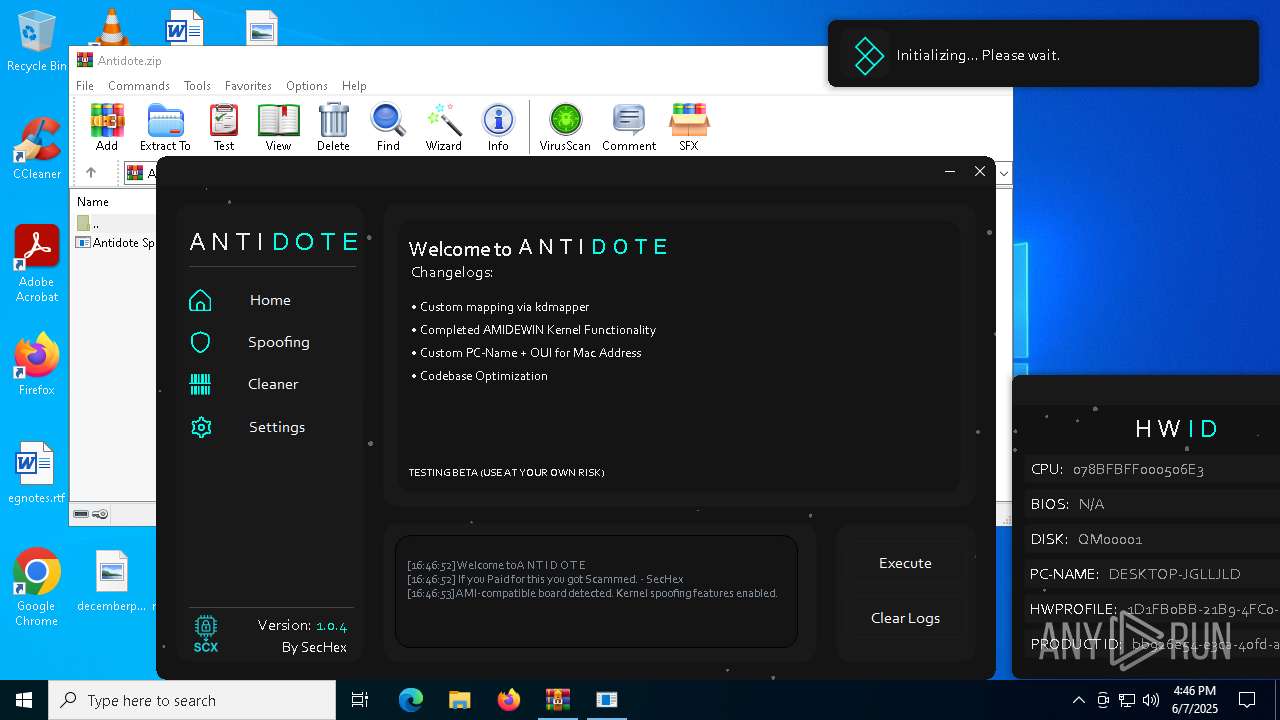
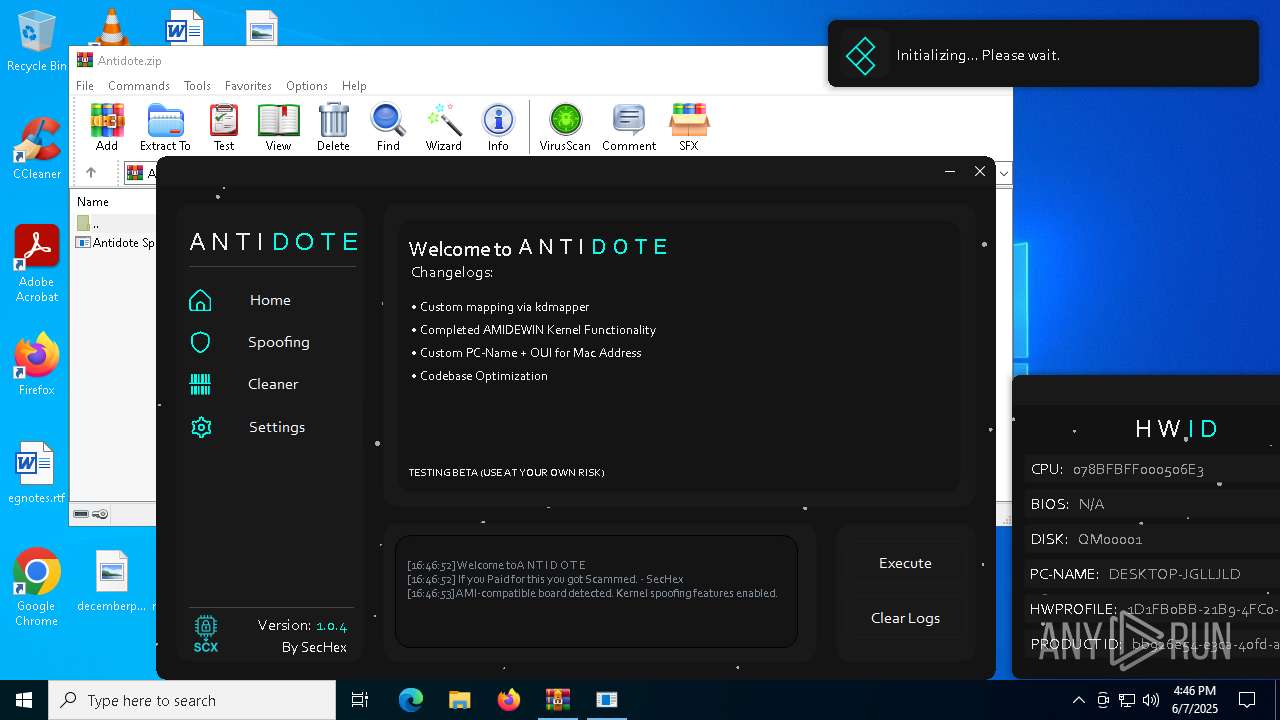
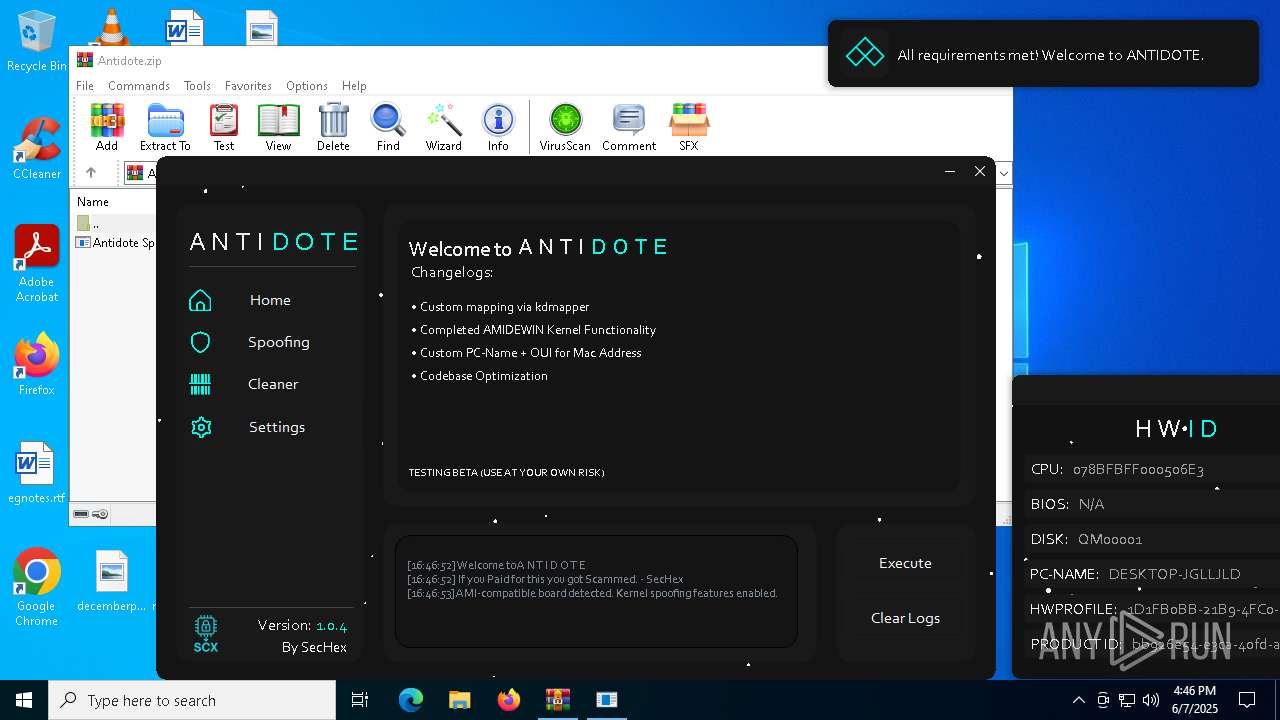
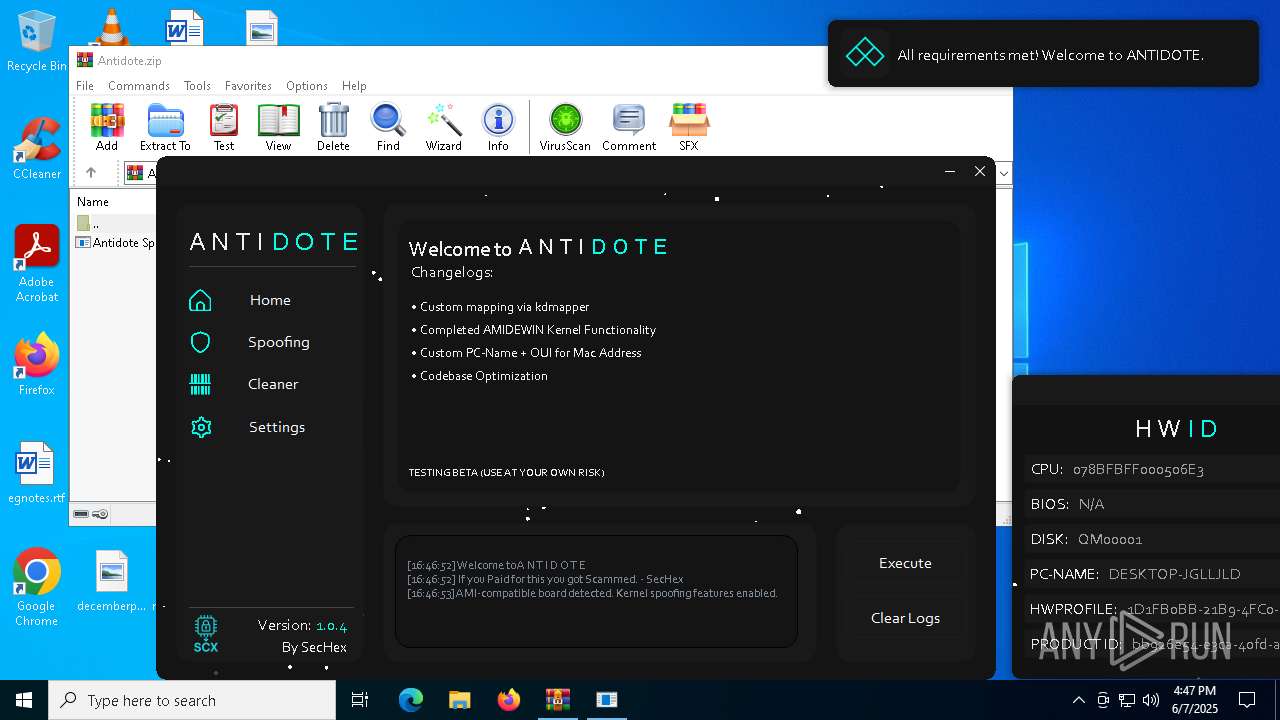
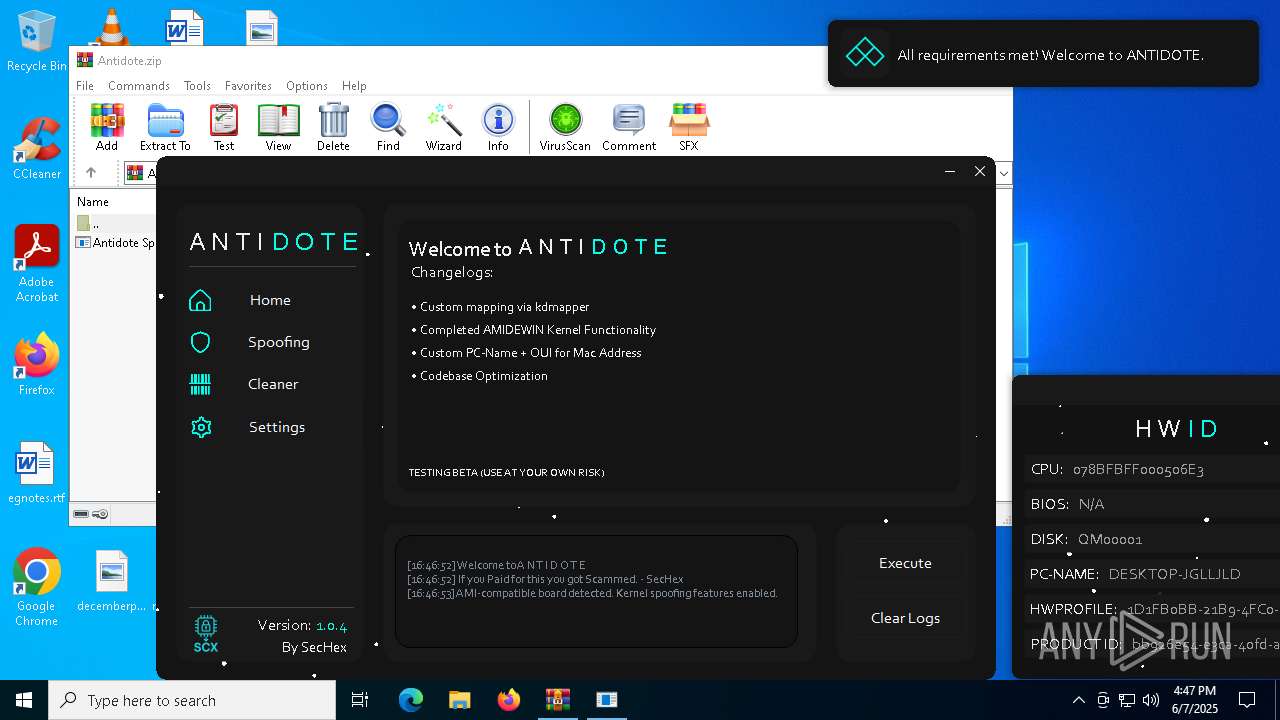
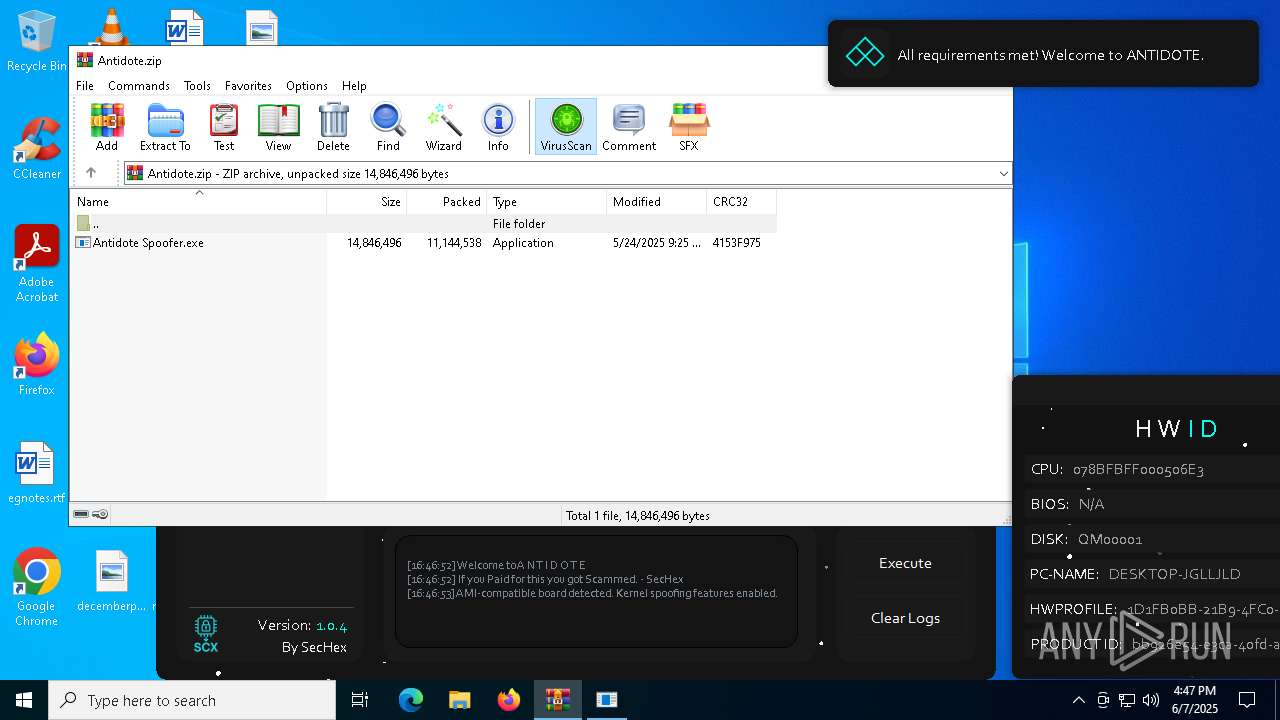
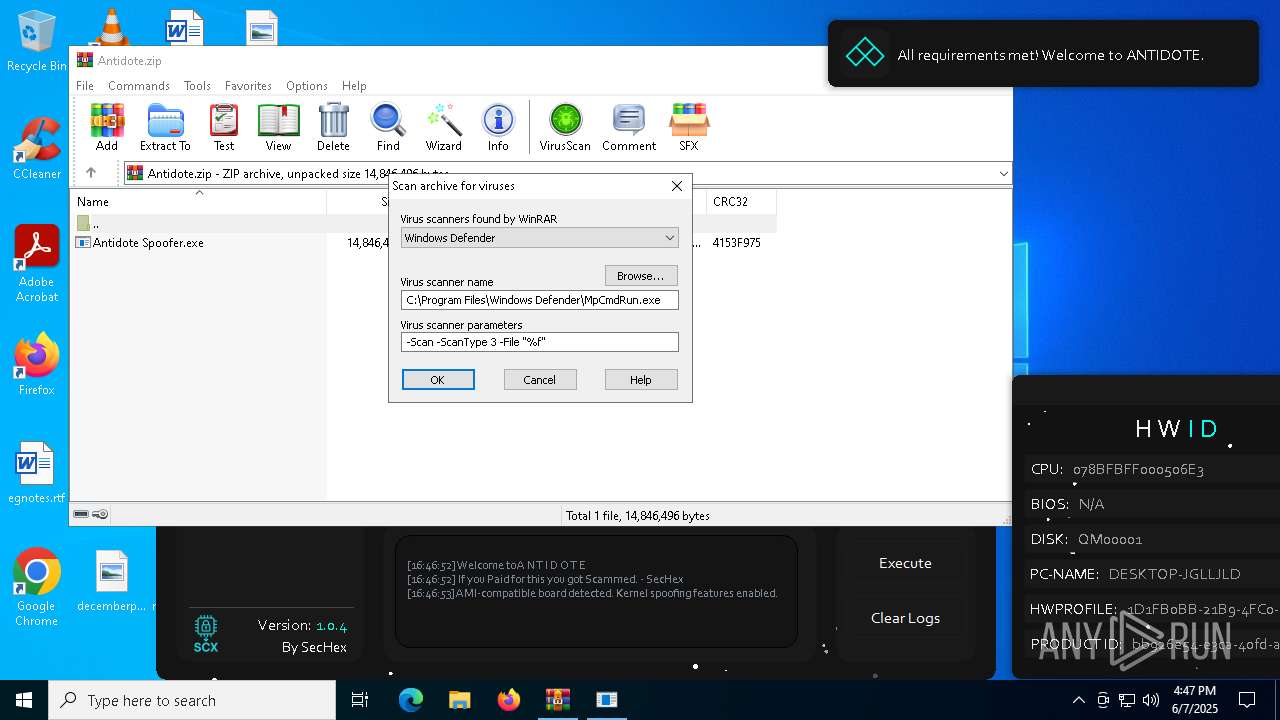
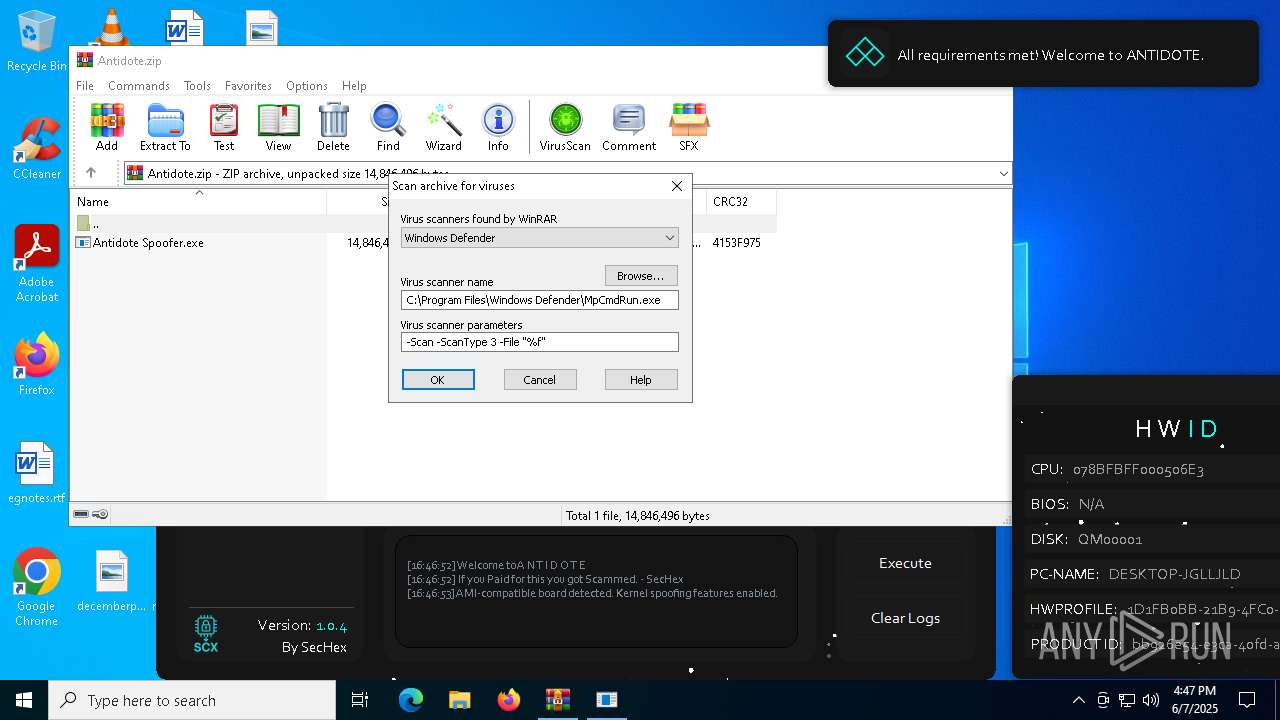
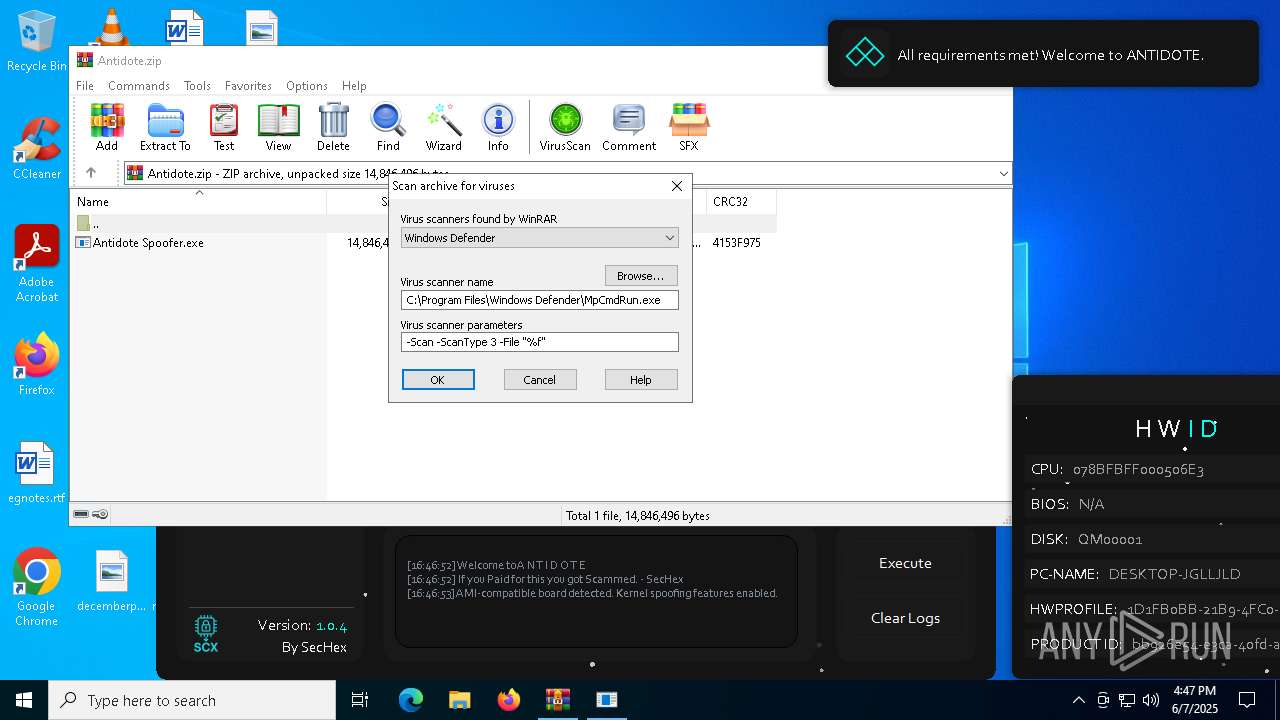
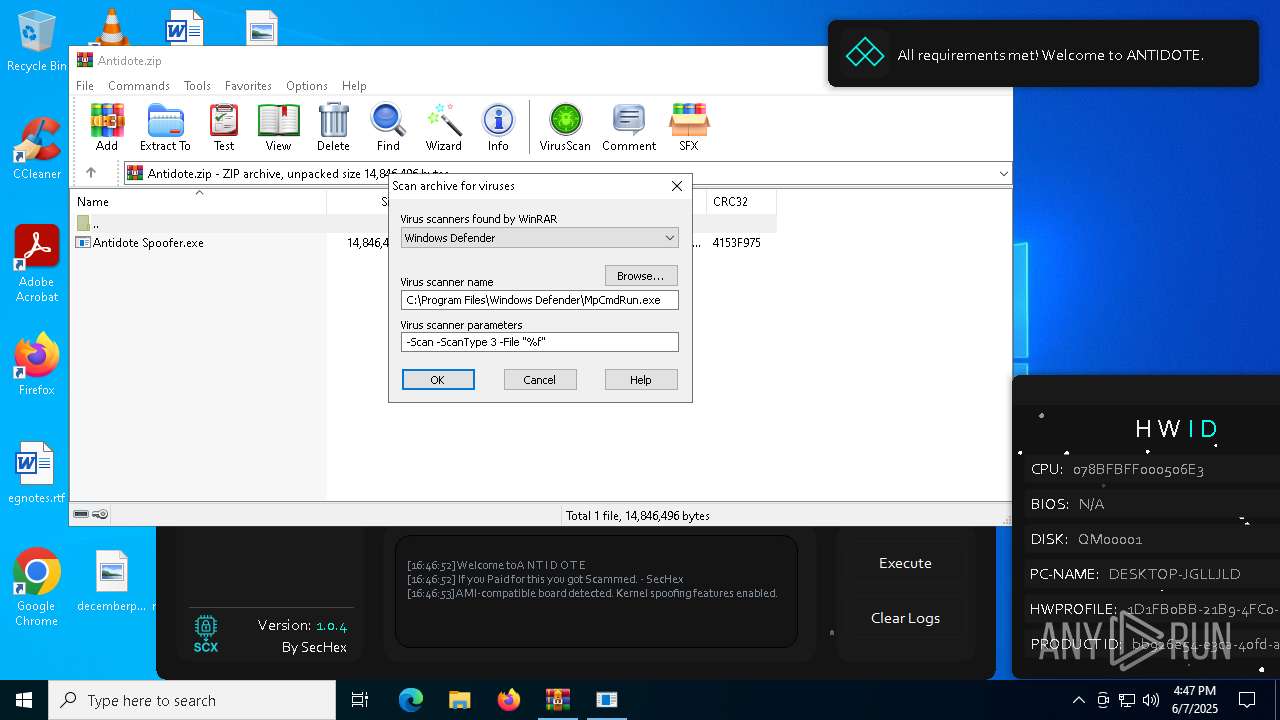
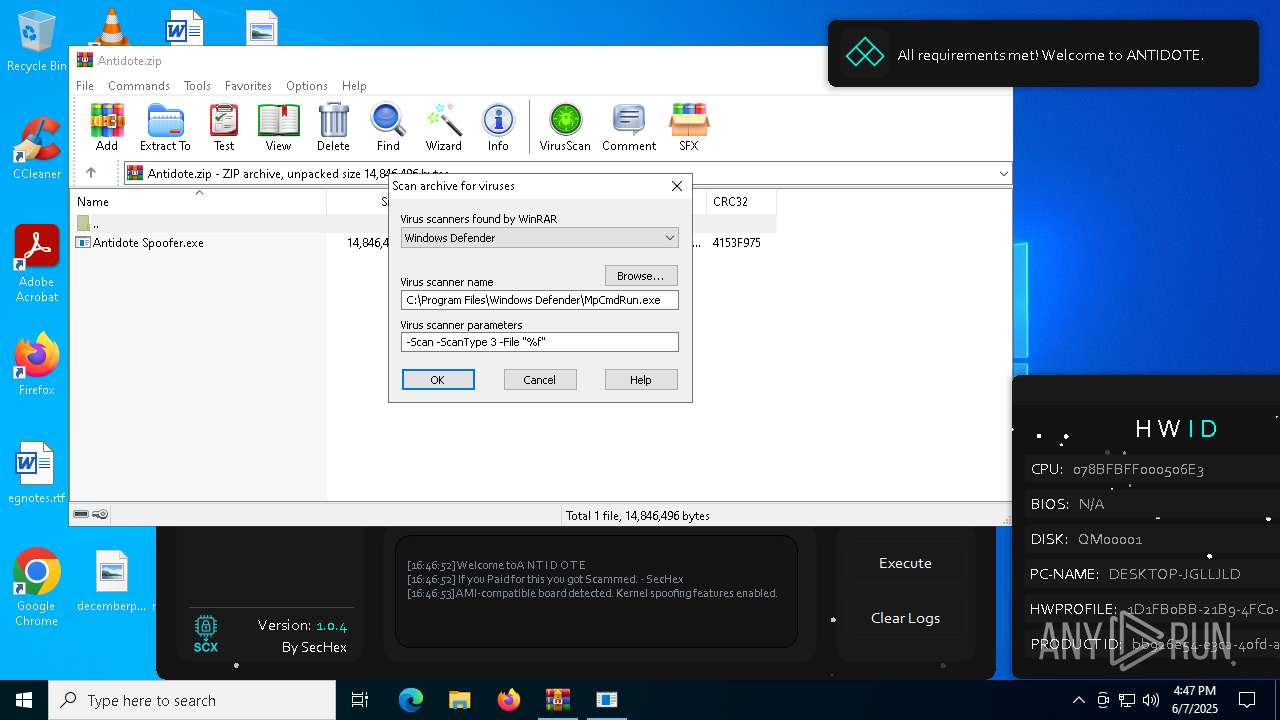
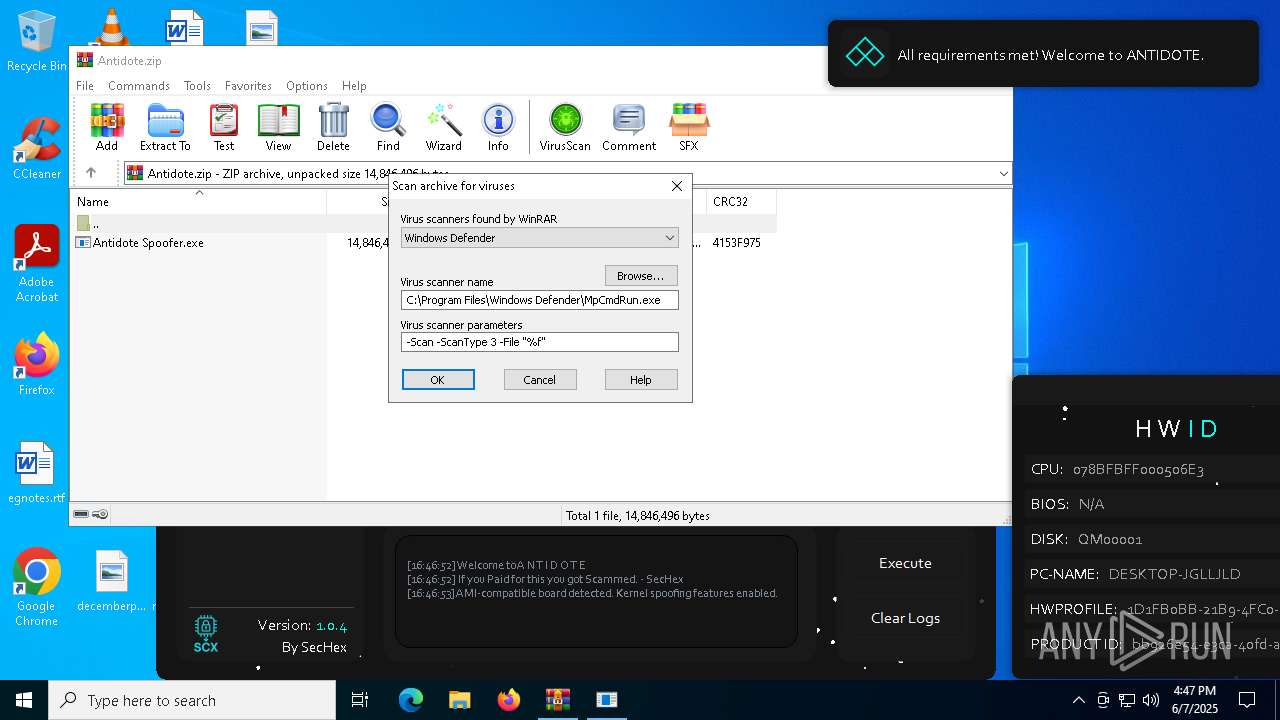
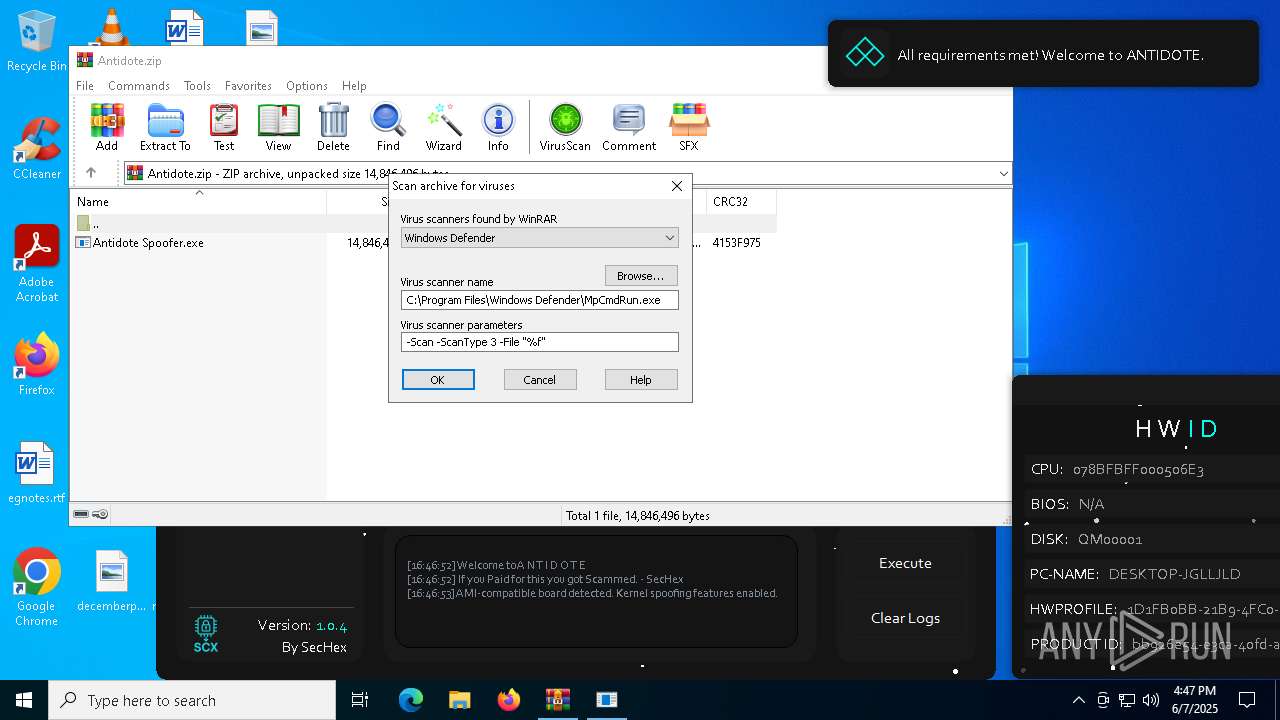
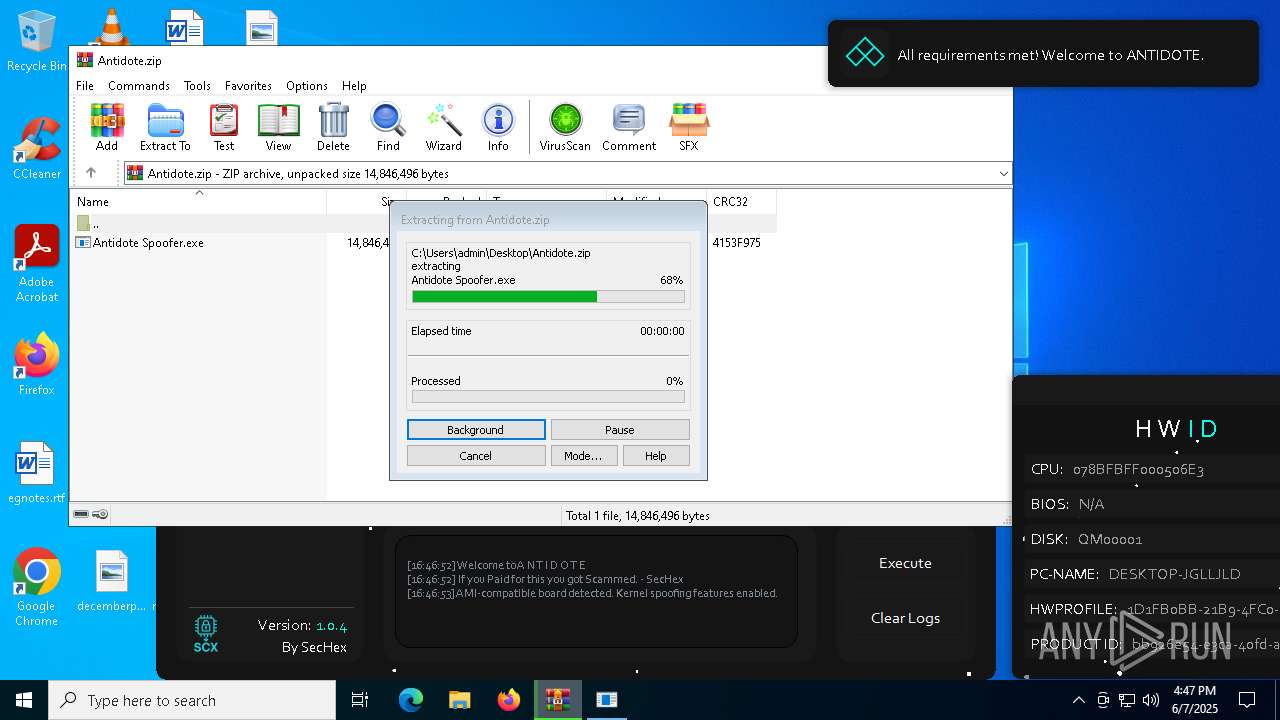
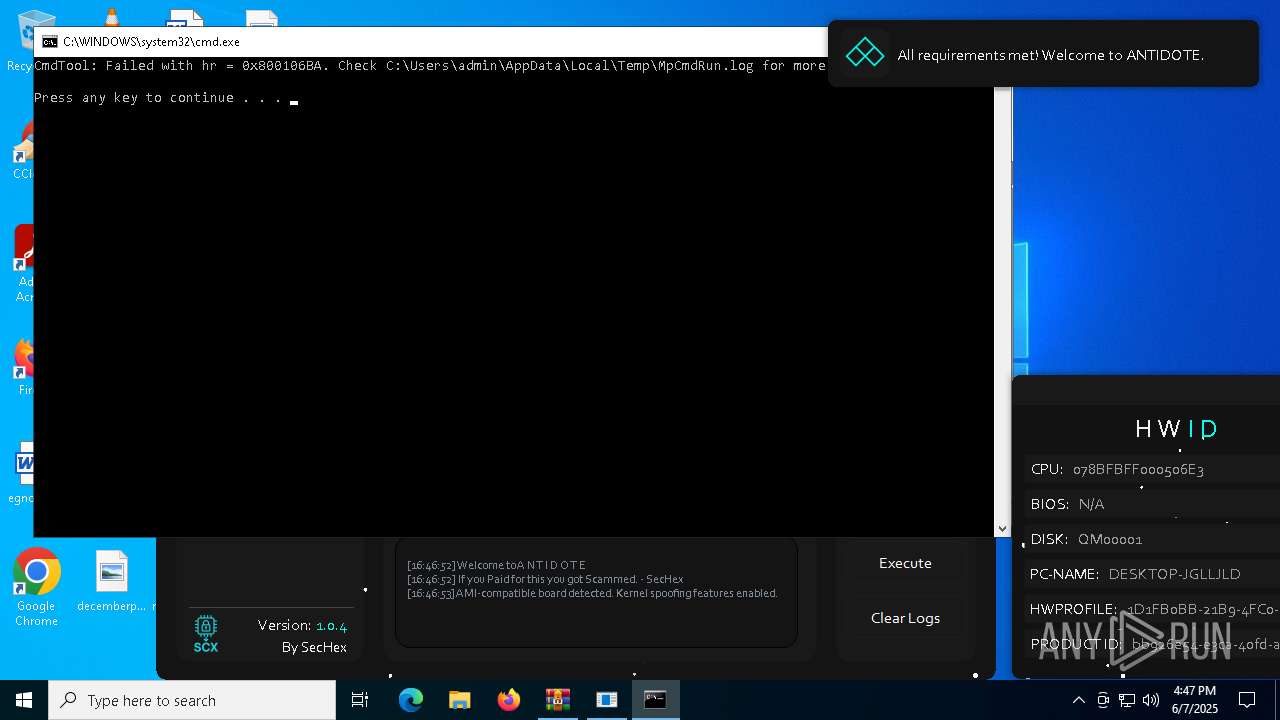
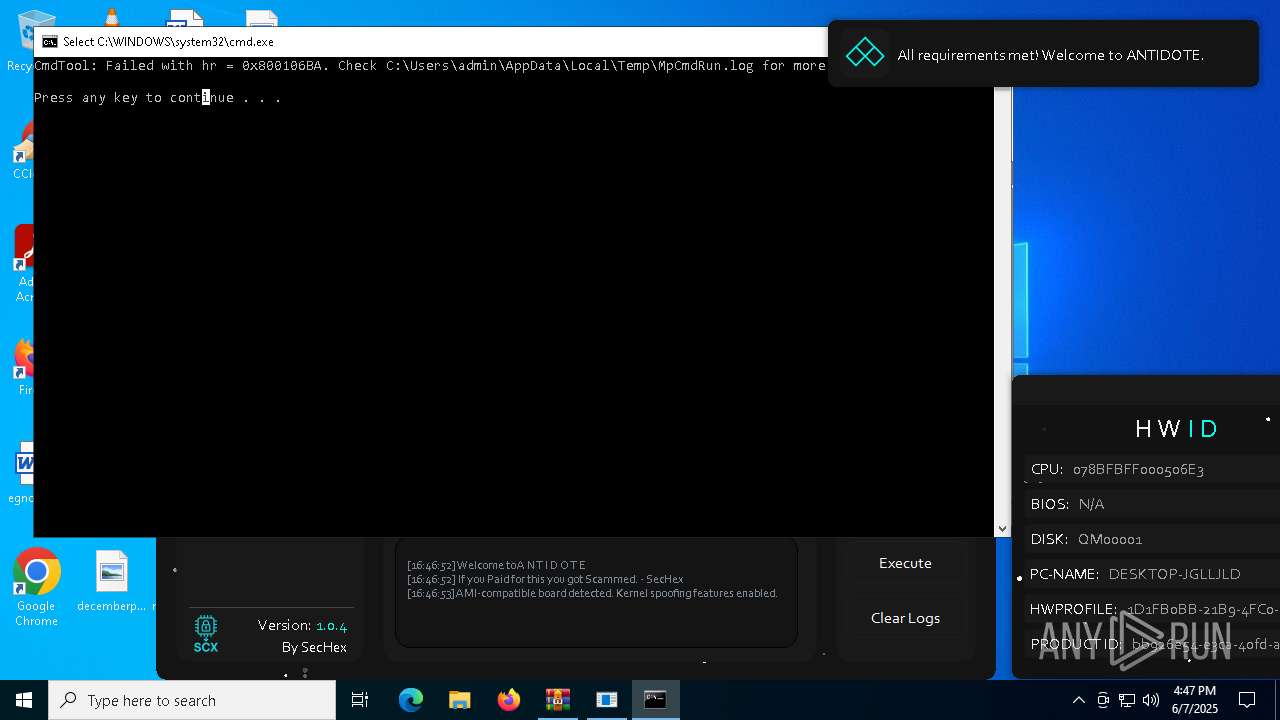
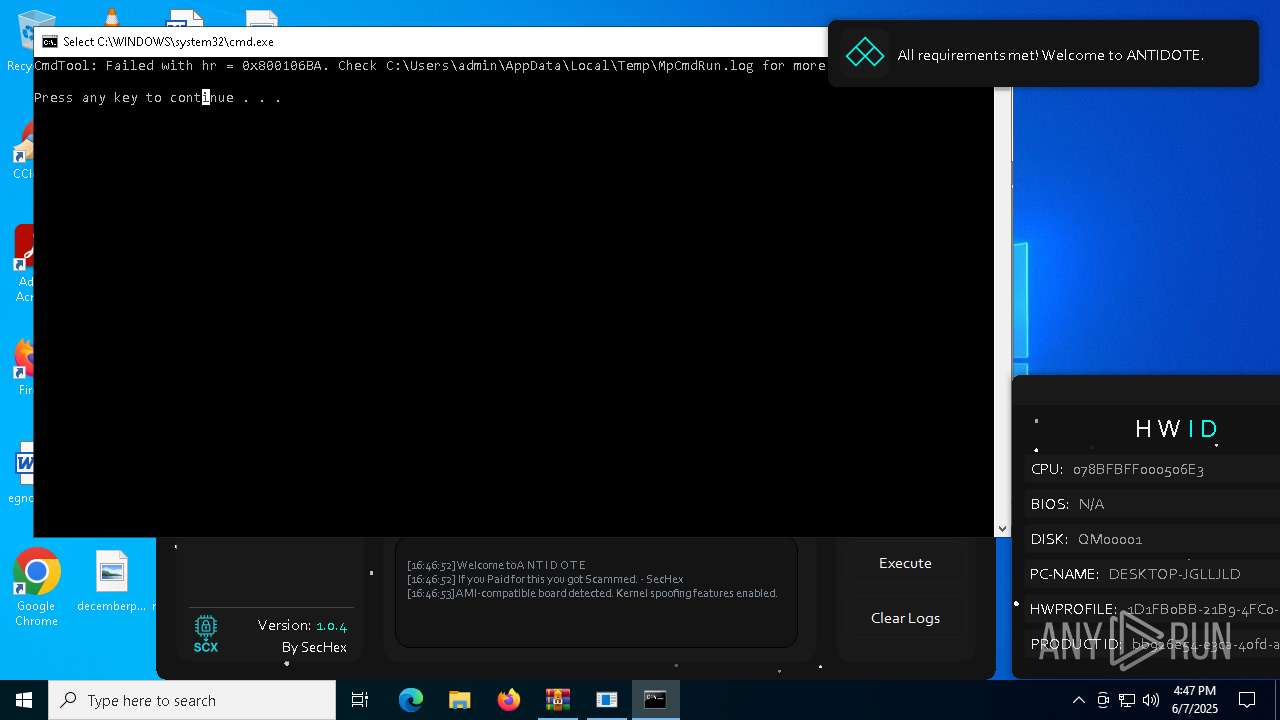
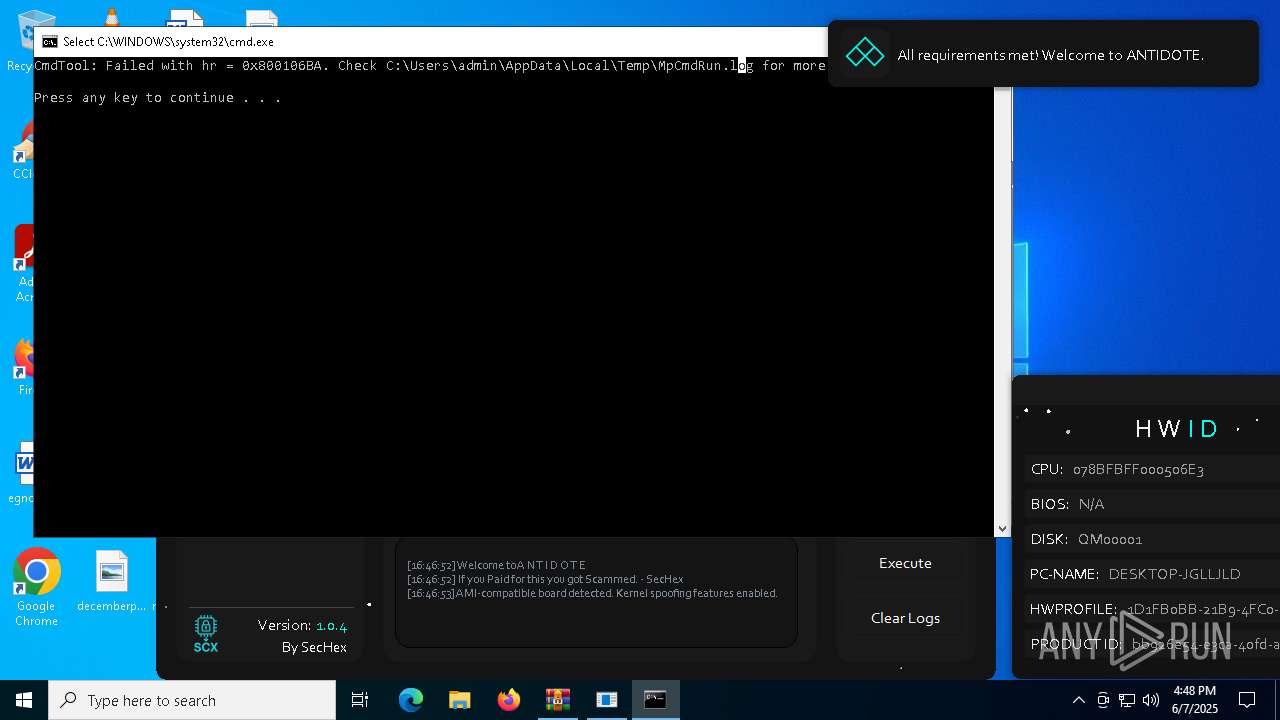
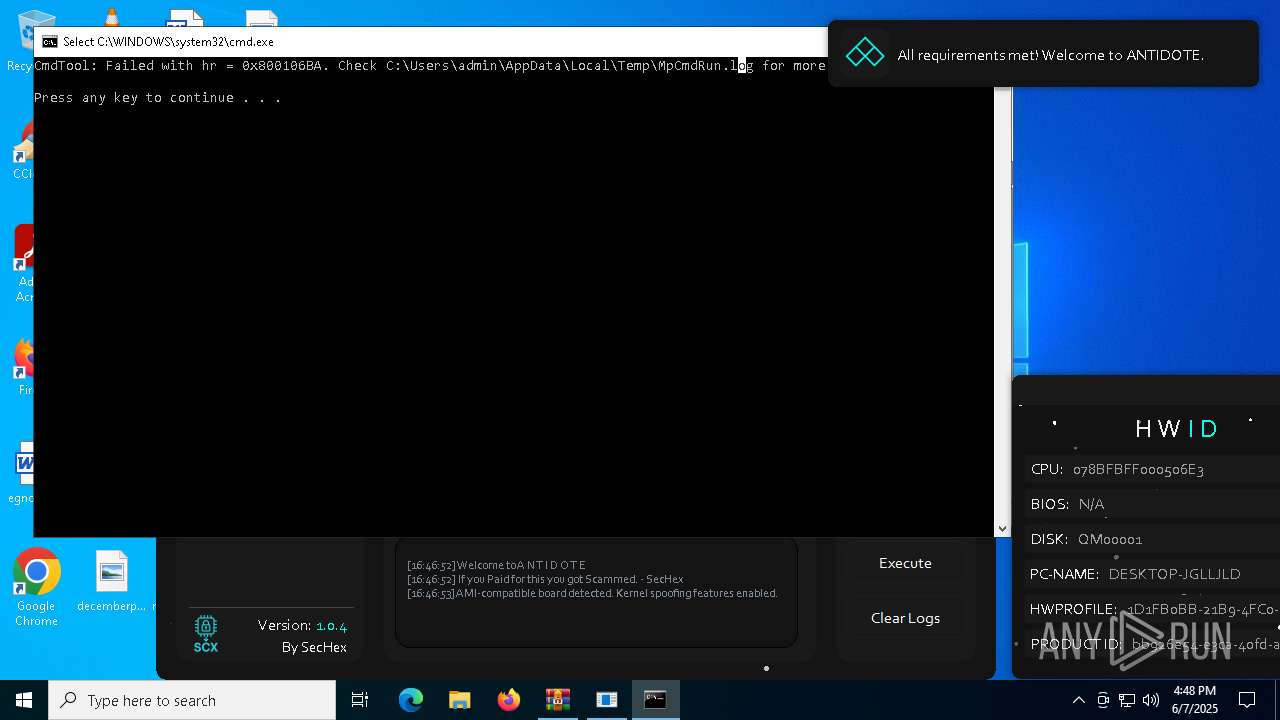
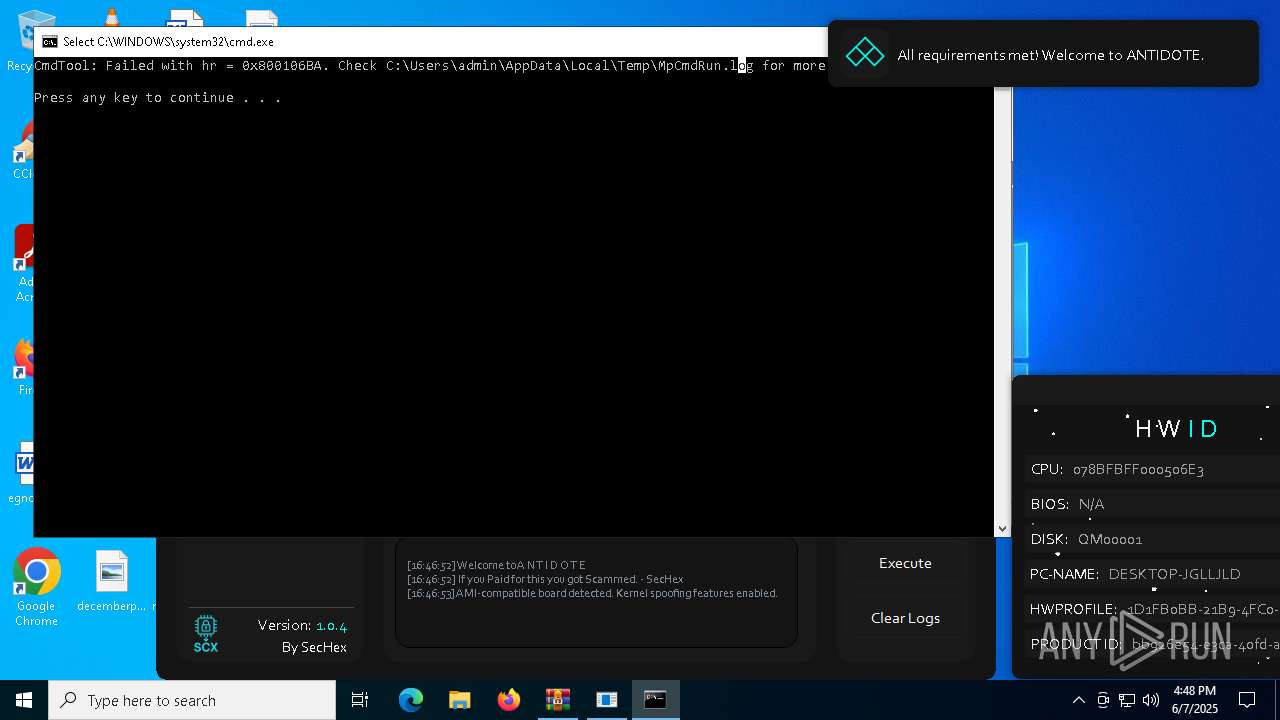
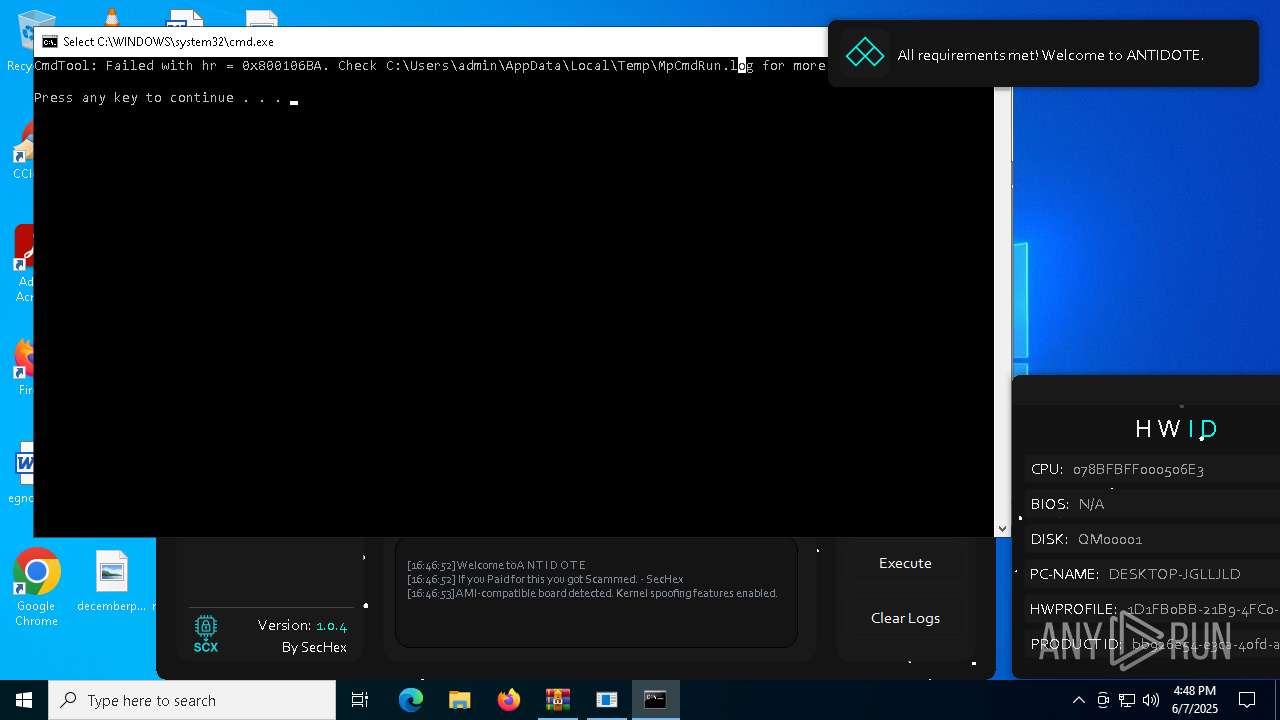
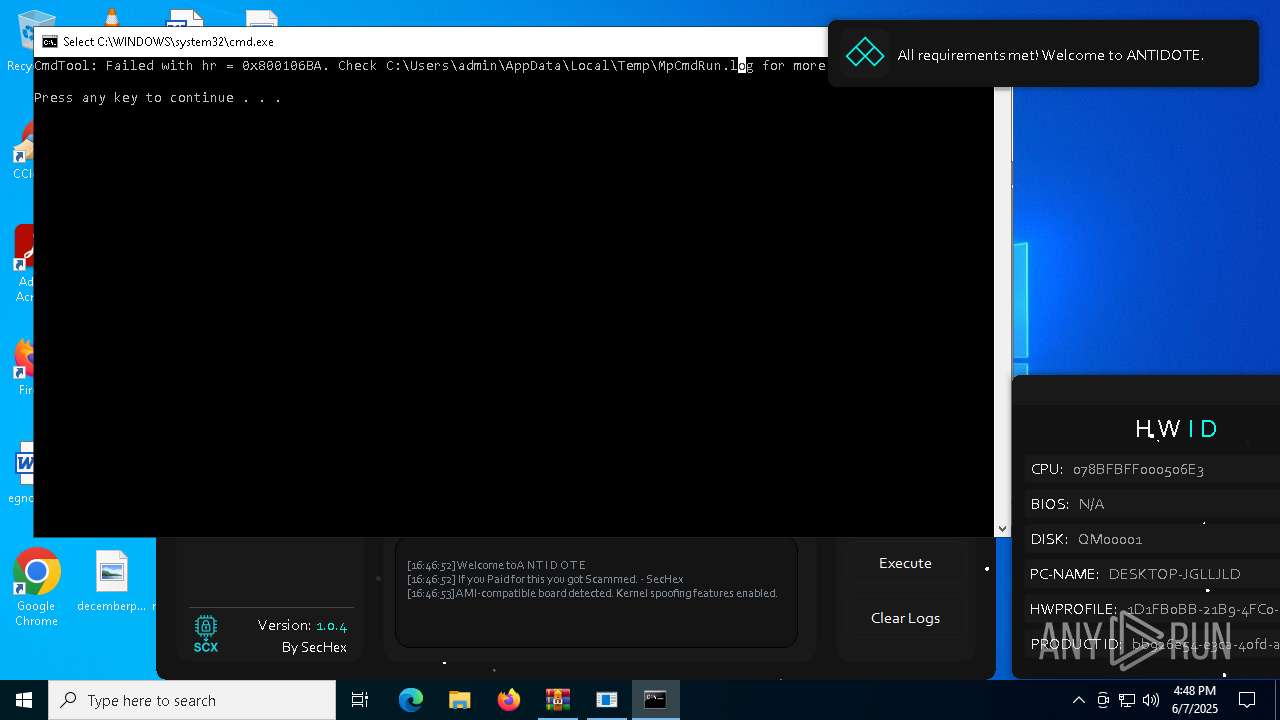
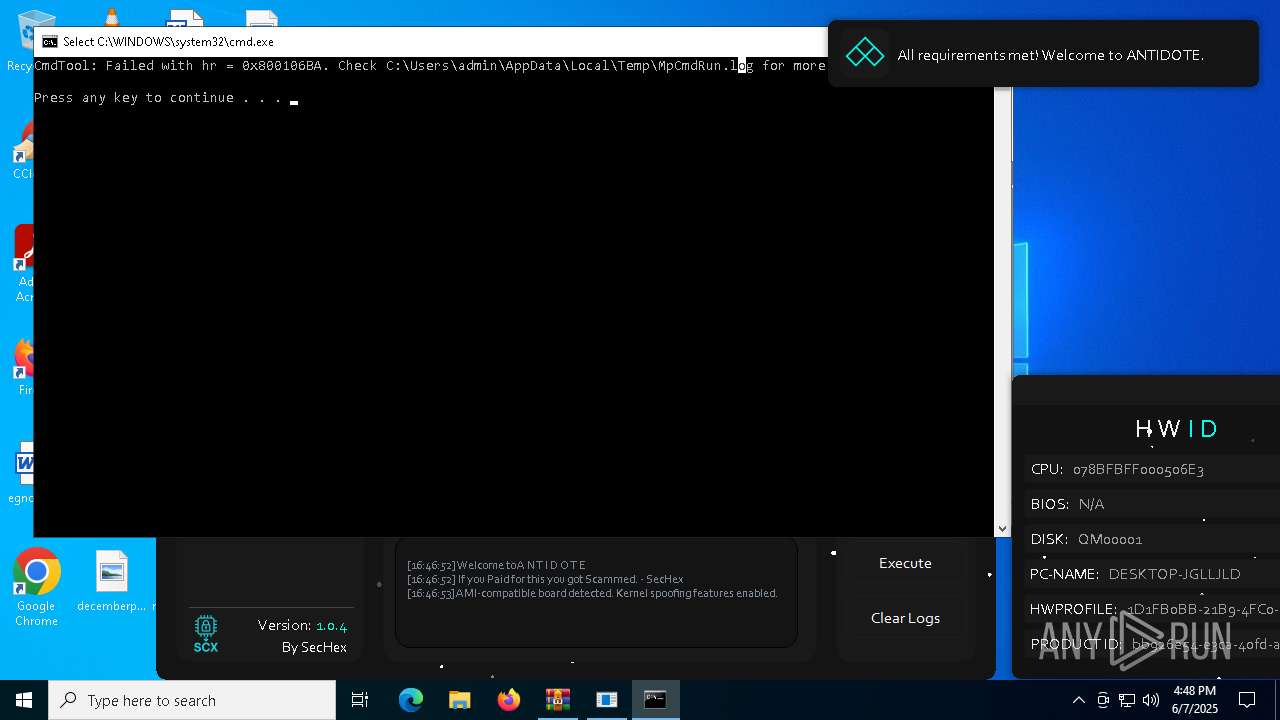
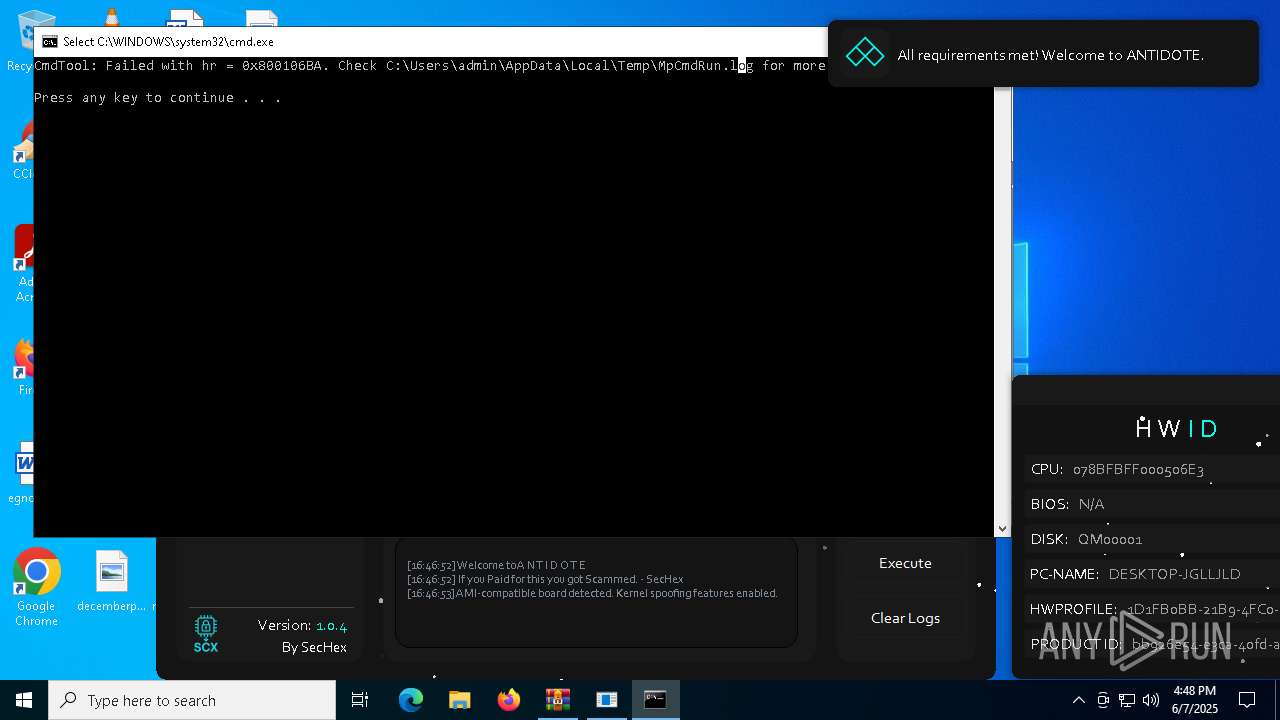
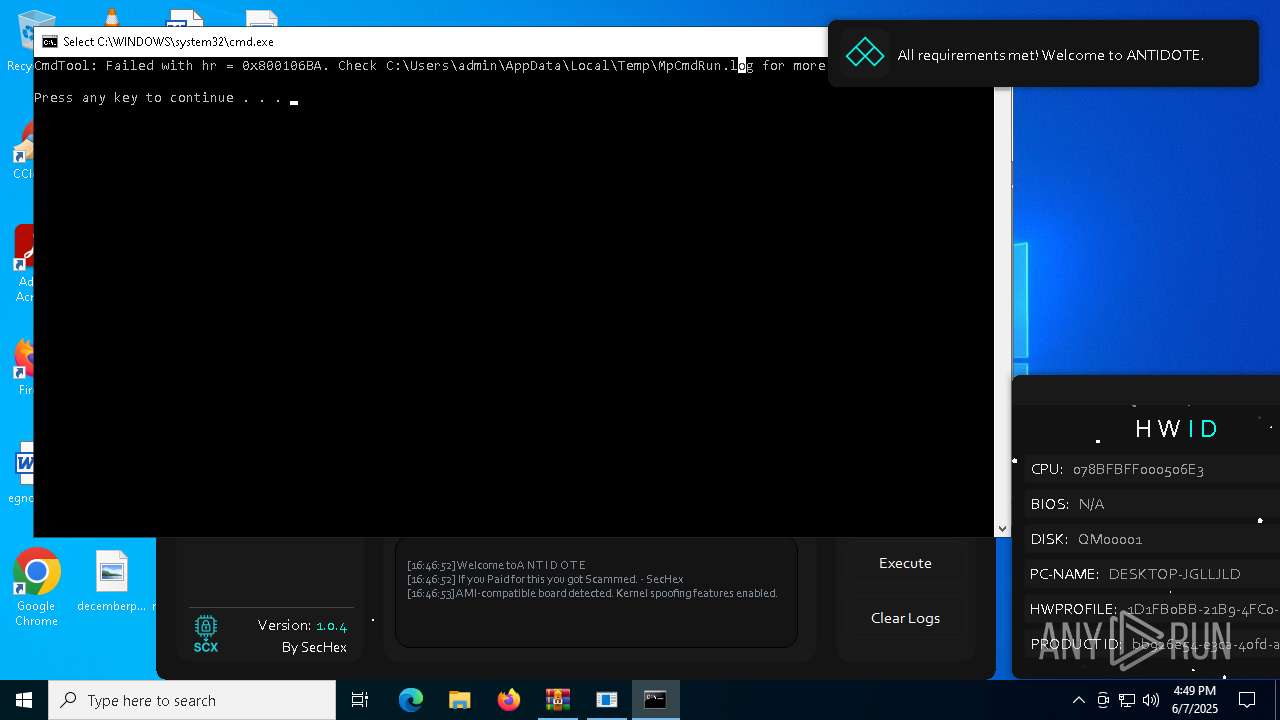
| File name: | Antidote.zip |
| Full analysis: | https://app.any.run/tasks/374901e0-2a94-4449-8d8c-6ead9257f5bb |
| Verdict: | Malicious activity |
| Analysis date: | June 07, 2025, 16:46:33 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C456EC032A71B4EDB0CCFC5AB40A36C3 |
| SHA1: | F66546935DDB73DADF6D5BB918759FFFA447CC1A |
| SHA256: | E63FA3BE2F0C869FB53958372EBDA14F37849C72DC0D4D7889C7A721544D7BC9 |
| SSDEEP: | 98304:cdTKChYrWwYdRfPrM3eejZ4AMO1AIJSJkKsEwDJ/fhlLOZzQ6fWZDnxQfwYuySCh:qmXIarZ+z6WEGUW27QIo |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7588)
SUSPICIOUS
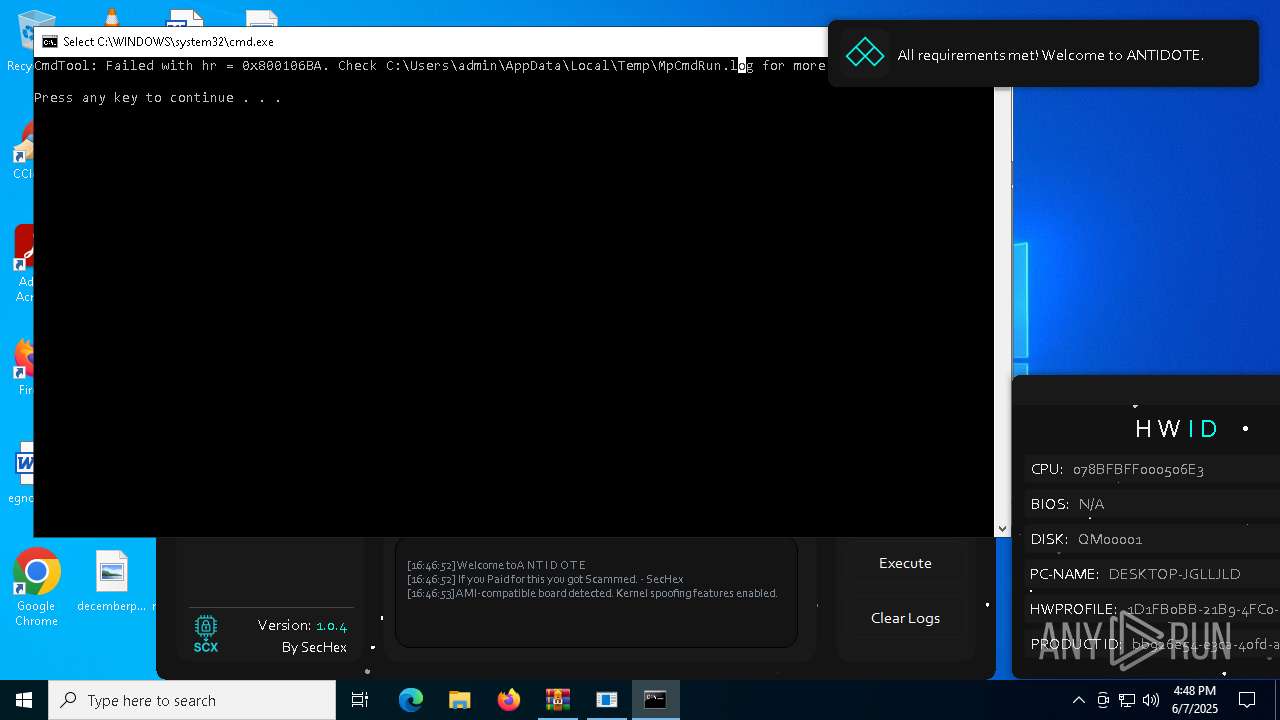
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 7588)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7588)
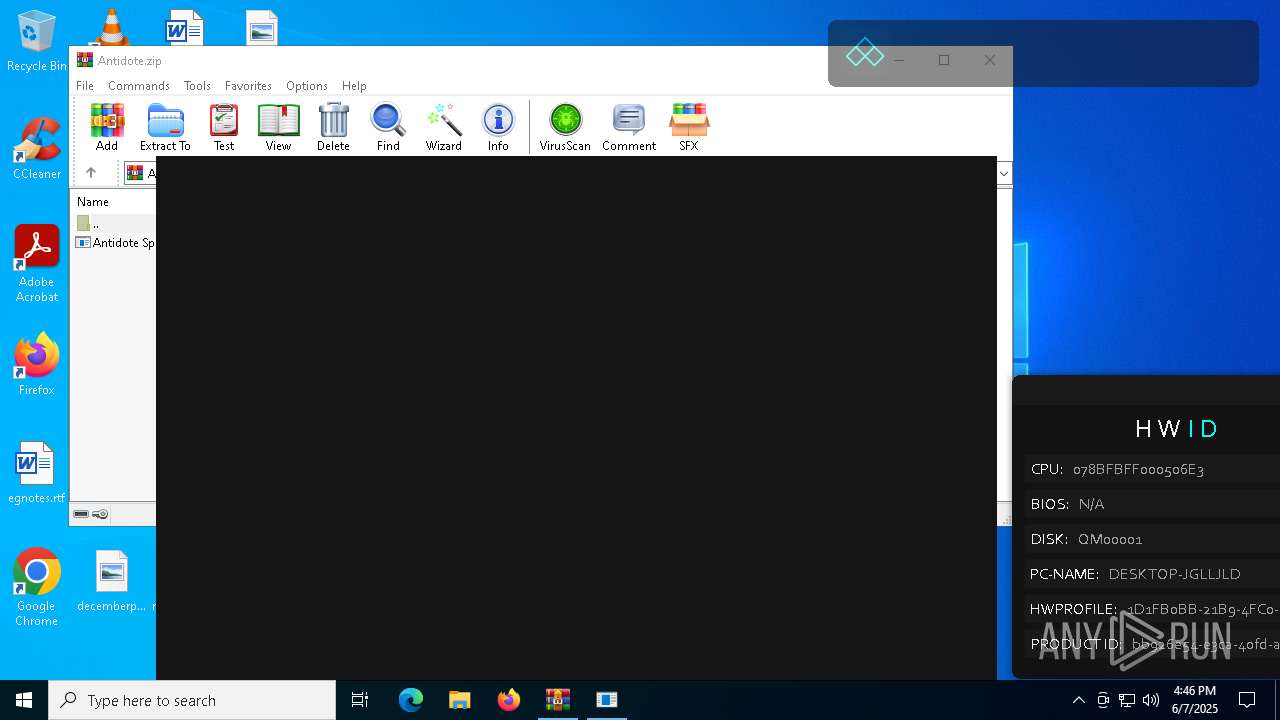
Read disk information to detect sandboxing environments
- Antidote Spoofer.exe (PID: 6248)
The process checks if it is being run in the virtual environment
- Antidote Spoofer.exe (PID: 6248)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 7588)
Reads the BIOS version
- Antidote Spoofer.exe (PID: 6248)
Starts POWERSHELL.EXE for commands execution
- Antidote Spoofer.exe (PID: 6248)
Query Microsoft Defender preferences
- Antidote Spoofer.exe (PID: 6248)
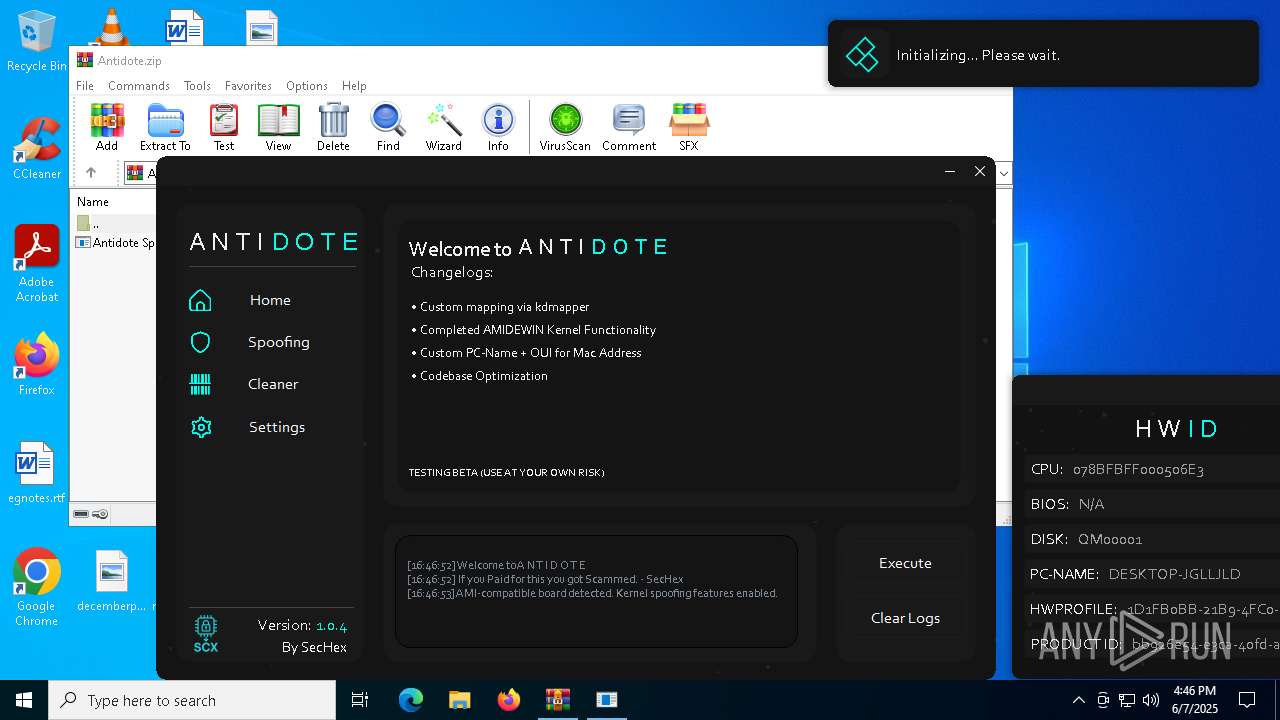
There is functionality for taking screenshot (YARA)
- Antidote Spoofer.exe (PID: 6248)
Script disables Windows Defender's real-time protection
- Antidote Spoofer.exe (PID: 6248)
INFO
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 4192)
Confuser has been detected (YARA)
- Antidote Spoofer.exe (PID: 6248)
Checks supported languages
- Antidote Spoofer.exe (PID: 6248)
- MpCmdRun.exe (PID: 4628)
Reads the computer name
- Antidote Spoofer.exe (PID: 6248)
- MpCmdRun.exe (PID: 4628)
Manual execution by a user
- Antidote Spoofer.exe (PID: 1052)
- Antidote Spoofer.exe (PID: 6248)
Reads the machine GUID from the registry
- Antidote Spoofer.exe (PID: 6248)
Create files in a temporary directory
- MpCmdRun.exe (PID: 4628)
- Antidote Spoofer.exe (PID: 6248)
Checks proxy server information
- slui.exe (PID: 7584)
Reads the software policy settings
- slui.exe (PID: 7584)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:24 11:25:08 |
| ZipCRC: | 0x4153f975 |
| ZipCompressedSize: | 11144538 |
| ZipUncompressedSize: | 14846496 |
| ZipFileName: | Antidote Spoofer.exe |
Total processes
131
Monitored processes
9
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | "C:\Users\admin\Desktop\Antidote Spoofer.exe" | C:\Users\admin\Desktop\Antidote Spoofer.exe | — | explorer.exe | |||||||||||
User: admin Company: HP Integrity Level: MEDIUM Description: Antidote Spoofer Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4192 | "powershell" -Command Get-MpPreference | Select-Object -ExpandProperty DisableRealtimeMonitoring | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Antidote Spoofer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4628 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR7588.17592" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6248 | "C:\Users\admin\Desktop\Antidote Spoofer.exe" | C:\Users\admin\Desktop\Antidote Spoofer.exe | explorer.exe | ||||||||||||
User: admin Company: HP Integrity Level: HIGH Description: Antidote Spoofer Version: 1.0.0.0 Modules
| |||||||||||||||
| 7252 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7584 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7588 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Antidote.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7596 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR7588.17592\Rar$Scan61259.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 811
Read events
12 799
Write events
12
Delete events
0
Modification events
| (PID) Process: | (7588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (7588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Antidote.zip | |||
| (PID) Process: | (7588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
1
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7588.17592\Antidote.zip\Antidote Spoofer.exe | executable | |
MD5:F2DECC9A52F52906421528A676A271EA | SHA256:02917C98B39013D382B72781B144759570294BB42E68FC4397F5396011B9185C | |||
| 4192 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ywkmrgzw.mti.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7588.17592\Rar$Scan61259.bat | text | |
MD5:3753351B38E977C44B725D0F03E130C3 | SHA256:E48C38679499B49E012446ACAAED13F359A00B03C8BDEC3155BCCB240AD4C500 | |||
| 4628 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:744537F4386F5A039BD083A0E5A516A5 | SHA256:12FC64E50882FEF75EF465E8C1E8258FD428FE398818C8B1FC8B5F6D36EECCF0 | |||
| 6248 | Antidote Spoofer.exe | C:\Users\admin\AppData\Local\Temp\antidote_config_icon.ico | image | |
MD5:D56116B23A832D23C662459FA52A619A | SHA256:434A3992F731CB21C71855D41E11F756AD0260189E671A3E9D215C1DED33B0EB | |||
| 4192 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jkqqucwl.4ox.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4192 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:BDAAA9E09779F68865632F9D43B7EB8E | SHA256:063BF150C652CB0DB5FD882DB40BBDFFCAF79461157099FDA34963DAE4910699 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
20
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
472 | RUXIMICS.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
472 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
472 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
472 | RUXIMICS.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
472 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
7792 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7584 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |