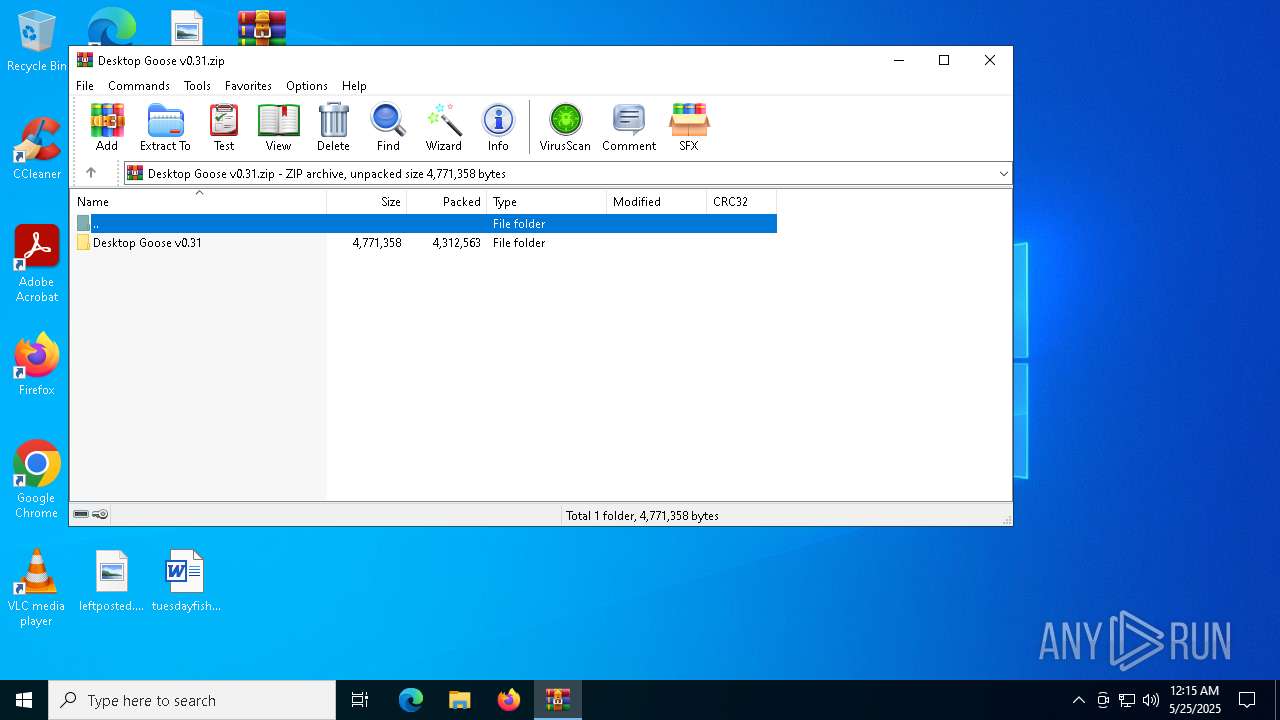
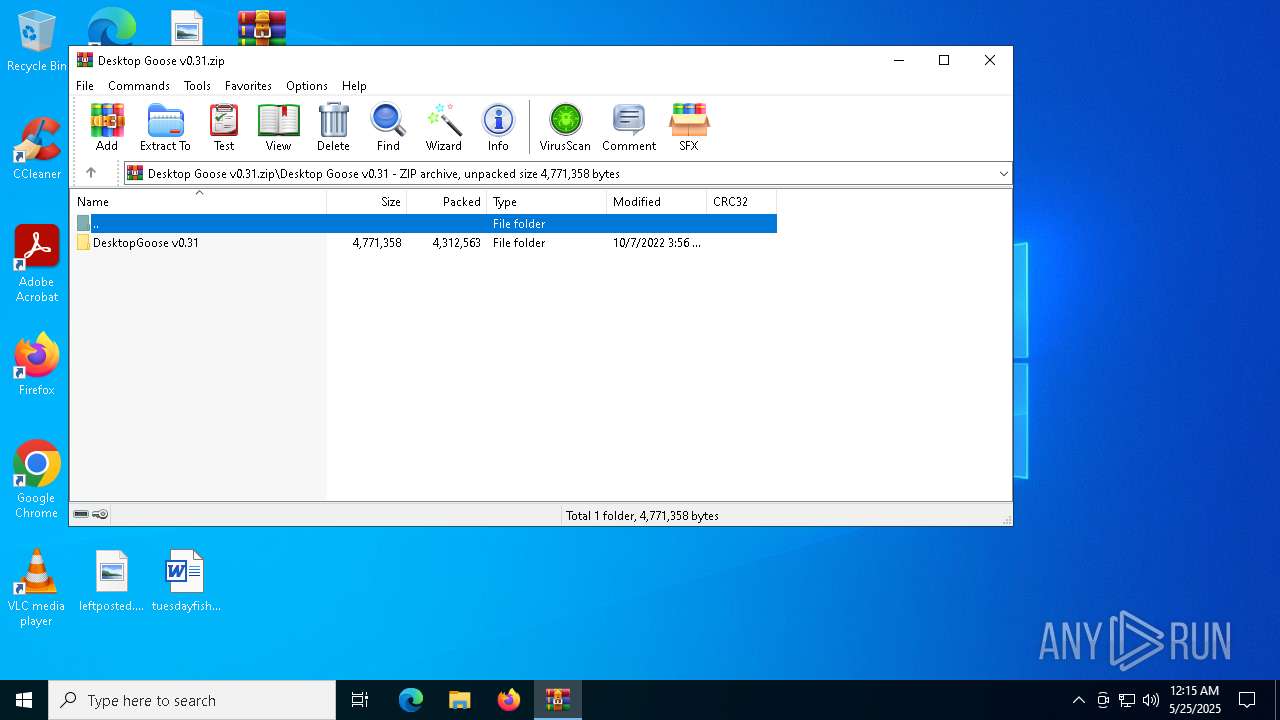
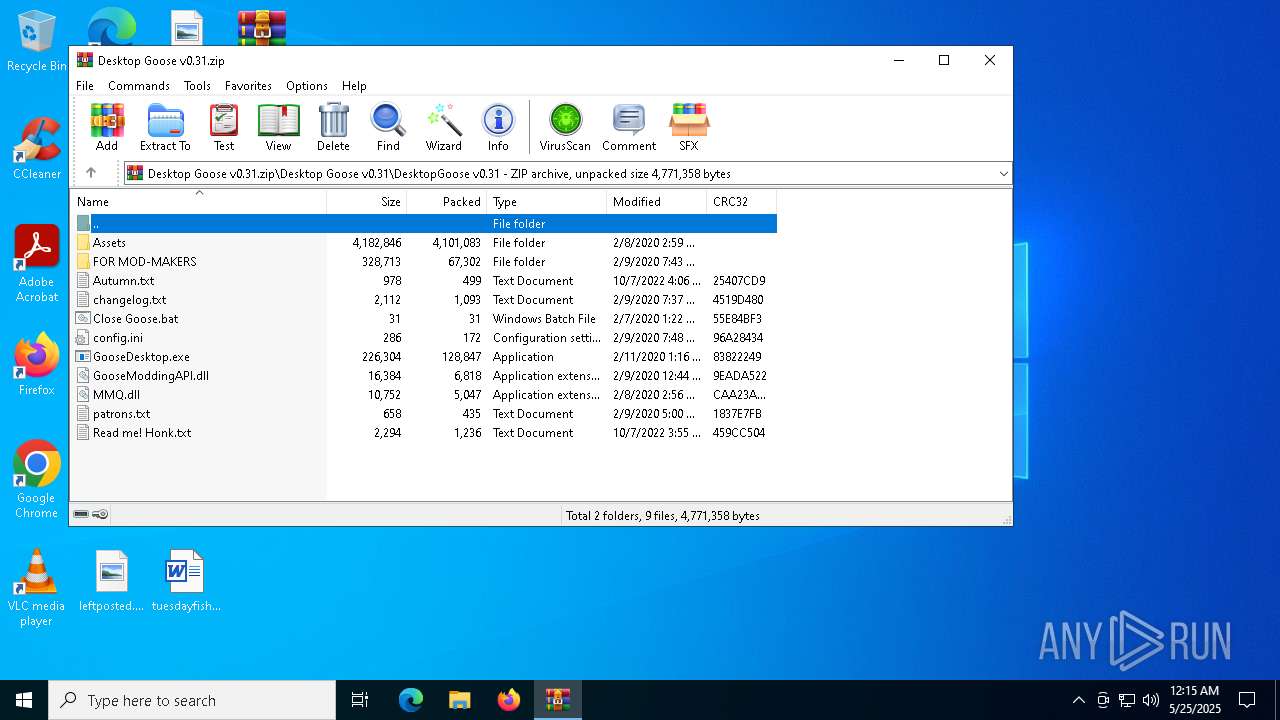
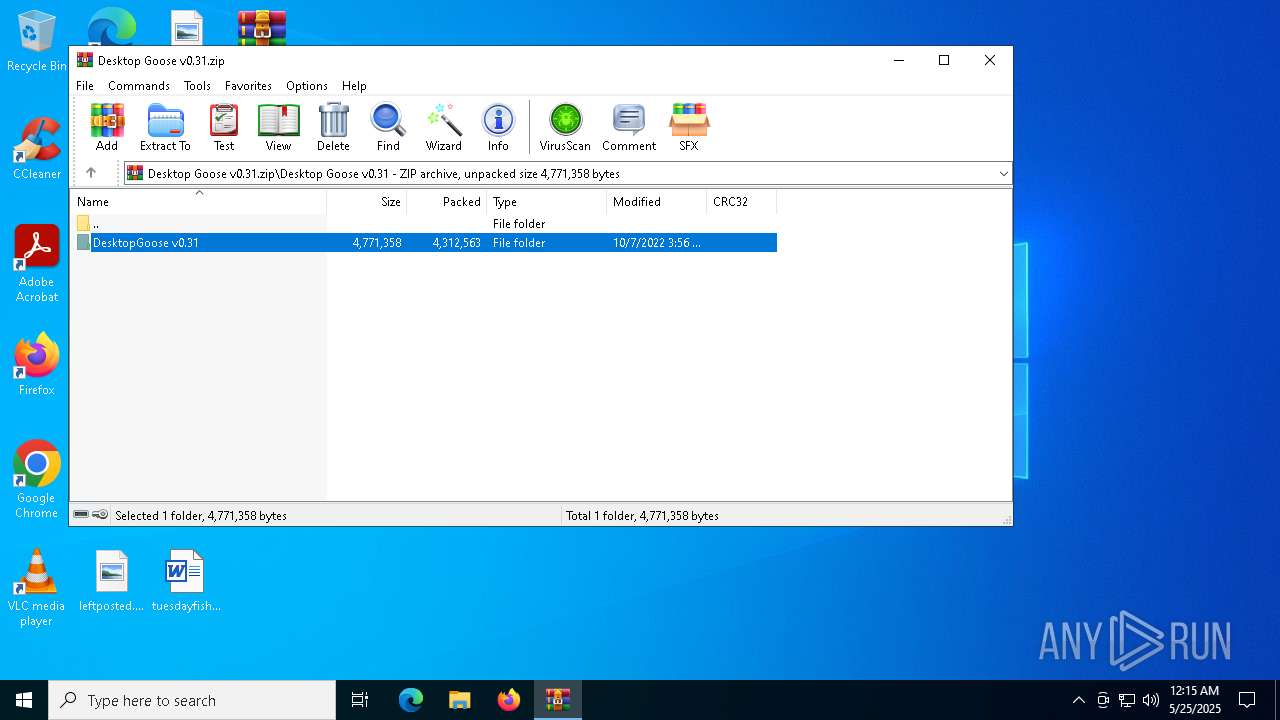
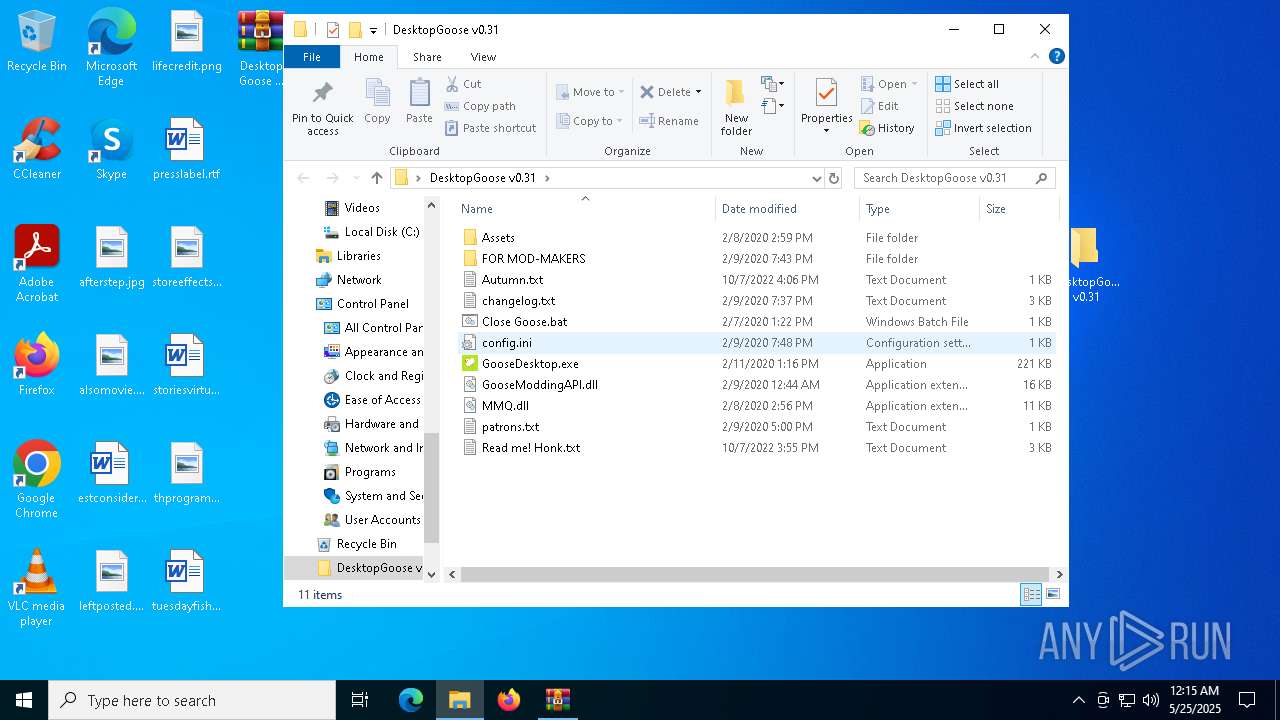
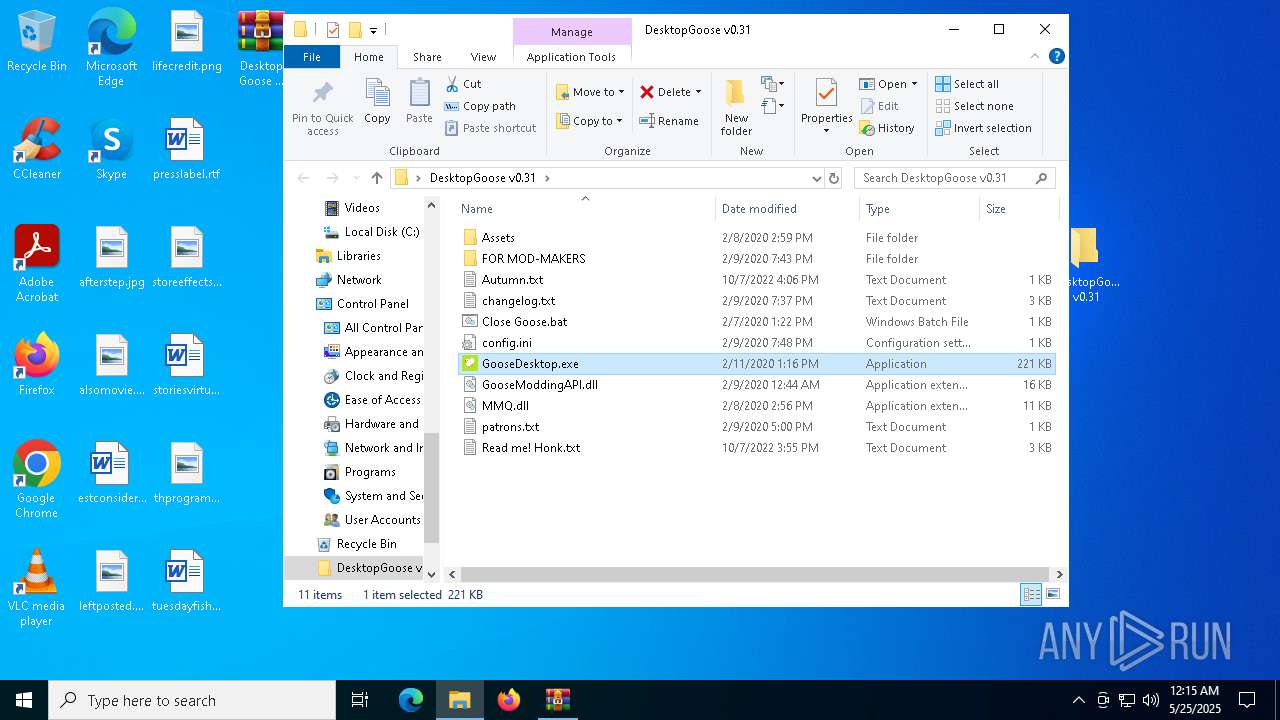
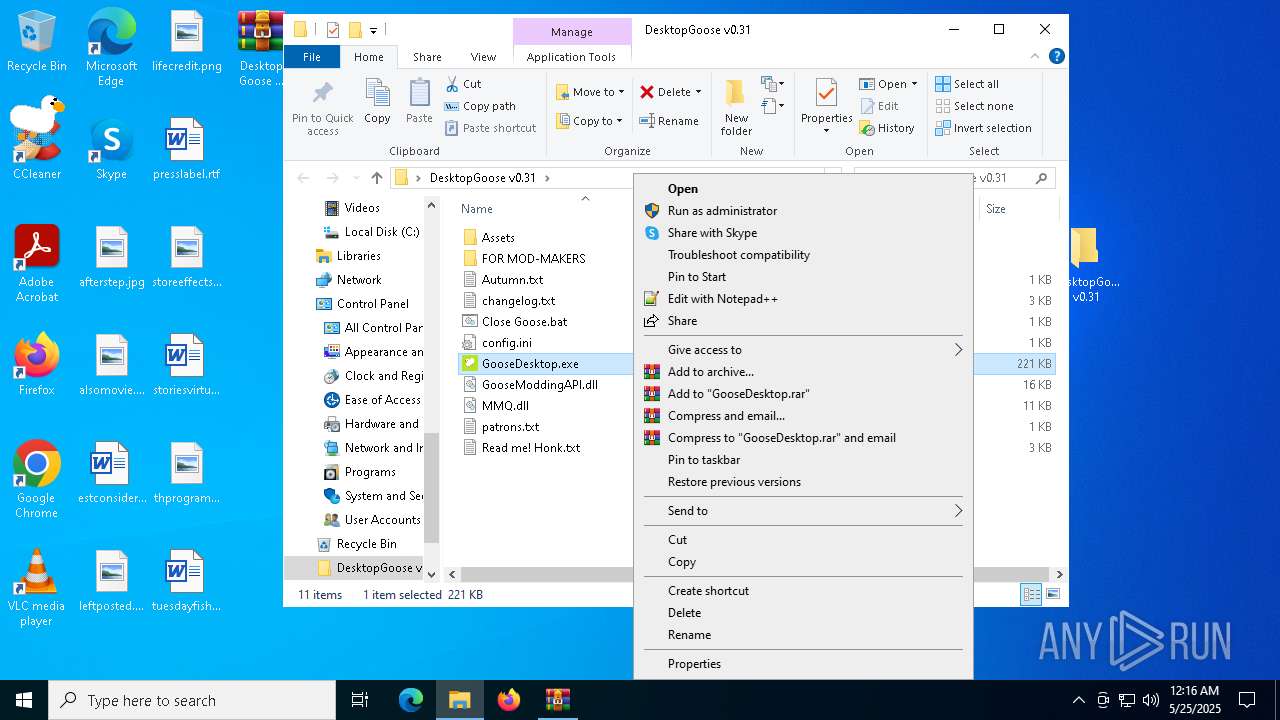
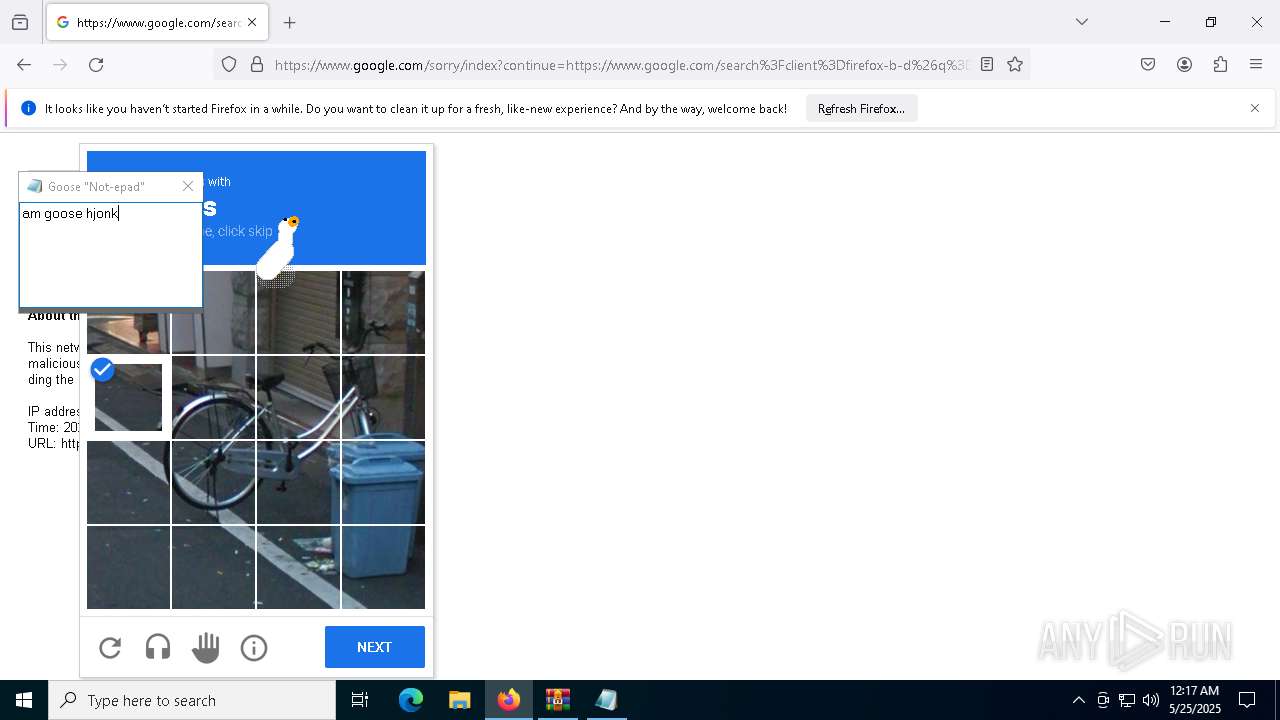
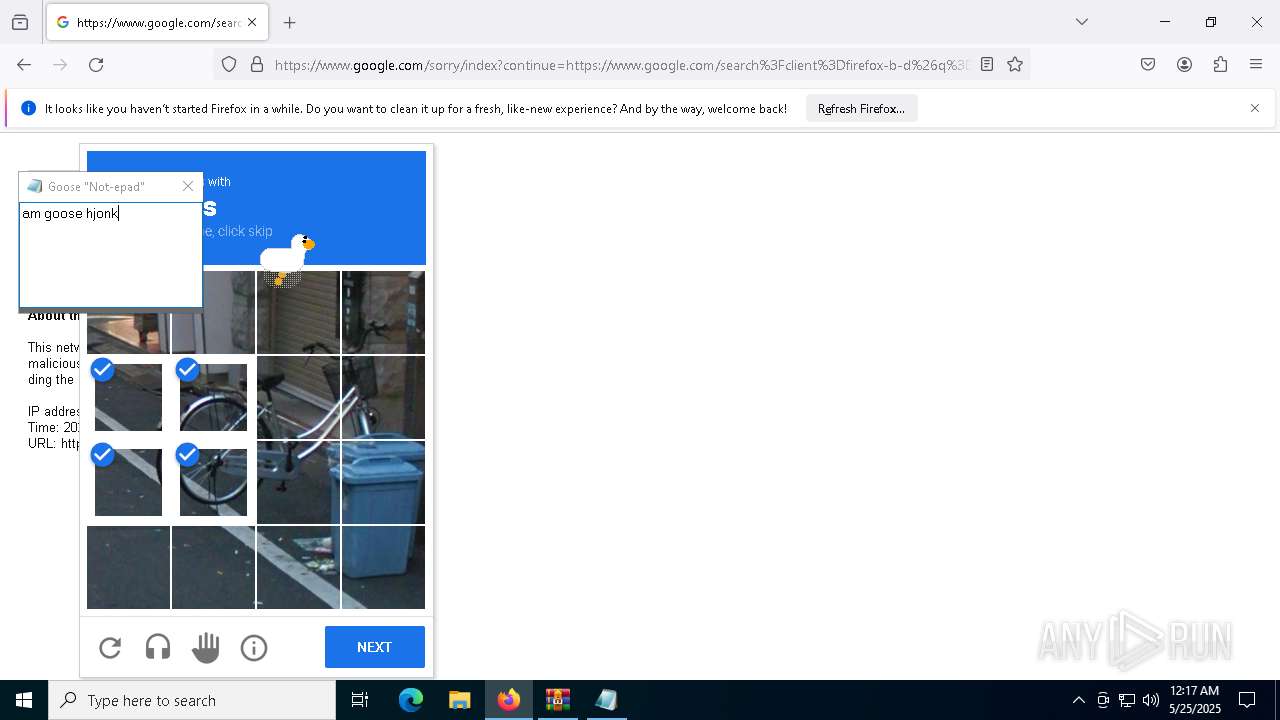
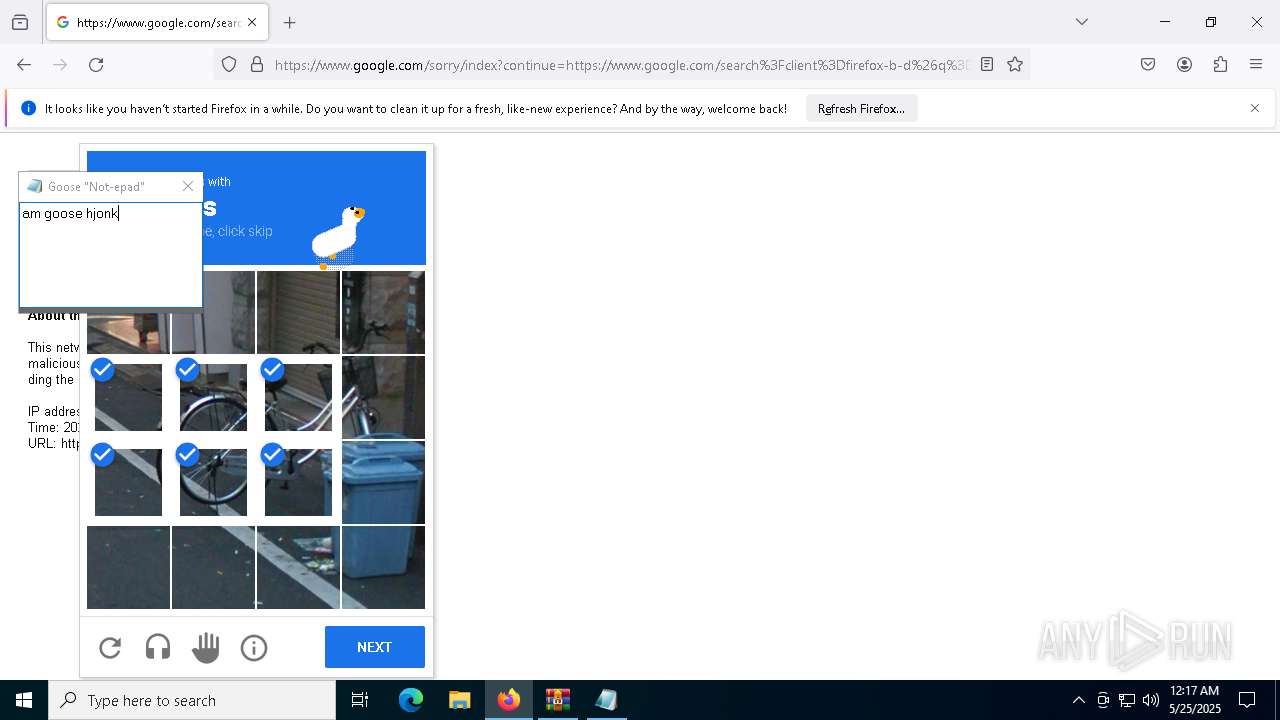
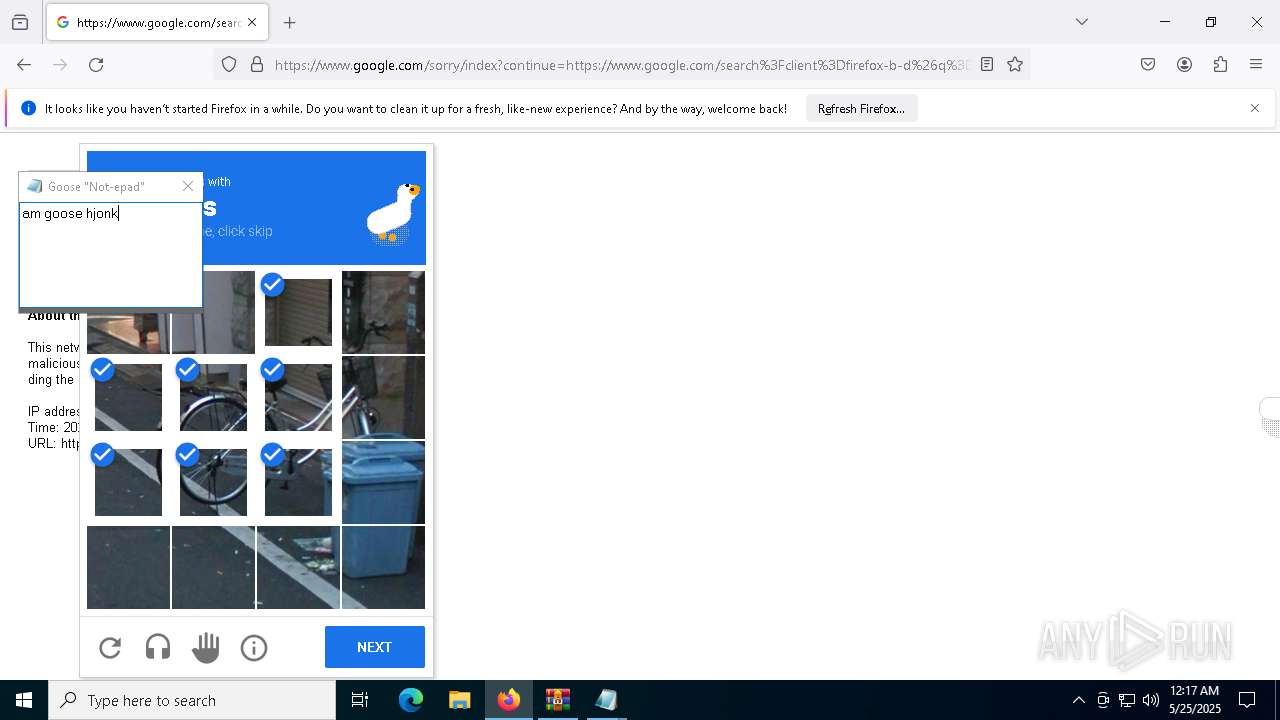
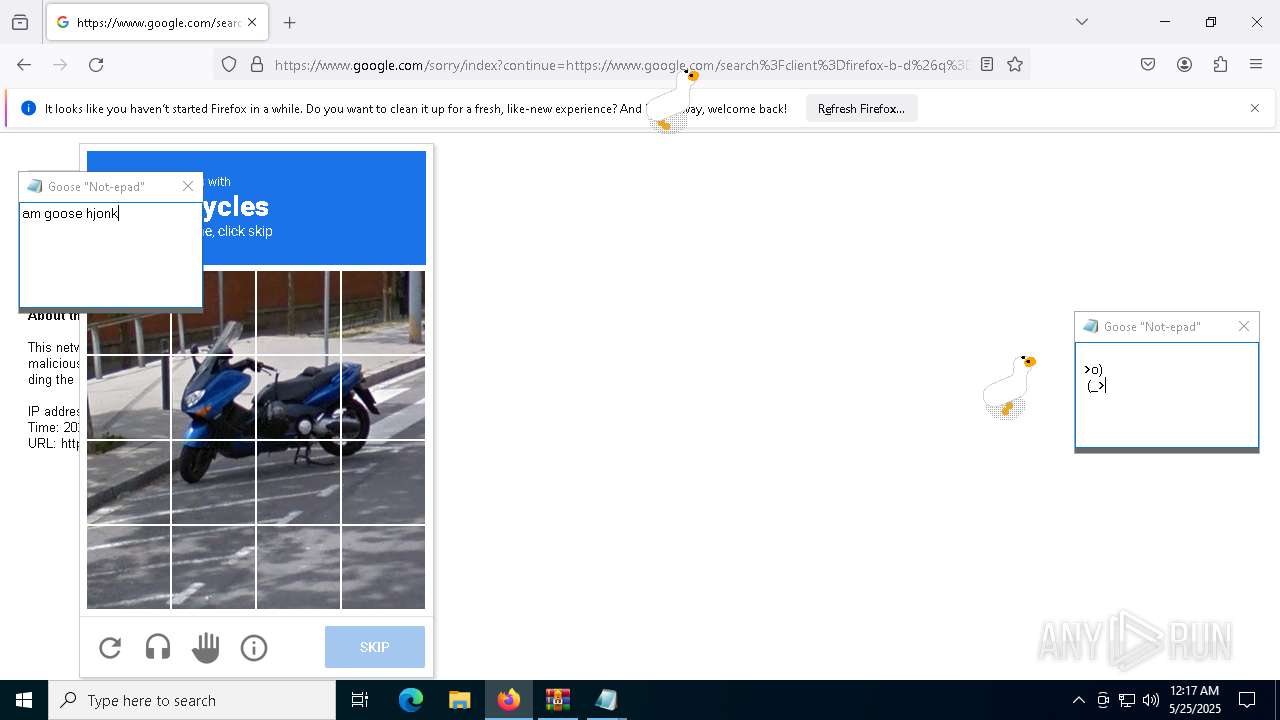
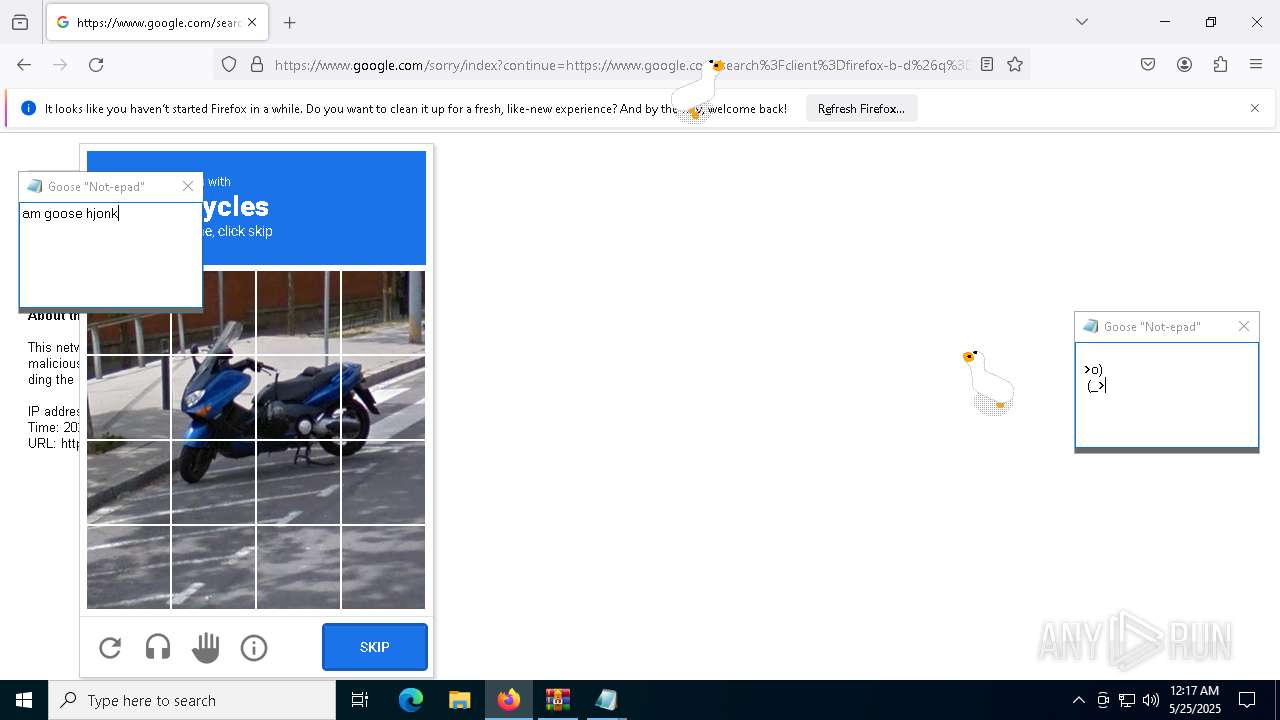
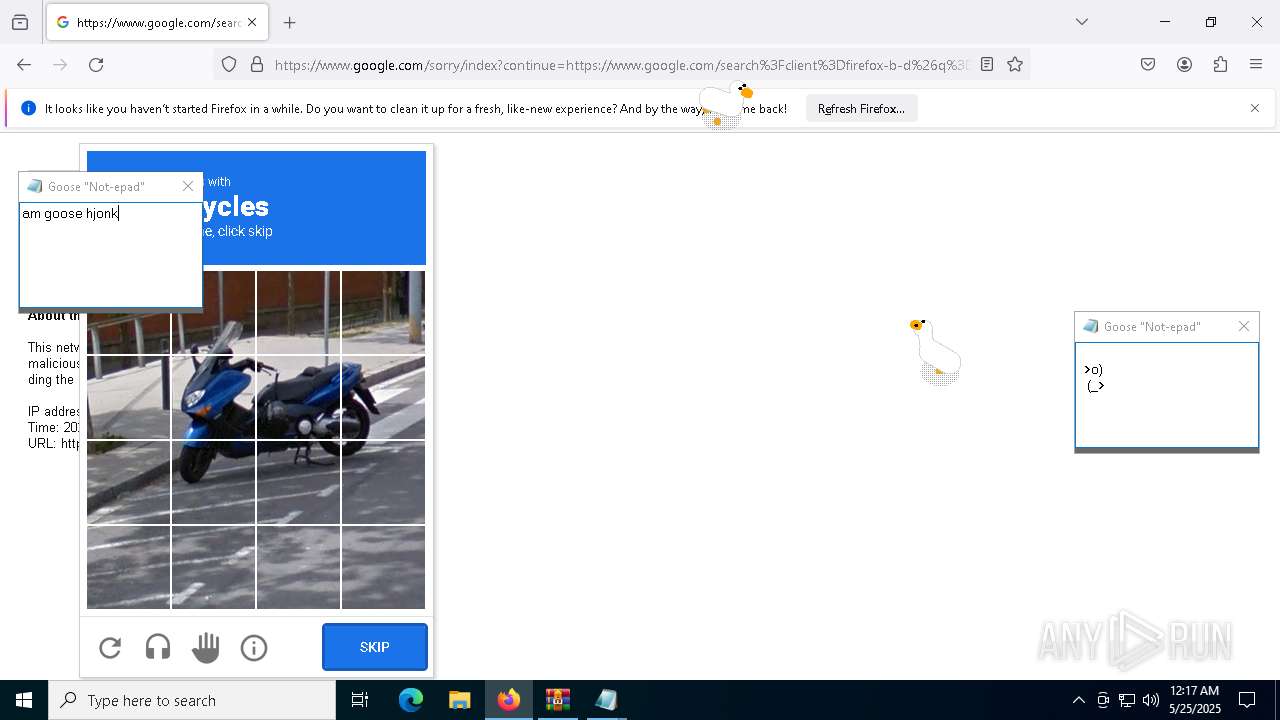
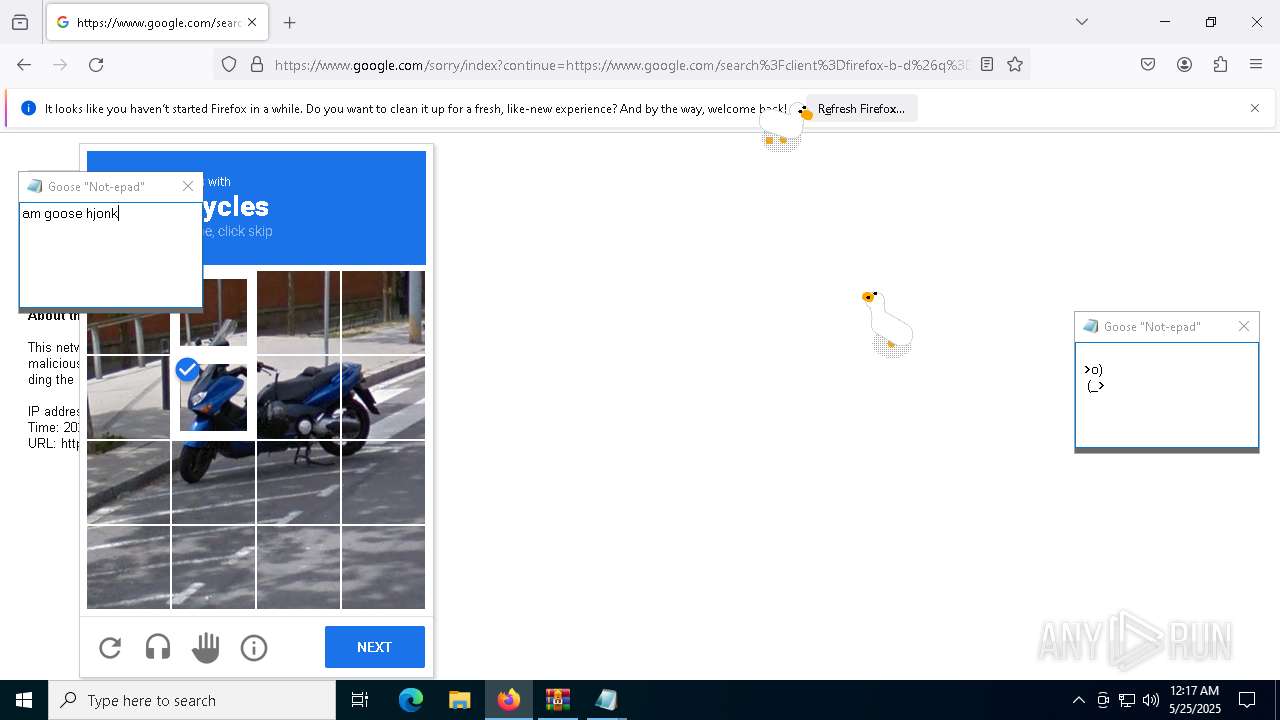
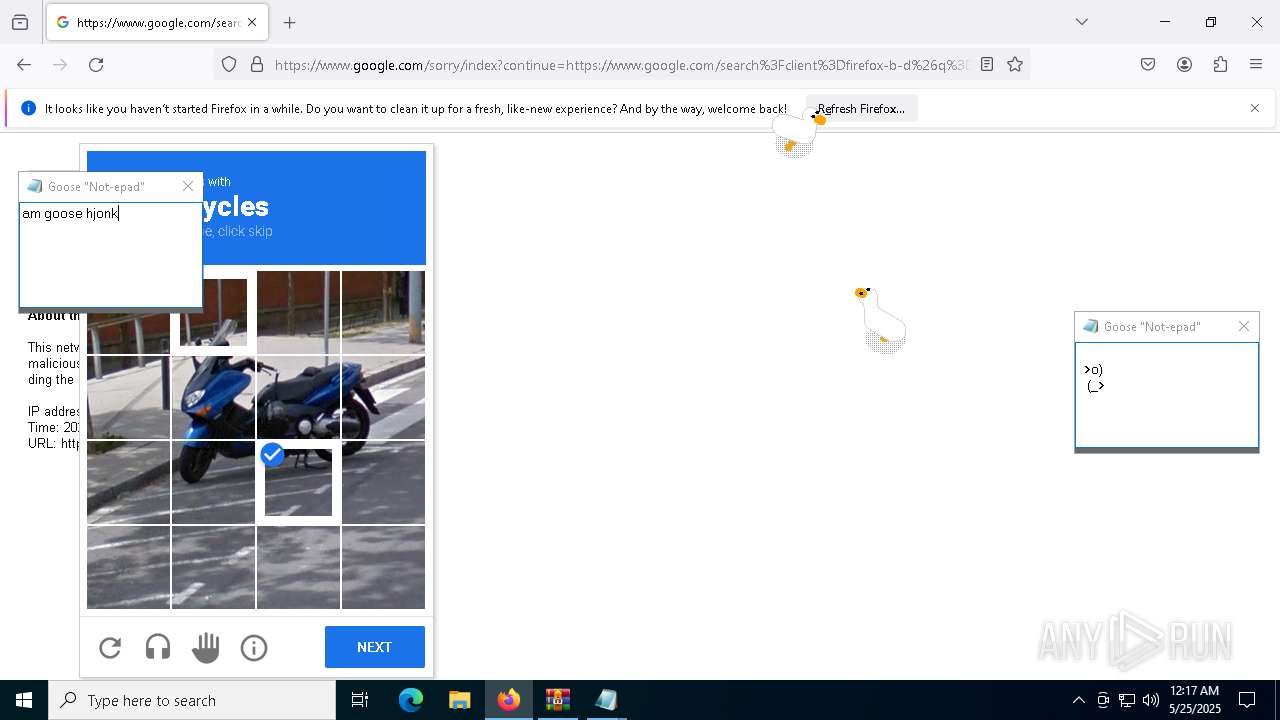
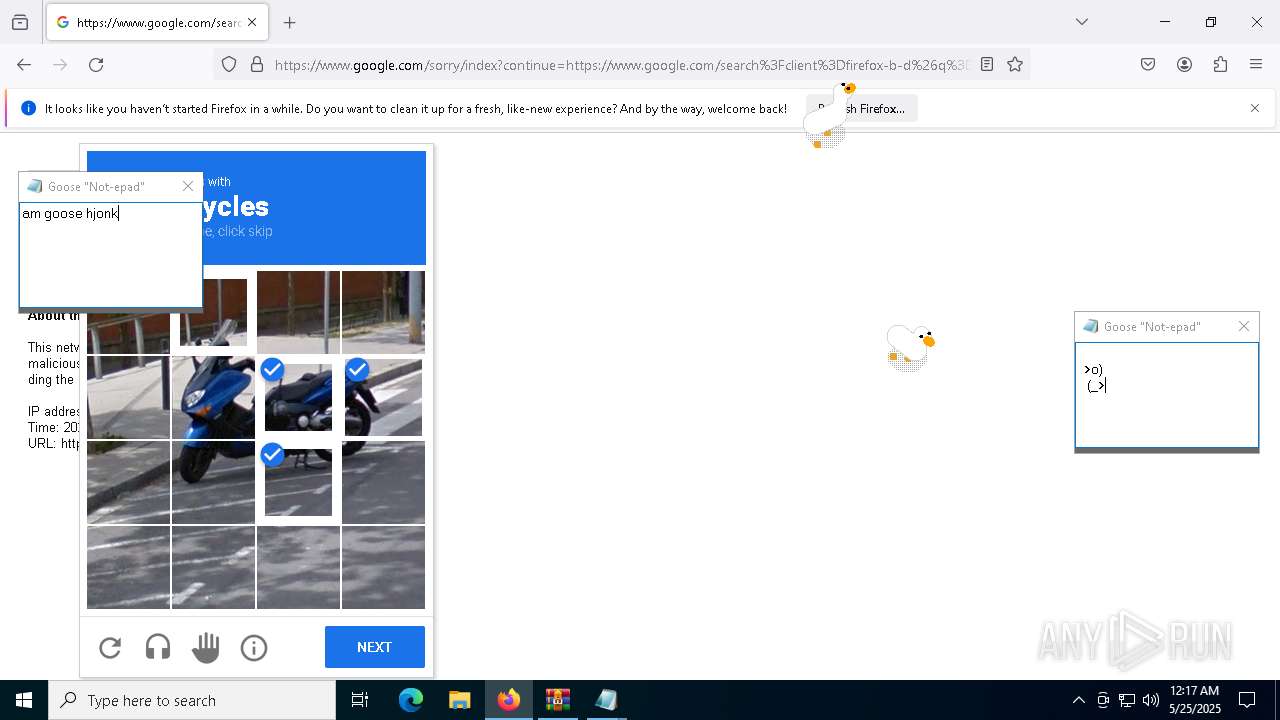
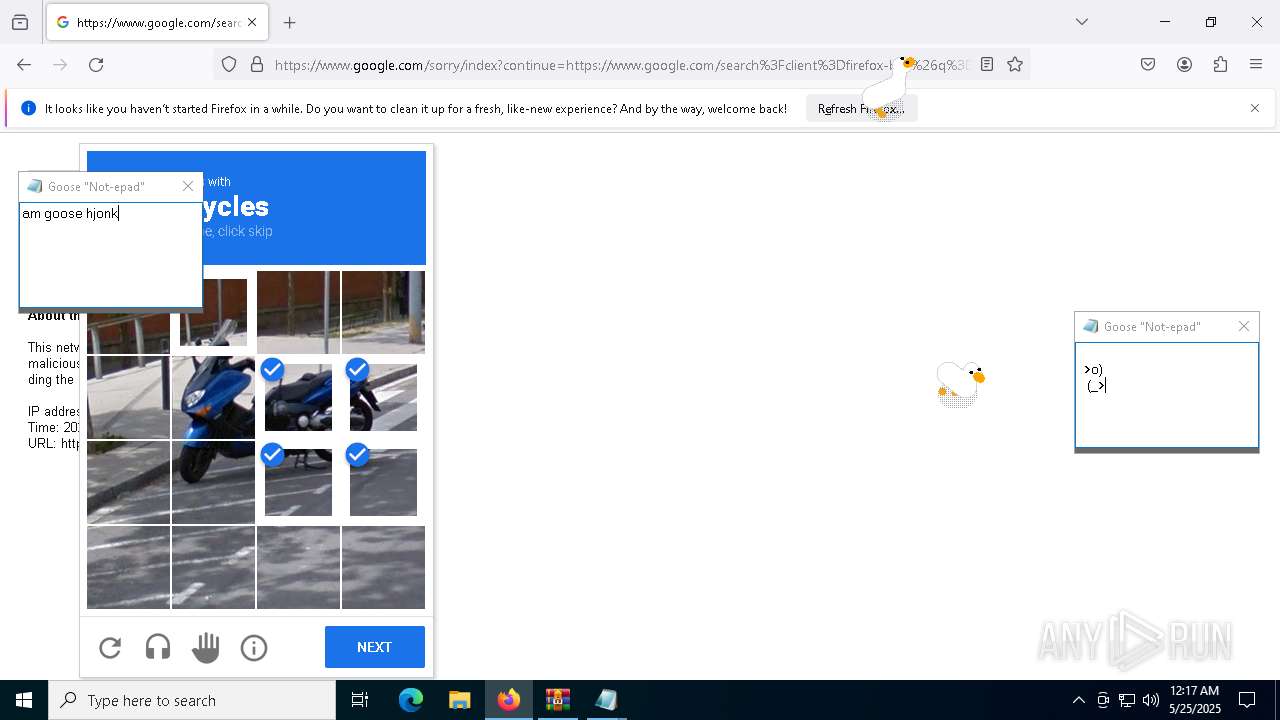
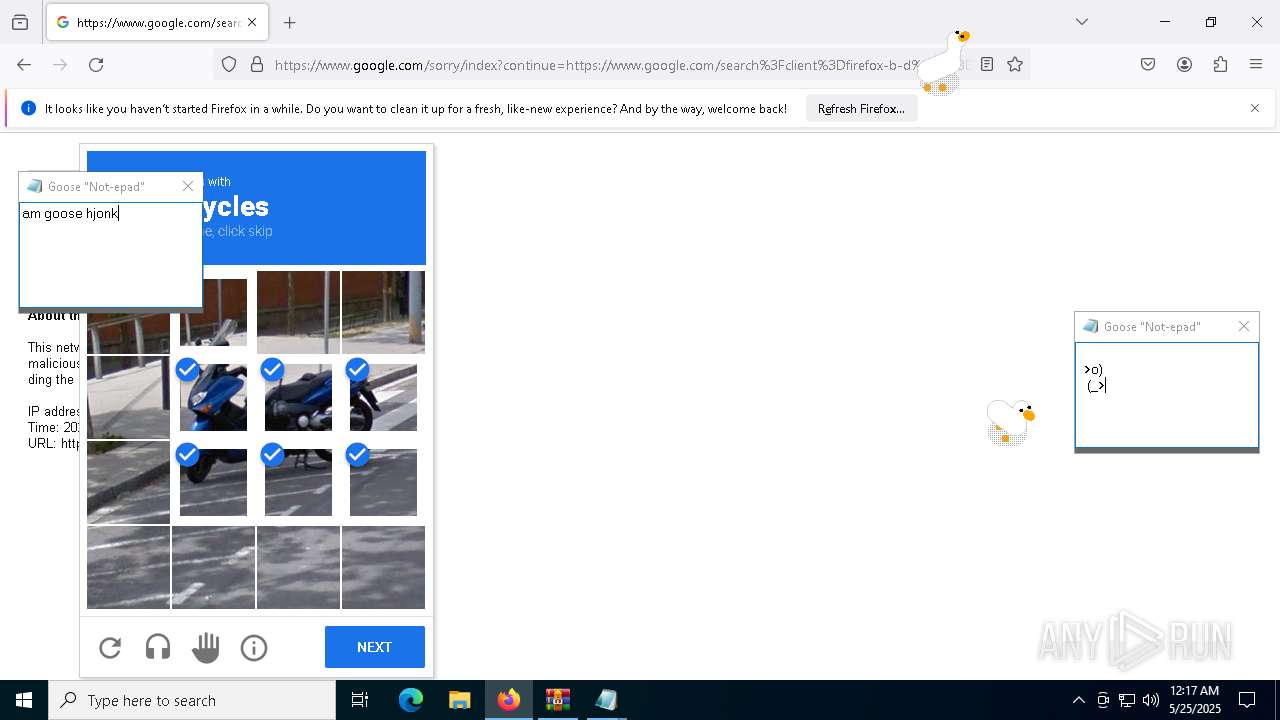
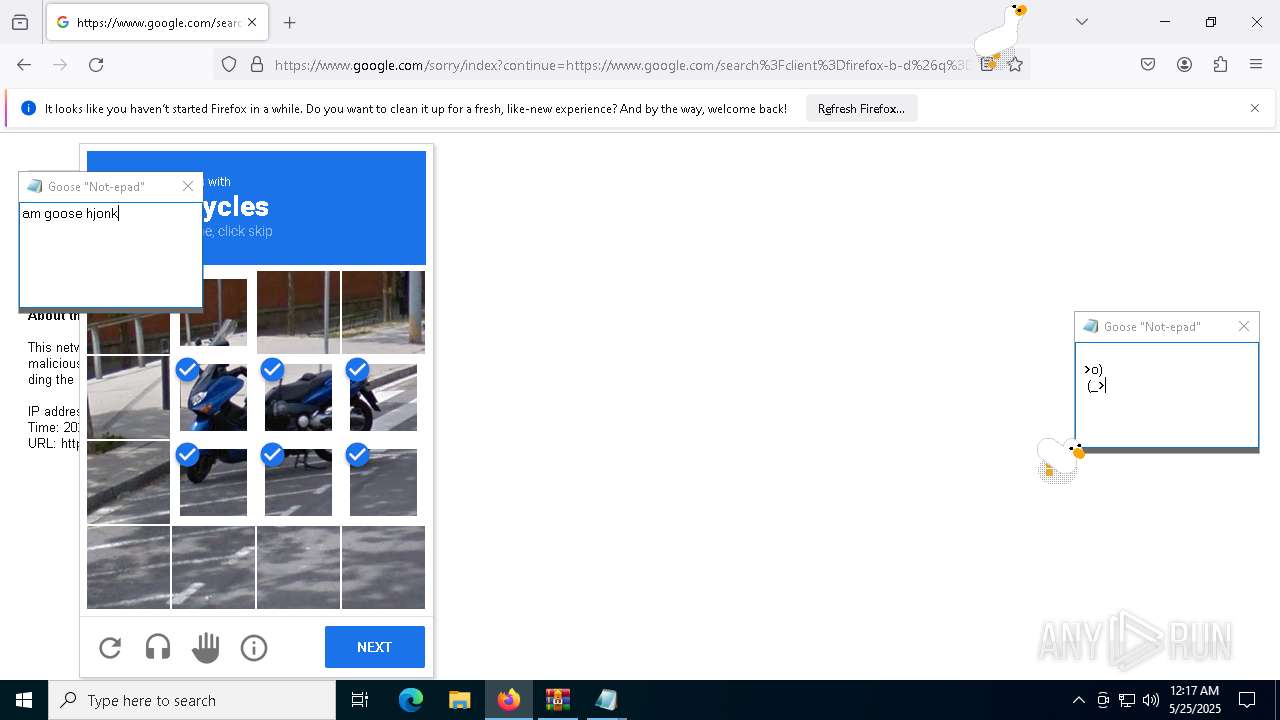
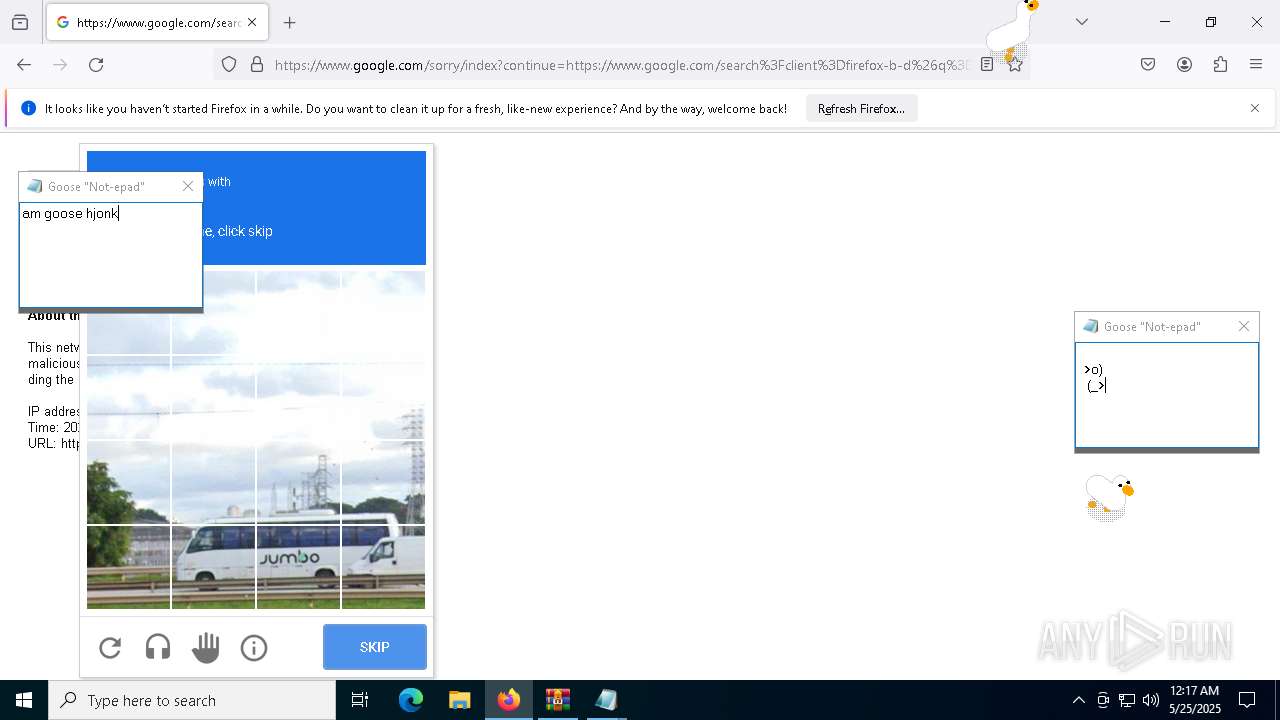
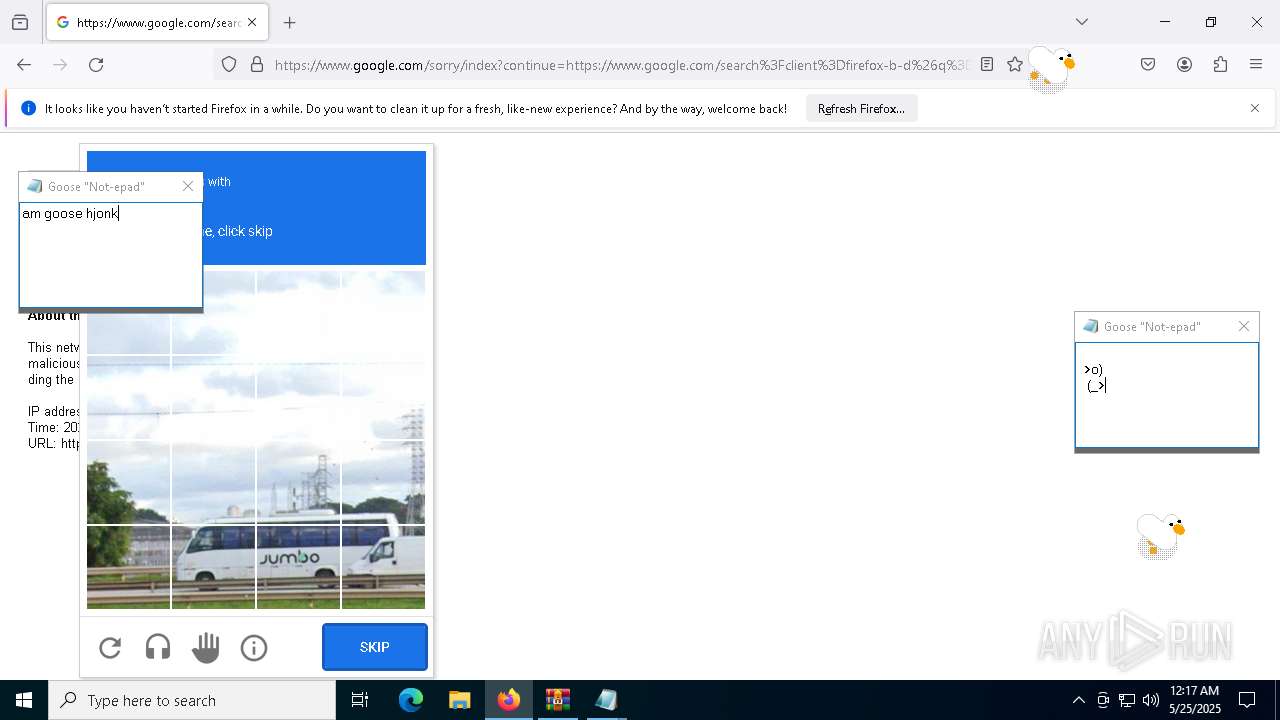
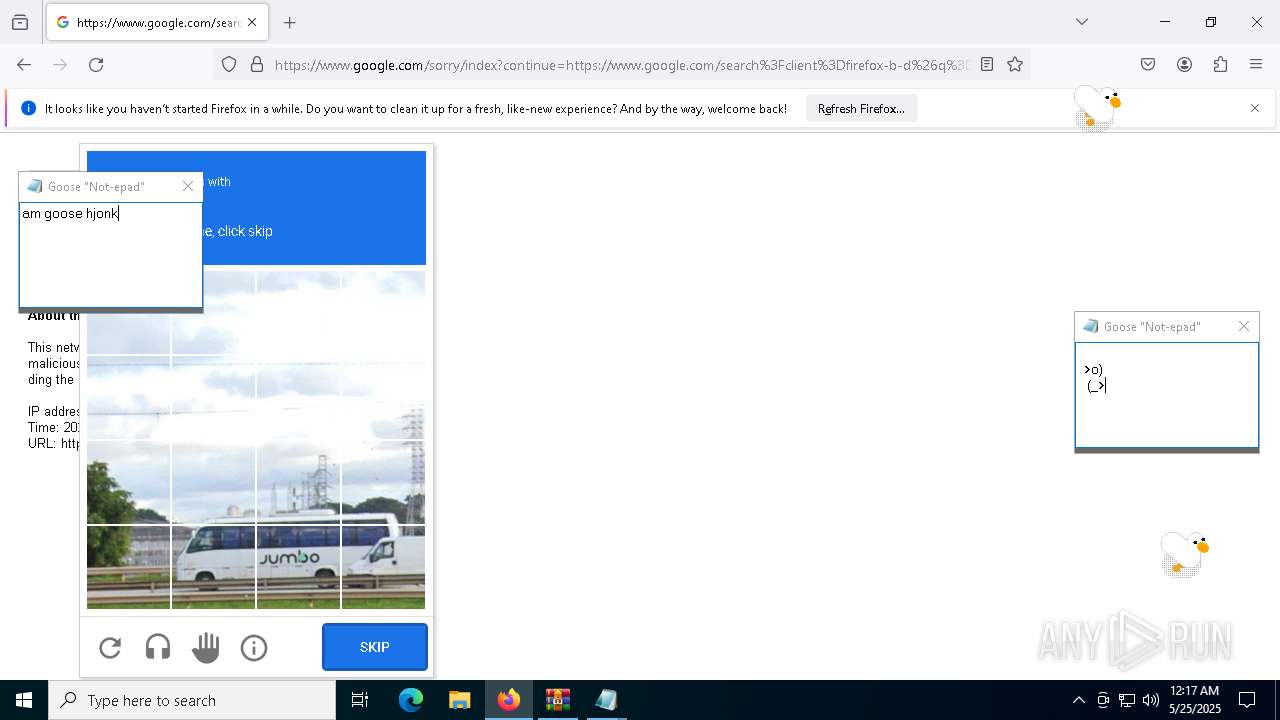
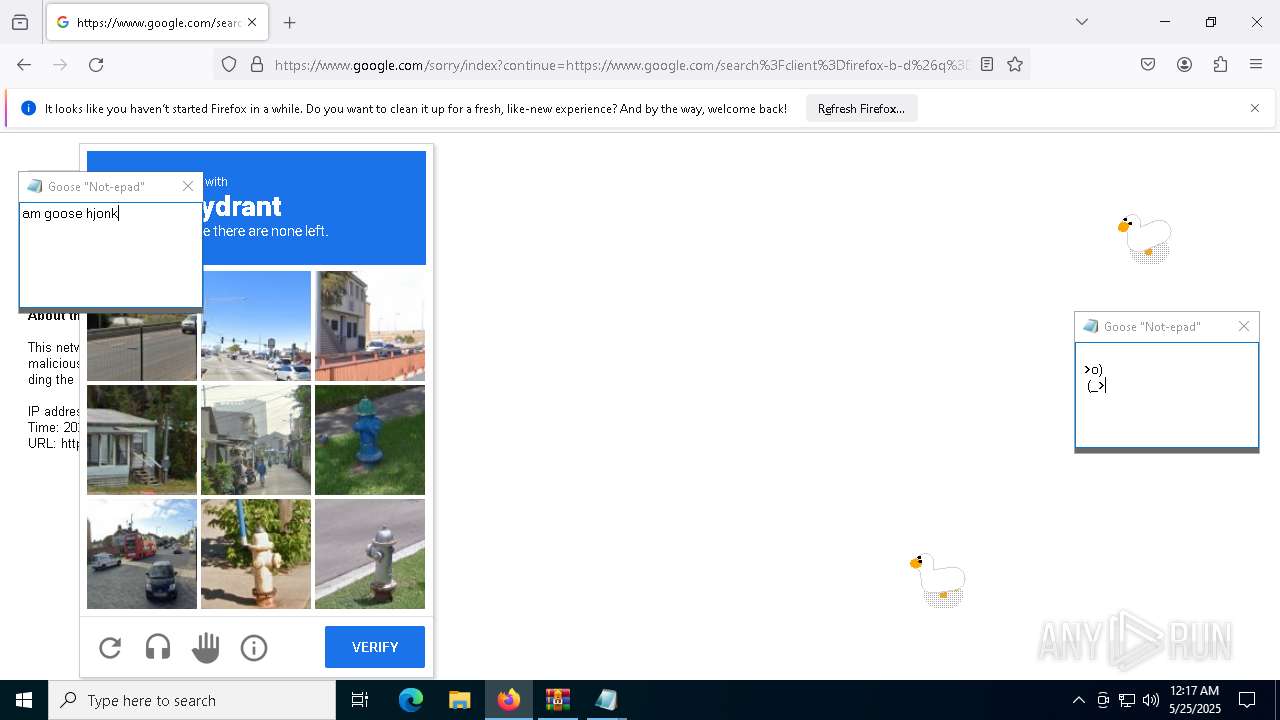
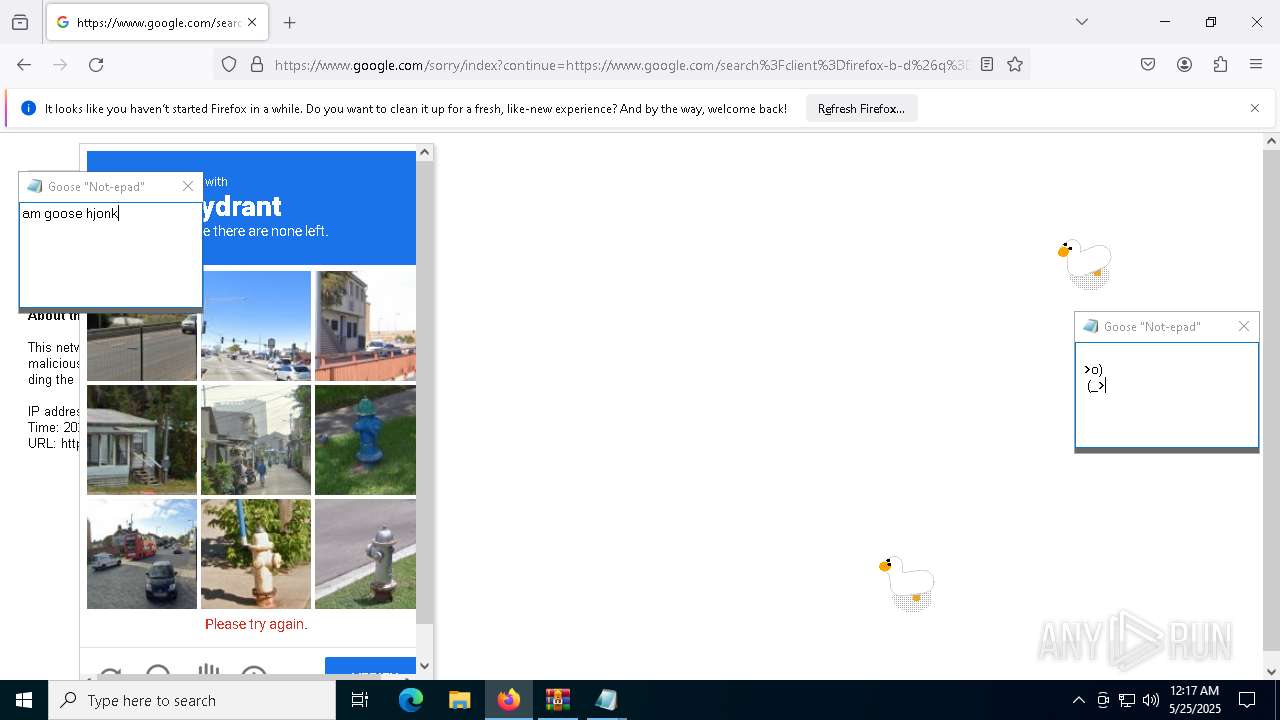
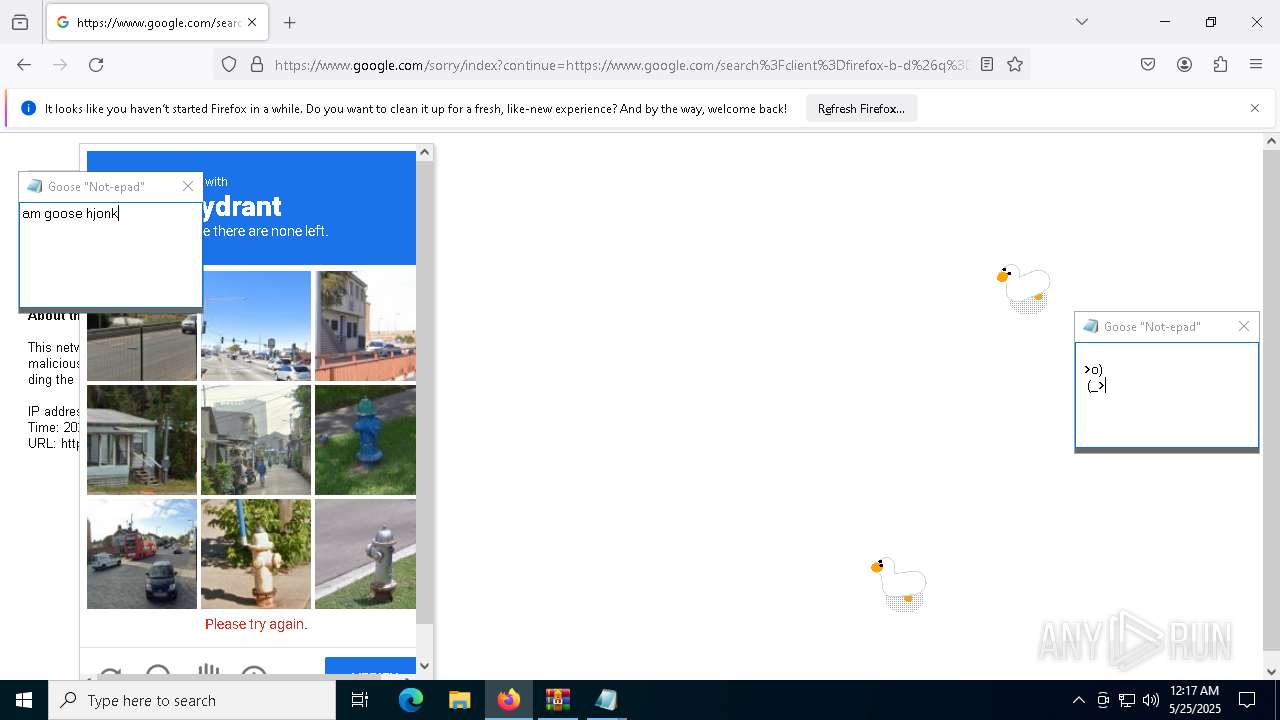
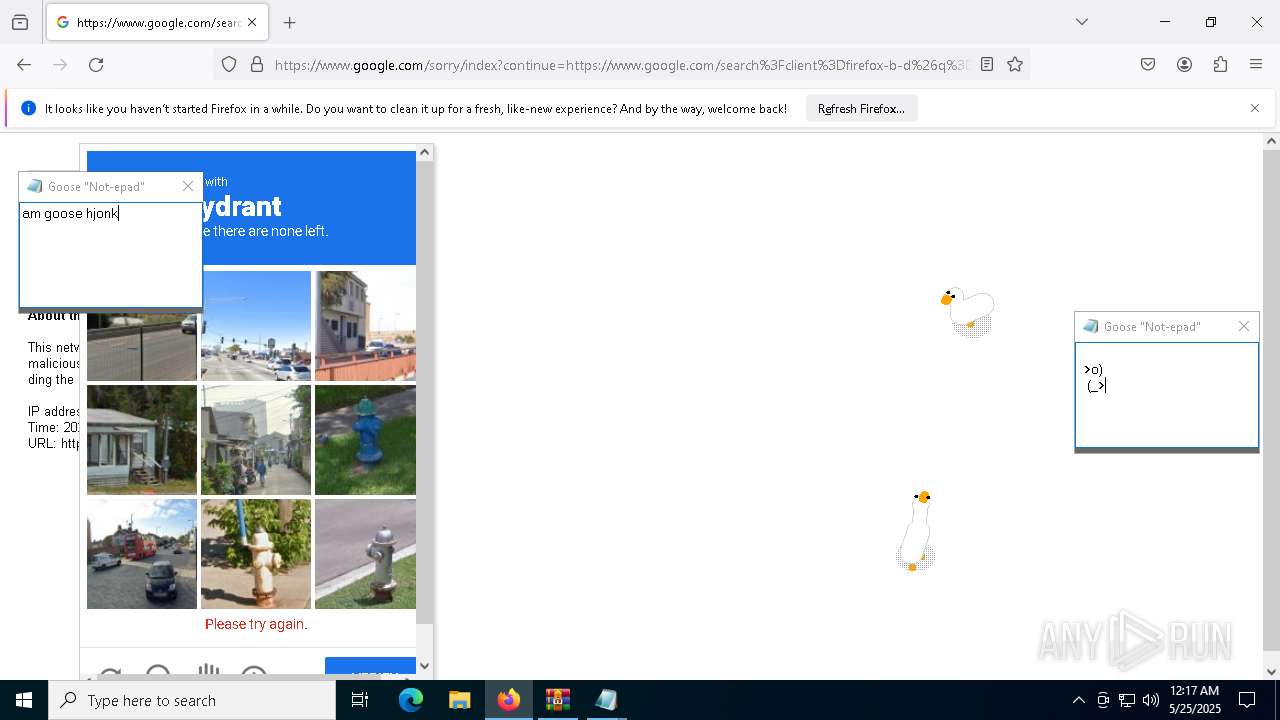
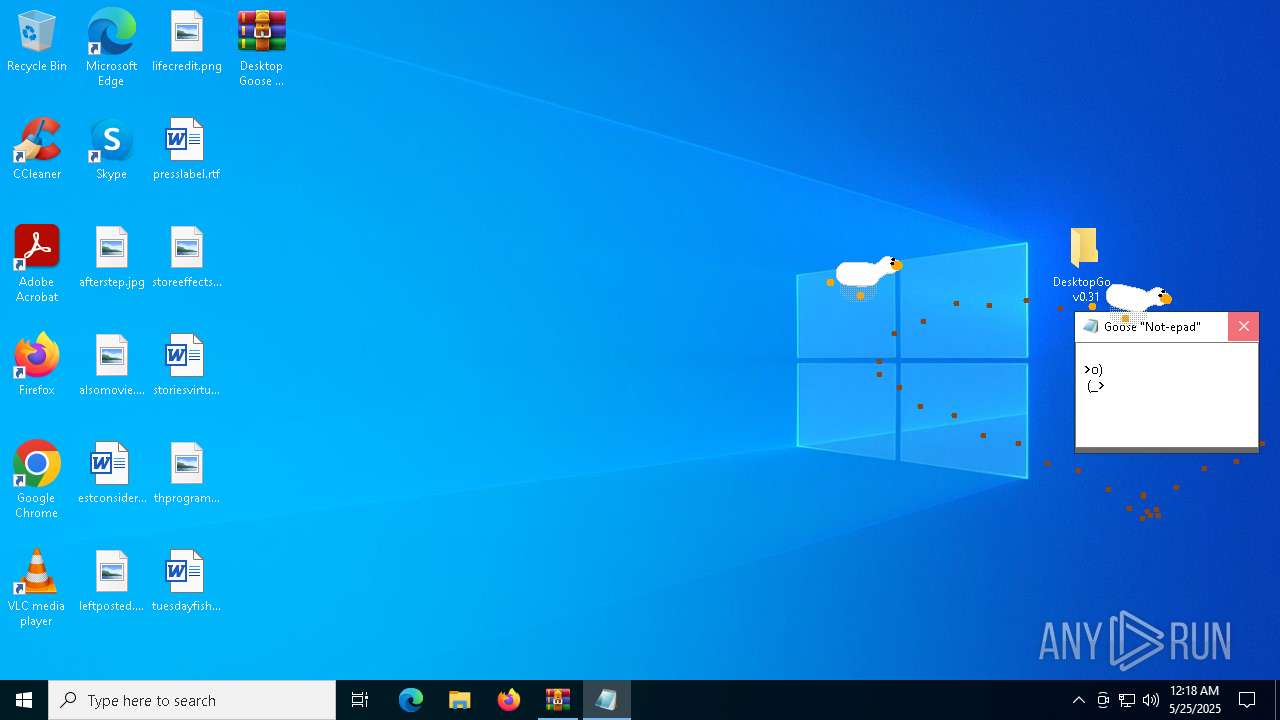
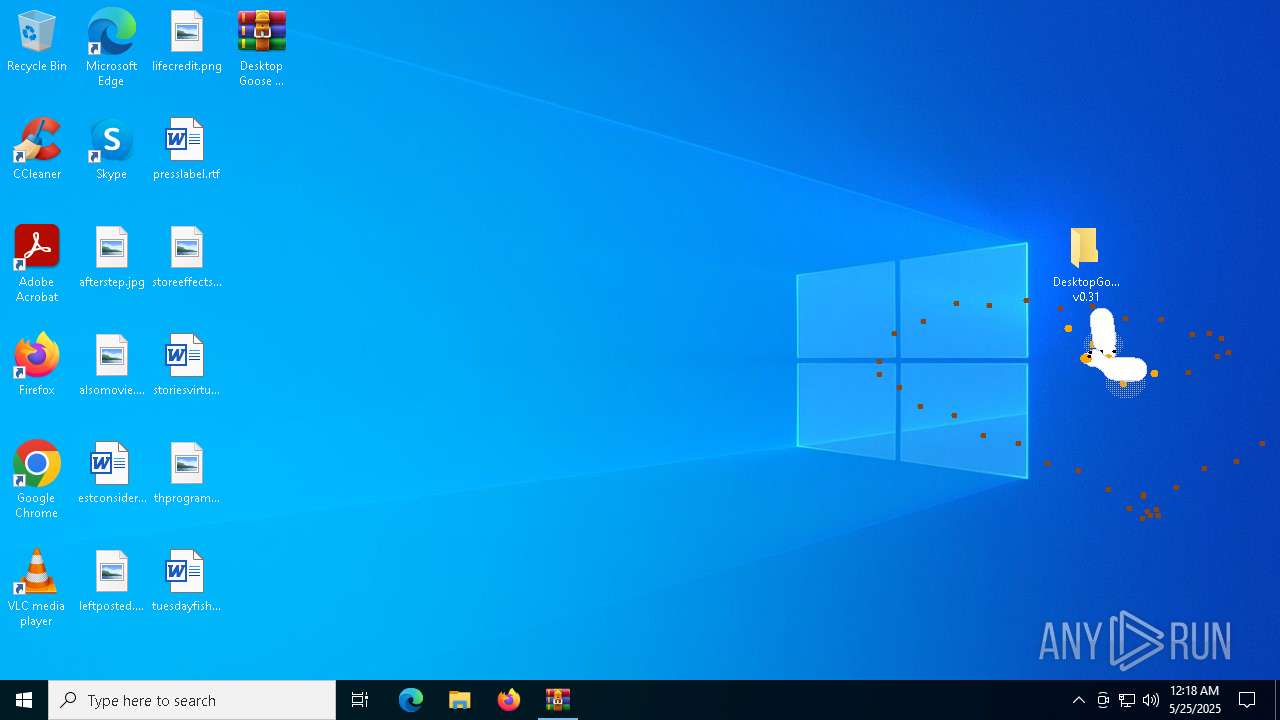
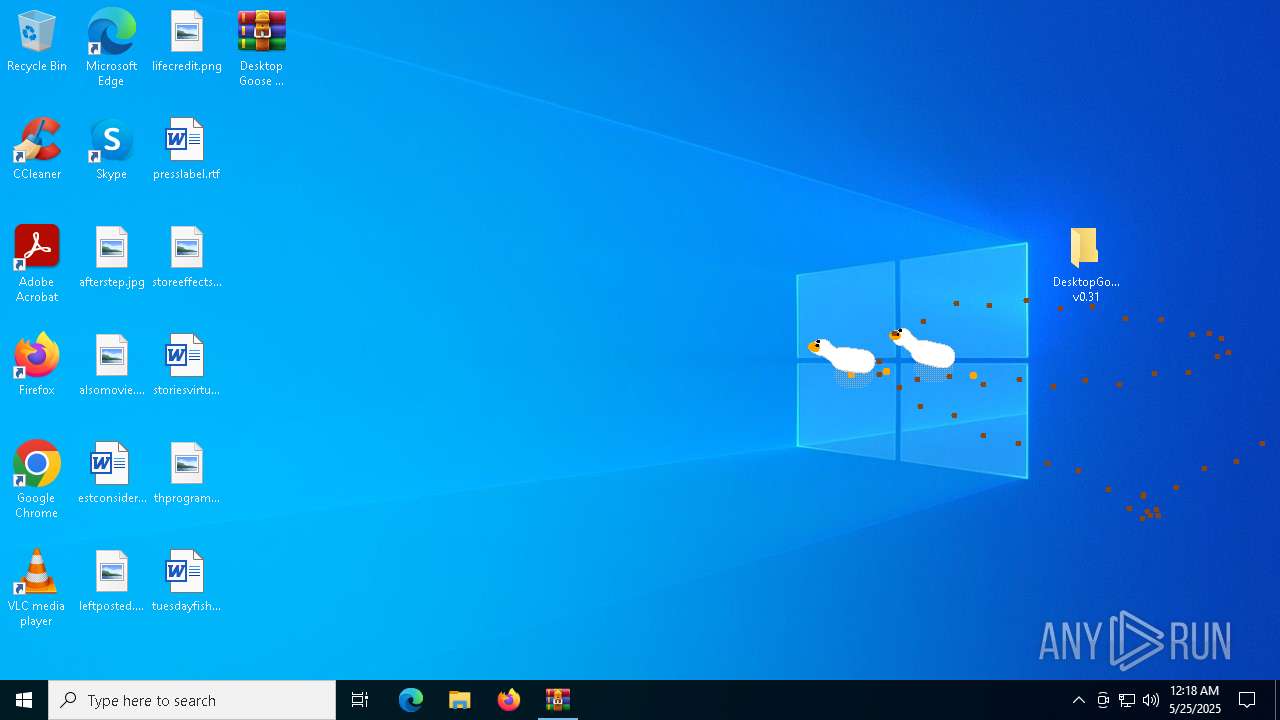
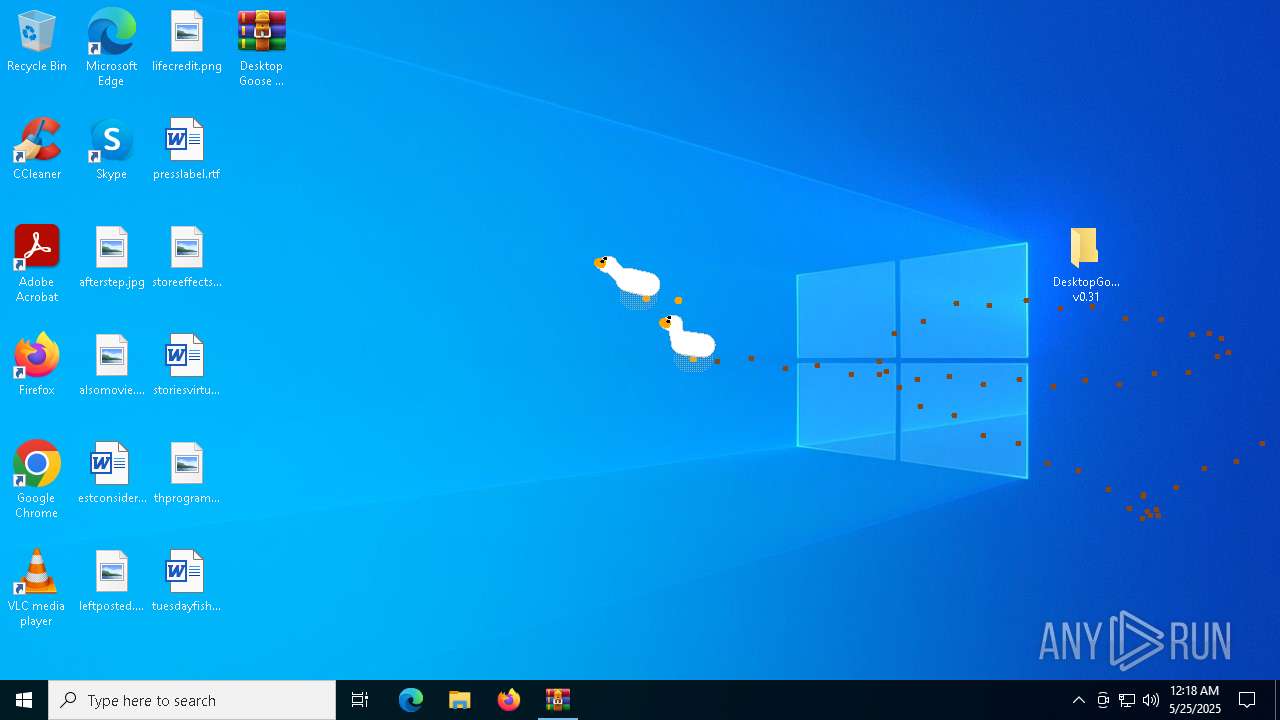
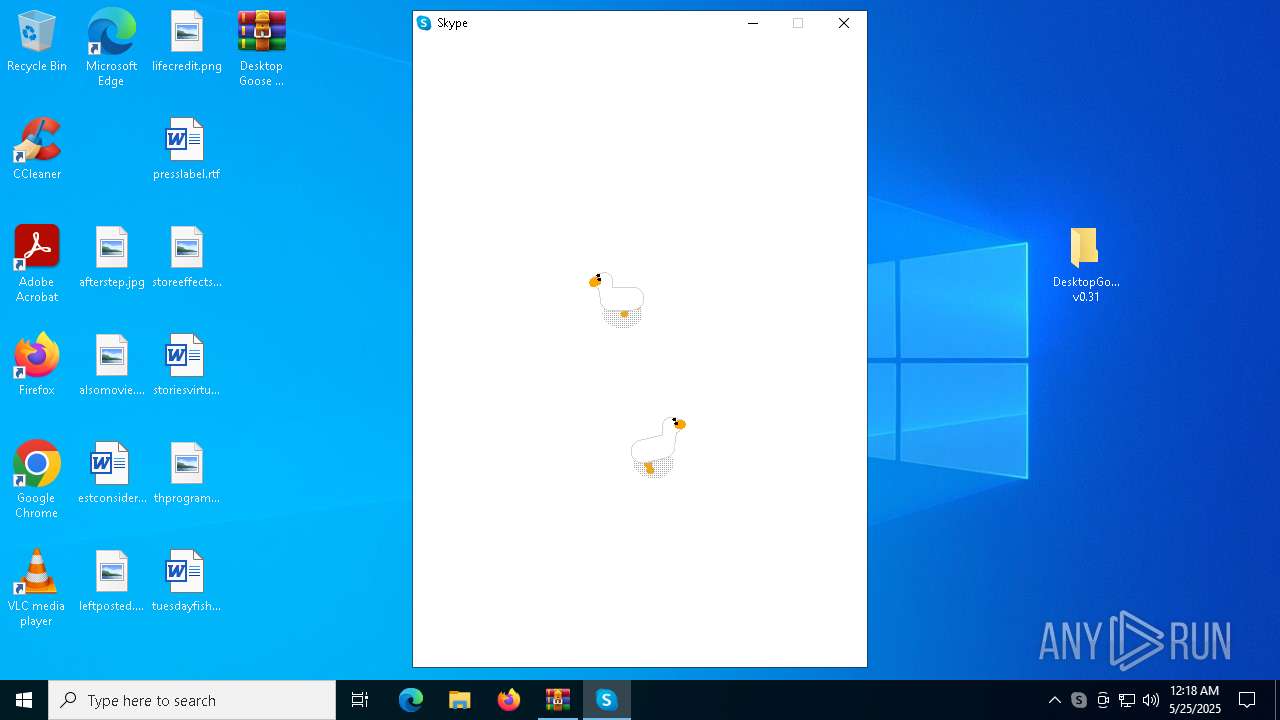
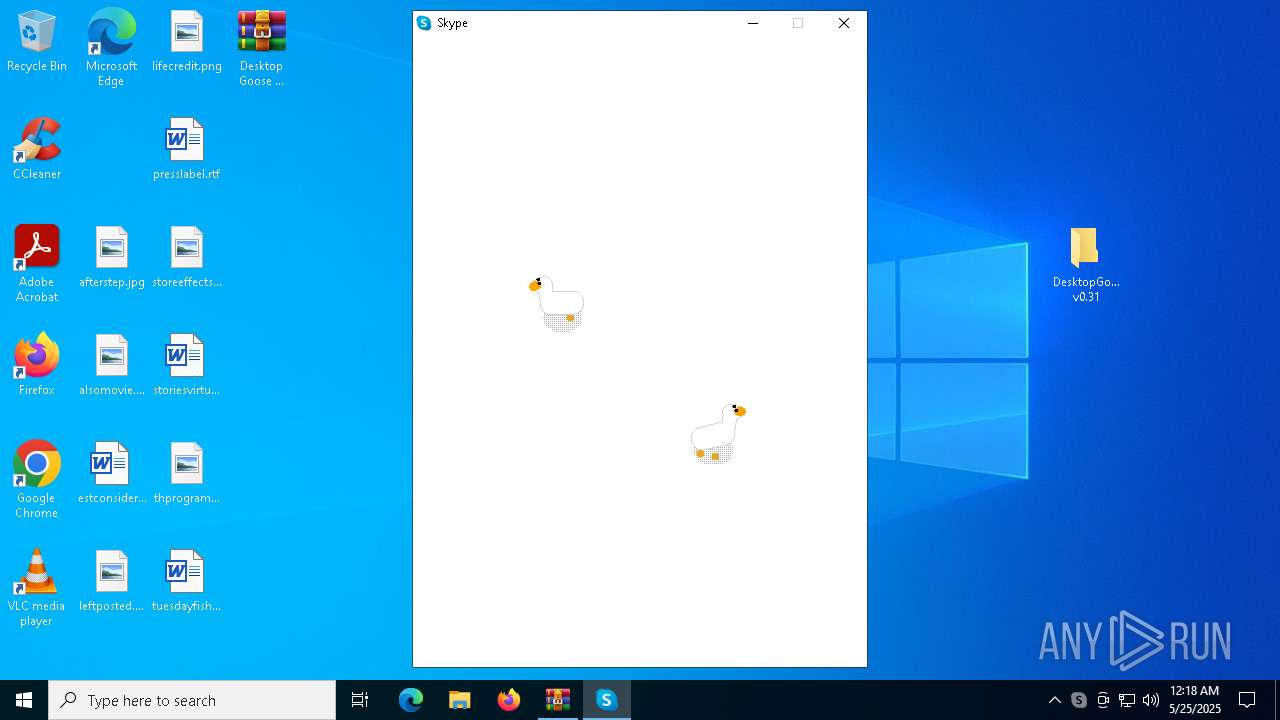
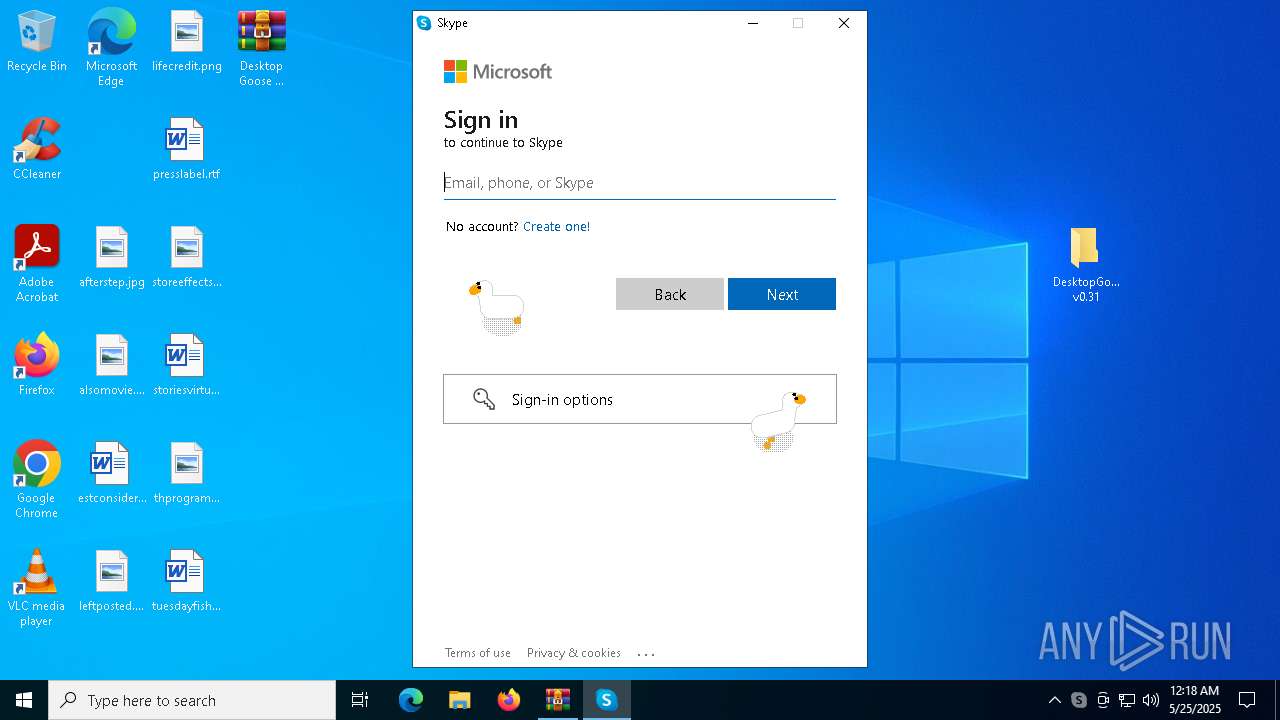
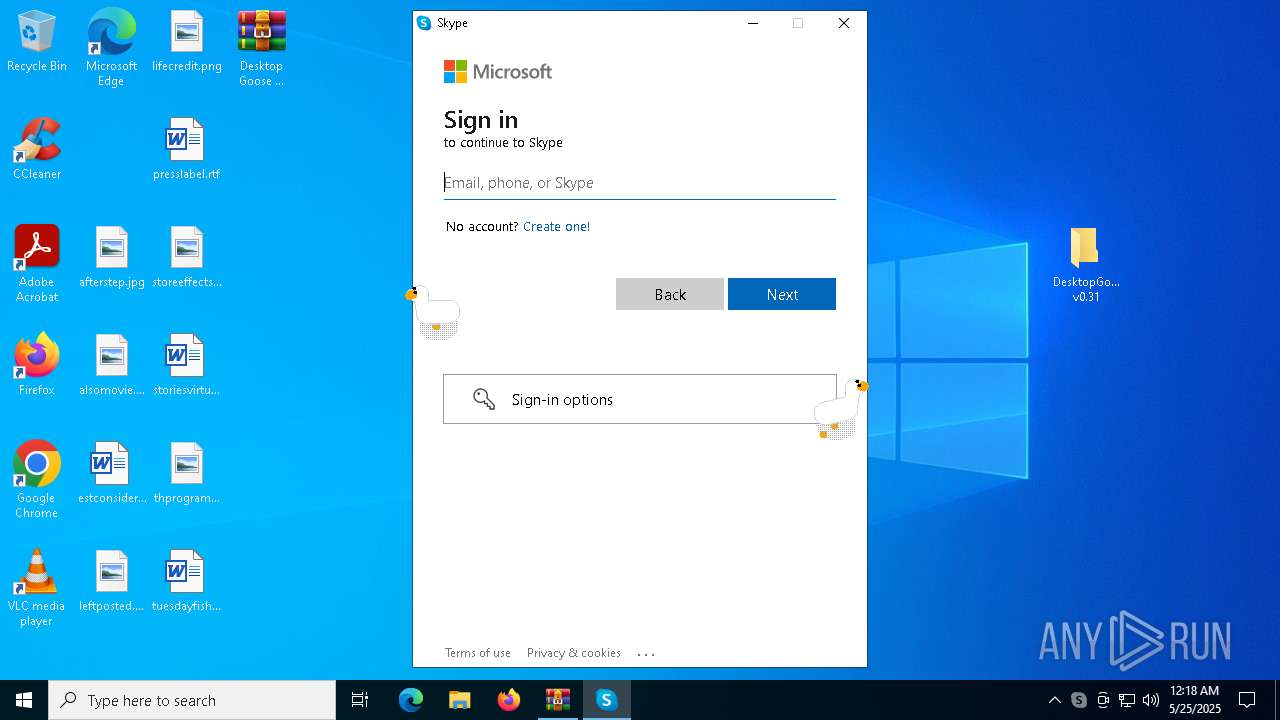
| File name: | Desktop Goose v0.31.zip |
| Full analysis: | https://app.any.run/tasks/c925eaf0-25cc-4cca-8d15-168baeb900db |
| Verdict: | Malicious activity |
| Analysis date: | May 25, 2025, 00:15:33 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | EAAD0961B52B14D9A323F092EF307D8A |
| SHA1: | FEB3AEDF16432B063FF93C90623A865A1FD5214A |
| SHA256: | E66264065923676807FD6D7B36F7C9DC52DB9EF1C5399B2811738EB5E22A30F6 |
| SSDEEP: | 98304:r2s1pAKXHAqe3S1s+2FpwDhbJ/XKGEzJKiMR7:dHAqEDP6D5J/tE1K3R7 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7684)
SUSPICIOUS
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 5600)
Application launched itself
- Skype.exe (PID: 7812)
Uses REG/REGEDIT.EXE to modify registry
- Skype.exe (PID: 7812)
There is functionality for taking screenshot (YARA)
- Skype.exe (PID: 7916)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 3024)
INFO
Reads the computer name
- GooseDesktop.exe (PID: 8108)
- GooseDesktop.exe (PID: 5556)
- ShellExperienceHost.exe (PID: 5600)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7684)
Checks supported languages
- GooseDesktop.exe (PID: 8108)
- GooseDesktop.exe (PID: 5556)
- ShellExperienceHost.exe (PID: 5600)
Manual execution by a user
- GooseDesktop.exe (PID: 8108)
- GooseDesktop.exe (PID: 5556)
- firefox.exe (PID: 6268)
- Skype.exe (PID: 7812)
- chrome.exe (PID: 1132)
- GooseDesktop.exe (PID: 6320)
- GooseDesktop.exe (PID: 6228)
Reads the machine GUID from the registry
- GooseDesktop.exe (PID: 8108)
- GooseDesktop.exe (PID: 5556)
Application launched itself
- firefox.exe (PID: 6268)
- firefox.exe (PID: 1012)
- chrome.exe (PID: 1132)
Node.js compiler has been detected
- Skype.exe (PID: 7812)
- Skype.exe (PID: 3800)
- Skype.exe (PID: 7916)
- Skype.exe (PID: 6244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (33.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2022:10:07 15:56:12 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Desktop Goose v0.31/DesktopGoose v0.31/ |
Total processes
307
Monitored processes
53
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3684 --field-trial-handle=1924,i,17266986424261216749,16796134871873530456,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1012 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1040 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2152 -parentBuildID 20240213221259 -prefsHandle 2144 -prefMapHandle 2132 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {c1b9f092-addf-4665-864a-3c6087fa96af} 1012 "\\.\pipe\gecko-crash-server-pipe.1012" 18611681110 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2192 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5132 -childID 3 -isForBrowser -prefsHandle 5124 -prefMapHandle 4236 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1496 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {1b3866f1-64d3-465a-9494-856232c5187e} 1012 "\\.\pipe\gecko-crash-server-pipe.1012" 18626ee5310 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2340 | C:\WINDOWS\system32\reg.exe QUERY HKCU\Software\Microsoft\Windows\Shell\Associations\UrlAssociations\microsoft-edge\UserChoice /v ProgId | C:\Windows\SysWOW64\reg.exe | — | Skype.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2432 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4812 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4924 -prefMapHandle 4920 -prefsLen 36588 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {ca67d011-b2df-41c9-a162-36e5962c9c42} 1012 "\\.\pipe\gecko-crash-server-pipe.1012" 186269e3b10 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 2852 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1904 -parentBuildID 20240213221259 -prefsHandle 1844 -prefMapHandle 1836 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {603d3e8d-2010-4c5a-a58d-d41f2fa69d0b} 1012 "\\.\pipe\gecko-crash-server-pipe.1012" 1861e3f0410 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 2984 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5884 -childID 6 -isForBrowser -prefsHandle 5896 -prefMapHandle 5892 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1496 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {461c128d-6e21-4c6f-9b72-e1faea9f689d} 1012 "\\.\pipe\gecko-crash-server-pipe.1012" 186269a5d90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
30 349
Read events
30 196
Write events
130
Delete events
23
Modification events
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Desktop Goose v0.31.zip | |||
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (8108) GooseDesktop.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\ActiveMovie\devenum\{4EFE2452-168A-11D1-BC76-00C04FB9453B}\Default MidiOut Device |
| Operation: | write | Name: | FriendlyName |
Value: Default MidiOut Device | |||
| (PID) Process: | (8108) GooseDesktop.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\ActiveMovie\devenum\{4EFE2452-168A-11D1-BC76-00C04FB9453B}\Default MidiOut Device |
| Operation: | write | Name: | CLSID |
Value: {07B65360-C445-11CE-AFDE-00AA006C14F4} | |||
Executable files
9
Suspicious files
350
Text files
87
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7684.46156\Desktop Goose v0.31\DesktopGoose v0.31\Assets\Images\MemeAttributions.txt | text | |
MD5:FC280867F6CF727FF169B24371019A93 | SHA256:C6134785BB0927CCE100B3B02EC08EDFA0A3E485F16B2481EE28F8CFAD208AB7 | |||
| 7684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7684.46156\Desktop Goose v0.31\DesktopGoose v0.31\Assets\Mods\Autumn\Autumn.dll | executable | |
MD5:AD4B80CC7EA519628734687452B8AC0E | SHA256:5C0024FD7CB4FE2424C3C04C6036A2C67BB460F67A04B652AFEEB5D4C757B70F | |||
| 7684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7684.46156\Desktop Goose v0.31\DesktopGoose v0.31\Assets\Images\Memes\Meme1.png | image | |
MD5:EC6A7941AA0D1C3CD0A7B724324FBB96 | SHA256:FE5EE195C07EBFC789F15CE771CC0F003AE43C0D5115C193D0F876DE00C18DBE | |||
| 7684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7684.46156\Desktop Goose v0.31\DesktopGoose v0.31\Assets\Images\Memes\Meme6.png | image | |
MD5:E46D6D7154CEBF37D064C537F5D01F36 | SHA256:A078C89DE64C606313E251122A4D6025FF3F76CD941F1FB2195938E6173CF9F1 | |||
| 7684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7684.46156\Desktop Goose v0.31\DesktopGoose v0.31\Assets\Images\Memes\Meme3.png | image | |
MD5:CEF6B9818BC01655614FB969CFFC155F | SHA256:37BC0E217C6D6BF3EAF31072C02F010E785F4935ABE9849FBEE96D586D0904A7 | |||
| 7684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7684.46156\Desktop Goose v0.31\DesktopGoose v0.31\Assets\Images\Memes\Meme2.png | image | |
MD5:4F21B82BAC2893AFEC41A77EB024E3BB | SHA256:77AA8C017272C774BB0BB59D21A409DF09635676443919C7E5523ABE3908AE88 | |||
| 7684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7684.46156\Desktop Goose v0.31\DesktopGoose v0.31\Assets\Images\Memes\Meme4.png | image | |
MD5:AF4BEF7B9F4F37AC62E782B5B59D02AA | SHA256:9FCC9A9ADCD231656E848B9B42BAB449EA5A083CBF3A7A987C2E52963D9CF6D0 | |||
| 7684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7684.46156\Desktop Goose v0.31\DesktopGoose v0.31\Assets\Images\OtherGfx\DonatePage.png | image | |
MD5:2E137058FEA9426215796FF5C341D4AA | SHA256:A6D7047BCF036513D32182339A049D04323CB5A113D0147514BF743E01EDEA2B | |||
| 7684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7684.46156\Desktop Goose v0.31\DesktopGoose v0.31\Assets\Sound\NotEmbedded\Honk2.mp3 | binary | |
MD5:3B86BF25CD702A3A071590F088FABF64 | SHA256:7C8864E0B63969E2469C2D80CD855648044CD15FD89DBABD275954EFB7EF6879 | |||
| 7684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7684.46156\Desktop Goose v0.31\DesktopGoose v0.31\Assets\Images\OtherGfx\heart.png | image | |
MD5:76F468AA187E5C042C7EF5AE6A8A0753 | SHA256:11AE0A796817293FA0FB66978614A0BB87D249299AB4A75439BF56502358C0ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
148
DNS requests
168
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7780 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7780 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1012 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
1012 | firefox.exe | POST | 200 | 2.16.206.143:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
1012 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
1012 | firefox.exe | POST | 200 | 2.16.206.143:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
1012 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6724 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |