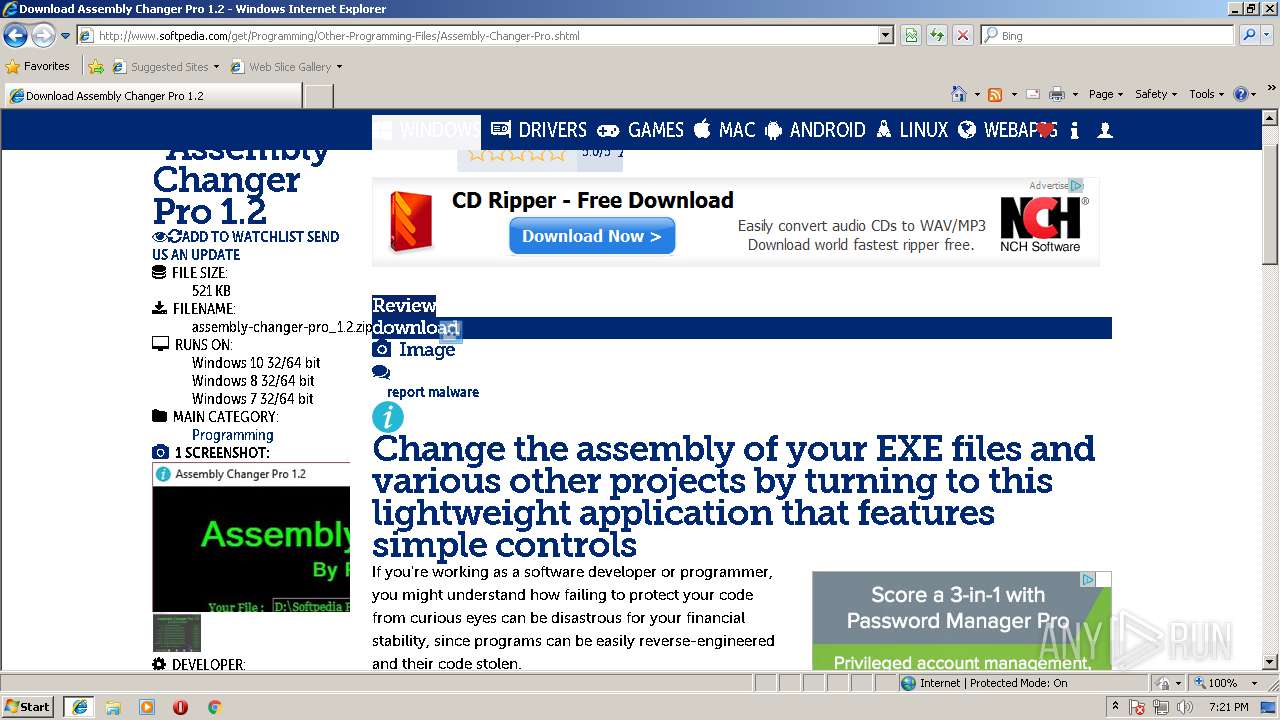
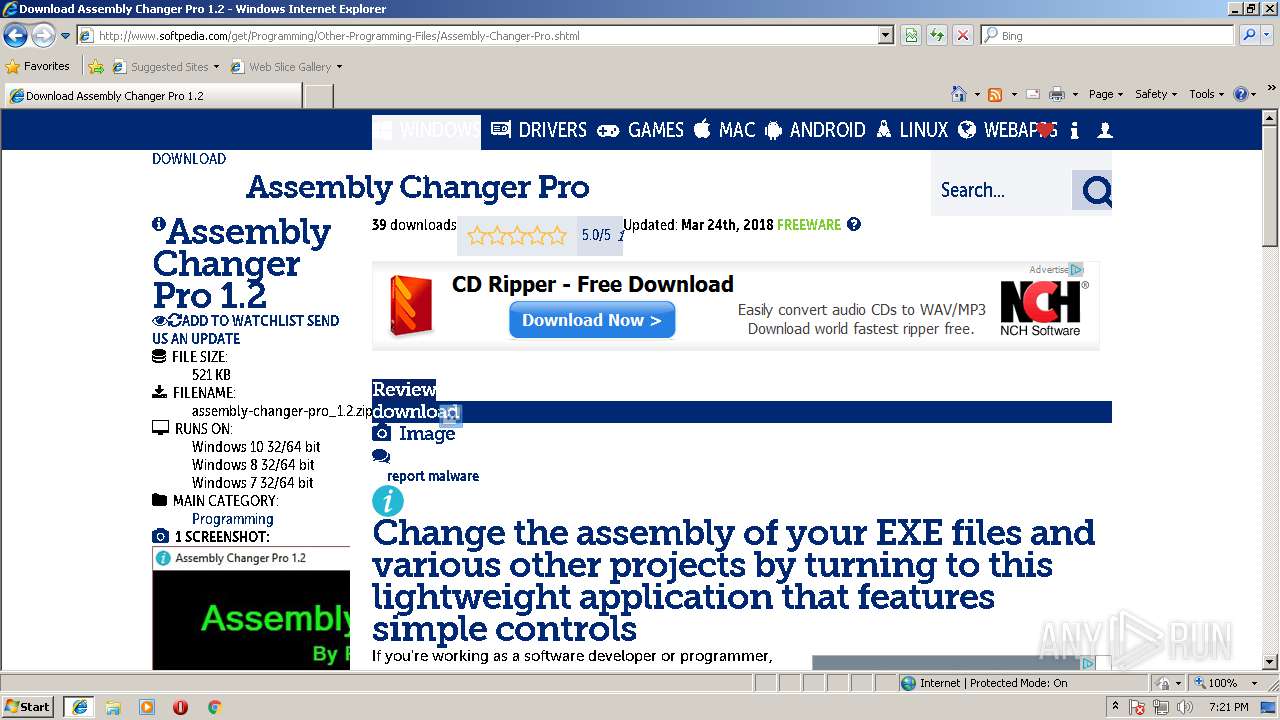
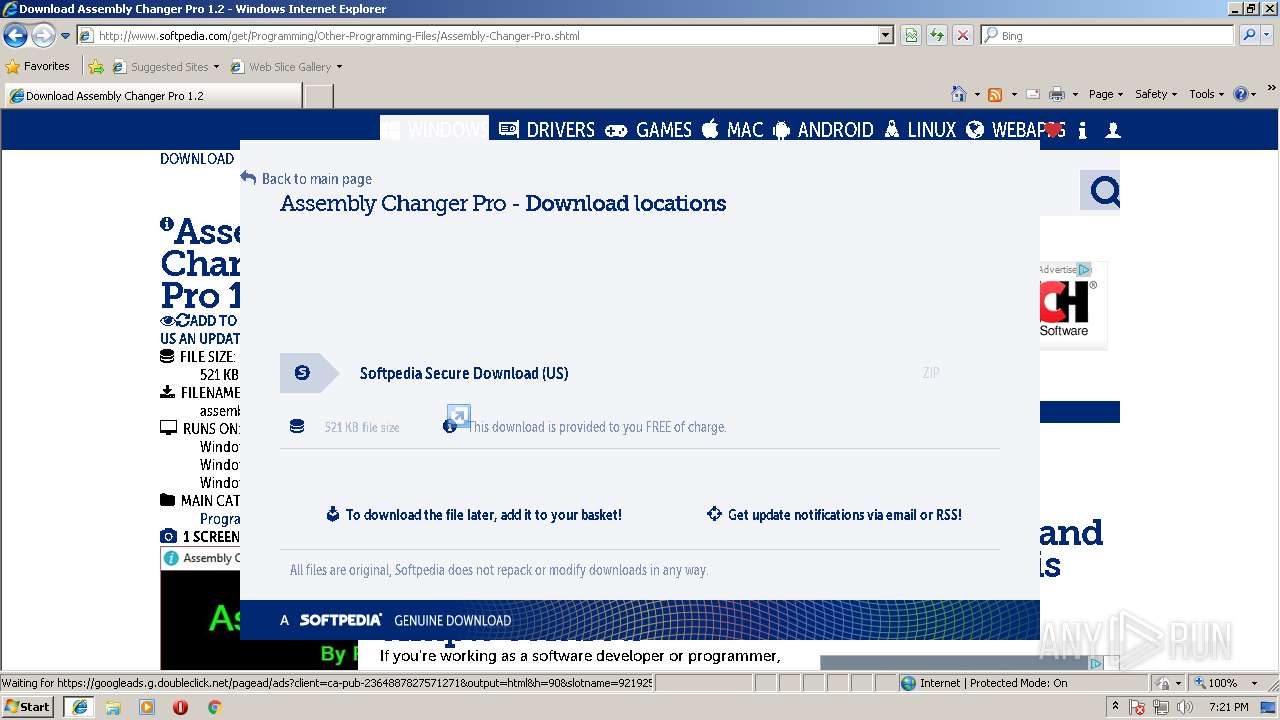
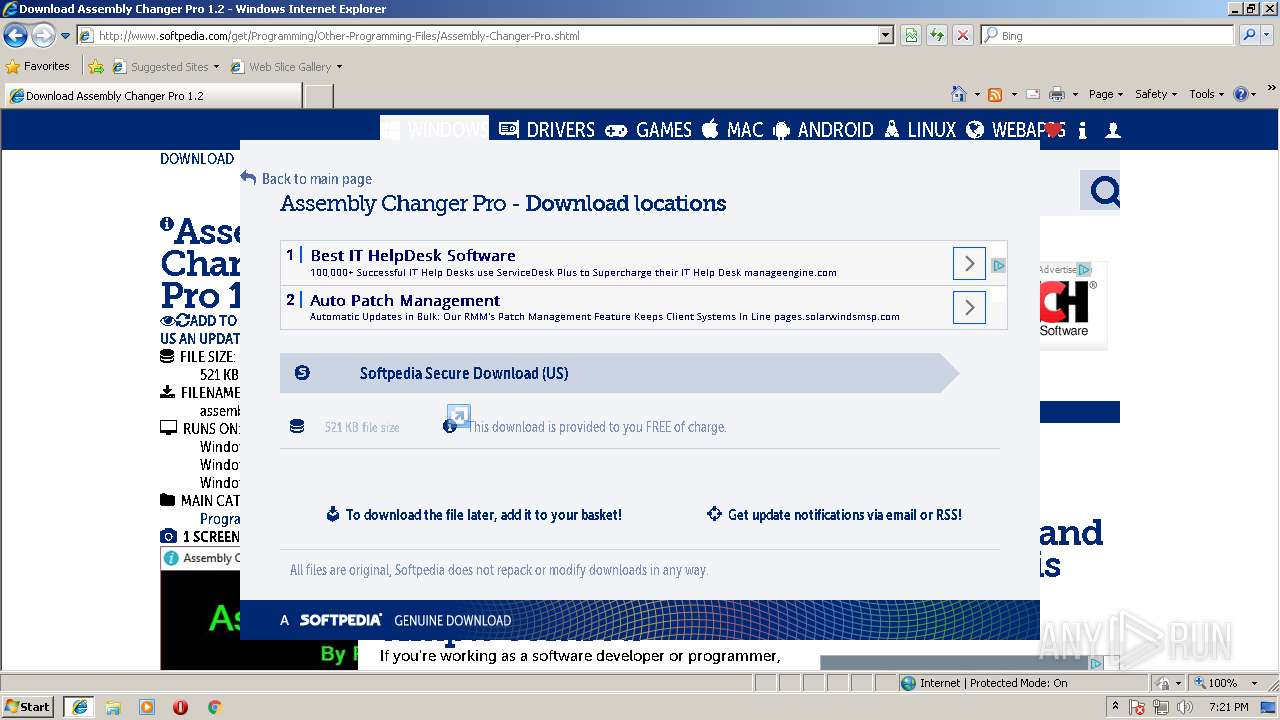
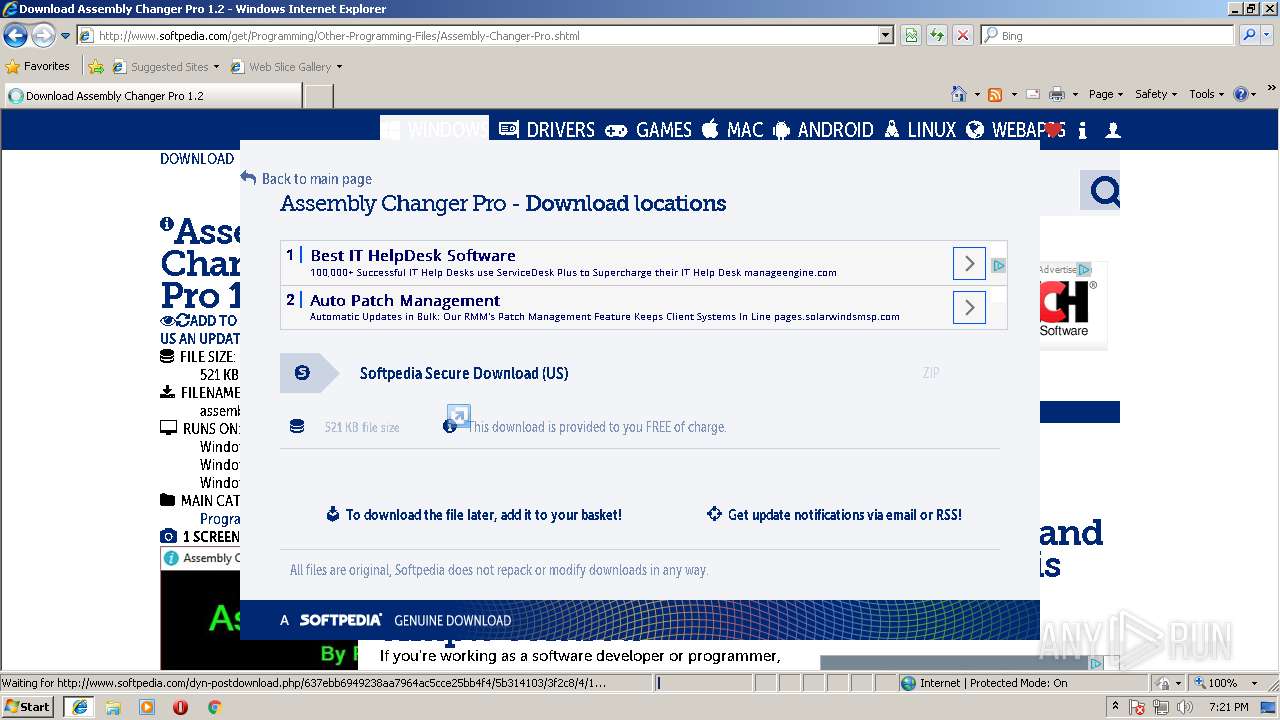
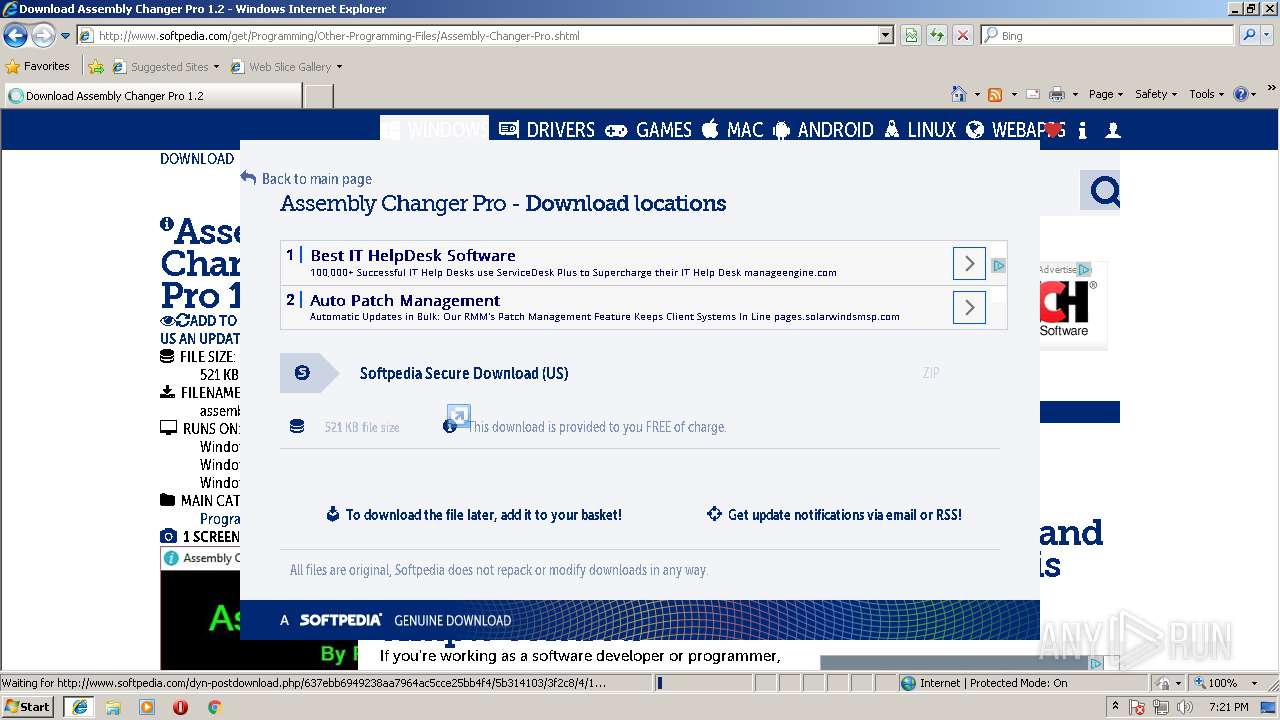
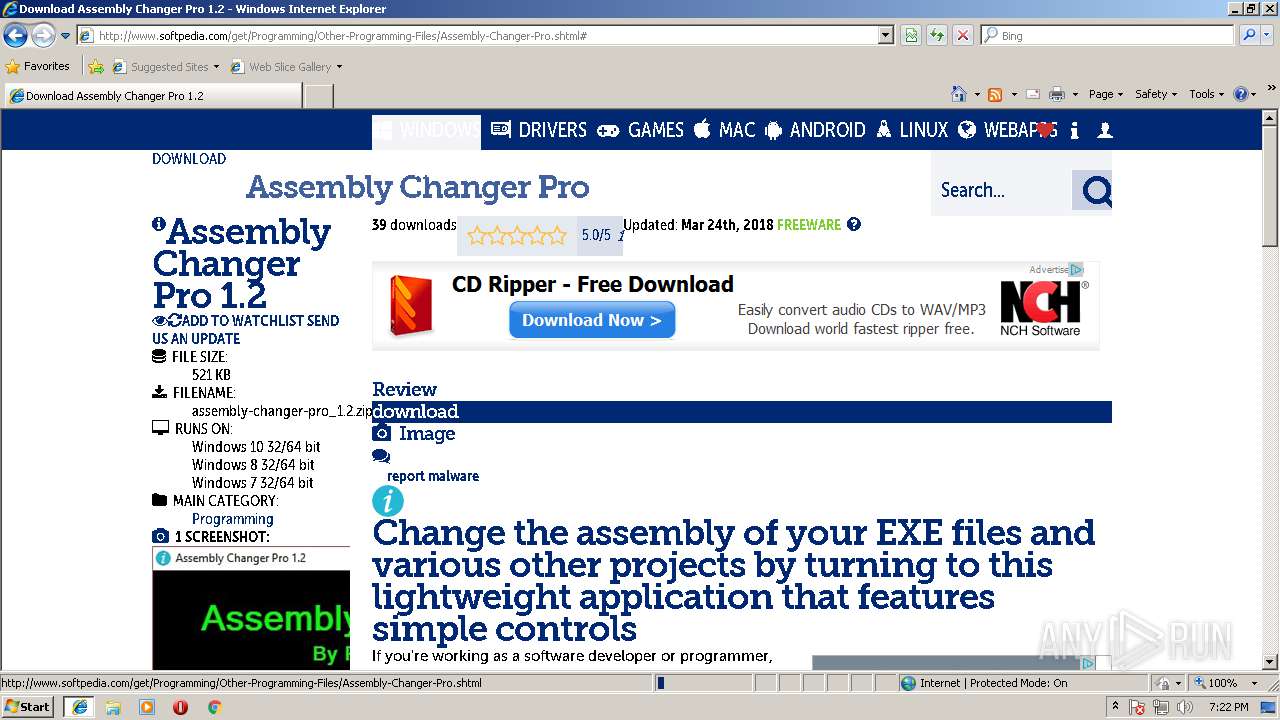
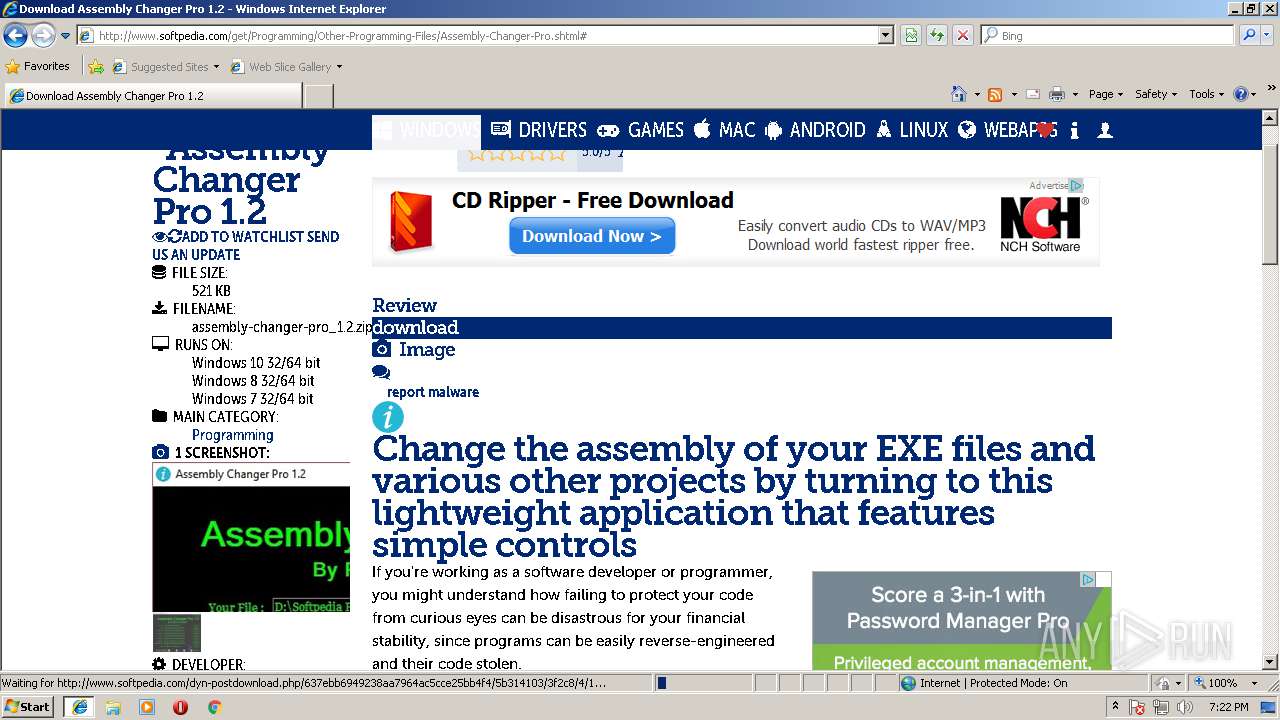
| URL: | http://www.softpedia.com/dyn-postdownload.php/d468c759cb3d4e3877d9febdbf80e91c/5b303345/3f2c8/4/1 |
| Full analysis: | https://app.any.run/tasks/2cb8c933-0183-4215-b408-be04e0fc33bd |
| Verdict: | Malicious activity |
| Analysis date: | June 25, 2018, 18:20:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A99937DB643F66C3863D19DF65A0C0B9 |
| SHA1: | 64323F380CC11084170EFA2F5EE09210C590F79D |
| SHA256: | E68A71BF8ECBF2DD0CEDAAC2D0F5CA07E2EE86E32F4F3BF2C97777E8B56F70C4 |
| SSDEEP: | 3:N1KJS4avwLIVdzleWGddNUvxQAA:Cc4UwLoFleWjxQAA |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- software_reporter_tool.exe (PID: 2704)
INFO
Changes internet zones settings
- iexplore.exe (PID: 1800)
Reads Internet Cache Settings
- iexplore.exe (PID: 820)
Reads settings of System Certificates
- iexplore.exe (PID: 820)
Dropped object may contain URL's
- iexplore.exe (PID: 1800)
- iexplore.exe (PID: 820)
Creates files in the user directory
- iexplore.exe (PID: 820)
- FlashUtil32_27_0_0_187_ActiveX.exe (PID: 1420)
- iexplore.exe (PID: 1800)
Loads the Task Scheduler COM API
- software_reporter_tool.exe (PID: 2704)
Application launched itself
- chrome.exe (PID: 2564)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1800)
Changes settings of System certificates
- iexplore.exe (PID: 1800)
Reads internet explorer settings
- iexplore.exe (PID: 820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
11
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 572 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=61.0.3163.100 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x6e9d7d7c,0x6e9d7da4,0x6e9d7d8c | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 764 | "c:\users\admin\appdata\local\google\chrome\user data\swreporter\23.129.0\software_reporter_tool.exe" --crash-handler "--database=c:\users\admin\appdata\local\Google\Software Reporter Tool" --url=https://clients2.google.com/cr/report --annotation=plat=Win32 --annotation=prod=ChromeFoil --annotation=ver=23.129.0 --initial-client-data=0xe4,0xec,0xf0,0xe8,0xf4,0x5bc42c,0x5bc43c,0x5bc44c | c:\users\admin\appdata\local\google\chrome\user data\swreporter\23.129.0\software_reporter_tool.exe | — | software_reporter_tool.exe | |||||||||||
User: admin Company: Google Integrity Level: MEDIUM Description: Software Reporter Tool Exit code: 0 Version: 23.129.0 Modules
| |||||||||||||||
| 808 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1616,11276875672024284662,692010019241150121,131072 --service-pipe-token=49653AFEEE3D40E7DC68A034D049A7D8 --lang=en-US --disable-client-side-phishing-detection --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=49653AFEEE3D40E7DC68A034D049A7D8 --renderer-client-id=5 --mojo-platform-channel-handle=3204 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 820 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1800 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1420 | C:\Windows\system32\Macromed\Flash\FlashUtil32_27_0_0_187_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_27_0_0_187_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 27.0 r0 Exit code: 0 Version: 27,0,0,187 Modules
| |||||||||||||||
| 1800 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1816 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1616,11276875672024284662,692010019241150121,131072 --service-pipe-token=38E848D7C2B4DFDCE2BB8F6E438854B8 --lang=en-US --disable-client-side-phishing-detection --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=38E848D7C2B4DFDCE2BB8F6E438854B8 --renderer-client-id=4 --mojo-platform-channel-handle=1628 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 2564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 2596 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1616,11276875672024284662,692010019241150121,131072 --service-pipe-token=1D6867274A3C21C117430B25E9E6D66C --lang=en-US --extension-process --disable-client-side-phishing-detection --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=1D6867274A3C21C117430B25E9E6D66C --renderer-client-id=2 --mojo-platform-channel-handle=1780 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 2704 | "C:\Users\admin\AppData\Local\Google\Chrome\User Data\SwReporter\23.129.0\software_reporter_tool.exe" --session-id=CKVTvTqpaBhbdUmCgseY6z4gSNj9gzHnYzfA5p30 | C:\Users\admin\AppData\Local\Google\Chrome\User Data\SwReporter\23.129.0\software_reporter_tool.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Integrity Level: MEDIUM Description: Software Reporter Tool Exit code: 2 Version: 23.129.0 Modules
| |||||||||||||||
Total events
1 174
Read events
816
Write events
342
Delete events
16
Modification events
| (PID) Process: | (1800) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1800) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1800) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1800) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (1800) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1800) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000070000000010000000000000000000000000000000000000000000000400C35B347C7D301000000000000000000000000020000001700000000000000FE80000000000000D45917EAB3ED3D860B000000000000001700000000000000FE80000000000000D45917EAB3ED3D860B000000000000001C00000000000000000000000000000000000000000000000000000000000000170000000000000000000000000000000000FFFFC0A8640B000000000000000002000000C0A801640000000000000000000000000000000000000000000000000C00000C37D0000010A73800D8703600000000000000000000000000000000000000000000000000000000000000000000000000000000000000000081F800009000230090002300380023000000000000702C000A00000000000000F8412C00 | |||
| (PID) Process: | (1800) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {8C080C6F-78A4-11E8-B27F-5254004AAD21} |
Value: 0 | |||
| (PID) Process: | (1800) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (1800) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 5 | |||
| (PID) Process: | (1800) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E207060001001900120015001000A402 | |||
Executable files
0
Suspicious files
24
Text files
89
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1800 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2LKO8ICX\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 1800 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 820 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab98C6.tmp | — | |
MD5:— | SHA256:— | |||
| 820 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab98C8.tmp | — | |
MD5:— | SHA256:— | |||
| 820 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab98C7.tmp | — | |
MD5:— | SHA256:— | |||
| 820 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar98C9.tmp | — | |
MD5:— | SHA256:— | |||
| 820 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar98CB.tmp | — | |
MD5:— | SHA256:— | |||
| 820 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar98CA.tmp | — | |
MD5:— | SHA256:— | |||
| 820 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab98DC.tmp | — | |
MD5:— | SHA256:— | |||
| 820 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab98DD.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
59
TCP/UDP connections
83
DNS requests
34
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
820 | iexplore.exe | GET | 301 | 64.225.158.190:80 | http://www.softpedia.com/dyn-postdownload.php/d468c759cb3d4e3877d9febdbf80e91c/5b303345/3f2c8/4/1 | CA | — | — | suspicious |
820 | iexplore.exe | GET | 200 | 64.225.158.190:80 | http://www.softpedia.com/_xaja/xdl.php?t=985b86ccd0cf30128237f7c6beac942ef5e50273&p=258760&rt=i | CA | compressed | 8.67 Kb | suspicious |
820 | iexplore.exe | GET | 200 | 172.217.23.130:80 | http://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js | US | text | 26.6 Kb | whitelisted |
820 | iexplore.exe | GET | 200 | 68.232.34.200:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 52.5 Kb | whitelisted |
820 | iexplore.exe | GET | 200 | 69.16.175.10:80 | http://i1-win.softpedia-static.com/screenshots/ico/Assembly-Changer-Pro.png | US | image | 698 b | whitelisted |
820 | iexplore.exe | GET | 200 | 69.16.175.10:80 | http://i1-win.softpedia-static.com/screenshots/ico/OpenGL-Extension-Viewer.gif | US | image | 1.79 Kb | whitelisted |
820 | iexplore.exe | GET | 200 | 64.225.158.190:80 | http://www.softpedia.com/_min/jsstore.php?l=cHJvZ3BhZ2VfanNfMjAxNixwcm9nc2NycG9wLHBvcHVwczIscHJvZ2Noa2hhc2gsZ2FfZXZlbnRfaW5pdA==&f=bGFuZy9FTi5qcyx3YXRjaGxpc3QuanMsZGxiYXNrZXQuanMsanF1ZXJ5LnN3aXBlYm94Lmpz&jv=2098 | CA | text | 61.7 Kb | suspicious |
820 | iexplore.exe | GET | 200 | 69.16.175.10:80 | http://i1-win.softpedia-static.com/screenshots/ico/NetBeans-IDE.png | US | image | 1.91 Kb | whitelisted |
820 | iexplore.exe | GET | 200 | 68.232.34.200:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 52.5 Kb | whitelisted |
820 | iexplore.exe | GET | 200 | 69.16.175.10:80 | http://i1-win.softpedia-static.com/screenshots/ico/Source-Insight.gif | US | image | 1.56 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1800 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
820 | iexplore.exe | 172.217.16.194:443 | adservice.google.com | Google Inc. | US | whitelisted |
820 | iexplore.exe | 68.232.34.200:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
820 | iexplore.exe | 172.217.23.162:443 | adservice.google.ch | Google Inc. | US | whitelisted |
820 | iexplore.exe | 172.217.22.1:80 | tpc.googlesyndication.com | Google Inc. | US | whitelisted |
820 | iexplore.exe | 69.16.175.10:80 | cdnssl.softpedia.com | Highwinds Network Group, Inc. | US | malicious |
820 | iexplore.exe | 172.217.23.130:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
820 | iexplore.exe | 172.217.22.1:443 | tpc.googlesyndication.com | Google Inc. | US | whitelisted |
820 | iexplore.exe | 172.217.23.130:80 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
820 | iexplore.exe | 216.58.207.34:80 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.softpedia.com |
| suspicious |
www.bing.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
www.googletagservices.com |
| whitelisted |
cdnssl.softpedia.com |
| malicious |
adservice.google.com |
| whitelisted |
adservice.google.ch |
| whitelisted |
www.google-analytics.com |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |