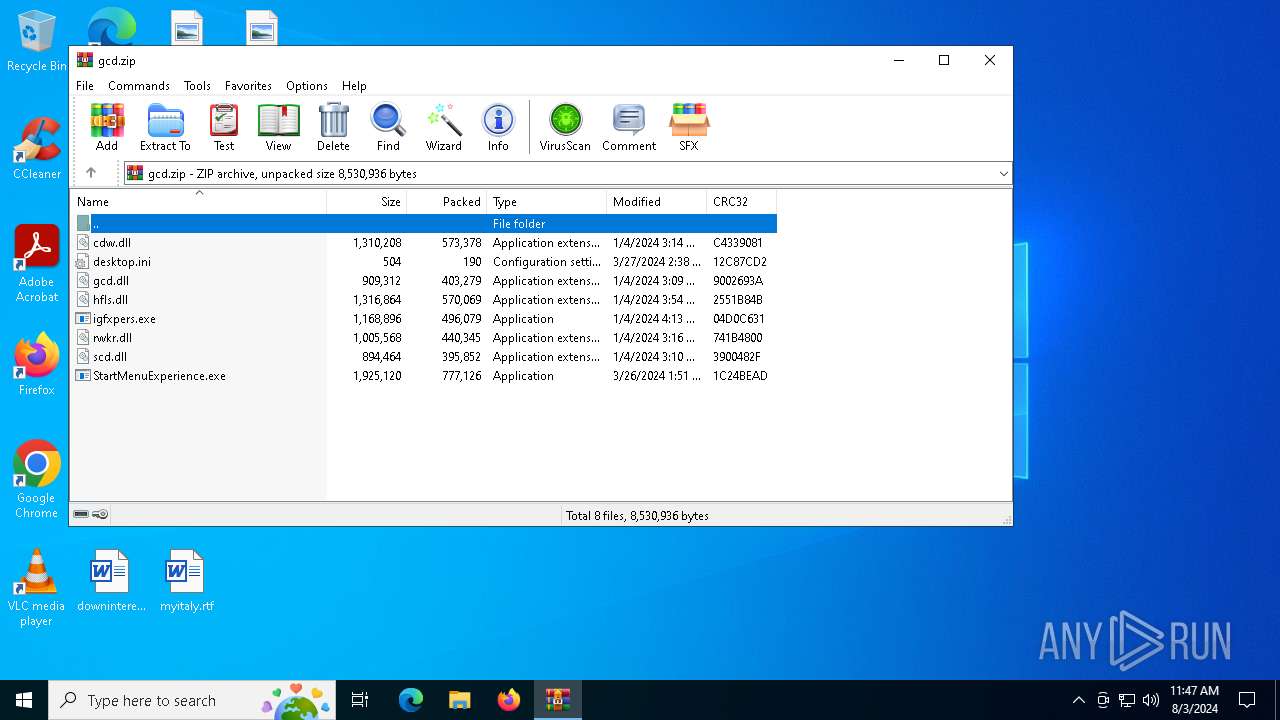
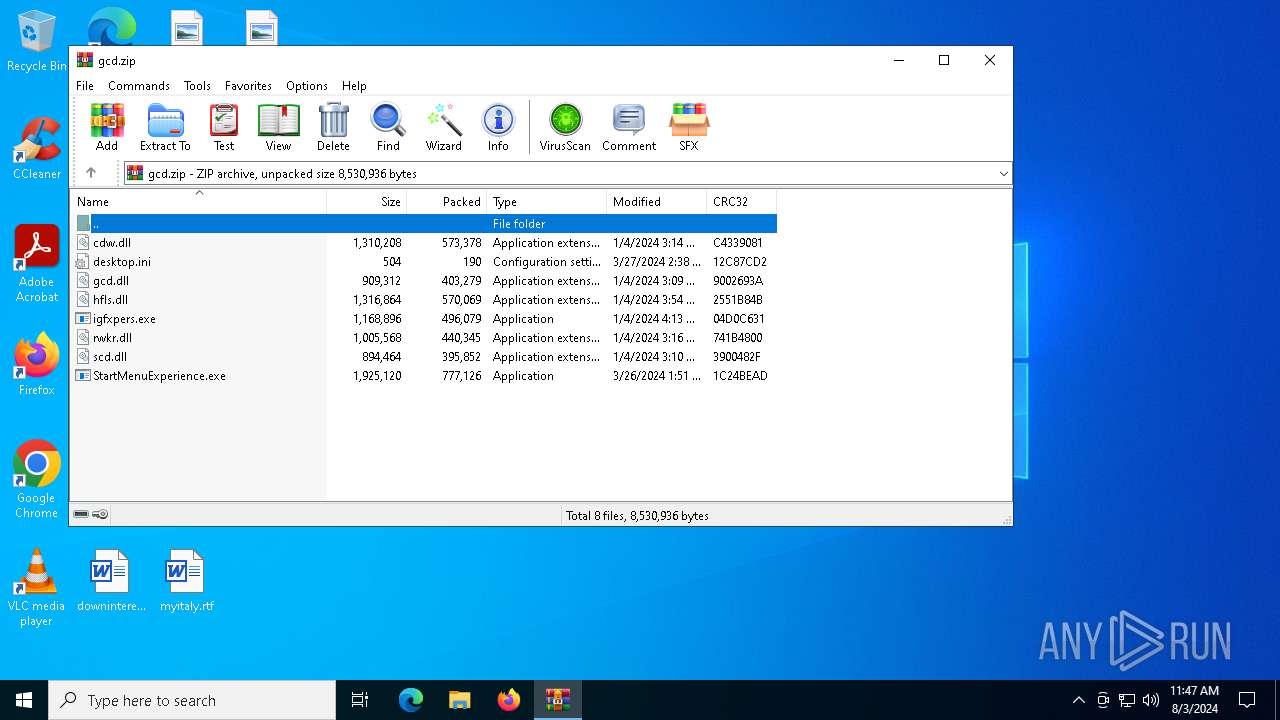
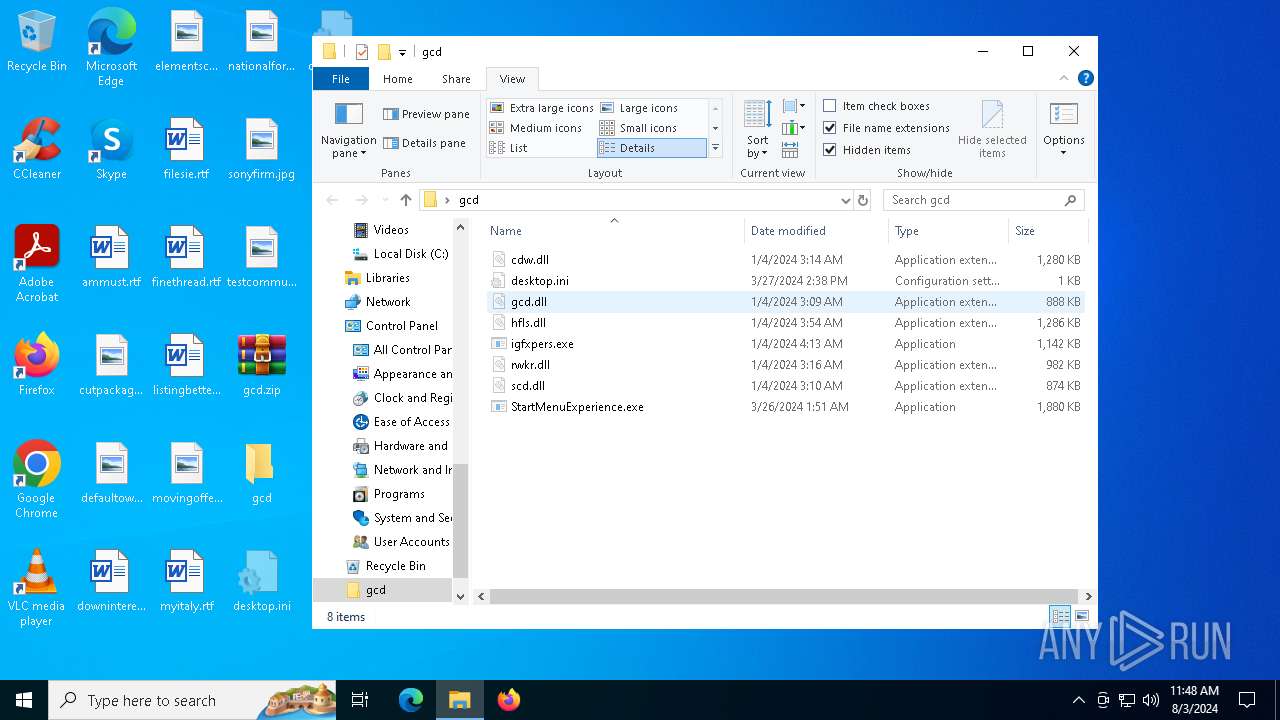
| File name: | gcd.zip |
| Full analysis: | https://app.any.run/tasks/2d37d85a-2f6b-4438-b1bb-da3a5576cf47 |
| Verdict: | Malicious activity |
| Analysis date: | August 03, 2024, 11:47:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
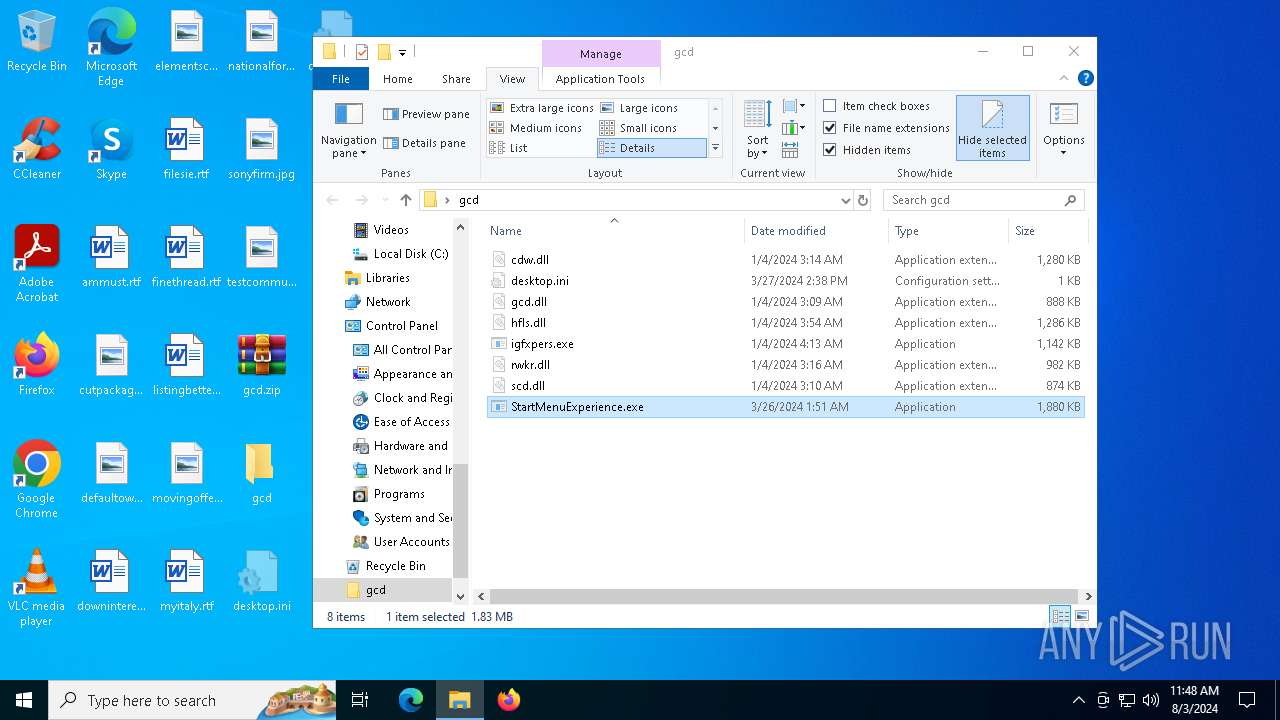
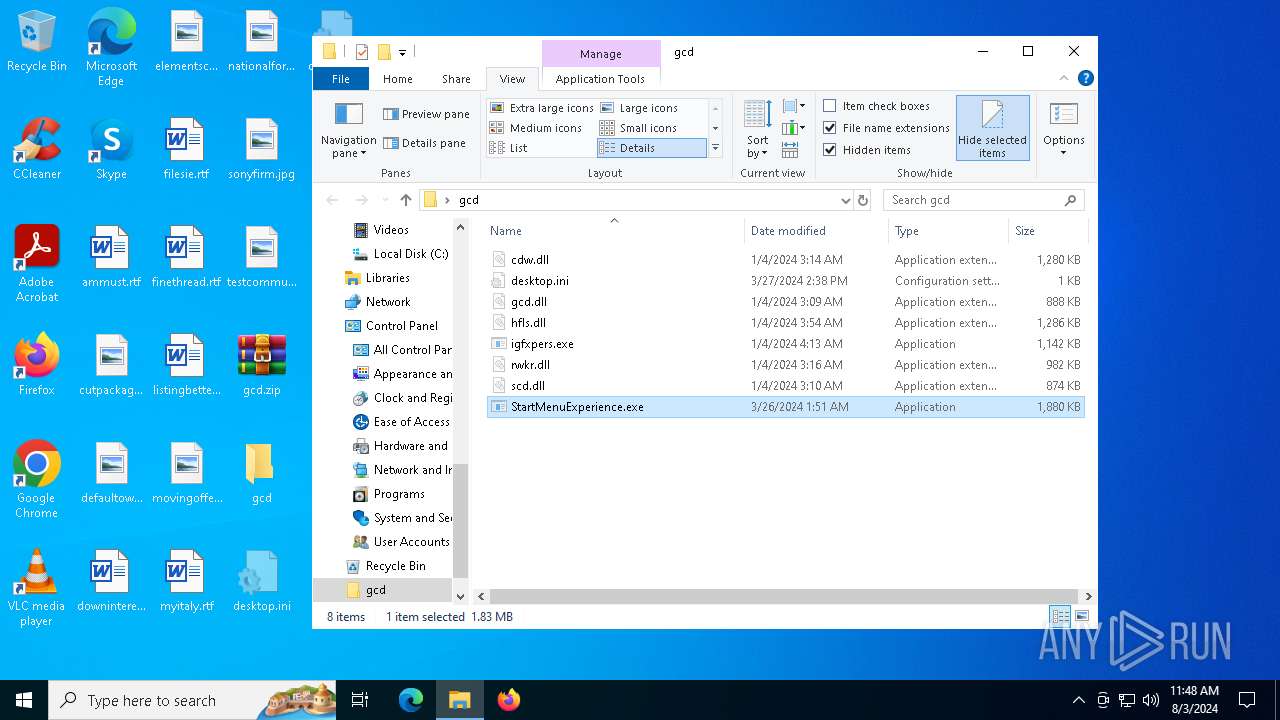
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 18C5826A5ABF8A39CA37EAF0F08F572C |
| SHA1: | C9004E1DF080CB434EF83A92D8699C1F16A75E16 |
| SHA256: | E72F2F9A7D3C6C2958852E972CD49D9F3B0531E66A1A5351E89A75DD03784217 |
| SSDEEP: | 98304:ZvJsYVVStEKY6arY64SZA/cCNGsKaxk11O7Kbl+BxaEAH55TWwpyMJ9lr96Ghmsm:WBMhnT58 |
MALICIOUS
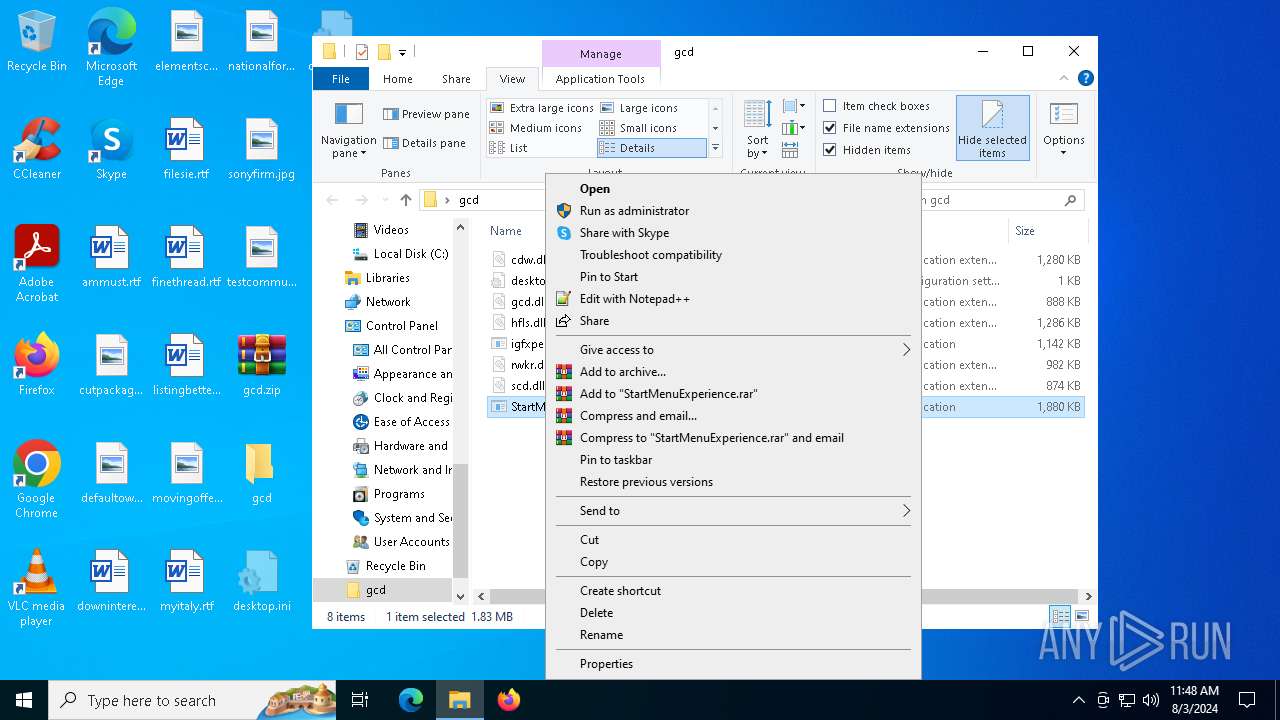
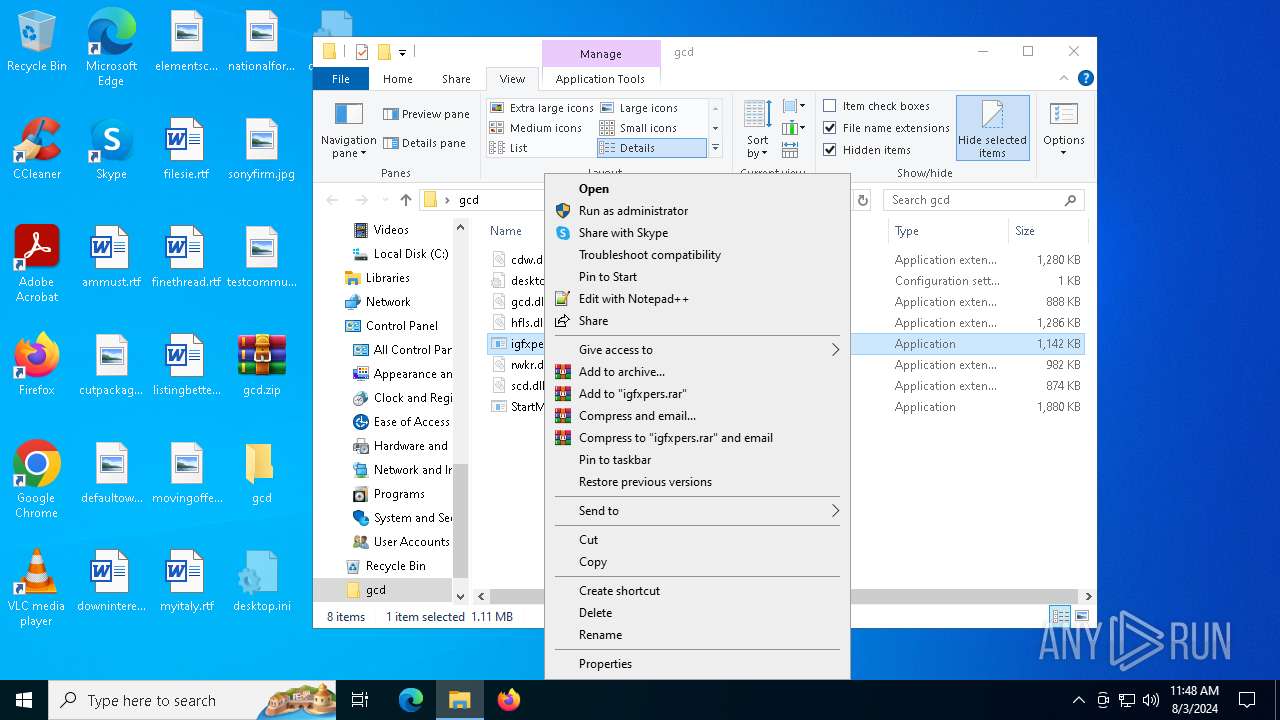
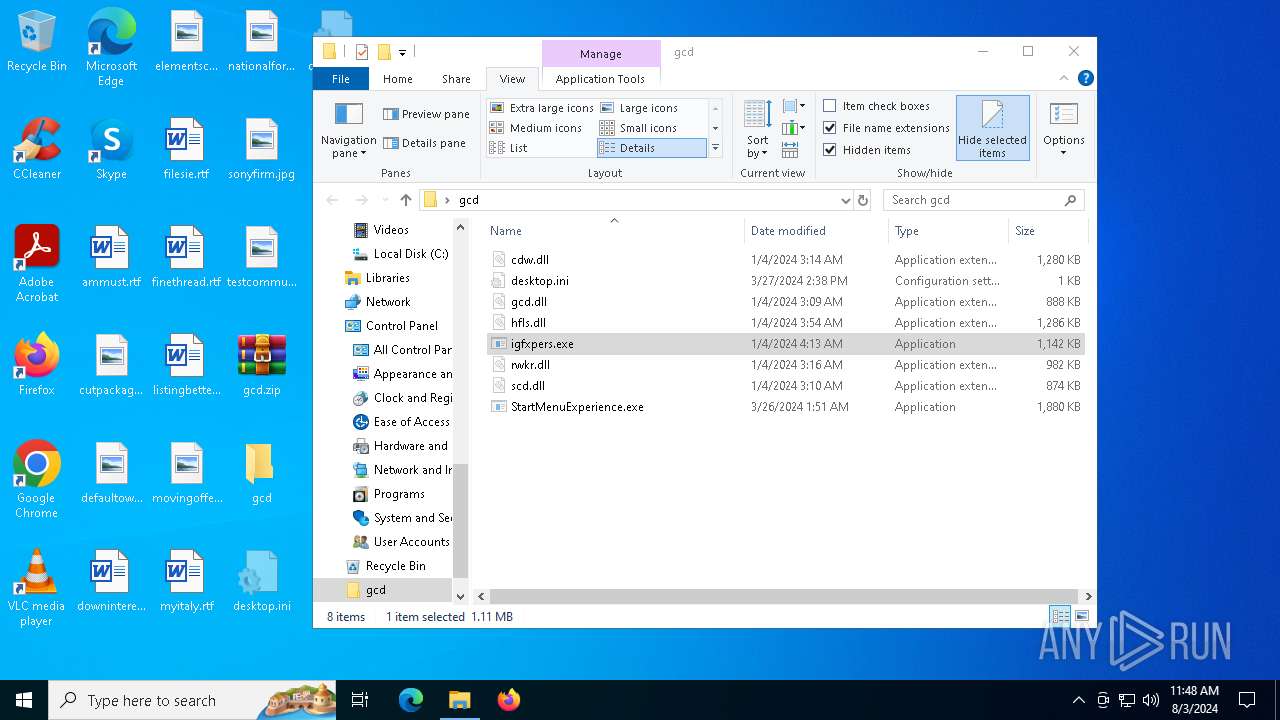
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6452)
Create files in the Startup directory
- StartMenuExperience.exe (PID: 6416)
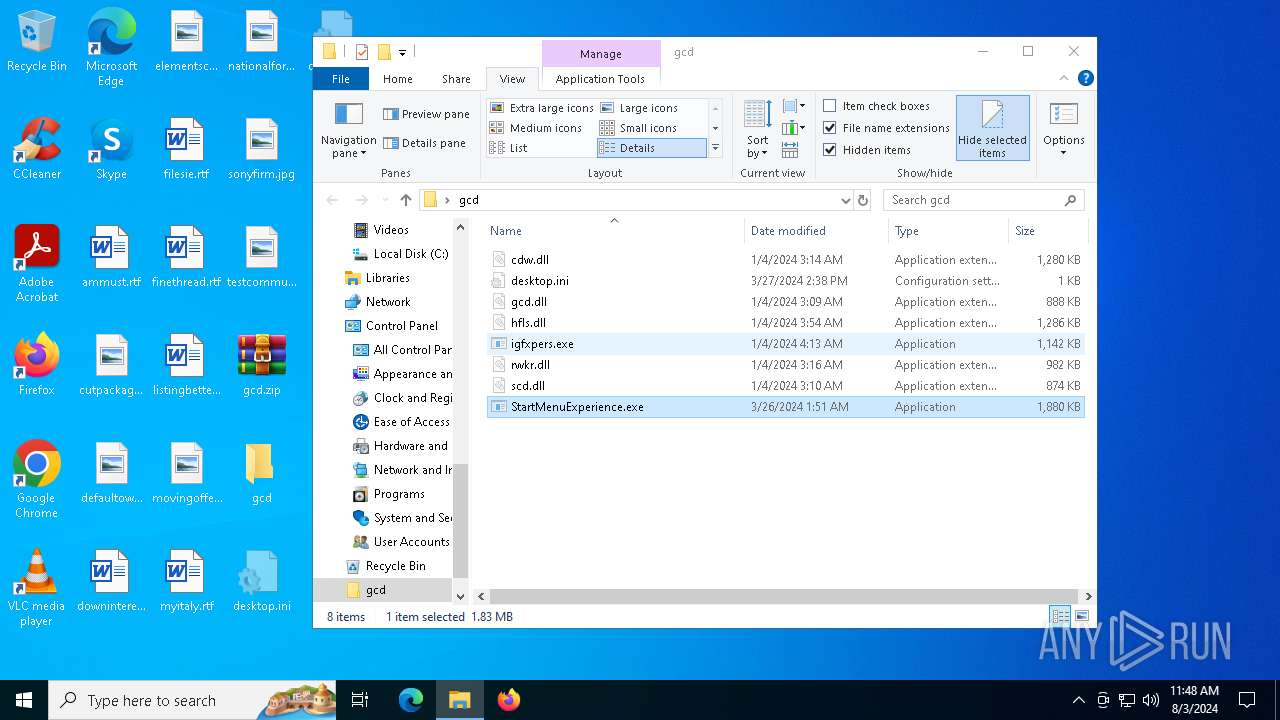
Changes the autorun value in the registry
- igfxpers.exe (PID: 6336)
SUSPICIOUS
Executes application which crashes
- igfxpers.exe (PID: 4232)
Uses ATTRIB.EXE to modify file attributes
- igfxpers.exe (PID: 6336)
Write to the desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 6452)
INFO
Checks supported languages
- StartMenuExperience.exe (PID: 6416)
- igfxpers.exe (PID: 4232)
- StartMenuExperience.exe (PID: 304)
- igfxpers.exe (PID: 6336)
Manual execution by a user
- StartMenuExperience.exe (PID: 6416)
- igfxpers.exe (PID: 4232)
- StartMenuExperience.exe (PID: 304)
- igfxpers.exe (PID: 6336)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6452)
Creates files or folders in the user directory
- StartMenuExperience.exe (PID: 6416)
Reads the computer name
- StartMenuExperience.exe (PID: 304)
- StartMenuExperience.exe (PID: 6416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:01:04 03:14:18 |
| ZipCRC: | 0xc4339081 |
| ZipCompressedSize: | 573378 |
| ZipUncompressedSize: | 1310208 |
| ZipFileName: | cdw.dll |
Total processes
157
Monitored processes
23
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Users\admin\Desktop\gcd\StartMenuExperience.exe" | C:\Users\admin\Desktop\gcd\StartMenuExperience.exe | explorer.exe | ||||||||||||
User: admin Company: KC Softwares Integrity Level: HIGH Description: Start Menu Experience Host Version: 1.21.0.43 Modules
| |||||||||||||||
| 1168 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | StartMenuExperience.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1372 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | attrib.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1680 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2336 | attrib +h +s C:\Users\admin\Desktop\gcd\gcd.dll | C:\Windows\SysWOW64\attrib.exe | — | igfxpers.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | StartMenuExperience.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3904 | attrib +h +s C:\Users\admin\Desktop\gcd\scd.dll | C:\Windows\SysWOW64\attrib.exe | — | igfxpers.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4060 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | igfxpers.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4084 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 4232 -s 324 | C:\Windows\SysWOW64\WerFault.exe | — | igfxpers.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4232 | "C:\Users\admin\Desktop\gcd\igfxpers.exe" | C:\Users\admin\Desktop\gcd\igfxpers.exe | explorer.exe | ||||||||||||
User: admin Company: Intel Corporation Integrity Level: MEDIUM Description: persistence Module Exit code: 3221225477 Version: 8.15.10.2900 Modules
| |||||||||||||||
Total events
6 259
Read events
6 238
Write events
21
Delete events
0
Modification events
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\gcd.zip | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\gcd | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
7
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6416 | StartMenuExperience.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\winhost.lnk | binary | |
MD5:9CC012CC6785765ED699851C2DCA05C8 | SHA256:0EA44BAA8341CF3CA41071CDE51E989BC73BE5D17424A9CC2DB844566DA4F4F4 | |||
| 6452 | WinRAR.exe | C:\Users\admin\Desktop\gcd\hfls.dll | executable | |
MD5:A580D28C592CA110C1883F7483F5A428 | SHA256:E75D0613BB55948520BFD284D11372B56F61CB9DD5ED69215C1A6D1A6EDECB4F | |||
| 6452 | WinRAR.exe | C:\Users\admin\Desktop\gcd\StartMenuExperience.exe | executable | |
MD5:8E4F4B994223BCCAE1CE28D2EA237687 | SHA256:22F587FF7023840A37266D2E9F0EF8FCDFB83334909D76D7F6A3100403B696CB | |||
| 6452 | WinRAR.exe | C:\Users\admin\Desktop\gcd\cdw.dll | executable | |
MD5:10EA24656553234CDB922E66C505872F | SHA256:29793C62D0B2CAA37ABD8926891F27C80978583AB4E600C0397EA4D45F9084E0 | |||
| 6452 | WinRAR.exe | C:\Users\admin\Desktop\gcd\gcd.dll | executable | |
MD5:F4A5D926704E06339E5A72CD3E47A8CA | SHA256:2FC3D3914184519A76AB9B3B6FC8A1F96A0145E1BD144D6FE89EF313857C103C | |||
| 6452 | WinRAR.exe | C:\Users\admin\Desktop\gcd\desktop.ini | text | |
MD5:06E8F7E6DDD666DBD323F7D9210F91AE | SHA256:8301E344371B0753D547B429C5FE513908B1C9813144F08549563AC7F4D7DA68 | |||
| 6452 | WinRAR.exe | C:\Users\admin\Desktop\gcd\rwkr.dll | executable | |
MD5:831E5610DB8178F69B12D70712F09135 | SHA256:E0E006775DD43369541042DB06C754E099DB4DDF19C15B1B5CD31AE811AFD01C | |||
| 6452 | WinRAR.exe | C:\Users\admin\Desktop\gcd\igfxpers.exe | executable | |
MD5:8D07234493EB76F8A26866E2AA690AAB | SHA256:7C9205B4E4AFAD45AAFDF883B1EE597D63CEB13B8134288F239CF97E8134DA65 | |||
| 6452 | WinRAR.exe | C:\Users\admin\Desktop\gcd\scd.dll | executable | |
MD5:9D4C42E03D830CAE0AC929FFD7817B7C | SHA256:ED7E877085C91DDA1BC82F78F2D5AED5826FBD487B39D31B764E30D91BFFB47F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
36
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3812 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6780 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6832 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2472 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4016 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5336 | SearchApp.exe | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3812 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |