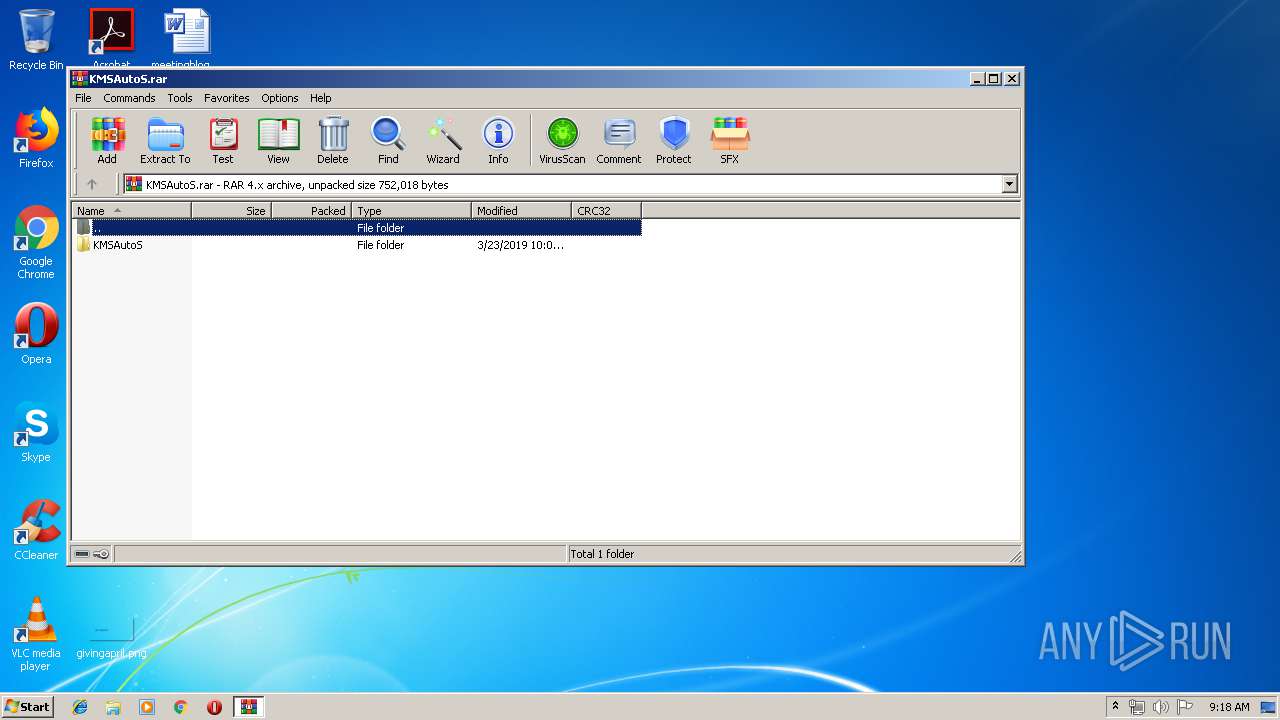
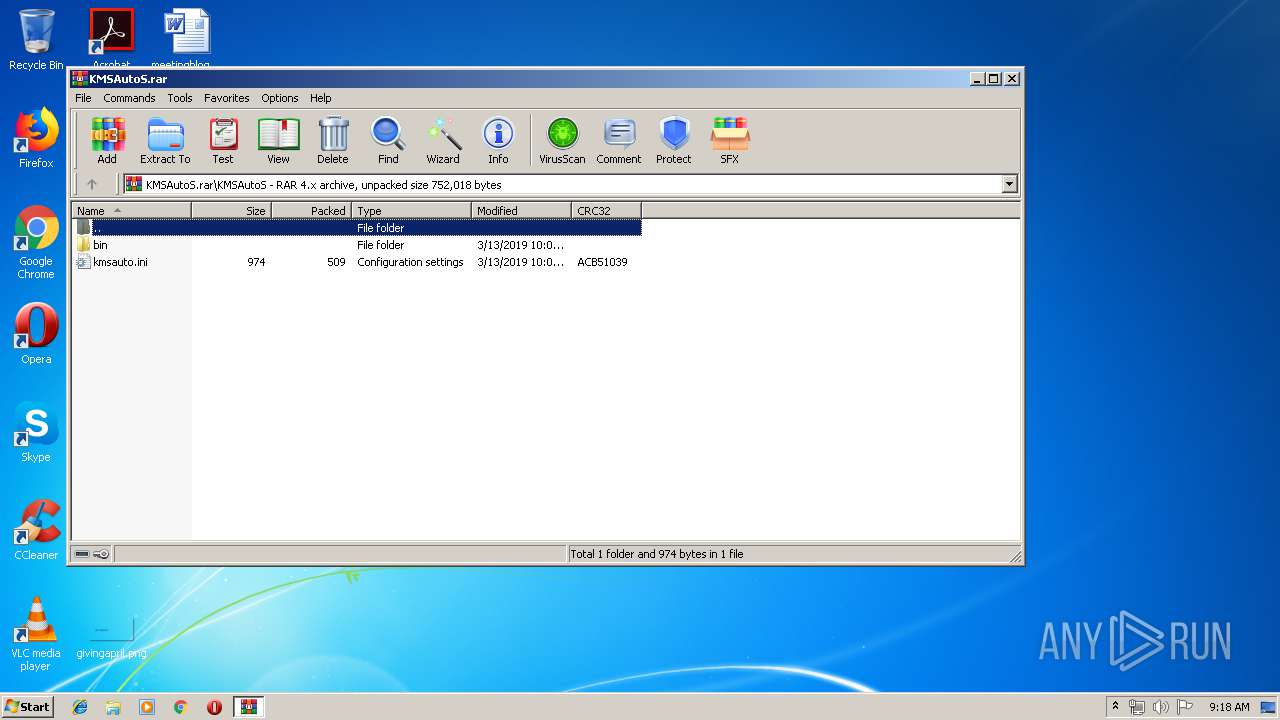
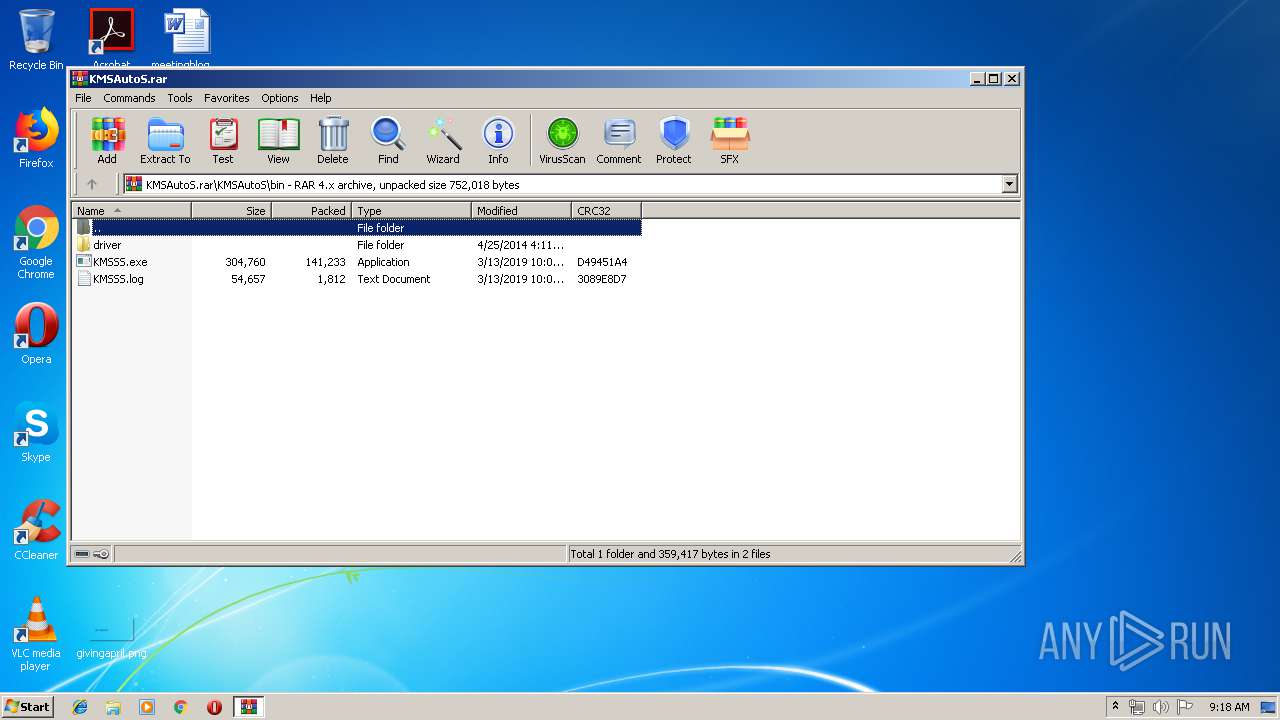
| File name: | KMSAutoS.rar |
| Full analysis: | https://app.any.run/tasks/4c306dd1-9ab3-4214-9f8b-47403be7e93c |
| Verdict: | No threats detected |
| Analysis date: | August 05, 2019, 08:17:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | E71157035CCE2006B964DA2AFCB582E4 |
| SHA1: | C1C5D29433691EDABFCB71BF23E32766088CD397 |
| SHA256: | E612A1B8AC2208144F0C8F0AE207B2C41C7B41FBC018274E999138E24DC275F2 |
| SSDEEP: | 6144:7N+YWMMCj9bjacSLvMUHcZZ+NKB1wIAd86SzbsyDbtF7:B+TCjFacDG6wtSzIa7 |
MALICIOUS
Application was dropped or rewritten from another process
- KMSSS.exe (PID: 3820)
- KMSSS.exe (PID: 3536)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2392)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 2392)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 1119 |
|---|---|
| UncompressedSize: | 1288 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2013:12:03 23:19:23 |
| PackingMethod: | Normal |
| ArchivedFileName: | KMSAutoS\bin\driver\oas_sert.cer |
Total processes
40
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
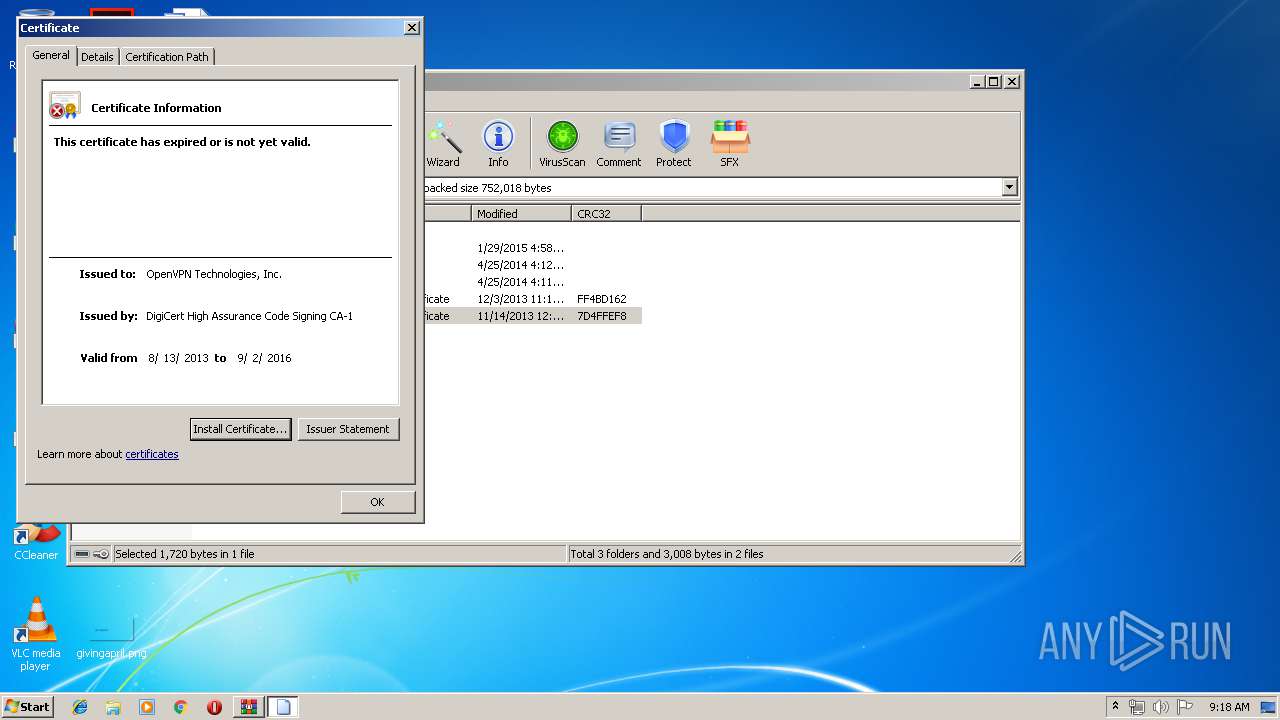
| 272 | "C:\Windows\system32\rundll32.exe" cryptext.dll,CryptExtOpenCER C:\Users\admin\AppData\Local\Temp\Rar$DIa2392.13700\tap0901.cer | C:\Windows\system32\rundll32.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
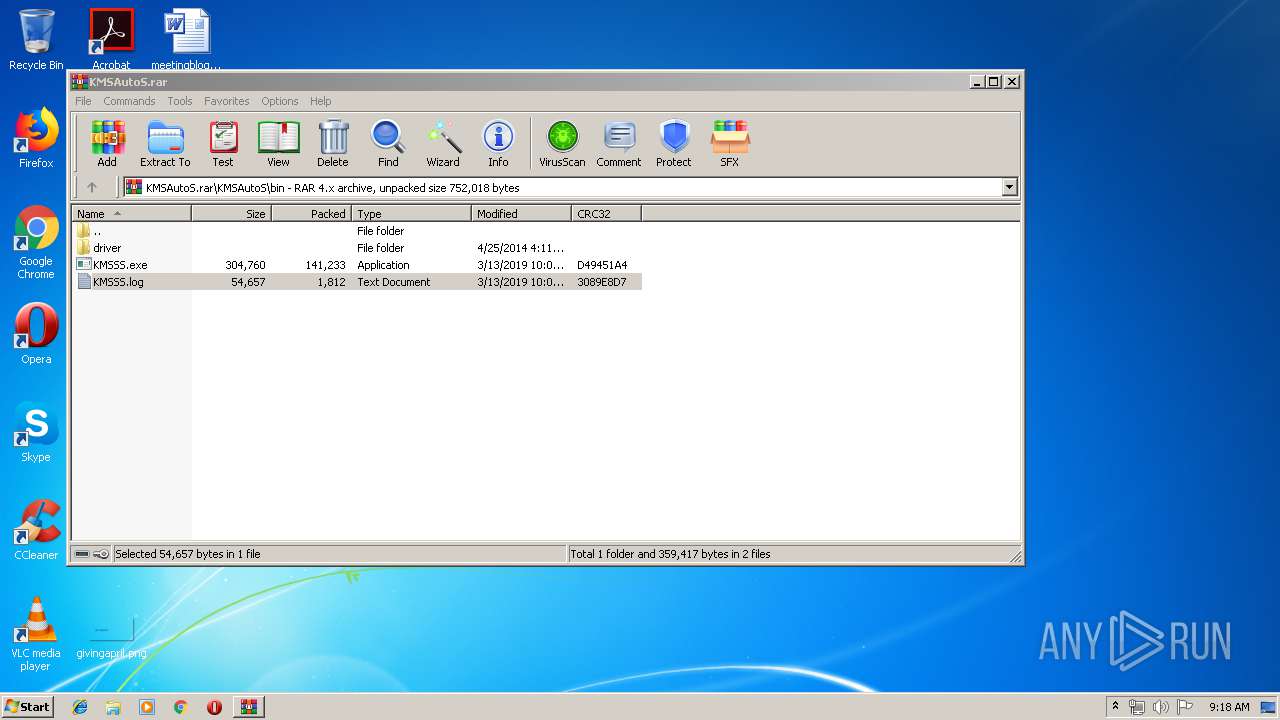
| 2392 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\KMSAutoS.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3536 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2392.10981\KMSAutoS\bin\KMSSS.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2392.10981\KMSAutoS\bin\KMSSS.exe | — | WinRAR.exe | |||||||||||
User: admin Company: MDL Forum, mod by Ratiborus Integrity Level: MEDIUM Description: KMS Server Emulator Service (XP) Exit code: 0 Version: 1.2.1.0 Modules
| |||||||||||||||
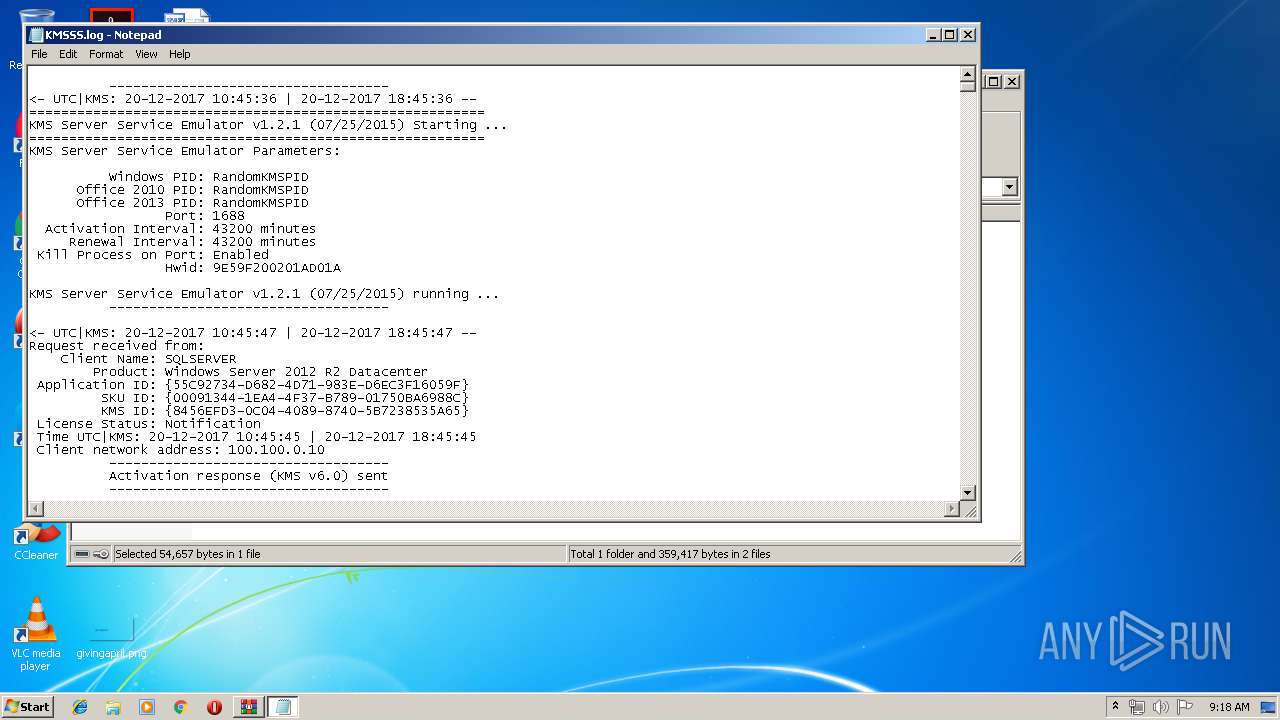
| 3756 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa2392.12589\KMSSS.log | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3820 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2392.11403\KMSAutoS\bin\KMSSS.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2392.11403\KMSAutoS\bin\KMSSS.exe | — | WinRAR.exe | |||||||||||
User: admin Company: MDL Forum, mod by Ratiborus Integrity Level: MEDIUM Description: KMS Server Emulator Service (XP) Exit code: 0 Version: 1.2.1.0 Modules
| |||||||||||||||
Total events
507
Read events
478
Write events
29
Delete events
0
Modification events
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMSAutoS.rar | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
18
Suspicious files
5
Text files
7
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2392.10981\KMSAutoS\bin\KMSSS.log | text | |
MD5:— | SHA256:— | |||
| 2392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2392.10981\KMSAutoS\bin\driver\x64TAP2\tapoas.sys | executable | |
MD5:927D0CDB3F96EFC1E98FB1A2C9FB67AD | SHA256:58F14DAA0EA21EA2F2A1D3D62C88BD8E5A0E0EF498B7B8D367BEEADE6A46843C | |||
| 2392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2392.10981\KMSAutoS\bin\driver\x64WDV\WdfCoInstaller01009.dll | executable | |
MD5:BE566E174EAF5B93B0474593CD8F2715 | SHA256:CEE8496BFA1080FD84FC48BA4375625238900FE93EA739B2DC0300206FDE8330 | |||
| 2392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2392.10981\KMSAutoS\bin\driver\x64TAP1\ptun0901.sys | executable | |
MD5:D8EB393983B644879DE0546122CC16DF | SHA256:4A11DDFB016B560E770660183AF1ADA4831D97DAEAF560E60259F81F2727CBFC | |||
| 2392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2392.10981\KMSAutoS\bin\driver\x64TAP2\tapoas.cat | cat | |
MD5:8DC91F1BF59F58554DC195C9FFCB59EC | SHA256:0B42F01E4C8732D246260B6BA76A5E096E1DA3047898DFF6FB71EEDE68951C87 | |||
| 2392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2392.10981\KMSAutoS\bin\driver\oas_sert.cer | der | |
MD5:0041584E5F66762B1FA9BE8910D0B92B | SHA256:BB27684B569CBB72DEC63EA6FDEF8E5F410CDAEB73717EEE1B36478DBCFF94CC | |||
| 2392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2392.10981\KMSAutoS\bin\driver\x64WDV\WinDivert.sys | executable | |
MD5:A0D15D8727D0780C51628DF46B7268B3 | SHA256:5E23F3ED1D6620C39A644F9879404A22DED86B3B076EC4A898B4B6BE244AFD64 | |||
| 2392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2392.10981\KMSAutoS\bin\driver\x64TAP1\ptun0901.cat | cat | |
MD5:28B3A205C15D9D722319D270B3500BD0 | SHA256:438B3CDB66A5E1CE7B659744B81A570EB7CB0C8B403738A17DD2629625B0C765 | |||
| 2392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2392.10981\KMSAutoS\bin\driver\x64WDV\FakeClient.exe | executable | |
MD5:B85F4CE841F3AE1EBDF76835D2EADBEF | SHA256:CE28748F6AE7B54AB35FC31D825E80A26E143737CF4748FFF523781E04C1EE79 | |||
| 2392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2392.10981\KMSAutoS\bin\driver\x64TAP1\devcon.exe | executable | |
MD5:3904D0698962E09DA946046020CBCB17 | SHA256:A51E25ACC489948B31B1384E1DC29518D19B421D6BC0CED90587128899275289 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
272 | rundll32.exe | GET | 200 | 104.18.11.39:80 | http://cacerts.digicert.com/DigiCertHighAssuranceCodeSigningCA-1.crt | US | der | 1.69 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
272 | rundll32.exe | 104.18.11.39:80 | cacerts.digicert.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cacerts.digicert.com |
| whitelisted |