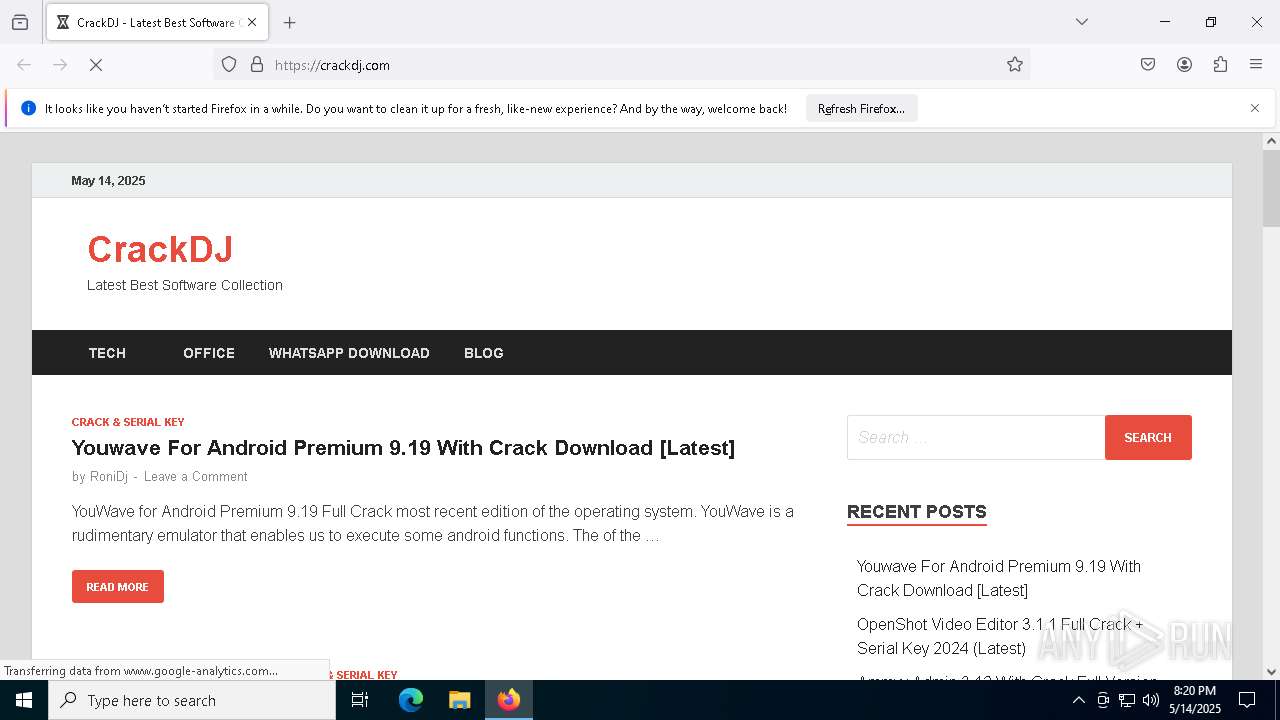
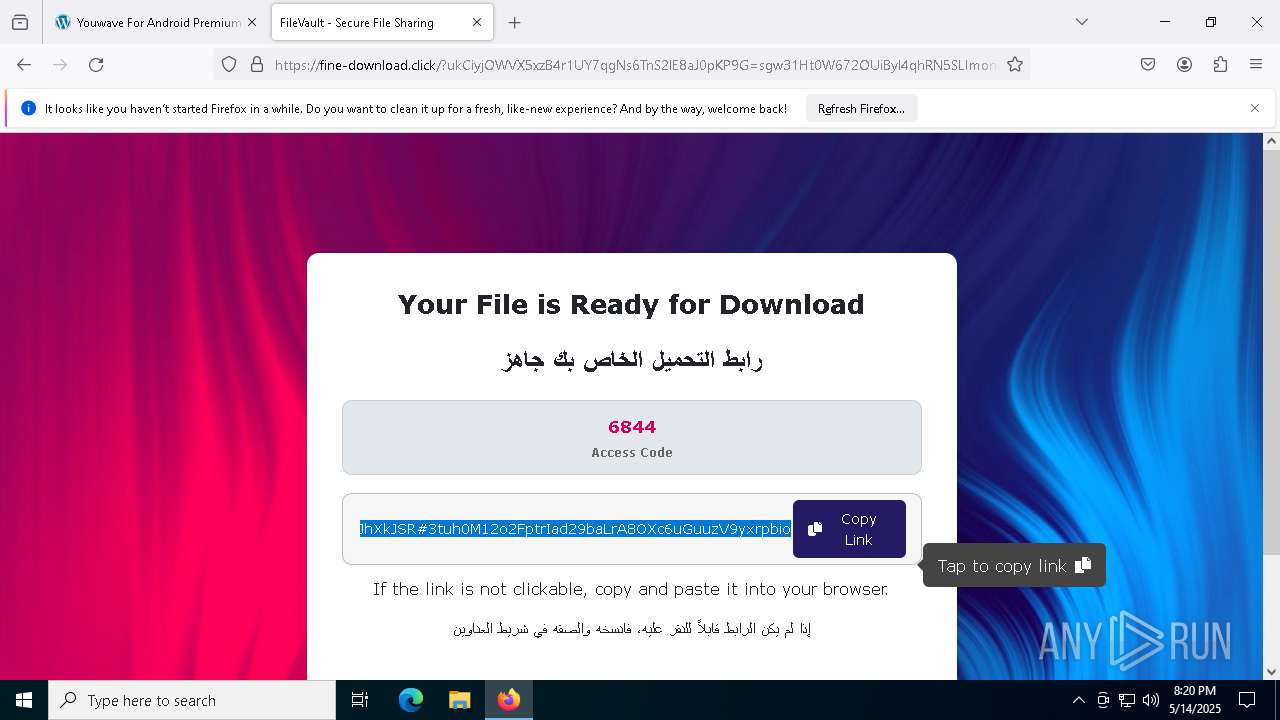
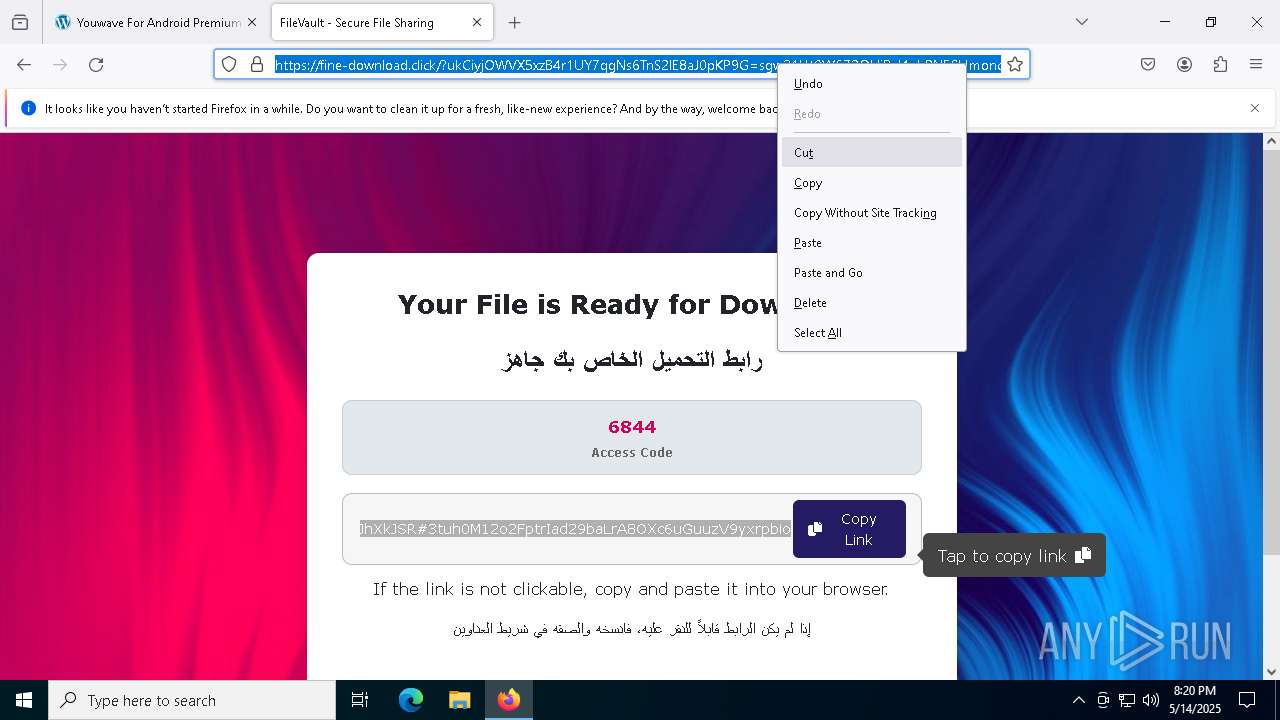
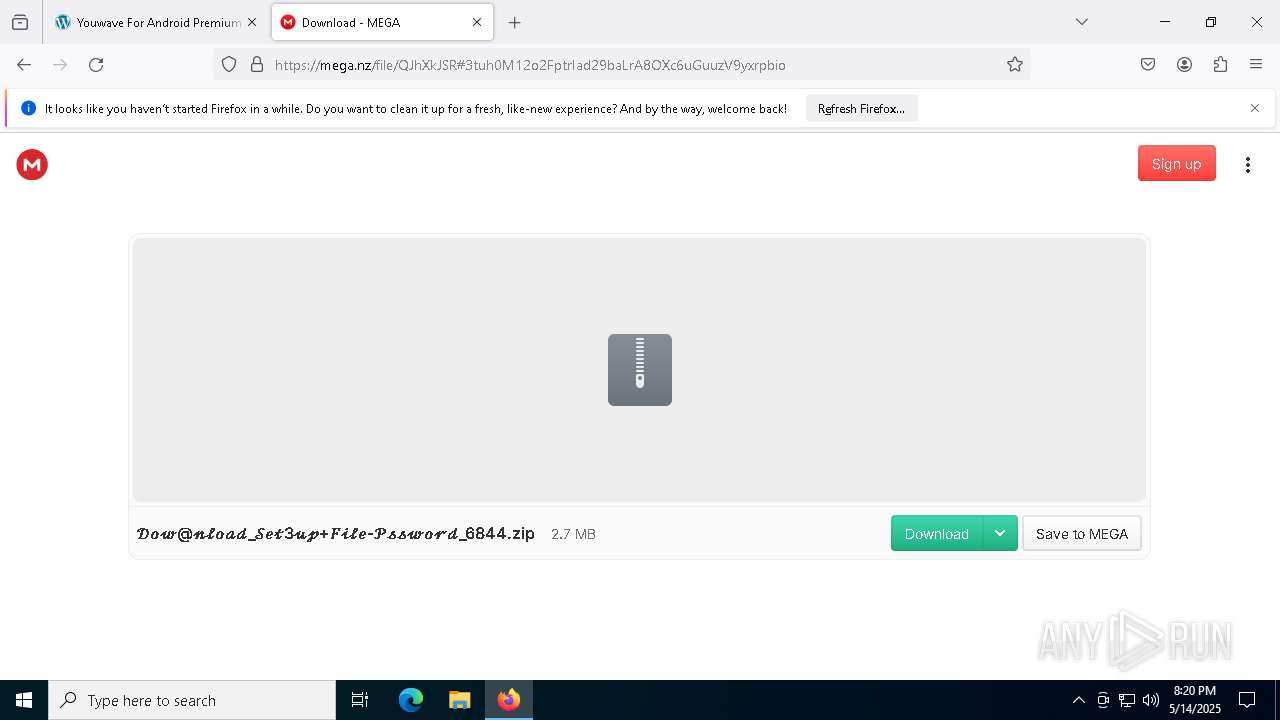
| URL: | crackdj.com |
| Full analysis: | https://app.any.run/tasks/564f373a-e7e1-4389-81f7-b7c254582d52 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | May 14, 2025, 20:20:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 1F23A212F2D5D36477A5F41E9BE87E78 |
| SHA1: | 32DDAC4DD3F0C03DDC5E23D31B81B9040041F79F |
| SHA256: | E69A92200744F23DAEF79FA89CBA9C048A99428293FE9F59039334431AB22CC0 |
| SSDEEP: | 3:lzGT:lO |
MALICIOUS
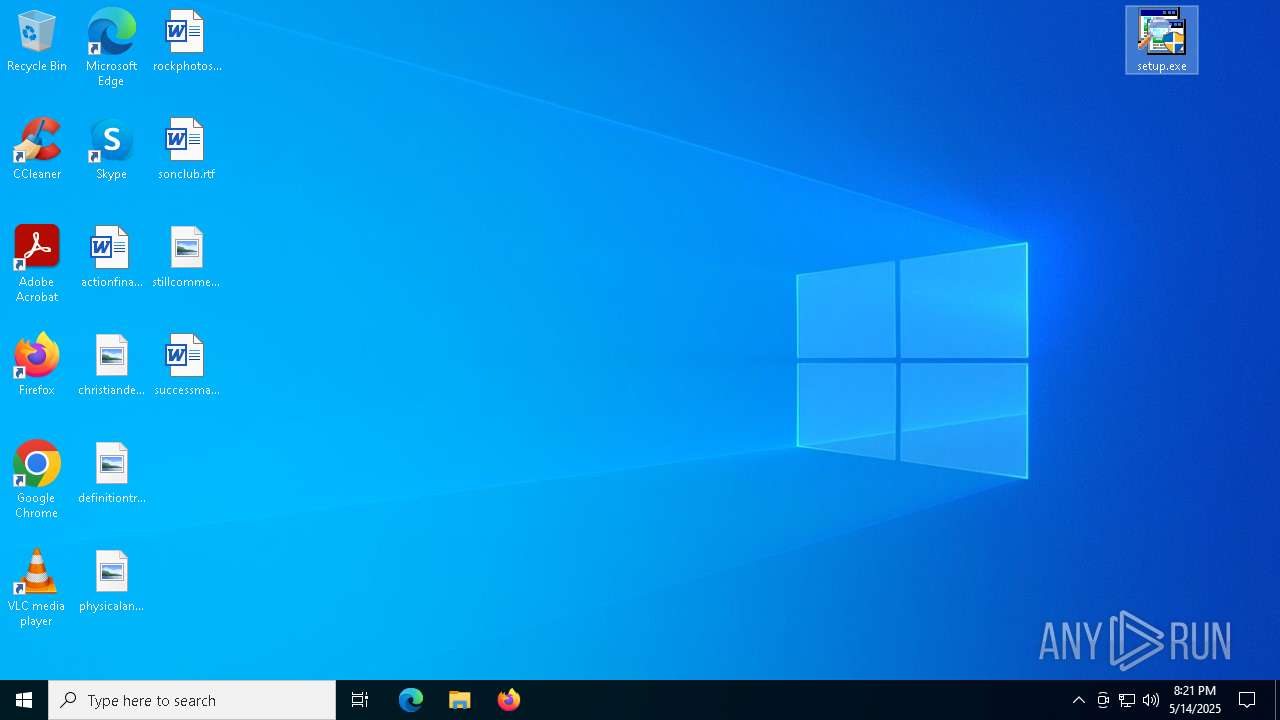
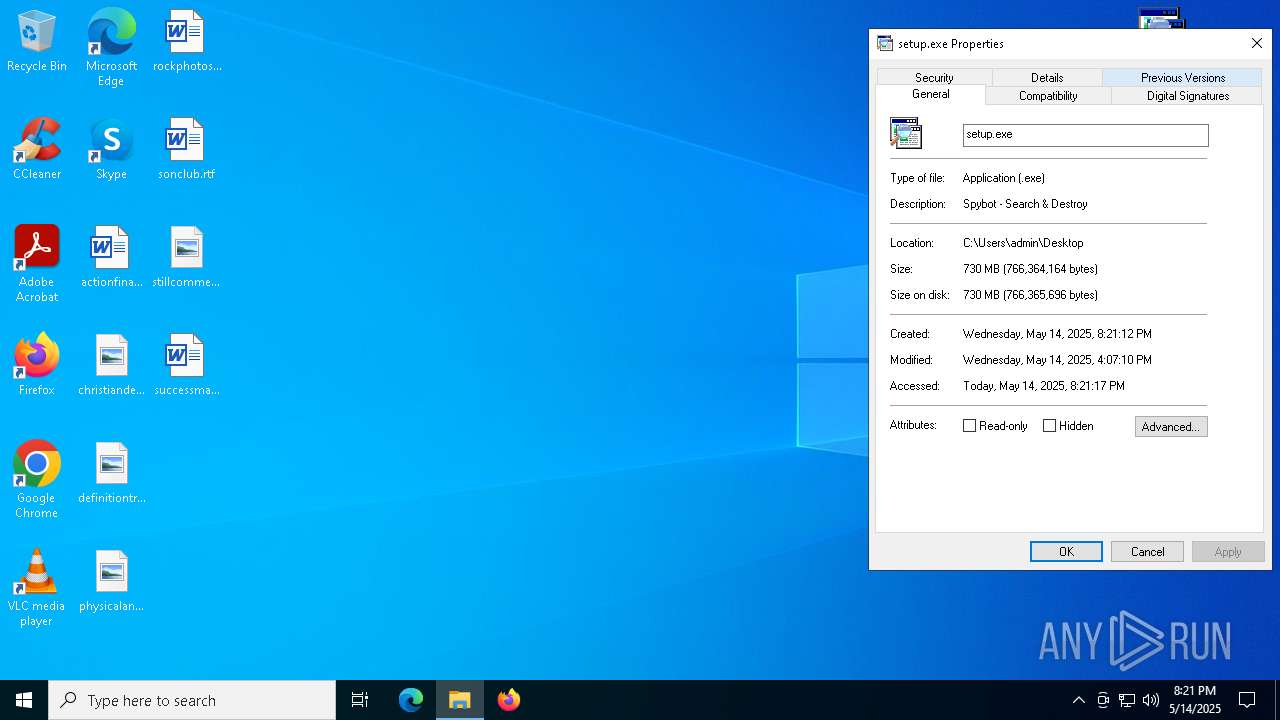
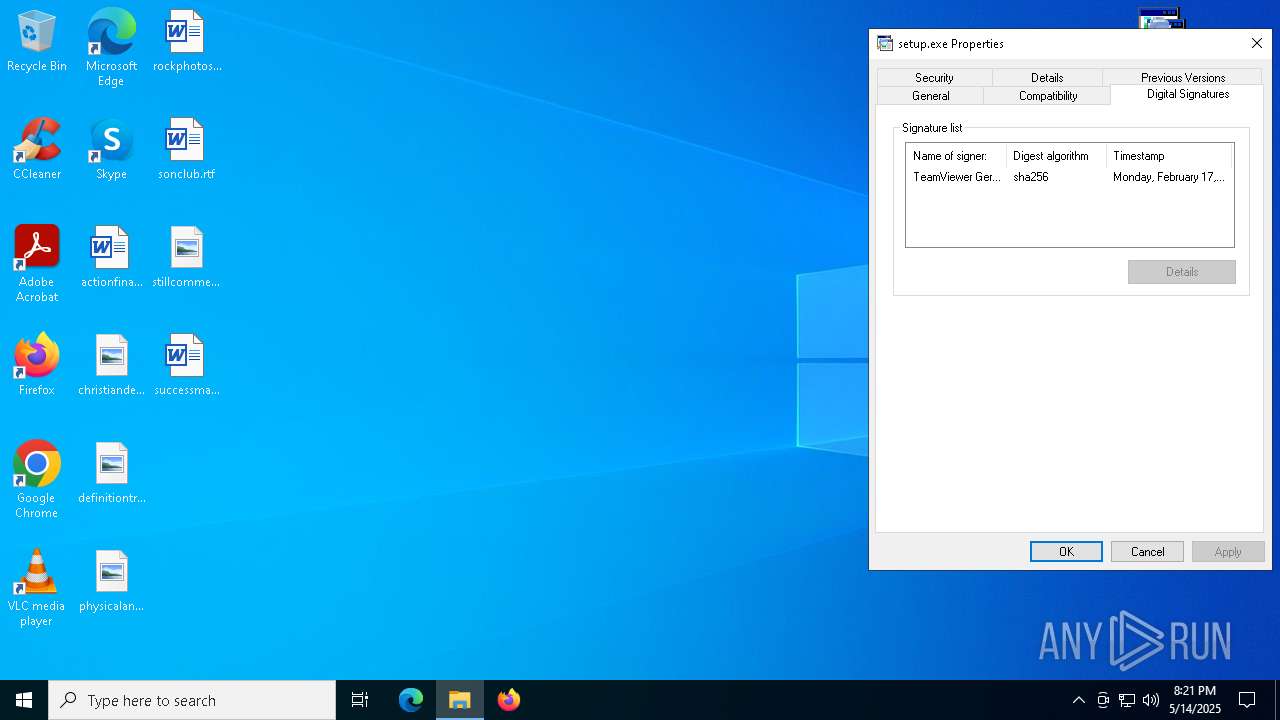
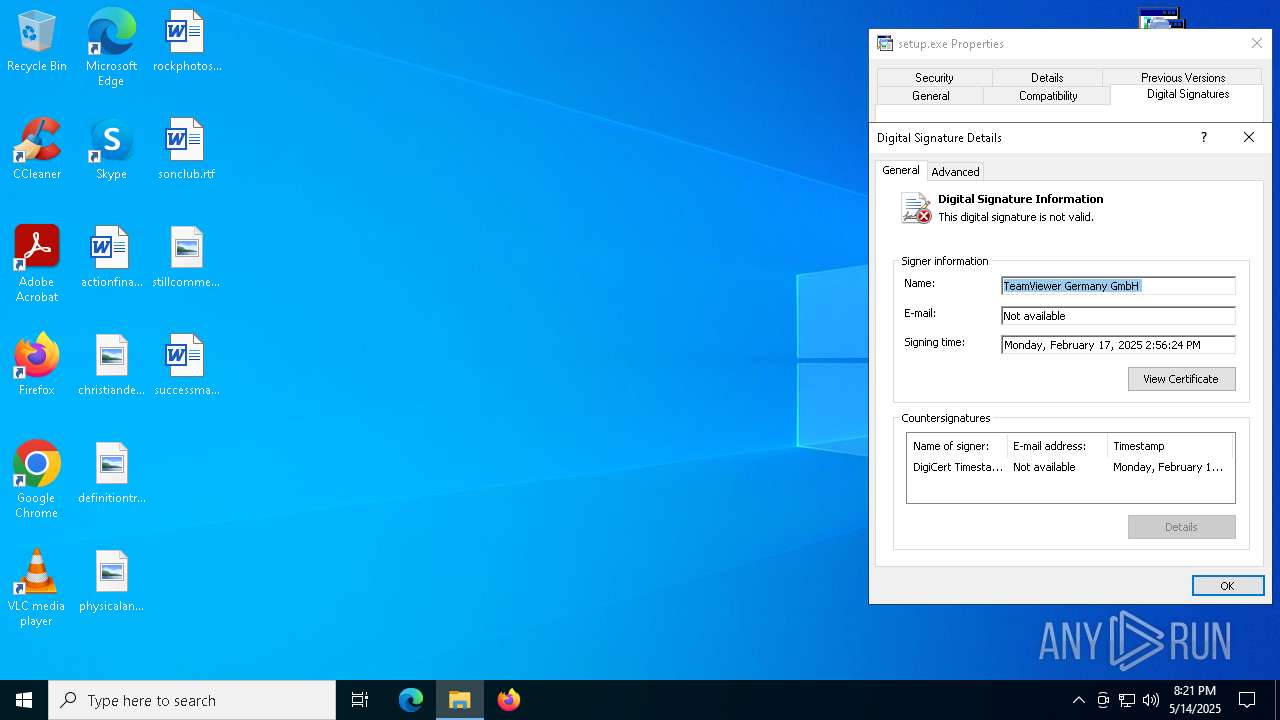
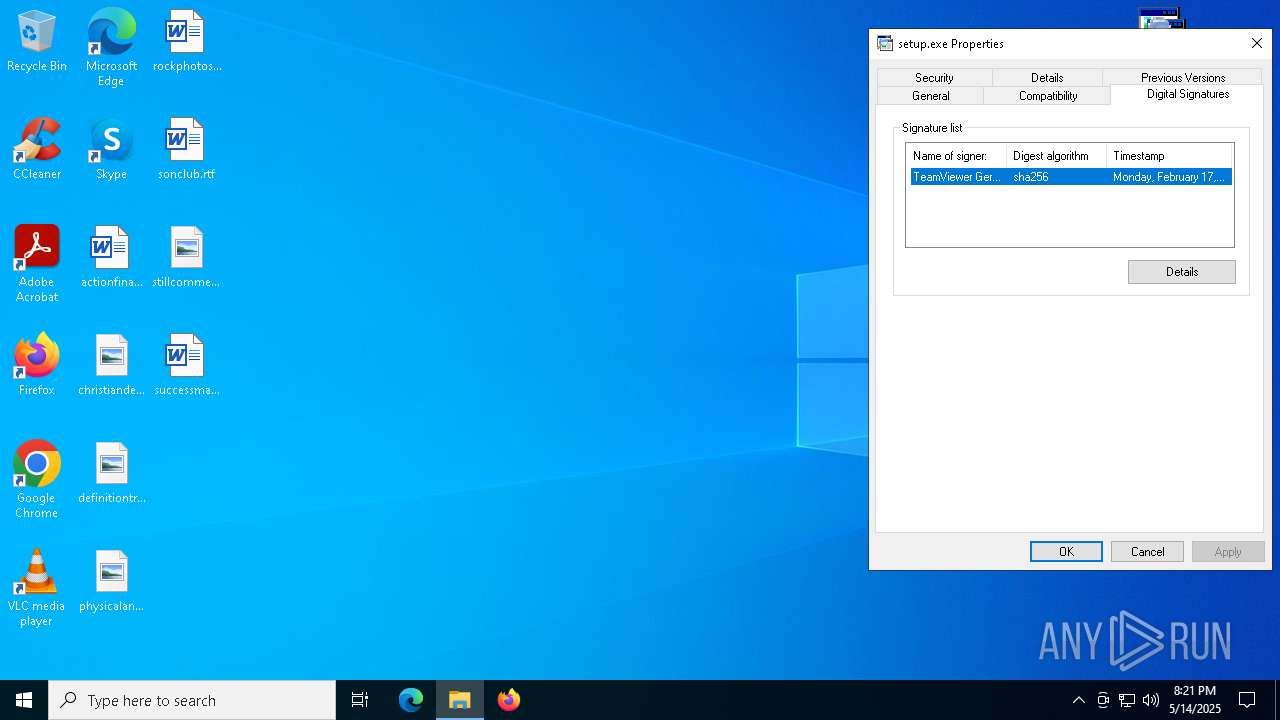
Executing a file with an untrusted certificate
- setup.exe (PID: 7572)
- setup.exe (PID: 660)
- hjksfi.exe (PID: 7340)
- hjksfa.exe (PID: 720)
- shark.exe (PID: 1348)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 7408)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 7864)
- WinRAR.exe (PID: 5324)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7864)
- WinRAR.exe (PID: 5324)
Creates file in the systems drive root
- explorer.exe (PID: 5492)
Potential Corporate Privacy Violation
- setup.exe (PID: 7572)
Executable content was dropped or overwritten
- setup.exe (PID: 7572)
- hjksfa.exe (PID: 720)
- hjksfi.exe (PID: 7340)
- wipe.com (PID: 7816)
- MicrosoftEdgeWebview2Setup.exe (PID: 4436)
Process requests binary or script from the Internet
- setup.exe (PID: 7572)
There is functionality for taking screenshot (YARA)
- hjksfi.exe (PID: 7340)
- shark.exe (PID: 1348)
Starts application with an unusual extension
- hjksfa.exe (PID: 720)
Starts CMD.EXE for commands execution
- hjksfi.exe (PID: 7340)
Executes application which crashes
- hjksfi.exe (PID: 7340)
- shark.exe (PID: 1348)
Process drops legitimate windows executable
- wipe.com (PID: 7816)
- MicrosoftEdgeUpdate.exe (PID: 7600)
- MicrosoftEdgeWebview2Setup.exe (PID: 4436)
Connects to unusual port
- wipe.com (PID: 7816)
- shark.exe (PID: 1348)
Starts process via Powershell
- powershell.exe (PID: 7172)
Starts a Microsoft application from unusual location
- MicrosoftEdgeUpdate.exe (PID: 7600)
The process executes via Task Scheduler
- shark.exe (PID: 1348)
Starts POWERSHELL.EXE for commands execution
- wipe.com (PID: 7816)
INFO
Application launched itself
- firefox.exe (PID: 6456)
- firefox.exe (PID: 2140)
Manual execution by a user
- WinRAR.exe (PID: 5324)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
Reads Microsoft Office registry keys
- explorer.exe (PID: 5492)
- WinRAR.exe (PID: 5324)
Executes as Windows Service
- elevation_service.exe (PID: 5436)
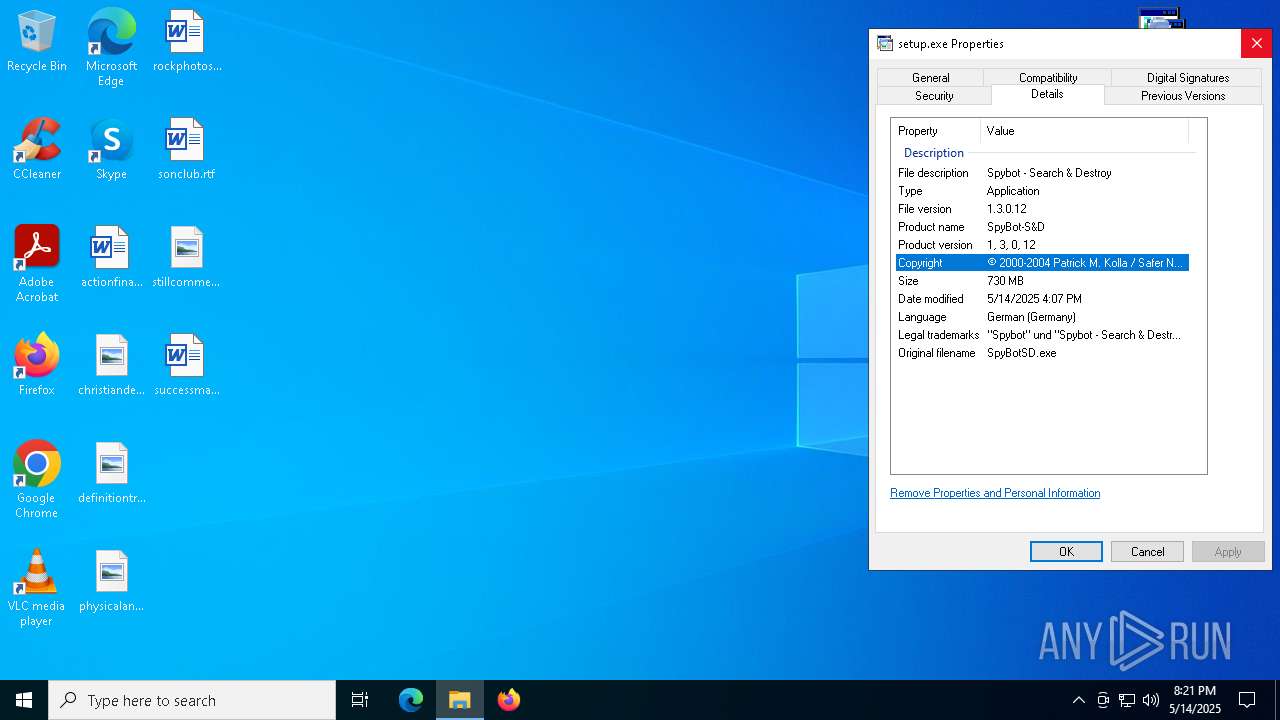
Detects InnoSetup installer (YARA)
- setup.exe (PID: 7572)
Compiled with Borland Delphi (YARA)
- setup.exe (PID: 7572)
- hjksfi.exe (PID: 7340)
- shark.exe (PID: 1348)
The sample compiled with english language support
- setup.exe (PID: 7572)
- hjksfa.exe (PID: 720)
- wipe.com (PID: 7816)
- MicrosoftEdgeUpdate.exe (PID: 7600)
- MicrosoftEdgeWebview2Setup.exe (PID: 4436)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
215
Monitored processes
65
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "C:\Users\admin\Desktop\setup.exe" | C:\Users\admin\Desktop\setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Safer Networking Limited Integrity Level: MEDIUM Description: Spybot - Search & Destroy Exit code: 3221226540 Version: 1.3.0.12 Modules
| |||||||||||||||
| 720 | "C:\Users\admin\hjksfa.exe" | C:\Users\admin\hjksfa.exe | setup.exe | ||||||||||||
User: admin Company: Qihoo 360 Technology Co. Ltd. Integrity Level: HIGH Description: File Smasher Application Exit code: 0 Version: 14, 0, 0, 1031 Modules
| |||||||||||||||
| 1056 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5180 -childID 6 -isForBrowser -prefsHandle 5216 -prefMapHandle 5220 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1296 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {1749f8f6-387d-43c6-a688-bb544ccd4d09} 2140 "\\.\pipe\gecko-crash-server-pipe.2140" 17083316bd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1272 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tcpvcon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | "C:\ProgramData\shark.exe" | C:\ProgramData\shark.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5772 -childID 11 -isForBrowser -prefsHandle 5760 -prefMapHandle 6048 -prefsLen 31324 -prefMapSize 244583 -jsInitHandle 1296 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {ee936943-d4f2-4a30-9196-c733f851dfea} 2140 "\\.\pipe\gecko-crash-server-pipe.2140" 17080622bd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2096 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4564 -childID 10 -isForBrowser -prefsHandle 5320 -prefMapHandle 5264 -prefsLen 31324 -prefMapSize 244583 -jsInitHandle 1296 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {3bb4d3f1-d7f8-4182-bd65-90a7d7909681} 2140 "\\.\pipe\gecko-crash-server-pipe.2140" 1707d4c7f50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2140 | "C:\Program Files\Mozilla Firefox\firefox.exe" crackdj.com | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2344 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7340 -s 832 | C:\Windows\SysWOW64\WerFault.exe | — | hjksfi.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5180 -childID 7 -isForBrowser -prefsHandle 5300 -prefMapHandle 5304 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1296 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {f4aa7f88-864c-4a6c-bbe1-b2b4f71e17c4} 2140 "\\.\pipe\gecko-crash-server-pipe.2140" 17083316d90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
50 232
Read events
50 058
Write events
162
Delete events
12
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:0000000000040304 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (2140) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppBadgeUpdated |
| Operation: | write | Name: | 308046B0AF4A39CB |
Value: 21 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000702B2 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
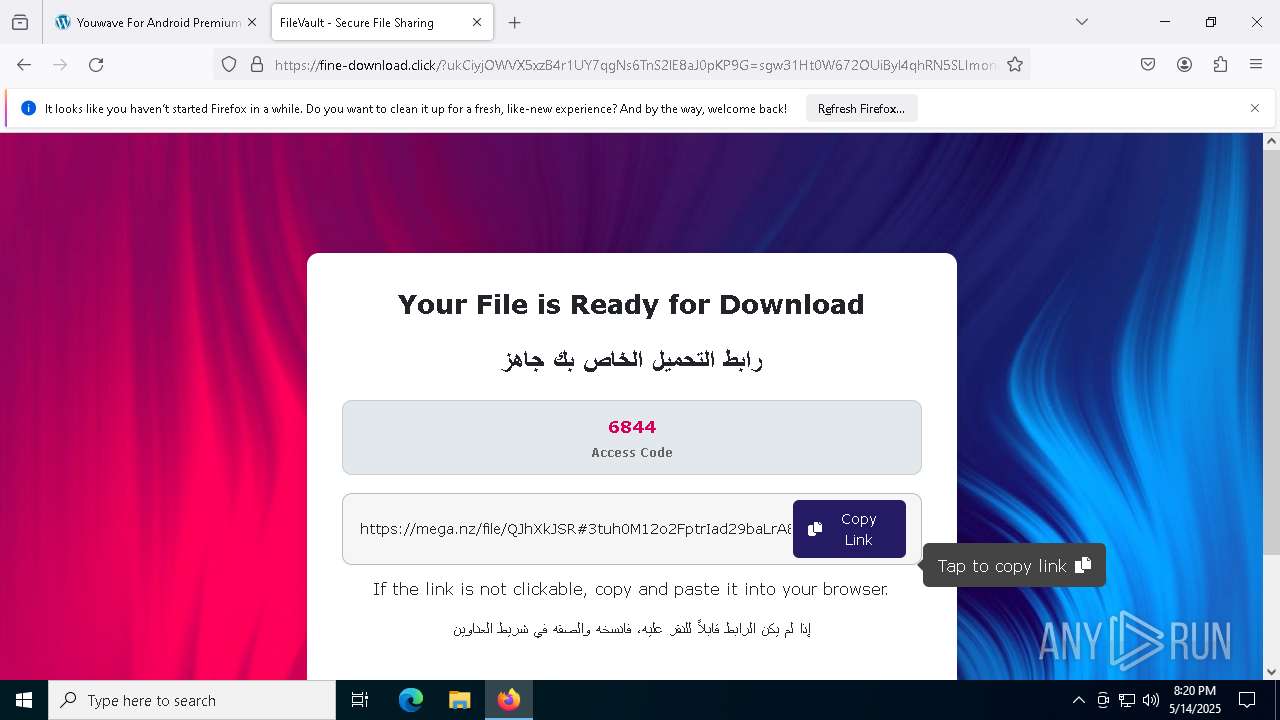
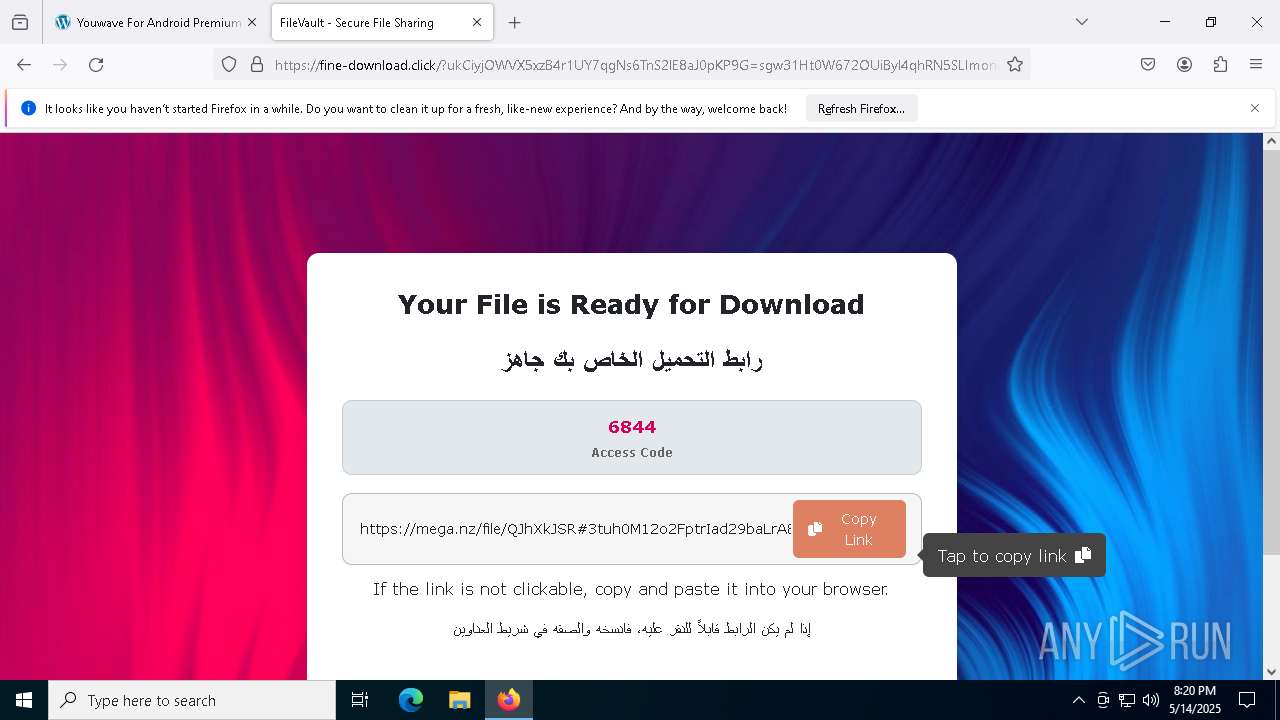
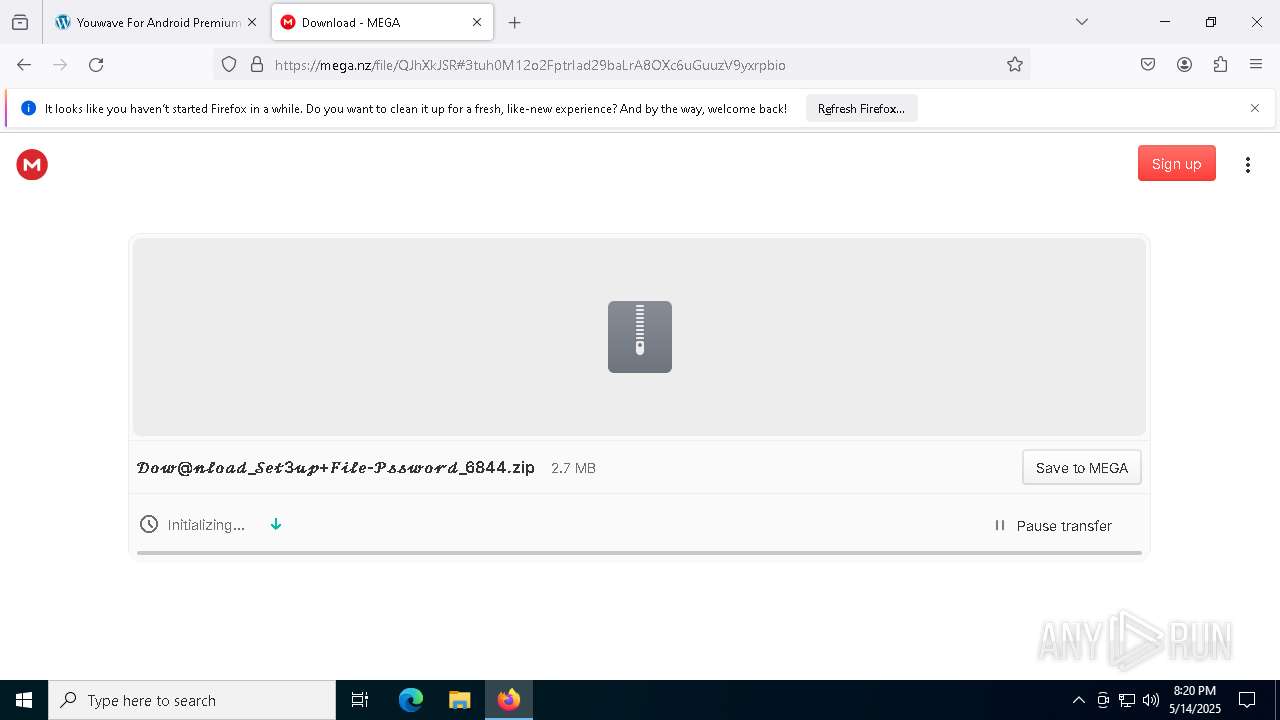
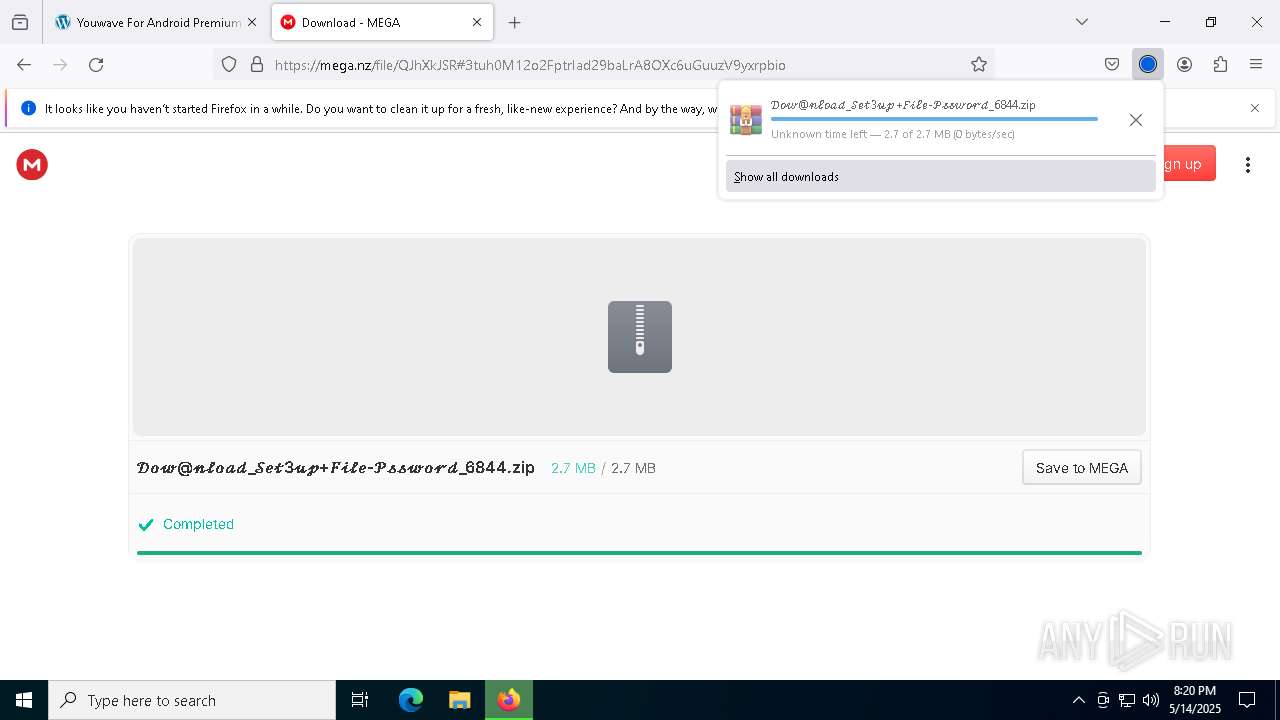
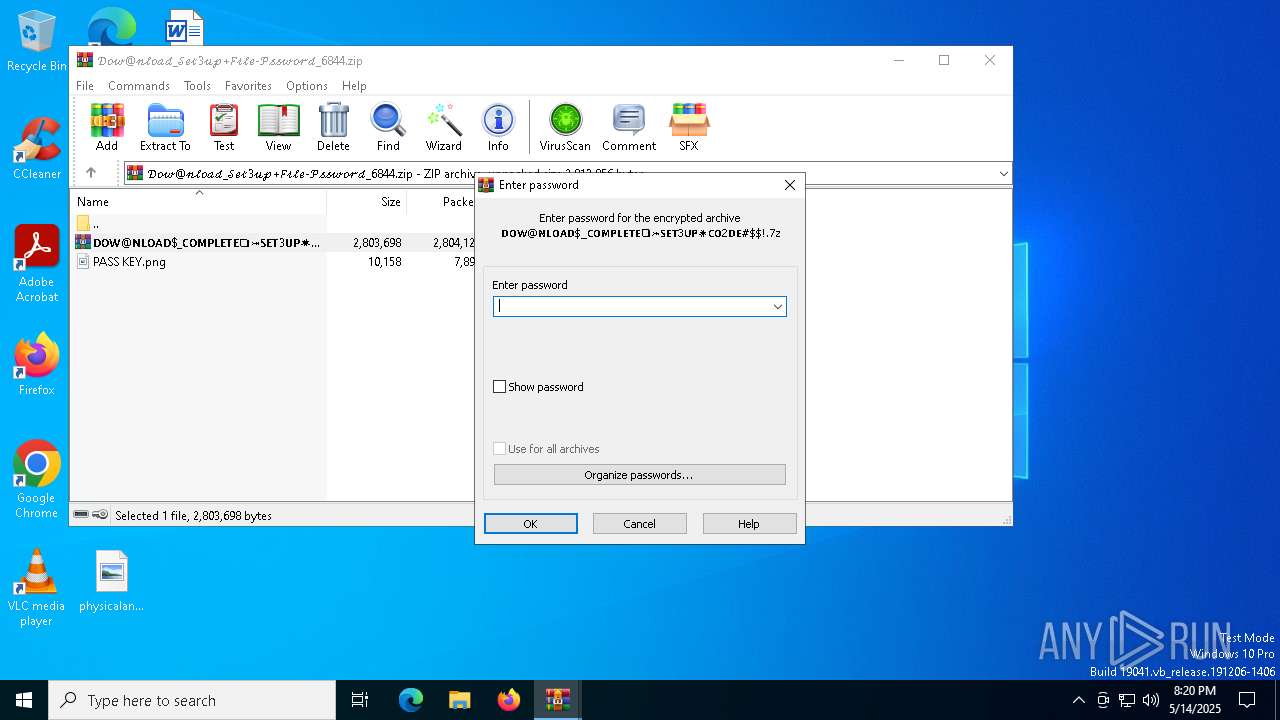
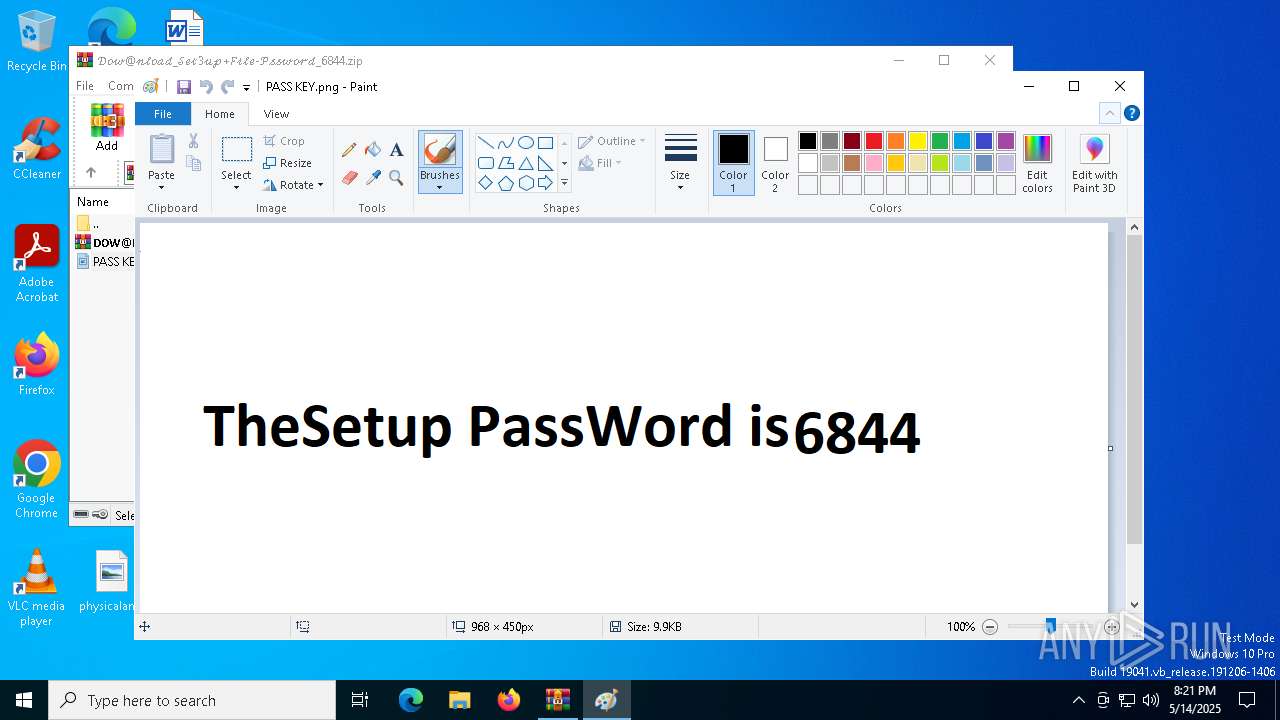
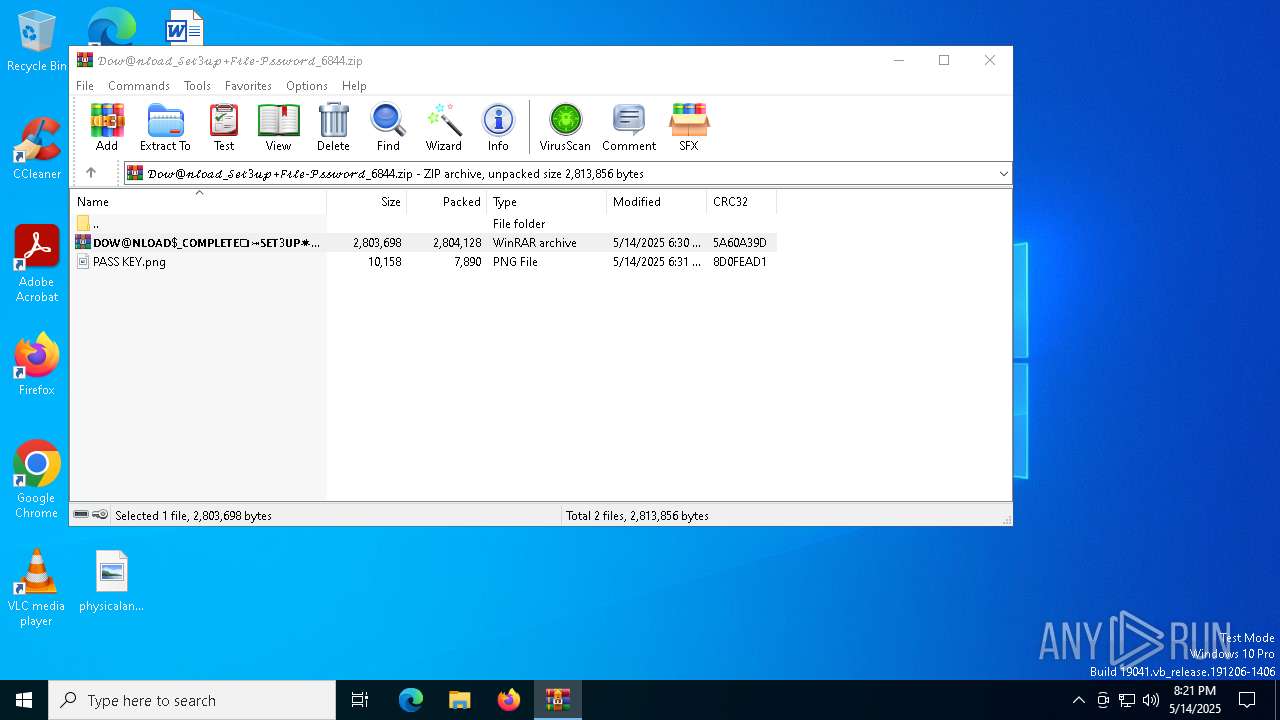
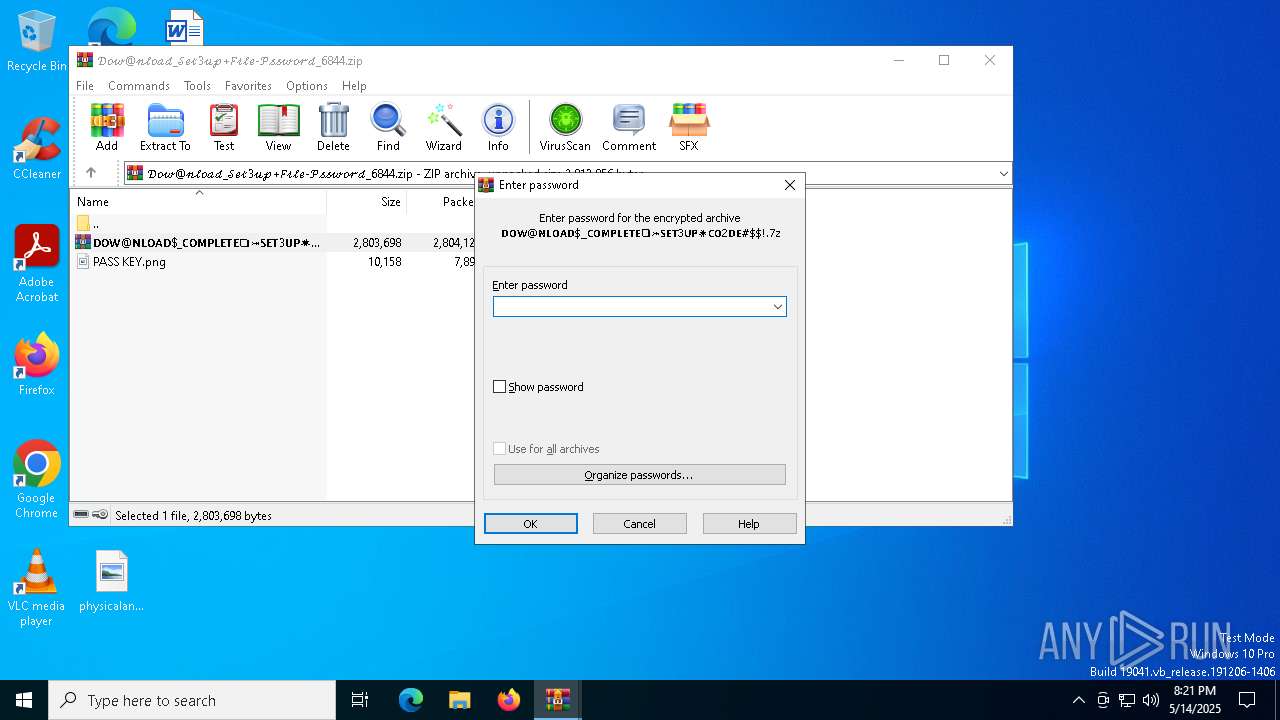
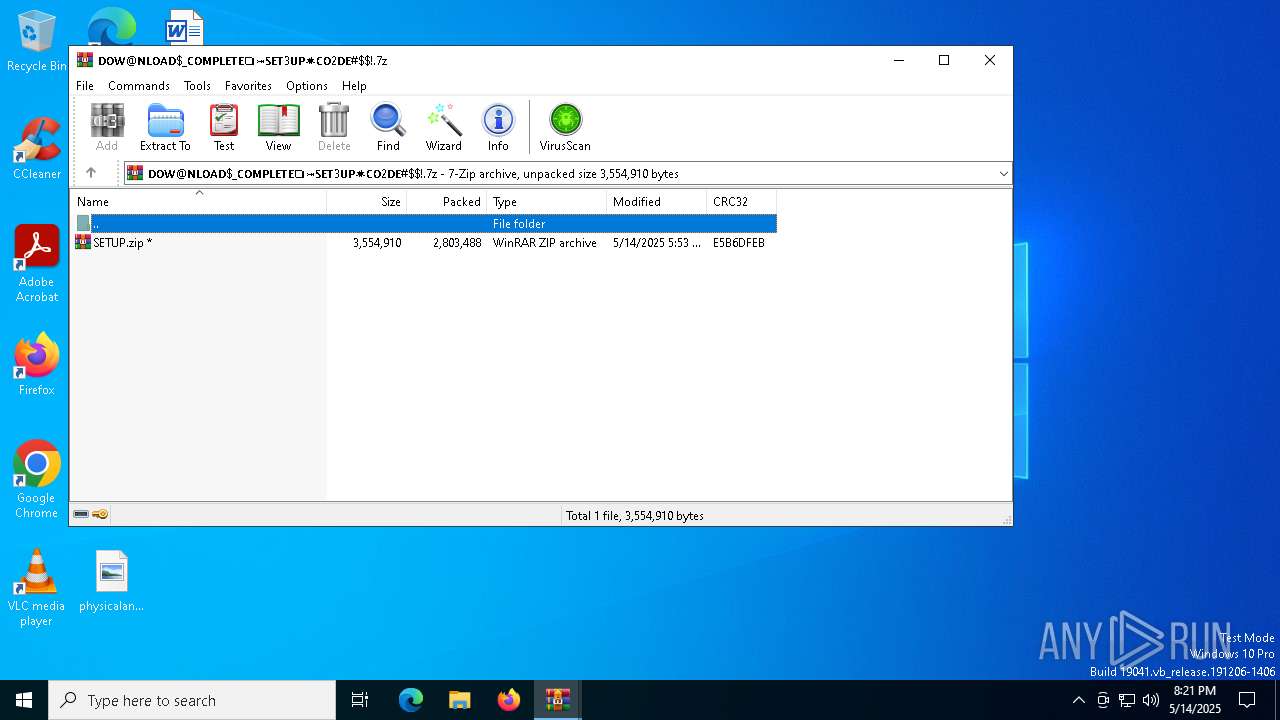
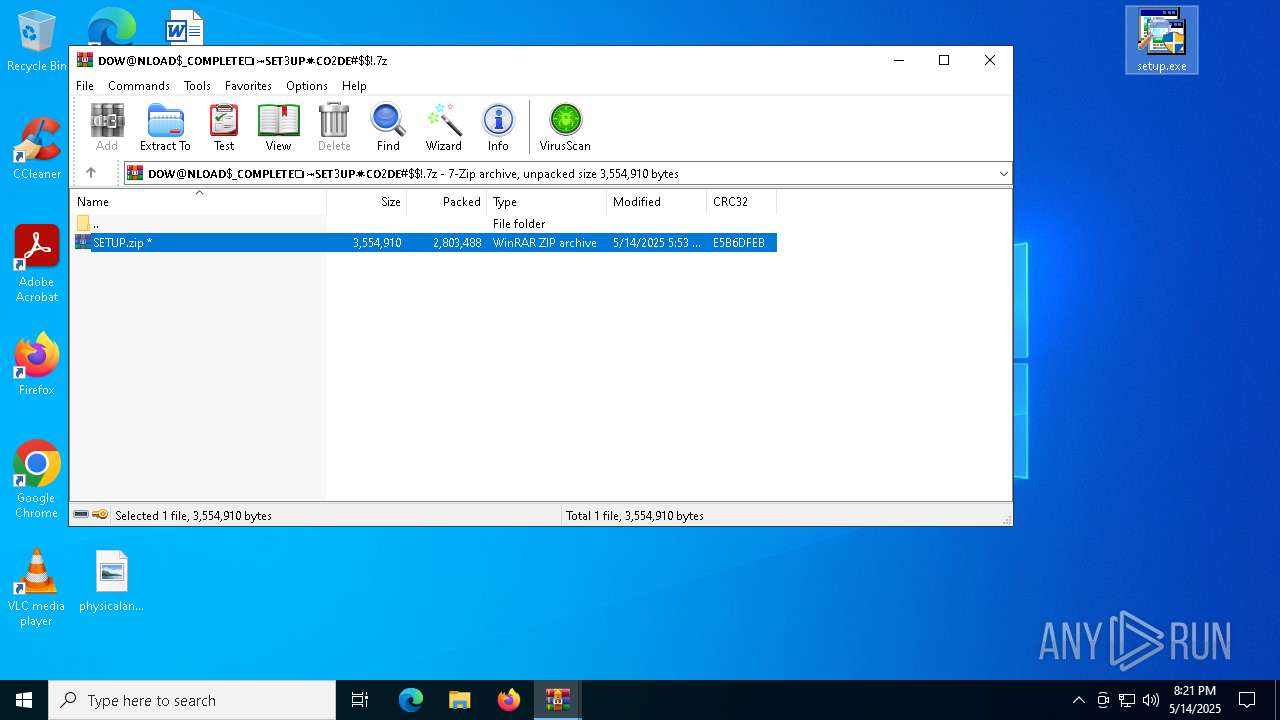
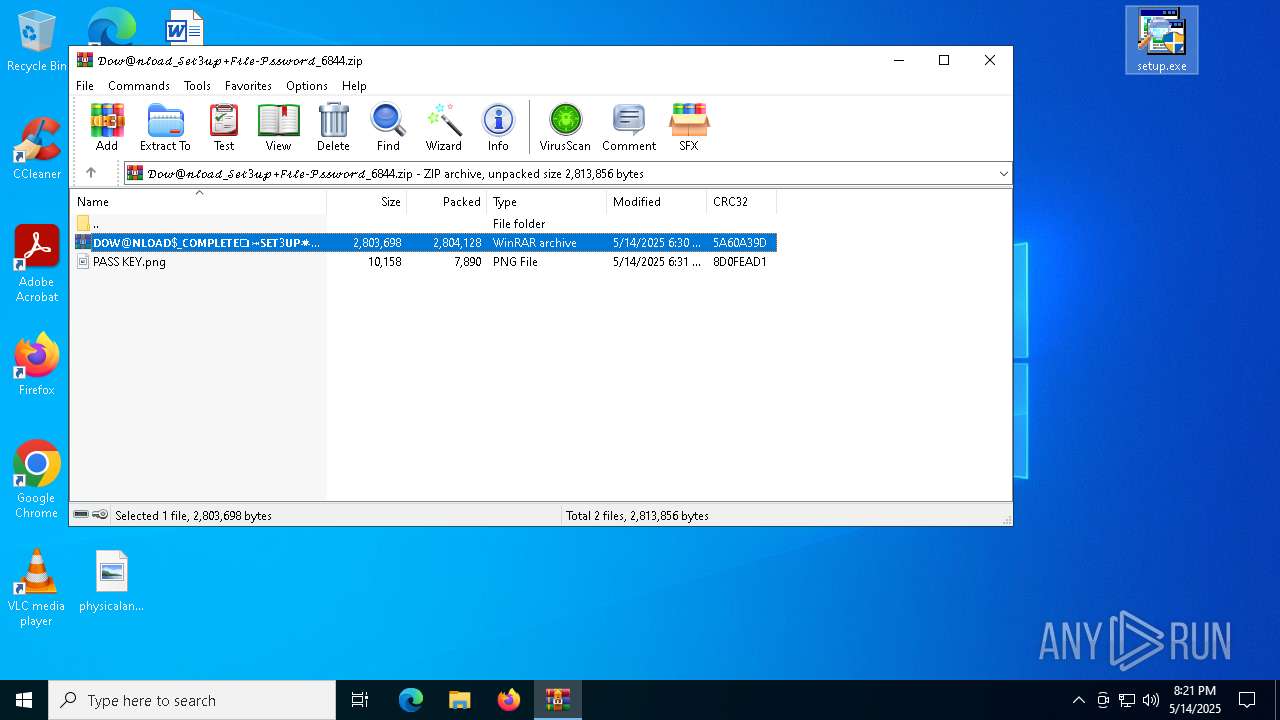
Value: C:\Users\admin\Downloads\𝒟𝑜𝓌@𝓃𝓁𝑜𝒶𝒹_𝒮𝑒𝓉3𝓊𝓅+𝐹𝒾𝓁𝑒-𝒫𝓈𝓈𝓌𝑜𝓇𝒹_6844.zip | |||
| (PID) Process: | (5324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
206
Suspicious files
221
Text files
23
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2140 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 5492 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\protections.sqlite-journal | binary | |
MD5:6F1323F5BCE8237CB7DBB6335D2075C1 | SHA256:7BEE1897FEC8E1077B502500032B57A38E9BD22E235D6FA3CAC0D40D53392C71 | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db-journal | binary | |
MD5:1E0A324653776E1DB691768925A94C8B | SHA256:30AD12E2D92B43107296366694543B0B490740014567A3F94447E12D612E8D3D | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db | binary | |
MD5:A260D8131A5C16A9E932767F48A52B3E | SHA256:FFCB958EB17C5BB02E3E0992E71B4E2836DAF4D8D271D824D51FEB48696E1FC9 | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
59
TCP/UDP connections
367
DNS requests
163
Threats
36
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2140 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
2140 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
2140 | firefox.exe | POST | 200 | 184.24.77.57:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
2140 | firefox.exe | POST | 200 | 184.24.77.57:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
2140 | firefox.exe | POST | 200 | 216.58.206.35:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
2140 | firefox.exe | GET | 301 | 188.114.97.3:80 | http://crackdj.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2140 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | — | — | whitelisted |
2140 | firefox.exe | 142.250.185.106:443 | safebrowsing.googleapis.com | — | — | whitelisted |
2140 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
crackdj.com |
| unknown |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |