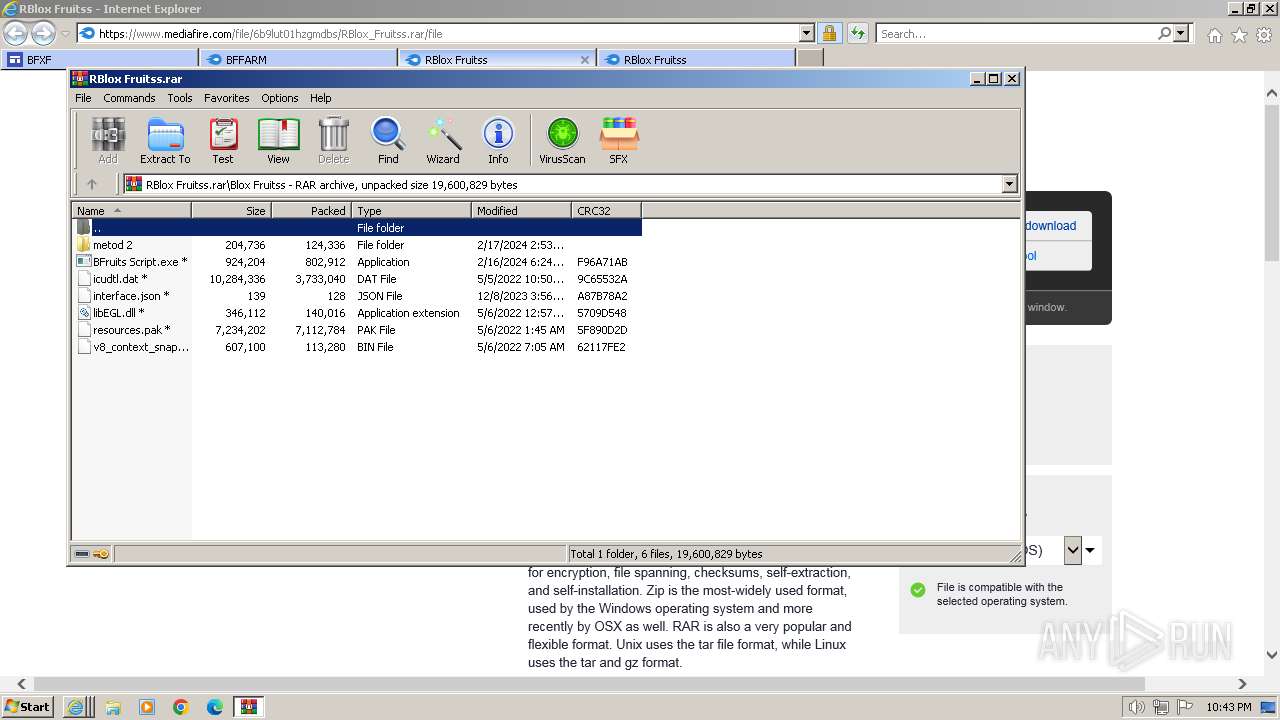
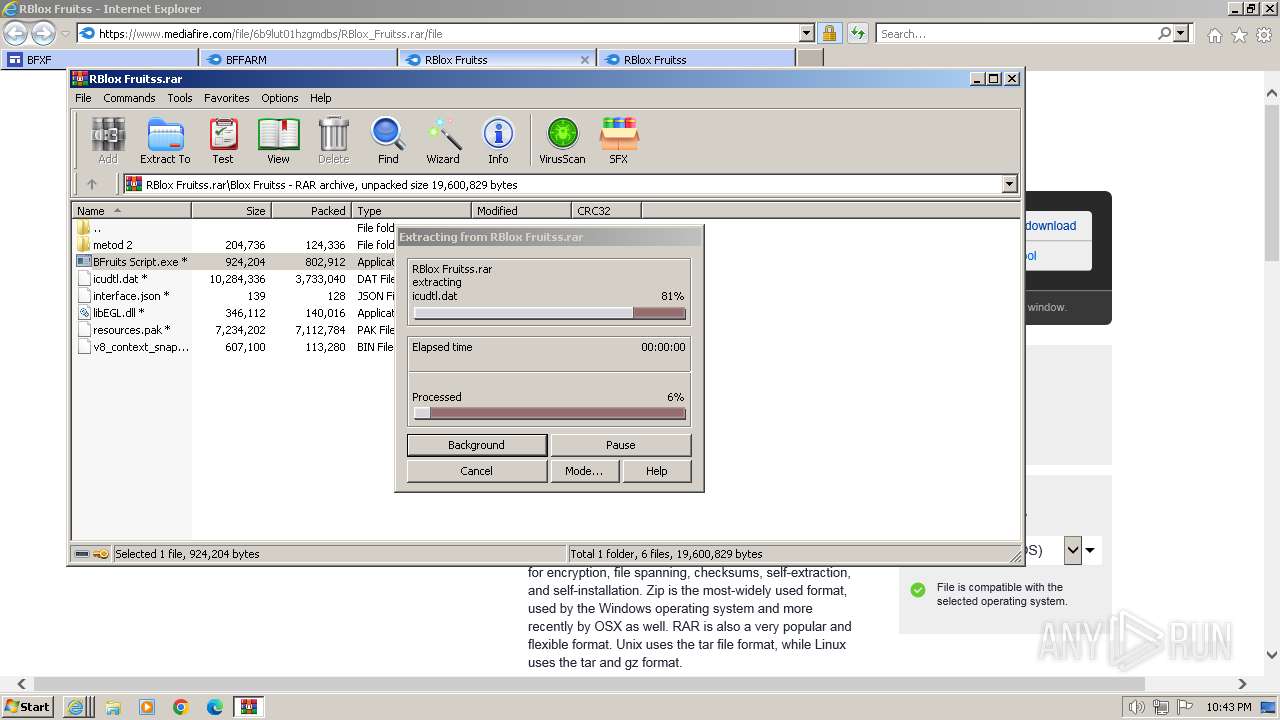
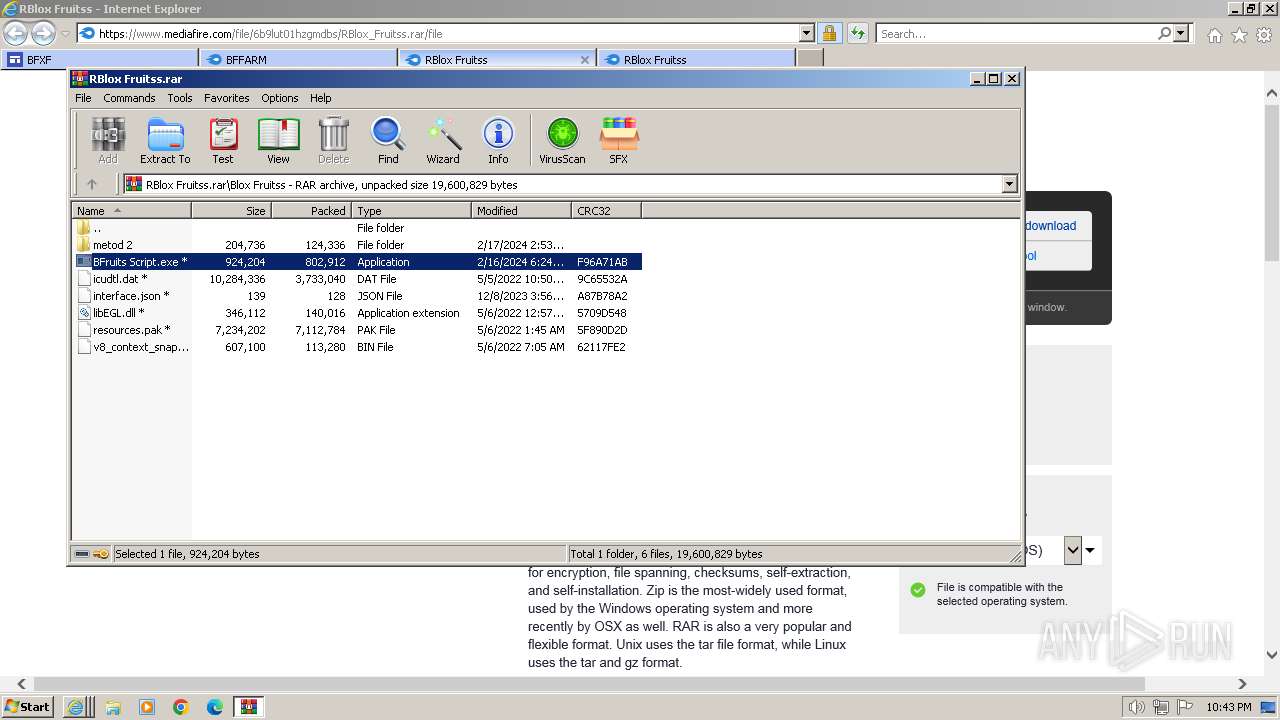
| URL: | https://sites.google.com/view/bfxj |
| Full analysis: | https://app.any.run/tasks/f0d6bc4a-a155-4b85-8bd2-5ce40471c2f4 |
| Verdict: | Malicious activity |
| Analysis date: | February 18, 2024, 22:40:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 72134BC5FDDE3246066BCDB44F0297D5 |
| SHA1: | 2CCC389A5CDEF97B8D082A30C74745647ADCBE05 |
| SHA256: | E79025F70B833854C11E2354712335DED39C8B1486FDEE92B42239B3D0A055A3 |
| SSDEEP: | 3:N8BhLJ3u1ndP:2J+3 |
MALICIOUS
Drops the executable file immediately after the start
- BFruits Script.exe (PID: 3172)
- cmd.exe (PID: 3988)
- BFruits Script.exe (PID: 3524)
- cmd.exe (PID: 3608)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 2736)
- findstr.exe (PID: 3152)
- findstr.exe (PID: 2512)
- findstr.exe (PID: 3060)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2560)
- BFruits Script.exe (PID: 3172)
- BFruits Script.exe (PID: 3524)
Executable content was dropped or overwritten
- BFruits Script.exe (PID: 3172)
- cmd.exe (PID: 3988)
- BFruits Script.exe (PID: 3524)
- cmd.exe (PID: 3608)
Reads the Internet Settings
- BFruits Script.exe (PID: 3172)
- BFruits Script.exe (PID: 3524)
Starts CMD.EXE for commands execution
- BFruits Script.exe (PID: 3172)
- cmd.exe (PID: 3292)
- BFruits Script.exe (PID: 3524)
- cmd.exe (PID: 3048)
Get information on the list of running processes
- cmd.exe (PID: 3292)
- cmd.exe (PID: 3048)
Executing commands from a ".bat" file
- BFruits Script.exe (PID: 3172)
- BFruits Script.exe (PID: 3524)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3292)
- cmd.exe (PID: 3048)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 3988)
- cmd.exe (PID: 3608)
Application launched itself
- cmd.exe (PID: 3292)
- cmd.exe (PID: 3048)
Starts application with an unusual extension
- cmd.exe (PID: 3292)
- cmd.exe (PID: 3048)
The executable file from the user directory is run by the CMD process
- Parking.pif (PID: 3744)
- Parking.pif (PID: 3452)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 3292)
- cmd.exe (PID: 3048)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3972)
Reads the computer name
- wmpnscfg.exe (PID: 3972)
- BFruits Script.exe (PID: 3172)
- BFruits Script.exe (PID: 3524)
- Parking.pif (PID: 3744)
- Parking.pif (PID: 3452)
Checks supported languages
- wmpnscfg.exe (PID: 3972)
- BFruits Script.exe (PID: 3172)
- Parking.pif (PID: 3744)
- BFruits Script.exe (PID: 3524)
- Parking.pif (PID: 3452)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2560)
The process uses the downloaded file
- iexplore.exe (PID: 3668)
- WinRAR.exe (PID: 2560)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3668)
Application launched itself
- iexplore.exe (PID: 3668)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2560)
Create files in a temporary directory
- BFruits Script.exe (PID: 3172)
- BFruits Script.exe (PID: 3524)
Reads mouse settings
- Parking.pif (PID: 3744)
- Parking.pif (PID: 3452)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
70
Monitored processes
28
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1816 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3668 CREDAT:2430266 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2448 | cmd /c copy /b Desktops + Crafts 21261\k | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2512 | findstr /I "avastui.exe avgui.exe nswscsvc.exe sophoshealth.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
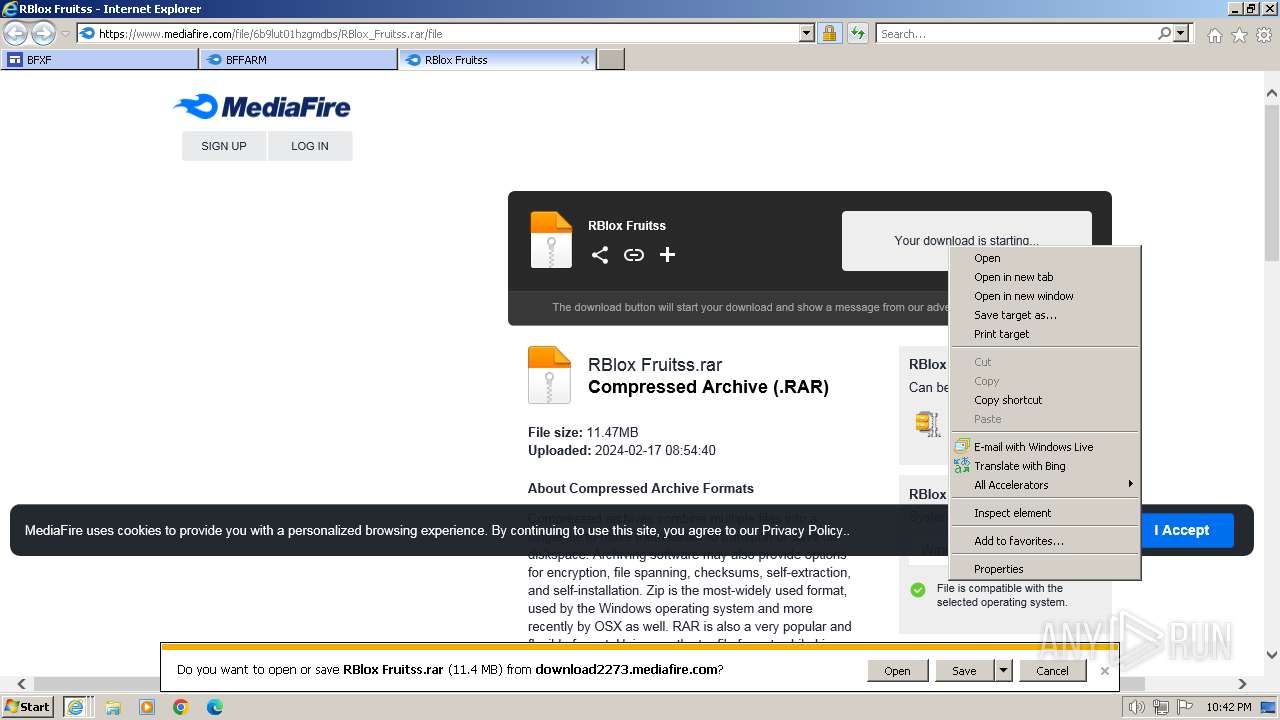
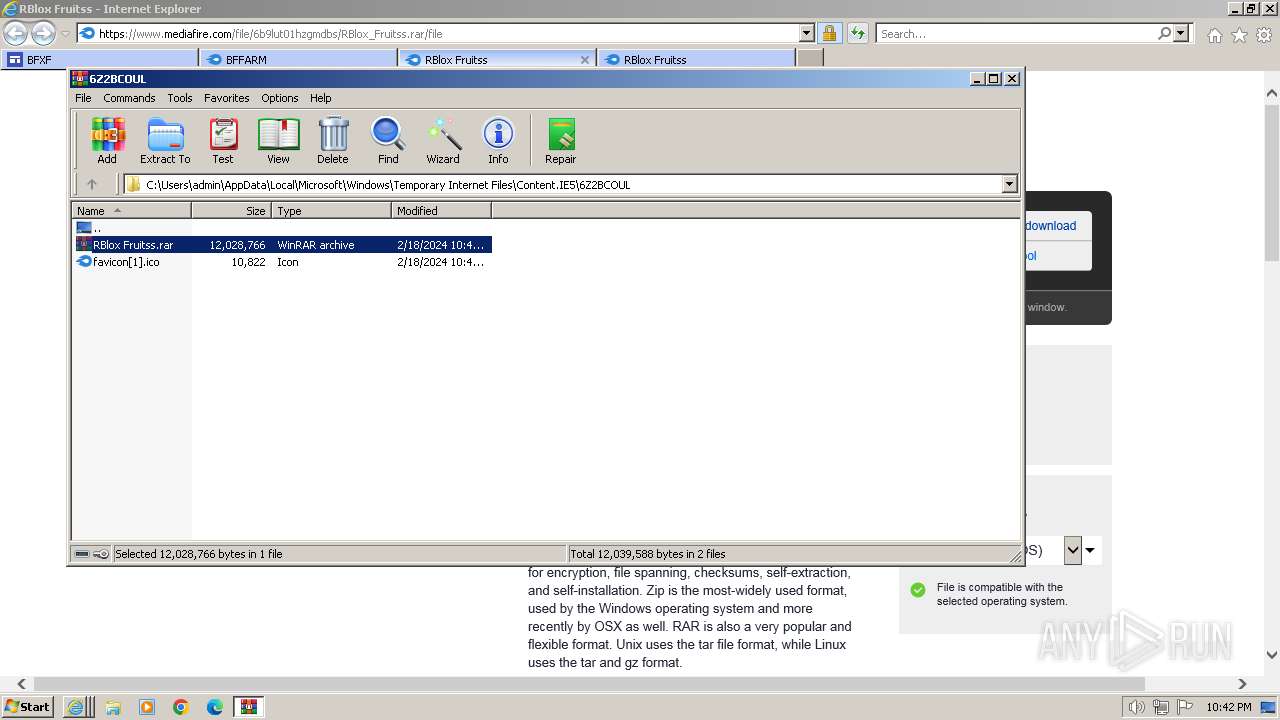
| 2560 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\RBlox Fruitss.rar" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2672 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3668 CREDAT:201997 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2736 | findstr /I "wrsa.exe opssvc.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3048 | "C:\Windows\System32\cmd.exe" /k move Agenda Agenda.bat & Agenda.bat & exit | C:\Windows\System32\cmd.exe | — | BFruits Script.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3060 | findstr /I "wrsa.exe opssvc.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3152 | findstr /I "avastui.exe avgui.exe nswscsvc.exe sophoshealth.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
58 235
Read events
57 968
Write events
211
Delete events
56
Modification events
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31089339 | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31089339 | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
10
Suspicious files
72
Text files
218
Unknown types
31
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:426883AB3344EB08FFC527A97B3D7154 | SHA256:8DF226FAAAC6B5BC856F57E6475A540262AA774E188AAE7CB832F8E8ACEF0566 | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:37BA9853365204D2B545F170F7C00F82 | SHA256:E60B8E946634937954F99FF5CE923FA227DDDFEDD65DE057C4262C7AC032DF75 | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A16C6C16D94F76E0808C087DFC657D99_A6E345A209B7DF4ADB773E2D365D8E1A | binary | |
MD5:10599CF459906071346E2A958D7E84D5 | SHA256:883759255693F69AE01C56295B7F1B49009EF96D4D712B7950E3B59A3CFDD0F4 | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A16C6C16D94F76E0808C087DFC657D99_8F986B155B6342EE1ACF678AFF6889B0 | binary | |
MD5:53BAD231622AE88A84FF69871D44C821 | SHA256:E105364F8ABAE75E7CA14A6131EB1C414D20C59476B55E30F5DC1985D613762F | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A16C6C16D94F76E0808C087DFC657D99_A6E345A209B7DF4ADB773E2D365D8E1A | binary | |
MD5:9CF87987CEAB48023D951DD83D267575 | SHA256:A5F06ED1BED28AA4488F00DC1648407CDD7352A3CFCE4638E3837E9808D49113 | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\rs=AGEqA5k4YenpCrANdfK_roCV4YYEhfGNpA[1].css | text | |
MD5:5E211A1DD30C5F4E89D26659DF5EF2A1 | SHA256:CD326C77AB92F21FF99F6BB2F684F19F298C946D594FC85B56247E9BFE205F1A | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A16C6C16D94F76E0808C087DFC657D99_8F986B155B6342EE1ACF678AFF6889B0 | binary | |
MD5:0C775CDAB0B027AD439761A5DDEFDCC6 | SHA256:FC1DC11221E57A97C4544568EEB3D4FDECEB386C8A945BD7E33BAB0C375F291C | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\bfxj[1].htm | html | |
MD5:2946DB3354F3547010C7D337CA7D5F17 | SHA256:B3AC1C40125A60526E9D6E75307AE36F64E1451D3CC2A8CF7BF00096E0830E4B | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\css[1].css | text | |
MD5:DC7F931B0DDAC3733F03720B77E9860C | SHA256:0BEEA499A00CA310C5603B9A0DEDF6CB697CFD2025CF1BCFE52B1D20A015D9A0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
151
DNS requests
56
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3664 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?545e1839169dd0e6 | unknown | — | — | unknown |
3664 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f78d505714a595e3 | unknown | — | — | unknown |
3664 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3664 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCSnN9%2FWcCK6QmbjMlxbrBK | unknown | binary | 472 b | unknown |
3664 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3664 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCAKlf1nuem1AlkNvBwxf5A | unknown | binary | 472 b | unknown |
3664 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEAch2W18yjrFCctU7xjW0Yc%3D | unknown | binary | 471 b | unknown |
3664 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCMm6oE1xo69QktXqx4YFni | unknown | binary | 472 b | unknown |
3664 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCMm6oE1xo69QktXqx4YFni | unknown | binary | 472 b | unknown |
3668 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?18014fff35250a83 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3664 | iexplore.exe | 142.250.184.238:443 | sites.google.com | GOOGLE | US | whitelisted |
3664 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3664 | iexplore.exe | 142.250.185.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3664 | iexplore.exe | 142.250.185.138:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
3664 | iexplore.exe | 142.250.186.131:443 | www.gstatic.com | GOOGLE | US | whitelisted |
3664 | iexplore.exe | 142.250.185.78:443 | apis.google.com | GOOGLE | US | whitelisted |
3664 | iexplore.exe | 142.250.186.35:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sites.google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |