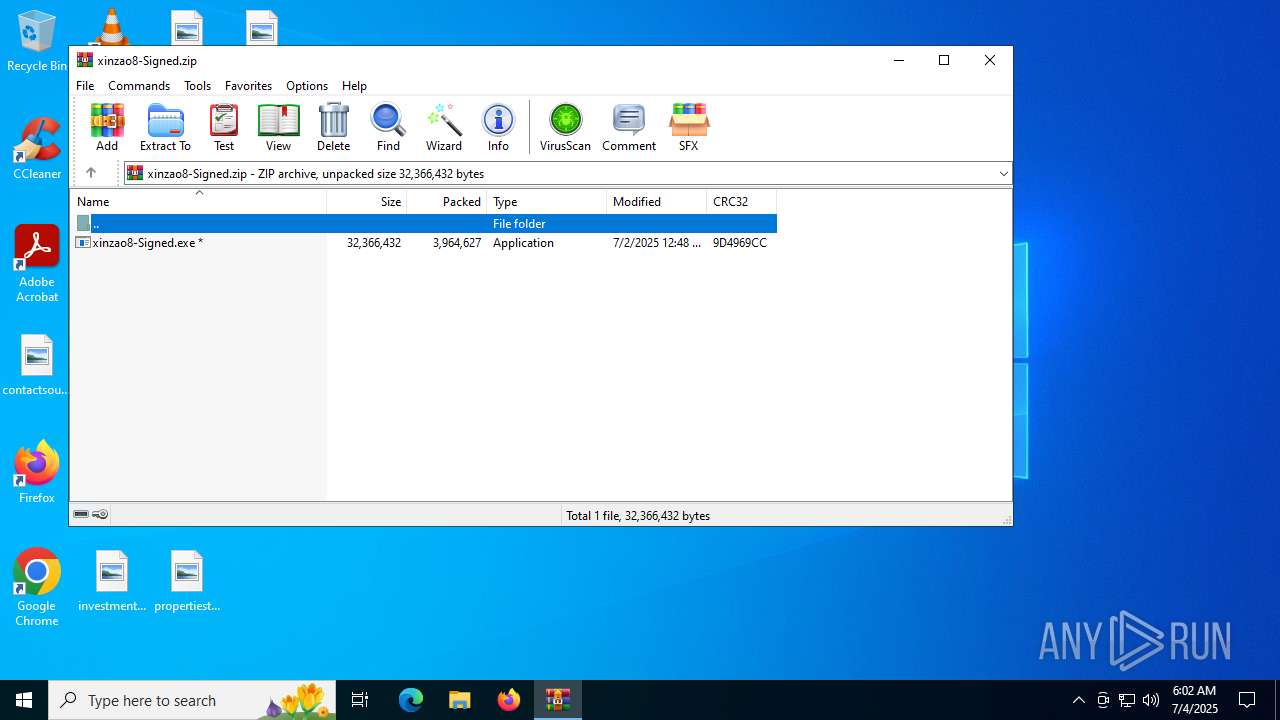
| File name: | xinzao8-Signed.zip |
| Full analysis: | https://app.any.run/tasks/4b16c019-2f99-4a1e-88a5-fedf52da0e85 |
| Verdict: | Malicious activity |
| Analysis date: | July 04, 2025, 06:02:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 9CADE91AF40C449F4AB7A3C8E0395706 |
| SHA1: | E2C431BBDA8CCE87AB11689DAC7258C38AF828C7 |
| SHA256: | E6E461372DF0A2B7FF5554D55ACB3D8590DAAA4CEB48B66BC140FCE6057E3293 |
| SSDEEP: | 98304:HwcQeKTtljSUC8ztLPKyKXYQ2mCtH3qg4gzpyjHFJzc+D2BLy47fmQhF0L8RPJj2:YYYCOri1l |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5808)
Executing a file with an untrusted certificate
- xinzao8-Signed.exe (PID: 5352)
- xinzao8-Signed.exe (PID: 4800)
- xinzao8-Signed.exe (PID: 728)
- xinzao8-Signed.exe (PID: 5060)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 5808)
- WinRAR.exe (PID: 868)
Starts a Microsoft application from unusual location
- xinzao8-Signed.exe (PID: 4800)
- xinzao8-Signed.exe (PID: 5352)
- xinzao8-Signed.exe (PID: 5060)
- xinzao8-Signed.exe (PID: 728)
Executes as Windows Service
- VSSVC.exe (PID: 5724)
Executable content was dropped or overwritten
- VSSVC.exe (PID: 5724)
There is functionality for taking screenshot (YARA)
- svchost.exe (PID: 5708)
- dllhost.exe (PID: 6980)
- VSSVC.exe (PID: 5724)
- svchost.exe (PID: 4372)
- dllhost.exe (PID: 3952)
- Taskmgr.exe (PID: 4932)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 5808)
- WinRAR.exe (PID: 868)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5808)
- WinRAR.exe (PID: 868)
Manual execution by a user
- xinzao8-Signed.exe (PID: 4800)
- xinzao8-Signed.exe (PID: 5352)
- WinRAR.exe (PID: 868)
- xinzao8-Signed.exe (PID: 5060)
- xinzao8-Signed.exe (PID: 728)
- Taskmgr.exe (PID: 1180)
- Taskmgr.exe (PID: 4932)
Reads the computer name
- xinzao8-Signed.exe (PID: 5352)
- xinzao8-Signed.exe (PID: 728)
Checks supported languages
- xinzao8-Signed.exe (PID: 5352)
- xinzao8-Signed.exe (PID: 728)
Creates files in the program directory
- VSSVC.exe (PID: 5724)
- dllhost.exe (PID: 6980)
Checks proxy server information
- slui.exe (PID: 6748)
Reads the software policy settings
- slui.exe (PID: 6748)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 4932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:07:02 08:48:02 |
| ZipCRC: | 0x9d4969cc |
| ZipCompressedSize: | 3964627 |
| ZipUncompressedSize: | 32366432 |
| ZipFileName: | xinzao8-Signed.exe |
Total processes
161
Monitored processes
14
Malicious processes
0
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | "C:\Users\admin\Desktop\xinzao8-Signed.exe" | C:\Users\admin\Desktop\xinzao8-Signed.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ApplyTrustOffline.PROGRAM Exit code: 0 Version: 10.0.19041.5737 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 868 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\xinzao8-Signed.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1180 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3952 | C:\WINDOWS\system32\dllhost.exe /Processid:{F8284233-48F4-4680-ADDD-F8284233} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4372 | C:\WINDOWS\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | VSSVC.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4800 | "C:\Users\admin\Desktop\xinzao8-Signed.exe" | C:\Users\admin\Desktop\xinzao8-Signed.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ApplyTrustOffline.PROGRAM Exit code: 3221226540 Version: 10.0.19041.5737 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4932 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5060 | "C:\Users\admin\Desktop\xinzao8-Signed.exe" | C:\Users\admin\Desktop\xinzao8-Signed.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ApplyTrustOffline.PROGRAM Exit code: 3221226540 Version: 10.0.19041.5737 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5352 | "C:\Users\admin\Desktop\xinzao8-Signed.exe" | C:\Users\admin\Desktop\xinzao8-Signed.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ApplyTrustOffline.PROGRAM Exit code: 0 Version: 10.0.19041.5737 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5708 | C:\WINDOWS\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | VSSVC.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 154
Read events
9 134
Write events
19
Delete events
1
Modification events
| (PID) Process: | (5808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\xinzao8-Signed.zip | |||
| (PID) Process: | (5808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5724 | VSSVC.exe | C:\Program Files\Internet Explorer\glbdll.bin | binary | |
MD5:38131AEECF4963D6DC18B643CD3BEFAA | SHA256:4823BF49942DCDF9438CFDFA634D496D496C8810D01D63E5F880B412FD0A7DD6 | |||
| 5724 | VSSVC.exe | C:\Program Files\Internet Explorer\glbdll.dll | executable | |
MD5:1496018EE0737EED95D3924A7E91CD77 | SHA256:D98C5980C57B5677EAAF337264C52E0BB6C297C3F8E2E62DB67ED116BB337D61 | |||
| 5808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5808.28544\xinzao8-Signed.exe | executable | |
MD5:CE1C28DECBEF24423B26AD13FC6E6530 | SHA256:A868E853A09D7B4F5BCE2A2066D2EB829038F1710DD98842A460F715023C645F | |||
| 6980 | dllhost.exe | C:\Program Files\Internet Explorer\temp.key | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 5724 | VSSVC.exe | C:\Program Files\Internet Explorer\nvsc.exe | executable | |
MD5:E7ABEFBDE34B4D91420C4C31F8AAE8BF | SHA256:C398671546874015FAD17620BB80111C77831A4A55FD632A1C8872EA6B7B7D1B | |||
| 868 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb868.35313\xinzao8-Signed.exe | executable | |
MD5:CE1C28DECBEF24423B26AD13FC6E6530 | SHA256:A868E853A09D7B4F5BCE2A2066D2EB829038F1710DD98842A460F715023C645F | |||
| 4932 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
33
DNS requests
45
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.241.14:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2612 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1128 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1128 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1520 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
4104 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5720 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.16.241.14:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2612 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2612 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
www.360.cn |
| whitelisted |
v.qq.com |
| whitelisted |
www.baidu.com |
| whitelisted |