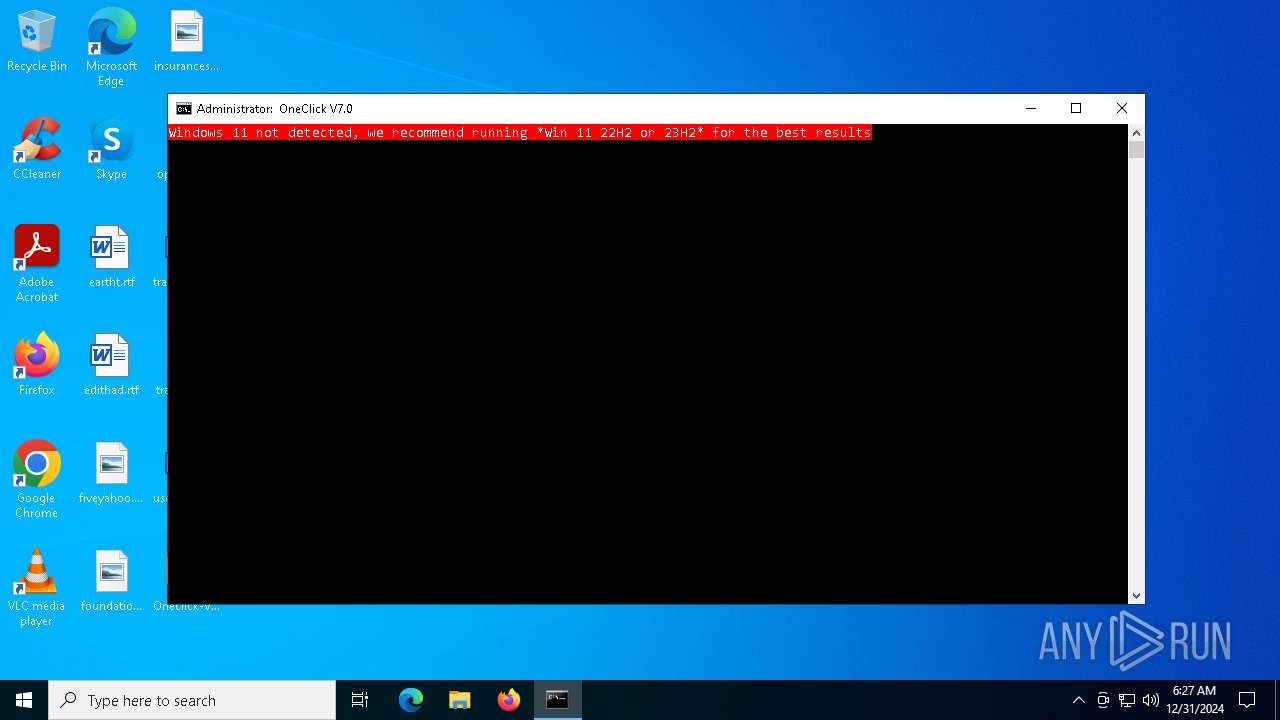
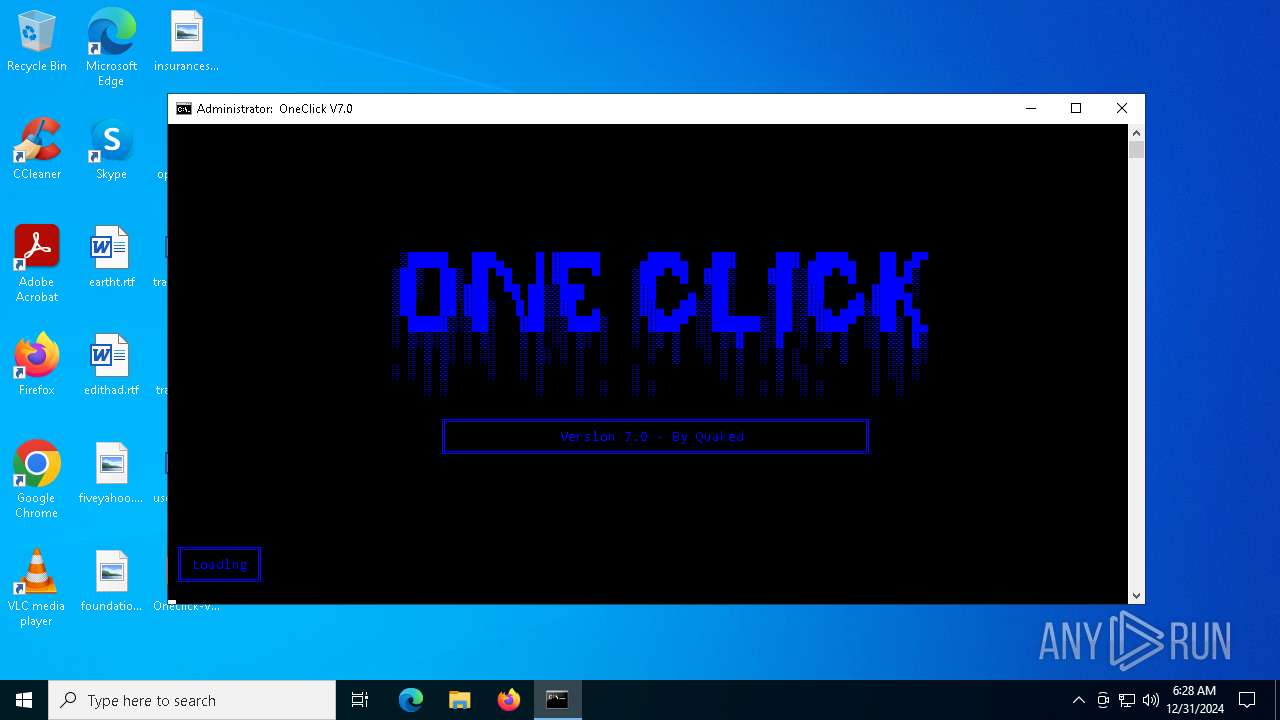
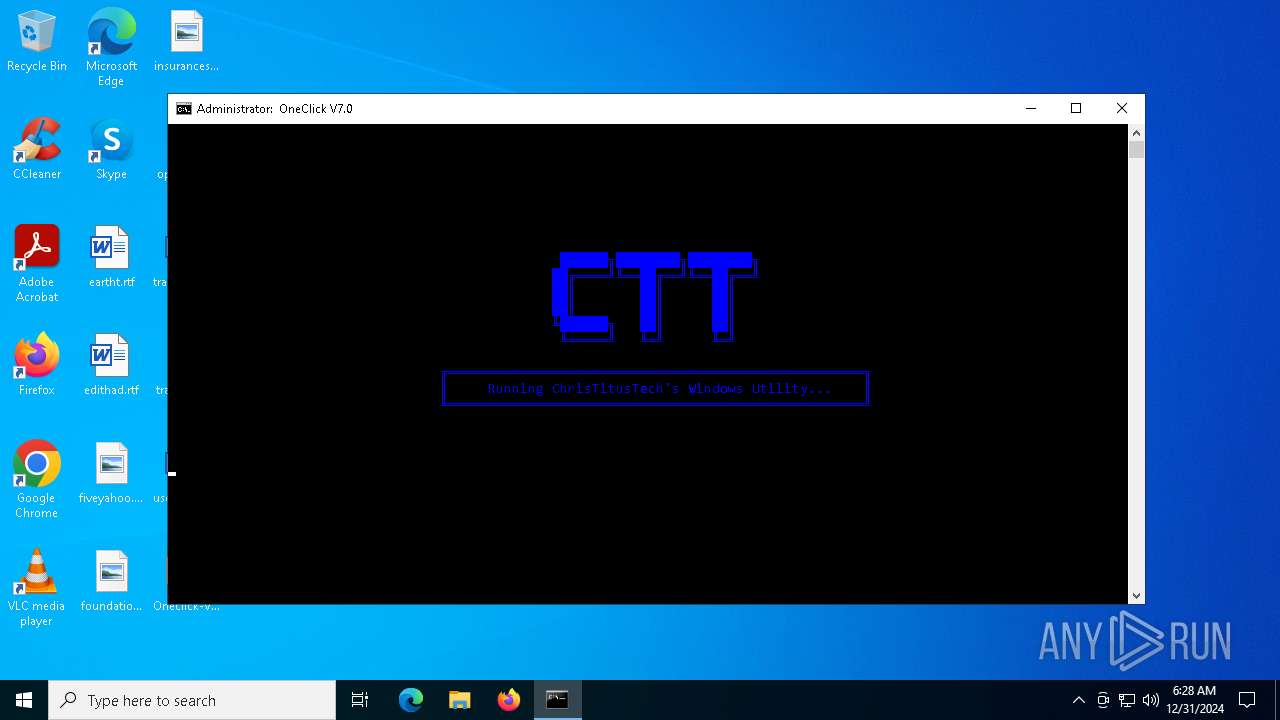
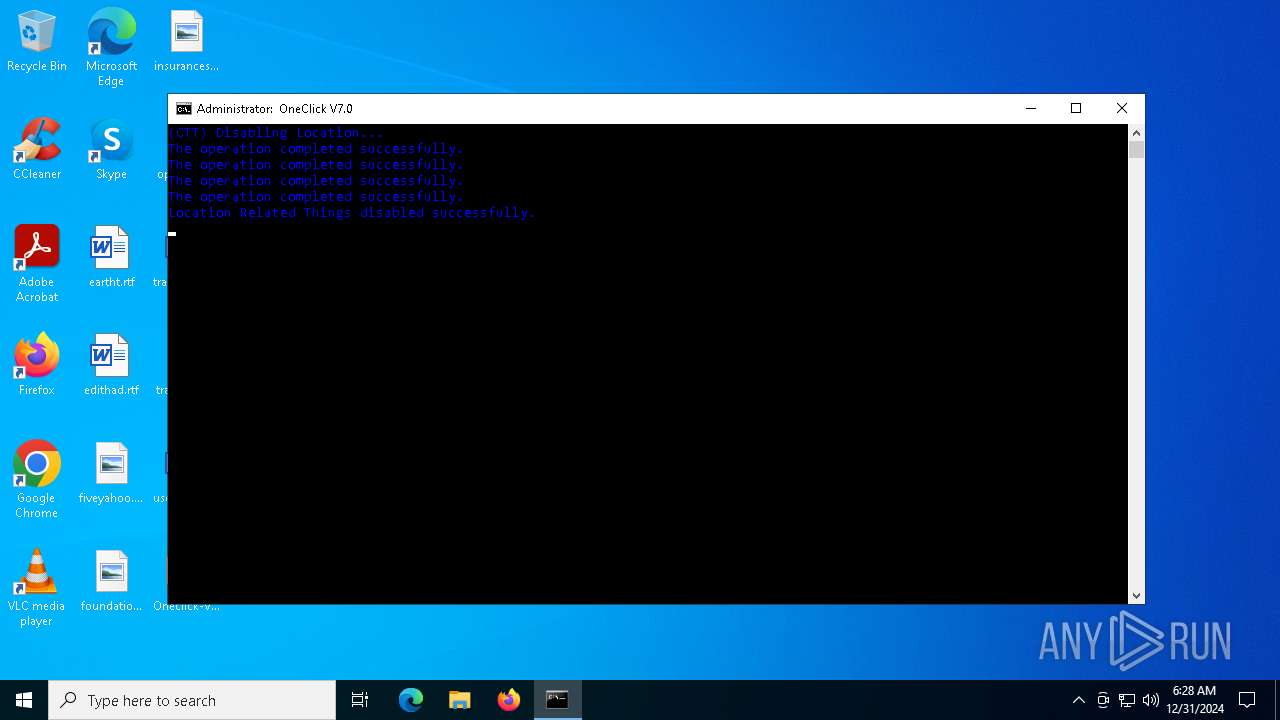
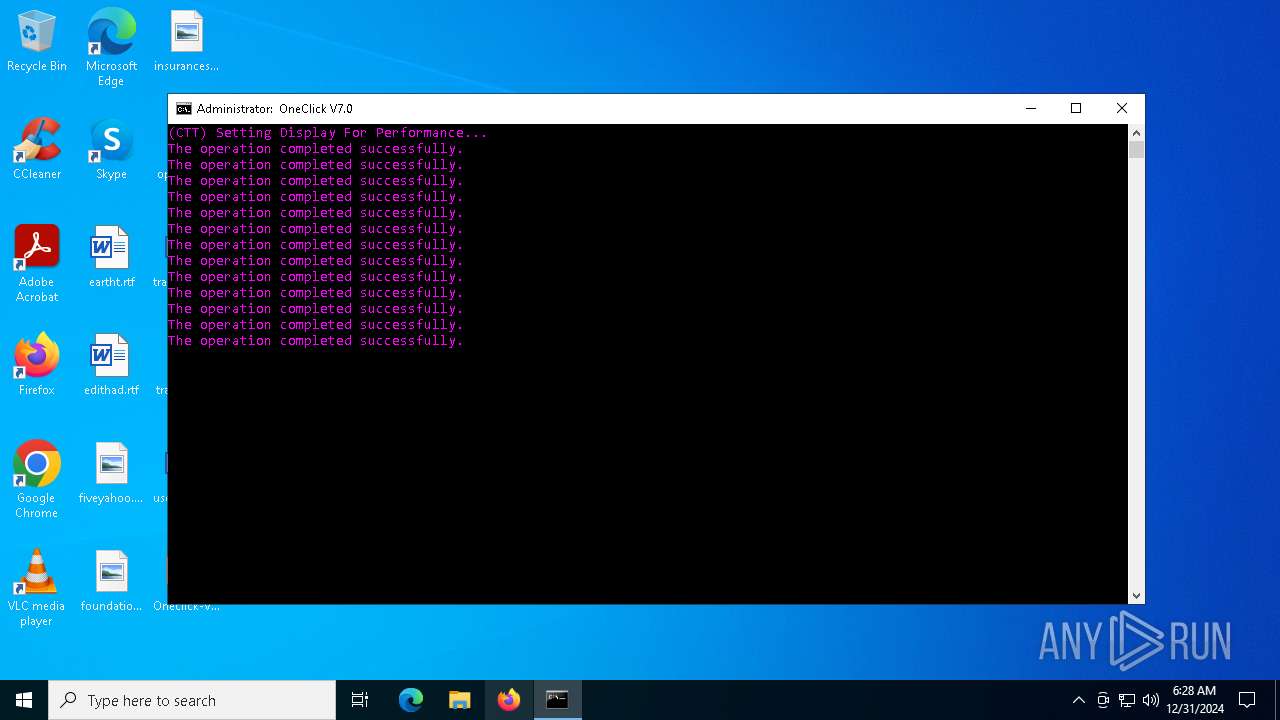
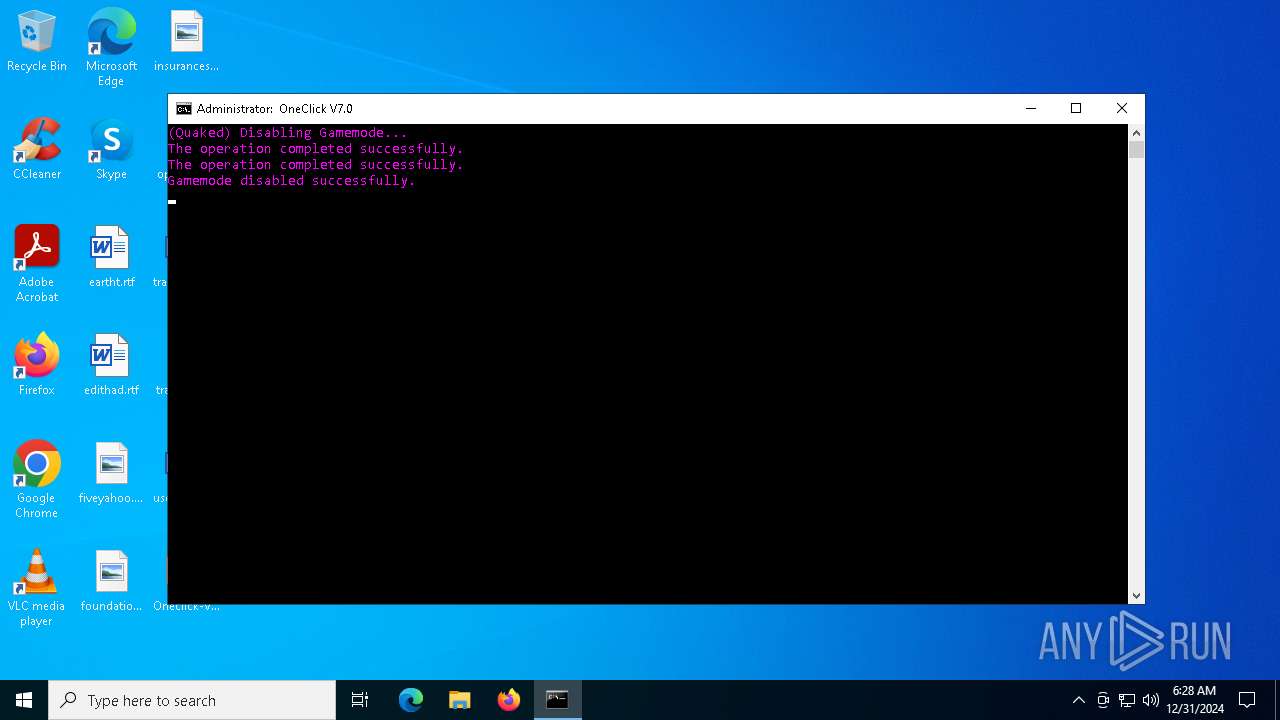
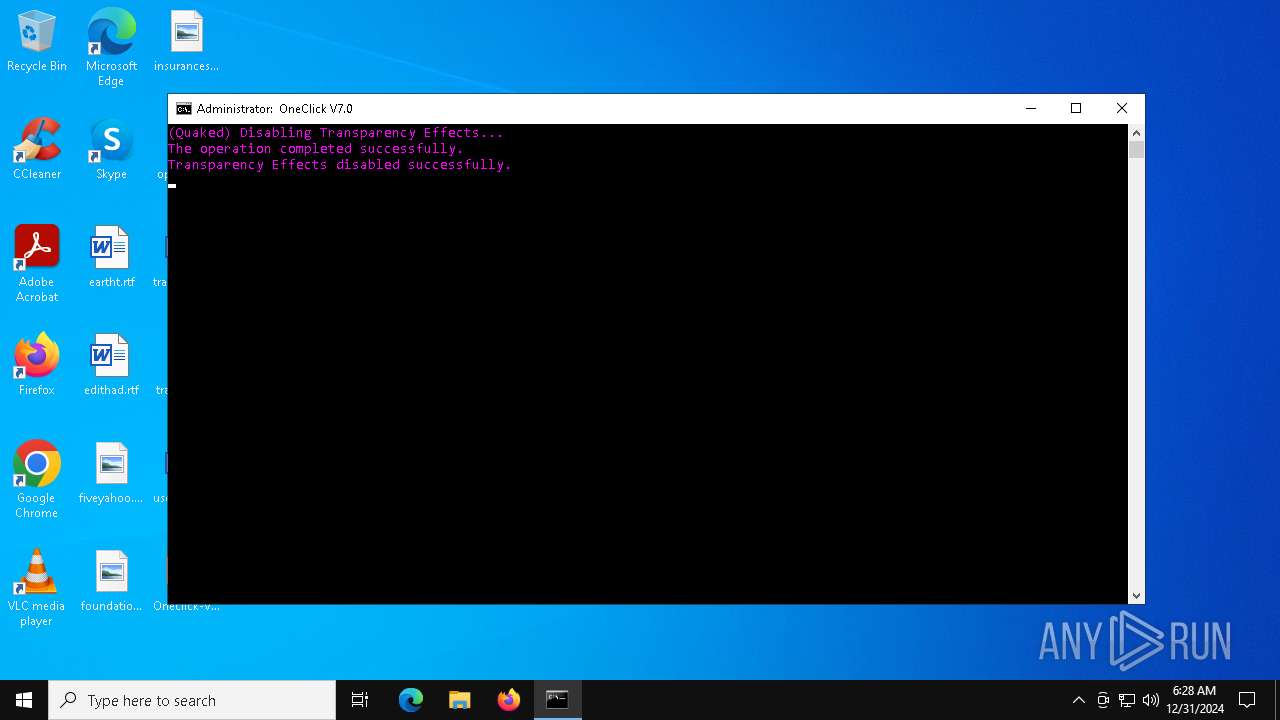
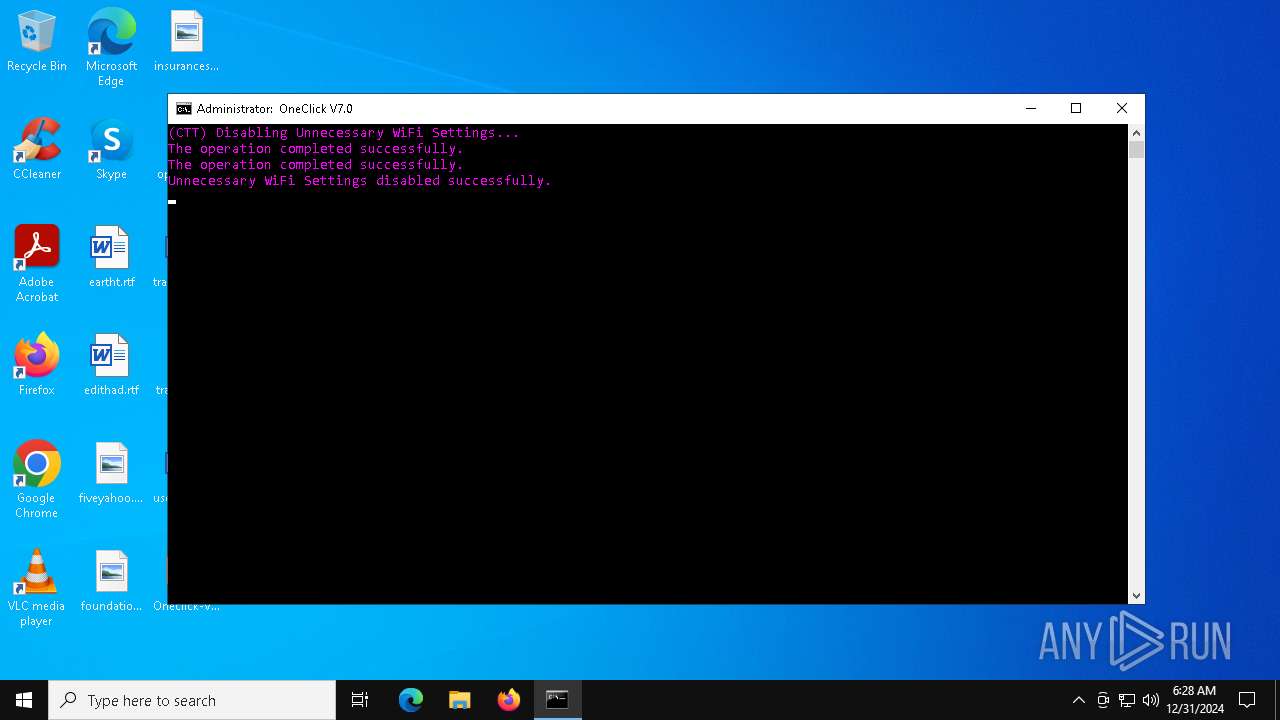
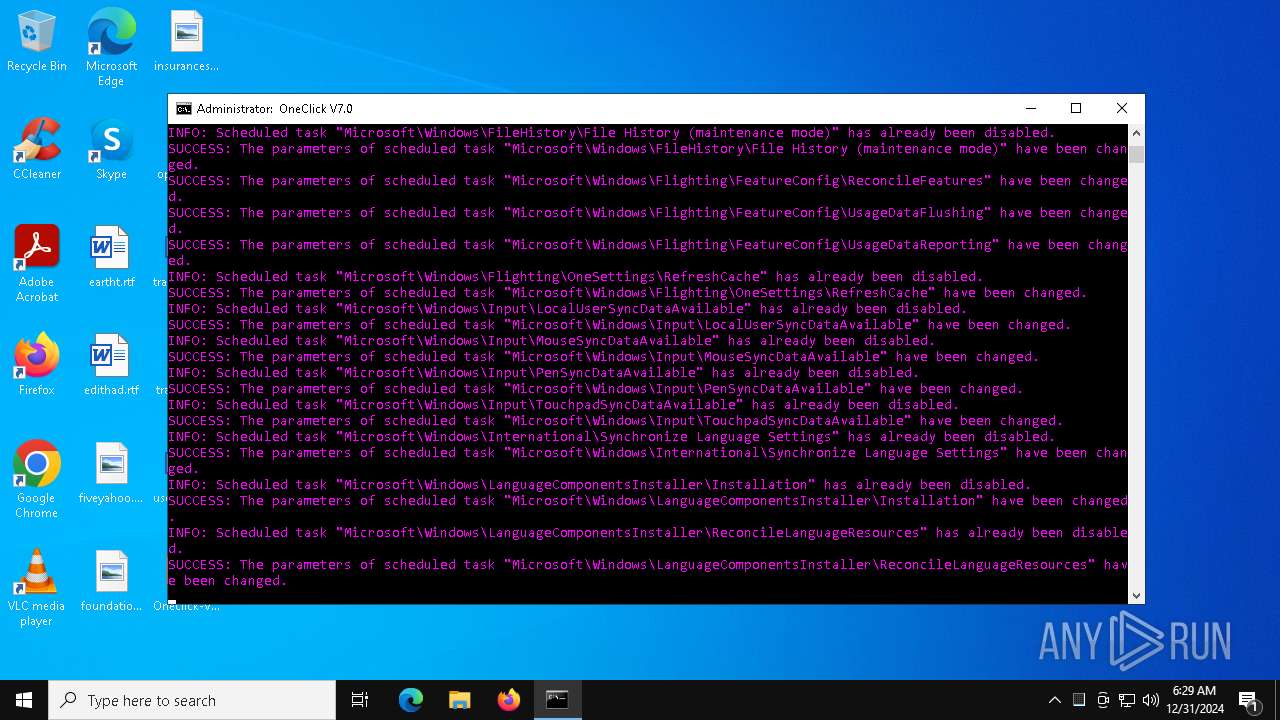
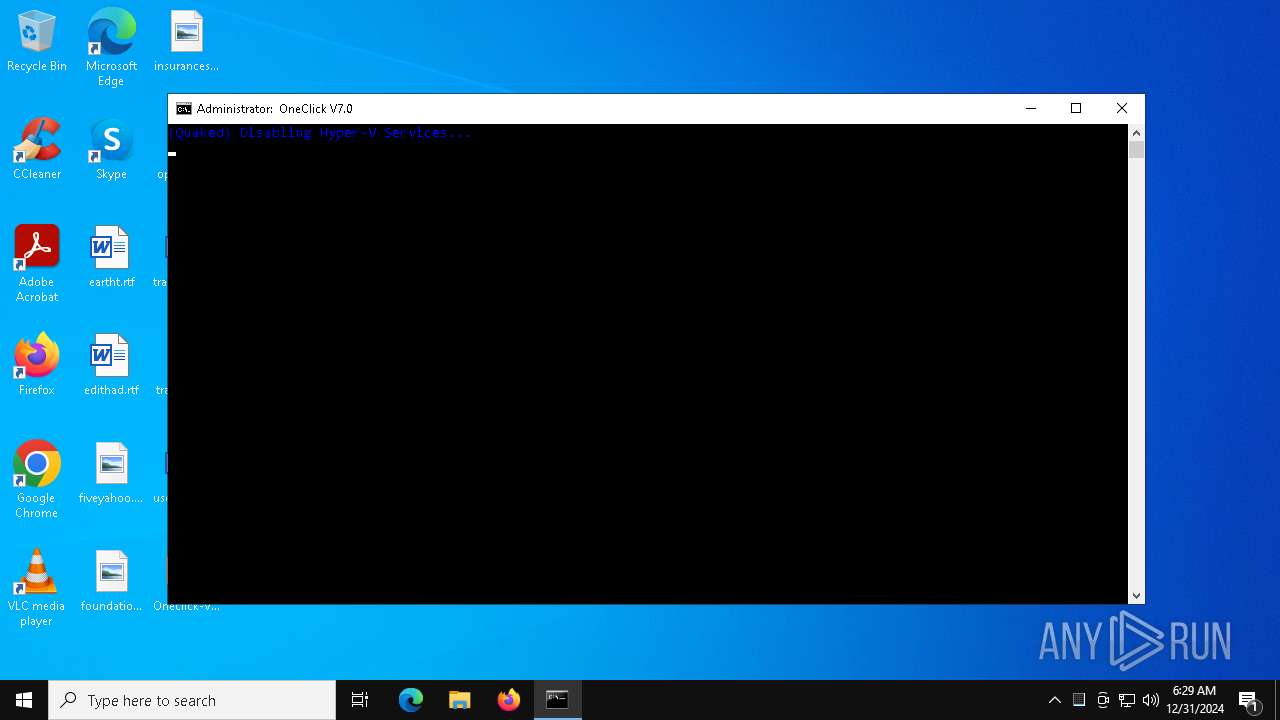
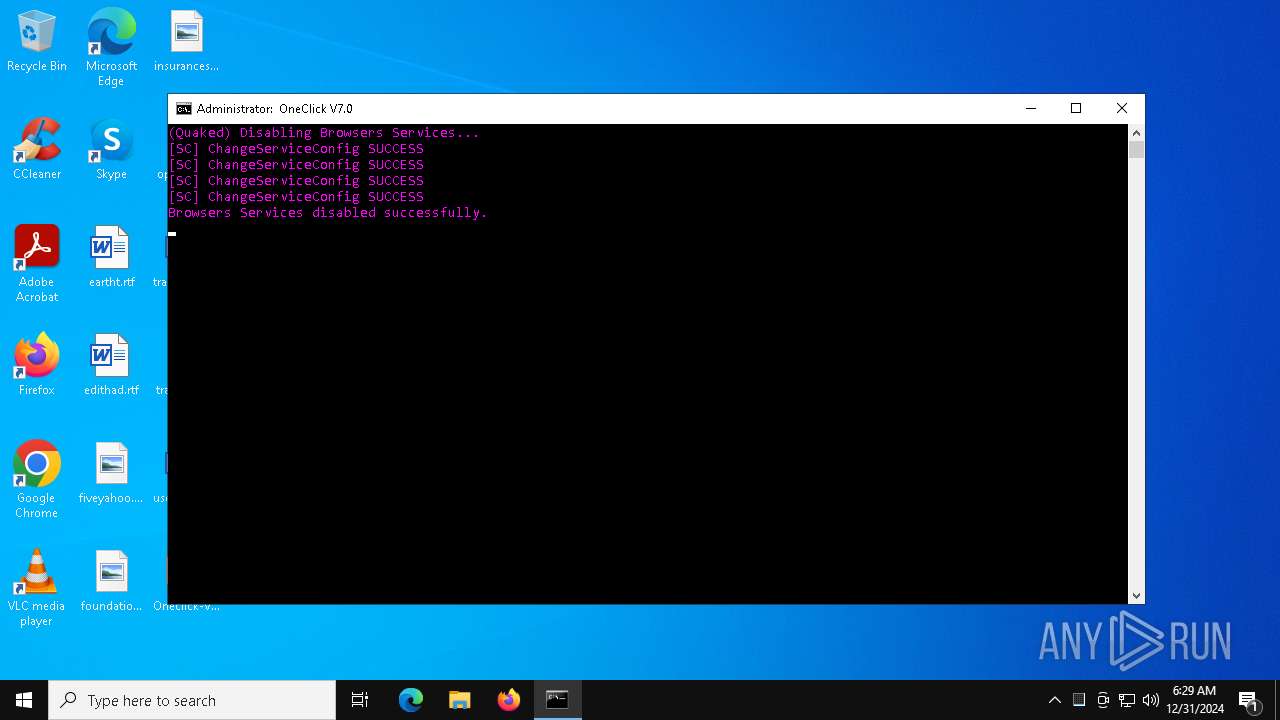
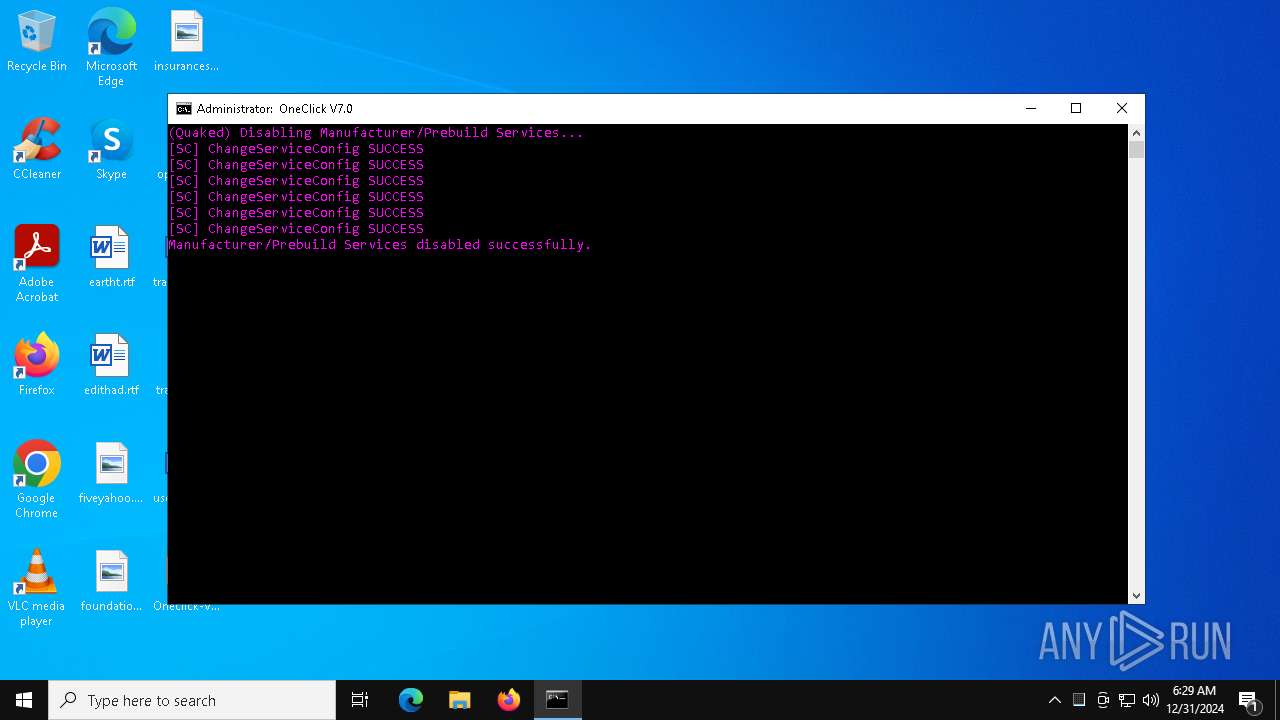
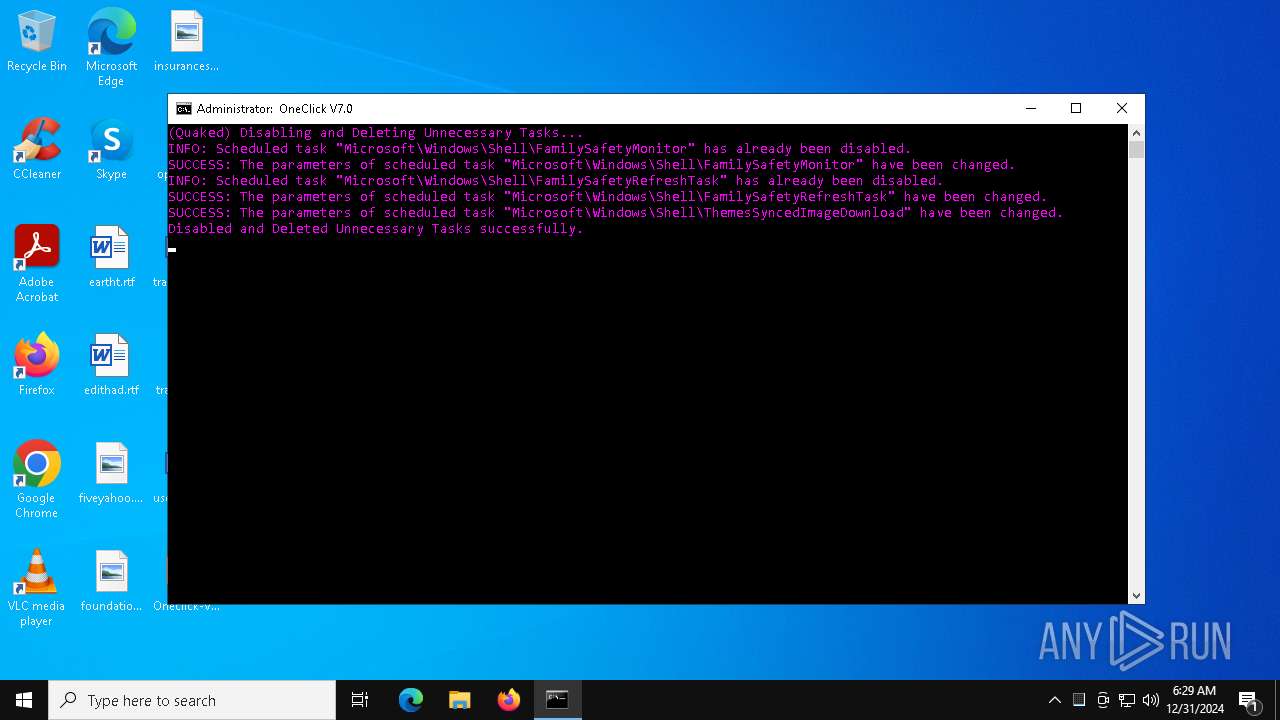
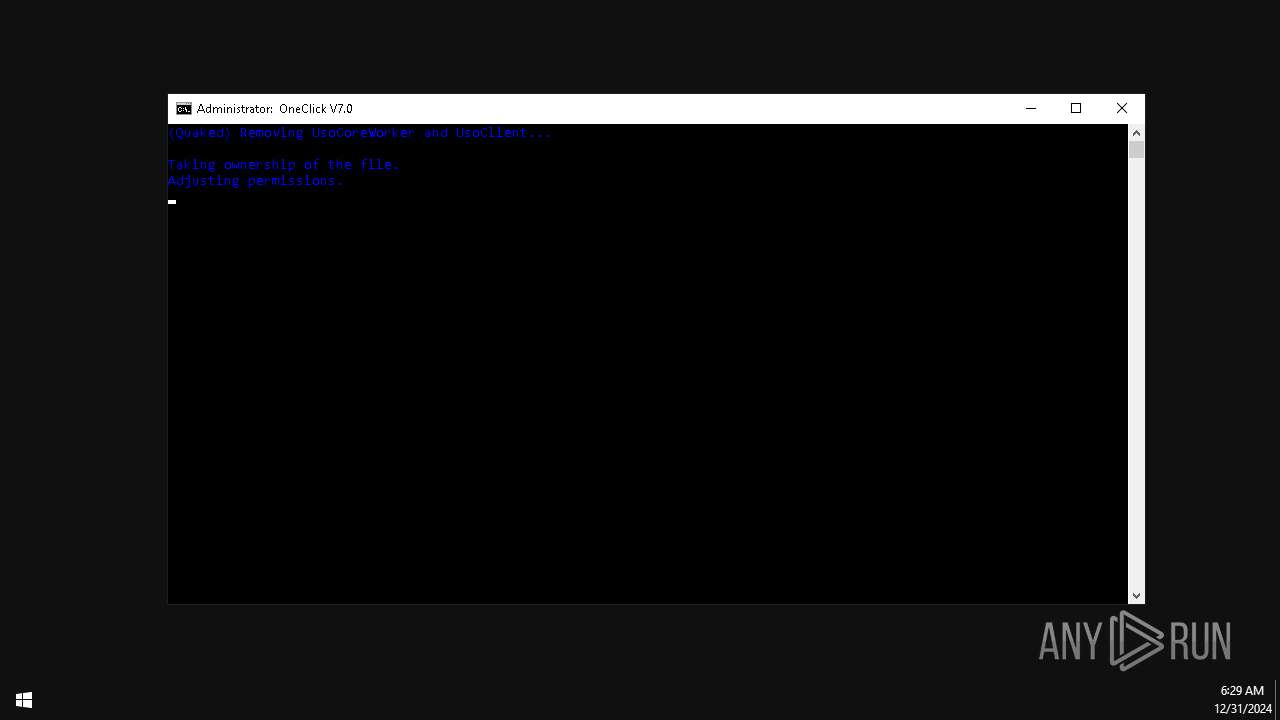
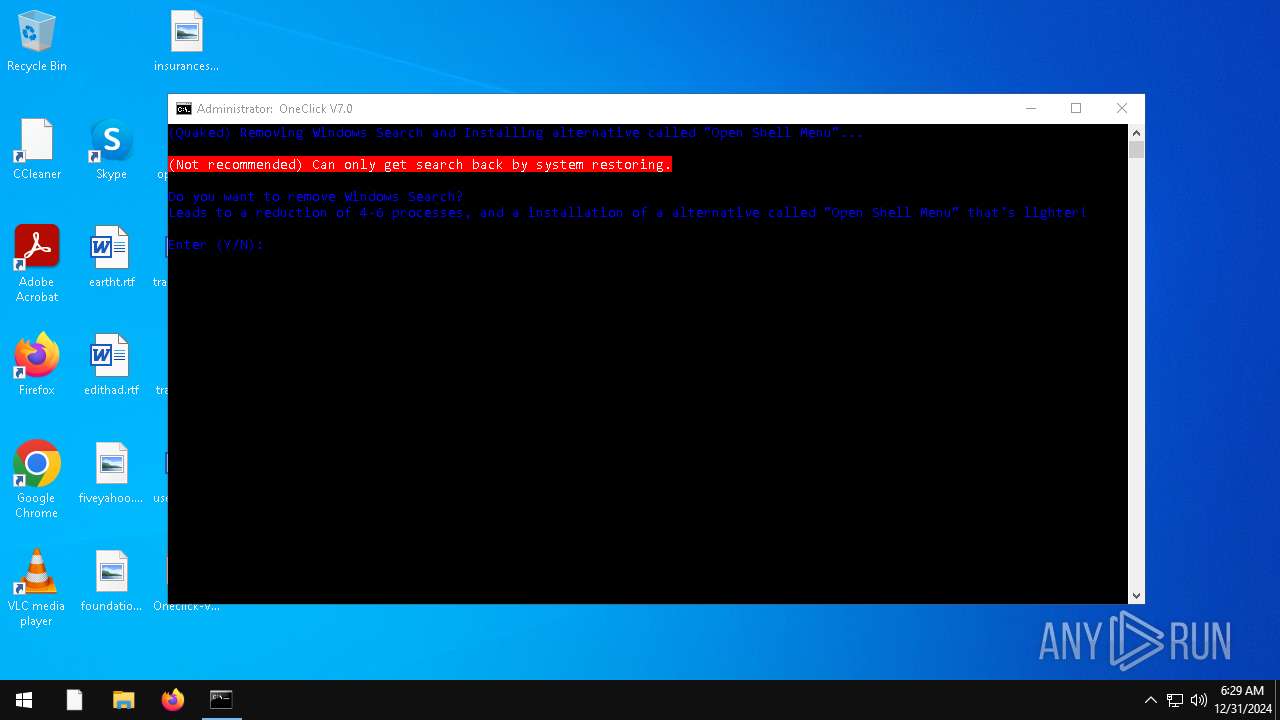
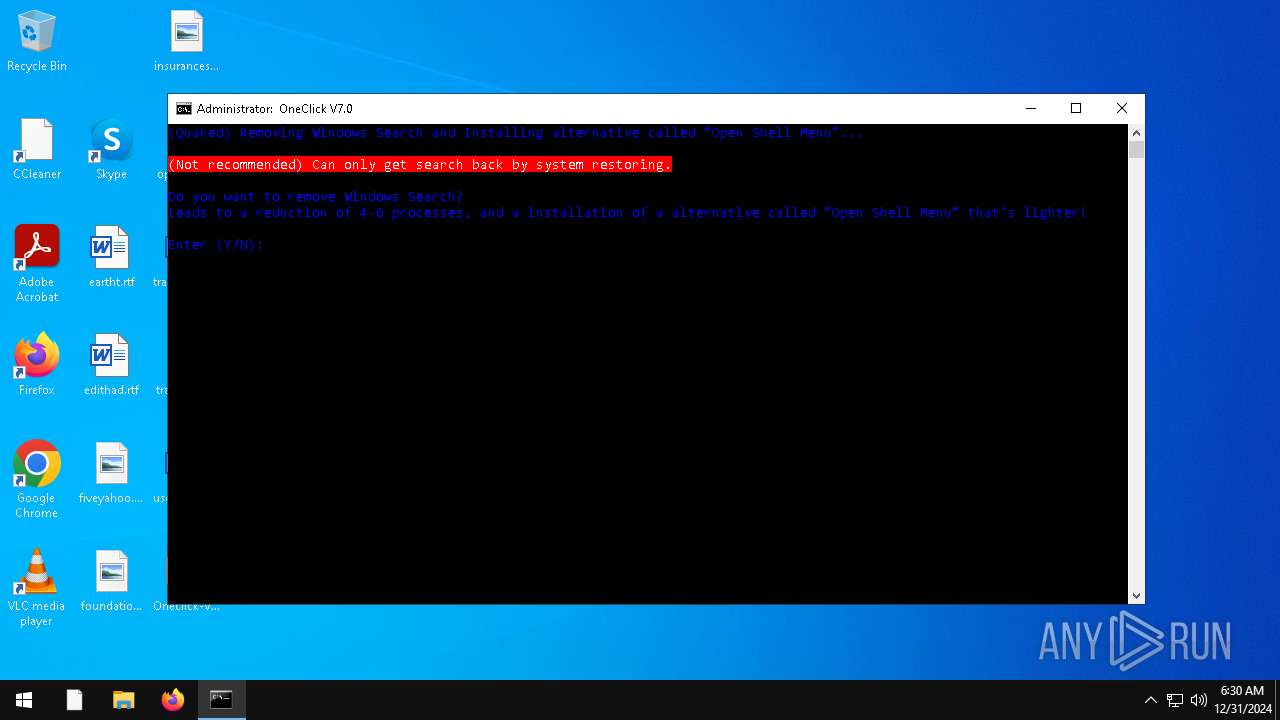
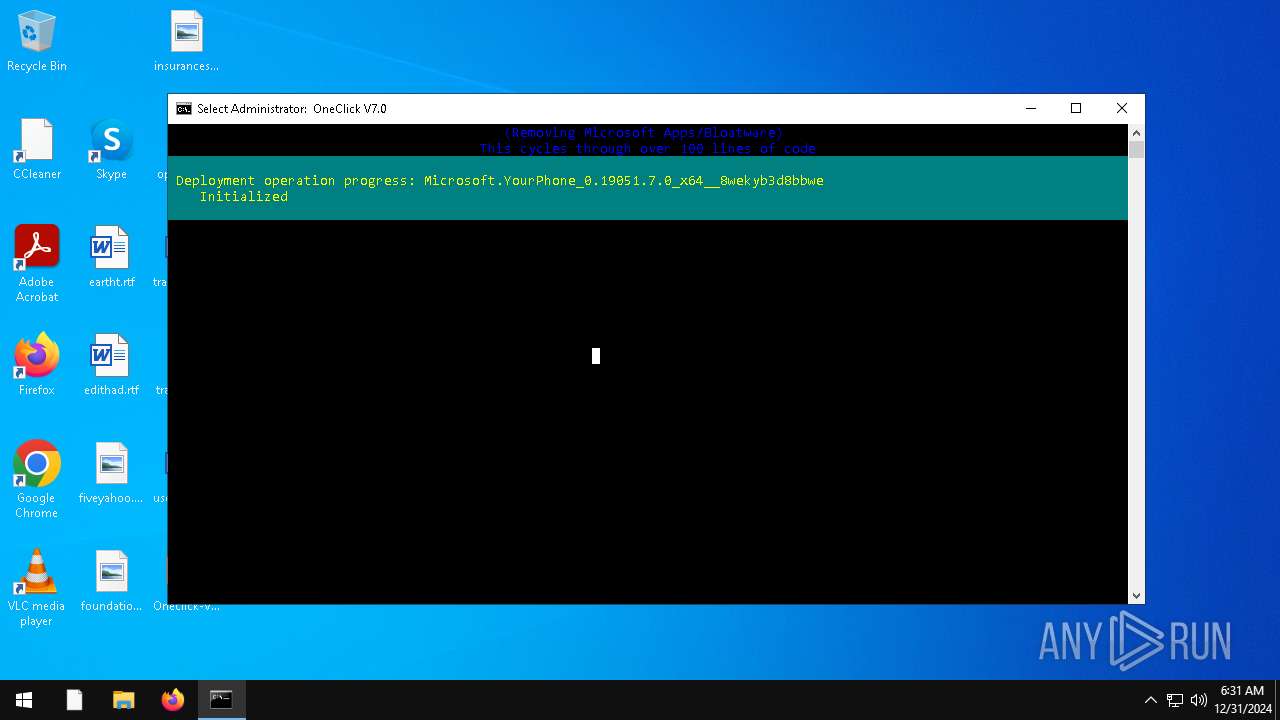
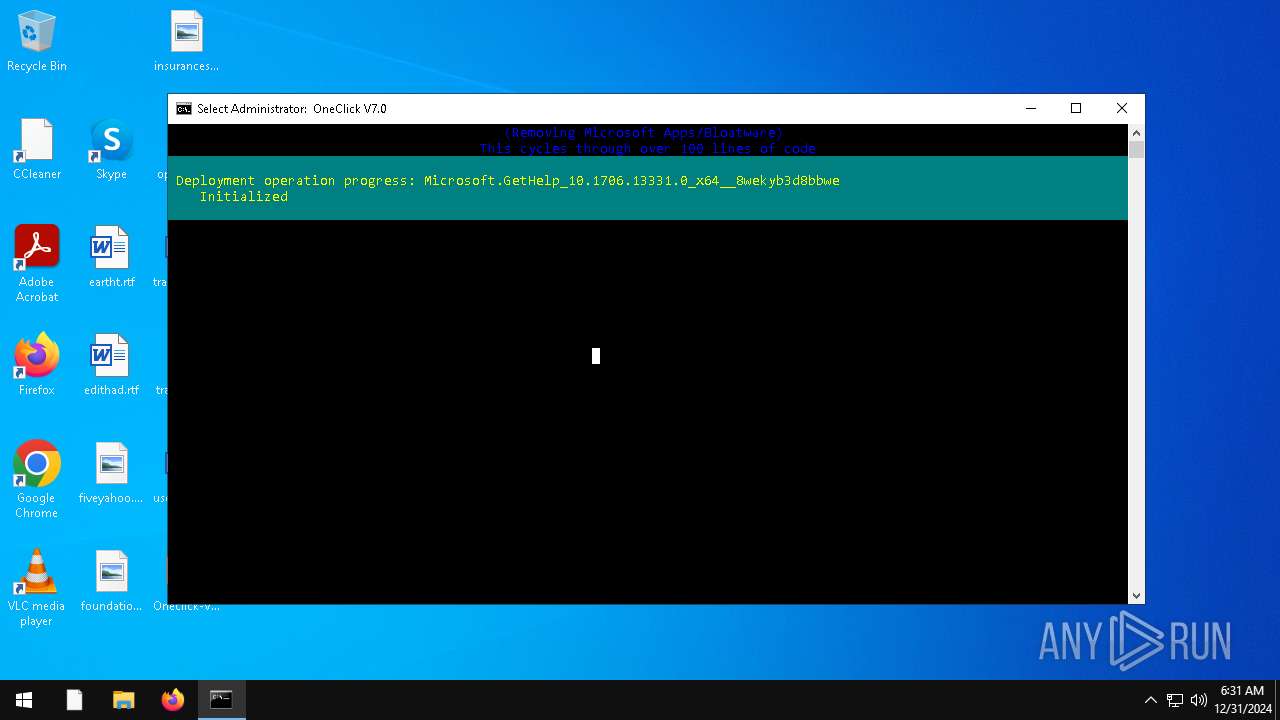
| File name: | Oneclick-V7.0.bat |
| Full analysis: | https://app.any.run/tasks/3c3e0d55-ef41-4548-b379-2a799e3f8196 |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | December 31, 2024, 06:27:30 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with CRLF line terminators |
| MD5: | 25AEF44C349C253B92678BECF5768DEC |
| SHA1: | 189AC793F5362B66963FDD06D08BC7977598BA57 |
| SHA256: | E7460CC36B59CCB756C8942C66552433903436A6F6BB11924D3AEC38B001F31D |
| SSDEEP: | 1536:8PSPKdigMQgPTjIV4QJ8STaggyjH/nvfHH4pXfCWOBEUCLii15TjSmcj/Dy:MfjvvfsT2mcTDy |
MALICIOUS
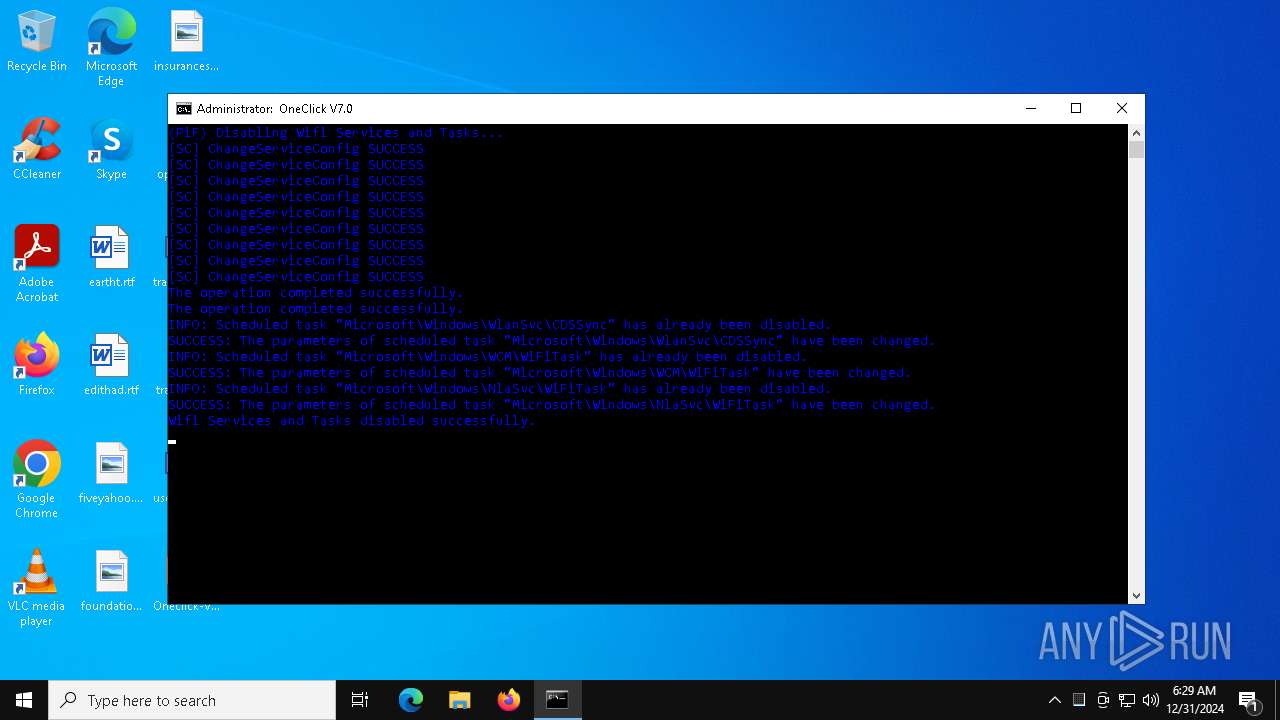
UAC/LUA settings modification
- reg.exe (PID: 5964)
Changes Windows Error Reporting flag
- reg.exe (PID: 2464)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 7028)
Run PowerShell with an invisible window
- powershell.exe (PID: 5964)
Bypass execution policy to execute commands
- powershell.exe (PID: 3144)
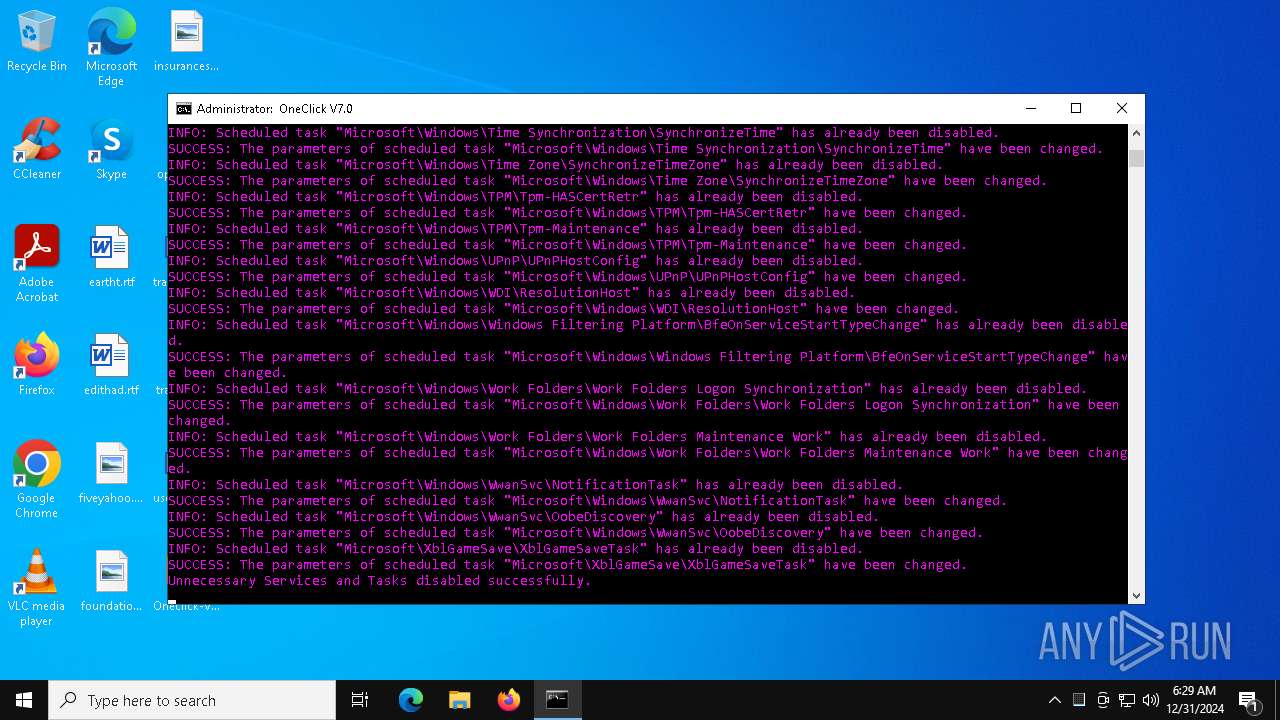
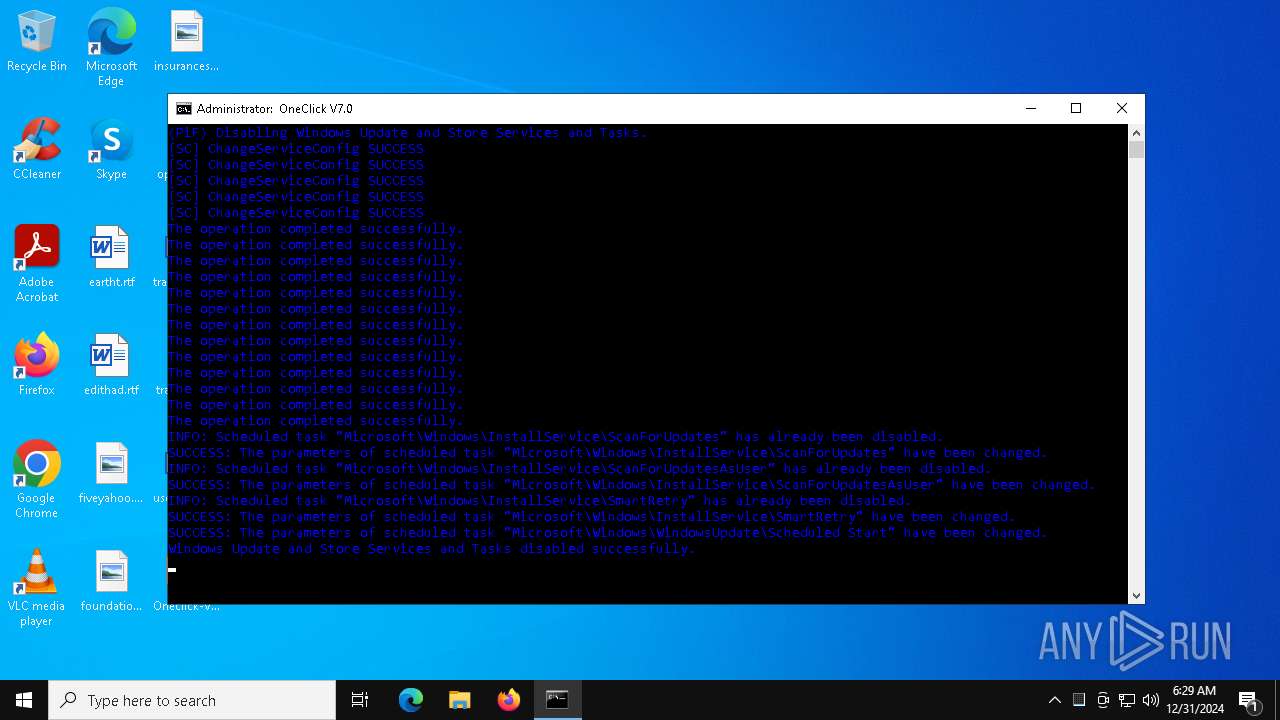
Changes the Windows auto-update feature
- OOSU10.exe (PID: 2904)
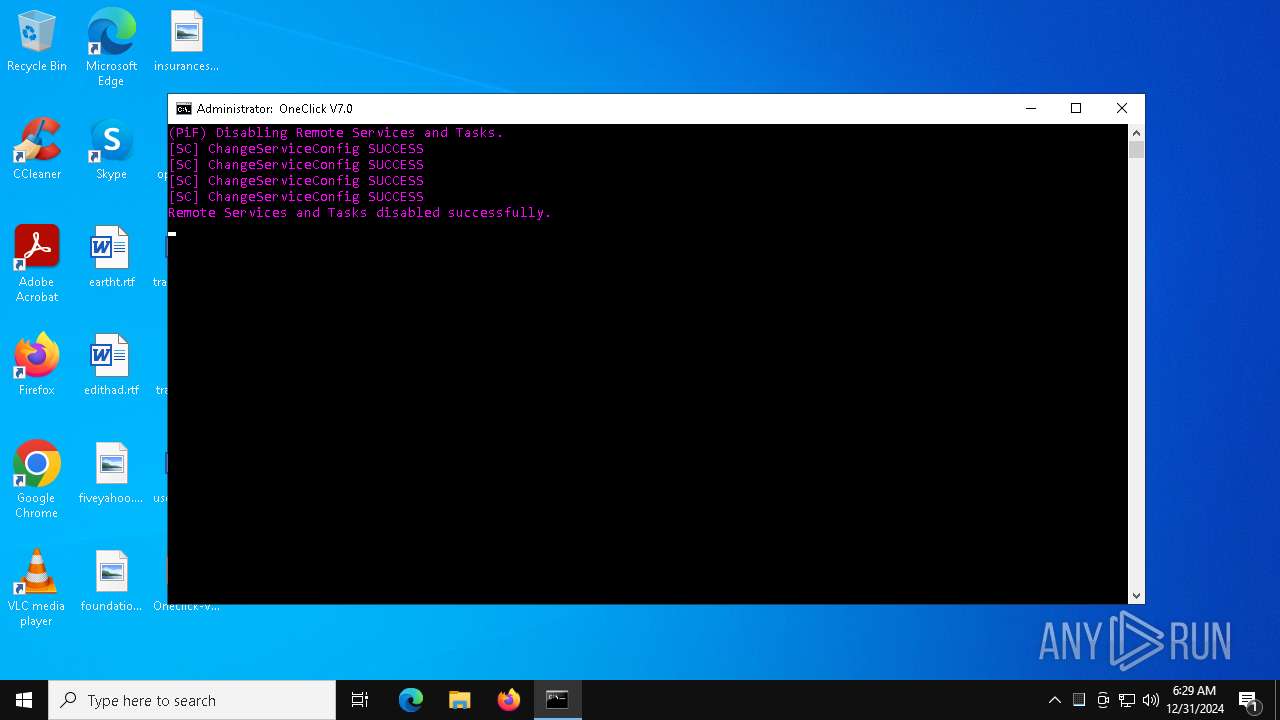
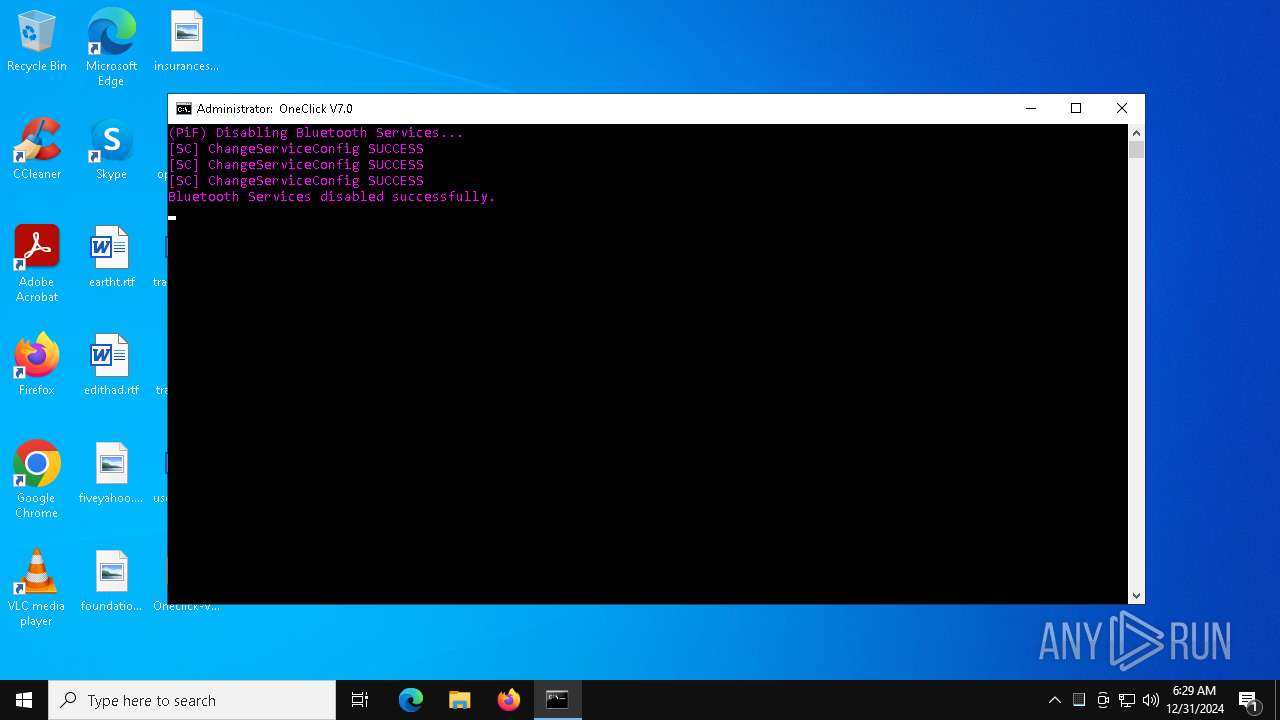
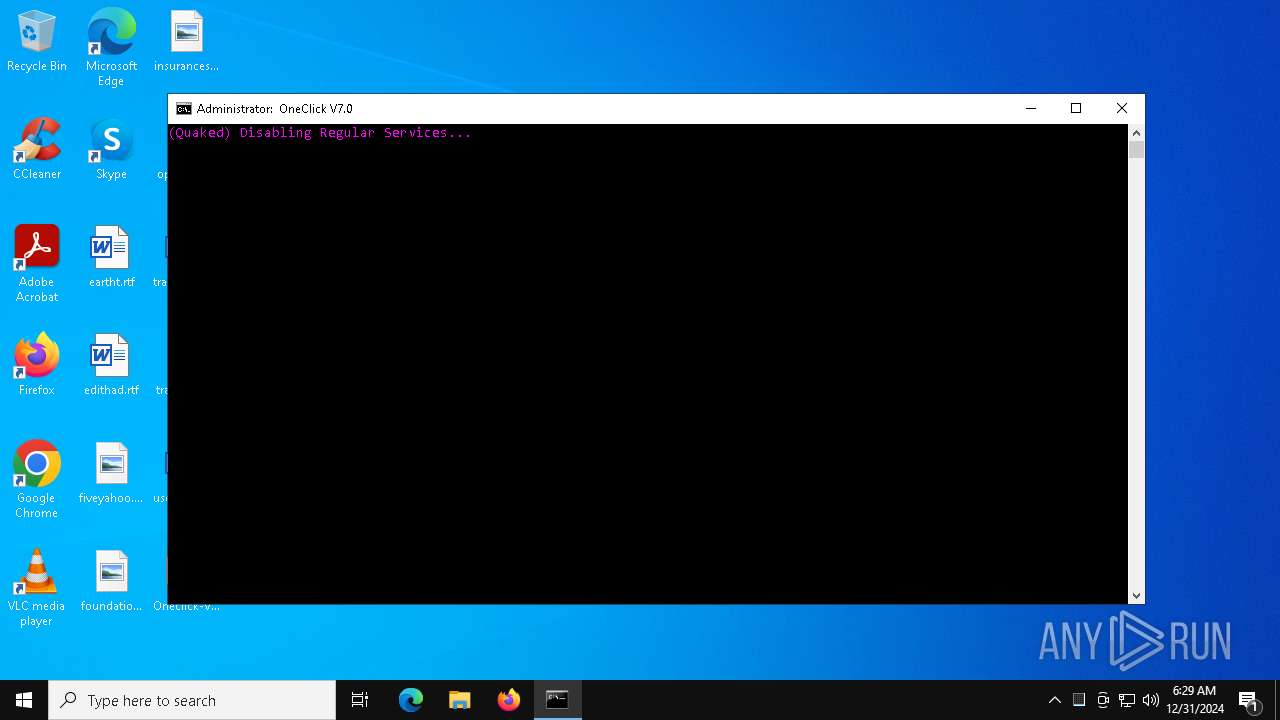
Creates or modifies Windows services
- OOSU10.exe (PID: 2904)
- reg.exe (PID: 1216)
Starts NET.EXE for service management
- cmd.exe (PID: 6960)
- net.exe (PID: 244)
- net.exe (PID: 4448)
- net.exe (PID: 5692)
- cmd.exe (PID: 7028)
- net.exe (PID: 5240)
- net.exe (PID: 3976)
- net.exe (PID: 3620)
- net.exe (PID: 5540)
- net.exe (PID: 5308)
Actions looks like stealing of personal data
- cmd.exe (PID: 7028)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4076)
- cmd.exe (PID: 7028)
- cmd.exe (PID: 936)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4076)
- cmd.exe (PID: 7028)
Executing commands from a ".bat" file
- powershell.exe (PID: 6864)
- NSudoLG.exe (PID: 1616)
- NSudoLG.exe (PID: 4504)
- NSudoLG.exe (PID: 6776)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 6864)
- cmd.exe (PID: 7028)
- NSudoLG.exe (PID: 4504)
- NSudoLG.exe (PID: 1616)
- NSudoLG.exe (PID: 6776)
Hides command output
- cmd.exe (PID: 7116)
- cmd.exe (PID: 5488)
- cmd.exe (PID: 6844)
- cmd.exe (PID: 5296)
Windows service management via SC.EXE
- sc.exe (PID: 6476)
- sc.exe (PID: 6832)
- sc.exe (PID: 6268)
- sc.exe (PID: 4740)
- sc.exe (PID: 3532)
- sc.exe (PID: 6928)
- sc.exe (PID: 3812)
- sc.exe (PID: 7132)
- sc.exe (PID: 7164)
- sc.exe (PID: 7136)
- sc.exe (PID: 3988)
- sc.exe (PID: 7156)
- sc.exe (PID: 3040)
- sc.exe (PID: 4976)
- sc.exe (PID: 1876)
- sc.exe (PID: 1544)
- sc.exe (PID: 5472)
- sc.exe (PID: 5536)
- sc.exe (PID: 3296)
- sc.exe (PID: 732)
- sc.exe (PID: 3060)
- sc.exe (PID: 3912)
- sc.exe (PID: 3536)
- sc.exe (PID: 4640)
- sc.exe (PID: 3140)
- sc.exe (PID: 3920)
- sc.exe (PID: 6316)
- sc.exe (PID: 244)
- sc.exe (PID: 1400)
- sc.exe (PID: 3984)
- sc.exe (PID: 5920)
- sc.exe (PID: 1356)
- sc.exe (PID: 6500)
- sc.exe (PID: 396)
- sc.exe (PID: 6584)
- sc.exe (PID: 5236)
- sc.exe (PID: 5972)
- sc.exe (PID: 3928)
- sc.exe (PID: 1080)
- sc.exe (PID: 5496)
- sc.exe (PID: 1140)
- sc.exe (PID: 5964)
- sc.exe (PID: 6844)
- sc.exe (PID: 6904)
- sc.exe (PID: 3700)
- sc.exe (PID: 5988)
- sc.exe (PID: 7144)
- sc.exe (PID: 7124)
- sc.exe (PID: 1760)
- sc.exe (PID: 6032)
- sc.exe (PID: 5340)
- sc.exe (PID: 5640)
- sc.exe (PID: 1488)
- sc.exe (PID: 3032)
- sc.exe (PID: 4648)
- sc.exe (PID: 2548)
- sc.exe (PID: 1540)
- sc.exe (PID: 3280)
- sc.exe (PID: 936)
- sc.exe (PID: 4136)
- sc.exe (PID: 3840)
- sc.exe (PID: 2200)
- sc.exe (PID: 968)
- sc.exe (PID: 4392)
- sc.exe (PID: 6312)
- sc.exe (PID: 3656)
- sc.exe (PID: 5404)
- sc.exe (PID: 6424)
- sc.exe (PID: 6728)
- sc.exe (PID: 3724)
- sc.exe (PID: 1852)
- sc.exe (PID: 3952)
- sc.exe (PID: 6772)
- sc.exe (PID: 6504)
- sc.exe (PID: 5628)
- sc.exe (PID: 2728)
- sc.exe (PID: 4388)
- sc.exe (PID: 6380)
- sc.exe (PID: 3808)
- sc.exe (PID: 5540)
- sc.exe (PID: 7076)
- sc.exe (PID: 6552)
- sc.exe (PID: 2680)
- sc.exe (PID: 6512)
- sc.exe (PID: 2008)
- sc.exe (PID: 6516)
- sc.exe (PID: 1216)
- sc.exe (PID: 6524)
- sc.exe (PID: 2996)
- sc.exe (PID: 6776)
- sc.exe (PID: 6932)
- sc.exe (PID: 6924)
- sc.exe (PID: 5464)
- sc.exe (PID: 2148)
- sc.exe (PID: 5300)
- sc.exe (PID: 4504)
- sc.exe (PID: 6392)
- sc.exe (PID: 6252)
- sc.exe (PID: 5740)
- sc.exe (PID: 6304)
- sc.exe (PID: 628)
- sc.exe (PID: 6296)
- sc.exe (PID: 6032)
- sc.exe (PID: 5536)
- sc.exe (PID: 3140)
- sc.exe (PID: 2972)
- sc.exe (PID: 4944)
- sc.exe (PID: 1876)
- sc.exe (PID: 7088)
- sc.exe (PID: 640)
- sc.exe (PID: 3584)
- sc.exe (PID: 4704)
- sc.exe (PID: 440)
- sc.exe (PID: 6096)
- sc.exe (PID: 3820)
- sc.exe (PID: 3536)
- sc.exe (PID: 5752)
- sc.exe (PID: 6272)
- sc.exe (PID: 3172)
- sc.exe (PID: 1400)
- sc.exe (PID: 3732)
- sc.exe (PID: 6468)
- sc.exe (PID: 308)
- sc.exe (PID: 5212)
- sc.exe (PID: 6316)
- sc.exe (PID: 6460)
- sc.exe (PID: 6824)
- sc.exe (PID: 2844)
- sc.exe (PID: 5308)
- sc.exe (PID: 1140)
- sc.exe (PID: 5496)
- sc.exe (PID: 3992)
- sc.exe (PID: 488)
- sc.exe (PID: 6868)
- sc.exe (PID: 3436)
- sc.exe (PID: 6900)
- sc.exe (PID: 7148)
- sc.exe (PID: 6500)
- sc.exe (PID: 6684)
- sc.exe (PID: 5236)
- sc.exe (PID: 5652)
- sc.exe (PID: 6284)
- sc.exe (PID: 2548)
- sc.exe (PID: 6204)
- sc.exe (PID: 3144)
- sc.exe (PID: 6164)
- sc.exe (PID: 5432)
- sc.exe (PID: 5780)
- sc.exe (PID: 4704)
- sc.exe (PID: 5916)
- sc.exe (PID: 3564)
- sc.exe (PID: 5112)
- sc.exe (PID: 6576)
- sc.exe (PID: 1544)
- sc.exe (PID: 5472)
- sc.exe (PID: 7136)
- sc.exe (PID: 1616)
- sc.exe (PID: 1536)
- sc.exe (PID: 440)
- sc.exe (PID: 4648)
- sc.exe (PID: 4816)
- sc.exe (PID: 6004)
- sc.exe (PID: 6236)
- sc.exe (PID: 6256)
- sc.exe (PID: 3172)
- sc.exe (PID: 2512)
- sc.exe (PID: 2496)
- sc.exe (PID: 4020)
- sc.exe (PID: 6468)
- sc.exe (PID: 5212)
- sc.exe (PID: 5892)
- sc.exe (PID: 3984)
- sc.exe (PID: 5752)
- sc.exe (PID: 6316)
- sc.exe (PID: 1732)
- sc.exe (PID: 6392)
- sc.exe (PID: 5628)
- sc.exe (PID: 6280)
- sc.exe (PID: 5236)
- sc.exe (PID: 6824)
- sc.exe (PID: 6512)
- sc.exe (PID: 6736)
- sc.exe (PID: 6460)
- sc.exe (PID: 6804)
- sc.exe (PID: 1140)
- sc.exe (PID: 2008)
- sc.exe (PID: 6868)
- sc.exe (PID: 3532)
- sc.exe (PID: 6900)
- sc.exe (PID: 6476)
- sc.exe (PID: 1080)
- sc.exe (PID: 4468)
- sc.exe (PID: 5300)
- sc.exe (PID: 6076)
- sc.exe (PID: 3144)
- sc.exe (PID: 5740)
- sc.exe (PID: 6300)
- sc.exe (PID: 6204)
- sc.exe (PID: 5432)
- sc.exe (PID: 5780)
- sc.exe (PID: 4704)
- sc.exe (PID: 4516)
- sc.exe (PID: 3280)
- sc.exe (PID: 4944)
- sc.exe (PID: 5112)
- sc.exe (PID: 7124)
- sc.exe (PID: 5472)
- sc.exe (PID: 732)
- sc.exe (PID: 4816)
- sc.exe (PID: 5320)
- sc.exe (PID: 2216)
- sc.exe (PID: 5588)
- sc.exe (PID: 2940)
- sc.exe (PID: 6256)
- sc.exe (PID: 5728)
- sc.exe (PID: 5752)
- sc.exe (PID: 3928)
- sc.exe (PID: 3172)
- sc.exe (PID: 6360)
- sc.exe (PID: 5872)
- sc.exe (PID: 1544)
- sc.exe (PID: 5388)
- sc.exe (PID: 440)
- sc.exe (PID: 6652)
- sc.exe (PID: 5212)
- sc.exe (PID: 5892)
- sc.exe (PID: 2928)
- sc.exe (PID: 6476)
- sc.exe (PID: 2496)
- sc.exe (PID: 4020)
- sc.exe (PID: 6456)
- sc.exe (PID: 1732)
- sc.exe (PID: 1140)
- sc.exe (PID: 7140)
- sc.exe (PID: 4932)
- sc.exe (PID: 4360)
- sc.exe (PID: 3888)
- sc.exe (PID: 5740)
- sc.exe (PID: 7104)
- sc.exe (PID: 5464)
- sc.exe (PID: 5988)
- sc.exe (PID: 7116)
- sc.exe (PID: 7144)
- sc.exe (PID: 3508)
- sc.exe (PID: 4984)
- sc.exe (PID: 6332)
- sc.exe (PID: 6868)
- sc.exe (PID: 5912)
- sc.exe (PID: 3288)
- sc.exe (PID: 7160)
- sc.exe (PID: 628)
- sc.exe (PID: 3144)
- sc.exe (PID: 6952)
- sc.exe (PID: 4996)
- sc.exe (PID: 3988)
- sc.exe (PID: 5112)
- sc.exe (PID: 4136)
- sc.exe (PID: 5640)
- sc.exe (PID: 936)
- sc.exe (PID: 6016)
- sc.exe (PID: 3420)
- sc.exe (PID: 4596)
- sc.exe (PID: 2260)
- sc.exe (PID: 6032)
- sc.exe (PID: 1616)
- sc.exe (PID: 5936)
- sc.exe (PID: 3060)
- sc.exe (PID: 2796)
- sc.exe (PID: 4740)
- sc.exe (PID: 2512)
- sc.exe (PID: 3952)
- sc.exe (PID: 2904)
- sc.exe (PID: 6188)
- sc.exe (PID: 6676)
- sc.exe (PID: 6796)
- sc.exe (PID: 6148)
- sc.exe (PID: 6360)
- sc.exe (PID: 6728)
- sc.exe (PID: 6236)
- sc.exe (PID: 5548)
- sc.exe (PID: 1488)
- sc.exe (PID: 2216)
- sc.exe (PID: 3296)
- sc.exe (PID: 3536)
- sc.exe (PID: 6268)
- sc.exe (PID: 5728)
- sc.exe (PID: 1400)
- sc.exe (PID: 6420)
- sc.exe (PID: 6500)
- sc.exe (PID: 6504)
- sc.exe (PID: 6280)
- sc.exe (PID: 6392)
- sc.exe (PID: 6772)
- sc.exe (PID: 2928)
- sc.exe (PID: 2132)
- sc.exe (PID: 2680)
- sc.exe (PID: 6584)
- sc.exe (PID: 6860)
- sc.exe (PID: 2844)
- sc.exe (PID: 5236)
- sc.exe (PID: 488)
- sc.exe (PID: 2412)
- sc.exe (PID: 3992)
- sc.exe (PID: 6780)
- sc.exe (PID: 4360)
- sc.exe (PID: 5912)
- sc.exe (PID: 4336)
- sc.exe (PID: 3288)
- sc.exe (PID: 5652)
- sc.exe (PID: 7160)
- sc.exe (PID: 2008)
- sc.exe (PID: 7104)
- sc.exe (PID: 5988)
- sc.exe (PID: 7128)
- sc.exe (PID: 3488)
- sc.exe (PID: 4984)
- sc.exe (PID: 1140)
- sc.exe (PID: 1916)
- sc.exe (PID: 6664)
- sc.exe (PID: 4932)
- sc.exe (PID: 7144)
- sc.exe (PID: 396)
- sc.exe (PID: 6772)
- sc.exe (PID: 6680)
- sc.exe (PID: 2928)
- sc.exe (PID: 6496)
- sc.exe (PID: 6748)
- sc.exe (PID: 3840)
- sc.exe (PID: 1540)
- sc.exe (PID: 6964)
- sc.exe (PID: 4516)
- sc.exe (PID: 7092)
- sc.exe (PID: 5112)
- sc.exe (PID: 3620)
- sc.exe (PID: 6380)
- sc.exe (PID: 440)
- sc.exe (PID: 4764)
- sc.exe (PID: 6272)
- sc.exe (PID: 2904)
- sc.exe (PID: 3172)
- sc.exe (PID: 4428)
- sc.exe (PID: 640)
- sc.exe (PID: 5748)
- sc.exe (PID: 4188)
- sc.exe (PID: 1732)
- sc.exe (PID: 6552)
- sc.exe (PID: 6516)
- sc.exe (PID: 6816)
- sc.exe (PID: 6940)
- sc.exe (PID: 4536)
- sc.exe (PID: 1216)
- sc.exe (PID: 1080)
- sc.exe (PID: 6944)
- sc.exe (PID: 6860)
- sc.exe (PID: 5496)
- sc.exe (PID: 6868)
- sc.exe (PID: 6392)
- sc.exe (PID: 5236)
- sc.exe (PID: 3992)
- sc.exe (PID: 7164)
- sc.exe (PID: 4468)
- sc.exe (PID: 6292)
- sc.exe (PID: 876)
- sc.exe (PID: 6176)
- sc.exe (PID: 4992)
- sc.exe (PID: 4504)
- sc.exe (PID: 7160)
- sc.exe (PID: 4932)
- sc.exe (PID: 1760)
- sc.exe (PID: 7128)
- sc.exe (PID: 5340)
- sc.exe (PID: 2212)
- sc.exe (PID: 3436)
- sc.exe (PID: 6664)
- sc.exe (PID: 4136)
- sc.exe (PID: 2800)
- sc.exe (PID: 4516)
- sc.exe (PID: 5936)
- sc.exe (PID: 6952)
- sc.exe (PID: 3564)
- sc.exe (PID: 5872)
- sc.exe (PID: 6576)
- sc.exe (PID: 5472)
- sc.exe (PID: 936)
- sc.exe (PID: 1536)
- sc.exe (PID: 3092)
- sc.exe (PID: 2216)
- sc.exe (PID: 5400)
- sc.exe (PID: 2548)
- sc.exe (PID: 3816)
- sc.exe (PID: 6696)
- sc.exe (PID: 1540)
- sc.exe (PID: 6872)
- sc.exe (PID: 6256)
- sc.exe (PID: 5588)
- sc.exe (PID: 4740)
- sc.exe (PID: 4164)
- sc.exe (PID: 968)
- sc.exe (PID: 5876)
- sc.exe (PID: 6436)
- sc.exe (PID: 2976)
- sc.exe (PID: 6116)
- sc.exe (PID: 6148)
- sc.exe (PID: 5856)
- sc.exe (PID: 6260)
- sc.exe (PID: 6276)
- sc.exe (PID: 6152)
- sc.exe (PID: 3692)
- sc.exe (PID: 6392)
- sc.exe (PID: 4020)
- sc.exe (PID: 6316)
- sc.exe (PID: 6476)
- sc.exe (PID: 6760)
- sc.exe (PID: 4188)
- sc.exe (PID: 6536)
- sc.exe (PID: 6516)
- sc.exe (PID: 6376)
- sc.exe (PID: 6280)
- sc.exe (PID: 2496)
- sc.exe (PID: 5604)
- sc.exe (PID: 3732)
- sc.exe (PID: 3040)
- sc.exe (PID: 3952)
- sc.exe (PID: 4952)
- sc.exe (PID: 5920)
- sc.exe (PID: 6860)
- sc.exe (PID: 3436)
- sc.exe (PID: 7056)
- sc.exe (PID: 6940)
- sc.exe (PID: 1576)
- sc.exe (PID: 4992)
- sc.exe (PID: 3996)
- sc.exe (PID: 3828)
- sc.exe (PID: 6252)
- sc.exe (PID: 1216)
- sc.exe (PID: 2412)
- sc.exe (PID: 5496)
- sc.exe (PID: 5236)
- sc.exe (PID: 4468)
- sc.exe (PID: 3140)
- sc.exe (PID: 6872)
- sc.exe (PID: 624)
- sc.exe (PID: 6952)
- sc.exe (PID: 2972)
- sc.exe (PID: 1916)
- sc.exe (PID: 6732)
- sc.exe (PID: 6676)
- sc.exe (PID: 3040)
- sc.exe (PID: 4136)
- sc.exe (PID: 5876)
- sc.exe (PID: 5244)
- sc.exe (PID: 6584)
- sc.exe (PID: 644)
- sc.exe (PID: 6068)
- sc.exe (PID: 2736)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7116)
- cmd.exe (PID: 5488)
Starts application with an unusual extension
- cmd.exe (PID: 7028)
Application launched itself
- cmd.exe (PID: 7028)
Executable content was dropped or overwritten
- tar.exe (PID: 6804)
Process uses powershell cmdlet to discover network configuration
- cmd.exe (PID: 7028)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 7028)
Hides errors and continues executing the command without stopping
- powershell.exe (PID: 3820)
- powershell.exe (PID: 3144)
Removes files via Powershell
- powershell.exe (PID: 3820)
- powershell.exe (PID: 3144)
Sets the service to start on system boot
- sc.exe (PID: 5780)
- sc.exe (PID: 4704)
- sc.exe (PID: 4128)
- sc.exe (PID: 2464)
- sc.exe (PID: 5256)
- sc.exe (PID: 640)
- sc.exe (PID: 5320)
- sc.exe (PID: 748)
- sc.exe (PID: 6732)
- sc.exe (PID: 6468)
- sc.exe (PID: 6648)
- sc.exe (PID: 2844)
- sc.exe (PID: 6268)
- sc.exe (PID: 2956)
- sc.exe (PID: 420)
- sc.exe (PID: 644)
- sc.exe (PID: 7080)
- sc.exe (PID: 7108)
- sc.exe (PID: 7152)
- sc.exe (PID: 1480)
- sc.exe (PID: 4428)
- sc.exe (PID: 5872)
- sc.exe (PID: 4624)
- sc.exe (PID: 2512)
- sc.exe (PID: 6496)
- sc.exe (PID: 6892)
- sc.exe (PID: 7096)
- sc.exe (PID: 5400)
- sc.exe (PID: 748)
- sc.exe (PID: 1536)
- sc.exe (PID: 6004)
- sc.exe (PID: 4516)
- sc.exe (PID: 4520)
- sc.exe (PID: 2496)
- sc.exe (PID: 2904)
- sc.exe (PID: 3984)
- sc.exe (PID: 4544)
- sc.exe (PID: 3208)
- sc.exe (PID: 1080)
- sc.exe (PID: 7112)
- sc.exe (PID: 3532)
- sc.exe (PID: 6356)
- sc.exe (PID: 3128)
- sc.exe (PID: 4932)
- sc.exe (PID: 5004)
- sc.exe (PID: 6260)
- sc.exe (PID: 5540)
- sc.exe (PID: 3808)
- sc.exe (PID: 2940)
- sc.exe (PID: 7060)
- sc.exe (PID: 7104)
- sc.exe (PID: 5652)
- sc.exe (PID: 3564)
- sc.exe (PID: 7112)
- sc.exe (PID: 5404)
- sc.exe (PID: 5540)
- sc.exe (PID: 968)
- sc.exe (PID: 6268)
- sc.exe (PID: 6312)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 6540)
- StartMenuExperienceHost.exe (PID: 6392)
- ShellExperienceHost.exe (PID: 7008)
Starts SC.EXE for service management
- cmd.exe (PID: 7028)
- cmd.exe (PID: 6960)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7028)
- cmd.exe (PID: 7160)
Modifies existing scheduled task
- schtasks.exe (PID: 420)
- schtasks.exe (PID: 4188)
- schtasks.exe (PID: 6824)
- schtasks.exe (PID: 6736)
- schtasks.exe (PID: 1916)
- schtasks.exe (PID: 644)
- schtasks.exe (PID: 1140)
- schtasks.exe (PID: 2008)
- schtasks.exe (PID: 4384)
- schtasks.exe (PID: 3812)
- schtasks.exe (PID: 3288)
- schtasks.exe (PID: 3532)
- schtasks.exe (PID: 3128)
- schtasks.exe (PID: 720)
- schtasks.exe (PID: 2084)
- schtasks.exe (PID: 936)
- schtasks.exe (PID: 3280)
- schtasks.exe (PID: 1536)
- schtasks.exe (PID: 6096)
- schtasks.exe (PID: 3092)
- schtasks.exe (PID: 3060)
- schtasks.exe (PID: 4764)
- schtasks.exe (PID: 3296)
- schtasks.exe (PID: 4640)
- schtasks.exe (PID: 2464)
- schtasks.exe (PID: 6328)
- schtasks.exe (PID: 6688)
- schtasks.exe (PID: 6436)
- schtasks.exe (PID: 3732)
- schtasks.exe (PID: 4012)
- schtasks.exe (PID: 556)
- schtasks.exe (PID: 1400)
- schtasks.exe (PID: 5696)
- schtasks.exe (PID: 6424)
- schtasks.exe (PID: 396)
- schtasks.exe (PID: 6680)
- schtasks.exe (PID: 2928)
- schtasks.exe (PID: 4716)
- schtasks.exe (PID: 2956)
- schtasks.exe (PID: 6312)
- schtasks.exe (PID: 6160)
- schtasks.exe (PID: 6248)
- schtasks.exe (PID: 2424)
- schtasks.exe (PID: 2324)
- schtasks.exe (PID: 6280)
- schtasks.exe (PID: 1596)
- schtasks.exe (PID: 488)
- schtasks.exe (PID: 2996)
- schtasks.exe (PID: 6776)
- schtasks.exe (PID: 4384)
- schtasks.exe (PID: 3992)
- schtasks.exe (PID: 5568)
- schtasks.exe (PID: 6304)
- schtasks.exe (PID: 4336)
- schtasks.exe (PID: 3896)
- schtasks.exe (PID: 4504)
- schtasks.exe (PID: 6816)
- schtasks.exe (PID: 6376)
- schtasks.exe (PID: 4536)
- schtasks.exe (PID: 2736)
- schtasks.exe (PID: 1916)
- schtasks.exe (PID: 7104)
- schtasks.exe (PID: 6092)
- schtasks.exe (PID: 6164)
- schtasks.exe (PID: 4516)
- schtasks.exe (PID: 5712)
- schtasks.exe (PID: 4824)
- schtasks.exe (PID: 4908)
- schtasks.exe (PID: 3564)
- schtasks.exe (PID: 6952)
- schtasks.exe (PID: 2800)
- schtasks.exe (PID: 7160)
- schtasks.exe (PID: 7152)
- schtasks.exe (PID: 5300)
- schtasks.exe (PID: 5340)
- schtasks.exe (PID: 4984)
- schtasks.exe (PID: 4164)
- schtasks.exe (PID: 3808)
- schtasks.exe (PID: 5320)
- schtasks.exe (PID: 440)
- schtasks.exe (PID: 3188)
- schtasks.exe (PID: 3772)
- schtasks.exe (PID: 6220)
- schtasks.exe (PID: 3172)
- schtasks.exe (PID: 5728)
- schtasks.exe (PID: 1544)
- schtasks.exe (PID: 3280)
- schtasks.exe (PID: 720)
- schtasks.exe (PID: 6016)
- schtasks.exe (PID: 1536)
- schtasks.exe (PID: 2464)
- schtasks.exe (PID: 3900)
- schtasks.exe (PID: 6292)
- schtasks.exe (PID: 4932)
- schtasks.exe (PID: 7136)
- schtasks.exe (PID: 7116)
- schtasks.exe (PID: 1668)
- schtasks.exe (PID: 5092)
- schtasks.exe (PID: 2212)
- schtasks.exe (PID: 3816)
- schtasks.exe (PID: 4132)
- schtasks.exe (PID: 4136)
- schtasks.exe (PID: 5640)
- schtasks.exe (PID: 3288)
- schtasks.exe (PID: 3552)
- schtasks.exe (PID: 2940)
- schtasks.exe (PID: 3776)
- schtasks.exe (PID: 6436)
- schtasks.exe (PID: 1292)
- schtasks.exe (PID: 3436)
- schtasks.exe (PID: 4384)
- schtasks.exe (PID: 6284)
- schtasks.exe (PID: 3888)
- schtasks.exe (PID: 7124)
- schtasks.exe (PID: 6288)
- schtasks.exe (PID: 7092)
- schtasks.exe (PID: 2612)
- schtasks.exe (PID: 5340)
- schtasks.exe (PID: 5092)
- schtasks.exe (PID: 7128)
- schtasks.exe (PID: 1540)
- schtasks.exe (PID: 7088)
- schtasks.exe (PID: 5112)
- schtasks.exe (PID: 2800)
- schtasks.exe (PID: 7080)
- schtasks.exe (PID: 6304)
- schtasks.exe (PID: 5300)
- schtasks.exe (PID: 3508)
- schtasks.exe (PID: 5400)
- schtasks.exe (PID: 2260)
- schtasks.exe (PID: 1760)
- schtasks.exe (PID: 3172)
- schtasks.exe (PID: 3188)
- schtasks.exe (PID: 6380)
- schtasks.exe (PID: 4764)
- schtasks.exe (PID: 3772)
- schtasks.exe (PID: 4716)
- schtasks.exe (PID: 5540)
- schtasks.exe (PID: 5876)
- schtasks.exe (PID: 244)
- schtasks.exe (PID: 3692)
- schtasks.exe (PID: 5640)
- schtasks.exe (PID: 6576)
- schtasks.exe (PID: 5872)
- schtasks.exe (PID: 4428)
- schtasks.exe (PID: 4596)
- schtasks.exe (PID: 6256)
- schtasks.exe (PID: 5588)
- schtasks.exe (PID: 4708)
Creates or modifies Windows services
- reg.exe (PID: 3724)
- reg.exe (PID: 2928)
- reg.exe (PID: 6424)
- reg.exe (PID: 2132)
- reg.exe (PID: 5452)
- reg.exe (PID: 6584)
- reg.exe (PID: 132)
- reg.exe (PID: 5244)
- reg.exe (PID: 420)
- reg.exe (PID: 5496)
- reg.exe (PID: 6512)
- reg.exe (PID: 7056)
- reg.exe (PID: 6932)
- reg.exe (PID: 4128)
- reg.exe (PID: 4976)
- reg.exe (PID: 2260)
Starts process via Powershell
- powershell.exe (PID: 5964)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7028)
- cmd.exe (PID: 6960)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 7028)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 7028)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 6164)
- schtasks.exe (PID: 5712)
- schtasks.exe (PID: 4516)
- schtasks.exe (PID: 4824)
- schtasks.exe (PID: 4908)
- schtasks.exe (PID: 6952)
- schtasks.exe (PID: 7088)
- schtasks.exe (PID: 3840)
- schtasks.exe (PID: 2908)
- schtasks.exe (PID: 5192)
- schtasks.exe (PID: 5404)
- schtasks.exe (PID: 4448)
- schtasks.exe (PID: 6504)
- schtasks.exe (PID: 4544)
- schtasks.exe (PID: 3040)
- schtasks.exe (PID: 5892)
- schtasks.exe (PID: 3952)
- schtasks.exe (PID: 6320)
- schtasks.exe (PID: 3776)
- schtasks.exe (PID: 2880)
- schtasks.exe (PID: 6236)
- schtasks.exe (PID: 2680)
- schtasks.exe (PID: 6584)
- schtasks.exe (PID: 6376)
- schtasks.exe (PID: 6564)
- schtasks.exe (PID: 5488)
- schtasks.exe (PID: 3280)
- schtasks.exe (PID: 6068)
- schtasks.exe (PID: 2112)
- schtasks.exe (PID: 6684)
- schtasks.exe (PID: 4864)
- schtasks.exe (PID: 4028)
- schtasks.exe (PID: 5240)
- schtasks.exe (PID: 6760)
- schtasks.exe (PID: 6536)
- schtasks.exe (PID: 6004)
Stops a currently running service
- sc.exe (PID: 6196)
- sc.exe (PID: 6688)
- sc.exe (PID: 6360)
- sc.exe (PID: 3732)
- sc.exe (PID: 5404)
- sc.exe (PID: 4020)
- sc.exe (PID: 6316)
- sc.exe (PID: 1852)
- sc.exe (PID: 188)
Uses TASKKILL.EXE to kill Browsers
- cmd.exe (PID: 7028)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 7028)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 6392)
The process executes via Task Scheduler
- explorer.exe (PID: 3808)
Uses WMIC.EXE to obtain commands that are run when users log in
- cmd.exe (PID: 4108)
INFO
The process uses the downloaded file
- powershell.exe (PID: 6864)
- powershell.exe (PID: 5964)
Reads the computer name
- curl.exe (PID: 6752)
- ShellExperienceHost.exe (PID: 6540)
- OOSU10.exe (PID: 2904)
- NSudoLG.exe (PID: 1616)
- NSudoLG.exe (PID: 4504)
- NSudoLG.exe (PID: 6776)
- TextInputHost.exe (PID: 6236)
- StartMenuExperienceHost.exe (PID: 6392)
- SearchApp.exe (PID: 6860)
- ShellExperienceHost.exe (PID: 7008)
The sample compiled with english language support
- curl.exe (PID: 6752)
- tar.exe (PID: 6804)
Checks supported languages
- curl.exe (PID: 6752)
- chcp.com (PID: 6780)
- chcp.com (PID: 7040)
- chcp.com (PID: 7128)
- chcp.com (PID: 6872)
- chcp.com (PID: 7112)
- tar.exe (PID: 6804)
- chcp.com (PID: 6332)
- ShellExperienceHost.exe (PID: 6540)
- chcp.com (PID: 3536)
- OOSU10.exe (PID: 2904)
- chcp.com (PID: 6748)
- chcp.com (PID: 4640)
- chcp.com (PID: 6236)
- chcp.com (PID: 4020)
- chcp.com (PID: 6316)
- chcp.com (PID: 4012)
- chcp.com (PID: 6420)
- NSudoLG.exe (PID: 4504)
- NSudoLG.exe (PID: 1616)
- NSudoLG.exe (PID: 6776)
- StartMenuExperienceHost.exe (PID: 6392)
- SearchApp.exe (PID: 6860)
- ShellExperienceHost.exe (PID: 7008)
- TextInputHost.exe (PID: 6236)
- chcp.com (PID: 5460)
- chcp.com (PID: 4892)
Execution of CURL command
- cmd.exe (PID: 7028)
Changes the display of characters in the console
- cmd.exe (PID: 7028)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6280)
Changes the registry key values via Powershell
- cmd.exe (PID: 7028)
Reads mouse settings
- reg.exe (PID: 5004)
- reg.exe (PID: 5640)
- reg.exe (PID: 3632)
- reg.exe (PID: 1852)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6460)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6280)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 7076)
- explorer.exe (PID: 3808)
- WMIC.exe (PID: 1708)
Reads the machine GUID from the registry
- OOSU10.exe (PID: 2904)
- SearchApp.exe (PID: 6860)
Reads Microsoft Office registry keys
- OOSU10.exe (PID: 2904)
Sends debugging messages
- StartMenuExperienceHost.exe (PID: 6392)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 6392)
- SearchApp.exe (PID: 6860)
Checks proxy server information
- explorer.exe (PID: 3808)
- SearchApp.exe (PID: 6860)
Reads Environment values
- SearchApp.exe (PID: 6860)
Creates files or folders in the user directory
- StartMenuExperienceHost.exe (PID: 6392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .cnt | | | Help File Contents (100) |
|---|
Total processes
1 309
Monitored processes
1 159
Malicious processes
6
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WaaSMedicSvc" /v Start /t reg_dword /d 4 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 188 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 188 | sc stop uhssvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | reg add "HKLM\SYSTEM\CurrentControlSet\Services\lfsvc\Service\Configuration" /v "Status" /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\lsass.exe\PerfOptions" /v "PagePriority" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 244 | sc config CscService start=demand | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 244 | net stop "GigabyteUpdateService" | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 244 | schtasks /Change /TN "Microsoft\Windows\Application Experience\SdbinstMergeDbTask" /Disable | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 308 | sc config SstpSvc start=demand | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | sc config DevicesFlowUserSvc_dc2a4 start=demand | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
467 923
Read events
467 437
Write events
413
Delete events
73
Modification events
| (PID) Process: | (6864) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.FriendlyAppName |
Value: Windows Command Processor | |||
| (PID) Process: | (6864) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
| (PID) Process: | (1760) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | write | Name: | EnableActivityFeed |
Value: 0 | |||
| (PID) Process: | (4984) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | write | Name: | UploadUserActivities |
Value: 0 | |||
| (PID) Process: | (4932) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | write | Name: | PublishUserActivities |
Value: 0 | |||
| (PID) Process: | (1540) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\CapabilityAccessManager\ConsentStore\location |
| Operation: | write | Name: | Value |
Value: Deny | |||
| (PID) Process: | (936) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Sensor\Overrides\{BFA794E4-F964-4FDB-90F6-51056BFE4B44} |
| Operation: | write | Name: | SensorPermissionState |
Value: 0 | |||
| (PID) Process: | (236) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\lfsvc\Service\Configuration |
| Operation: | write | Name: | Status |
Value: 0 | |||
| (PID) Process: | (2828) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Maps |
| Operation: | write | Name: | AutoUpdateEnabled |
Value: 0 | |||
| (PID) Process: | (5004) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\Explorer |
| Operation: | write | Name: | DisableNotificationCenter |
Value: 1 | |||
Executable files
5
Suspicious files
18
Text files
208
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5392 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hgmed4kb.1ni.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5392 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:1DE2CC0BCCF10510241DAD99EEEDF87D | SHA256:7C512B8B1256DD701B174CF24E7CA6D7105A5D1C233B43DC69C8FC659084A030 | |||
| 5392 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_anqm0jga.srb.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3564 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_e5znflrr.3i3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6420 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2rpa214w.qzy.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1540 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qyh0a4i3.ckw.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6864 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_e1vugfib.un0.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1540 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uuwlhood.r2w.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6752 | curl.exe | C:\Oneclick Tools.zip | compressed | |
MD5:517B76CBA1C1B12EC146A60A2745B28E | SHA256:C0F0D33D18D79C58D0956A5057EC26407D50BEBB8960514CEB88D7FB7FB2502B | |||
| 6804 | tar.exe | C:\Oneclick Tools\Amd\1- What's AMD.txt | text | |
MD5:70E86F4293A455E906EED0DA485445B4 | SHA256:BFAAB5D507C771D3374850D6107E2CFA903A2C187947A59638EF4B54BE53343E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
43
DNS requests
24
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6156 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
5392 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
5392 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2632 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.23.209.140:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| unknown |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |