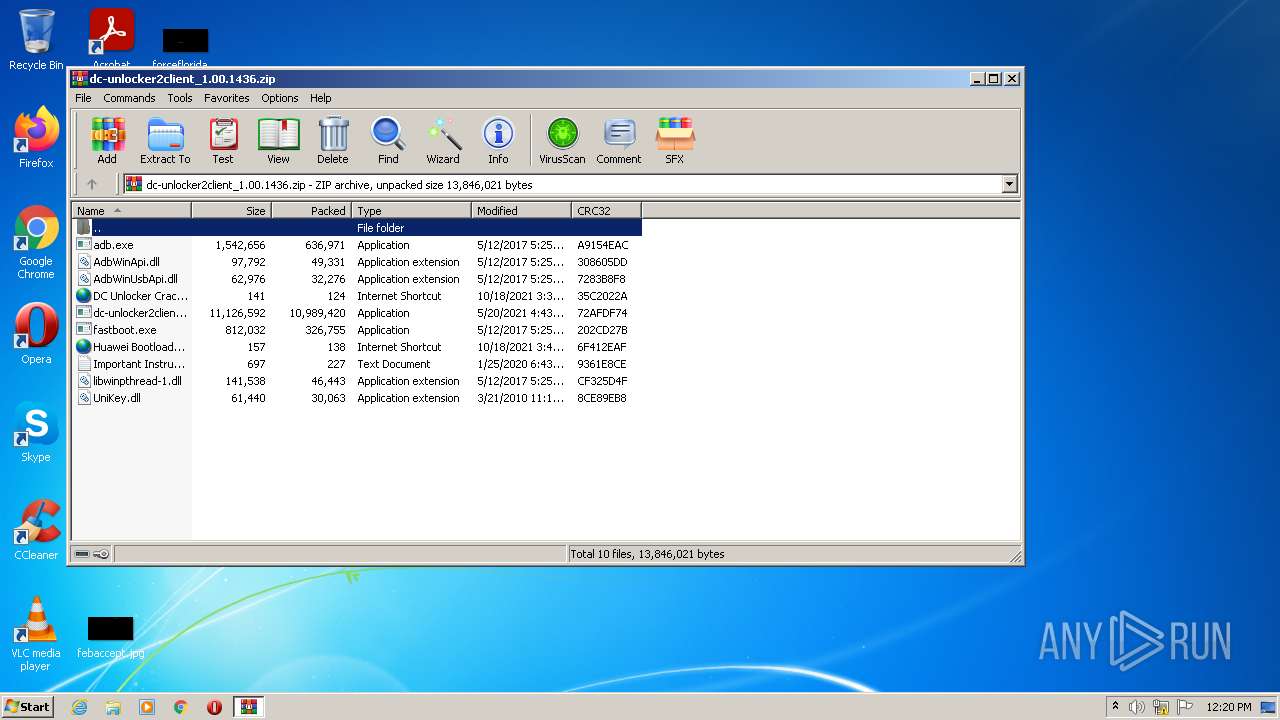
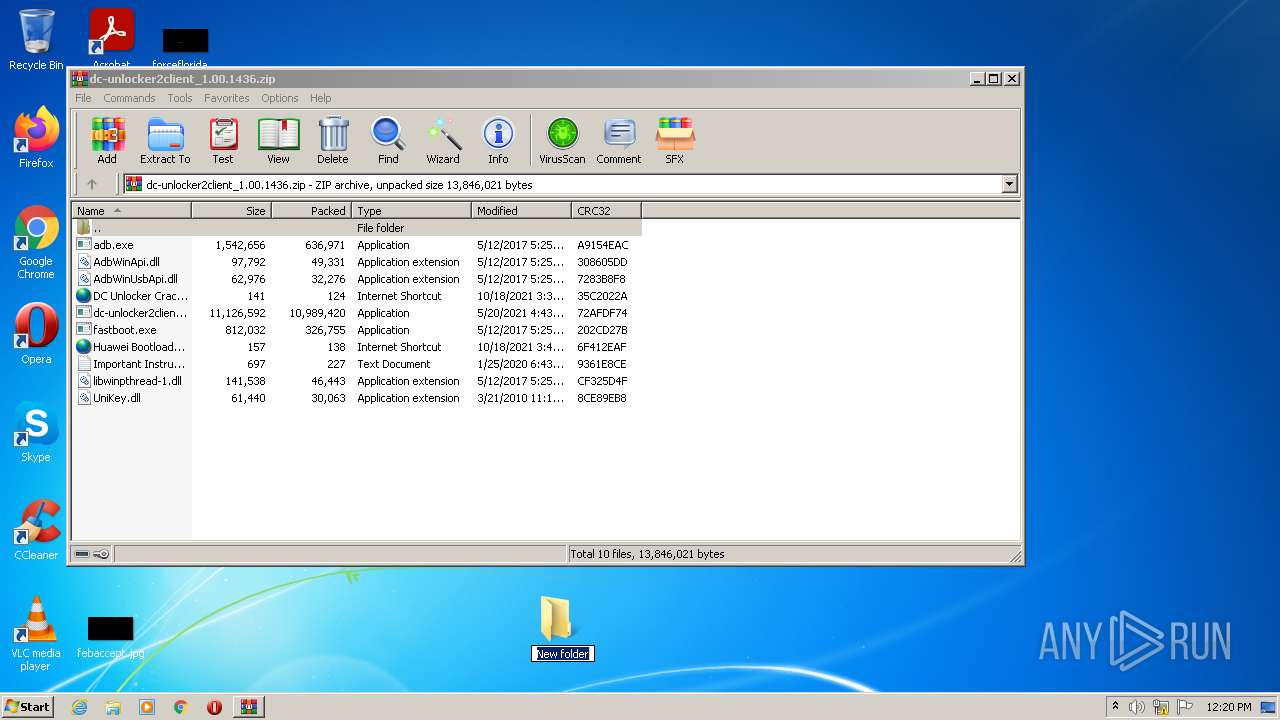
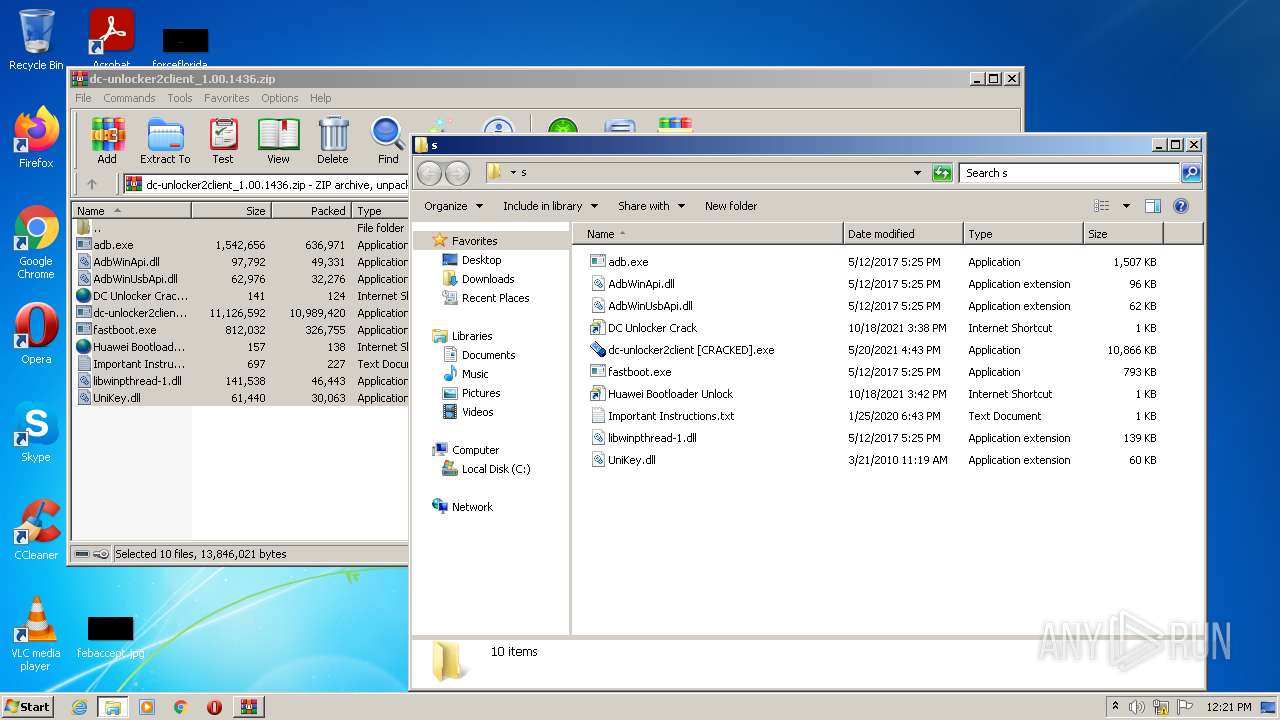
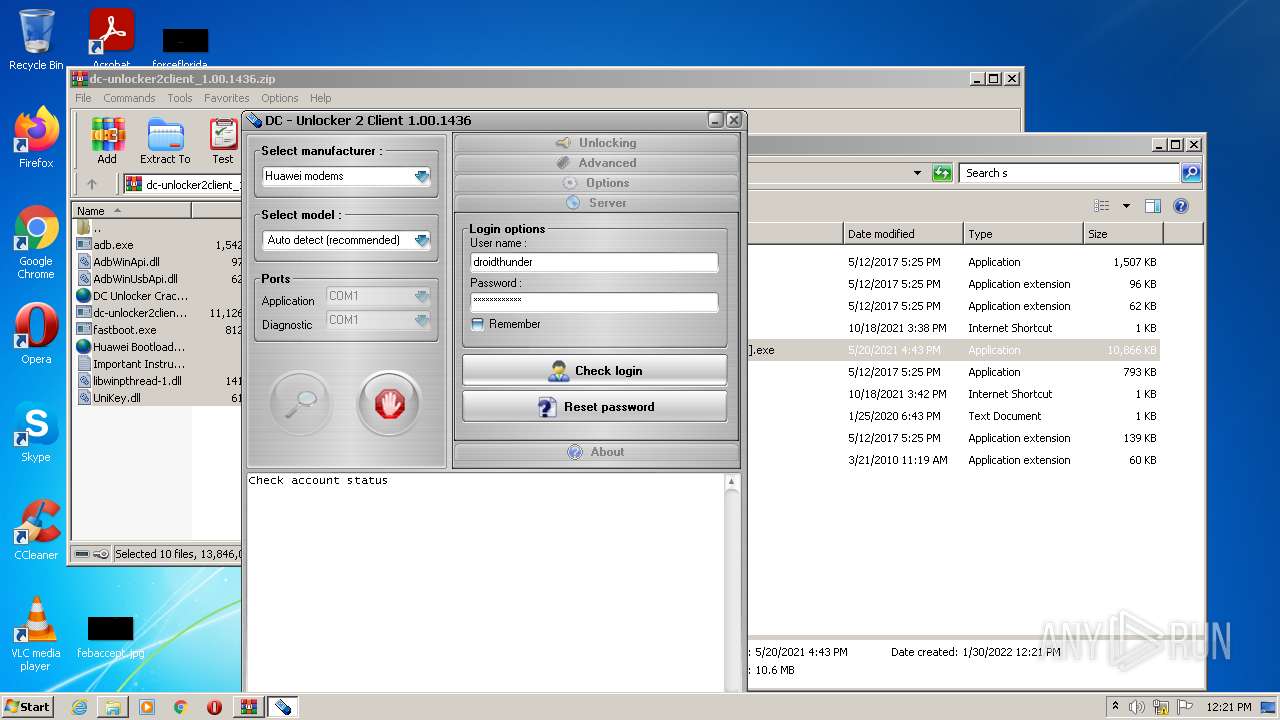
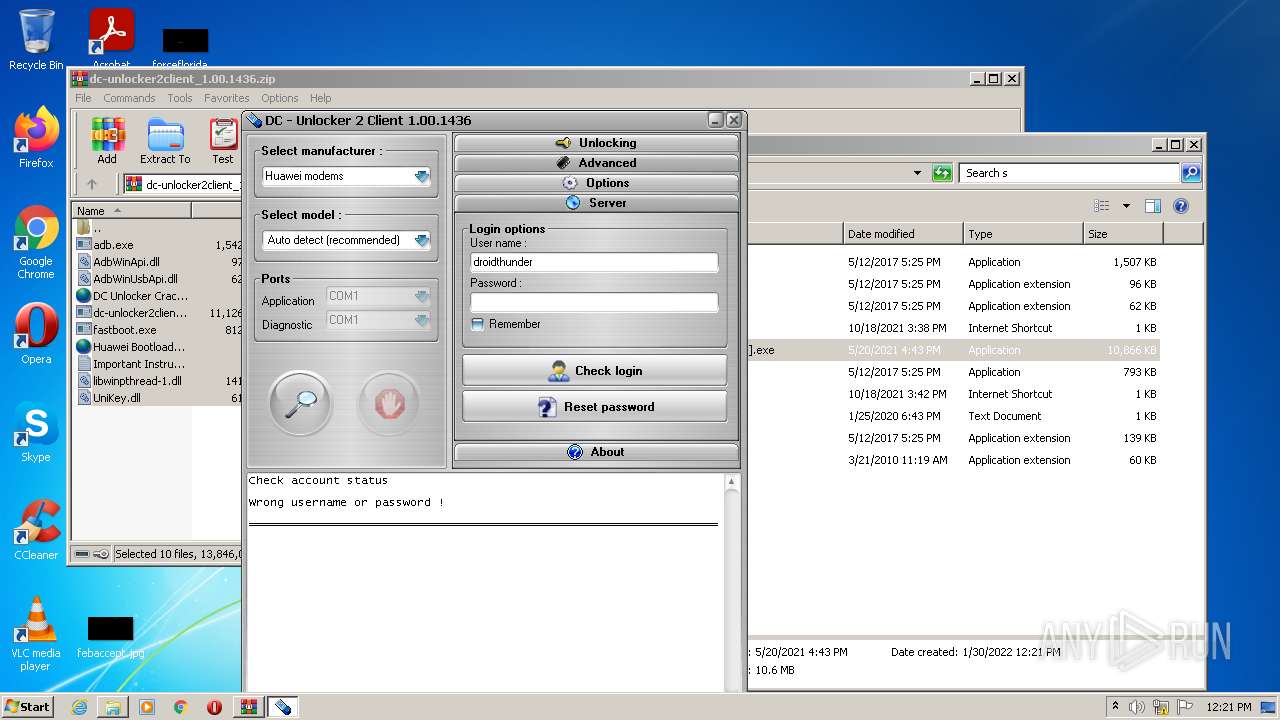
| File name: | dc-unlocker2client_1.00.1436.zip |
| Full analysis: | https://app.any.run/tasks/7d79cd69-dae2-4956-85b8-266fe5b9a816 |
| Verdict: | Malicious activity |
| Analysis date: | January 30, 2022, 12:20:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 130C0F7E805DA2FD2A0B718CB1E1A848 |
| SHA1: | 30FFD3CDA3533A453ED6F5952558DA6D1F28C35A |
| SHA256: | E6908C6B1C0BDA1E8505B25546B5128C1700D03803D5E47BA09B80C9D6C44D0C |
| SSDEEP: | 196608:hyfGa8ZGeD+JmjZNLtbZO+e3S7qogT/zI2OPKT/5aoRZ1P8iJXdI9IZ1MnJvYNBZ:hyfGa8AyHZNLtbfe3S7kzzI2kSNZGiJz |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3076)
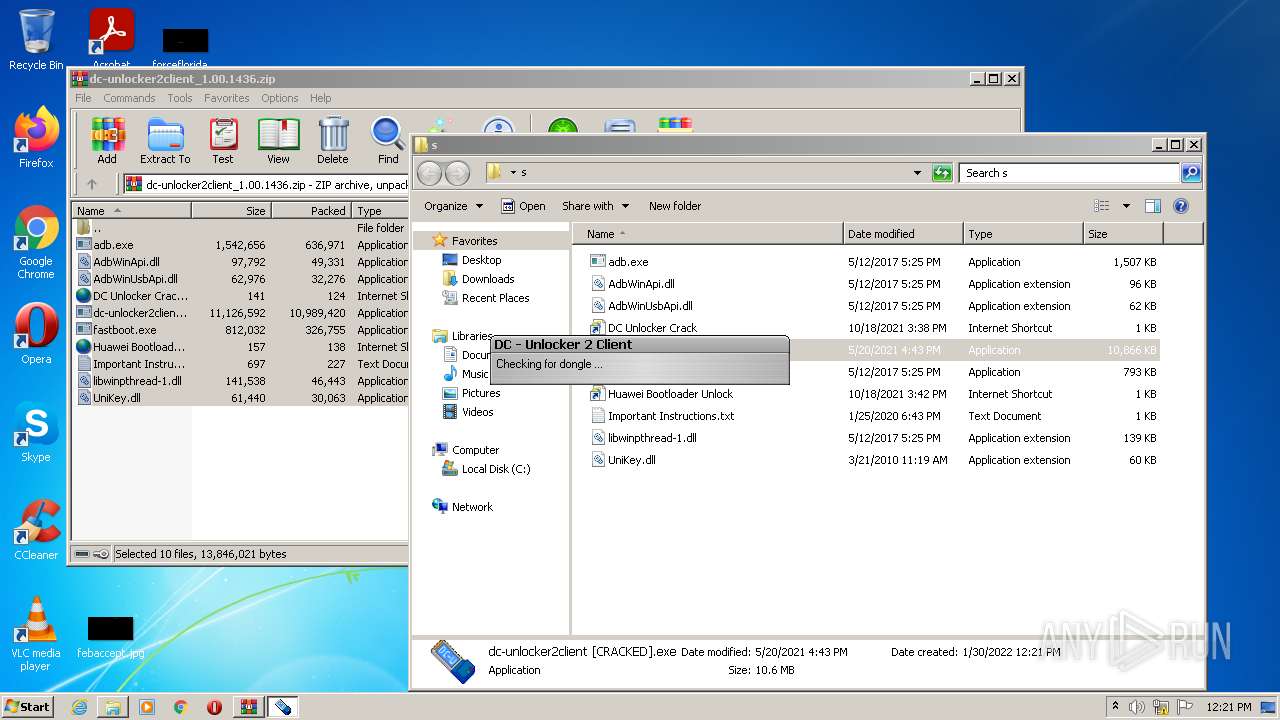
- dc-unlocker2client [CRACKED].exe (PID: 2328)
Application was dropped or rewritten from another process
- dc-unlocker2client [CRACKED].exe (PID: 2328)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3120)
- dc-unlocker2client [CRACKED].exe (PID: 2328)
- cmd.exe (PID: 3820)
Reads the computer name
- WinRAR.exe (PID: 3120)
- dc-unlocker2client [CRACKED].exe (PID: 2328)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3120)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3120)
Drops a file with too old compile date
- WinRAR.exe (PID: 3120)
Starts CMD.EXE for commands execution
- dc-unlocker2client [CRACKED].exe (PID: 2328)
INFO
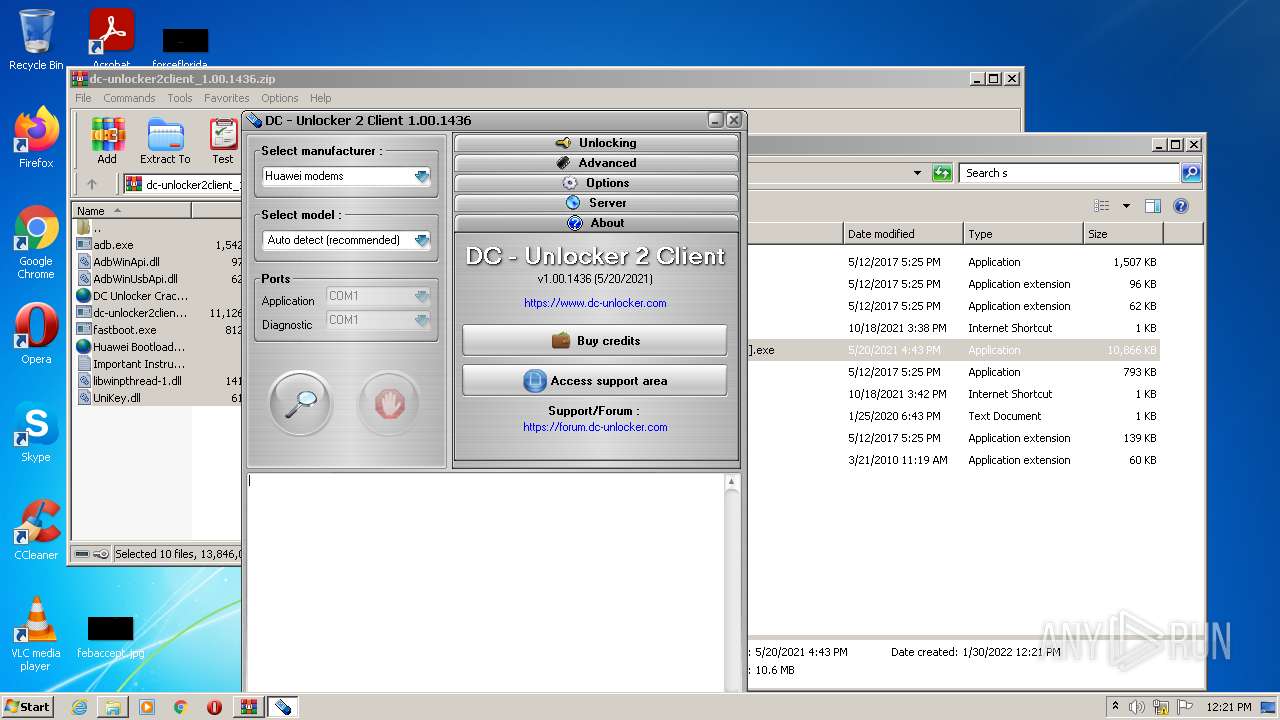
Manual execution by user
- dc-unlocker2client [CRACKED].exe (PID: 2328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | adb.exe |
|---|---|
| ZipUncompressedSize: | 1542656 |
| ZipCompressedSize: | 636971 |
| ZipCRC: | 0xa9154eac |
| ZipModifyDate: | 2017:05:12 21:55:02 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
38
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2328 | "C:\Users\admin\Desktop\s\dc-unlocker2client [CRACKED].exe" | C:\Users\admin\Desktop\s\dc-unlocker2client [CRACKED].exe | Explorer.EXE | ||||||||||||
User: admin Company: UAB Digiteka Integrity Level: MEDIUM Description: Data Card Unlocker client software Exit code: 0 Version: 1.0.0.1436 Modules
| |||||||||||||||
| 3076 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 3120 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\dc-unlocker2client_1.00.1436.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3820 | cmd.exe /C ver | C:\Windows\system32\cmd.exe | — | dc-unlocker2client [CRACKED].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 489
Read events
2 453
Write events
36
Delete events
0
Modification events
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\dc-unlocker2client_1.00.1436.zip | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
7
Suspicious files
0
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3120.41898\Huawei Bootloader Unlock.url | url | |
MD5:— | SHA256:— | |||
| 3120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3120.41898\dc-unlocker2client [CRACKED].exe | executable | |
MD5:— | SHA256:— | |||
| 3120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3120.41898\DC Unlocker Crack.url | url | |
MD5:— | SHA256:— | |||
| 3120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3120.41898\UniKey.dll | executable | |
MD5:— | SHA256:— | |||
| 3120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3120.41898\Important Instructions.txt | text | |
MD5:— | SHA256:— | |||
| 3120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3120.41898\fastboot.exe | executable | |
MD5:CC023BC3427CBDFE115A7F32084B8272 | SHA256:8E2BE00D58D7C5792C3C57033184B61406D73CA2EFFA5C65F1706488B9CC6CDD | |||
| 3120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3120.41898\adb.exe | executable | |
MD5:DEC7E5E645ADED51F9D7F02D60E9ED41 | SHA256:A3887975396C74B6D4BDB49D2030881165E09B4ED89B0C7BBAF4B821D44D4643 | |||
| 3120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3120.41898\AdbWinApi.dll | executable | |
MD5:ED5A809DC0024D83CBAB4FB9933D598D | SHA256:D60103A5E99BC9888F786EE916F5D6E45493C3247972CB053833803DE7E95CF9 | |||
| 3120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3120.41898\AdbWinUsbApi.dll | executable | |
MD5:0E24119DAF1909E398FA1850B6112077 | SHA256:25207C506D29C4E8DCEB61B4BD50E8669BA26012988A43FBF26A890B1E60FC97 | |||
| 3120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3120.41898\libwinpthread-1.dll | executable | |
MD5:27B901BB44C6E3417BAEEE03C9CDC4BF | SHA256:83D6E9CB6151C9ECDB330ED9CCDA7CAB7F27E5F1585D494954526A17FF69D02E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
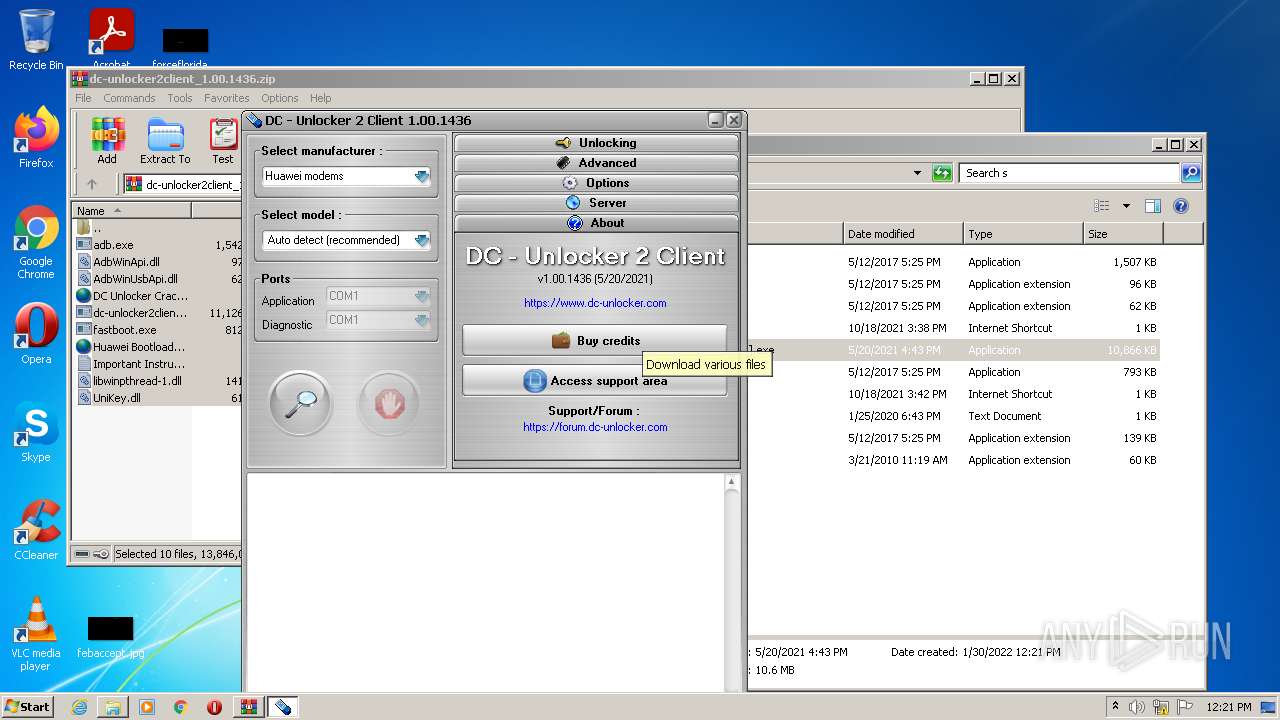
2328 | dc-unlocker2client [CRACKED].exe | 89.116.151.215:443 | server1.dc-unlocker.com | SC Lithuanian Radio and TV Center | LT | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
server1.dc-unlocker.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2328 | dc-unlocker2client [CRACKED].exe | Generic Protocol Command Decode | SURICATA Applayer Wrong direction first Data |