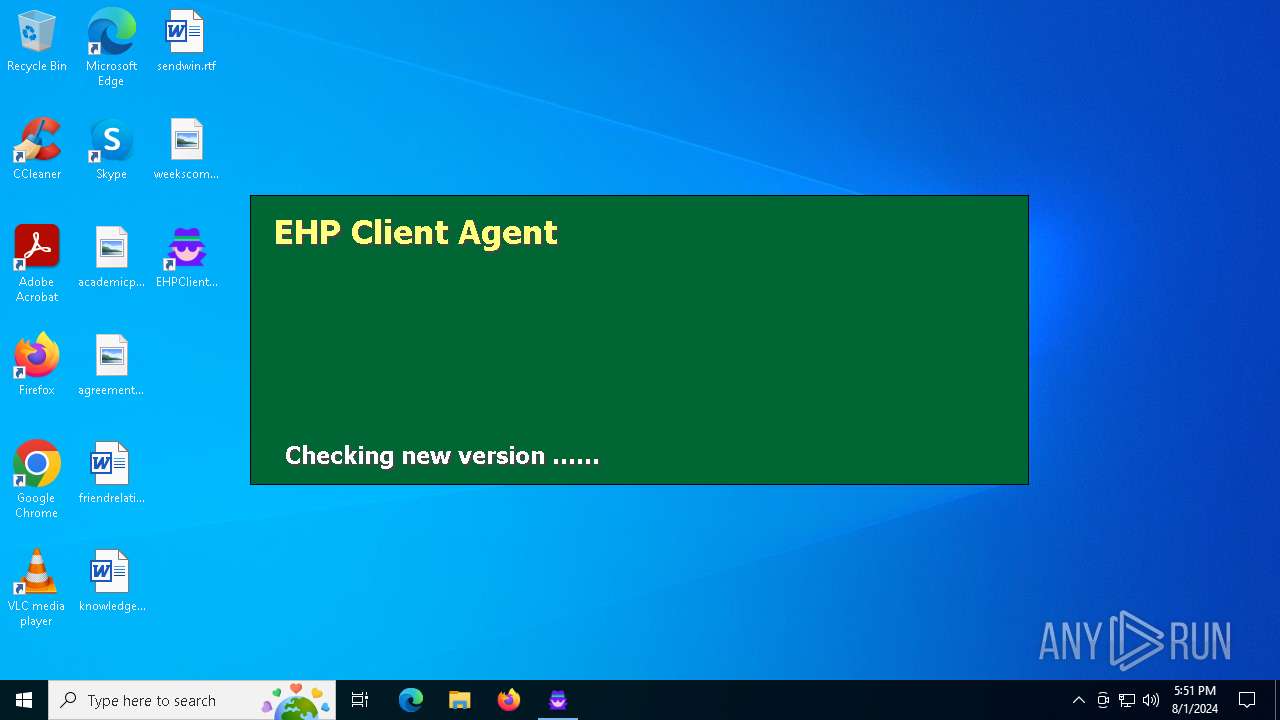
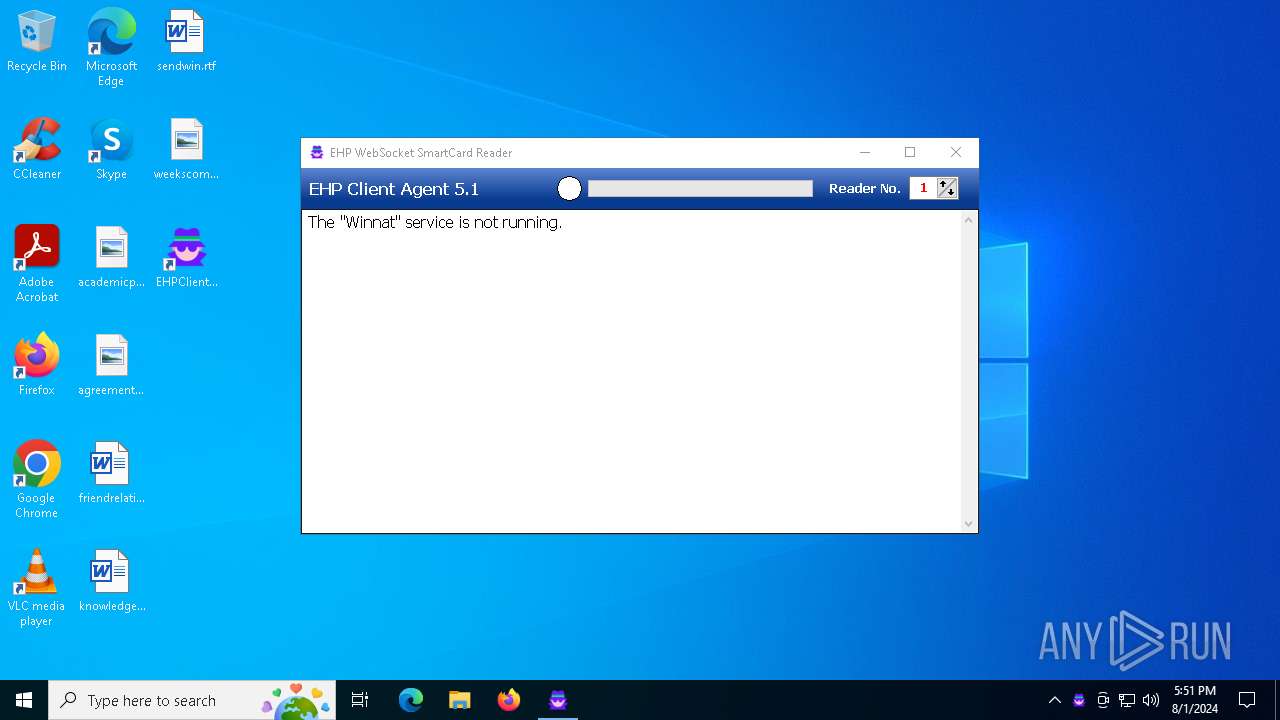
| File name: | SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417 |
| Full analysis: | https://app.any.run/tasks/e27841a4-3547-46f6-a1c8-4fdfabbd08cb |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2024, 17:51:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | B7CFA25321334064893666ECC2BCF9DA |
| SHA1: | 5829E85E9BB196A42D71B83206D777951DD7F90E |
| SHA256: | E6947908ECFA3F110FE380E07A2941E1B558E12F0481EA8B6075658B06661262 |
| SSDEEP: | 98304:vAyWw3S+ZxIIwKCPgB9YFHxqDom/wmUyD8wM2QrR+JobXjcVeI01Qi6eiEKLsM0N:7qYVTRY7DrwxZi/IMW09ve38 |
MALICIOUS
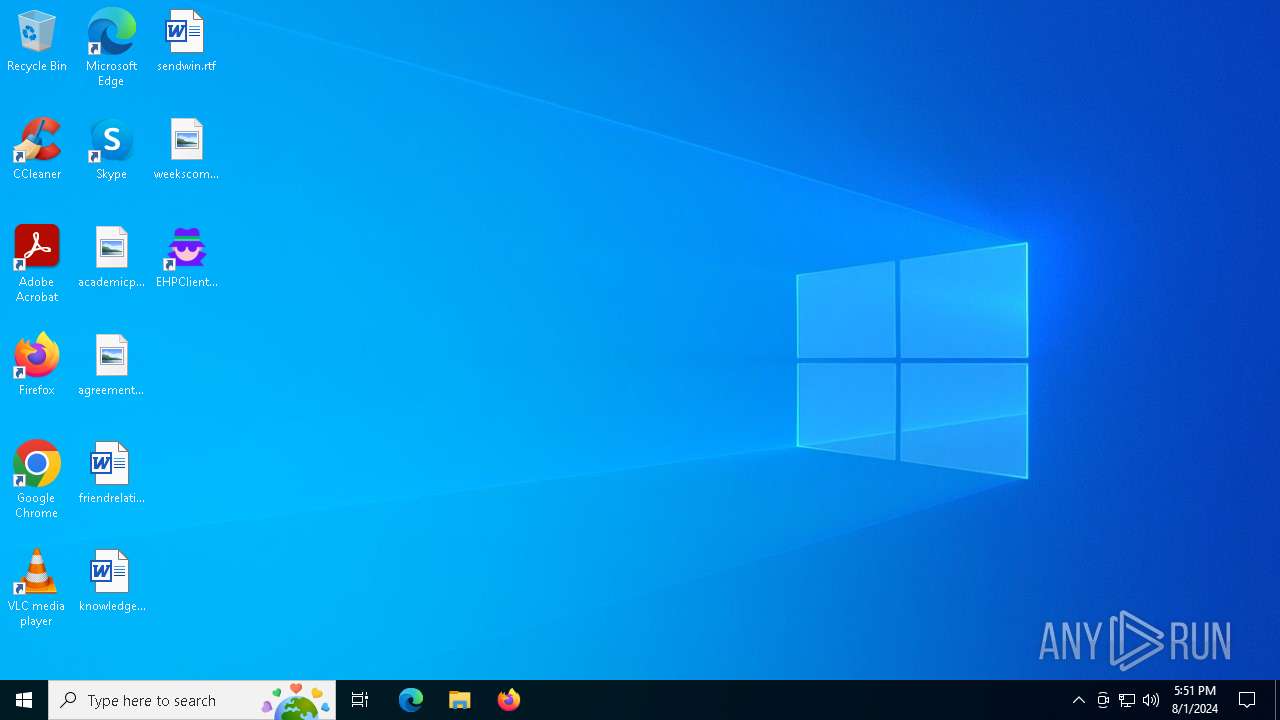
Drops the executable file immediately after the start
- SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe (PID: 6404)
- EHPClientAgent.exe (PID: 6520)
Changes the autorun value in the registry
- EHPClientAgent.exe (PID: 6520)
SUSPICIOUS
Executable content was dropped or overwritten
- SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe (PID: 6404)
- EHPClientAgent.exe (PID: 6520)
Read disk information to detect sandboxing environments
- EHPClientAgent.exe (PID: 6520)
Reads the date of Windows installation
- EHPClientAgent.exe (PID: 6520)
INFO
Reads the computer name
- SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe (PID: 6404)
- EHPClientAgent.exe (PID: 6520)
Checks supported languages
- SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe (PID: 6404)
- EHPClientAgent.exe (PID: 6520)
Reads Environment values
- EHPClientAgent.exe (PID: 6520)
- SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe (PID: 6404)
Reads product name
- EHPClientAgent.exe (PID: 6520)
Create files in a temporary directory
- EHPClientAgent.exe (PID: 6520)
- SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe (PID: 6404)
Creates files or folders in the user directory
- EHPClientAgent.exe (PID: 6520)
- SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe (PID: 6404)
Reads CPU info
- EHPClientAgent.exe (PID: 6520)
Reads security settings of Internet Explorer
- splwow64.exe (PID: 6868)
Dropped object may contain TOR URL's
- EHPClientAgent.exe (PID: 6520)
Reads the machine GUID from the registry
- EHPClientAgent.exe (PID: 6520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 22:50:41+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23040 |
| InitializedDataSize: | 119808 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30cb |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.65.8.8 |
| ProductVersionNumber: | 4.65.8.8 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | ASCII |
| Comments: | EHP |
| CompanyName: | EHP |
| FileDescription: | EHP |
| FileVersion: | 4.65.8.8 |
| LegalCopyright: | EHP |
| LegalTrademarks: | EHP |
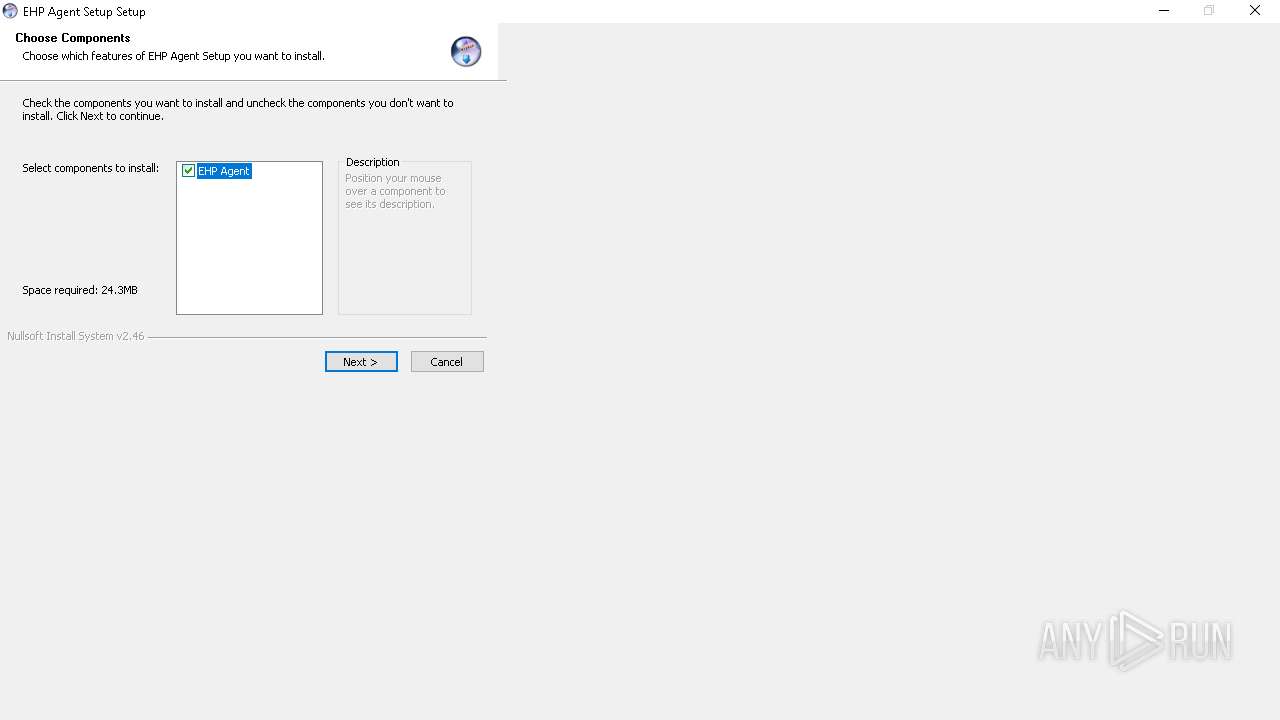
| ProductName: | EHP Agent Installer |
Total processes
134
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6352 | "C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe" | C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe | — | explorer.exe | |||||||||||
User: admin Company: EHP Integrity Level: MEDIUM Description: EHP Exit code: 3221226540 Version: 4.65.8.8 Modules
| |||||||||||||||
| 6404 | "C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe" | C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe | explorer.exe | ||||||||||||
User: admin Company: EHP Integrity Level: HIGH Description: EHP Exit code: 0 Version: 4.65.8.8 Modules
| |||||||||||||||
| 6520 | "C:\Users\admin\AppData\Roaming\EHPAgent\EHPClientAgent.exe" | C:\Users\admin\AppData\Roaming\EHPAgent\EHPClientAgent.exe | SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 4.66.11.8 Modules
| |||||||||||||||
| 6868 | C:\WINDOWS\splwow64.exe 12288 | C:\Windows\splwow64.exe | — | EHPClientAgent.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 823
Read events
12 821
Write events
2
Delete events
0
Modification events
| (PID) Process: | (6520) EHPClientAgent.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | EHPAgent |
Value: C:\Users\admin\AppData\Roaming\EHPAgent\EHPClientAgent.exe | |||
| (PID) Process: | (6868) splwow64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\splwow64.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 18800E0000000000 | |||
Executable files
4
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6520 | EHPClientAgent.exe | C:\Users\admin\AppData\Local\Temp\TBMS_HOSXP_CURL_ZIP.zip | compressed | |
MD5:0A1FD9B962CD528CA62755DE06F125F5 | SHA256:E2AF03E37E9270A2AECB9C9B729F71A181B7A8308E2767D3894D96C3FFFB786F | |||
| 6520 | EHPClientAgent.exe | C:\Users\admin\AppData\Roaming\EHPAgent\libcurl.dll | executable | |
MD5:1DDF9C18A892A7225045900C18A4C351 | SHA256:BEC0BED6B3418DF6681D4607E223CD0833E99E4EBE5BC988FD8D8EA6097D8085 | |||
| 6404 | SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\EHPClientAgent.lnk | binary | |
MD5:2E9C2C4DA0B3C3F6AA679CCA9E463616 | SHA256:38E72052453CAF801A56A55A8AA8AD6C5FCB19825F5DCDBCE3D6CEB4E7253F72 | |||
| 6404 | SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe | C:\Users\admin\Desktop\EHPClientAgent.lnk | binary | |
MD5:B6C5156DF0B9FC7854820AE034C472FB | SHA256:CD32CF882187E86D7EEFF2B82F661778BF3D2203276450CE4F3416D645134160 | |||
| 6404 | SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe | C:\Users\admin\AppData\Local\Temp\nsf6176.tmp\Processes.dll | executable | |
MD5:2CFBA79D485CF441C646DD40D82490FC | SHA256:86B302FA9C85DFA0C1C03BA000864A928365DAB571F3355347DBA02DA22949B7 | |||
| 6404 | SecuriteInfo.com.HEUR.Trojan.Win32.Agent.gen.21445.28417.exe | C:\Users\admin\AppData\Roaming\EHPAgent\EHPClientAgent.exe | executable | |
MD5:A12C1A66F564BBFE82A3F0021E24523D | SHA256:339141CFB67D734009258B9B96BC41CDB1FA8BBB295E5697390B3720FB72D555 | |||
| 6520 | EHPClientAgent.exe | C:\Users\admin\AppData\Roaming\EHPAgent\curl.exe | executable | |
MD5:075212860CB6E69EB5C991044FE5E29C | SHA256:E484DD4374163B32EBEF913A769324649C2E663144B4673185FC7B3E0A903A62 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
43
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7164 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7100 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4708 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2088 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6520 | EHPClientAgent.exe | 203.151.166.226:443 | cloud3.hosxp.net | Internet Thailand Company Limited | TH | unknown |
5336 | SearchApp.exe | 104.126.37.171:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2272 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
cloud3.hosxp.net |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |