| File name: | autorun.exe |
| Full analysis: | https://app.any.run/tasks/a856d377-1c8a-4291-85cf-7990c46b7b1f |
| Verdict: | Malicious activity |
| Analysis date: | November 05, 2023, 01:57:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 58E66EE45A7A61F29F0B4DF99C728ED1 |
| SHA1: | 9A7B47FE93C0EAA2B52A7858FD1025B4B0153352 |
| SHA256: | E61B8A74F1DC176C77556FC2A45895CA3F25339CAF955BD95496EFD7F978351C |
| SSDEEP: | 98304:CBV2HLcYLcuG2YueecfKMewSGIwCaPIpliU7PVw3KP6iOt+OtrbwC9OT6nxNGbMR:BB5Cc7il |
MALICIOUS
Drops the executable file immediately after the start
- autorun.exe (PID: 3196)
- autorun.exe (PID: 3916)
- autorun.exe (PID: 4024)
SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- autorun.exe (PID: 3196)
- wmpnscfg.exe (PID: 3540)
- autorun.exe (PID: 3916)
- autorun.exe (PID: 4024)
Checks supported languages
- wmpnscfg.exe (PID: 3540)
- autorun.exe (PID: 3196)
- autorun.exe (PID: 3916)
- autorun.exe (PID: 4024)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3540)
Manual execution by a user
- wmpnscfg.exe (PID: 3540)
- autorun.exe (PID: 3916)
- autorun.exe (PID: 4024)
Creates files or folders in the user directory
- autorun.exe (PID: 3916)
- autorun.exe (PID: 3196)
- autorun.exe (PID: 4024)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (3.6) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (1.6) |
| .exe | | | DOS Executable Generic (1.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:02:10 22:03:05+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 110080 |
| InitializedDataSize: | 201216 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1448 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.5.0.0 |
| ProductVersionNumber: | 8.5.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | Created with AutoPlay Media Studio |
| FileDescription: | AutoPlay Application |
| FileVersion: | 8.5.0.0 |
| InternalName: | ams_runtime |
| LegalCopyright: | Runtime Engine Copyright © 2015 Indigo Rose Corporation (www.indigorose.com) |
| LegalTrademarks: | AutoPlay Media Studio is a Trademark of Indigo Rose Corporation |
| OriginalFileName: | ams_runtime.exe |
| ProductName: | AutoPlay Media Studio Runtime |
| ProductVersion: | 8.5.0.0 |
| ThinAppBuildDateTime: | 20231105 025132 |
| ThinAppLicense: | ca |
| ThinAppVersion: | 2212.0.0-21059475 |
Total processes
40
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
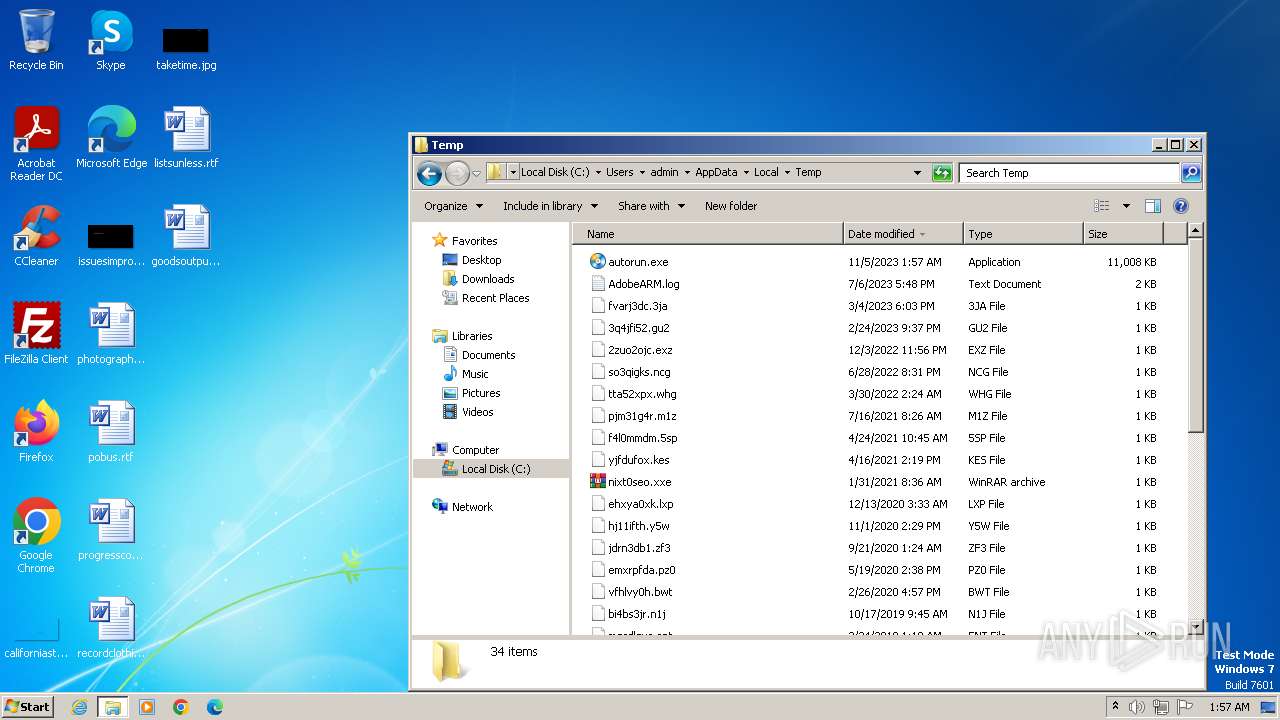
| 3196 | "C:\Users\admin\AppData\Local\Temp\autorun.exe" | C:\Users\admin\AppData\Local\Temp\autorun.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: AutoPlay Application Exit code: 4294967295 Version: 8.5.0.0 Modules
| |||||||||||||||
| 3540 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3916 | "C:\Users\admin\Desktop\autorun.exe" | C:\Users\admin\Desktop\autorun.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: AutoPlay Application Exit code: 4294967295 Version: 8.5.0.0 Modules
| |||||||||||||||
| 4024 | "C:\Users\admin\Desktop\autorun.exe" | C:\Users\admin\Desktop\autorun.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: AutoPlay Application Exit code: 4294967295 Version: 8.5.0.0 Modules
| |||||||||||||||
Total events
178
Read events
175
Write events
0
Delete events
3
Modification events
| (PID) Process: | (3540) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{1DD23DC3-74B1-45D6-BB54-529BDF1A7BD8}\{F7B6F2CC-467A-4A23-BAA8-DB1B073A238A} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3540) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{1DD23DC3-74B1-45D6-BB54-529BDF1A7BD8} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3540) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{F09D73D6-0856-4516-AA86-4051024D5FE6} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
12
Suspicious files
9
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3916 | autorun.exe | — | ||
MD5:— | SHA256:— | |||
| 4024 | autorun.exe | — | ||
MD5:— | SHA256:— | |||
| 3916 | autorun.exe | C:\Users\admin\AppData\Roaming\Thinstall\autorun\DummyTLS\-3908.3916.tmp | executable | |
MD5:05DC5AE141E2EAFF6CDB954E7B1B6A8A | SHA256:1C2FB97273304C3B9C9A72569B1F9EC0EE8323DB118E5330736F9C33F8371DC1 | |||
| 3916 | autorun.exe | C:\Users\admin\AppData\Roaming\Thinstall\autorun\DummyTLS\dummyTLS64.dll | executable | |
MD5:CA30E35F7A6E587960D11EF47778B160 | SHA256:7D90D6217C6850030F108A4466C0728C51D84DFD39A15285CEE55807FF922ABC | |||
| 3916 | autorun.exe | C:\Users\admin\AppData\Roaming\Thinstall\autorun\Registry.rw.tvr.lck | binary | |
MD5:142E841AF4C894CF47057072BDEEFA34 | SHA256:82F5587C6A7B1CE5DA7D372C87608994BC9B3D7F70E0F423492944C910F89324 | |||
| 3196 | autorun.exe | C:\Users\admin\AppData\Roaming\Thinstall\autorun\Registry.rw.tvr.lck.USER-PC.ffffffff.d9c | binary | |
MD5:F9FEBB488C26570B3302D38E3E3FB597 | SHA256:15D8645EE7543BE04F898B20109A8975D331A98C5A276531FF45DF810E51CB12 | |||
| 3196 | autorun.exe | C:\Users\admin\AppData\Roaming\Thinstall\autorun\Registry.rw.tvr | binary | |
MD5:9E63A402AB14167CFEF9F24BB345DA6F | SHA256:64087D712234F37641FF0FE2B6BF1DDBFFF1A9033FF69898905081F0511ECC99 | |||
| 3196 | autorun.exe | C:\Users\admin\AppData\Roaming\Thinstall\autorun\Registry.rw.tvr.transact | binary | |
MD5:9E63A402AB14167CFEF9F24BB345DA6F | SHA256:64087D712234F37641FF0FE2B6BF1DDBFFF1A9033FF69898905081F0511ECC99 | |||
| 3196 | autorun.exe | C:\Users\admin\AppData\Roaming\Thinstall\autorun\DummyTLS\dummyTLS.dll | executable | |
MD5:05DC5AE141E2EAFF6CDB954E7B1B6A8A | SHA256:1C2FB97273304C3B9C9A72569B1F9EC0EE8323DB118E5330736F9C33F8371DC1 | |||
| 3196 | autorun.exe | C:\Users\admin\AppData\Roaming\Thinstall\autorun\DummyTLS\dummyTLS64.dll | executable | |
MD5:CA30E35F7A6E587960D11EF47778B160 | SHA256:7D90D6217C6850030F108A4466C0728C51D84DFD39A15285CEE55807FF922ABC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Threats
Process | Message |
|---|---|
autorun.exe | <?dml?>#2 p=3196/C7Ch t=3484/D9Ch: Loading packaged nt0_dll.dll...
|
autorun.exe | <?dml?>#1 p=3196/C7Ch t=3484/D9Ch: <link cmd=".reload /f boot_loader.exe=0x66200000">Reload</link> <b>boot_loader.exe</b> 0x66200000
|
autorun.exe | <?dml?>#3 p=3196/C7Ch t=3484/D9Ch: <link cmd=".reload /f nt0_dll.dll=0x7FDE0000">Reload</link> <b>nt0_dll.dll</b> 0x7FDE0000 packaged
|
autorun.exe | <?dml?>#2 p=3916/F4Ch t=3908/F44h: Loading packaged nt0_dll.dll...
|
autorun.exe | <?dml?>#1 p=3916/F4Ch t=3908/F44h: <link cmd=".reload /f boot_loader.exe=0x66200000">Reload</link> <b>boot_loader.exe</b> 0x66200000
|
autorun.exe | <?dml?>#3 p=3916/F4Ch t=3908/F44h: <link cmd=".reload /f nt0_dll.dll=0x7FDE0000">Reload</link> <b>nt0_dll.dll</b> 0x7FDE0000 packaged
|
autorun.exe | <?dml?>#1 p=4024/FB8h t=4020/FB4h: <link cmd=".reload /f boot_loader.exe=0x66200000">Reload</link> <b>boot_loader.exe</b> 0x66200000
|
autorun.exe | <?dml?>#2 p=4024/FB8h t=4020/FB4h: Loading packaged nt0_dll.dll...
|
autorun.exe | <?dml?>#3 p=4024/FB8h t=4020/FB4h: <link cmd=".reload /f nt0_dll.dll=0x7FDE0000">Reload</link> <b>nt0_dll.dll</b> 0x7FDE0000 packaged
|