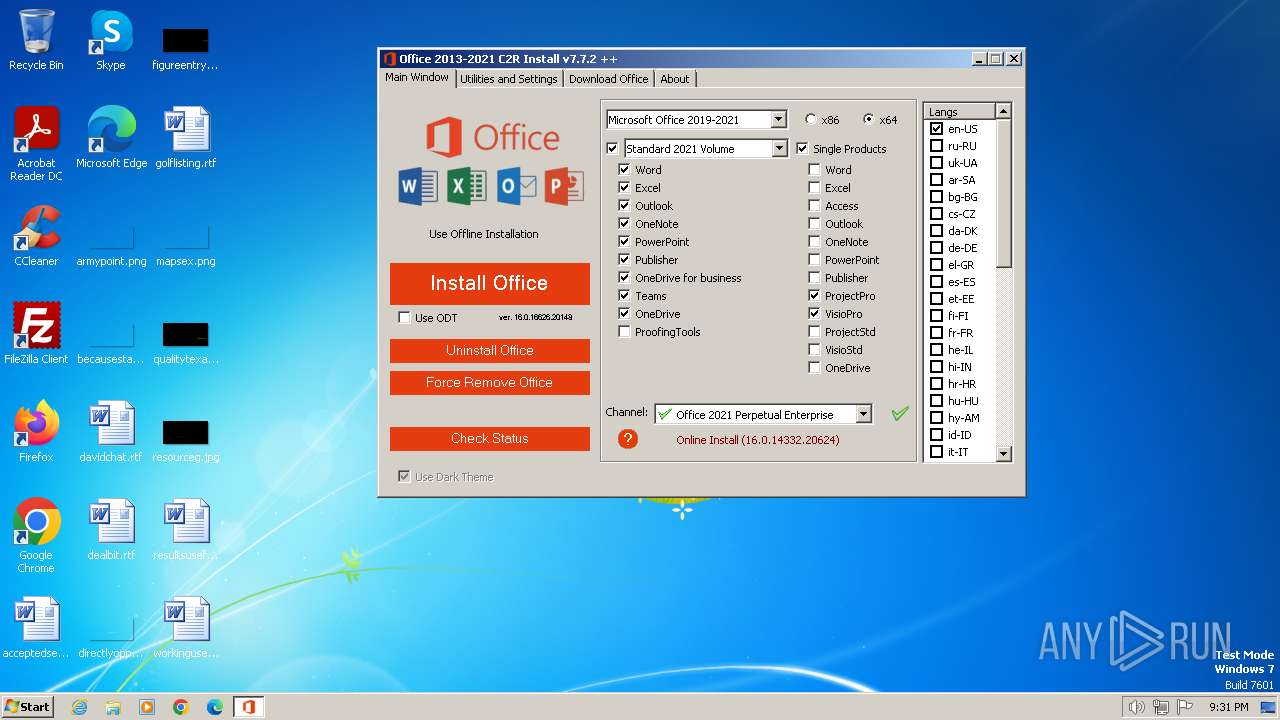
| File name: | OInstall.exe |
| Full analysis: | https://app.any.run/tasks/d6f32fb0-4911-4206-a090-962cfe4b112f |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2024, 21:30:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 209635421416545CB239F7484909FCF8 |
| SHA1: | 850FB53685BC7E70FE267AAED72F45AE7589EE03 |
| SHA256: | E71D9DAE0AE73CA4950FD14CC868DE8FFDC25985C93B033994631271C74C98E7 |
| SSDEEP: | 196608:O09sOIeV8WTmnAyv+T9hq6F7ZPXLmohRlQ:jsOIOTmnPv+xhqcZPXtlQ |
MALICIOUS
Drops the executable file immediately after the start
- OInstall.exe (PID: 2268)
- files.dat (PID: 1632)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- OInstall.exe (PID: 2268)
Executable content was dropped or overwritten
- OInstall.exe (PID: 2268)
- files.dat (PID: 1632)
The executable file from the user directory is run by the CMD process
- files.dat (PID: 1632)
Starts CMD.EXE for commands execution
- OInstall.exe (PID: 2268)
Uses REG/REGEDIT.EXE to modify registry
- OInstall.exe (PID: 2268)
Starts application with an unusual extension
- cmd.exe (PID: 480)
The process drops C-runtime libraries
- files.dat (PID: 1632)
Process drops legitimate windows executable
- files.dat (PID: 1632)
- OInstall.exe (PID: 2268)
Probably download files using WebClient
- OInstall.exe (PID: 2268)
Starts POWERSHELL.EXE for commands execution
- OInstall.exe (PID: 2268)
Reads the Internet Settings
- powershell.exe (PID: 3128)
- powershell.exe (PID: 1556)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 1584)
The Powershell connects to the Internet
- powershell.exe (PID: 1556)
- powershell.exe (PID: 1584)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 3128)
Unusual connection from system programs
- powershell.exe (PID: 2852)
- powershell.exe (PID: 1584)
- powershell.exe (PID: 1556)
- powershell.exe (PID: 3128)
INFO
Checks supported languages
- OInstall.exe (PID: 2268)
- files.dat (PID: 1632)
Reads the computer name
- OInstall.exe (PID: 2268)
Reads Environment values
- OInstall.exe (PID: 2268)
Create files in a temporary directory
- OInstall.exe (PID: 2268)
- files.dat (PID: 1632)
- expand.exe (PID: 1784)
- expand.exe (PID: 240)
- expand.exe (PID: 3016)
Creates files in the program directory
- OInstall.exe (PID: 2268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (76) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.6) |
| .exe | | | Generic Win/DOS Executable (5.6) |
| .exe | | | DOS Executable Generic (5.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:09:15 06:09:08+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 15802368 |
| InitializedDataSize: | 90112 |
| UninitializedDataSize: | 16822272 |
| EntryPoint: | 0x1f1db90 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.7.2.0 |
| ProductVersionNumber: | 7.7.2.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
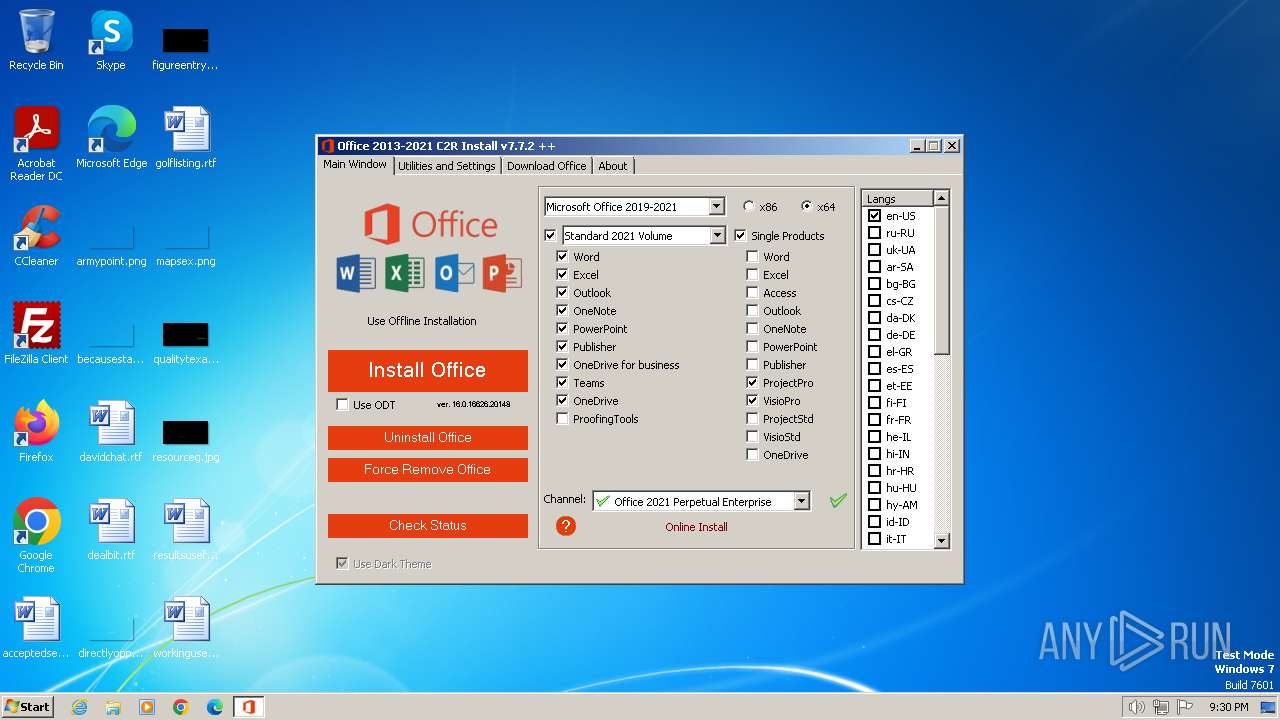
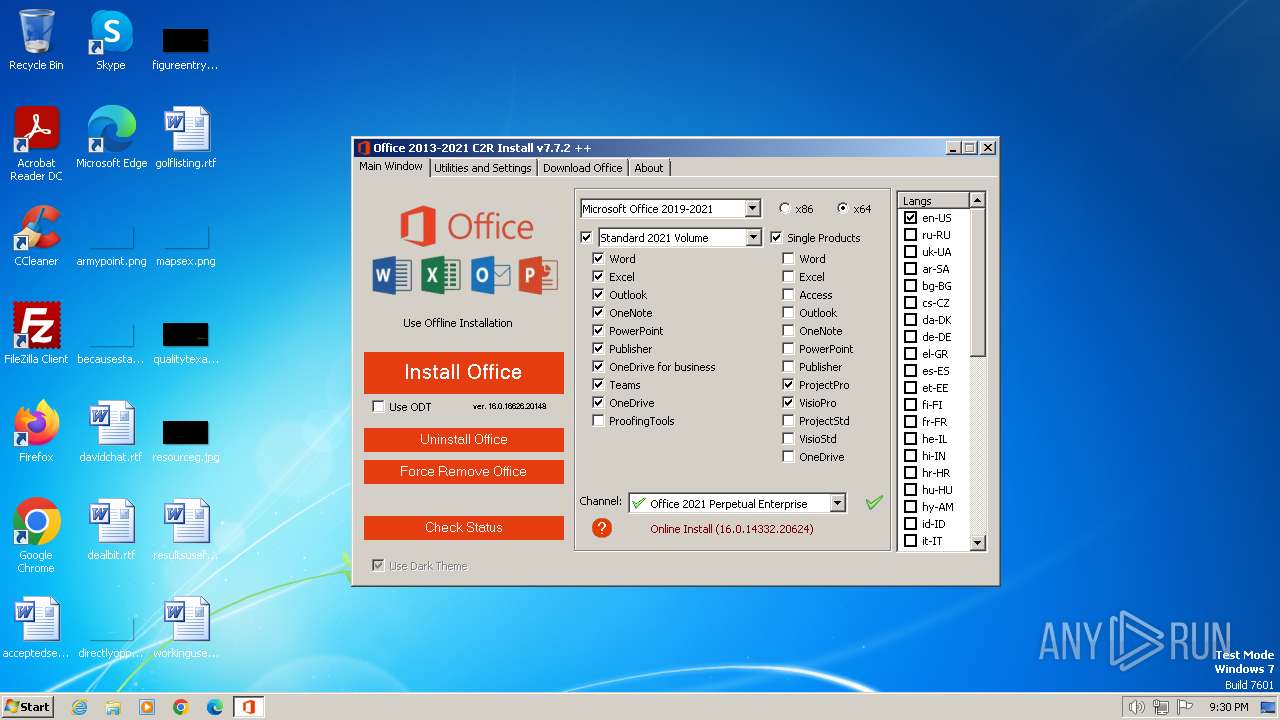
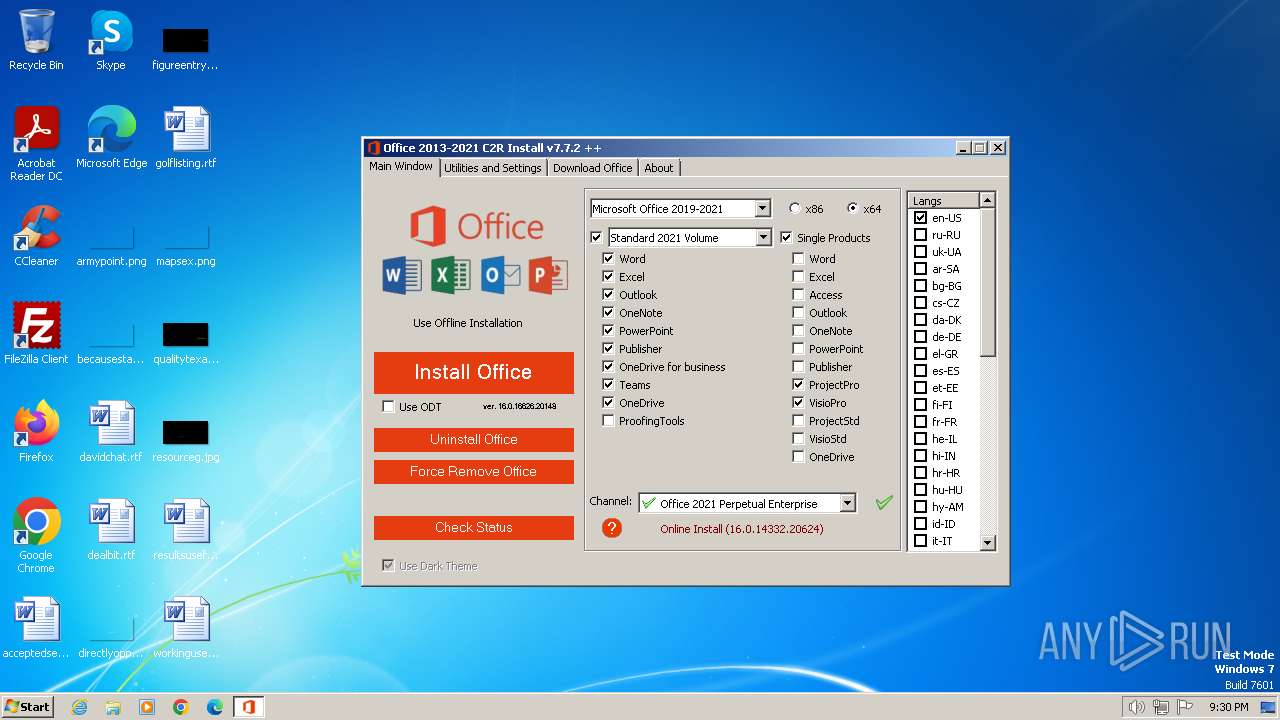
| ProductName: | Office 2013-2021 C2R Install |
| FileDescription: | Office 2013-2021 C2R Install |
Total processes
68
Monitored processes
18
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "expand" v32.cab -F:VersionDescriptor.xml C:\Users\admin\AppData\Local\Temp\over7247566 | C:\Windows\System32\expand.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: LZ Expansion Utility Exit code: 0 Version: 6.1.7601.24535 (win7sp1_ldr_escrow.191105-1059) Modules
| |||||||||||||||
| 480 | "C:\Windows\System32\cmd.exe" /D /c files.dat -y -pkmsauto | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1380 | "C:\Windows\System32\reg.exe" add "HKLM\SOFTWARE\Microsoft\Windows Script Host\Settings" /v Enabled /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1408 | "powershell" -command "& { Get-Content C:\Users\admin\AppData\Local\Temp\over177436\VersionDescriptor.xml | Set-Content -Encoding ASCII v32.txt } | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
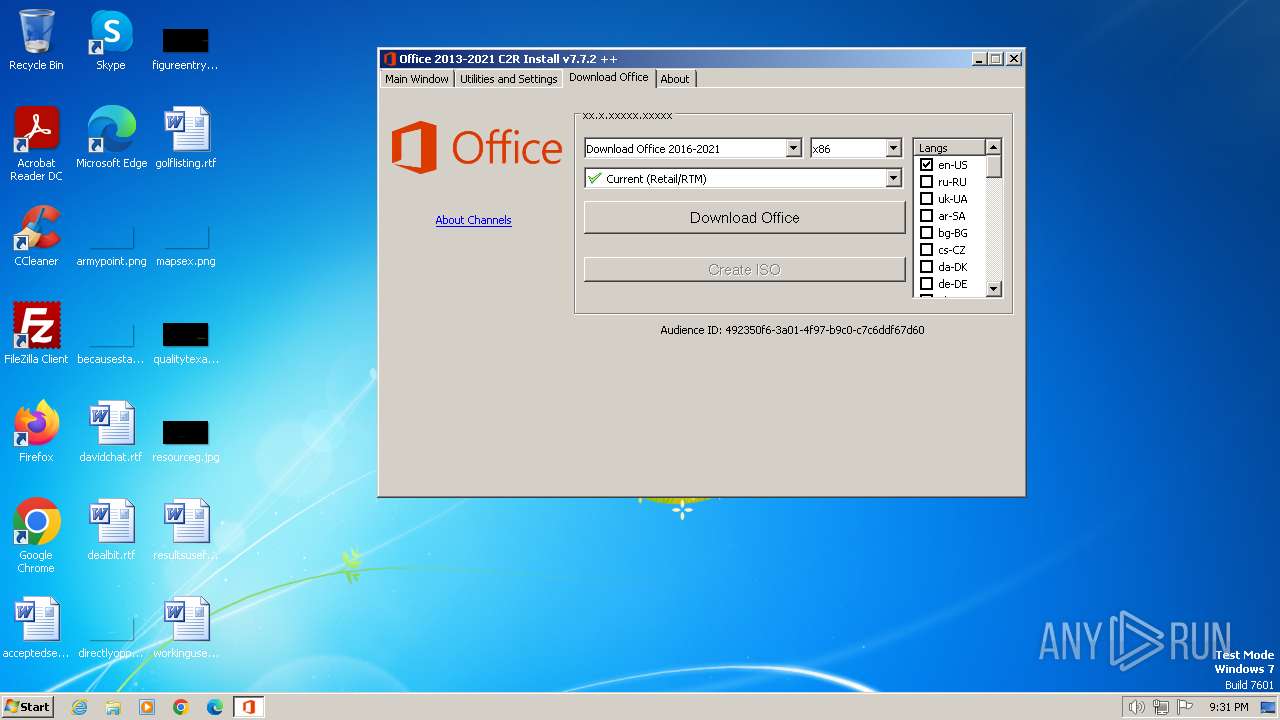
| 1556 | "powershell" -command "& { (New-Object Net.WebClient).DownloadFile('http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab', 'C:\Users\admin\AppData\Local\Temp\over7247566\v32.cab') }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | OInstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1584 | "powershell" -command "& { (New-Object Net.WebClient).DownloadFile('http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/v32.cab', 'C:\Users\admin\AppData\Local\Temp\over6591861\v32.cab') }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | OInstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1632 | files.dat -y -pkmsauto | C:\Users\admin\AppData\Local\Temp\files\files.dat | cmd.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Console SFX Exit code: 0 Version: 18.05 Modules
| |||||||||||||||
| 1656 | "powershell" -command "& { Get-Content C:\Users\admin\AppData\Local\Temp\over6591861\VersionDescriptor.xml | Set-Content -Encoding ASCII v32.txt } | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1784 | "expand" v32.cab -F:VersionDescriptor.xml C:\Users\admin\AppData\Local\Temp\over6591861 | C:\Windows\System32\expand.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: LZ Expansion Utility Exit code: 0 Version: 6.1.7601.24535 (win7sp1_ldr_escrow.191105-1059) Modules
| |||||||||||||||
| 2044 | "C:\Users\admin\AppData\Local\Temp\OInstall.exe" | C:\Users\admin\AppData\Local\Temp\OInstall.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Office 2013-2021 C2R Install Exit code: 3221226540 Modules
| |||||||||||||||
Total events
5 318
Read events
5 315
Write events
3
Delete events
0
Modification events
| (PID) Process: | (2268) OInstall.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
Executable files
7
Suspicious files
18
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2268 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\files\files.dat | executable | |
MD5:BB5569B15D68C10B7FF2D96B45825120 | SHA256:4E3B13B56BEC0E41778E6506430282BBBD75CCAA600FD4B645CE37DD95B44C8E | |||
| 1584 | powershell.exe | C:\Users\admin\AppData\Local\Temp\over6591861\v32.cab | compressed | |
MD5:E9E084E4196FEBA820AB0F51E47AA2C9 | SHA256:9453C7D0E5A2015825C909EA53603D7D6111B4F2A3C346CE36493A86715A4D0F | |||
| 1632 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x86\msvcr100.dll | executable | |
MD5:BF38660A9125935658CFA3E53FDC7D65 | SHA256:60C06E0FA4449314DA3A0A87C1A9D9577DF99226F943637E06F61188E5862EFA | |||
| 2268 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\files\setup.exe | executable | |
MD5:42E491A02ADA4560F31FFA389A12F8A8 | SHA256:AF196EECB1FBEC2BE1F3088E755AF97A27F04EA4A744DA39C3715832AC4D8FF7 | |||
| 1632 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x64\msvcr100.dll | executable | |
MD5:DF3CA8D16BDED6A54977B30E66864D33 | SHA256:1D1A1AE540BA132F998D60D3622F0297B6E86AE399332C3B47462D7C0F560A36 | |||
| 1632 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x86\cleanospp.exe | executable | |
MD5:98821A7A5737D656633D10A3AFB724BD | SHA256:04BA4487F95290E0B0557B44300C18F637FBAF0872EE96E3111013B8A1539F25 | |||
| 2268 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\files\Configure.xml | text | |
MD5:F693E4FB8D3907E6CC44A34E1CC87296 | SHA256:CDCD3FA3CB1EBFAFC98273AE52632F80B95CB9D25933EE1C7D2FDEC640B264D0 | |||
| 1584 | powershell.exe | C:\Users\admin\AppData\Local\Temp\oj2xfofc.y44.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1584 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 1632 | files.dat | C:\Users\admin\AppData\Local\Temp\files\Uninstall.xml | text | |
MD5:364F86F97324EA82FE0D142CD01CF6DD | SHA256:09D5B42140BAB13165BA97FBD0E77792304C3C93555BE02C3DCE21A7A69C66DD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
8
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1584 | powershell.exe | GET | 200 | 152.199.21.175:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/v32.cab | unknown | compressed | 10.9 Kb | unknown |
1556 | powershell.exe | GET | 200 | 152.199.21.175:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab | unknown | compressed | 11.2 Kb | unknown |
3128 | powershell.exe | GET | — | 152.199.21.175:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20624/i320.cab | unknown | — | — | unknown |
2852 | powershell.exe | GET | 200 | 152.199.21.175:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/v32.cab | unknown | compressed | 10.9 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1584 | powershell.exe | 152.199.21.175:80 | officecdn.microsoft.com | EDGECAST | DE | whitelisted |
1556 | powershell.exe | 152.199.21.175:80 | officecdn.microsoft.com | EDGECAST | DE | whitelisted |
2852 | powershell.exe | 152.199.21.175:80 | officecdn.microsoft.com | EDGECAST | DE | whitelisted |
3128 | powershell.exe | 152.199.21.175:80 | officecdn.microsoft.com | EDGECAST | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officecdn.microsoft.com |
| whitelisted |