| File name: | Wind0sl0aderv3.6995.zip |
| Full analysis: | https://app.any.run/tasks/5630b911-3617-4fc2-8466-39614305600b |
| Verdict: | Malicious activity |
| Analysis date: | February 25, 2024, 08:55:25 |
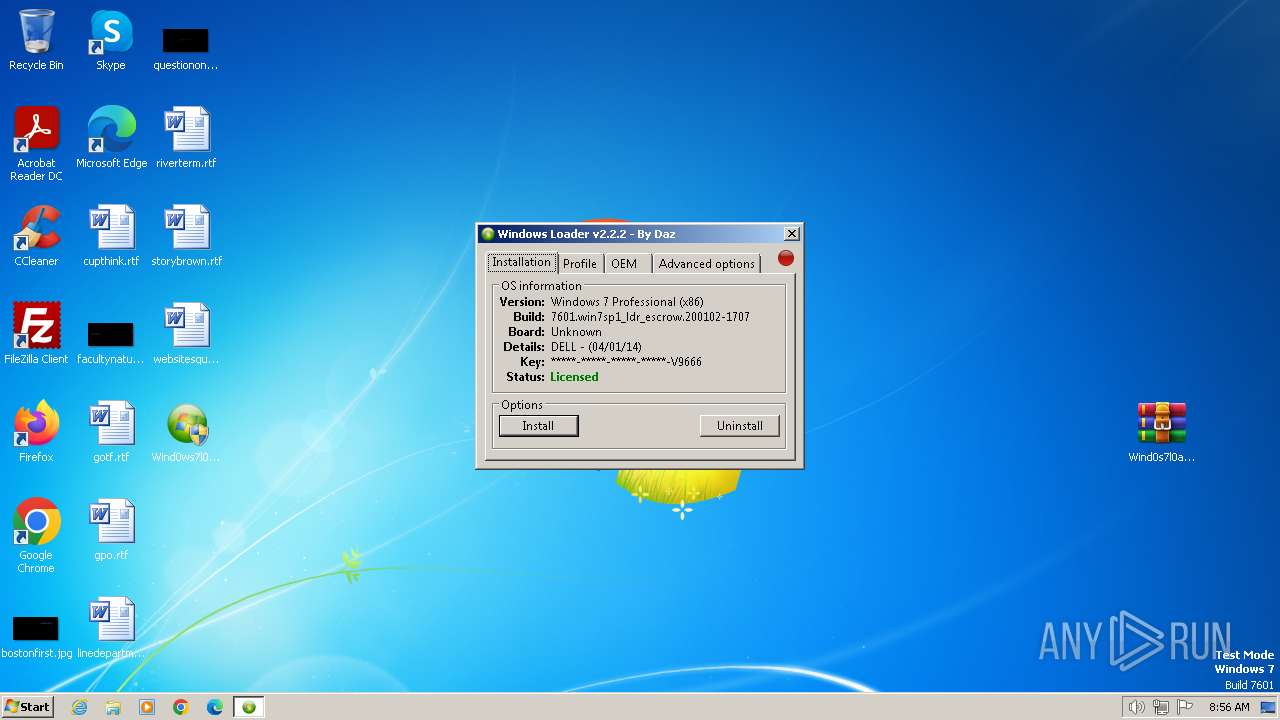
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | BDACC3B56567192026A0A07EC145B700 |
| SHA1: | 5A846A160DA3A9F8557A21DE36B208A007867249 |
| SHA256: | E68903B8BB4722E9DE6C91AD5E044954FC08A63731DF2884A5D57CD5741A9234 |
| SSDEEP: | 98304:6H3Uc/HeDOgsFbUT51iLK9LRnzMwsa9/pPhtC36a67JMdyDina84sasKQ315BdNC:CNYPCr8TD |
MALICIOUS
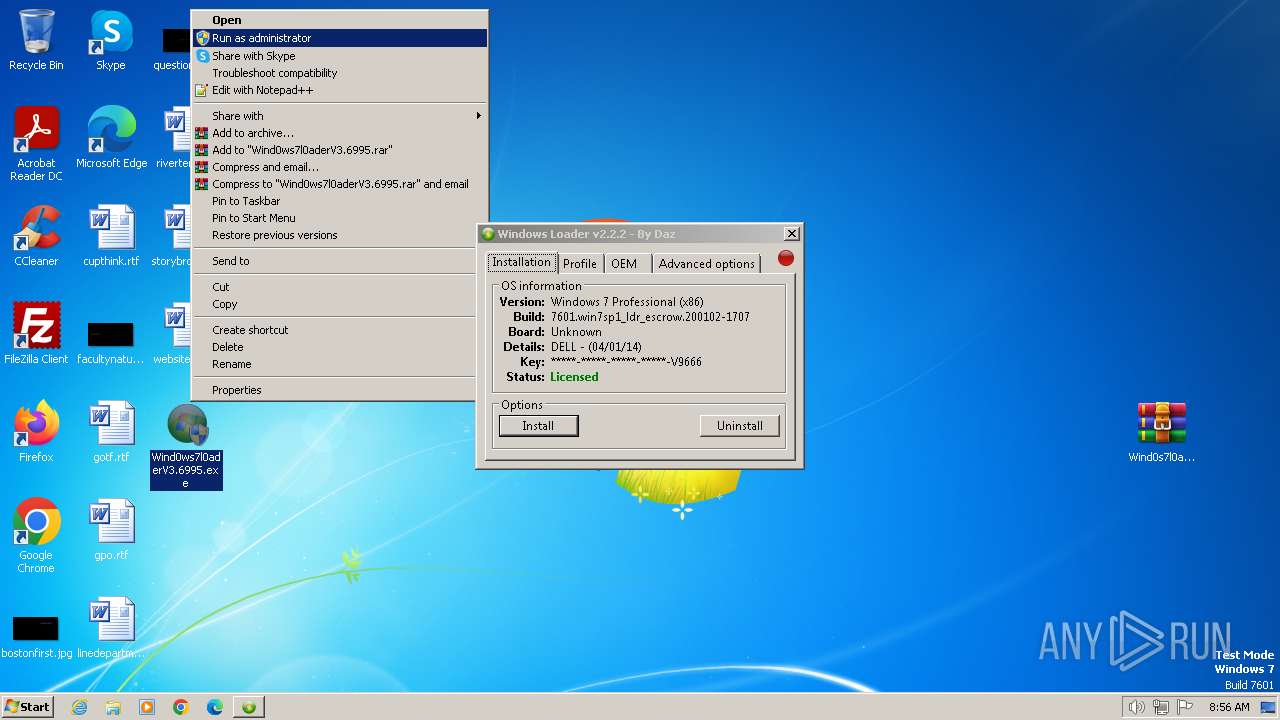
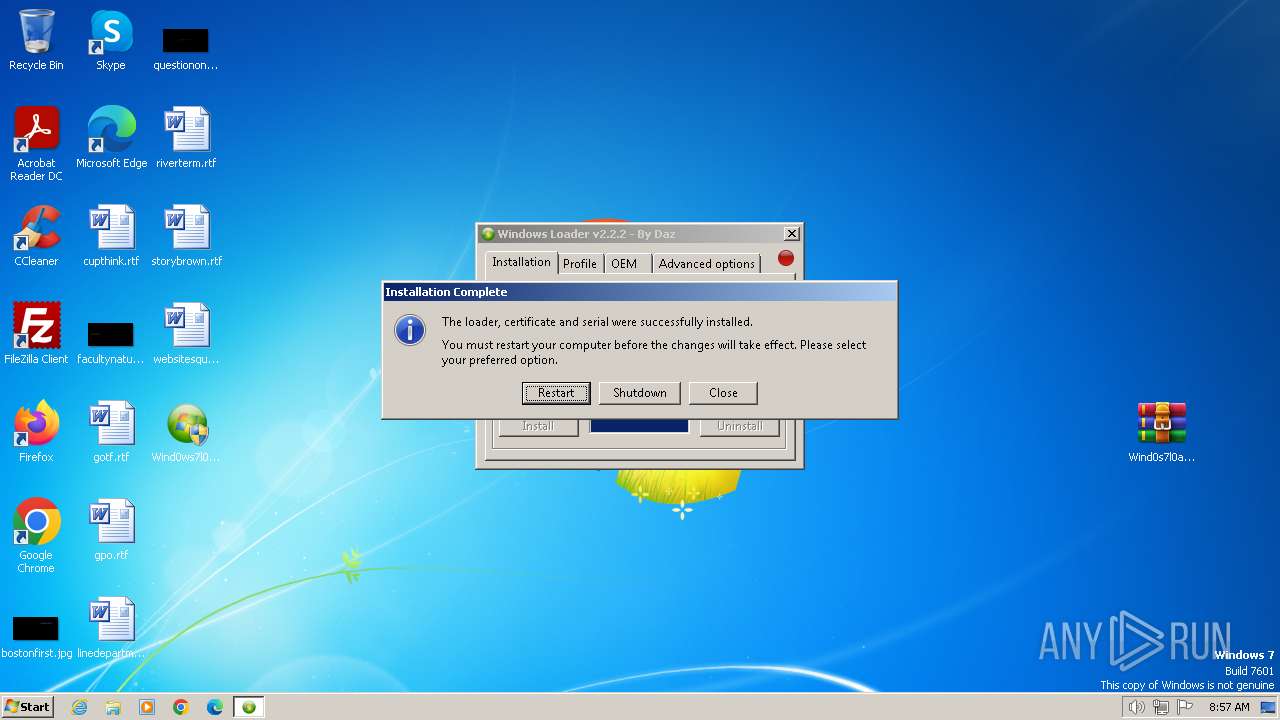
Drops the executable file immediately after the start
- Wind0ws7l0aderV3.6995.exe (PID: 2232)
- WindowsLoader.exe (PID: 3092)
Changes the autorun value in the registry
- Wind0ws7l0aderV3.6995.exe (PID: 1236)
- Wind0ws7l0aderV3.6995.exe (PID: 2232)
- Wind0ws7l0aderV3.6995.exe (PID: 3028)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 1352)
- cmd.exe (PID: 696)
- cmd.exe (PID: 1624)
Opens a text file (SCRIPT)
- cscript.exe (PID: 3112)
- cscript.exe (PID: 3232)
SUSPICIOUS
Executable content was dropped or overwritten
- Wind0ws7l0aderV3.6995.exe (PID: 2232)
- WindowsLoader.exe (PID: 3092)
Starts CMD.EXE for commands execution
- Wind0ws7l0aderV3.6995.exe (PID: 1236)
- Wind0ws7l0aderV3.6995.exe (PID: 2232)
- Wind0ws7l0aderV3.6995.exe (PID: 3028)
- WindowsLoader.exe (PID: 3092)
- cmd.exe (PID: 2468)
- cmd.exe (PID: 2588)
Reads the BIOS version
- WindowsLoader.exe (PID: 3092)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 128)
- cmd.exe (PID: 124)
Application launched itself
- cmd.exe (PID: 2468)
- cmd.exe (PID: 2588)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 3444)
- cmd.exe (PID: 2404)
The process executes VB scripts
- cmd.exe (PID: 784)
- cmd.exe (PID: 3152)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 3232)
- cscript.exe (PID: 3112)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 3232)
- cscript.exe (PID: 3112)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 3232)
Changes charset (SCRIPT)
- cscript.exe (PID: 3232)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 3232)
- cscript.exe (PID: 3112)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 3112)
- cscript.exe (PID: 3232)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 3112)
- cscript.exe (PID: 3232)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 3112)
- cscript.exe (PID: 3232)
Reads data from a file (SCRIPT)
- cscript.exe (PID: 3232)
Process drops legitimate windows executable
- WindowsLoader.exe (PID: 3092)
INFO
Manual execution by a user
- Wind0ws7l0aderV3.6995.exe (PID: 2304)
- WinRAR.exe (PID: 2848)
- Wind0ws7l0aderV3.6995.exe (PID: 2232)
- Wind0ws7l0aderV3.6995.exe (PID: 1236)
- Wind0ws7l0aderV3.6995.exe (PID: 2504)
- Wind0ws7l0aderV3.6995.exe (PID: 3028)
- Wind0ws7l0aderV3.6995.exe (PID: 748)
- wmpnscfg.exe (PID: 3612)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2848)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2848)
Checks supported languages
- Wind0ws7l0aderV3.6995.exe (PID: 2232)
- WindowsLoader.exe (PID: 3092)
- Wind0ws7l0aderV3.6995.exe (PID: 1236)
- WindowsLoader.exe (PID: 1808)
- Wind0ws7l0aderV3.6995.exe (PID: 3028)
- WindowsLoader.exe (PID: 712)
- wmpnscfg.exe (PID: 3612)
- bootsect.exe (PID: 1072)
Reads mouse settings
- Wind0ws7l0aderV3.6995.exe (PID: 2232)
- Wind0ws7l0aderV3.6995.exe (PID: 1236)
- Wind0ws7l0aderV3.6995.exe (PID: 3028)
Create files in a temporary directory
- Wind0ws7l0aderV3.6995.exe (PID: 2232)
Reads Environment values
- WindowsLoader.exe (PID: 3092)
Reads the computer name
- WindowsLoader.exe (PID: 3092)
- wmpnscfg.exe (PID: 3612)
Reads the machine GUID from the registry
- WindowsLoader.exe (PID: 3092)
Reads product name
- WindowsLoader.exe (PID: 3092)
Reads security settings of Internet Explorer
- cscript.exe (PID: 3232)
- cscript.exe (PID: 3112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:08:08 18:06:22 |
| ZipCRC: | 0x2888c088 |
| ZipCompressedSize: | 20 |
| ZipUncompressedSize: | 20 |
| ZipFileName: | password_is_112233.txt |
Total processes
96
Monitored processes
36
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | cmd.exe /A /C "icacls C:\ldrscan\bootwin /grant *S-1-1-0:(F)" | C:\Windows\System32\cmd.exe | — | WindowsLoader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 128 | cmd.exe /A /C "icacls C:\ldrscan\bootwin /grant *S-1-1-0:(F)" | C:\Windows\System32\cmd.exe | — | WindowsLoader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 696 | C:\Windows\system32\cmd.exe /c start regsvr32 -s "C:\Users\admin\AppData\Local\Temp\sfx.dll" | C:\Windows\System32\cmd.exe | — | Wind0ws7l0aderV3.6995.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 712 | C:\Users\admin\AppData\Local\Temp\WindowsLoader.exe | C:\Users\admin\AppData\Local\Temp\WindowsLoader.exe | — | Wind0ws7l0aderV3.6995.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 748 | "C:\Users\admin\Desktop\Wind0ws7l0aderV3.6995.exe" | C:\Users\admin\Desktop\Wind0ws7l0aderV3.6995.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 784 | cmd.exe /A /C "C:\Windows\System32\cscript.exe //nologo C:\Windows\System32\slmgr.vbs -ilc "C:\Dell.XRM-MS"" | C:\Windows\System32\cmd.exe | — | WindowsLoader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1072 | C:\bootsect.exe /nt60 SYS /force | C:\bootsect.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Sector Manipulation Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1216 | icacls C:\ldrscan\bootwin /grant *S-1-1-0:(F) | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1236 | "C:\Users\admin\Desktop\Wind0ws7l0aderV3.6995.exe" | C:\Users\admin\Desktop\Wind0ws7l0aderV3.6995.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1352 | C:\Windows\system32\cmd.exe /c start regsvr32 -s "C:\Users\admin\AppData\Local\Temp\sfx.dll" | C:\Windows\System32\cmd.exe | — | Wind0ws7l0aderV3.6995.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
5 610
Read events
5 577
Write events
33
Delete events
0
Modification events
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Wind0sl0aderv3.6995.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
6
Suspicious files
1
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1072 | bootsect.exe | \Device\HarddiskVolume1 | — | |
MD5:— | SHA256:— | |||
| 2848 | WinRAR.exe | C:\Users\admin\Desktop\Wind0ws7l0aderV3.6995.exe | executable | |
MD5:089277FAF48CD37EF789D7F0738F3018 | SHA256:D19ED4854AFED32180347D06517B28741ACDDF5B770D83DE1AA5293F57FBF8B9 | |||
| 2232 | Wind0ws7l0aderV3.6995.exe | C:\Users\admin\AppData\Local\Temp\aut7C7F.tmp | executable | |
MD5:DC892DEF31F6A3C1FC164544D21FB584 | SHA256:8AB71516FBC0B31D319F6849A39309CDE6FF673E1B39F808F85A6E03A7AF1641 | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3864.33412\Wind0s7l0ader_v3.6995pass_112233.zip | compressed | |
MD5:1B2580F946EA4ECF5648BB0FD04ADD7E | SHA256:D53E3140ACD8CF532D1727FB853C5BAC6C0BE43ECB3F3B41B7ADC72A9446B964 | |||
| 3092 | WindowsLoader.exe | C:\bootsect.dat | executable | |
MD5:CDACDF9537A03855FF33FFB740E9D6EF | SHA256:C06D0ABFB6364D279CCFB0E0E1D94D7A032C0C0138D291783EEB8AC9A6BEC966 | |||
| 2232 | Wind0ws7l0aderV3.6995.exe | C:\Users\admin\AppData\Local\Temp\sfx.dll | executable | |
MD5:DC892DEF31F6A3C1FC164544D21FB584 | SHA256:8AB71516FBC0B31D319F6849A39309CDE6FF673E1B39F808F85A6E03A7AF1641 | |||
| 2232 | Wind0ws7l0aderV3.6995.exe | C:\Users\admin\AppData\Local\Temp\WindowsLoader.exe | executable | |
MD5:323C0FD51071400B51EEDB1BE90A8188 | SHA256:2F2ABA1E074F5F4BAA08B524875461889F8F04D4FFC43972AC212E286022AB94 | |||
| 3092 | WindowsLoader.exe | C:\Dell.XRM-MS | xml | |
MD5:18B1E45BF56F40C3C4BBE65831178216 | SHA256:D072A059D3ED3E75C98B85B41E4319E8D5CFAE0E0C239B62436A3AD34003AB4A | |||
| 3092 | WindowsLoader.exe | C:\bootsect.exe | executable | |
MD5:CDACDF9537A03855FF33FFB740E9D6EF | SHA256:C06D0ABFB6364D279CCFB0E0E1D94D7A032C0C0138D291783EEB8AC9A6BEC966 | |||
| 3092 | WindowsLoader.exe | \\?\Volume{e1a82db3-a9f0-11e7-b142-806e6f6e6963}\HEUKC | binary | |
MD5:6C0EBE35D861E040DDD086E61670D842 | SHA256:01A51B074D38C5D6CACE2A1247C822B98B8A412A9AF7663EB1EE090769D5EE11 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |