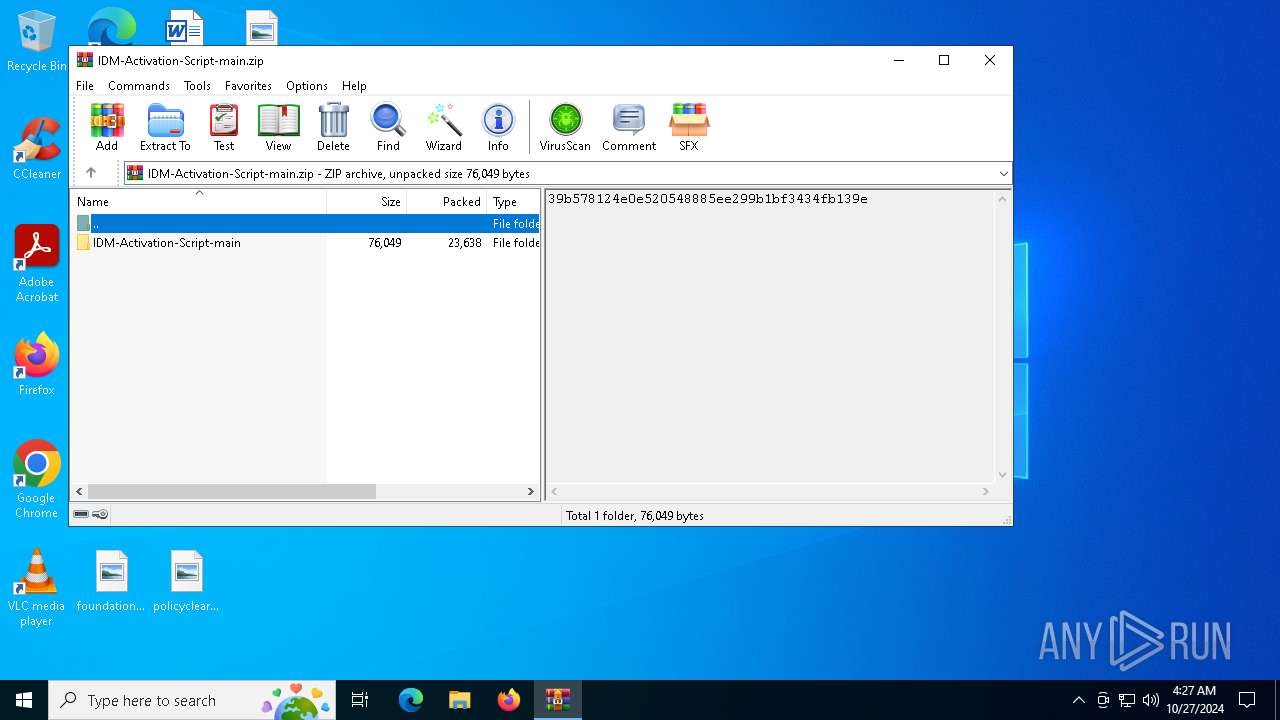
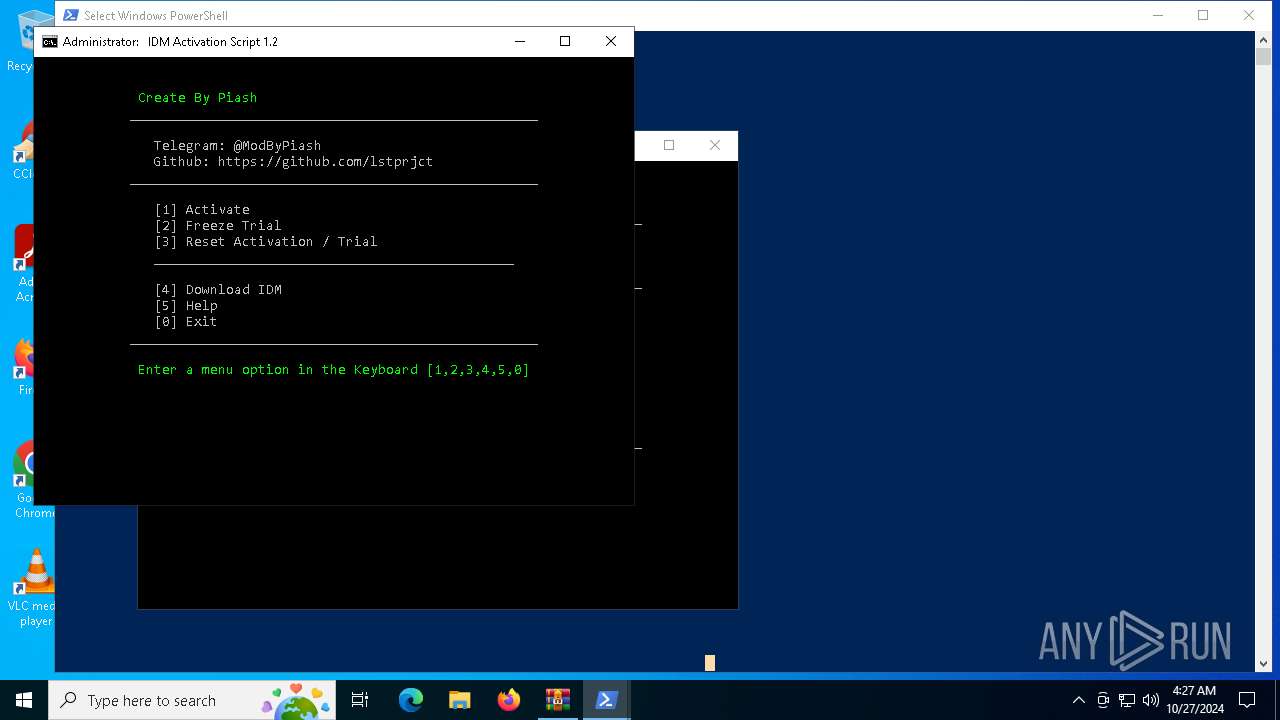
| File name: | IDM-Activation-Script-main.zip |
| Full analysis: | https://app.any.run/tasks/336c0c2a-89ad-46dd-ac7b-f382378462a3 |
| Verdict: | Malicious activity |
| Analysis date: | October 27, 2024, 04:27:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | B9F5F9C365593D0F6848D75F0B03F966 |
| SHA1: | 5144B0DB62B11BBDBB6E2B233F4D07C2827AE689 |
| SHA256: | E7003B0A15F9C5C377D5DEB3A44C08BE497801259B40B88768623940372168C7 |
| SSDEEP: | 768:RNXNa3iCCwTjifjHqFTsISEGM/zEZIWUZtbFXb0zaUn:RNXNGiVdjHqRsIaM6NU3RbRU |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4828)
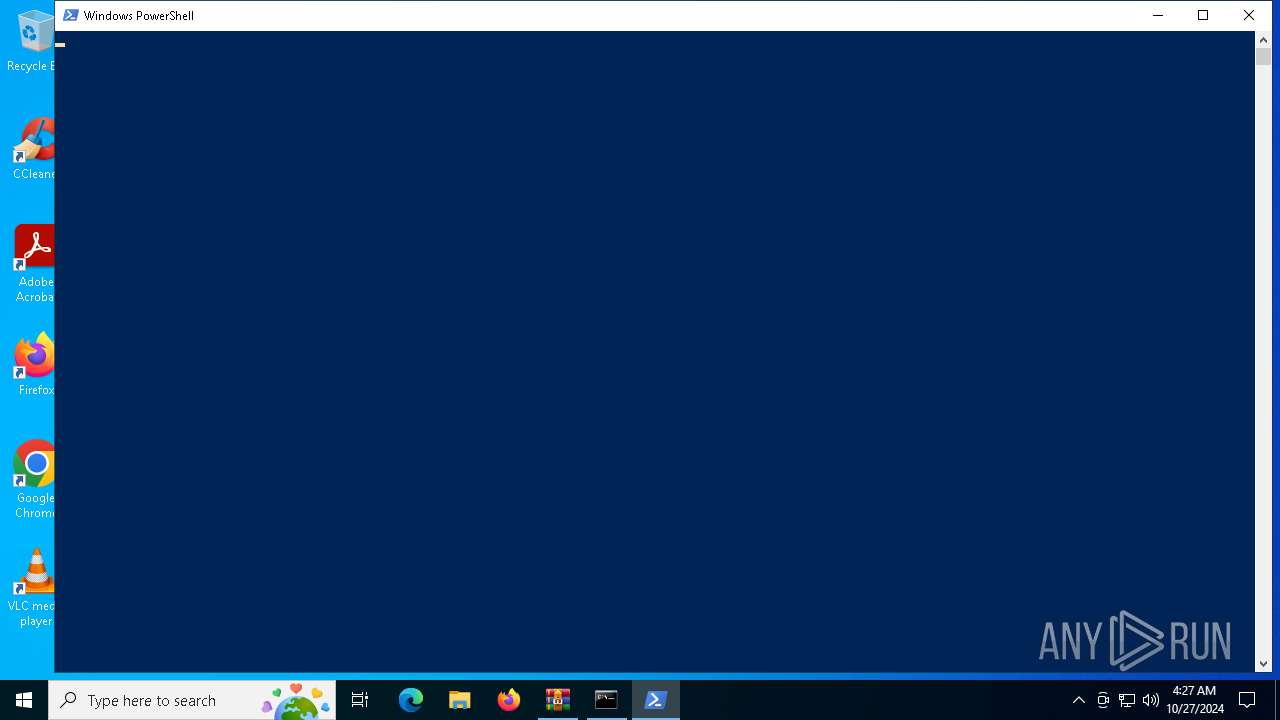
Bypass execution policy to execute commands
- powershell.exe (PID: 948)
Execute application with conhost.exe as parent process
- powershell.exe (PID: 1572)
- powershell.exe (PID: 6184)
SUSPICIOUS
Starts SC.EXE for service management
- cmd.exe (PID: 6756)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 884)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 6216)
- cmd.exe (PID: 204)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6756)
- cmd.exe (PID: 6240)
- powershell.exe (PID: 948)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 7160)
- powershell.exe (PID: 4348)
- cmd.exe (PID: 884)
- cmd.exe (PID: 2360)
- powershell.exe (PID: 916)
- powershell.exe (PID: 1572)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 5940)
- cmd.exe (PID: 6216)
- cmd.exe (PID: 4448)
- powershell.exe (PID: 6184)
- cmd.exe (PID: 204)
- cmd.exe (PID: 5944)
Application launched itself
- cmd.exe (PID: 6240)
- cmd.exe (PID: 6756)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 7160)
- cmd.exe (PID: 884)
- cmd.exe (PID: 2360)
- cmd.exe (PID: 5940)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 6216)
- cmd.exe (PID: 4448)
- cmd.exe (PID: 204)
- cmd.exe (PID: 5944)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6756)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 884)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 6216)
- cmd.exe (PID: 204)
Executing commands from ".cmd" file
- cmd.exe (PID: 6756)
- powershell.exe (PID: 948)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 884)
- powershell.exe (PID: 4348)
- powershell.exe (PID: 916)
- powershell.exe (PID: 1572)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 6216)
- powershell.exe (PID: 6184)
- cmd.exe (PID: 204)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6756)
- cmd.exe (PID: 884)
- cmd.exe (PID: 4408)
- conhost.exe (PID: 1588)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 6216)
- conhost.exe (PID: 1172)
- cmd.exe (PID: 204)
- cmd.exe (PID: 6376)
- cmd.exe (PID: 4448)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 6756)
- cmd.exe (PID: 884)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 6216)
- cmd.exe (PID: 204)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 6756)
- cmd.exe (PID: 884)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 6216)
- cmd.exe (PID: 204)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 948)
Hides command output
- cmd.exe (PID: 6376)
- cmd.exe (PID: 1768)
- cmd.exe (PID: 4448)
- cmd.exe (PID: 6816)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6216)
- cmd.exe (PID: 1768)
- cmd.exe (PID: 204)
- cmd.exe (PID: 6816)
INFO
Manual execution by a user
- cmd.exe (PID: 6756)
- powershell.exe (PID: 948)
- OpenWith.exe (PID: 6960)
- OpenWith.exe (PID: 6328)
Checks operating system version
- cmd.exe (PID: 6756)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 884)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 6216)
- cmd.exe (PID: 204)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6960)
- OpenWith.exe (PID: 6328)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 1784)
- powershell.exe (PID: 1700)
- powershell.exe (PID: 6356)
- powershell.exe (PID: 4088)
- powershell.exe (PID: 5100)
- powershell.exe (PID: 4088)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 1784)
- powershell.exe (PID: 1700)
- powershell.exe (PID: 6356)
- powershell.exe (PID: 4088)
- powershell.exe (PID: 5100)
- powershell.exe (PID: 4088)
Disables trace logs
- powershell.exe (PID: 948)
Checks proxy server information
- powershell.exe (PID: 948)
The process uses the downloaded file
- powershell.exe (PID: 948)
- powershell.exe (PID: 4348)
- powershell.exe (PID: 916)
Starts MODE.COM to configure console settings
- mode.com (PID: 6516)
- mode.com (PID: 916)
Checks supported languages
- mode.com (PID: 6516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:02:20 07:29:12 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | IDM-Activation-Script-main/ |
Total processes
271
Monitored processes
147
Malicious processes
13
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | "C:\WINDOWS\System32\cmd.exe" /c ""C:\Users\admin\AppData\Local\Temp\IAS_99676170.cmd" -el -el -qedit" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 696 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 884 | "C:\WINDOWS\System32\cmd.exe" /c ""C:\Users\admin\Desktop\IAS.cmd" -el " | C:\Windows\System32\cmd.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 884 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo prompt $E " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 916 | powershell.exe "start cmd.exe -arg '/c \""""C:\Users\admin\AppData\Local\Temp\IAS_99676170.cmd""" -el \"' -verb runas" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 916 | mode 75, 28 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | find /i "C:\Users\admin\AppData\Local\Temp" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 948 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\IAS.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo "C:\Users\admin\Desktop\IAS.cmd" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
68 516
Read events
68 506
Write events
6
Delete events
4
Modification events
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\IDM-Activation-Script-main.zip | |||
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5168) reg.exe | Key: | HKEY_CURRENT_USER\IAS_TEST |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6996) reg.exe | Key: | HKEY_CLASSES_ROOT\WOW6432Node\CLSID\IAS_TEST |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6872) reg.exe | Key: | HKEY_CURRENT_USER\IAS_TEST |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3828) reg.exe | Key: | HKEY_CLASSES_ROOT\WOW6432Node\CLSID\IAS_TEST |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
4
Text files
31
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 948 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF8cd7a.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 1784 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fkbusszf.bp1.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1784 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ypll3nbh.pro.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 916 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_woqtetk0.1nh.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6356 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_evdtpf00.tpn.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1784 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:23F222025F348516E8F047B554459A7D | SHA256:7575CB52E59ACB738A62CA62A95D85872F44849EAEA48ADF484595103D07FBE5 | |||
| 6356 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_33ggrchq.2qu.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1700 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qvrm0gt5.ha2.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 948 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:DE6795F95D7DC4276C69001DDF9D90F4 | SHA256:091A463201DA5AD32CF96A9EC008AD90FCBD937DF8675DDBC72384650A847C03 | |||
| 916 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rhmjbsan.jku.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
28
DNS requests
8
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1588 | RUXIMICS.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1588 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 140.82.121.3:443 | https://raw.githubusercontent.com/lstprjct/IDM-Activation-Script/main/IAS.cmd | unknown | text | 30.4 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1588 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Get-WmiObject Cmdlet has been detected |