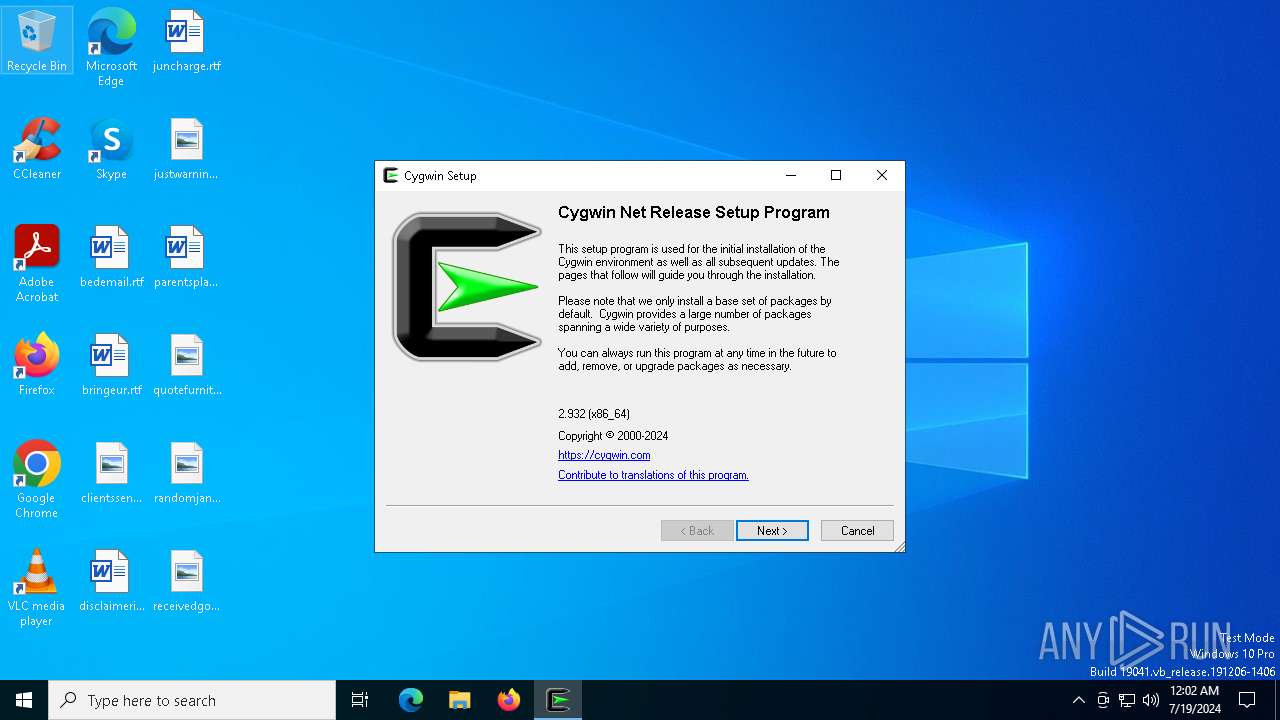
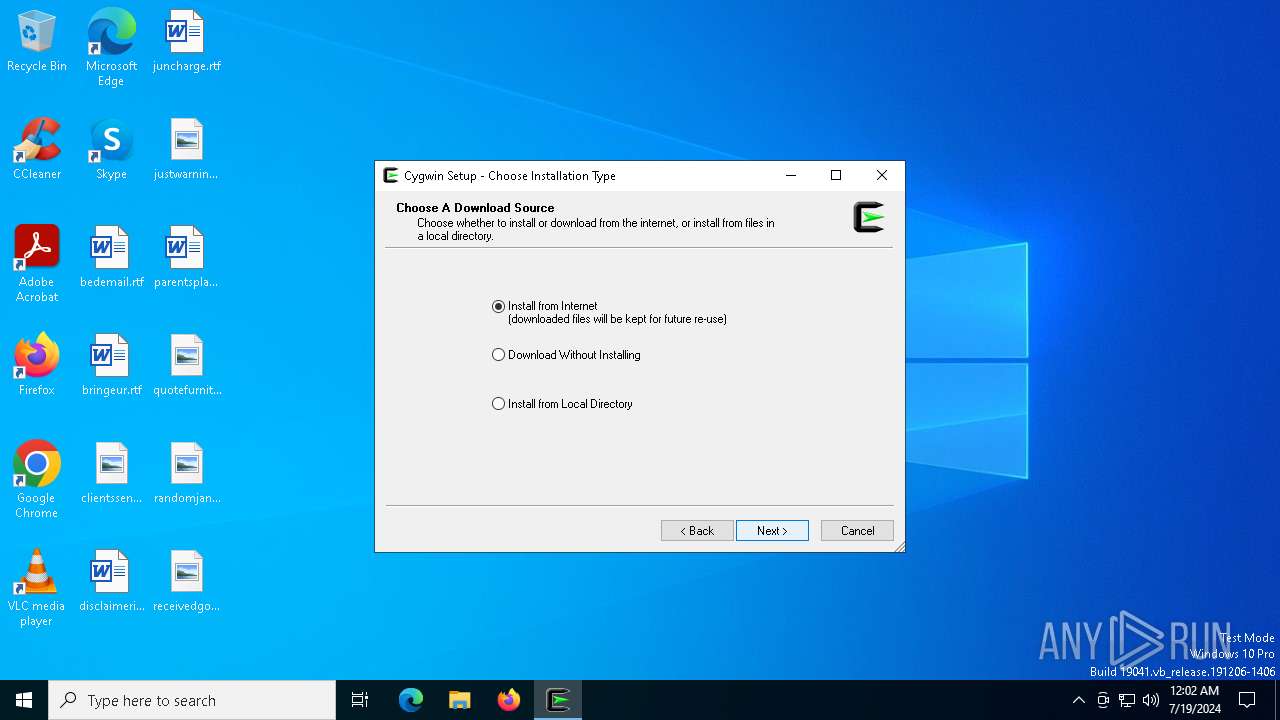
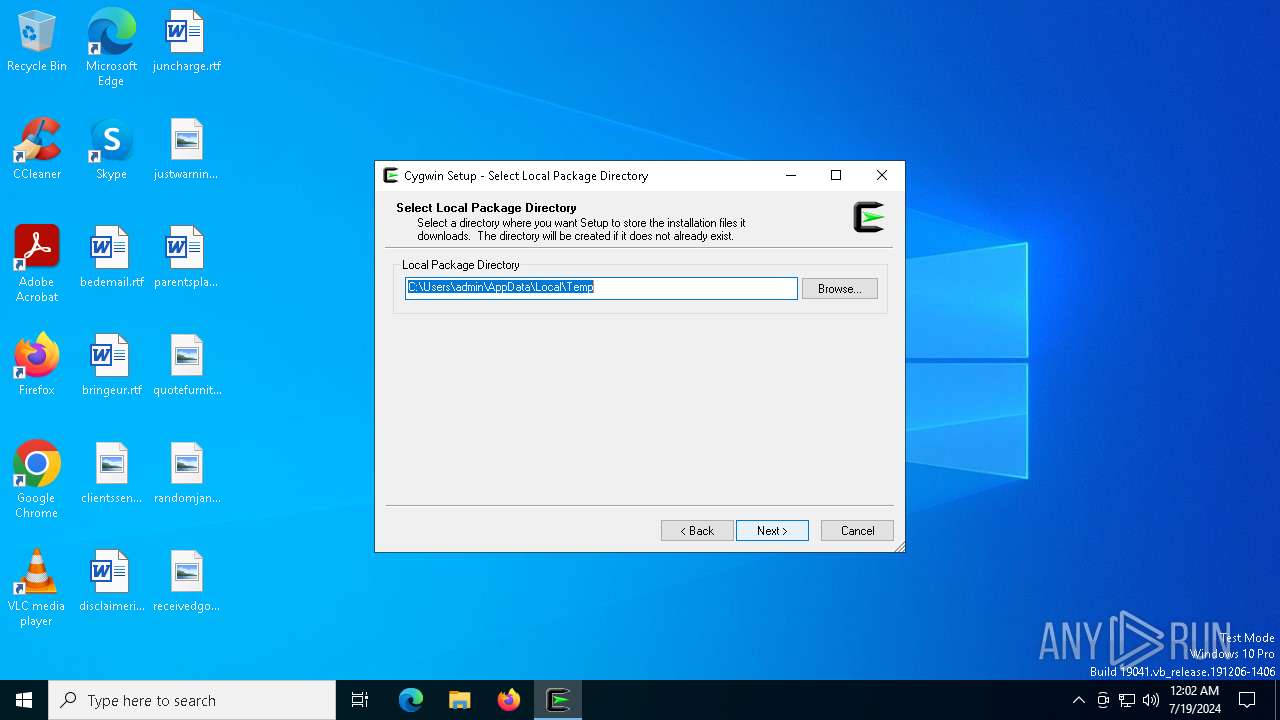
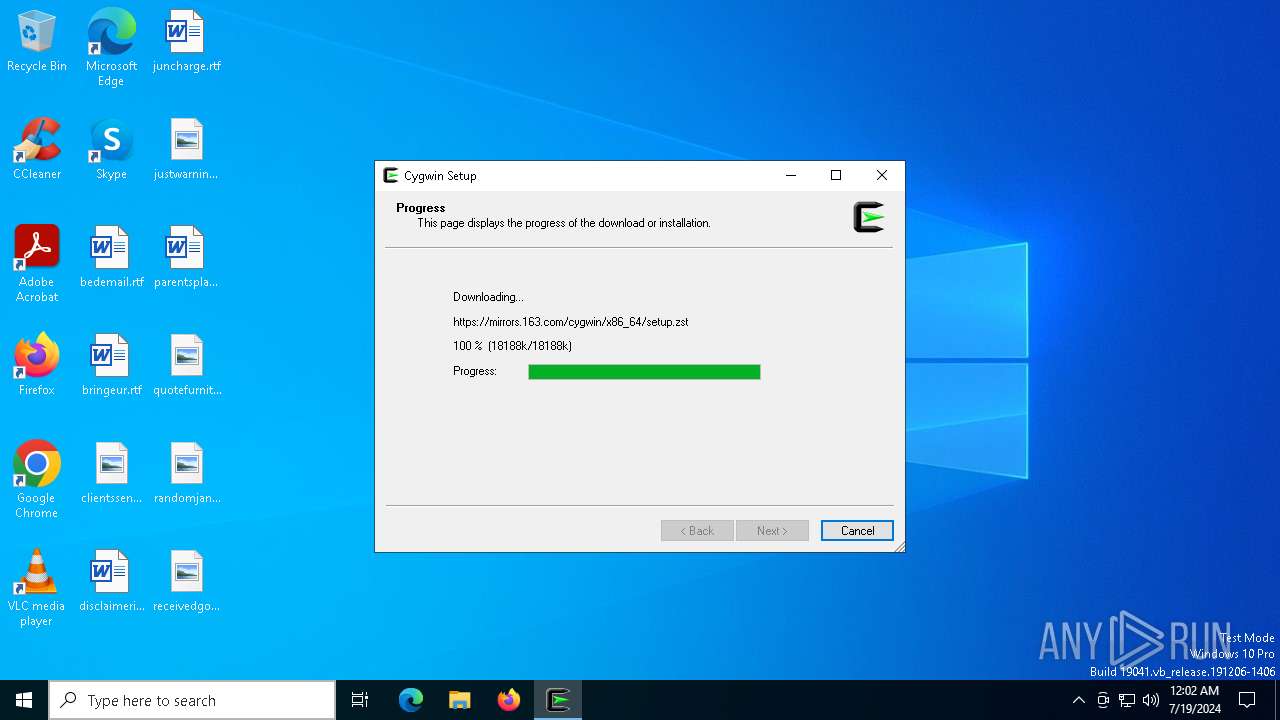
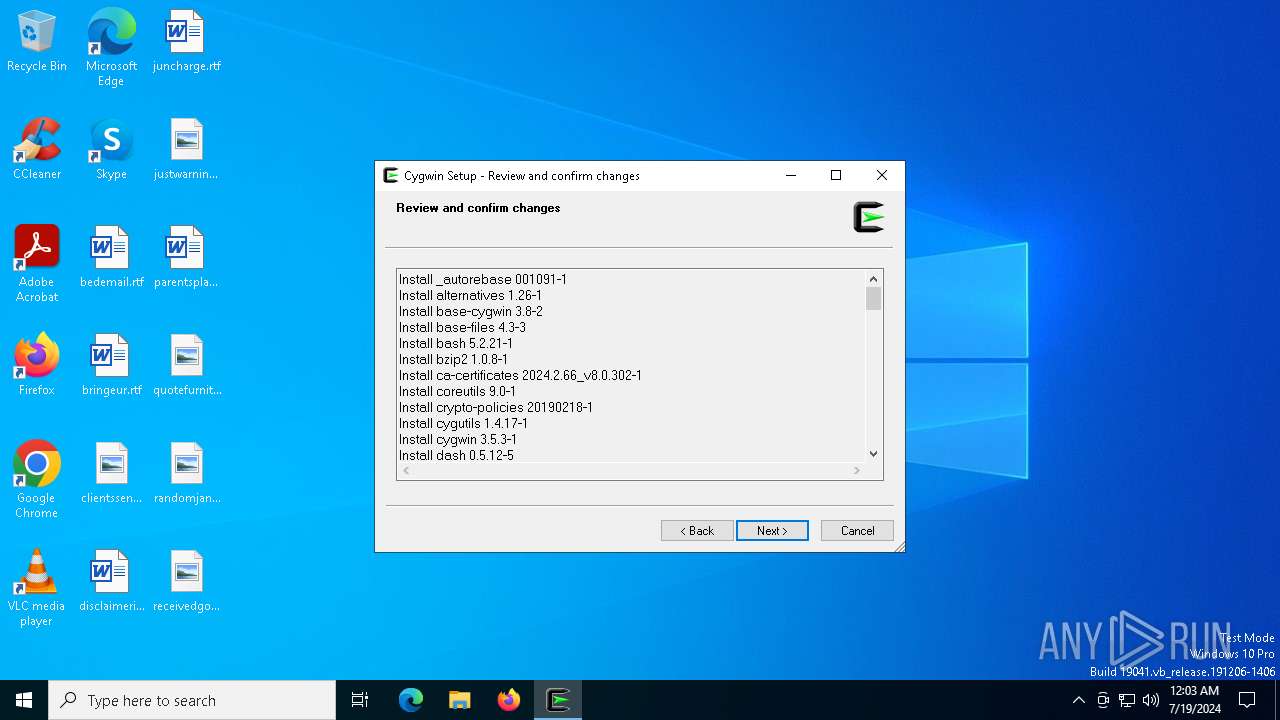
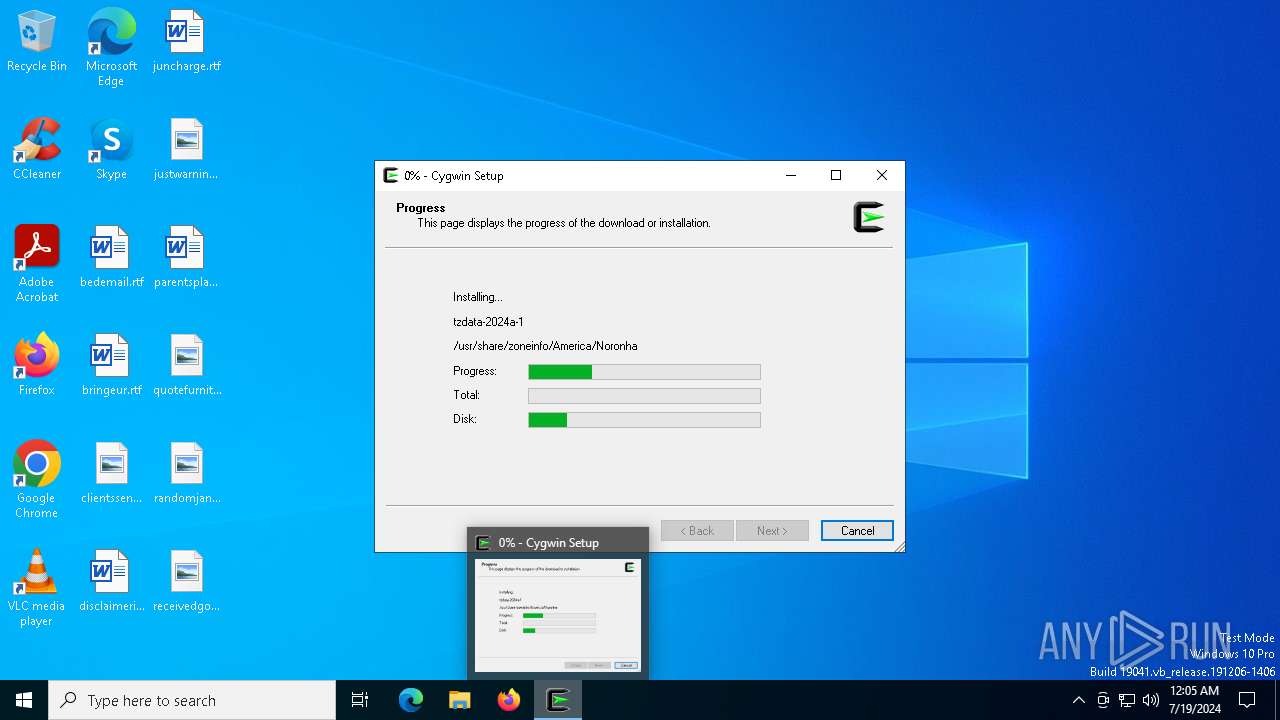
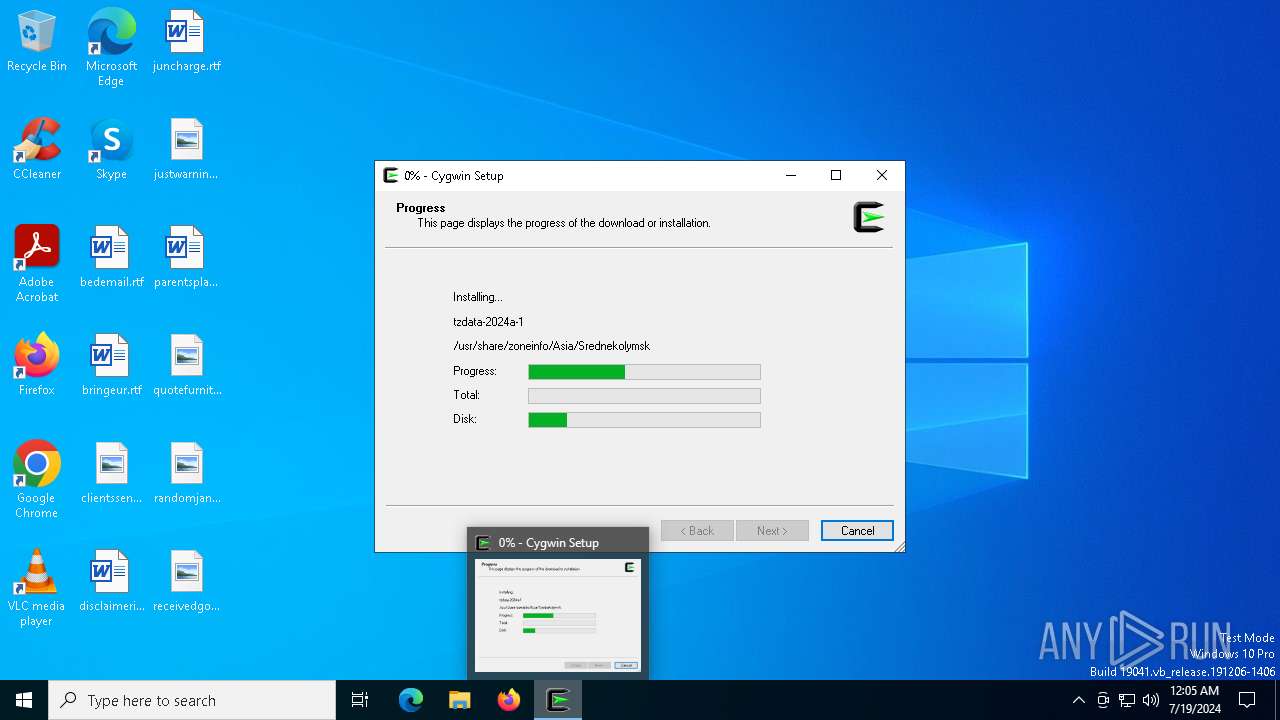
| File name: | setup-x86_64.exe |
| Full analysis: | https://app.any.run/tasks/ddefa758-6e88-44c1-ba0e-67fb1f09b88d |
| Verdict: | Malicious activity |
| Analysis date: | July 19, 2024, 00:02:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | A667FC9D471DD1BD0CD7A9AD9408024C |
| SHA1: | 382BFD2C2988773F53219843E59D43DFA13FA248 |
| SHA256: | E7815D360AB098FDD1F03F10F43F363C73A632E8866E304C72573CF1E6A0DEC8 |
| SSDEEP: | 49152:hw+gW4cC91q4tEv1WLuyKSPk6pQgh+yu4i61ejbfx1nvwEcD8qx9UuaxhACVFvkN:hw+PNt1WLvPpQg3u+1sb51nvw3D8Y99v |
MALICIOUS
Drops the executable file immediately after the start
- setup-x86_64.exe (PID: 7404)
- setup-x86_64.exe (PID: 8160)
SUSPICIOUS
Reads security settings of Internet Explorer
- setup-x86_64.exe (PID: 7404)
- setup-x86_64.exe (PID: 8160)
Reads the date of Windows installation
- setup-x86_64.exe (PID: 7404)
Application launched itself
- setup-x86_64.exe (PID: 7404)
Checks Windows Trust Settings
- setup-x86_64.exe (PID: 8160)
INFO
Checks supported languages
- setup-x86_64.exe (PID: 7404)
- setup-x86_64.exe (PID: 8160)
Reads the computer name
- setup-x86_64.exe (PID: 7404)
- setup-x86_64.exe (PID: 8160)
Process checks computer location settings
- setup-x86_64.exe (PID: 7404)
UPX packer has been detected
- setup-x86_64.exe (PID: 8160)
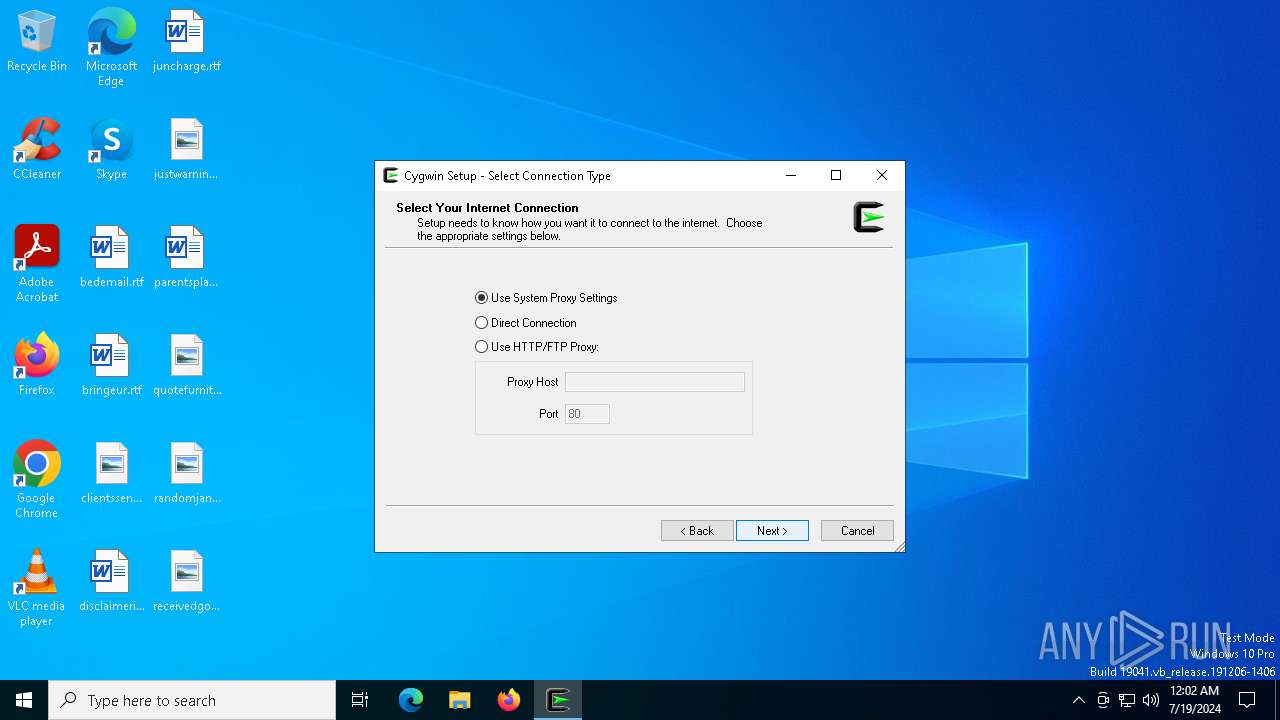
Checks proxy server information
- setup-x86_64.exe (PID: 8160)
Reads the machine GUID from the registry
- setup-x86_64.exe (PID: 8160)
Reads the software policy settings
- setup-x86_64.exe (PID: 8160)
Creates files or folders in the user directory
- setup-x86_64.exe (PID: 8160)
Create files in a temporary directory
- setup-x86_64.exe (PID: 8160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (87) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.4) |
| .exe | | | DOS Executable Generic (6.4) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.32 |
| CodeSize: | 1339392 |
| InitializedDataSize: | 73728 |
| UninitializedDataSize: | 3969024 |
| EntryPoint: | 0x50f420 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
121
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5520 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7404 | "C:\Users\admin\AppData\Local\Temp\setup-x86_64.exe" | C:\Users\admin\AppData\Local\Temp\setup-x86_64.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 8160 | "C:\Users\admin\AppData\Local\Temp\setup-x86_64.exe" -B | C:\Users\admin\AppData\Local\Temp\setup-x86_64.exe | setup-x86_64.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
4 543
Read events
4 523
Write events
20
Delete events
0
Modification events
| (PID) Process: | (7404) setup-x86_64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (7404) setup-x86_64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (7404) setup-x86_64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (7404) setup-x86_64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (8160) setup-x86_64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8160) setup-x86_64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8160) setup-x86_64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (8160) setup-x86_64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (8160) setup-x86_64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (8160) setup-x86_64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
0
Suspicious files
664
Text files
20
Unknown types
82
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
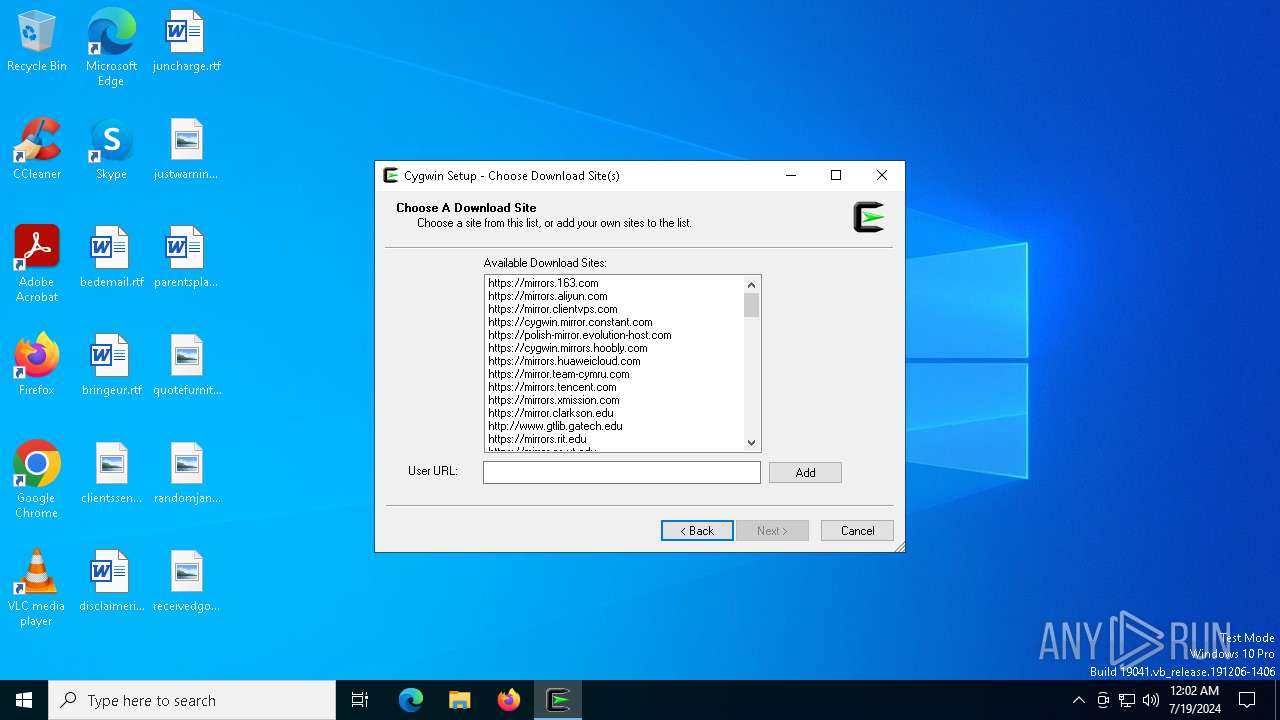
| 8160 | setup-x86_64.exe | C:\Users\admin\AppData\Local\Temp\https%3a%2f%2fmirrors.163.com%2fcygwin%2f\x86_64\setup.ini | — | |
MD5:— | SHA256:— | |||
| 8160 | setup-x86_64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\018A3FCAF3108930185172113A859CEB | binary | |
MD5:A196FD92E01B99C44E93491C36118094 | SHA256:643DC6ACA3A096F07E2D7DD83078C11F2C59DEEEB086BB0D7B0FD2D666DD74F3 | |||
| 8160 | setup-x86_64.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\mirrors[1].lst | text | |
MD5:50296C97162CD649529FCC4BD737DAF4 | SHA256:7899010AC2DBBB0A5636EE2F5CDFFC6E1EBE5E0BE3E2EA8B5F0F8740E7BA27F6 | |||
| 8160 | setup-x86_64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:3DFCA46E00FFA4795C72A41375F159D3 | SHA256:DCBA1A505396539BAC40A7253C9F5DCCF06CBB79957E21D56305E1FC3AF5F40E | |||
| 8160 | setup-x86_64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\018A3FCAF3108930185172113A859CEB | binary | |
MD5:316AC5DC47181F9950065FB2E5FC8E8D | SHA256:A08C91AF8F85AB11BDB0EA6E06F5E538E23884C20874892AD2AA1E11A3701287 | |||
| 8160 | setup-x86_64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B65229F95224AF781EBC900B5E8320B5 | binary | |
MD5:481F0784C5A4226D44DEC81B5A50B204 | SHA256:0997C1A253CE886F6A0980D6CA17F44F550AD536BB5D29BC5D408C9677A3BEE5 | |||
| 8160 | setup-x86_64.exe | C:\Users\admin\AppData\Local\Temp\https%3a%2f%2fmirrors.163.com%2fcygwin%2f\x86_64\release\popt\libpopt-common\libpopt-common-1.19-1.tar.xz.tmp | binary | |
MD5:F8E86A2098FE3A16867FEBFAA6AB9967 | SHA256:EE5DA725DA5C83A517F09E4FFD49183A26484E62A36E99BE84D5C0A0A711F77F | |||
| 8160 | setup-x86_64.exe | C:\Users\admin\AppData\Local\Temp\https%3a%2f%2fmirrors.163.com%2fcygwin%2f\noarch\release\tzdata\tzdata-2024a-1.tar.xz.tmp | binary | |
MD5:8F365E858A12ED39EE8CE59F1171EB71 | SHA256:BE04AAE1F2A6190F2B40572AC9E23355CED96E62D024449721CE70037CBC7B8C | |||
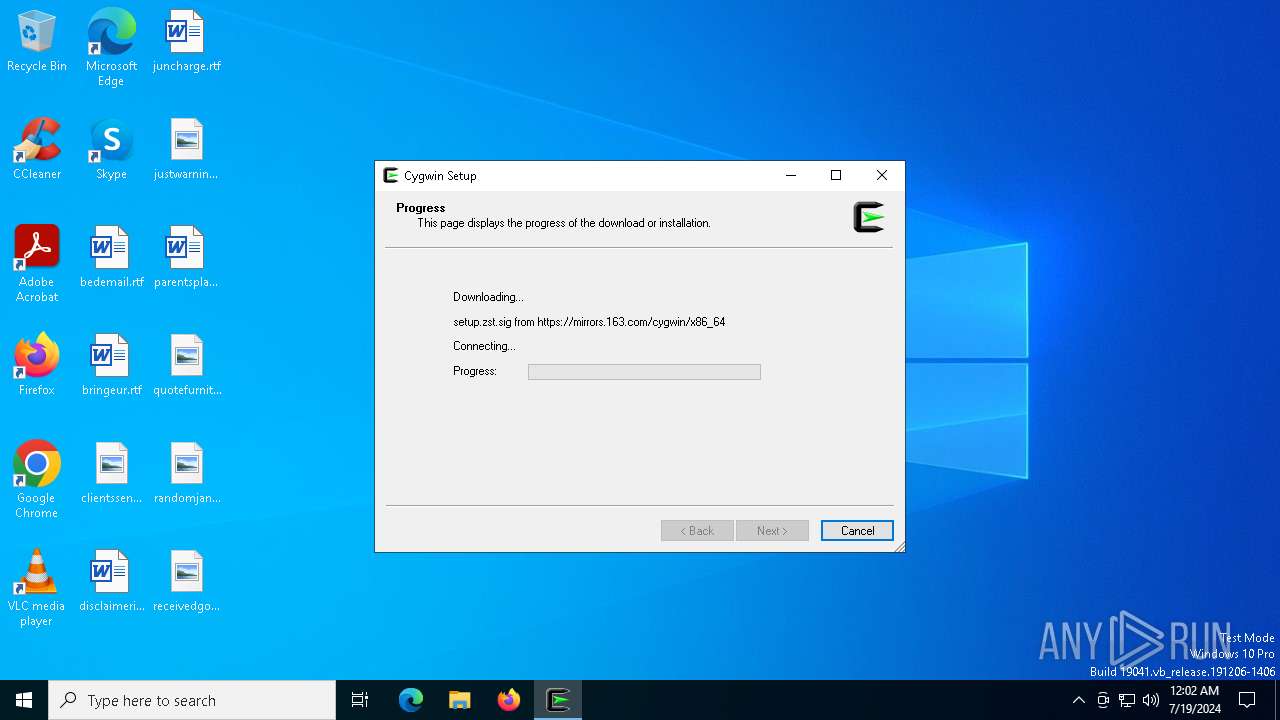
| 8160 | setup-x86_64.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\setup[1].zst | binary | |
MD5:9CB83870EB2EFC4B8BBC9B6F464BEB3D | SHA256:077ED4701798E760B76823EC2D3BD7DB9C2A3E047EF71E23480F55F3B96AF29F | |||
| 8160 | setup-x86_64.exe | C:\Users\admin\AppData\Local\Temp\https%3a%2f%2fmirrors.163.com%2fcygwin%2f\x86_64\release\ncurses\terminfo\terminfo-6.5+20240427-1.tar.xz.tmp | xz | |
MD5:4A552E4D08DE4A4AFFB51B9313C207B1 | SHA256:2F55B9233FD027B2A63A1731B90A10C304B9FB94E206DEDDEE90F2137D10F604 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
18
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8160 | setup-x86_64.exe | GET | 200 | 2.16.241.8:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgMDP7MDYI1oO212M2%2BtDDvI1g%3D%3D | unknown | — | — | whitelisted |
3032 | svchost.exe | GET | 304 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
8160 | setup-x86_64.exe | GET | 200 | 2.16.241.15:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgOuylx83sDPZOt%2Fy0ohZIAL2A%3D%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1796 | backgroundTaskHost.exe | 20.199.58.43:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
4716 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
7856 | svchost.exe | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1796 | backgroundTaskHost.exe | 20.223.35.26:443 | fd.api.iris.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2760 | svchost.exe | 40.115.3.253:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3384 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
8160 | setup-x86_64.exe | 8.43.85.97:443 | cygwin.com | REDHAT-HOSTED | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
arc.msn.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
cygwin.com |
| malicious |
r3.o.lencr.org |
| whitelisted |
www.bing.com |
| whitelisted |
mirrors.163.com |
| malicious |
r11.o.lencr.org |
| whitelisted |