| File name: | file-info-install.exe |
| Full analysis: | https://app.any.run/tasks/4a18ebfd-0bc5-419c-8fca-83229bbd61e4 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2025, 05:31:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | E1D796049B0CB07856D9829B4763C461 |
| SHA1: | B50177A00BF5043A6645B89EB1A8FE0D4F0E0283 |
| SHA256: | E70482FED94CC60554074378836FC79512AEE92C5F2C6BC16A29EE3DADC3FC90 |
| SSDEEP: | 49152:sT+tPQkaVdF/8UAbmvpuDhhOcvtaHvAgsFp89mUrXpWUbBiQiwFNM53KIrtwYikz:ltPQ3/UNqUsWaPAg0eNrXp7NFNMBt3U0 |
MALICIOUS
Executing a file with an untrusted certificate
- highdpimfcx86.exe (PID: 5708)
- highdpimfcx86.exe (PID: 2148)
Changes the autorun value in the registry
- highdpimfcx86.exe (PID: 5708)
SUSPICIOUS
Reads Microsoft Outlook installation path
- file_info_.exe (PID: 304)
Reads security settings of Internet Explorer
- file-info-install.exe (PID: 1068)
- file_info_.exe (PID: 304)
- highdpimfcx86.exe (PID: 5708)
Creates a software uninstall entry
- file_info_.exe (PID: 304)
- highdpimfcx86.exe (PID: 5708)
Executable content was dropped or overwritten
- file_info_.exe (PID: 304)
- highdpimfcx86.exe (PID: 2148)
- highdpimfcx86.exe (PID: 5708)
Reads Internet Explorer settings
- file_info_.exe (PID: 304)
Process drops legitimate windows executable
- file_info_.exe (PID: 304)
- highdpimfcx86.exe (PID: 2148)
- highdpimfcx86.exe (PID: 5708)
- msiexec.exe (PID: 7392)
Starts a Microsoft application from unusual location
- highdpimfcx86.exe (PID: 5708)
- highdpimfcx86.exe (PID: 2148)
Application launched itself
- highdpimfcx86.exe (PID: 5708)
Executes as Windows Service
- VSSVC.exe (PID: 2792)
Searches for installed software
- dllhost.exe (PID: 3800)
- highdpimfcx86.exe (PID: 2148)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7392)
There is functionality for taking screenshot (YARA)
- highdpimfcx86.exe (PID: 2148)
INFO
Checks supported languages
- file-info-install.exe (PID: 1068)
- file_info_.exe (PID: 304)
- highdpimfcx86.exe (PID: 2148)
- highdpimfcx86.exe (PID: 5708)
- SearchApp.exe (PID: 5328)
- msiexec.exe (PID: 7392)
The sample compiled with english language support
- file-info-install.exe (PID: 1068)
- file_info_.exe (PID: 304)
- highdpimfcx86.exe (PID: 2148)
- msiexec.exe (PID: 7392)
Checks proxy server information
- file-info-install.exe (PID: 1068)
- file_info_.exe (PID: 304)
- highdpimfcx86.exe (PID: 5708)
- slui.exe (PID: 1044)
Create files in a temporary directory
- file-info-install.exe (PID: 1068)
- file_info_.exe (PID: 304)
- highdpimfcx86.exe (PID: 2148)
- highdpimfcx86.exe (PID: 5708)
Reads the computer name
- file-info-install.exe (PID: 1068)
- file_info_.exe (PID: 304)
- highdpimfcx86.exe (PID: 2148)
- highdpimfcx86.exe (PID: 5708)
- msiexec.exe (PID: 7392)
Process checks whether UAC notifications are on
- file_info_.exe (PID: 304)
Creates files in the program directory
- file_info_.exe (PID: 304)
- highdpimfcx86.exe (PID: 5708)
Reads the software policy settings
- file_info_.exe (PID: 304)
- SearchApp.exe (PID: 5328)
- highdpimfcx86.exe (PID: 5708)
- msiexec.exe (PID: 7392)
- slui.exe (PID: 1044)
Process checks computer location settings
- file_info_.exe (PID: 304)
- SearchApp.exe (PID: 5328)
- file-info-install.exe (PID: 1068)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5328)
- highdpimfcx86.exe (PID: 5708)
- msiexec.exe (PID: 7392)
Manual execution by a user
- chrome.exe (PID: 4156)
- OUTLOOK.EXE (PID: 7680)
Launching a file from a Registry key
- highdpimfcx86.exe (PID: 5708)
Application launched itself
- chrome.exe (PID: 4156)
Manages system restore points
- SrTasks.exe (PID: 2536)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7392)
Creates files or folders in the user directory
- highdpimfcx86.exe (PID: 5708)
- file_info_.exe (PID: 304)
The sample compiled with chinese language support
- msiexec.exe (PID: 7392)
The sample compiled with spanish language support
- msiexec.exe (PID: 7392)
The sample compiled with german language support
- msiexec.exe (PID: 7392)
Creates a software uninstall entry
- msiexec.exe (PID: 7392)
The sample compiled with Italian language support
- msiexec.exe (PID: 7392)
The sample compiled with russian language support
- msiexec.exe (PID: 7392)
The sample compiled with japanese language support
- msiexec.exe (PID: 7392)
The sample compiled with korean language support
- msiexec.exe (PID: 7392)
The sample compiled with french language support
- msiexec.exe (PID: 7392)
Reads Internet Explorer settings
- OUTLOOK.EXE (PID: 7680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (76) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.6) |
| .exe | | | Generic Win/DOS Executable (5.6) |
| .exe | | | DOS Executable Generic (5.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:07:09 11:26:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 917504 |
| InitializedDataSize: | 24576 |
| UninitializedDataSize: | 1892352 |
| EntryPoint: | 0x2ad9f0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
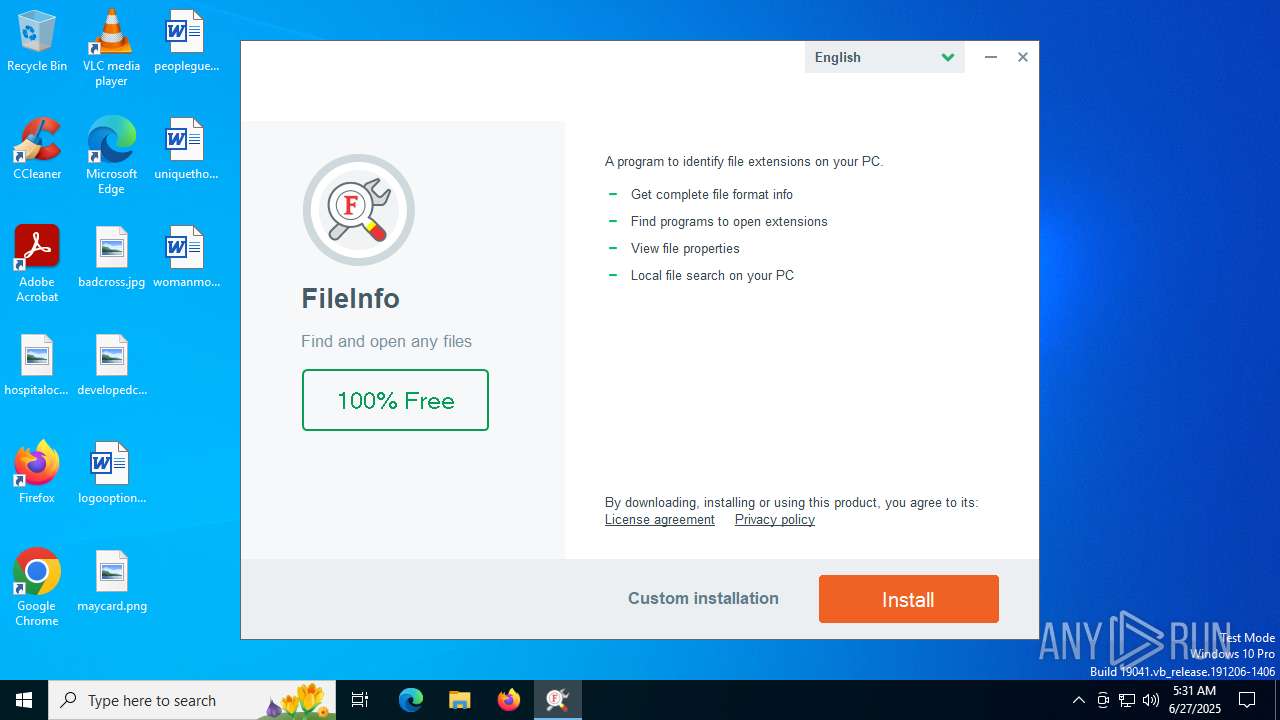
| CompanyName: | ROSTPAY LTD. |
| FileDescription: | FileInfo Installer |
| FileVersion: | 1.0.0.0 |
| InternalName: | FileInfo Installer.exe |
| LegalCopyright: | ROSTPAY LTD. All rights reserved. 2012 |
| OriginalFileName: | FileInfo Installer.exe |
| ProductName: | FileInfo |
| ProductVersion: | 1.0.0.0 |
Total processes
169
Monitored processes
23
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Users\admin\AppData\Local\Temp\file_info_.exe" /vid=6 /avastUrl="https://bits.avcdn.net/platform_WIN/productfamily_ANTIVIRUS/cookie_mmm_rsp_ppi_003_462_a" /PidDisko="2do" /ap="22" /fusionChannel="3" /installUrl="https://api.az-partners.net/apps/file-info/install?ap=22&offers=" /uninstallUrl="https://api.az-partners.net/apps/file-info/uninstall?ap=22" | C:\Users\admin\AppData\Local\Temp\file_info_.exe | file-info-install.exe | ||||||||||||
User: admin Company: ROSTPAY LTD. Integrity Level: HIGH Description: Install FileInfo Version: 3.4.0 Modules
| |||||||||||||||
| 1044 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | "C:\Users\admin\AppData\Local\Temp\file-info-install.exe" | C:\Users\admin\AppData\Local\Temp\file-info-install.exe | explorer.exe | ||||||||||||
User: admin Company: ROSTPAY LTD. Integrity Level: HIGH Description: FileInfo Installer Exit code: 97143864 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --field-trial-handle=3180,i,10406382404050236993,8938198464612695457,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3192 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 2148 | "C:\Users\admin\AppData\Local\Temp\FileInfo\highdpimfcx86.exe" /q /norestart -burn.unelevated BurnPipe.{302446FA-23FD-4576-B7AC-6D08495B1067} {91B78263-8350-4B8A-B53F-6C112C5B304F} 5708 | C:\Users\admin\AppData\Local\Temp\FileInfo\highdpimfcx86.exe | highdpimfcx86.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2013 Redistributable (x86) - 12.0.30501 Exit code: 0 Version: 12.0.30501.0 Modules
| |||||||||||||||
| 2536 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2792 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --extension-process --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=3496,i,10406382404050236993,8938198464612695457,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3588 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 3488 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --field-trial-handle=2416,i,10406382404050236993,8938198464612695457,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=2432 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 3800 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
30 810
Read events
29 733
Write events
990
Delete events
87
Modification events
| (PID) Process: | (304) file_info_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (304) file_info_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (304) file_info_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (304) file_info_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\FileInfo |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\FileInfo\FileInfoUninstaller.exe | |||
| (PID) Process: | (304) file_info_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\FileInfo |
| Operation: | write | Name: | DisplayName |
Value: FileInfo | |||
| (PID) Process: | (304) file_info_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\FileInfo |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\FileInfo | |||
| (PID) Process: | (304) file_info_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\FileInfo |
| Operation: | write | Name: | Publisher |
Value: ROSTPAY LTD. | |||
| (PID) Process: | (304) file_info_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\FileInfo |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\FileInfo\FileInfoApp.exe | |||
| (PID) Process: | (304) file_info_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\FileInfo |
| Operation: | write | Name: | URLInfoAbout |
Value: https://www.file-info.ru/ | |||
| (PID) Process: | (304) file_info_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\FileInfo |
| Operation: | write | Name: | HelpLink |
Value: https://www.file-info.ru/how-to-delete.html | |||
Executable files
37
Suspicious files
157
Text files
147
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1068 | file-info-install.exe | C:\Users\admin\AppData\Local\Temp\file_info_.exe | — | |
MD5:— | SHA256:— | |||
| 304 | file_info_.exe | C:\Program Files (x86)\FileInfo\extupdater.rcc | — | |
MD5:— | SHA256:— | |||
| 1068 | file-info-install.exe | C:\Users\admin\AppData\Local\Temp\.txt | binary | |
MD5:00194F933FDCAC7C5A6EA6C95BE88C94 | SHA256:CF22E1D225B133AA7EB6617A96BFA28AF2404AD7FABA2845EB5B53A3448ACDF5 | |||
| 304 | file_info_.exe | C:\Program Files (x86)\FileInfo\Qt5Gui.dll | executable | |
MD5:309B7EB7F2E954129909E853E02A6915 | SHA256:97109E3DEB6B478F06621D60A0AF2228F7C36781E84B074C3CCCBF4F88C79B13 | |||
| 304 | file_info_.exe | C:\Users\admin\AppData\Local\Temp\FileInfo\highdpimfcx86.exe | executable | |
MD5:0FC525B6B7B96A87523DAA7A0013C69D | SHA256:A22895E55B26202EAE166838EDBE2EA6AAD00D7EA600C11F8A31EDE5CBCE2048 | |||
| 2148 | highdpimfcx86.exe | C:\Users\admin\AppData\Local\Temp\{f65db027-aff3-4070-886a-0d87064aabb1}\.ba1\thm.wxl | xml | |
MD5:FBFCBC4DACC566A3C426F43CE10907B6 | SHA256:70400F181D00E1769774FF36BCD8B1AB5FBC431418067D31B876D18CC04EF4CE | |||
| 304 | file_info_.exe | C:\Program Files (x86)\FileInfo\Qt5Network.dll | executable | |
MD5:7E1350A7C4166C98D6354CC05934490F | SHA256:488A19B6EAAC54DB8CDFD2CD5D25547F800B41CFC75B0FE95696D8BDA31FB841 | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:3A0FBE9AE67A5F9FF5138246765F5F5D | SHA256:EA741164AE04ADE5F1E4D5A10F499EF8D9A2A2C4C0D511223F427D229CF395B4 | |||
| 2148 | highdpimfcx86.exe | C:\Users\admin\AppData\Local\Temp\{f65db027-aff3-4070-886a-0d87064aabb1}\.ba1\license.rtf | text | |
MD5:1E47EE7B71B22488068343DF4CE30534 | SHA256:8518F0420972C1DBE8A323FFC6F57863AF0B80C6A3B27FD0C6FC9BDABB7E2D13 | |||
| 2148 | highdpimfcx86.exe | C:\Users\admin\AppData\Local\Temp\{f65db027-aff3-4070-886a-0d87064aabb1}\.ba1\thm.xml | xml | |
MD5:0056F10A42638EA8B4BEFC614741DDD6 | SHA256:6B1BA0DEA830E556A58C883290FAA5D49C064E546CBFCD0451596A10CC693F87 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
104
DNS requests
58
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1068 | file-info-install.exe | GET | 301 | 142.250.186.78:80 | http://google.com/ | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 104.18.20.213:80 | http://e5.c.lencr.org/84.crl | unknown | — | — | whitelisted |
2764 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5928 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5928 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6876 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1068 | file-info-install.exe | 142.250.186.78:80 | google.com | GOOGLE | US | whitelisted |
1068 | file-info-install.exe | 188.130.153.33:443 | file-info.ru | Rostpay Ltd | RU | suspicious |
764 | lsass.exe | 104.18.20.213:80 | e5.c.lencr.org | CLOUDFLARENET | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2764 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
file-info.ru |
| unknown |
e5.c.lencr.org |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1068 | file-info-install.exe | A Network Trojan was detected | ET MALWARE Rostpay Downloader User-Agent |