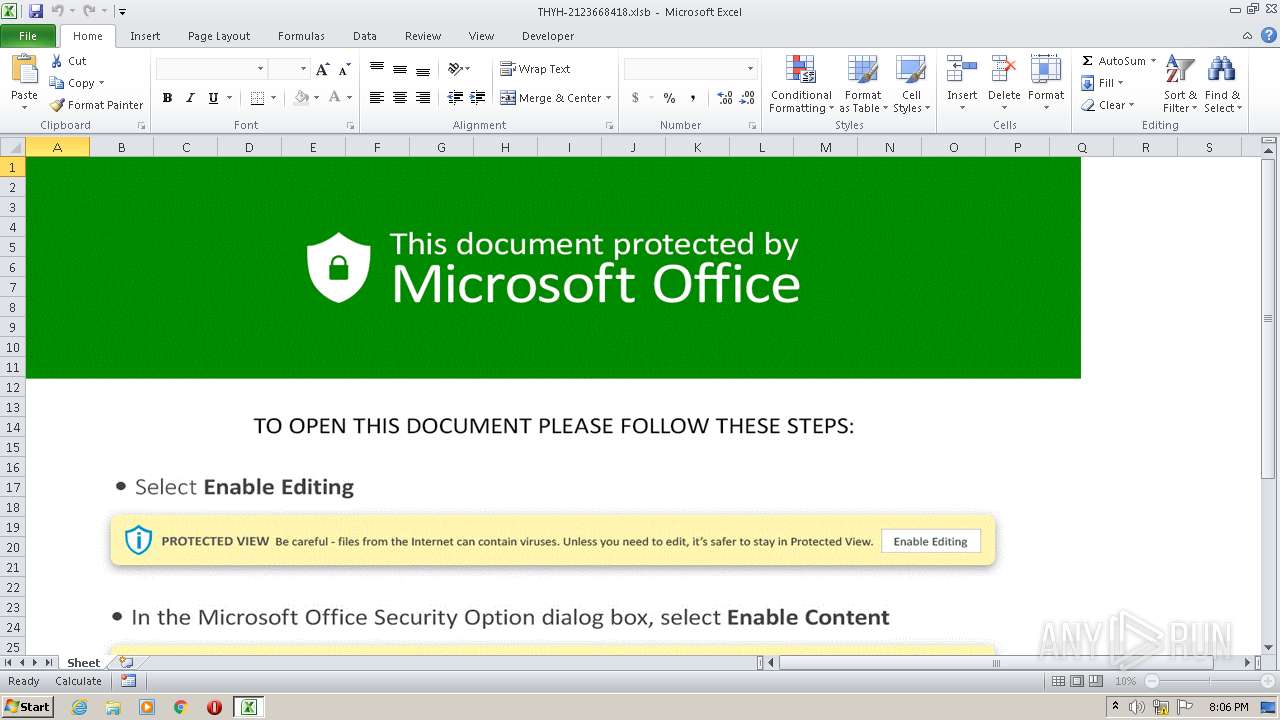
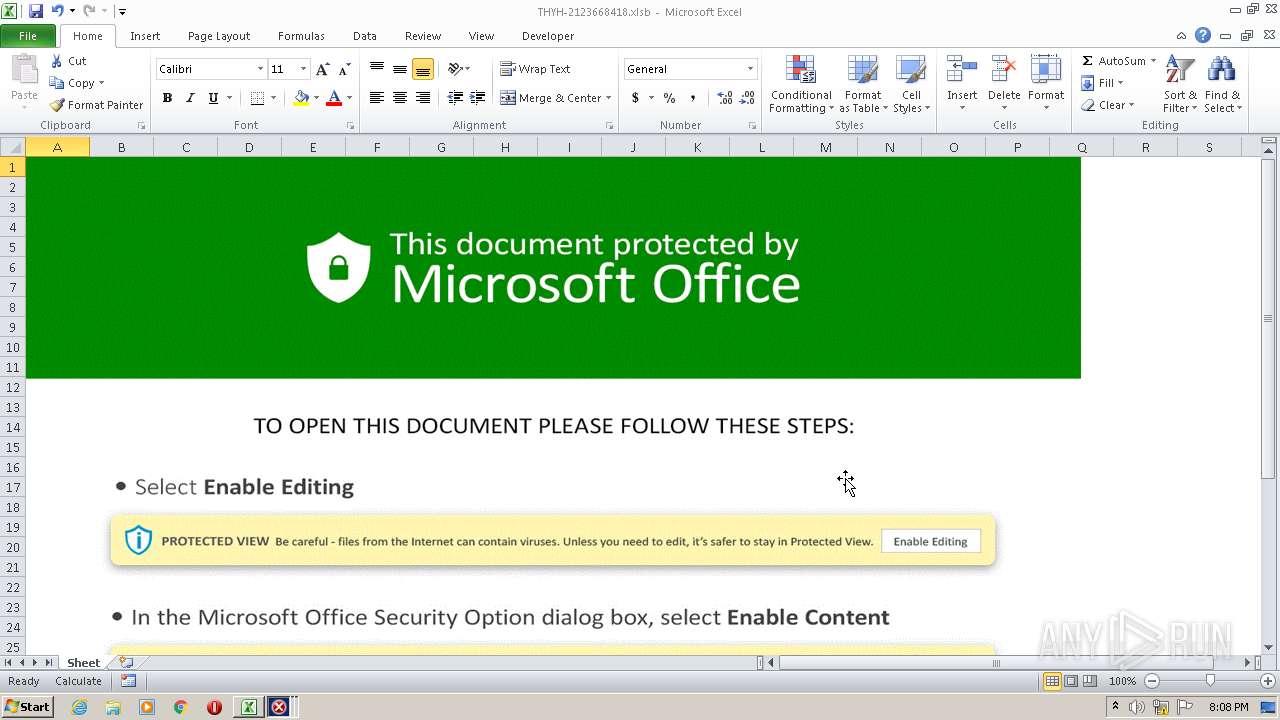
| File name: | THYH-2123668418.xlsb |
| Full analysis: | https://app.any.run/tasks/cfbd2e7a-fc40-4c20-9a15-277099158f5b |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 20:06:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | 0ACEC62B3D5269314D8E84F072CD4A86 |
| SHA1: | 498F8B30C0C55B22FBFB26CC481A9D667E2F0063 |
| SHA256: | E724D88853E29F5A71B81633E459AD7CC5F766DBC1B66E5C5D82BA5DE2DC7B04 |
| SSDEEP: | 3072:M5ZQF483ux6KoT/jki1XCqRRAcQnEWzY249:M5dsrkmDRicQnE7249 |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- EXCEL.EXE (PID: 2892)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2892)
SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- EXCEL.EXE (PID: 2892)
- explorer.exe (PID: 1176)
Checks Windows Trust Settings
- EXCEL.EXE (PID: 2892)
Reads settings of System Certificates
- EXCEL.EXE (PID: 2892)
Checks supported languages
- EXCEL.EXE (PID: 2892)
- regsvr32.exe (PID: 492)
- regsvr32.exe (PID: 3824)
- regsvr32.exe (PID: 1028)
- explorer.exe (PID: 1176)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2892)
Manual execution by user
- explorer.exe (PID: 1176)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlsx | | | Excel Microsoft Office Open XML Format document (61.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (31.5) |
| .zip | | | ZIP compressed archive (7.2) |
EXIF
XML
| AppVersion: | 16.03 |
|---|---|
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| Company: | - |
| TitlesOfParts: |
|
| HeadingPairs: |
|
| ScaleCrop: | No |
| DocSecurity: | None |
| Application: | Microsoft Excel |
| ModifyDate: | 2022:01:24 07:16:50Z |
| CreateDate: | 2015:06:05 18:19:34Z |
| LastModifiedBy: | Admin |
XMP
| Creator: | Admin |
|---|
ZIP
| ZipFileName: | [Content_Types].xml |
|---|---|
| ZipUncompressedSize: | 4405 |
| ZipCompressedSize: | 632 |
| ZipCRC: | 0x43fbdf7d |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0006 |
| ZipRequiredVersion: | 20 |
Total processes
43
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 492 | regsvr32 C:\Busta\tevc.ocx | C:\Windows\system32\regsvr32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1028 | regsvr32 C:\Busta\tevd.ocx | C:\Windows\system32\regsvr32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1176 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2892 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3824 | regsvr32 C:\Busta\teva.ocx | C:\Windows\system32\regsvr32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 093
Read events
6 005
Write events
77
Delete events
11
Modification events
| (PID) Process: | (2892) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | 5$( |
Value: 352428004C0B0000010000000000000000000000 | |||
| (PID) Process: | (2892) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2892) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2892) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2892) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2892) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2892) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2892) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2892) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2892) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
6
Text files
0
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR3435.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C0A419DBBA361754D896A8615DC53C0F | binary | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\377E6729DE07B96E9E4BCADBF4AF95C4 | der | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C0A419DBBA361754D896A8615DC53C0F | der | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\016041D287FF4A0891BC95A872570616 | der | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\377E6729DE07B96E9E4BCADBF4AF95C4 | binary | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\016041D287FF4A0891BC95A872570616 | binary | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
6
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2892 | EXCEL.EXE | GET | 200 | 23.45.105.185:80 | http://x1.c.lencr.org/ | NL | der | 717 b | whitelisted |
2892 | EXCEL.EXE | GET | 200 | 23.32.238.67:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgPSYN4i4BqqFZgzp5reUehpbg%3D%3D | US | der | 503 b | shared |
2892 | EXCEL.EXE | GET | 200 | 23.32.238.67:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgSDX2OTu2fH9YvZC%2FO%2BSv8n2A%3D%3D | US | der | 503 b | shared |
2892 | EXCEL.EXE | GET | 200 | 13.107.4.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7aa8bcb365a0a8cf | US | compressed | 4.70 Kb | whitelisted |
2892 | EXCEL.EXE | GET | 200 | 23.32.238.67:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgMEewGPViU8xx8lvh0jhiJ%2BuA%3D%3D | US | der | 503 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2892 | EXCEL.EXE | 192.185.141.13:443 | pakunolaschool.com | CyrusOne LLC | US | unknown |
2892 | EXCEL.EXE | 50.87.253.11:443 | elimatlacomulco.com | Unified Layer | US | suspicious |
2892 | EXCEL.EXE | 192.254.234.248:443 | keltexfinancial.com | Unified Layer | US | unknown |
2892 | EXCEL.EXE | 23.45.105.185:80 | x1.c.lencr.org | Akamai International B.V. | NL | unknown |
2892 | EXCEL.EXE | 23.32.238.67:80 | r3.o.lencr.org | XO Communications | US | unknown |
2892 | EXCEL.EXE | 13.107.4.50:80 | ctldl.windowsupdate.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pakunolaschool.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
elimatlacomulco.com |
| unknown |
keltexfinancial.com |
| unknown |