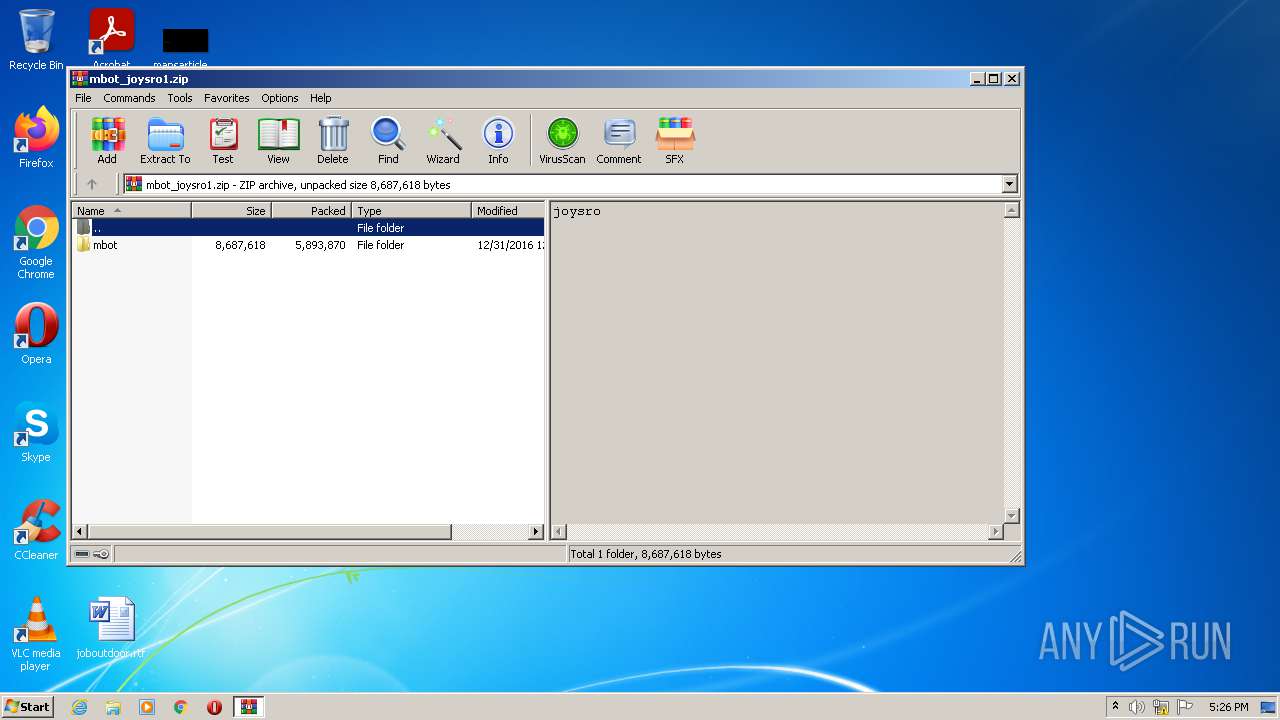
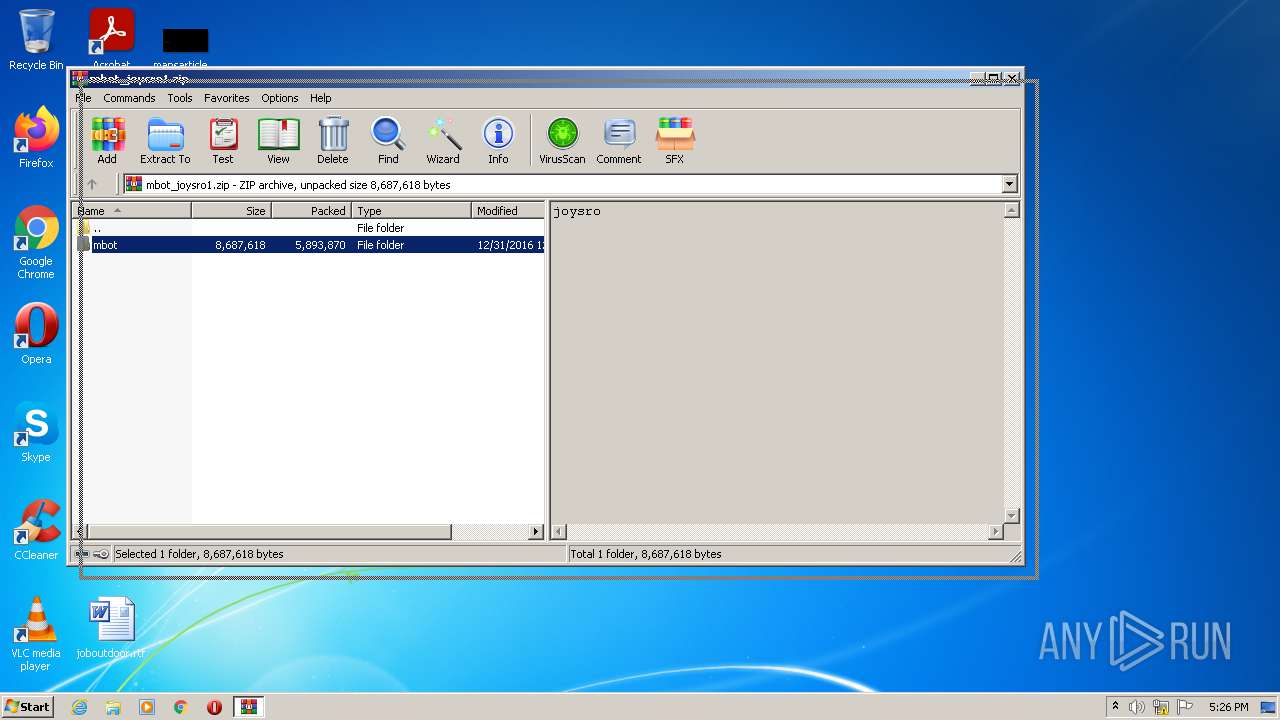
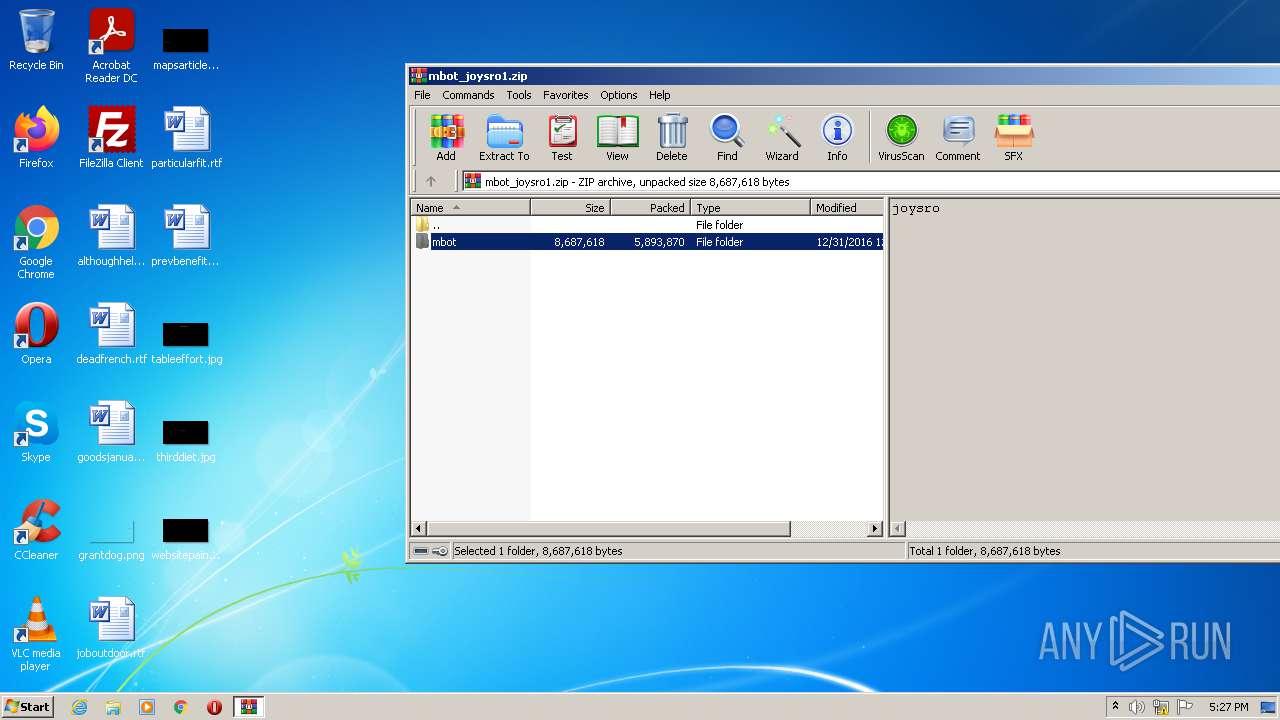
| File name: | mbot_joysro1.zip |
| Full analysis: | https://app.any.run/tasks/2fd5064f-41bd-4d6b-a46a-e5381776a482 |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2021, 16:26:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 2F2E21DF2A528DD230562DEEF2BB6EBA |
| SHA1: | F4B33AE91F1DB73BFFBC5F7D8D3B3EB5185E2F43 |
| SHA256: | E6978C4F4FEEC5D8C153EE0CC12FFC7DDF43BCC2E38178C57E353B4E728BB2BE |
| SSDEEP: | 98304:k32i9R3iZzSjQIBajCllV+MhFUmI4lzlaMd1OFjh0W8aauVevr660prteBvceTsy:k3xSZzSjNCilgQvlBOFjhX8aB8vr66o8 |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3708)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 1680)
Checks supported languages
- WinRAR.exe (PID: 1680)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1680)
Writes to a desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 1680)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 1680)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 1680)
Drops a file with too old compile date
- WinRAR.exe (PID: 1680)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | mbot/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2016:12:31 14:38:26 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
35
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1680 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\mbot_joysro1.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3708 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
Total events
1 688
Read events
1 675
Write events
13
Delete events
0
Modification events
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\mbot_joysro1.zip | |||
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
8
Suspicious files
0
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1680.17914\mbot\softdata.bin | text | |
MD5:— | SHA256:— | |||
| 1680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1680.17914\mbot\mBotLoader.exe | executable | |
MD5:34D0265ADB3093B9A792B0AE53294B24 | SHA256:2A49EF672F8BC67A39D7D66E645846380DF3BCD31E38EAFF85BFB63FEFC0861E | |||
| 1680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1680.17914\mbot\mBotCrack.dll | executable | |
MD5:45097BE0F7B5010A1A25DE470DD461EC | SHA256:6BFC916ECC15B4B9ED6888ABA5595DBFC67610A475276E3EBDC75FCDF9DA7A0F | |||
| 1680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1680.17914\mbot\pk2config.ini | ini | |
MD5:F84C2D34FFDB1D47BF79DB133281BE67 | SHA256:DD0932B3FB45F9882CC177BFBBB847439F2A4B574B97B8DB23E3C622FE6F7456 | |||
| 1680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1680.17914\mbot\psilk.dll | executable | |
MD5:F10823B20021569726929CBE2B3E9114 | SHA256:BCC0A22AABEA03511150C83E0573CE73D0035D2DF7FE3302D0CF499066AA6457 | |||
| 1680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1680.17914\mbot\merrsend.exe | executable | |
MD5:7BEEB35C3BDE8CAAB110B5DC3A45218C | SHA256:62738C3E6E2DC132DBCE415191383C64B76E460F80AF5714D7EF4A4ACEABC25A | |||
| 1680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1680.17914\mbot\chatBlock.txt | ini | |
MD5:C240A27B5954378745EFFAC898944C63 | SHA256:C9B520FBF28A8D9F2342B51D5A66CD4D191194B9D1BEB4C35F61A1ACDDB85E6C | |||
| 1680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1680.17914\mbot\desktop.ini | text | |
MD5:15478B340A8362BB79FD2A6EA0DDE1A0 | SHA256:27991CD3E2892702F610FD5262898F1C3DFA37E2A05082FD793BCE61E99E2D98 | |||
| 1680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1680.17914\mbot\config.ini | text | |
MD5:— | SHA256:— | |||
| 1680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1680.17914\mbot\picksettings.dat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report