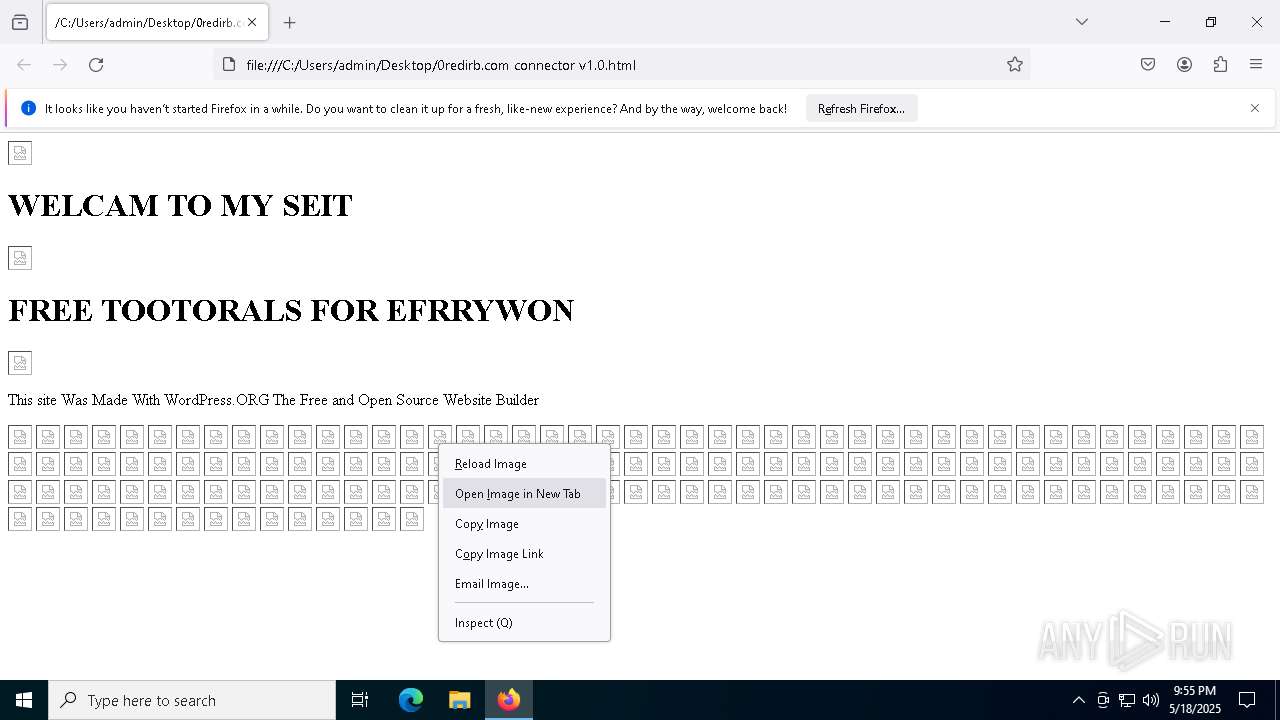
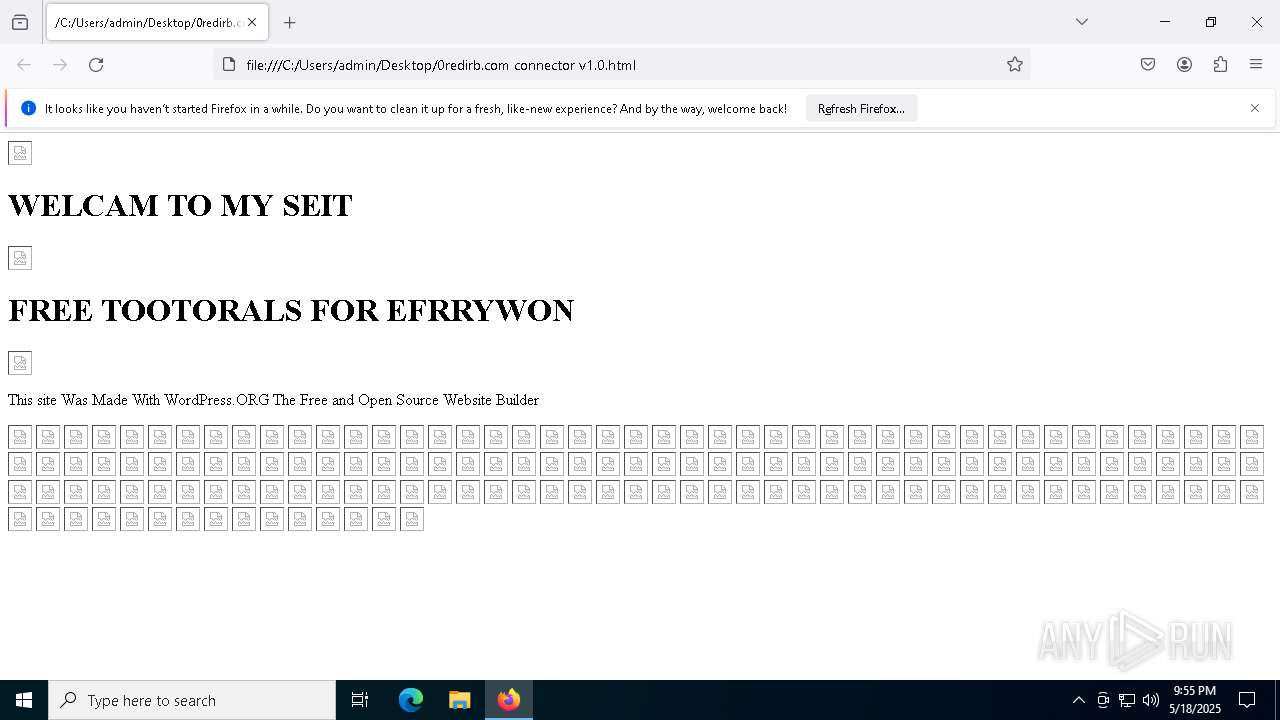
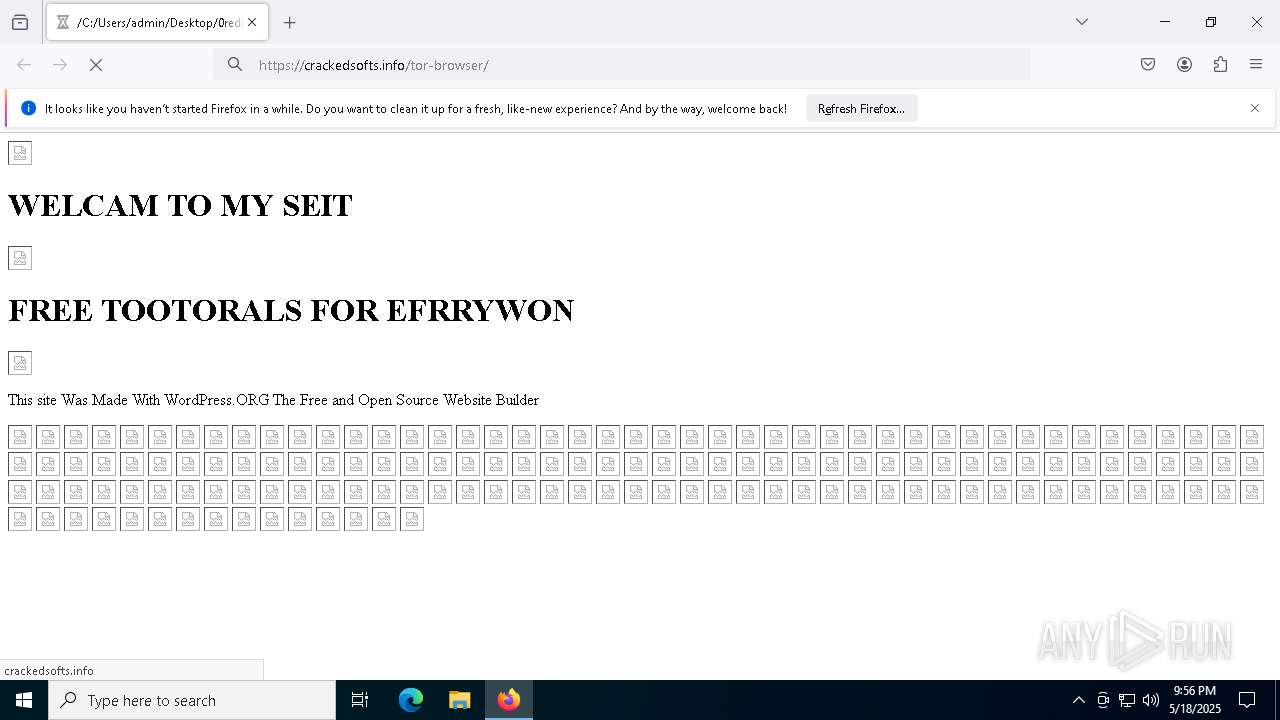
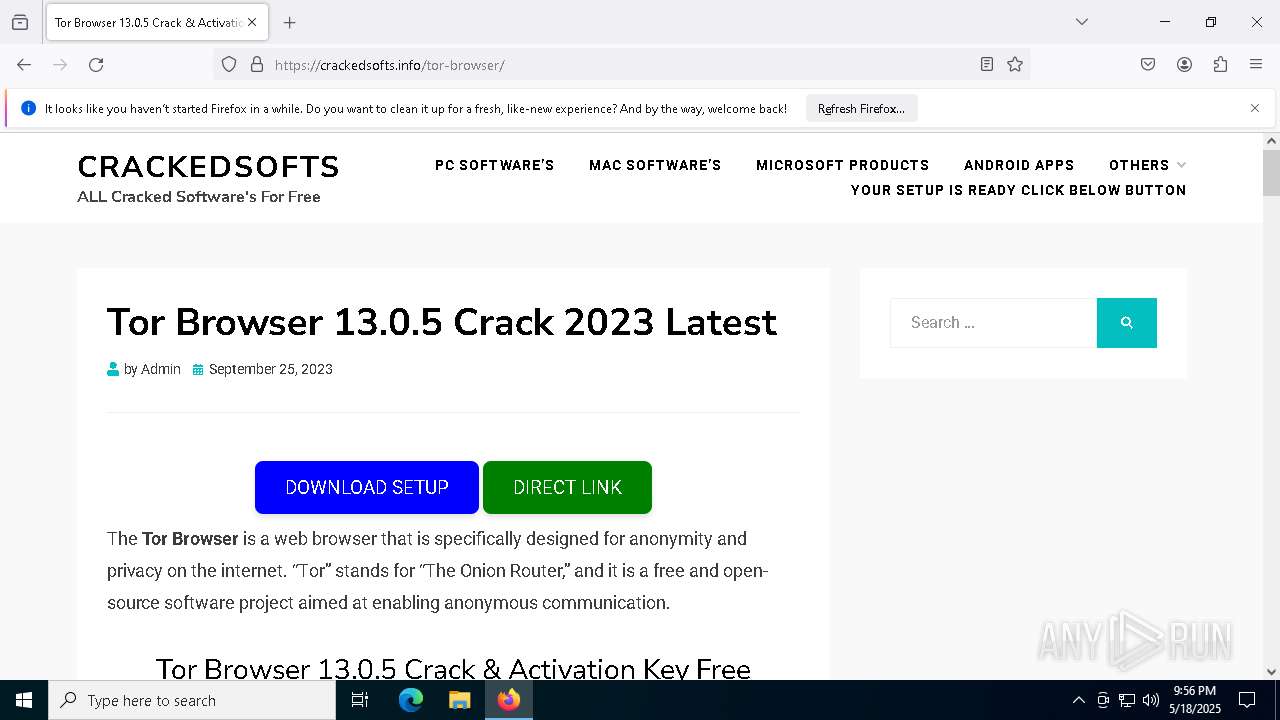
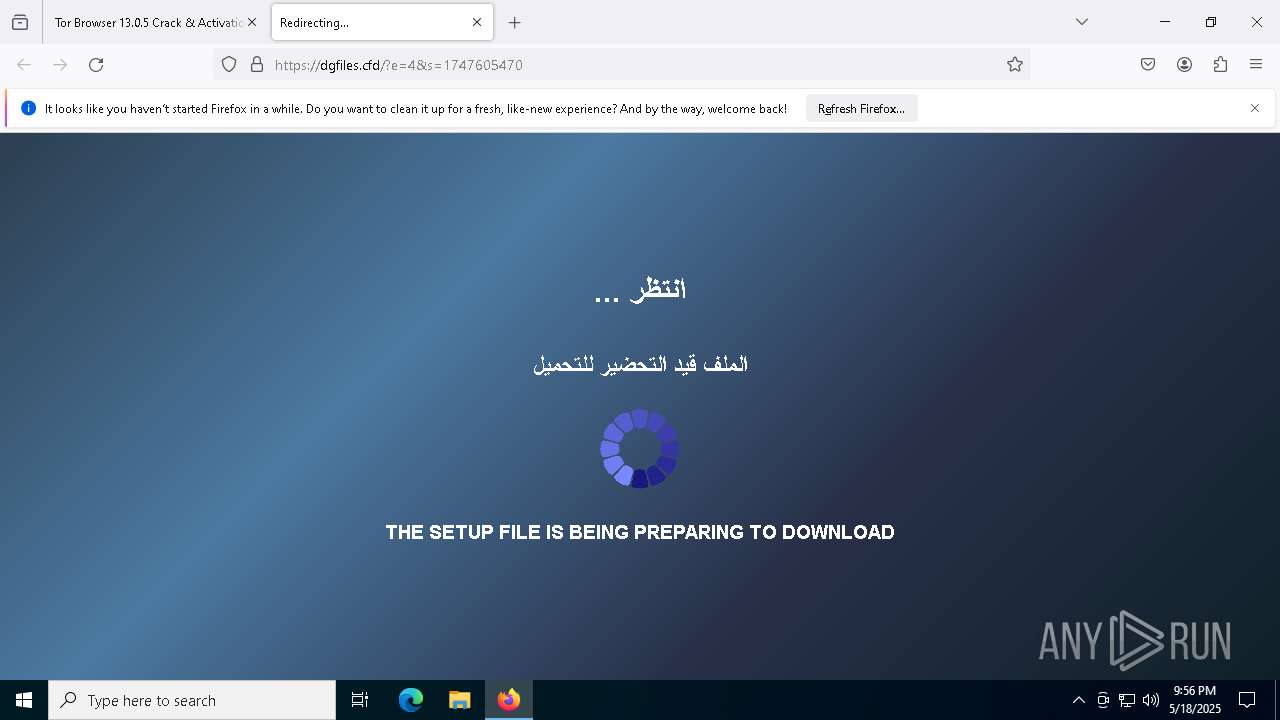
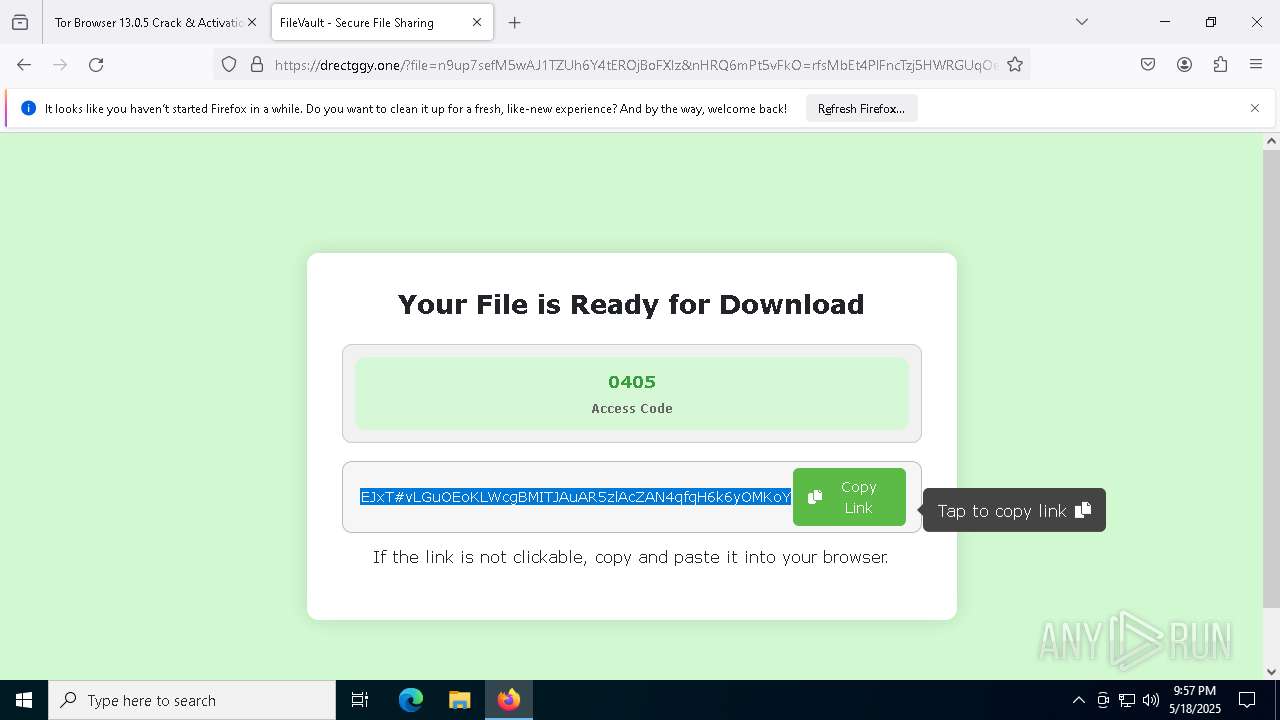
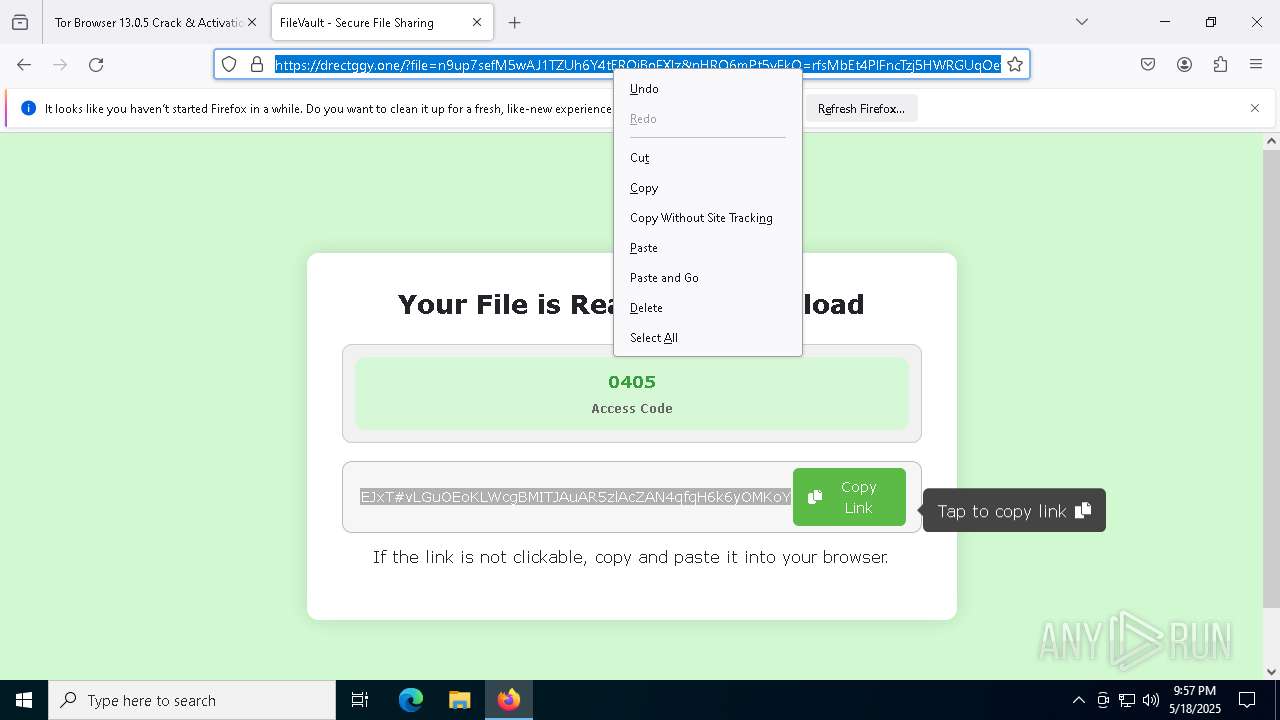
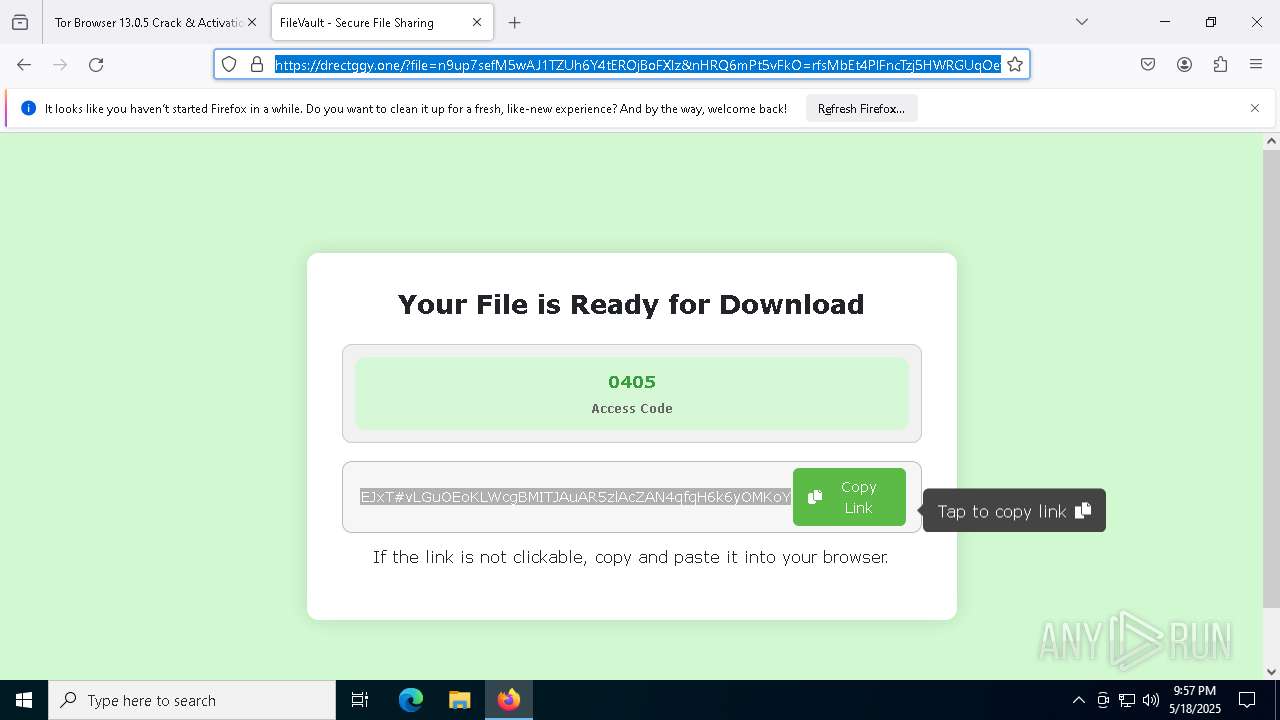
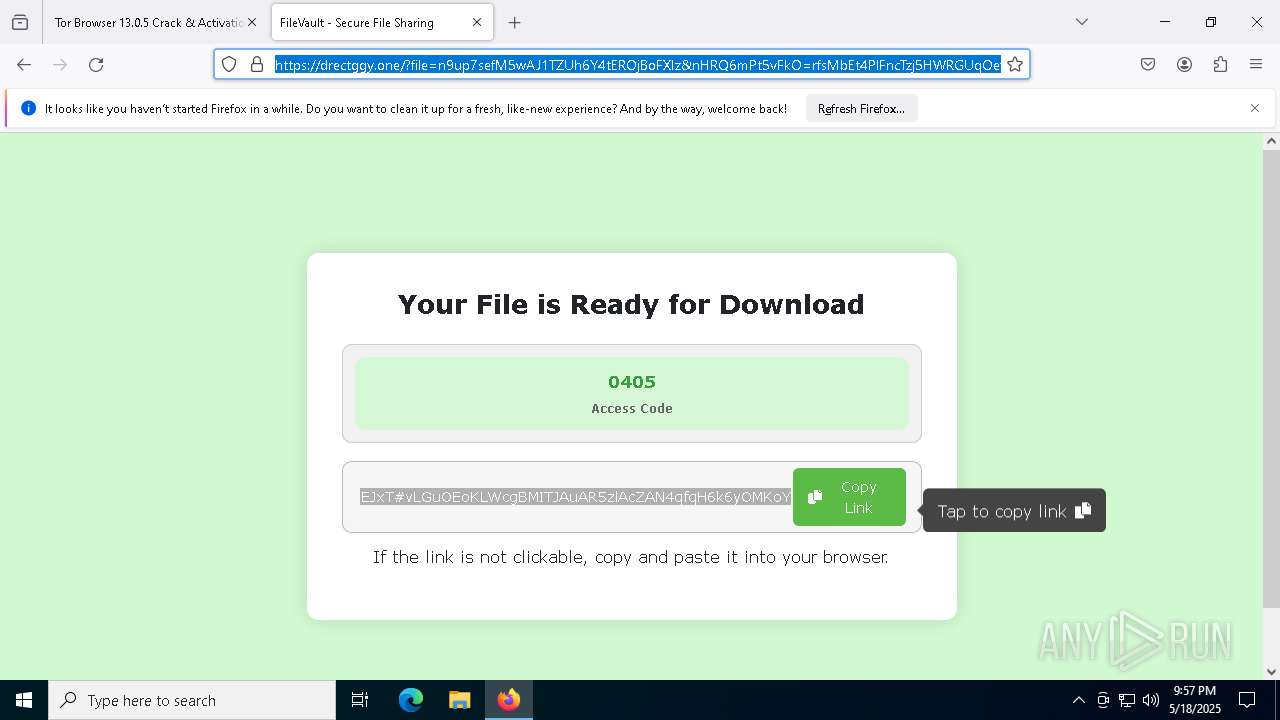
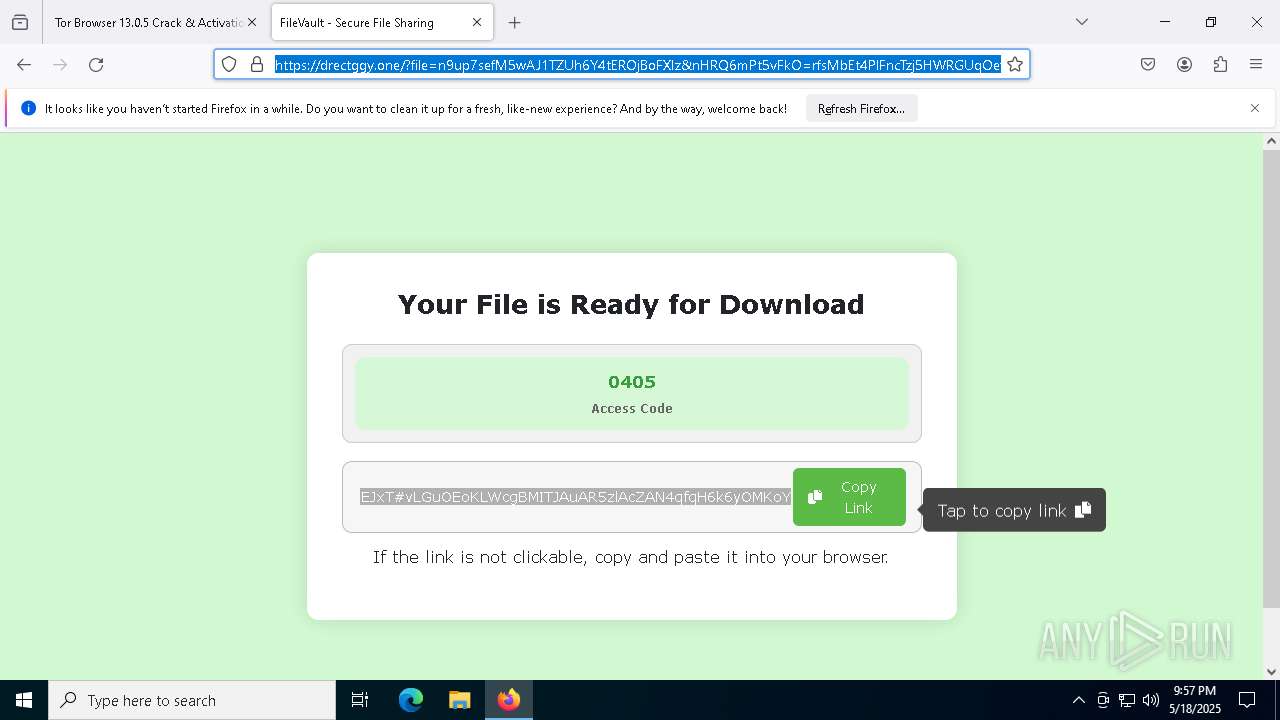
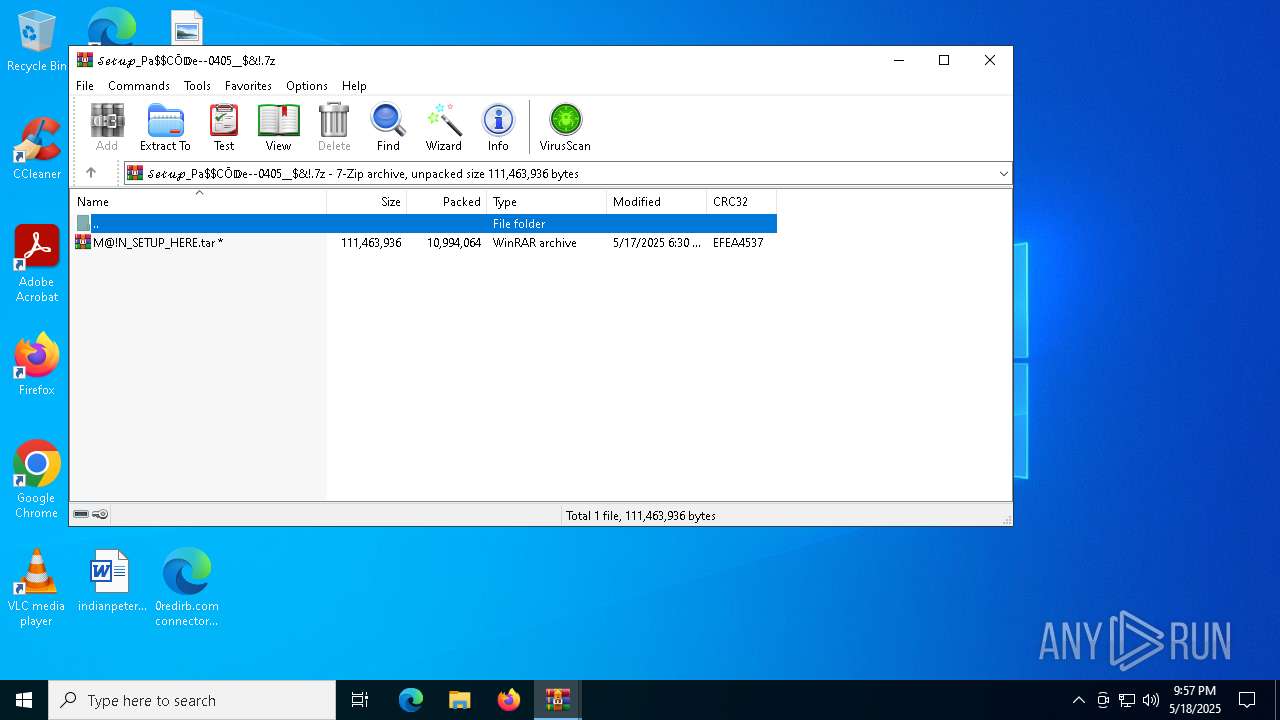
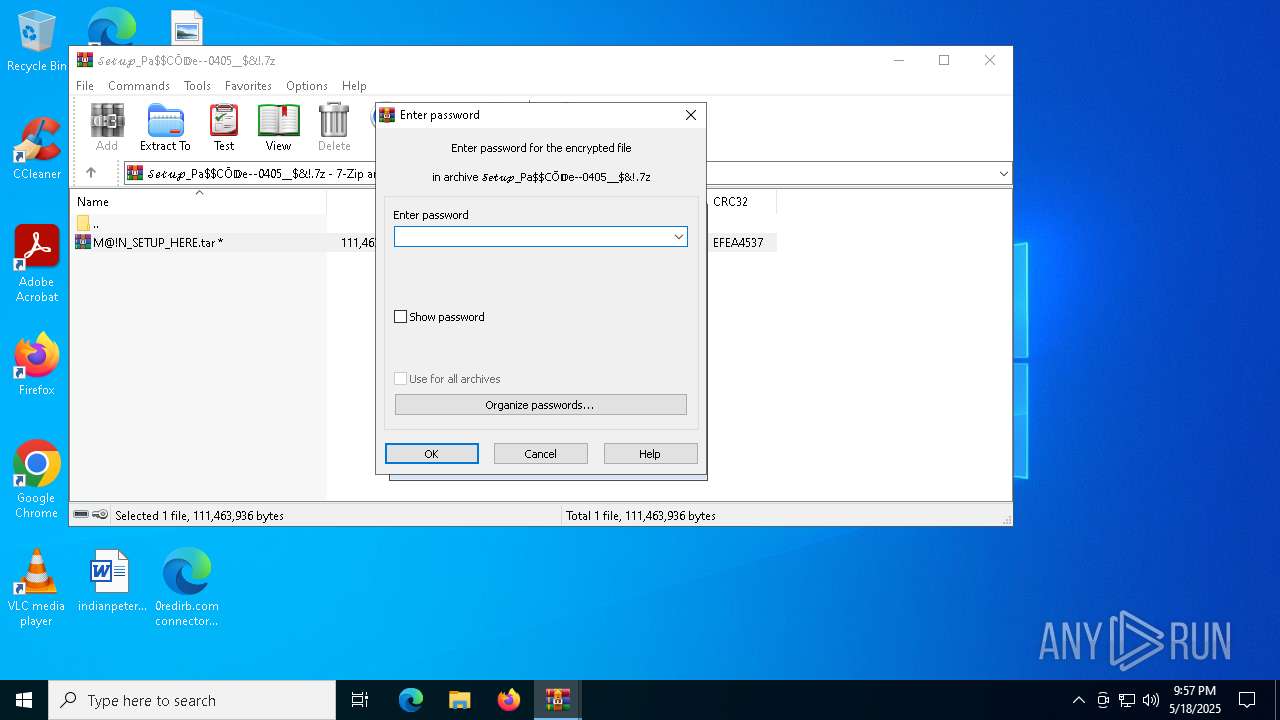
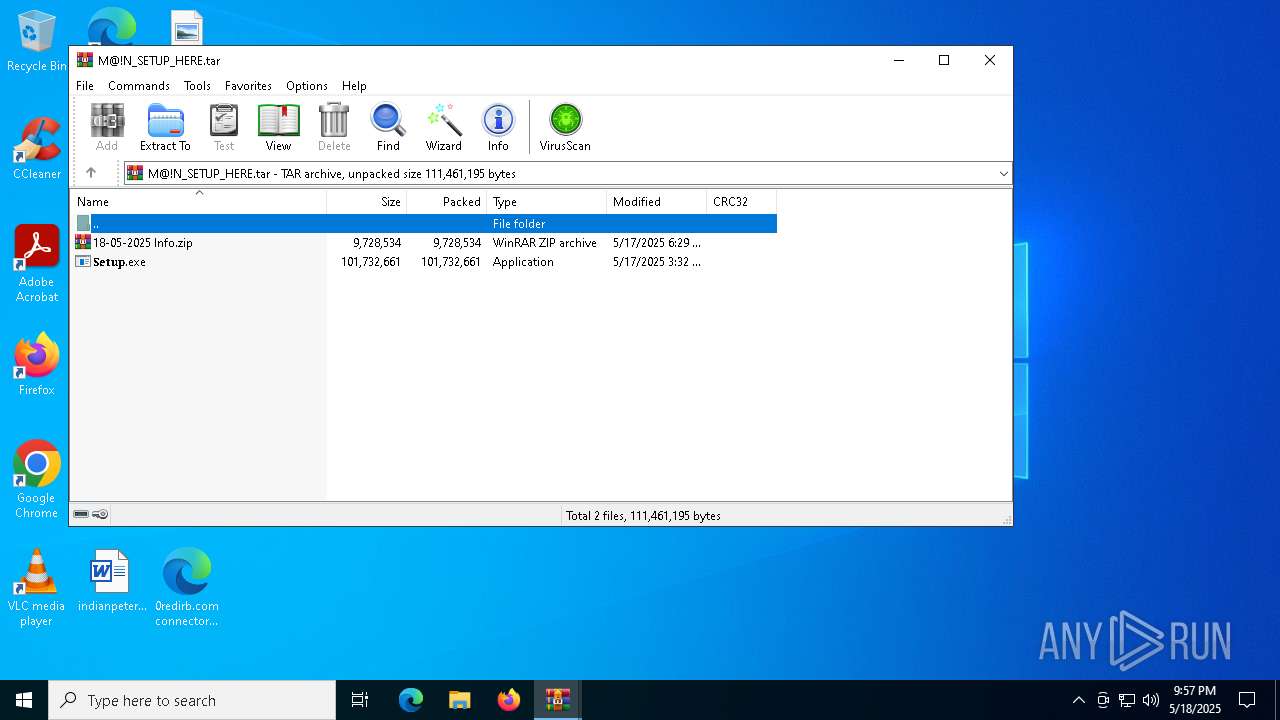
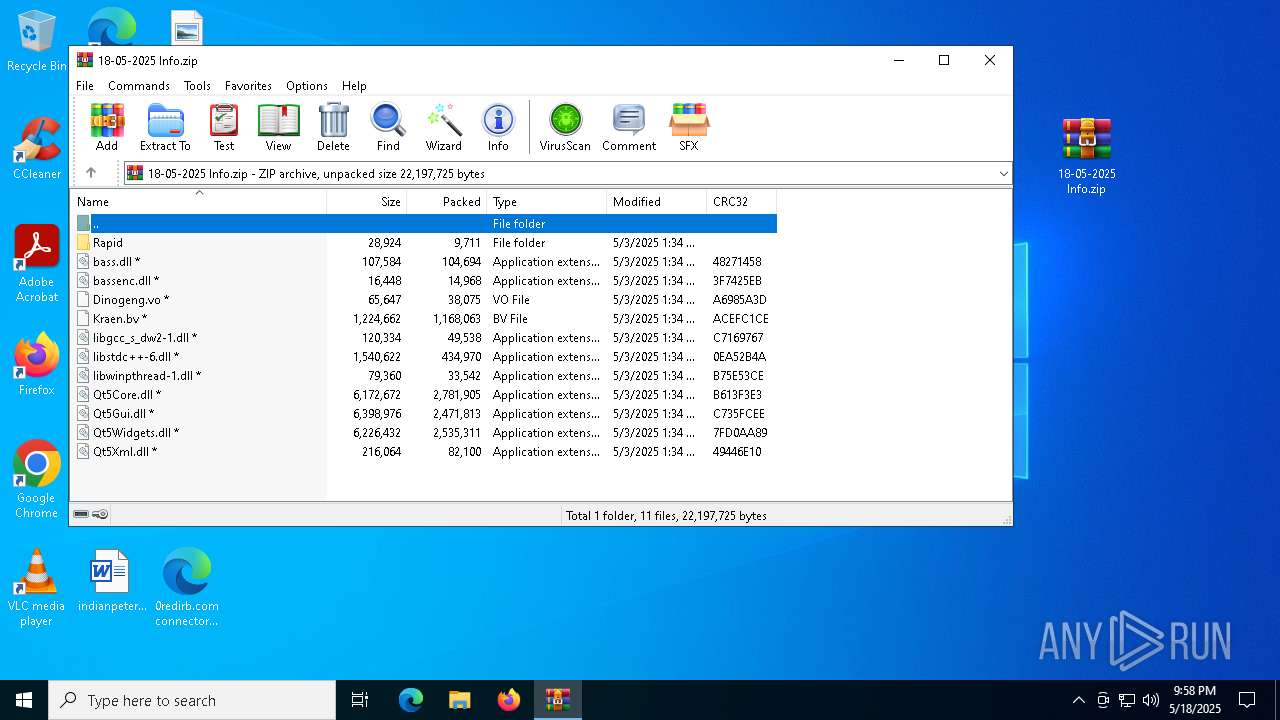
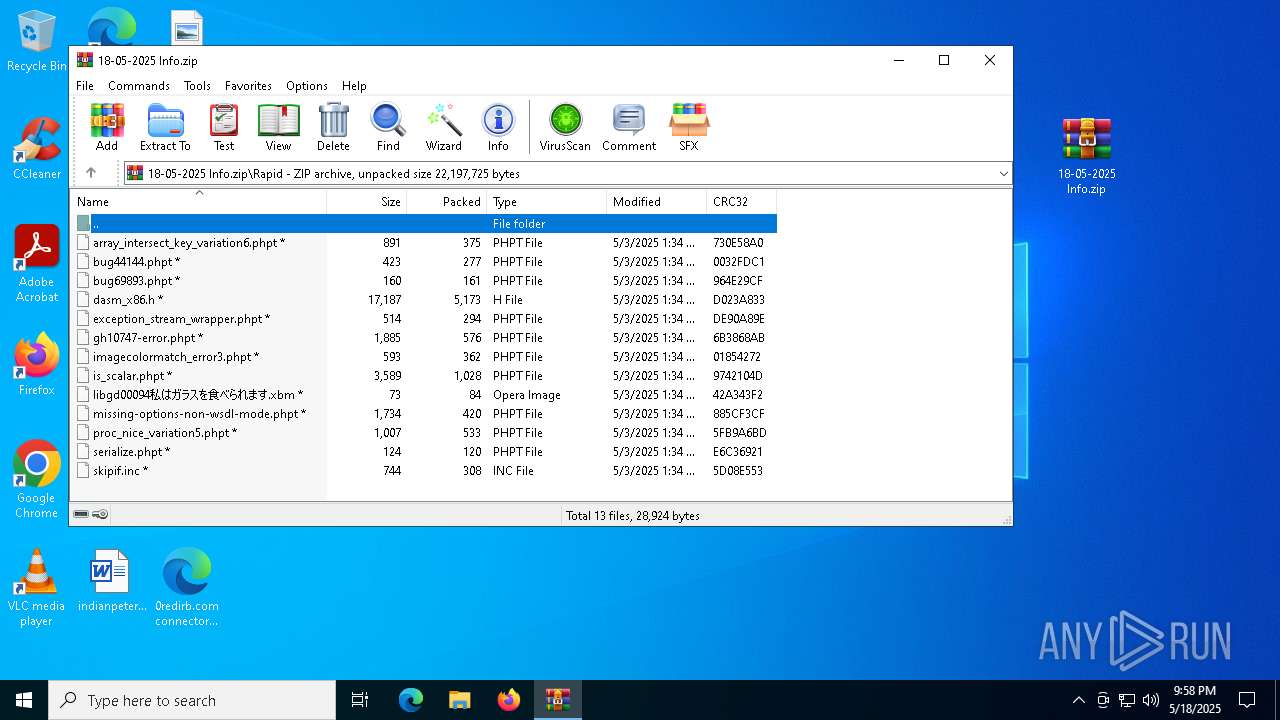
| File name: | 0redirb.com connector v1.0.html |
| Full analysis: | https://app.any.run/tasks/92817510-ed48-469e-b452-7055c77fd214 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 21:54:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text |
| MD5: | 80343FCD5AF81DA53EC097D115332803 |
| SHA1: | 22E32223358B7F353E6F4BA9A064CD8033E5ABB7 |
| SHA256: | E745EC8559ECD055035FC27ED13C0642A0CBB783DE383DCE15C7372F28125CF1 |
| SSDEEP: | 48:a6e+jfYwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAu:3fn |
MALICIOUS
Executing a file with an untrusted certificate
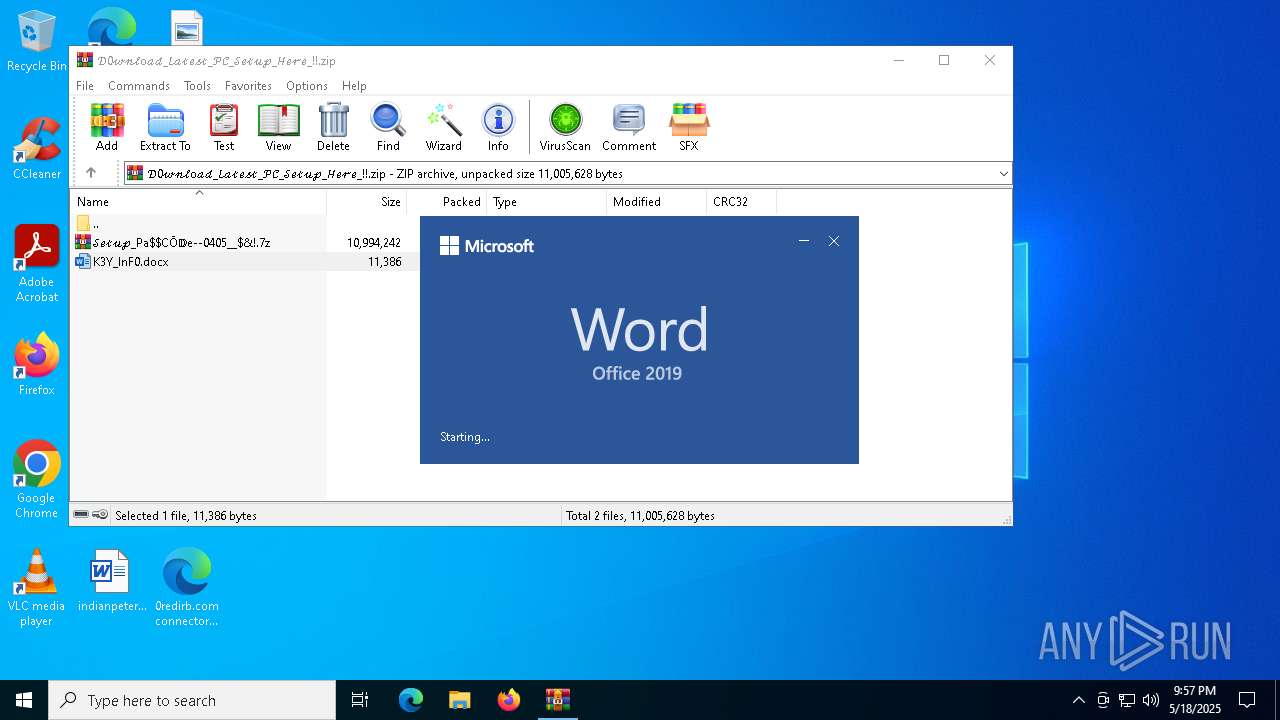
- 𝐒𝐞𝐭𝐮𝐩.exe (PID: 7944)
AutoIt loader has been detected (YARA)
- Expansys.com (PID: 2908)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6908)
Application launched itself
- WinRAR.exe (PID: 6908)
- WinRAR.exe (PID: 5972)
- cmd.exe (PID: 8172)
- WinRAR.exe (PID: 872)
Starts CMD.EXE for commands execution
- 𝐒𝐞𝐭𝐮𝐩.exe (PID: 7944)
- cmd.exe (PID: 8172)
Executing commands from a ".bat" file
- 𝐒𝐞𝐭𝐮𝐩.exe (PID: 7944)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 8172)
Get information on the list of running processes
- cmd.exe (PID: 8172)
Starts the AutoIt3 executable file
- cmd.exe (PID: 8172)
The executable file from the user directory is run by the CMD process
- Expansys.com (PID: 2908)
Starts application with an unusual extension
- cmd.exe (PID: 8172)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Expansys.com (PID: 2908)
There is functionality for taking screenshot (YARA)
- Expansys.com (PID: 2908)
INFO
Application launched itself
- firefox.exe (PID: 7392)
- firefox.exe (PID: 7420)
Reads the software policy settings
- slui.exe (PID: 7212)
- slui.exe (PID: 2908)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6908)
Checks proxy server information
- slui.exe (PID: 2908)
Manual execution by a user
- WinRAR.exe (PID: 6908)
- 𝐒𝐞𝐭𝐮𝐩.exe (PID: 7944)
- WinRAR.exe (PID: 7924)
Creates a new folder
- cmd.exe (PID: 7856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
178
Monitored processes
41
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
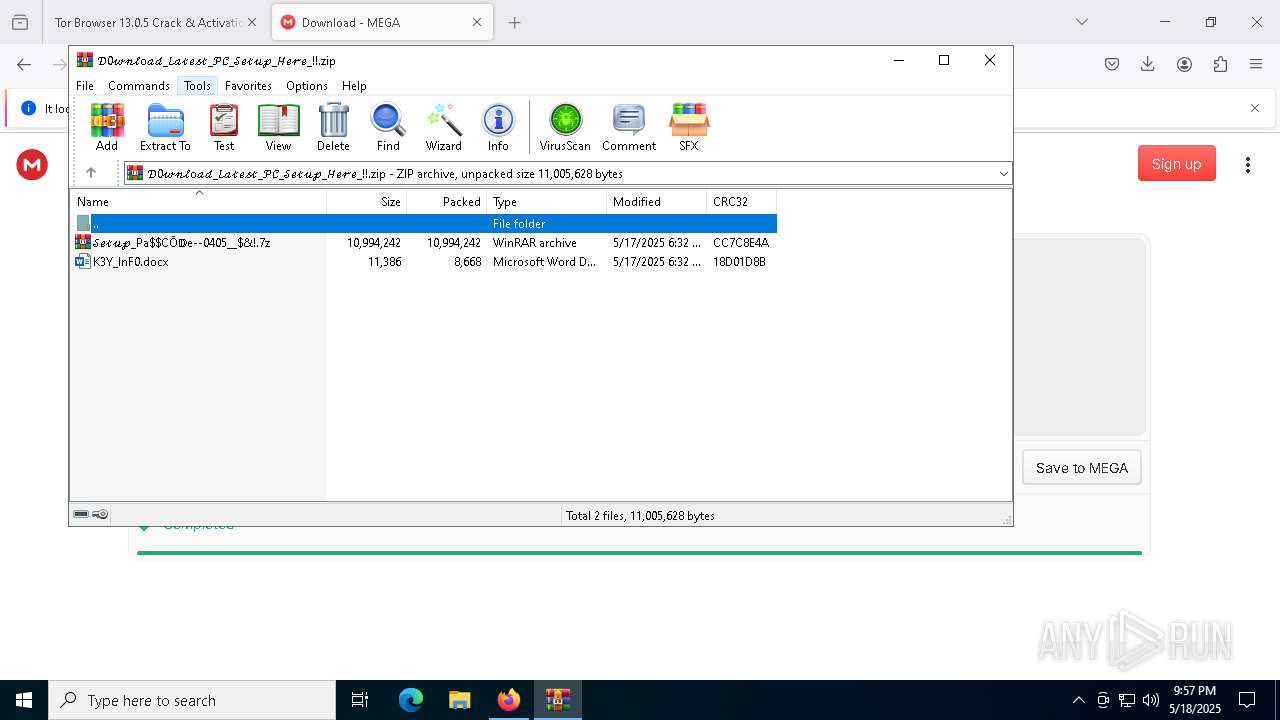
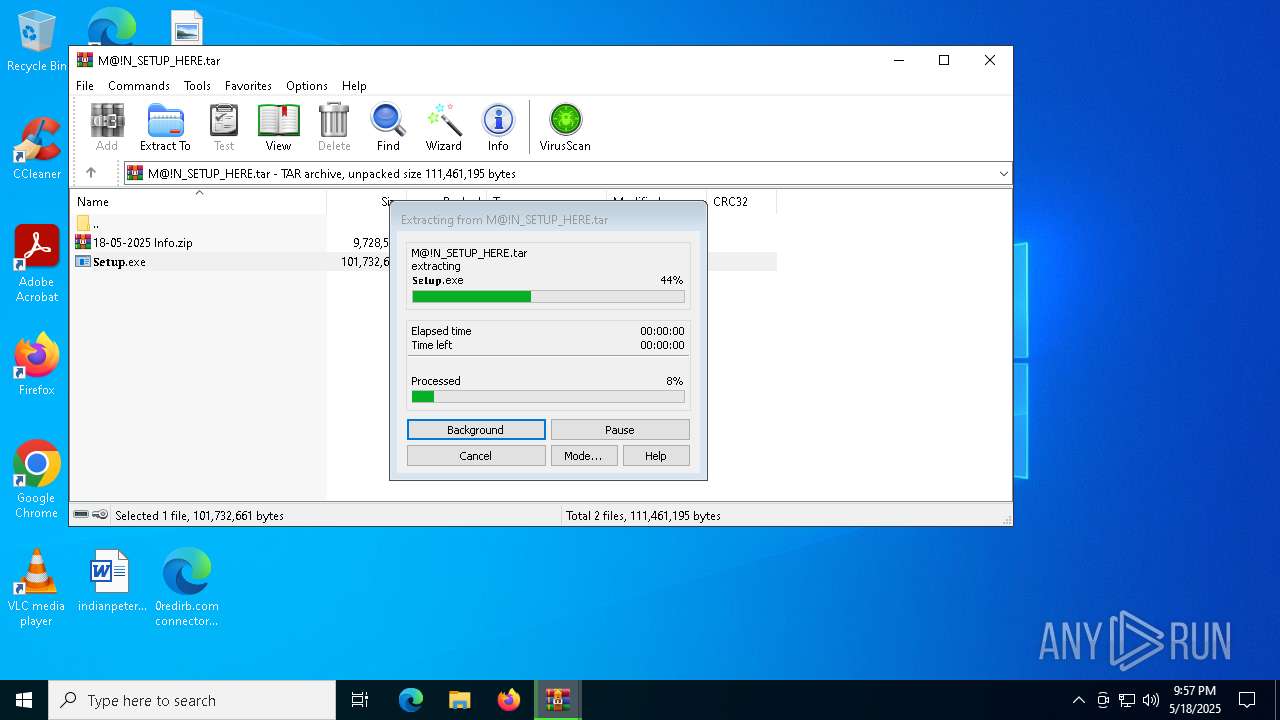
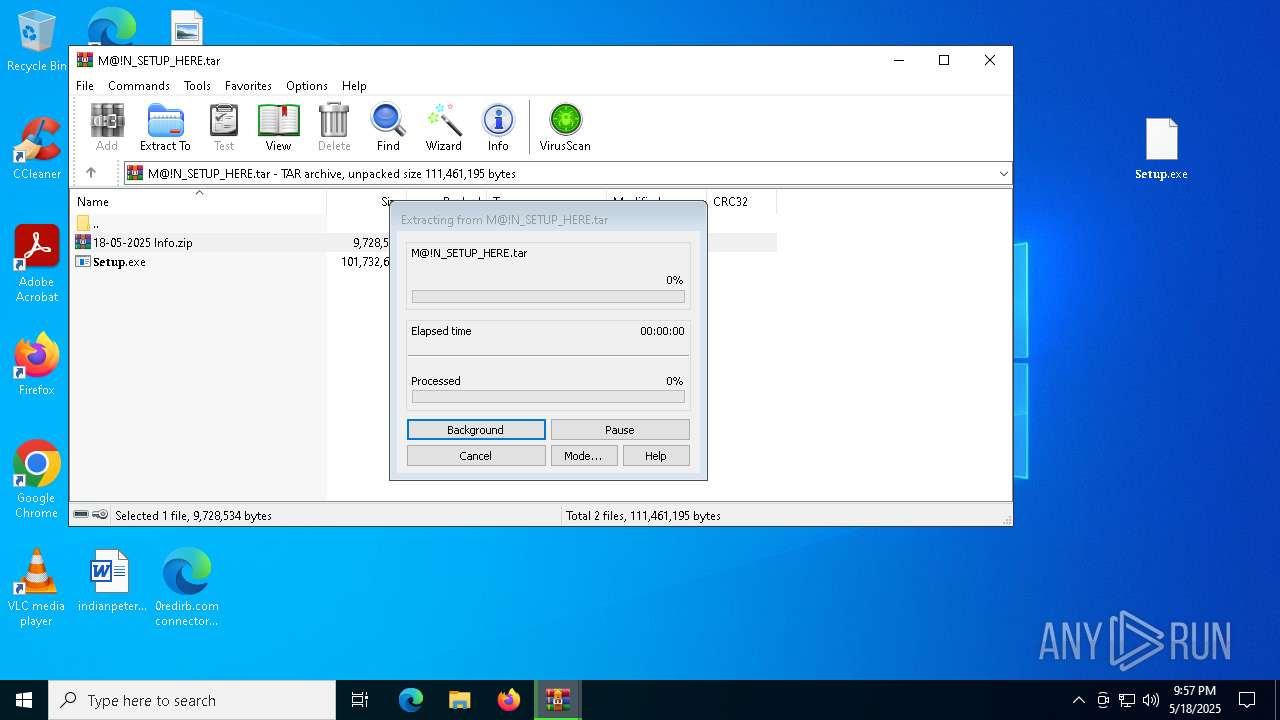
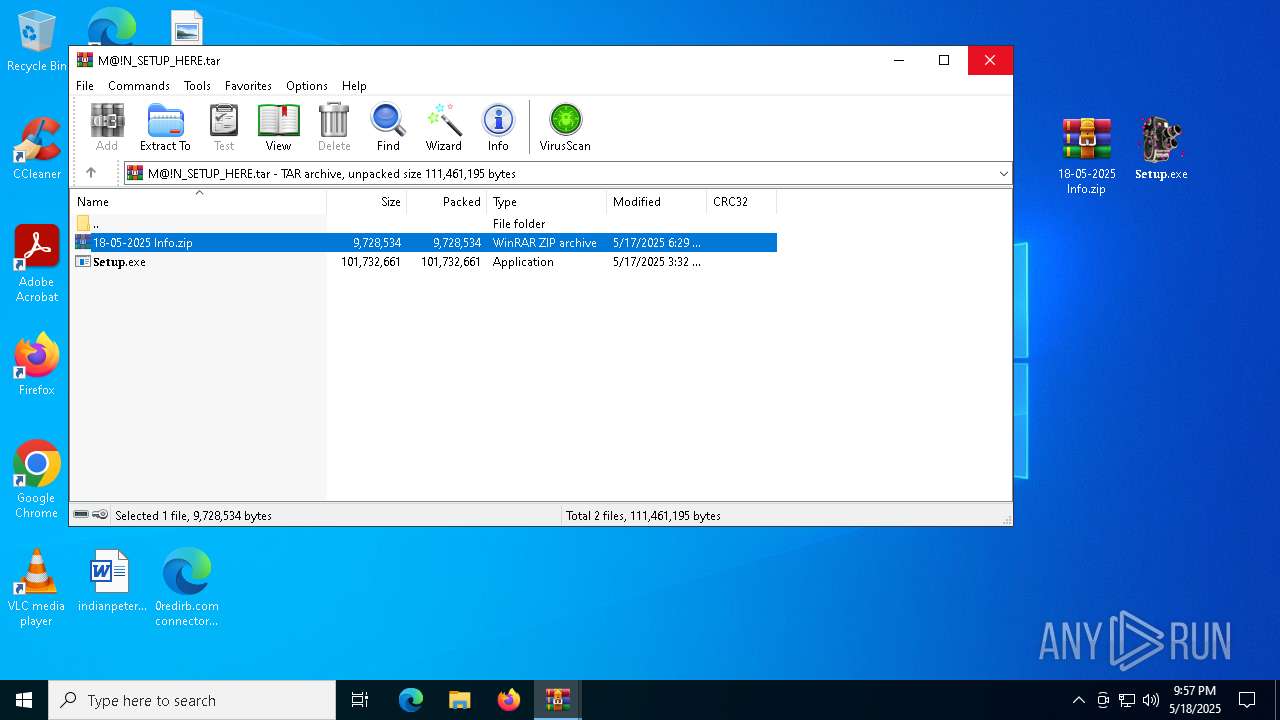
| 872 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb5972.27143\M@!N_SETUP_HERE.tar | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1056 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5692 -childID 7 -isForBrowser -prefsHandle 5640 -prefMapHandle 5652 -prefsLen 31658 -prefMapSize 244583 -jsInitHandle 1228 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {b44798ad-d643-4369-8e76-4c596bd508be} 7420 "\\.\pipe\gecko-crash-server-pipe.7420" 1cc6325bd90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
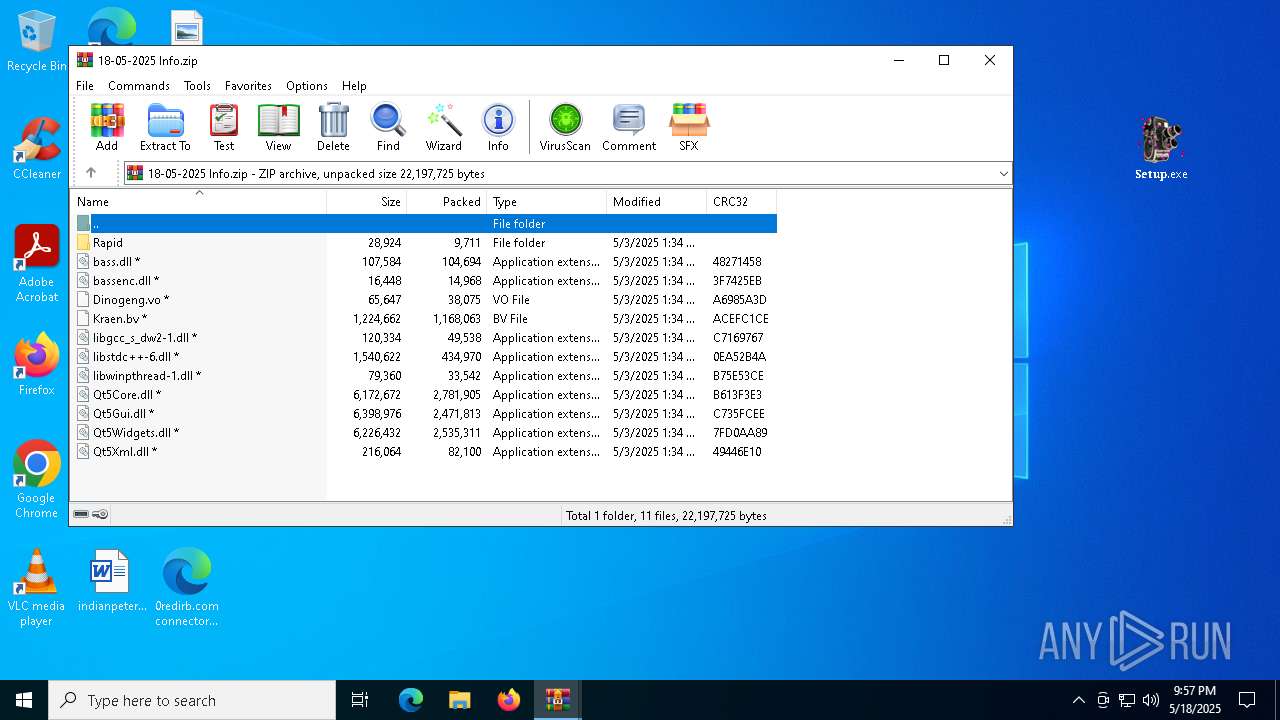
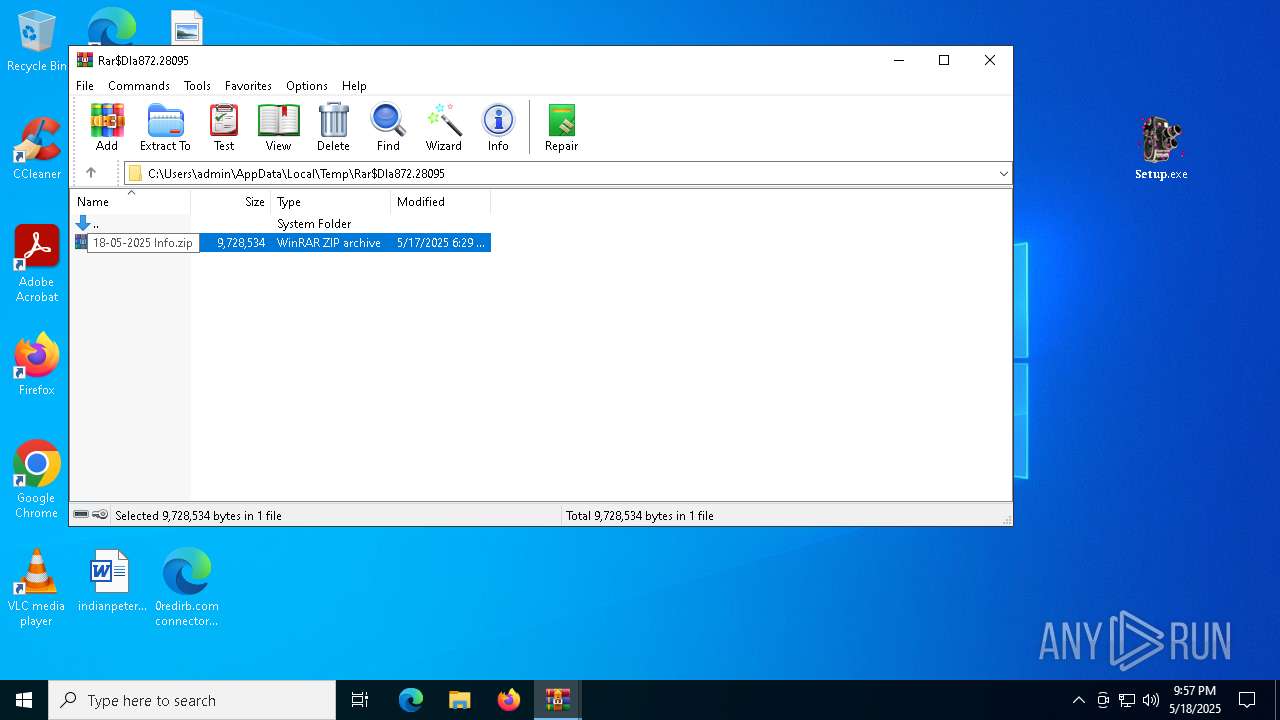
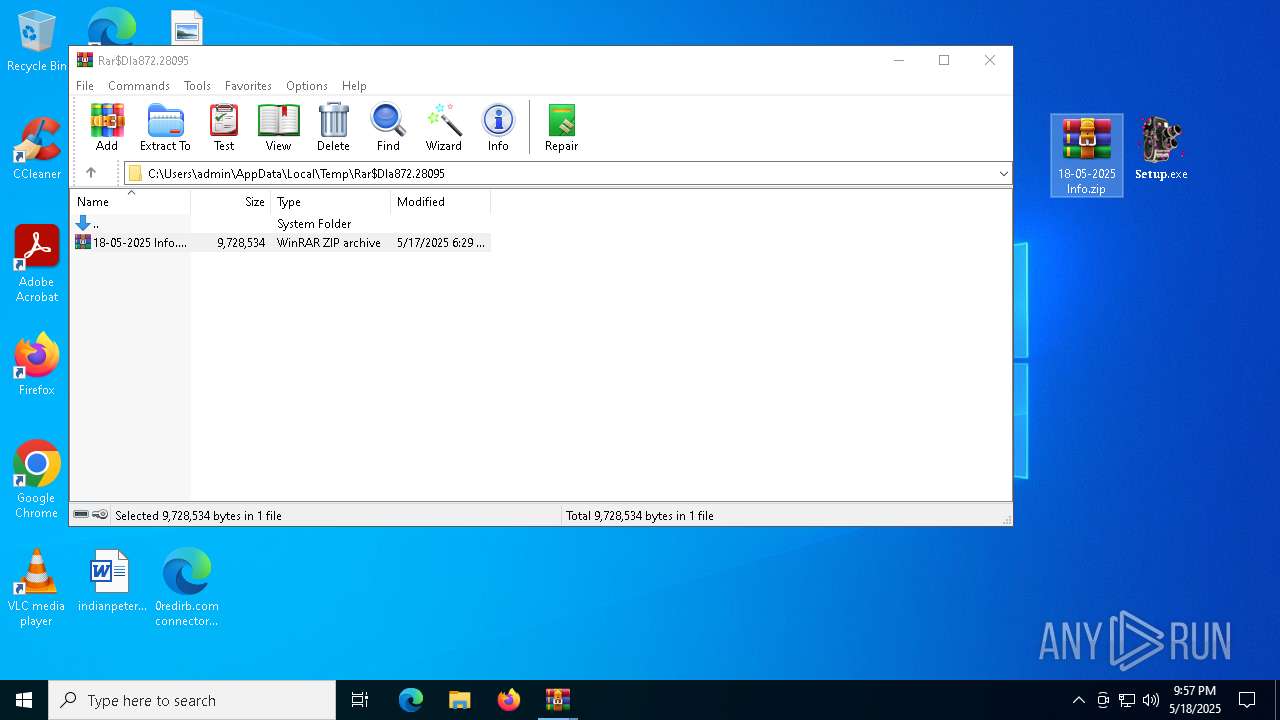
| 1240 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa872.28095\18-05-2025 Info.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1512 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5016 -childID 9 -isForBrowser -prefsHandle 2580 -prefMapHandle 5988 -prefsLen 31736 -prefMapSize 244583 -jsInitHandle 1228 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {8b4175ef-d09f-4541-8b8f-ed42bcee7c6b} 7420 "\\.\pipe\gecko-crash-server-pipe.7420" 1cc65defa10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2136 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4924 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4916 -prefMapHandle 4908 -prefsLen 36588 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {d36028f2-abdb-4ea4-8b98-49ab30b57022} 7420 "\\.\pipe\gecko-crash-server-pipe.7420" 1cc66f4c710 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 2908 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2908 | Expansys.com A | C:\Users\admin\AppData\Local\Temp\295291\Expansys.com | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Version: 3, 3, 15, 5 Modules
| |||||||||||||||
| 3396 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6508 -childID 13 -isForBrowser -prefsHandle 1324 -prefMapHandle 6264 -prefsLen 31736 -prefMapSize 244583 -jsInitHandle 1228 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {1ad307dc-4fd6-4c9d-844f-c15a1f5b6ac9} 7420 "\\.\pipe\gecko-crash-server-pipe.7420" 1cc674a2850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 4016 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5812 -childID 12 -isForBrowser -prefsHandle 5988 -prefMapHandle 6416 -prefsLen 31736 -prefMapSize 244583 -jsInitHandle 1228 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {07b8c187-ad74-4062-996c-58b51430c626} 7420 "\\.\pipe\gecko-crash-server-pipe.7420" 1cc65deff50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 5036 | findstr /V "Reproduce" Rider | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
37 364
Read events
37 001
Write events
339
Delete events
24
Modification events
| (PID) Process: | (7420) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (6908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
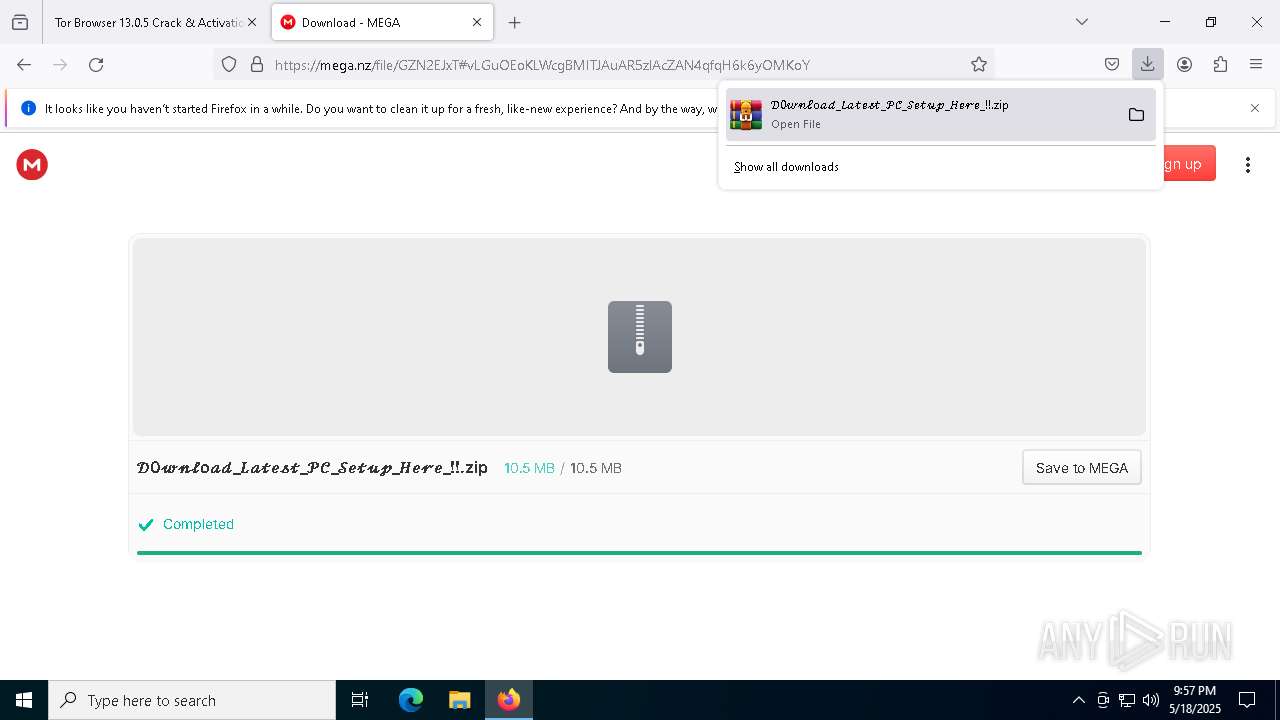
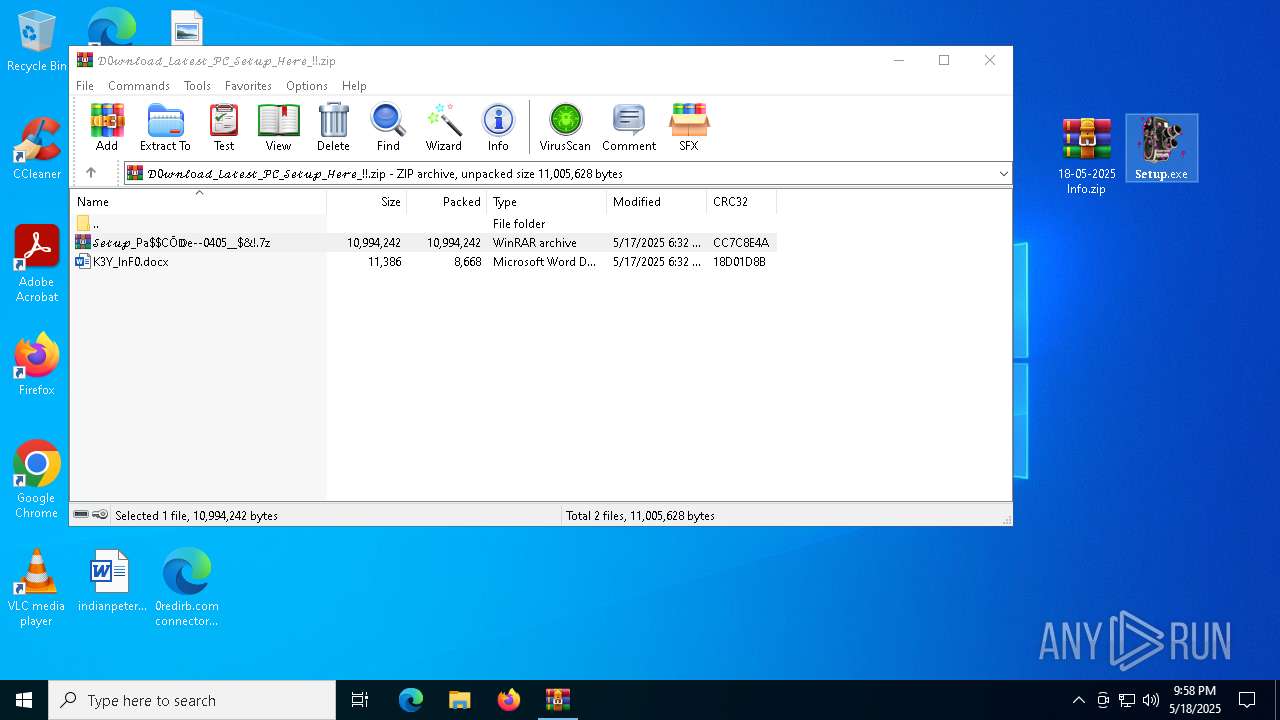
Value: C:\Users\admin\Downloads\𝒟0𝓌𝓃𝓁o𝒶𝒹_𝐿𝒶𝓉𝑒𝓈𝓉_𝒫𝒞_𝒮𝑒𝓉𝓊𝓅_𝐻𝑒𝓇𝑒_!!.zip | |||
| (PID) Process: | (6908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
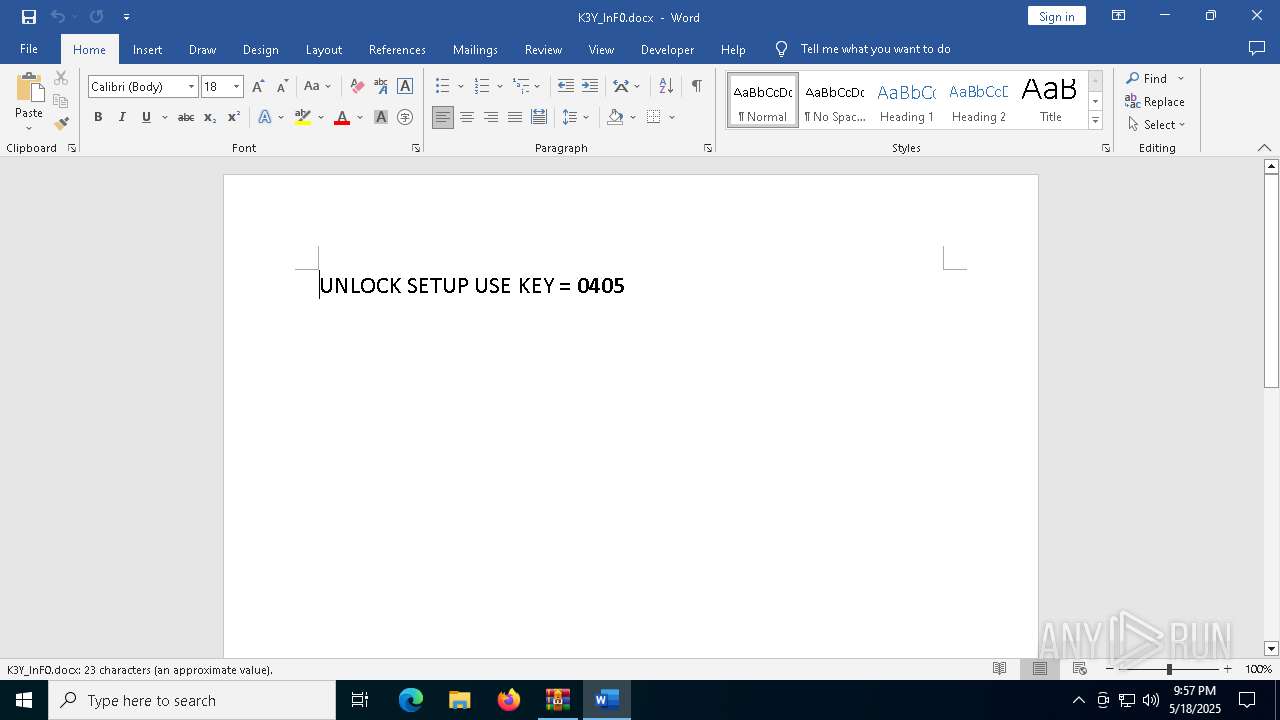
| (PID) Process: | (6908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.docx\OpenWithProgids |
| Operation: | write | Name: | Word.Document.12 |
Value: | |||
Executable files
0
Suspicious files
272
Text files
39
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7420 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-wal | — | |
MD5:— | SHA256:— | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
59
TCP/UDP connections
181
DNS requests
180
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7420 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7420 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7420 | firefox.exe | POST | — | 142.250.184.195:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
7420 | firefox.exe | POST | 200 | 95.101.54.211:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7420 | firefox.exe | POST | 200 | 95.101.54.211:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7420 | firefox.exe | POST | 200 | 95.101.54.114:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7420 | firefox.exe | POST | 200 | 95.101.54.114:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7420 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
7420 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
7420 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | — | — | whitelisted |
7420 | firefox.exe | 142.250.185.170:443 | safebrowsing.googleapis.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
0redirb.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
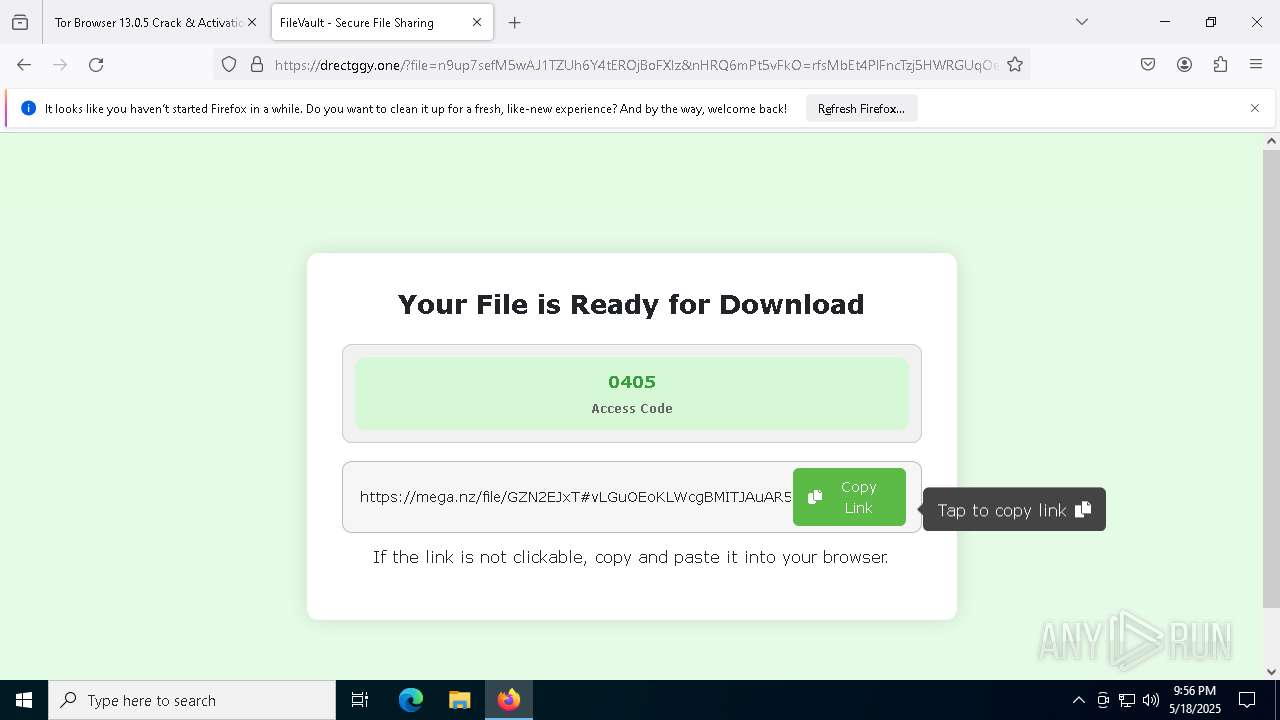
2196 | svchost.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
2196 | svchost.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
2196 | svchost.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
7420 | firefox.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
7420 | firefox.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
7420 | firefox.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |