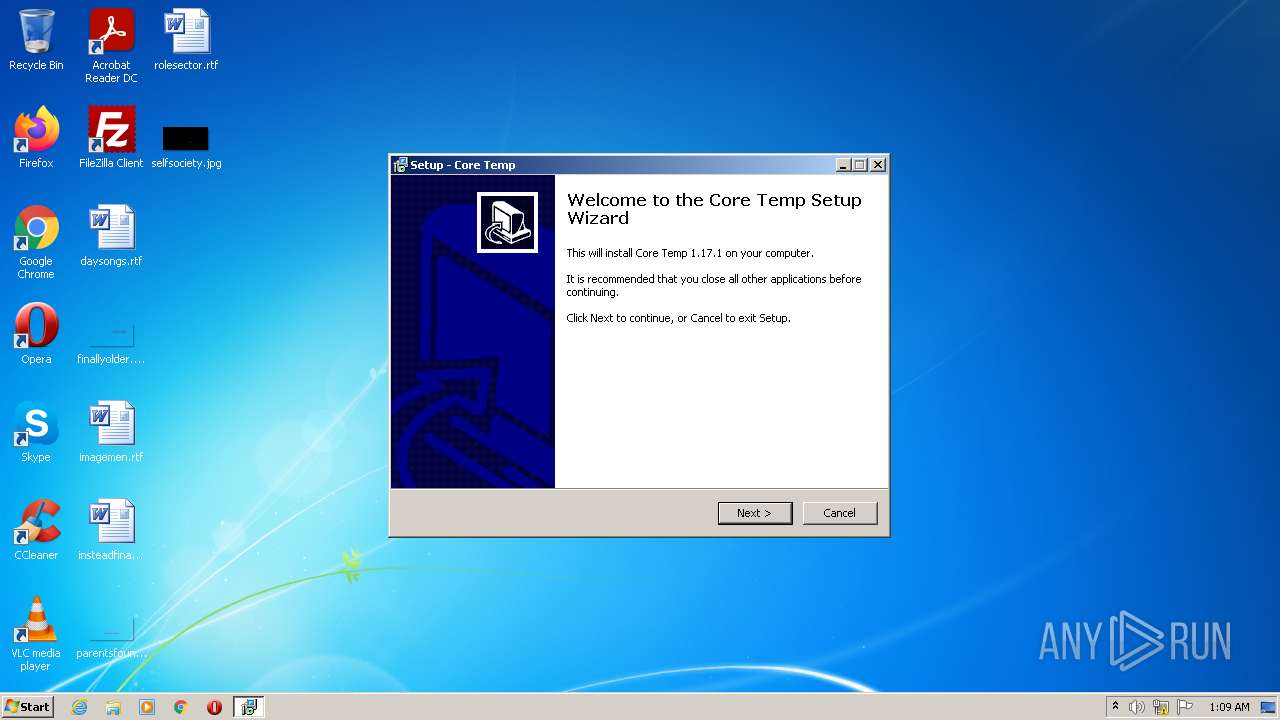
| File name: | Core-Temp-setup.exe |
| Full analysis: | https://app.any.run/tasks/ff11d54d-3d10-4a99-b097-4e7640650ce9 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 00:09:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 77448F48D66FA4565CDD962324BFD5B8 |
| SHA1: | 6B0C74040AD0FCAB182C87C3B3C3DF152646BDD2 |
| SHA256: | E6EFC39C1F95D4E6286640A10459FE9A14AE1CB6FBC95CCEC95D063AC27F0978 |
| SSDEEP: | 24576:q86HODFbrDdsxg8MGMm8ZlfVI+z91BoQ9uZUR+zZdFr:4udDqAGaZDIcpV9u1X |
MALICIOUS
Drops executable file immediately after starts
- Core-Temp-setup.exe (PID: 1144)
- Core-Temp-setup.exe (PID: 672)
- Core-Temp-setup.tmp (PID: 2332)
- Core Temp.exe (PID: 2176)
Application was dropped or rewritten from another process
- Core Temp.exe (PID: 2176)
Loads the Task Scheduler COM API
- Core Temp.exe (PID: 2176)
SUSPICIOUS
Drops a file with a compile date too recent
- Core-Temp-setup.exe (PID: 1144)
- Core-Temp-setup.exe (PID: 672)
- Core Temp.exe (PID: 2176)
- Core-Temp-setup.tmp (PID: 2332)
Executable content was dropped or overwritten
- Core-Temp-setup.exe (PID: 1144)
- Core-Temp-setup.exe (PID: 672)
- Core Temp.exe (PID: 2176)
- Core-Temp-setup.tmp (PID: 2332)
Checks supported languages
- Core-Temp-setup.exe (PID: 672)
- Core-Temp-setup.exe (PID: 1144)
- Core-Temp-setup.tmp (PID: 2332)
- Core-Temp-setup.tmp (PID: 3376)
- Core Temp.exe (PID: 2176)
Reads the computer name
- Core-Temp-setup.tmp (PID: 3376)
- Core-Temp-setup.tmp (PID: 2332)
- Core Temp.exe (PID: 2176)
Creates a directory in Program Files
- Core-Temp-setup.tmp (PID: 2332)
Reads Windows owner or organization settings
- Core-Temp-setup.tmp (PID: 2332)
Reads the Windows organization settings
- Core-Temp-setup.tmp (PID: 2332)
Creates files in the program directory
- Core Temp.exe (PID: 2176)
INFO
Application was dropped or rewritten from another process
- Core-Temp-setup.tmp (PID: 3376)
- Core-Temp-setup.tmp (PID: 2332)
Creates files in the program directory
- Core-Temp-setup.tmp (PID: 2332)
Creates a software uninstall entry
- Core-Temp-setup.tmp (PID: 2332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (45.2) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (20.9) |
| .exe | | | Win32 Executable (generic) (14.3) |
| .exe | | | Win16/32 Executable Delphi generic (6.6) |
| .exe | | | Generic Win/DOS Executable (6.3) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2018-Jun-14 13:27:46 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | ALCPU |
| FileDescription: | Core Temp Setup |
| FileVersion: | 1.17.1.0 |
| LegalCopyright: | - |
| ProductName: | Core Temp |
| ProductVersion: | 1.17.1 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 80 |
| e_cp: | 2 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | 15 |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | 26 |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 256 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 8 |
| TimeDateStamp: | 2018-Jun-14 13:27:46 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 62044 | 62464 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.37588 |
.itext | 69632 | 4004 | 4096 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.77877 |
.data | 73728 | 3212 | 3584 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.30283 |
.bss | 77824 | 22204 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.idata | 102400 | 3588 | 4096 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.59781 |
.tls | 106496 | 8 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.rdata | 110592 | 24 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.204488 |
.rsrc | 114688 | 45568 | 45568 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.14048 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.25755 | 296 | UNKNOWN | Dutch - Netherlands | RT_ICON |
2 | 3.47151 | 1384 | UNKNOWN | Dutch - Netherlands | RT_ICON |
3 | 3.91708 | 744 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4 | 3.91366 | 2216 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4091 | 2.56031 | 104 | UNKNOWN | UNKNOWN | RT_STRING |
4092 | 3.25287 | 212 | UNKNOWN | UNKNOWN | RT_STRING |
4093 | 3.26919 | 164 | UNKNOWN | UNKNOWN | RT_STRING |
4094 | 3.33268 | 684 | UNKNOWN | UNKNOWN | RT_STRING |
4095 | 3.34579 | 844 | UNKNOWN | UNKNOWN | RT_STRING |
4096 | 3.28057 | 660 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
advapi32.dll |
advapi32.dll (#2) |
advapi32.dll (#3) |
comctl32.dll |
kernel32.dll |
kernel32.dll (#2) |
kernel32.dll (#3) |
kernel32.dll (#4) |
oleaut32.dll |
user32.dll |
Total processes
41
Monitored processes
5
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | "C:\Users\admin\AppData\Local\Temp\Core-Temp-setup.exe" /SPAWNWND=$20130 /NOTIFYWND=$20138 | C:\Users\admin\AppData\Local\Temp\Core-Temp-setup.exe | Core-Temp-setup.tmp | ||||||||||||
User: admin Company: ALCPU Integrity Level: HIGH Description: Core Temp Setup Exit code: 0 Version: 1.17.1.0 Modules
| |||||||||||||||
| 1144 | "C:\Users\admin\AppData\Local\Temp\Core-Temp-setup.exe" | C:\Users\admin\AppData\Local\Temp\Core-Temp-setup.exe | Explorer.EXE | ||||||||||||
User: admin Company: ALCPU Integrity Level: MEDIUM Description: Core Temp Setup Exit code: 0 Version: 1.17.1.0 Modules
| |||||||||||||||
| 2176 | "C:\Program Files\Core Temp\Core Temp.exe" | C:\Program Files\Core Temp\Core Temp.exe | Core-Temp-setup.tmp | ||||||||||||
User: admin Company: ALCPU Integrity Level: HIGH Description: CPU temperature and system information utility Exit code: 0 Version: 1.17.1.0 Modules
| |||||||||||||||
| 2332 | "C:\Users\admin\AppData\Local\Temp\is-MP2UK.tmp\Core-Temp-setup.tmp" /SL5="$2013A,851632,121344,C:\Users\admin\AppData\Local\Temp\Core-Temp-setup.exe" /SPAWNWND=$20130 /NOTIFYWND=$20138 | C:\Users\admin\AppData\Local\Temp\is-MP2UK.tmp\Core-Temp-setup.tmp | Core-Temp-setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3376 | "C:\Users\admin\AppData\Local\Temp\is-G12FT.tmp\Core-Temp-setup.tmp" /SL5="$20138,851632,121344,C:\Users\admin\AppData\Local\Temp\Core-Temp-setup.exe" | C:\Users\admin\AppData\Local\Temp\is-G12FT.tmp\Core-Temp-setup.tmp | — | Core-Temp-setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
1 377
Read events
1 341
Write events
30
Delete events
6
Modification events
| (PID) Process: | (2332) Core-Temp-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 1C090000DCDCAFBD4ED8D801 | |||
| (PID) Process: | (2332) Core-Temp-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 93E0FAF2016A742286E592EF6BBD8F8F3898A25C5334E8231ED3B4B36B73F1E1 | |||
| (PID) Process: | (2332) Core-Temp-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2332) Core-Temp-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Core Temp\Core Temp.exe | |||
| (PID) Process: | (2332) Core-Temp-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: D7537AA0A36DF0C33F07D17795F8402F357C560F1A60E0A13890AB94E77D73FF | |||
| (PID) Process: | (2332) Core-Temp-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{086D343F-8E78-4AFC-81AC-D6D414AFD8AC}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.6.1 (u) | |||
| (PID) Process: | (2332) Core-Temp-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{086D343F-8E78-4AFC-81AC-D6D414AFD8AC}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\Core Temp | |||
| (PID) Process: | (2332) Core-Temp-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{086D343F-8E78-4AFC-81AC-D6D414AFD8AC}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Core Temp\ | |||
| (PID) Process: | (2332) Core-Temp-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{086D343F-8E78-4AFC-81AC-D6D414AFD8AC}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Core Temp | |||
| (PID) Process: | (2332) Core-Temp-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{086D343F-8E78-4AFC-81AC-D6D414AFD8AC}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
7
Suspicious files
0
Text files
66
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2332 | Core-Temp-setup.tmp | C:\Program Files\Core Temp\is-PLEFQ.tmp | text | |
MD5:— | SHA256:— | |||
| 2332 | Core-Temp-setup.tmp | C:\Program Files\Core Temp\Languages\bg-BG.lng | xml | |
MD5:— | SHA256:— | |||
| 2332 | Core-Temp-setup.tmp | C:\Program Files\Core Temp\Languages\da-DK.lng | xml | |
MD5:— | SHA256:— | |||
| 2332 | Core-Temp-setup.tmp | C:\Program Files\Core Temp\Languages\ca.lng | xml | |
MD5:— | SHA256:— | |||
| 2332 | Core-Temp-setup.tmp | C:\Program Files\Core Temp\Languages\is-H7O7N.tmp | xml | |
MD5:— | SHA256:— | |||
| 2332 | Core-Temp-setup.tmp | C:\Program Files\Core Temp\is-1S4B3.tmp | text | |
MD5:9AB877751224D96448876F7ECF15559F | SHA256:ABB84CF36BD0E8F39248F5477CA0D427DA9B7E3C10B6666254B98D6E06B40E7B | |||
| 2332 | Core-Temp-setup.tmp | C:\Program Files\Core Temp\Core Temp.exe | executable | |
MD5:94246356857F0E72C917A4A8CE331A03 | SHA256:AA4BDF0A6D21A59822B1000EFED64E9287CE30108FE3943C6AA0139D86B5E3E7 | |||
| 2332 | Core-Temp-setup.tmp | C:\Program Files\Core Temp\Languages\cs.lng | xml | |
MD5:— | SHA256:— | |||
| 672 | Core-Temp-setup.exe | C:\Users\admin\AppData\Local\Temp\is-MP2UK.tmp\Core-Temp-setup.tmp | executable | |
MD5:34ACC2BDB45A9C436181426828C4CB49 | SHA256:9C81817ACD4982632D8C7F1DF3898FCA1477577738184265D735F49FC5480F07 | |||
| 2332 | Core-Temp-setup.tmp | C:\Program Files\Core Temp\is-BADQV.tmp | executable | |
MD5:94246356857F0E72C917A4A8CE331A03 | SHA256:AA4BDF0A6D21A59822B1000EFED64E9287CE30108FE3943C6AA0139D86B5E3E7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2176 | Core Temp.exe | GET | 200 | 192.185.41.230:80 | http://www.alcpu.com/CoreTemp/coretempver.xml | US | xml | 1.22 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2176 | Core Temp.exe | 192.185.41.230:80 | www.alcpu.com | UNIFIEDLAYER-AS-1 | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.alcpu.com |
| suspicious |