| File name: | e78585b251b21b8a29f1764edece62719e73103f583585b5d35e5e2f1cf9c409 |
| Full analysis: | https://app.any.run/tasks/18407c65-0273-425b-99d3-5df802a2299e |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 20:47:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1251, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Mon Apr 11 09:14:00 2016, Last Saved Time/Date: Mon Apr 11 14:11:00 2016, Number of Pages: 1, Number of Words: 6, Number of Characters: 36, Security: 0 |
| MD5: | C2EC2EE7824A8BD2A2A049EC9D348E2B |
| SHA1: | 22515FCF60A21BBAD54F0BE5D61118310E0F9B84 |
| SHA256: | E78585B251B21B8A29F1764EDECE62719E73103F583585B5D35E5E2F1CF9C409 |
| SSDEEP: | 3072:LhjyJNLCFxSl6CkuzTAE3urKzsQCsJVc2oemTxRSKUqla6BU4fW4+:NO/2el6Ck4TL3HXCsJVzoXjo+U0W4+ |
MALICIOUS
Unusual execution from MS Office
- WINWORD.EXE (PID: 2644)
SUSPICIOUS
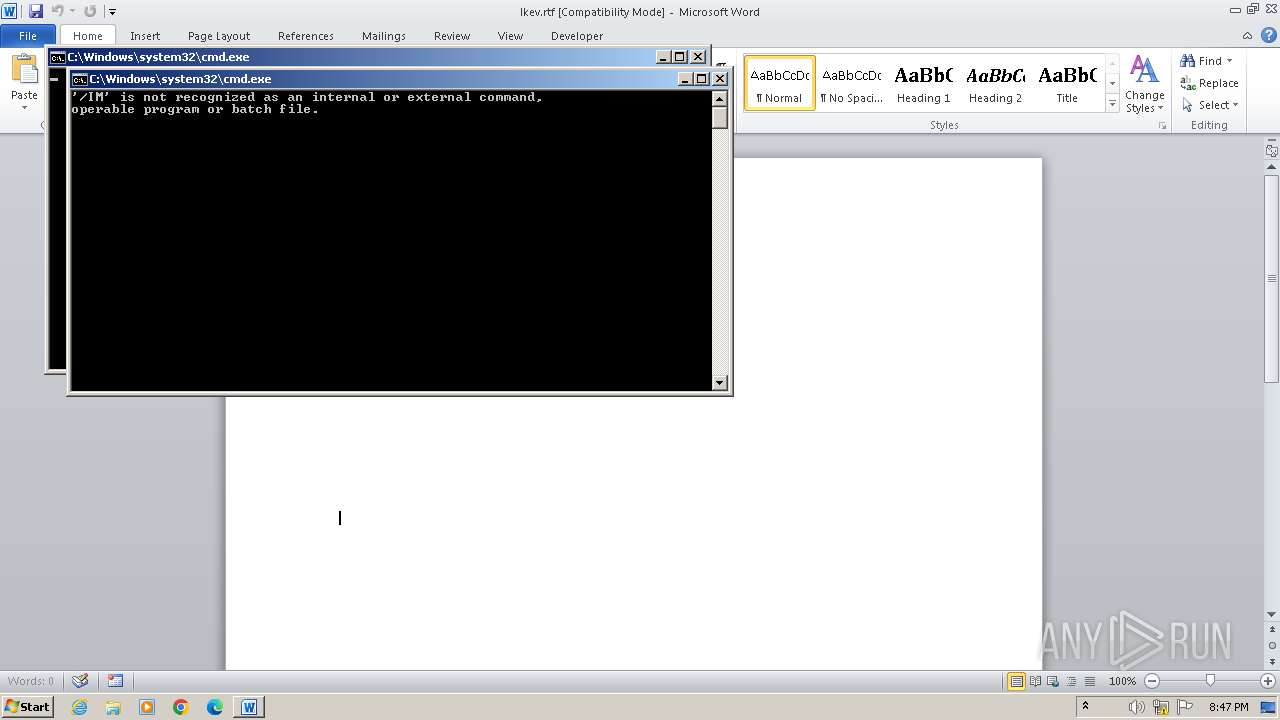
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 2644)
Starts CMD.EXE for commands execution
- q1.gif (PID: 2920)
Starts application with an unusual extension
- WINWORD.EXE (PID: 2644)
INFO
Checks supported languages
- q1.gif (PID: 2920)
Drops the executable file immediately after the start
- WINWORD.EXE (PID: 124)
The process uses the downloaded file
- WINWORD.EXE (PID: 124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (35.9) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (33.7) |
| .doc | | | Microsoft Word document (old ver.) (21.3) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| Software: | Microsoft Office Word |
| CreateDate: | 2016:04:11 08:14:00 |
| ModifyDate: | 2016:04:11 13:11:00 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Company: | - |
| CharCountWithSpaces: | 41 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | ???????? Microsoft Word 97-2003 |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 6 |
| Characters: | 36 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
44
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Automation -Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1852 | C:\Windows\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | q1.gif | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2136 | C:\Windows\system32\cmd.exe /c /IM | C:\Windows\System32\cmd.exe | — | q1.gif | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2644 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\e78585b251b21b8a29f1764edece62719e73103f583585b5d35e5e2f1cf9c409.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2920 | C:\Users\admin\AppData\Local\Temp\q1.gif | C:\Users\admin\AppData\Local\Temp\q1.gif | — | WINWORD.EXE | |||||||||||
User: admin Company: http://zenden.ws Integrity Level: MEDIUM Description: Fed 4074 Rong Achievable Exit code: 0 Version: 7.4.7.790 Modules
| |||||||||||||||
Total events
6 194
Read events
5 341
Write events
730
Delete events
123
Modification events
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
1
Suspicious files
13
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR647B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 124 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR7071.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\bveqq.rtf | text | |
MD5:6911E5D8C83B4717A927880032B6F298 | SHA256:B1CAD0A895B6F6F1C25FB77596E75D40CB770C81AD8C062722252EAA1A1FAD1F | |||
| 124 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\q1.gif:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 2644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$bveqq.rtf | binary | |
MD5:0C1C07353719F767EE4FFCF6B95A2840 | SHA256:76FFC7B14318AF83F8151FDCD3F600266996015437EA47D7920988681214E37D | |||
| 2644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\EC98212D.emf | binary | |
MD5:35C99DB31BD6001066D31A6A096A3D41 | SHA256:E859A0626D2F4AF5A2102866171AD7D8C5B5DDC90382D4B2459894194D7EBA53 | |||
| 124 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRC0000.tmp | document | |
MD5:989A3956166DC18EF86542DC0268C3E9 | SHA256:1083CA2AB383E7939EBFF1BB9BC1A94167A98003BF3B0A942FD9F35204A5D470 | |||
| 2644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~WRD0000.tmp | text | |
MD5:6911E5D8C83B4717A927880032B6F298 | SHA256:B1CAD0A895B6F6F1C25FB77596E75D40CB770C81AD8C062722252EAA1A1FAD1F | |||
| 2644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$8585b251b21b8a29f1764edece62719e73103f583585b5d35e5e2f1cf9c409.doc | binary | |
MD5:283CB51581D5175F59637425B526F692 | SHA256:170B6DC6A05E5713954D7DA97712F20E2F6D790F9866C3DF521922F2B5E65C7C | |||
| 2644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~WRD0001.tmp | text | |
MD5:D295C84B5B1B25B9772484447D501F3E | SHA256:0B810BC10C29AE40CCC607F0417DB6804D8842D37EBDEB07DAB7F31303C7CC2B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |