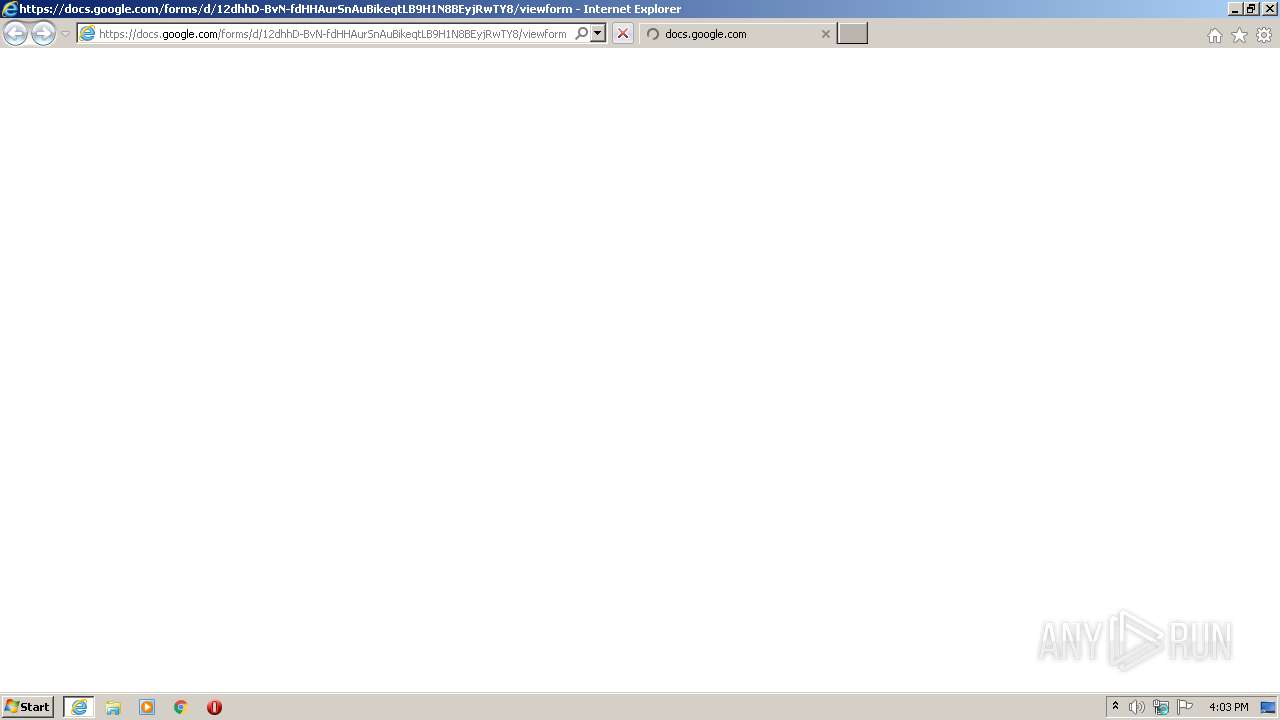
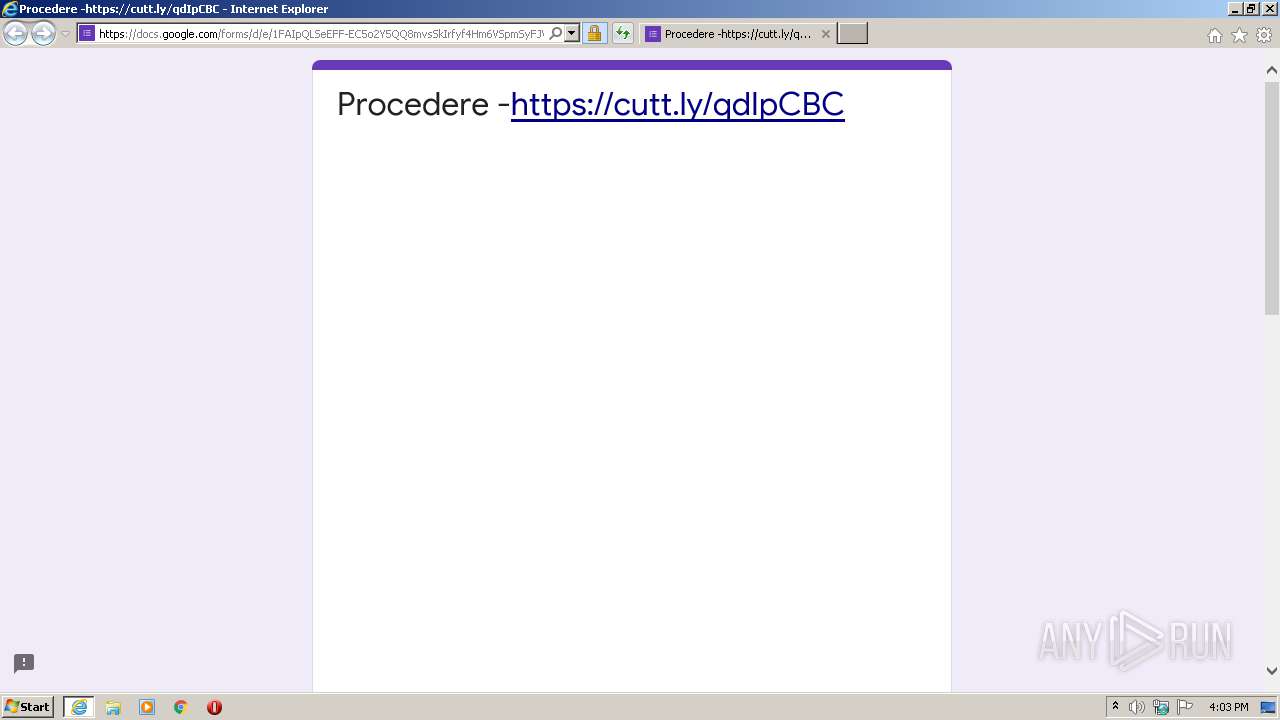
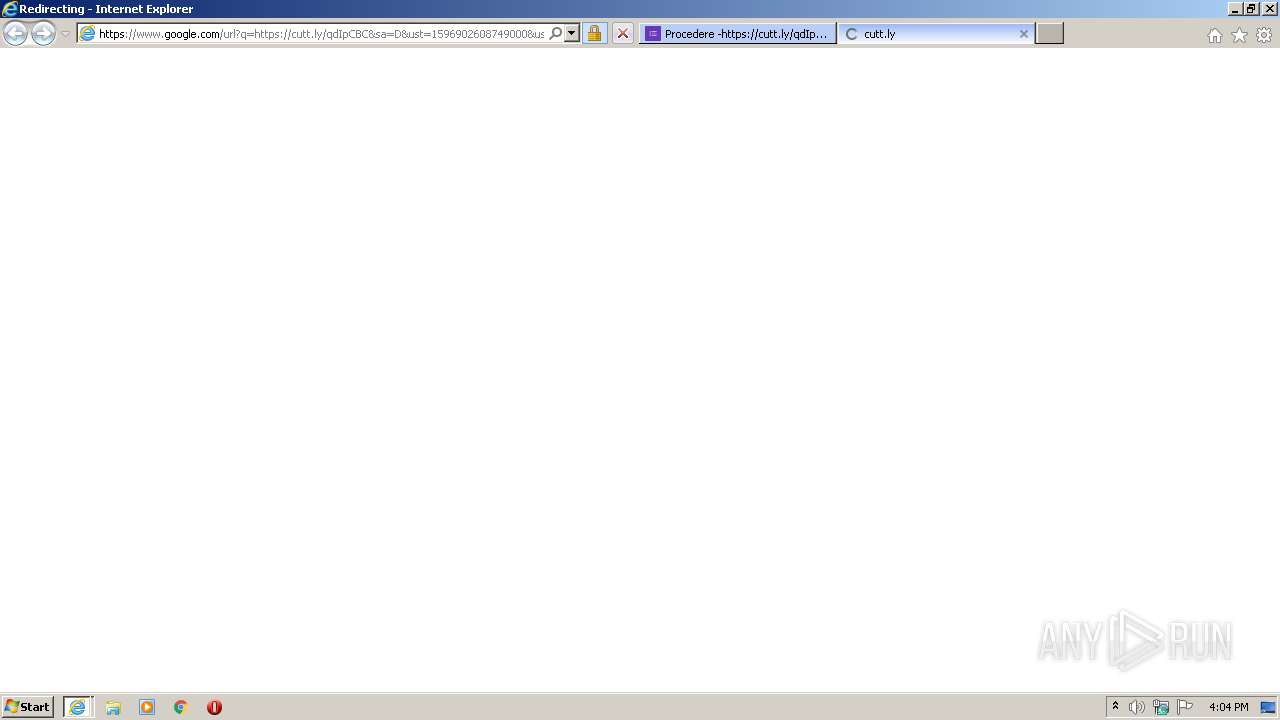
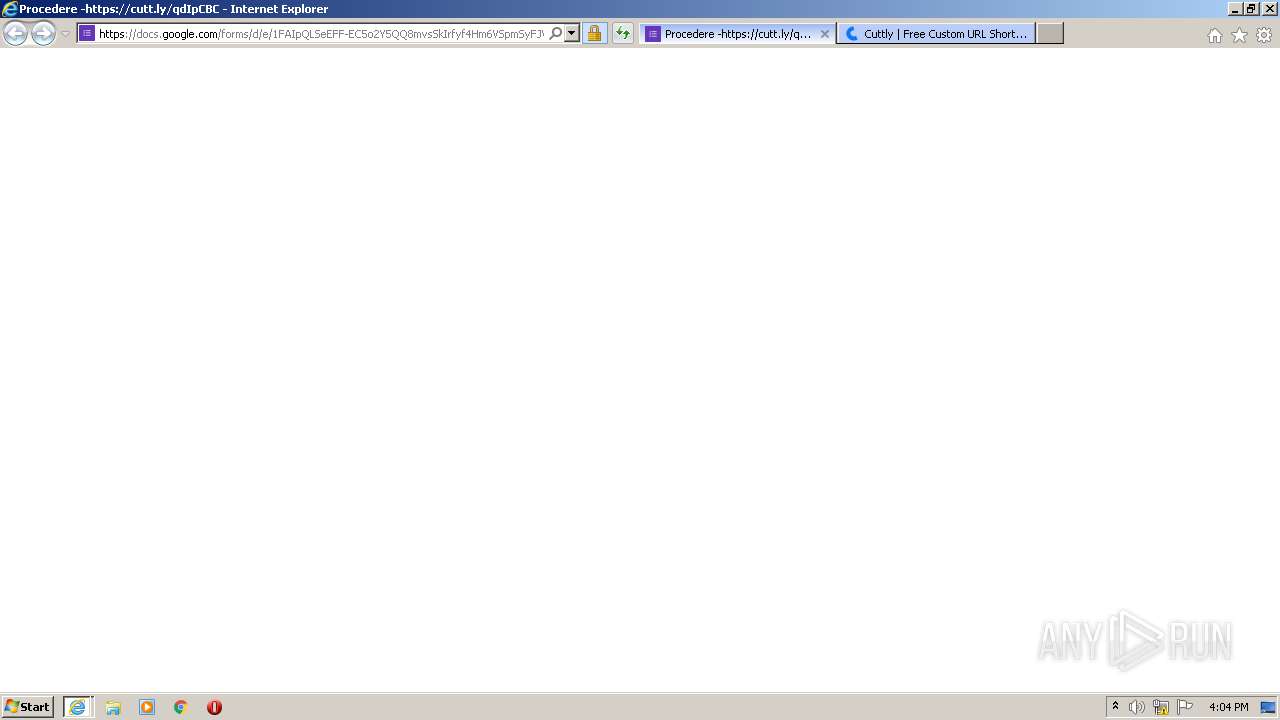
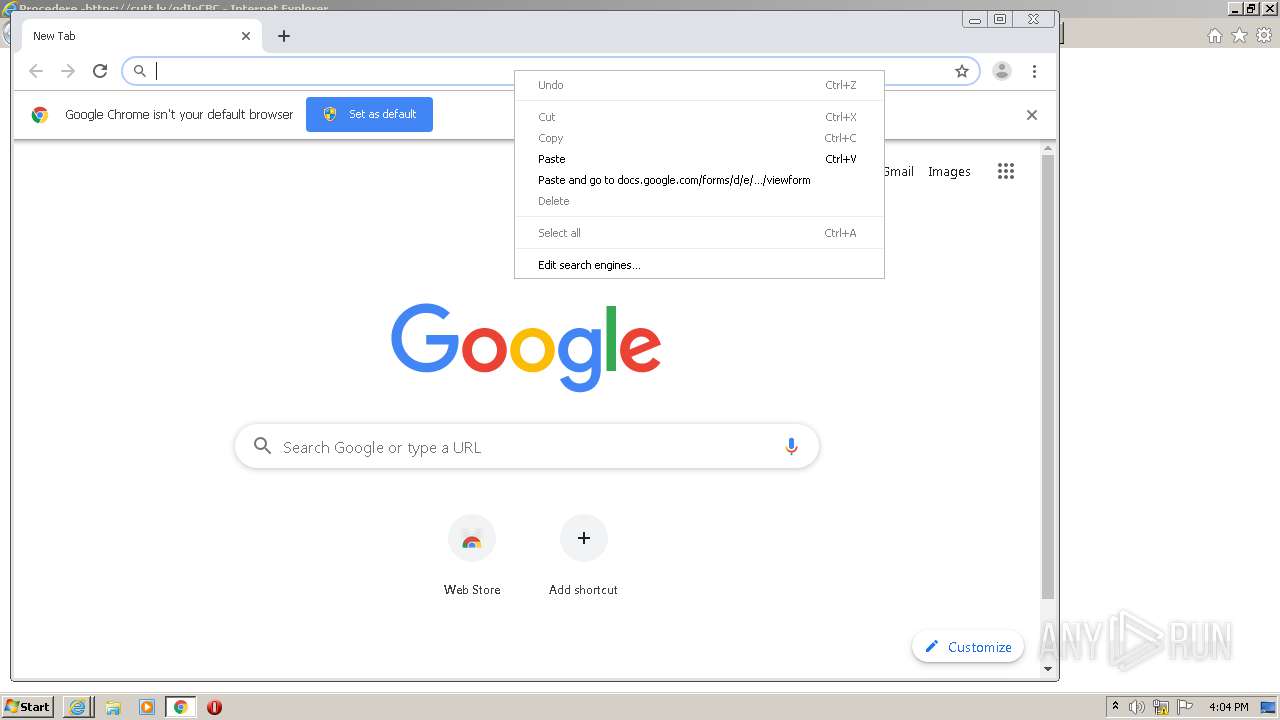
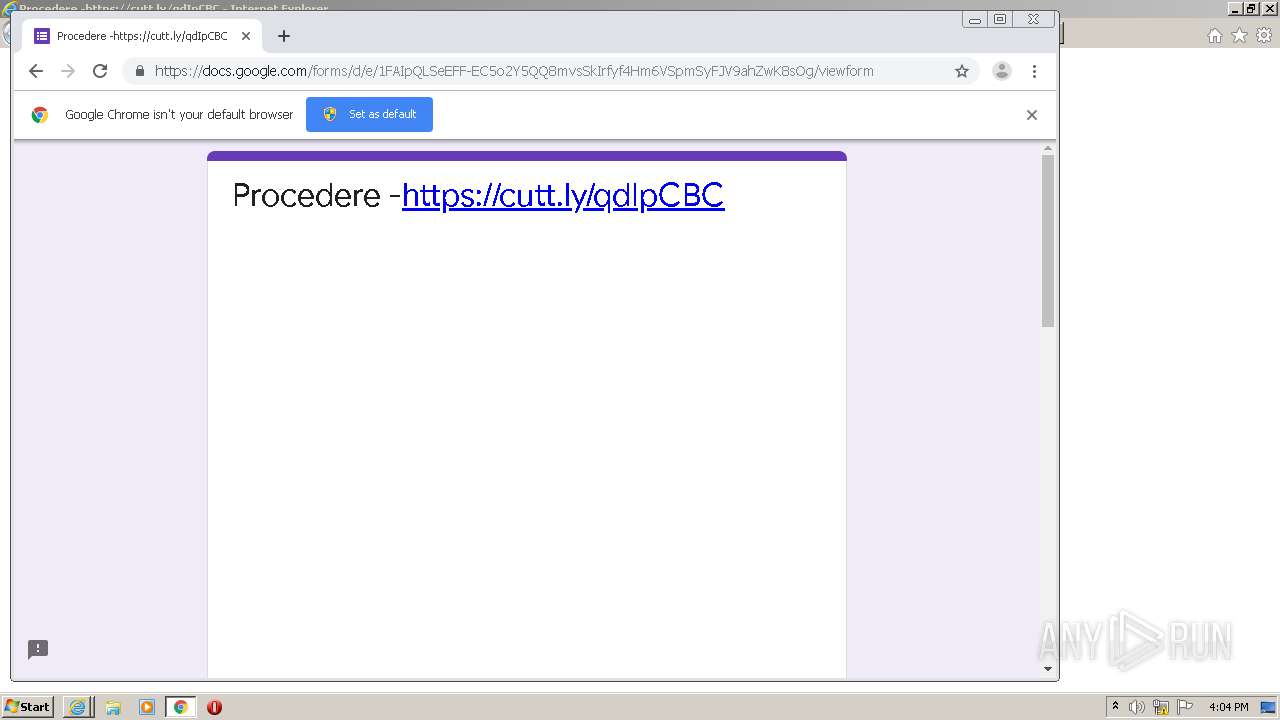
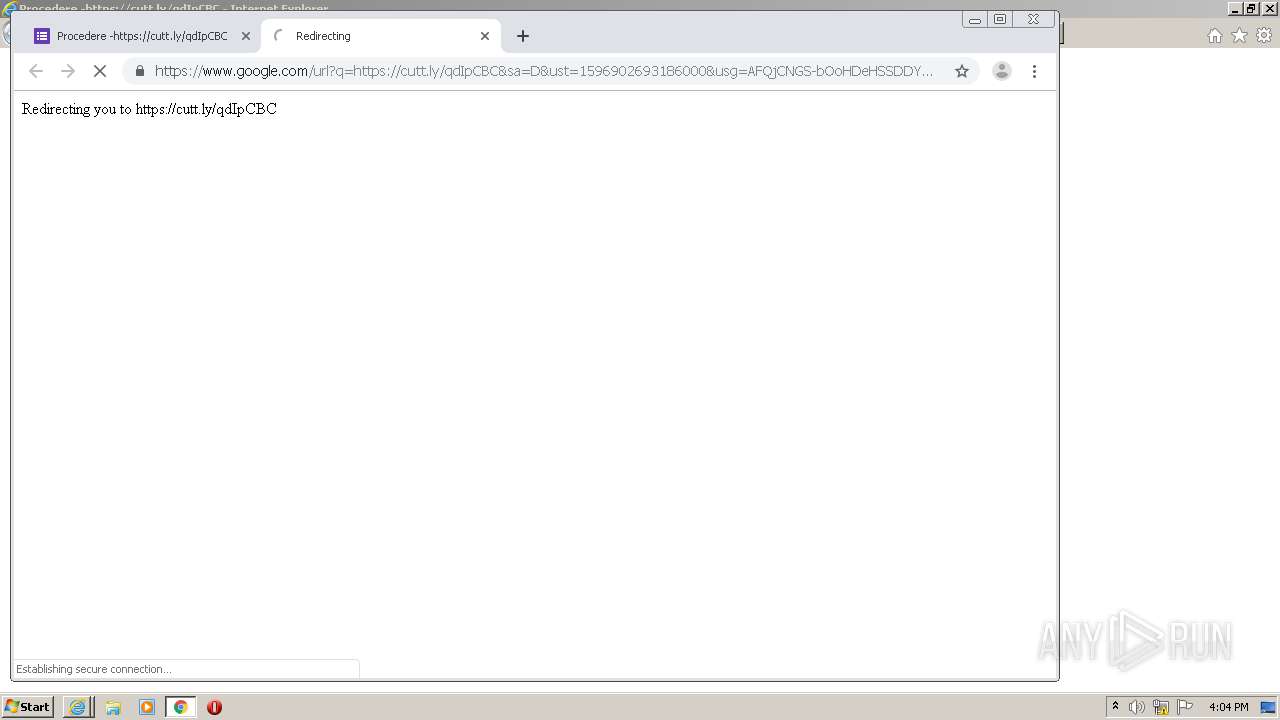
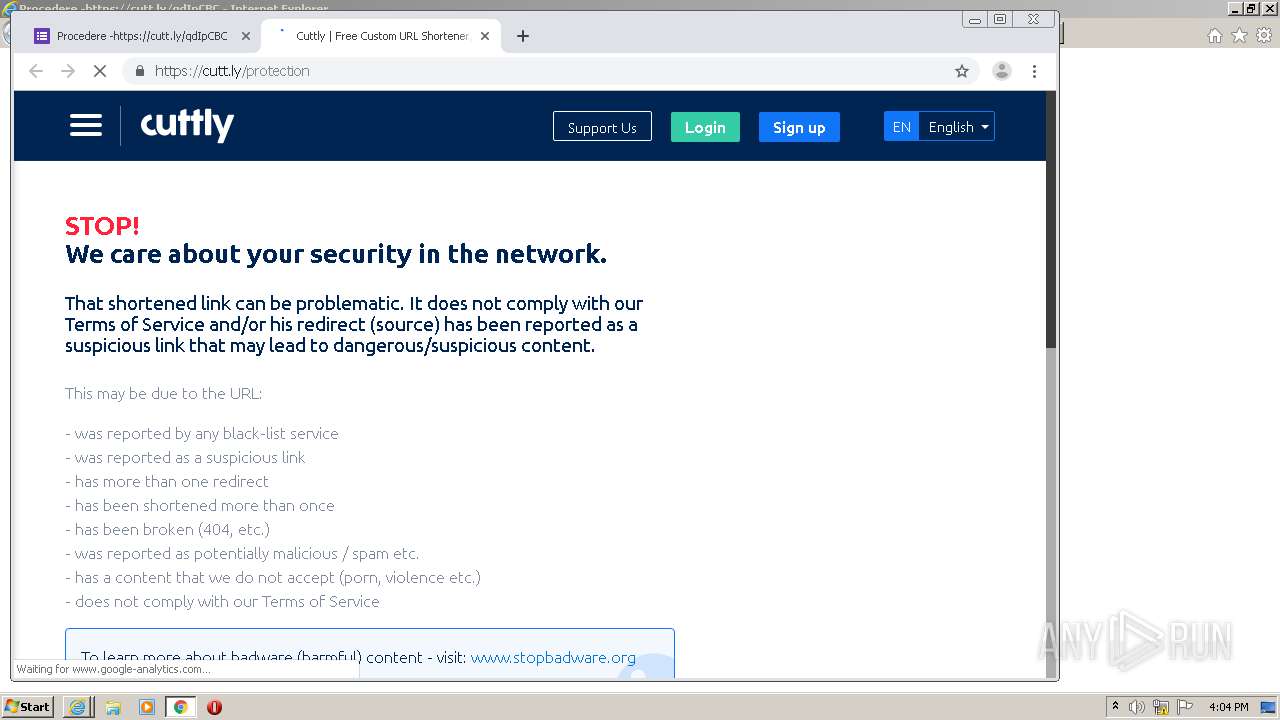
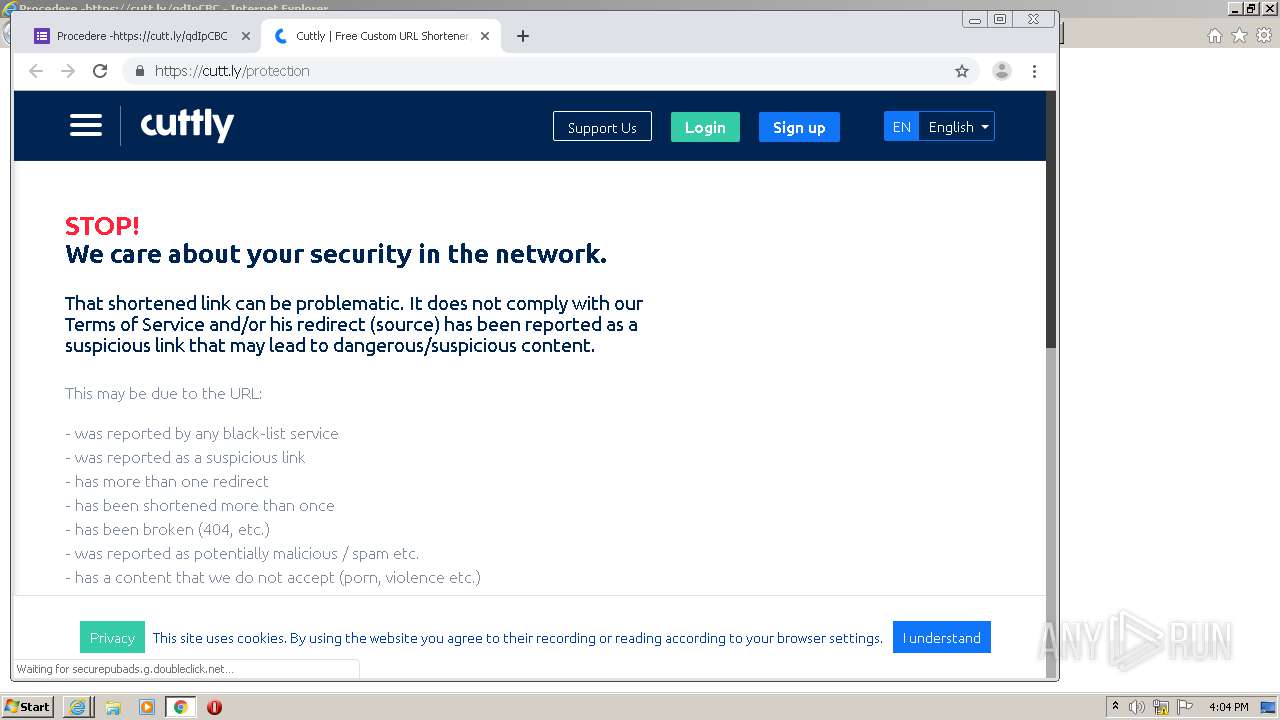
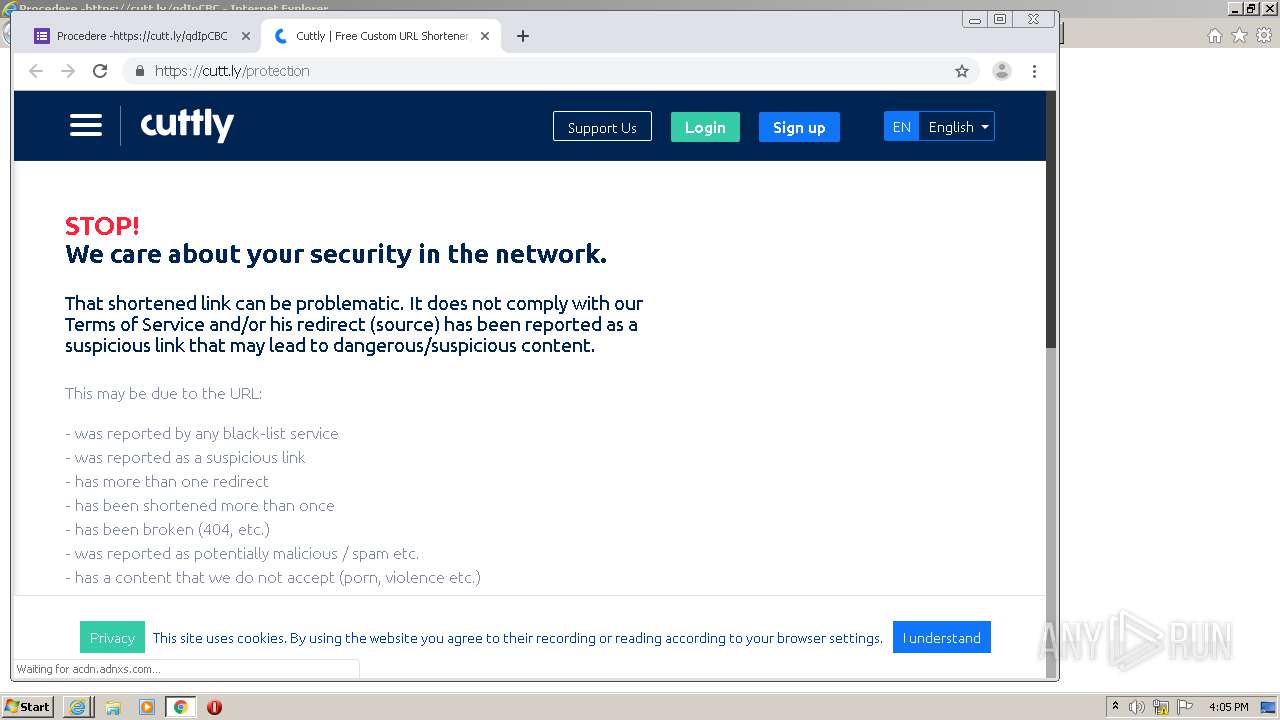
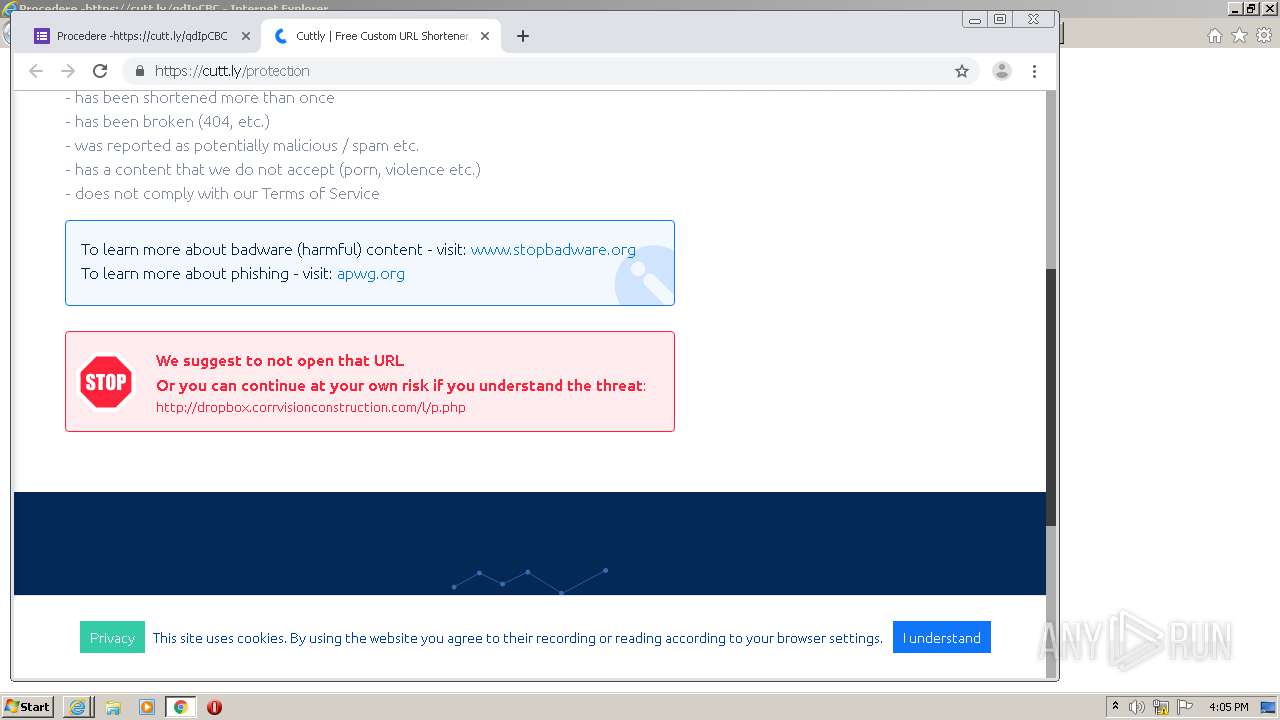
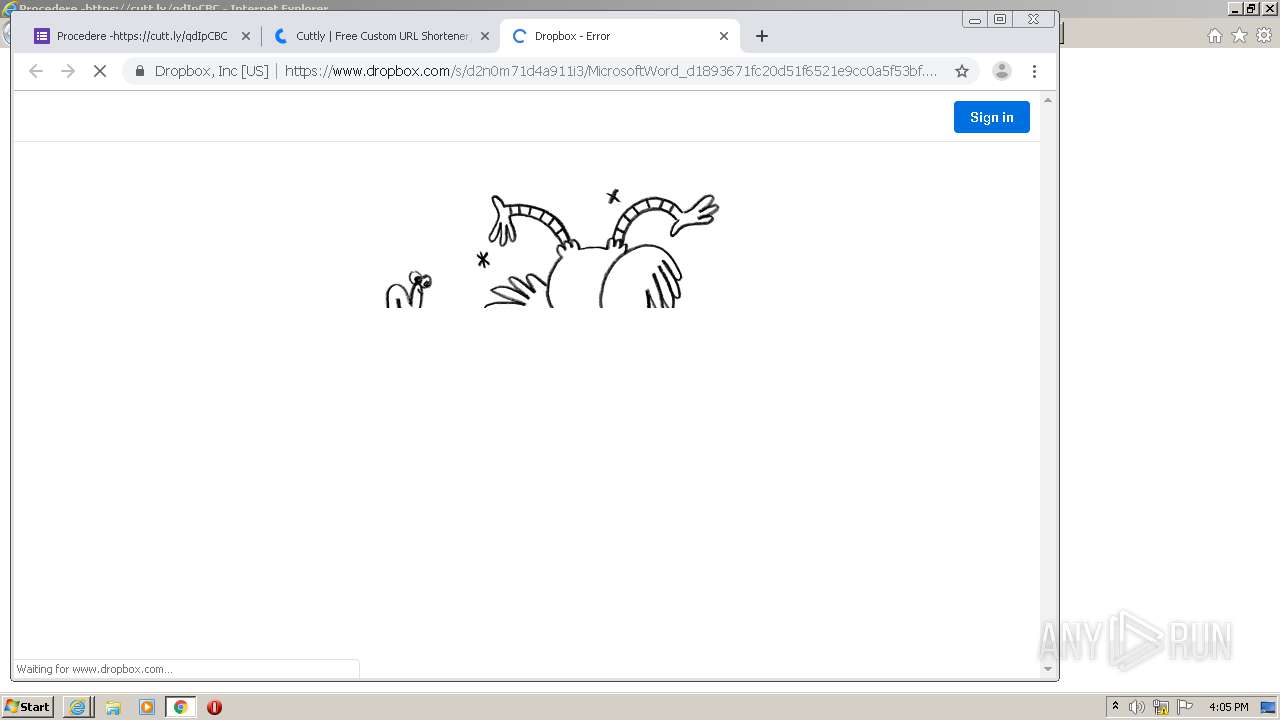
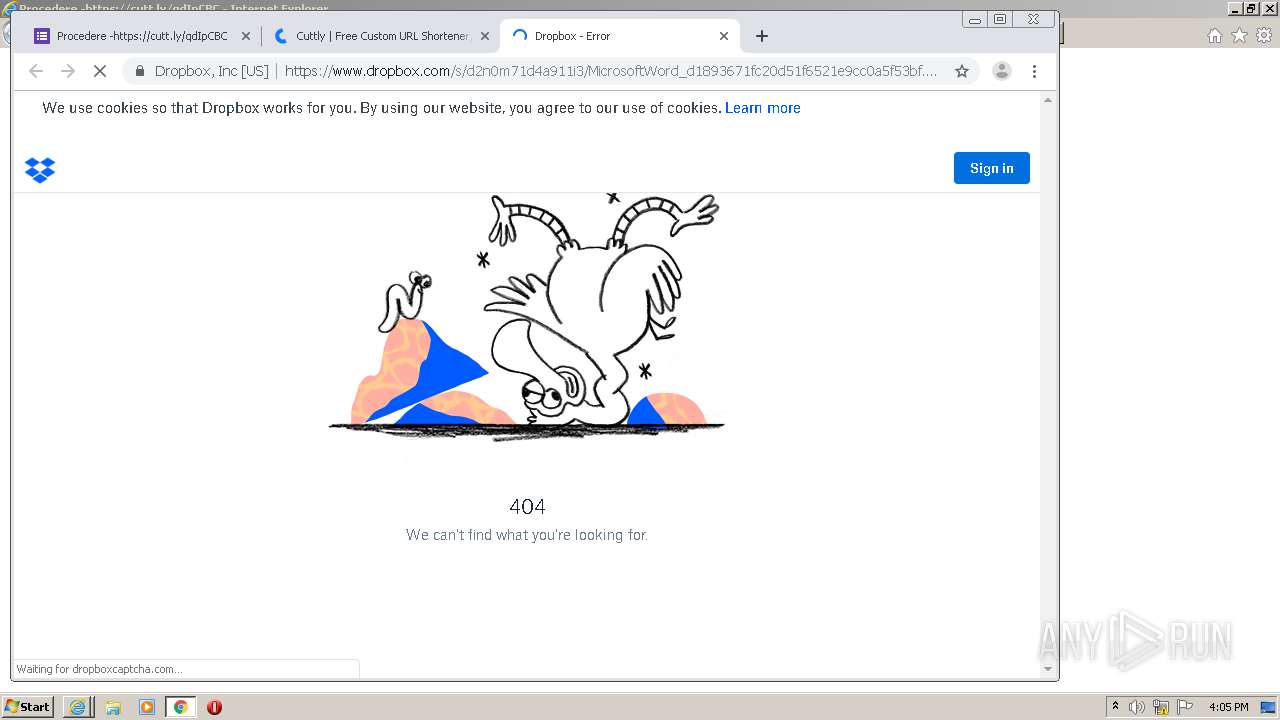
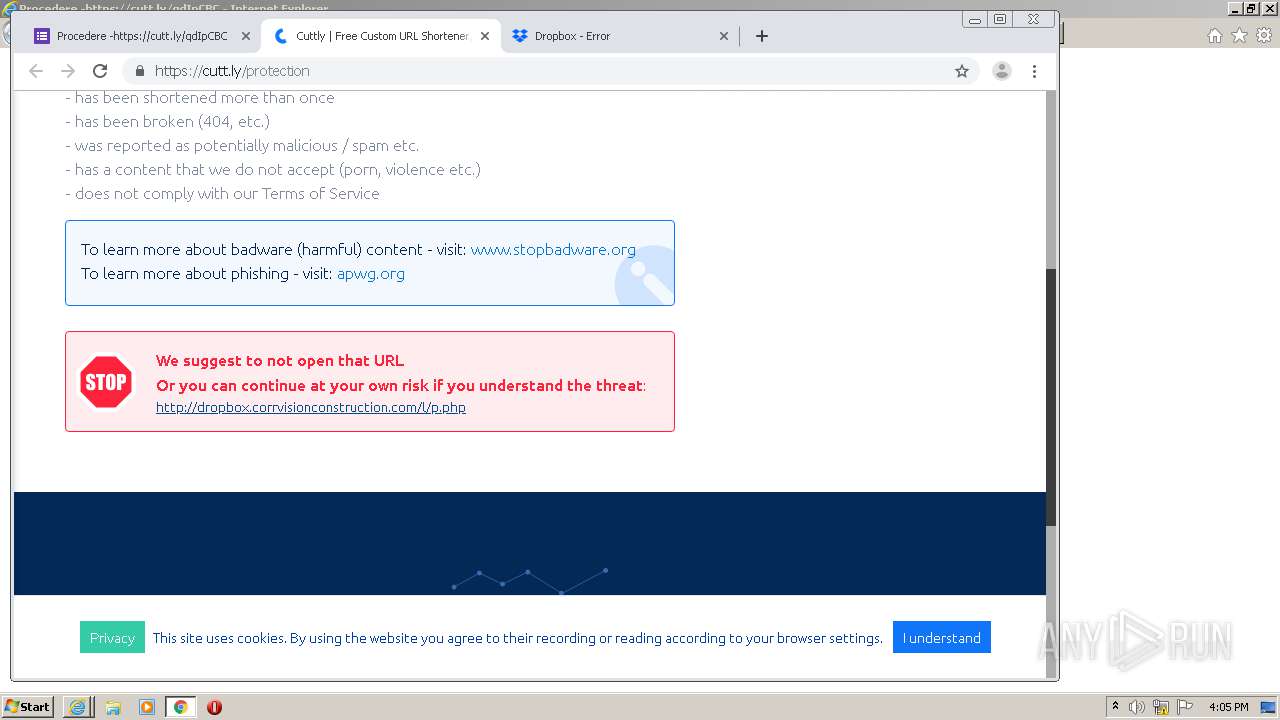
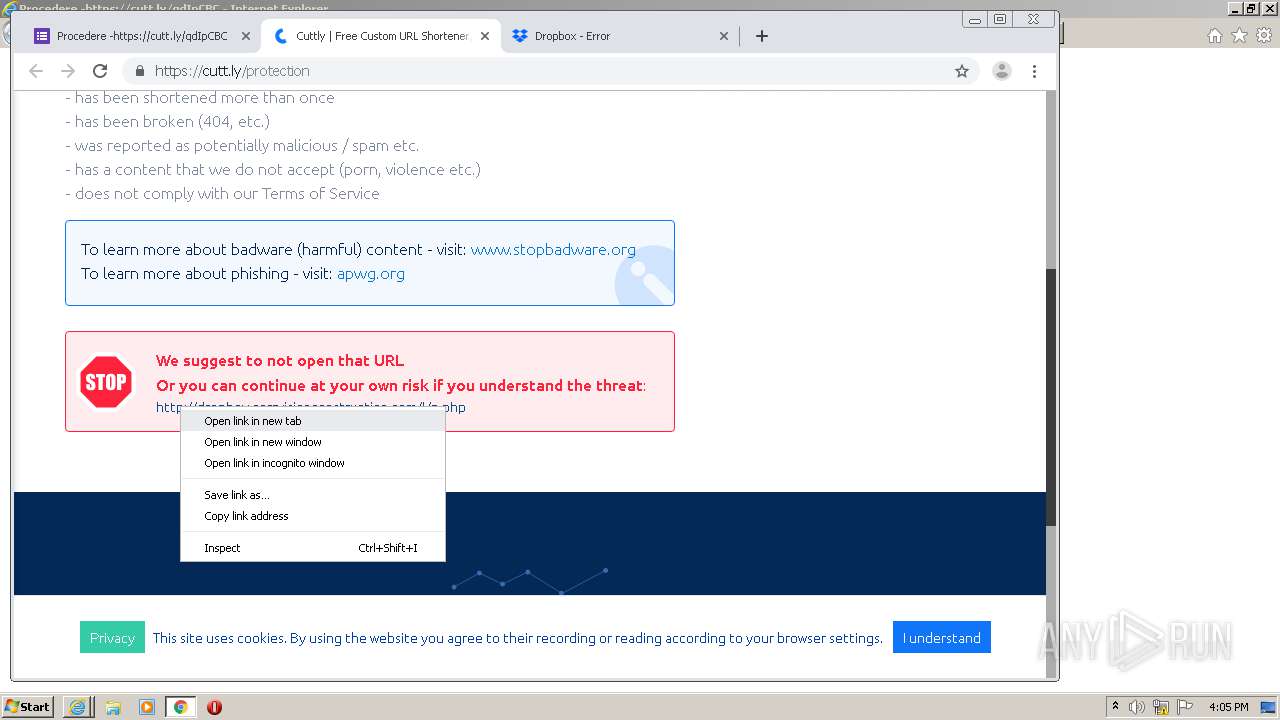
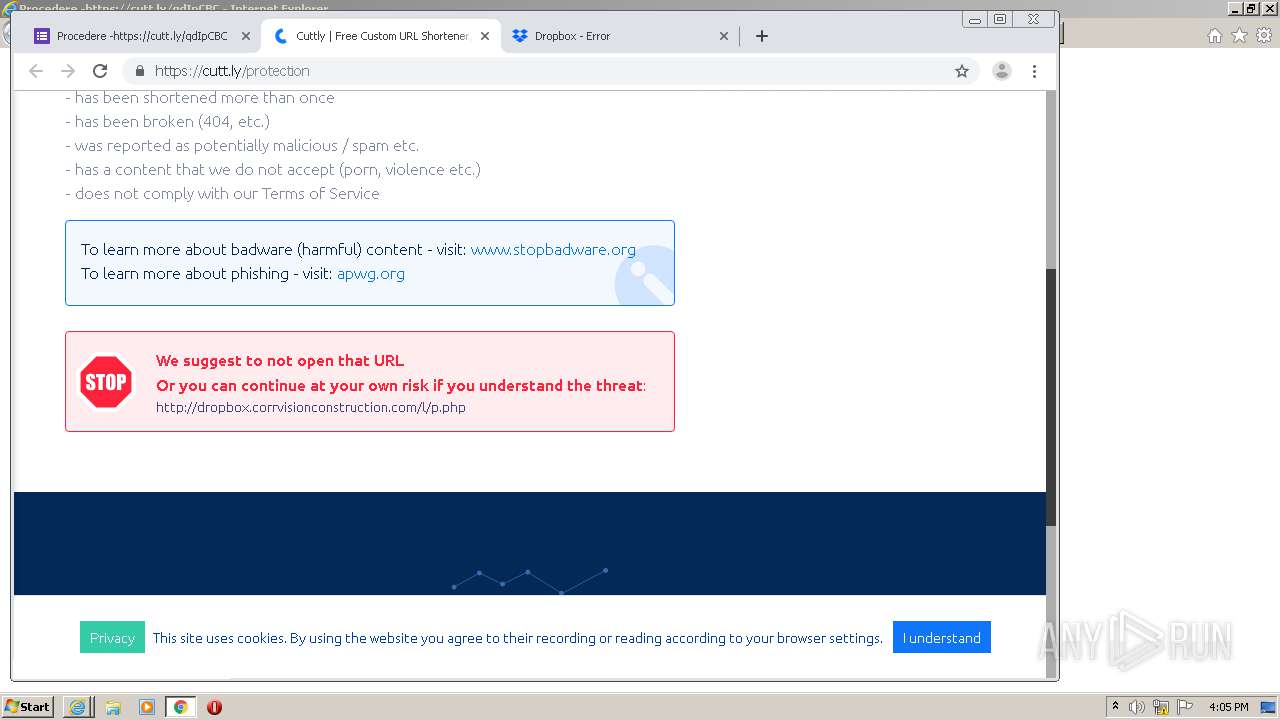
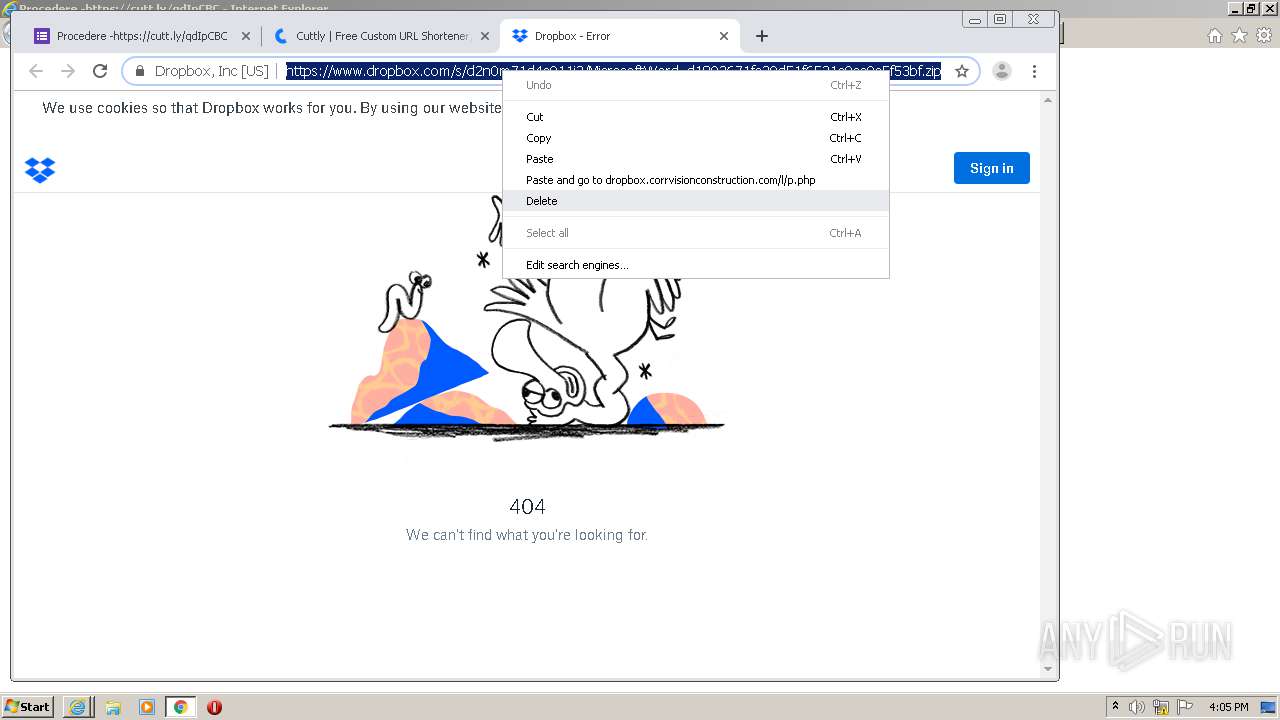
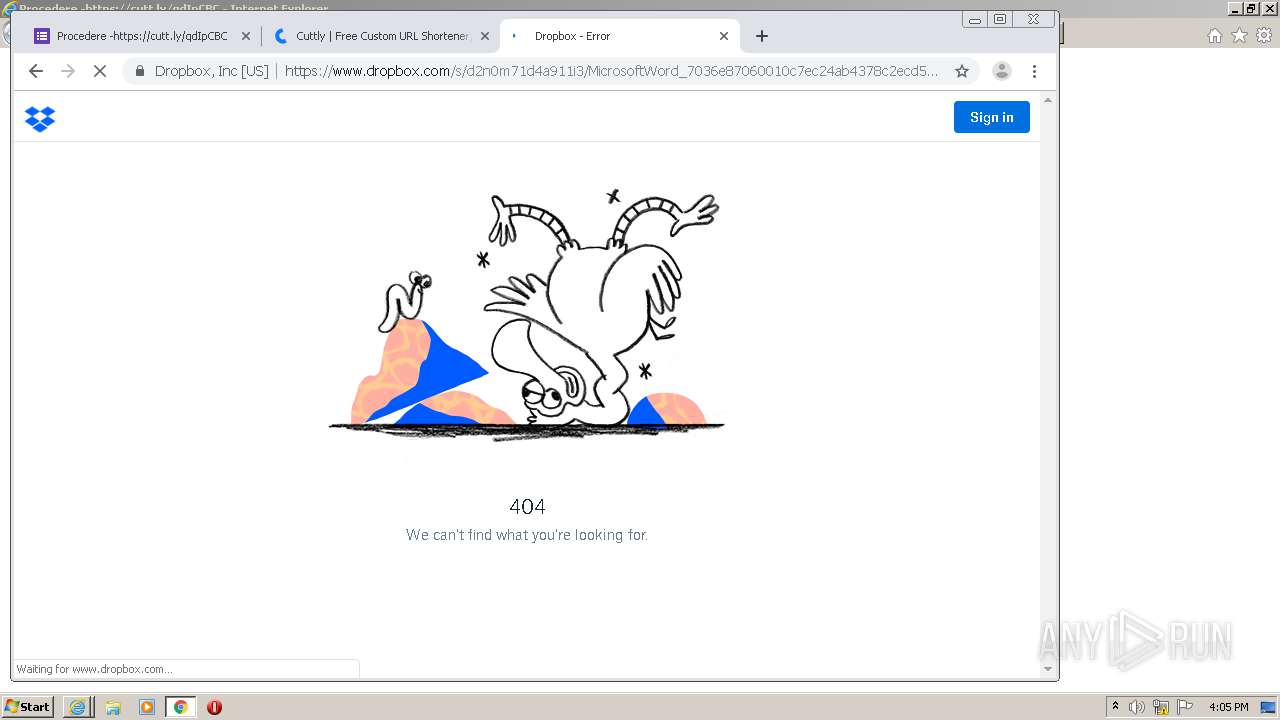
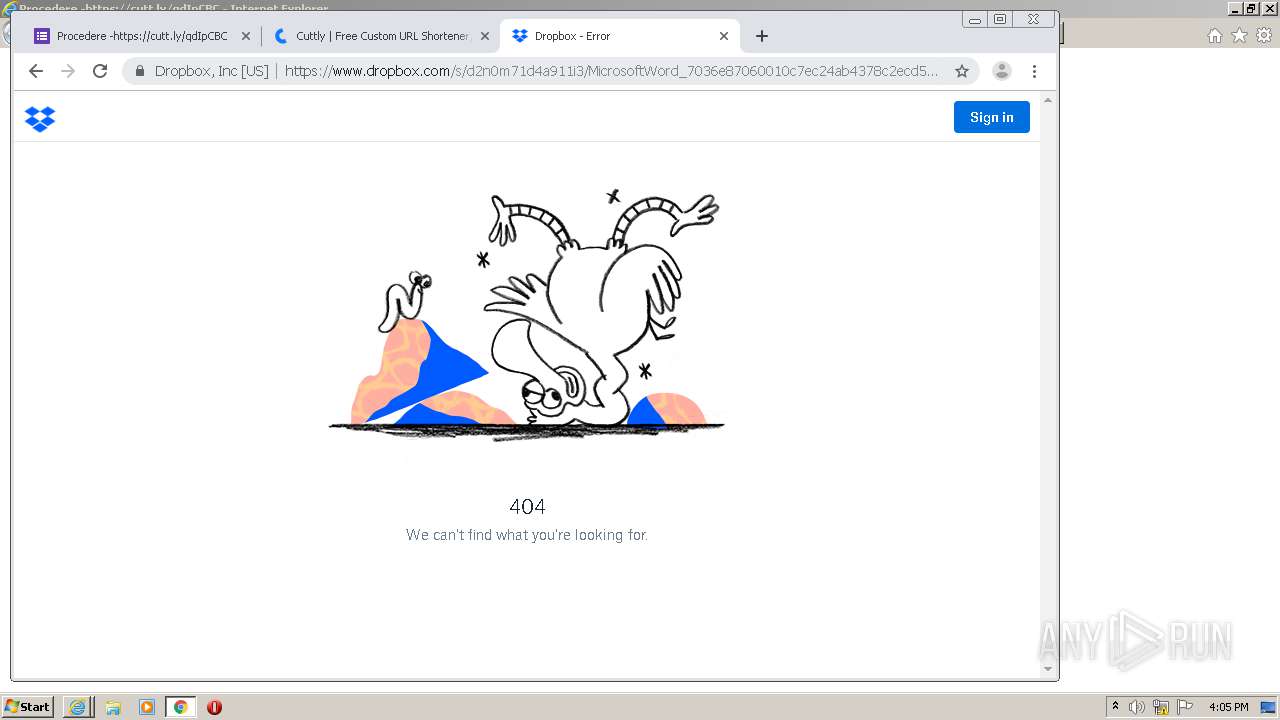
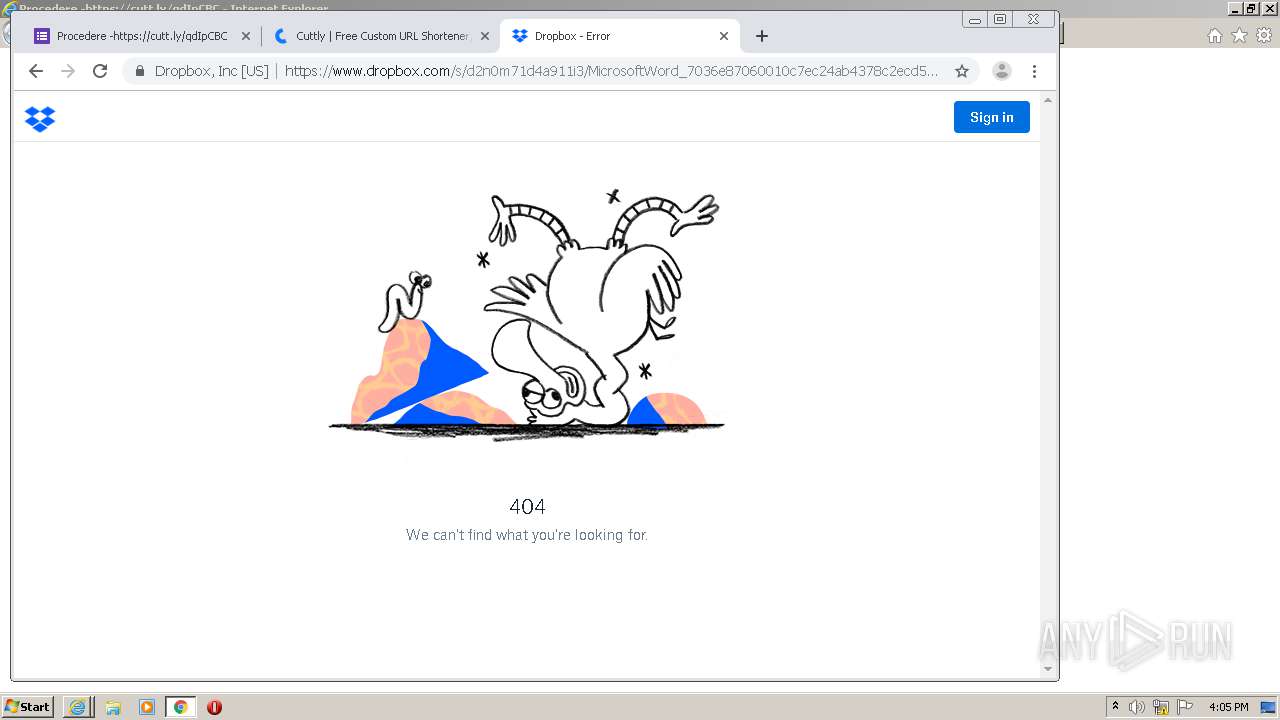
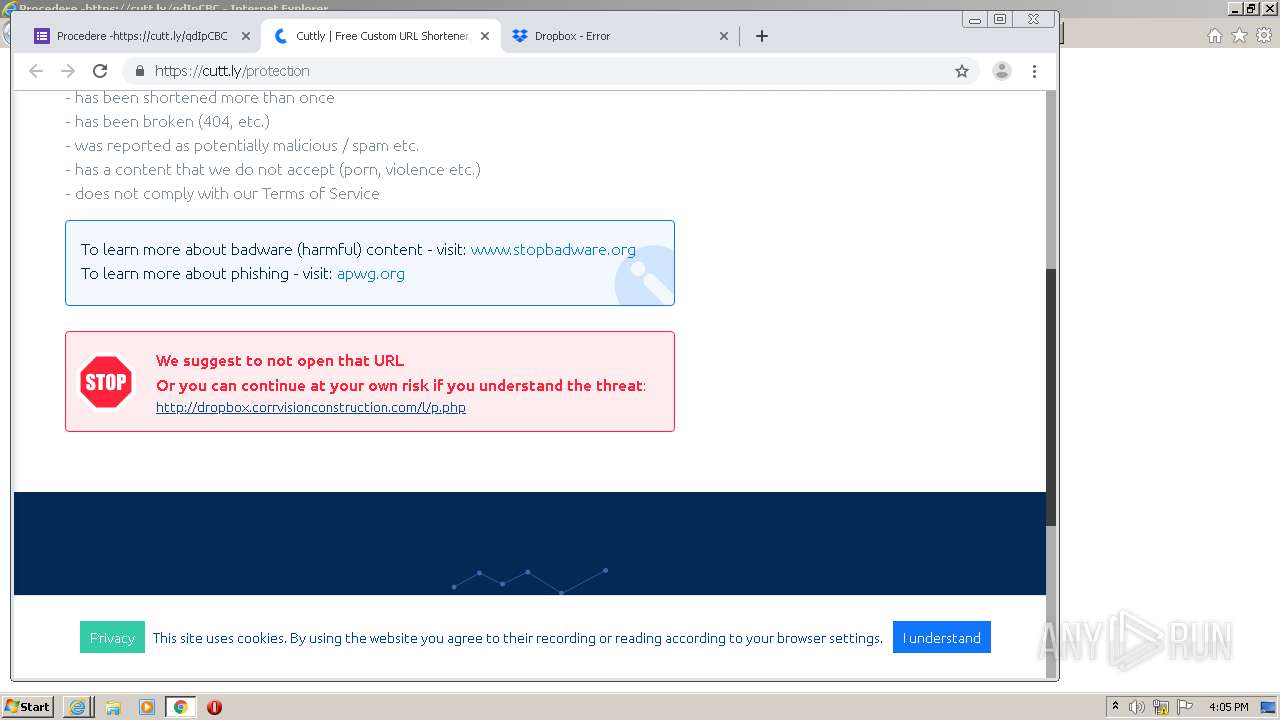
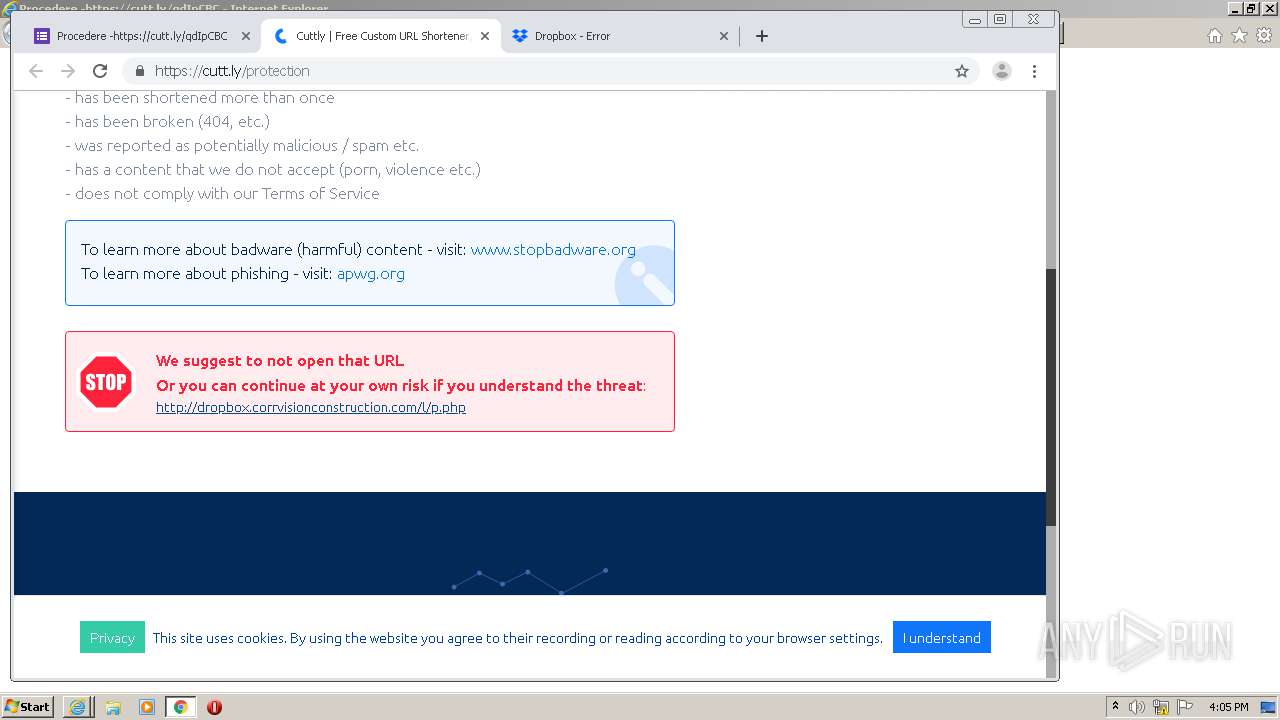
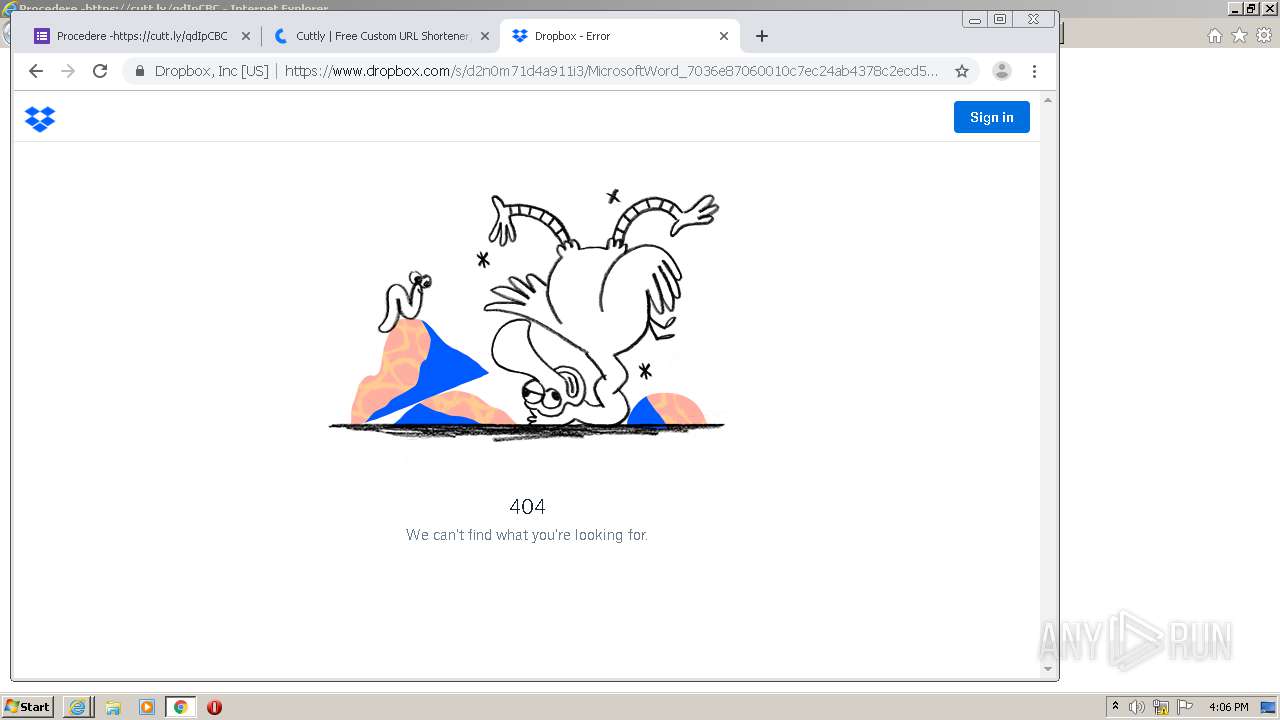
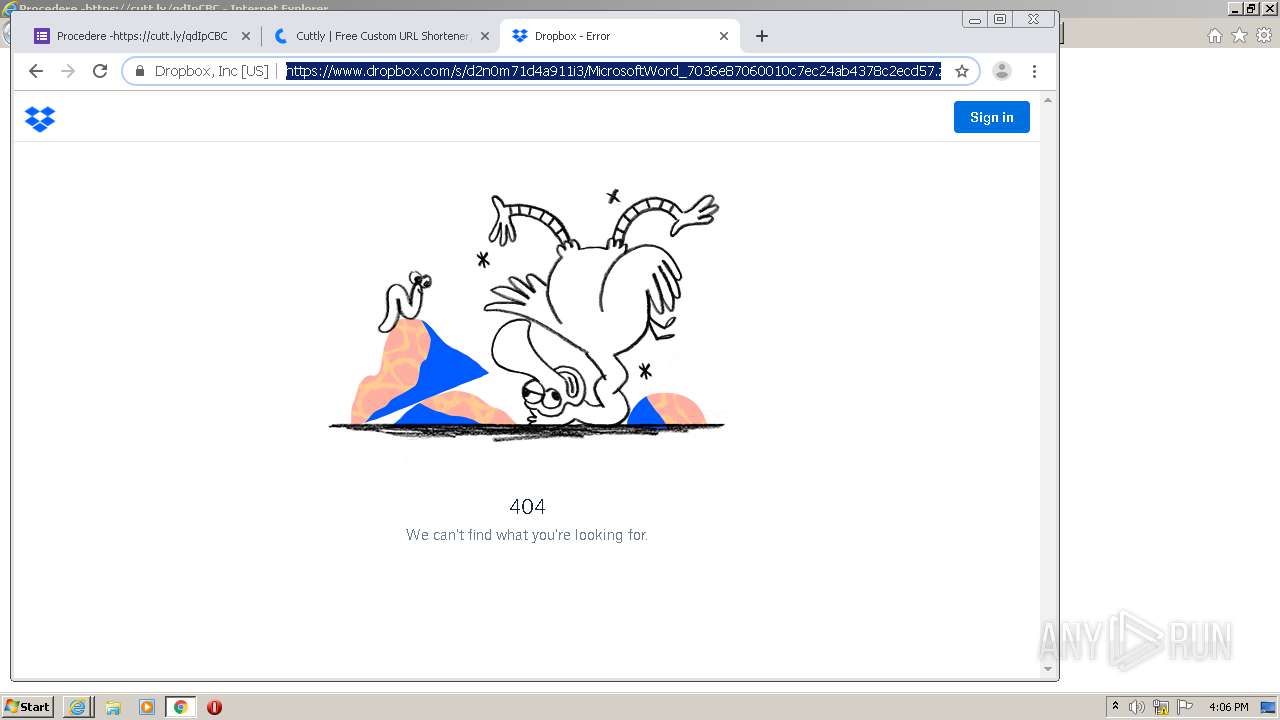
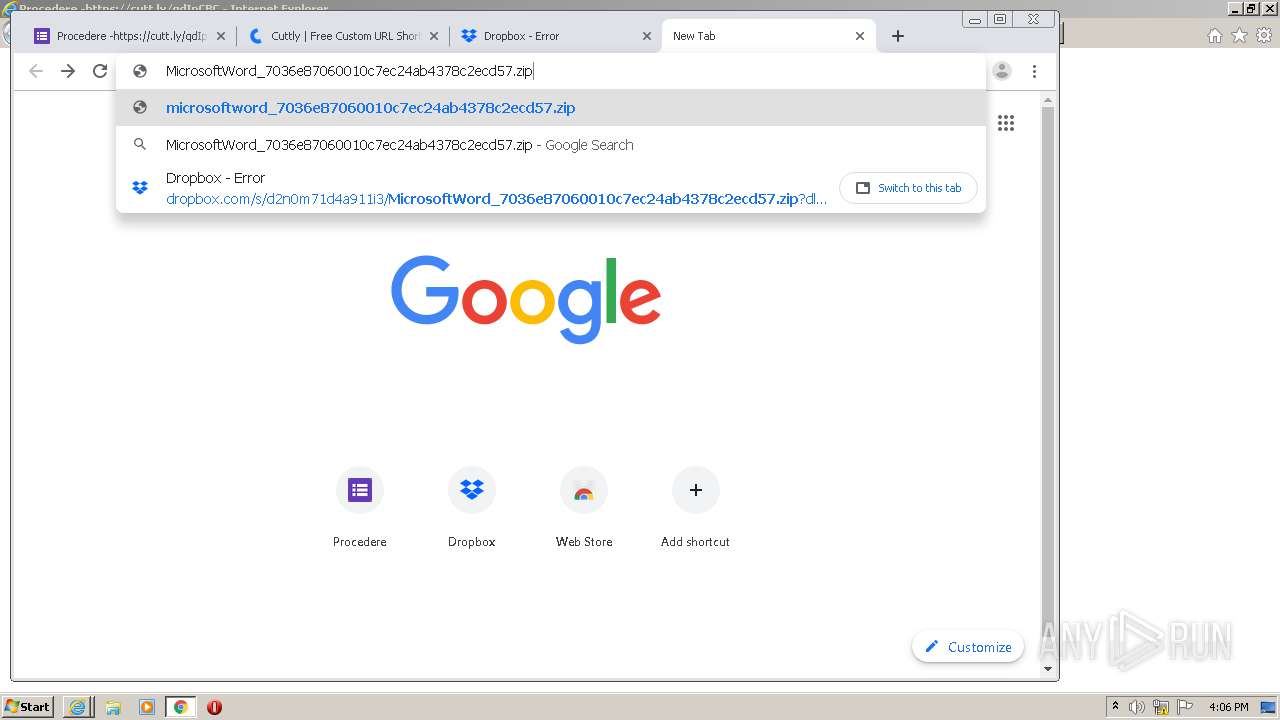
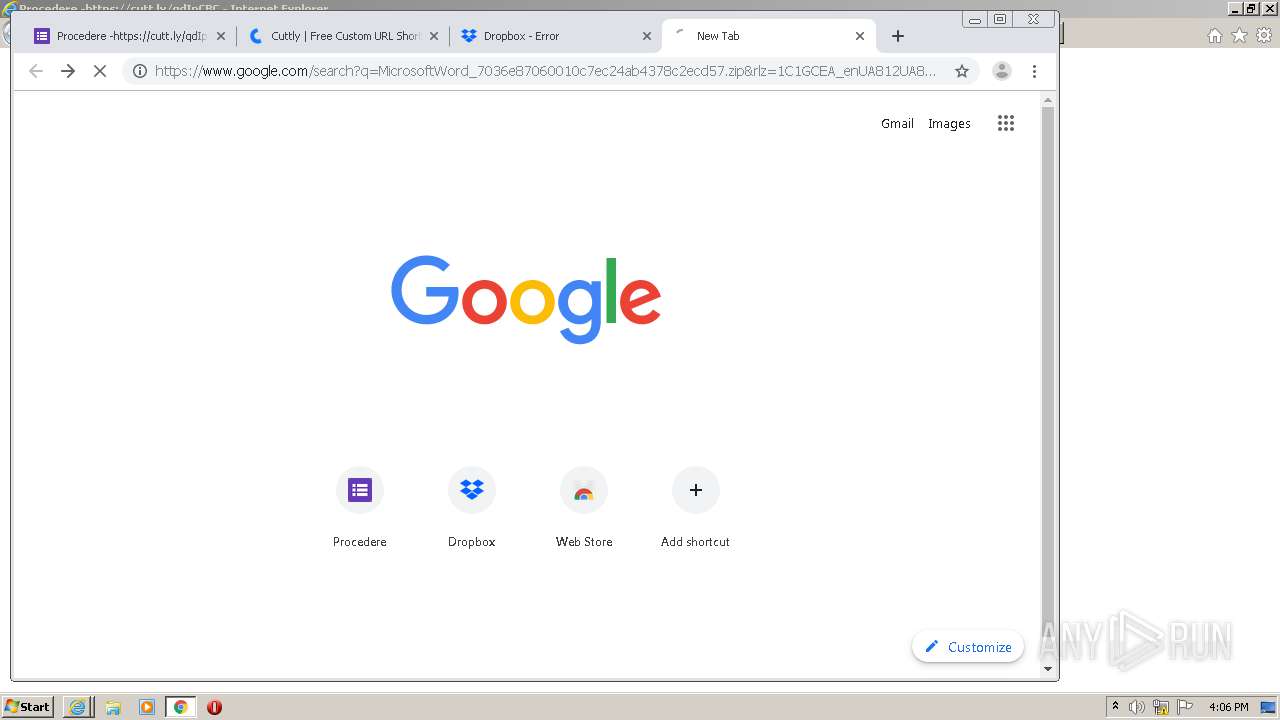
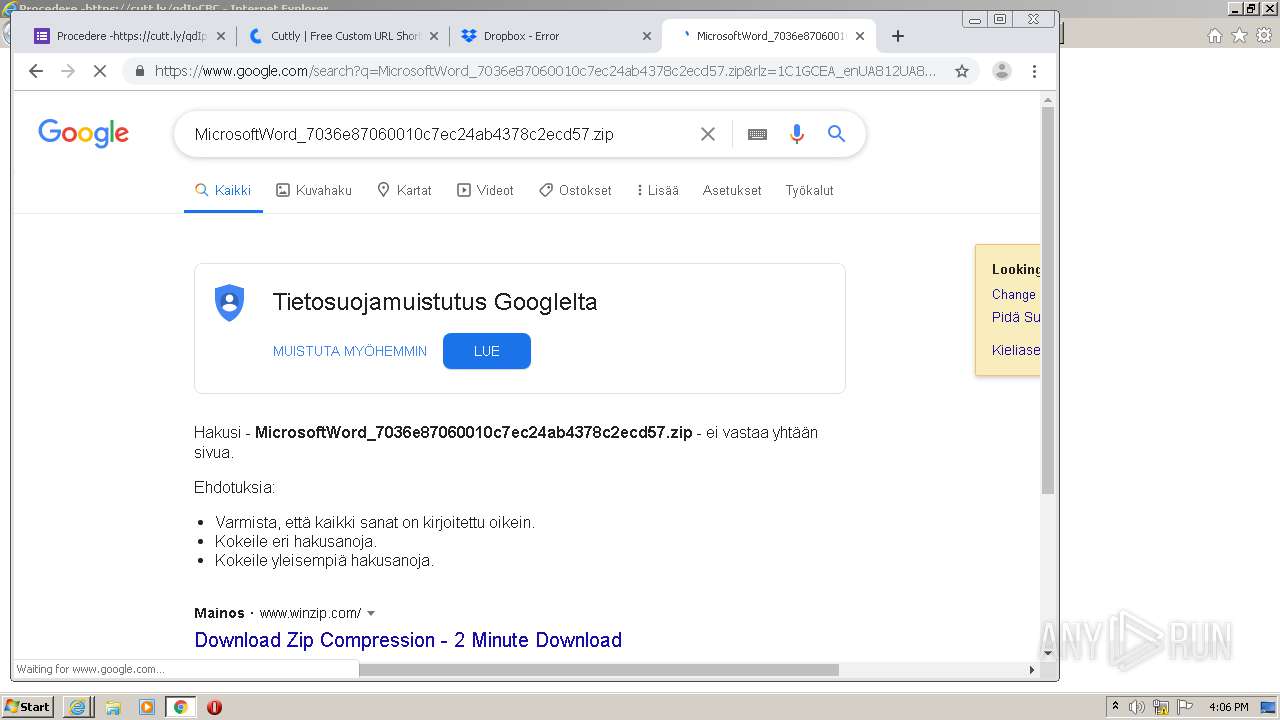
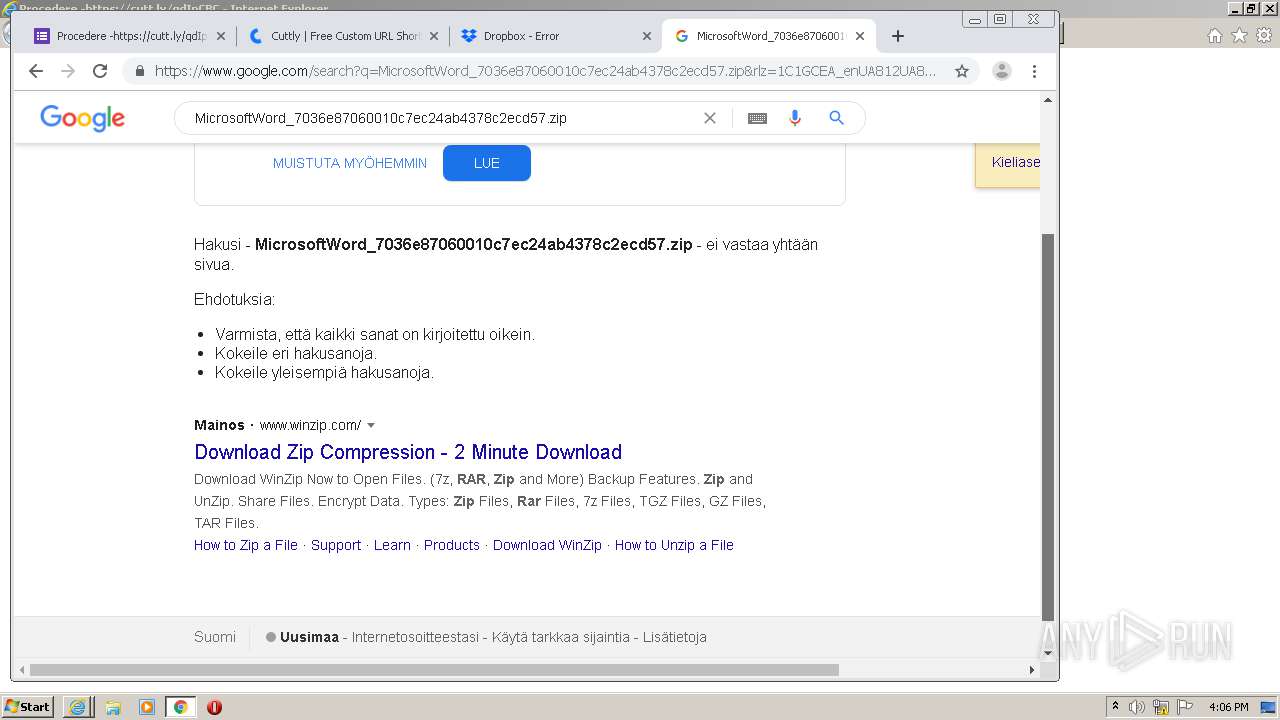
| URL: | https://docs.google.com/forms/d/12dhhD-BvN-fdHHAurSnAuBikeqtLB9H1N8BEyjRwTY8/viewform |
| Full analysis: | https://app.any.run/tasks/1d57ea85-ead8-485d-9fe8-38fa36c3de6d |
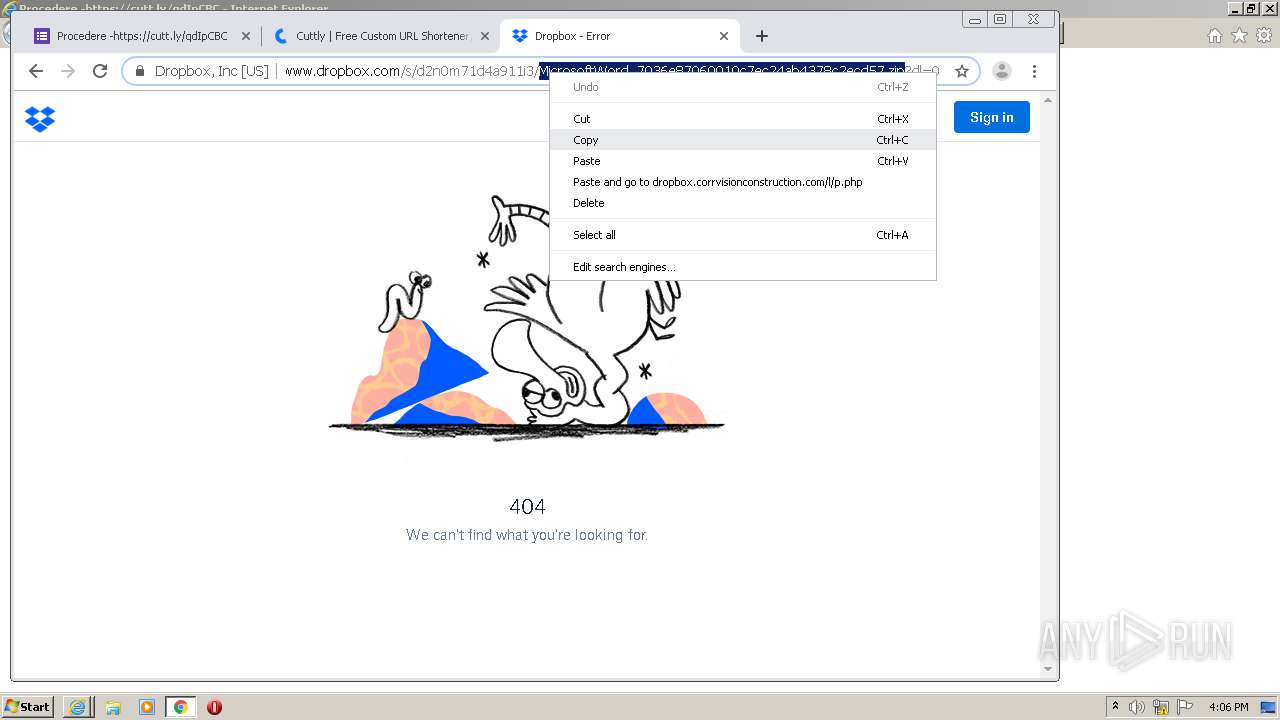
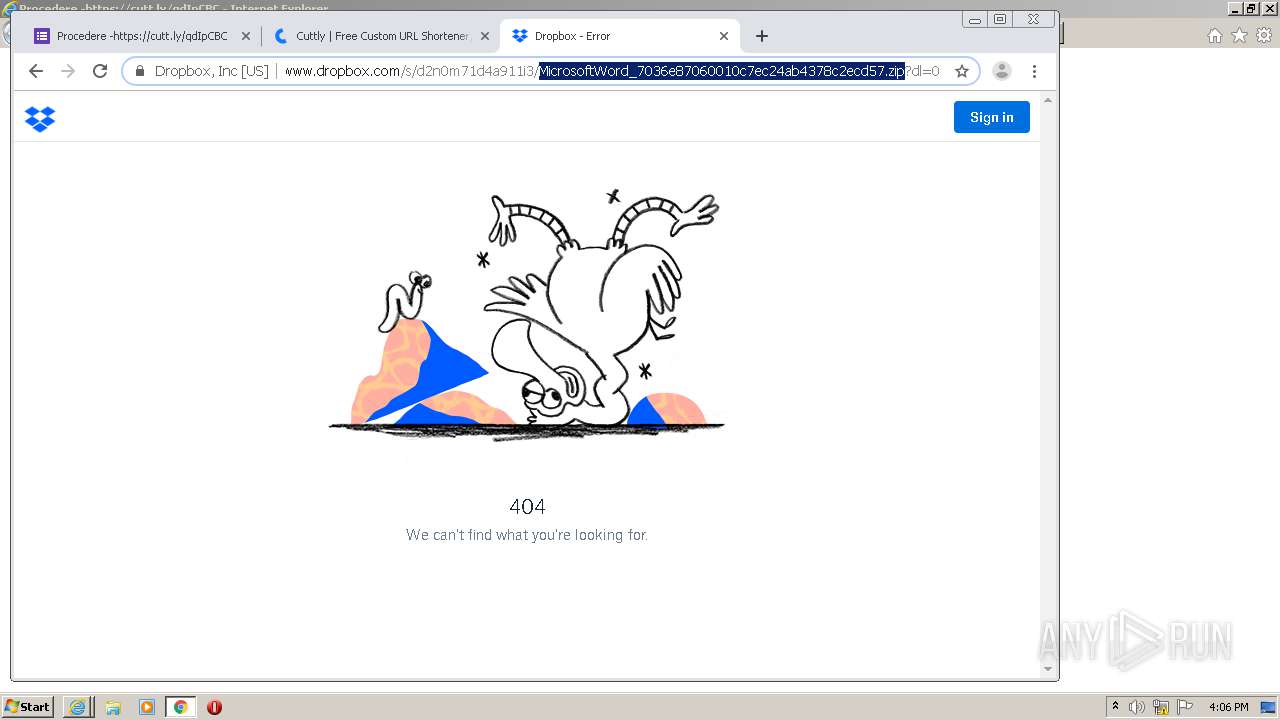
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2020, 15:03:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 24643F465E3D99E8C210A2B32360986A |
| SHA1: | B0C9D6D7930A4F39A49EA3D4A48C0CB5EAA8A604 |
| SHA256: | E5E4A909E693A7F5A555BC628B2C847DC2E56EF4C216C3165F13132CB55665B1 |
| SSDEEP: | 3:N8SP3ulYaltH2QkPncePGBwMIn:2Smv3H2PGKMI |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2288)
- iexplore.exe (PID: 2724)
- iexplore.exe (PID: 2732)
Application launched itself
- iexplore.exe (PID: 2288)
- chrome.exe (PID: 2156)
Reads settings of System Certificates
- iexplore.exe (PID: 2724)
- iexplore.exe (PID: 2288)
- iexplore.exe (PID: 2732)
- chrome.exe (PID: 1120)
Changes internet zones settings
- iexplore.exe (PID: 2288)
Reads internet explorer settings
- iexplore.exe (PID: 2724)
- iexplore.exe (PID: 2732)
Creates files in the user directory
- iexplore.exe (PID: 2724)
- iexplore.exe (PID: 2288)
- iexplore.exe (PID: 2732)
Reads the hosts file
- chrome.exe (PID: 1120)
- chrome.exe (PID: 2156)
Manual execution by user
- chrome.exe (PID: 2156)
Changes settings of System certificates
- iexplore.exe (PID: 2288)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2288)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
91
Monitored processes
51
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,12378402814703958072,12058489573650433326,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3854439359437070804 --renderer-client-id=43 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4576 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,12378402814703958072,12058489573650433326,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=8141154155937299982 --mojo-platform-channel-handle=1516 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1244 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,12378402814703958072,12058489573650433326,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10305996941979005638 --mojo-platform-channel-handle=3356 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1424 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,12378402814703958072,12058489573650433326,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14374582733464457503 --renderer-client-id=47 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4168 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1508 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,12378402814703958072,12058489573650433326,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15545571423541761292 --renderer-client-id=19 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3964 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,12378402814703958072,12058489573650433326,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2854036974769231795 --renderer-client-id=41 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5076 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1808 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,12378402814703958072,12058489573650433326,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11494744830583834949 --mojo-platform-channel-handle=1024 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1816 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,12378402814703958072,12058489573650433326,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13196656470877405465 --renderer-client-id=30 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4032 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1912 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,12378402814703958072,12058489573650433326,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15143418235678526053 --renderer-client-id=40 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4036 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1948 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,12378402814703958072,12058489573650433326,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13535757862158318866 --renderer-client-id=25 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4772 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 754
Read events
1 519
Write events
226
Delete events
9
Modification events
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 591301992 | |||
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30829973 | |||
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A3000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
275
Text files
158
Unknown types
52
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2724 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab3A17.tmp | — | |
MD5:— | SHA256:— | |||
| 2724 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar3A27.tmp | — | |
MD5:— | SHA256:— | |||
| 2724 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\OXL1H5P9.txt | text | |
MD5:— | SHA256:— | |||
| 2724 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\T0I2WFOK.txt | text | |
MD5:— | SHA256:— | |||
| 2724 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CC197601BE0898B7B0FCC91FA15D8A69_66063E1D41DB33DA9172ED5118AD6EE3 | der | |
MD5:— | SHA256:— | |||
| 2724 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CC197601BE0898B7B0FCC91FA15D8A69_66063E1D41DB33DA9172ED5118AD6EE3 | binary | |
MD5:— | SHA256:— | |||
| 2724 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\7IWOK9KH.txt | text | |
MD5:— | SHA256:— | |||
| 2288 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab47A3.tmp | — | |
MD5:— | SHA256:— | |||
| 2288 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab47A4.tmp | — | |
MD5:— | SHA256:— | |||
| 2288 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar47A5.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
190
DNS requests
114
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2724 | iexplore.exe | GET | 200 | 216.58.210.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCEs0cc0pt0BwIAAAAAc8zc | US | der | 472 b | whitelisted |
2724 | iexplore.exe | GET | 200 | 216.58.210.3:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2724 | iexplore.exe | GET | 200 | 216.58.210.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCEs0cc0pt0BwIAAAAAc8zc | US | der | 472 b | whitelisted |
2732 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://status.rapidssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRJiUKgT2m88fZ4nxc1Lu6M%2FjvkagQUDNtsgkkPSmcKuBTuesRIUojrVjgCEAZTxDKF8FTpV2C9b5Jl9Kw%3D | US | der | 471 b | shared |
2724 | iexplore.exe | GET | 200 | 216.58.210.3:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEAKhmcGKkEWcAgAAAABzzGw%3D | US | der | 471 b | whitelisted |
2724 | iexplore.exe | GET | 200 | 216.58.210.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCEs0cc0pt0BwIAAAAAc8zc | US | der | 472 b | whitelisted |
2724 | iexplore.exe | GET | 200 | 216.58.210.3:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEDdE1cf4Gvu%2FAgAAAABzzNg%3D | US | der | 471 b | whitelisted |
2724 | iexplore.exe | GET | 200 | 216.58.210.3:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEDdE1cf4Gvu%2FAgAAAABzzNg%3D | US | der | 471 b | whitelisted |
2288 | iexplore.exe | GET | 200 | 104.18.24.243:80 | http://ocsp.msocsp.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIGkp0%2Fv9GUvNUu1EP06Tu7%2BChyAQUkZ47RGw9V5xCdyo010%2FRzEqXLNoCExwAFF8jA2u85i8%2FLFYAAAAUXyM%3D | US | der | 1.79 Kb | whitelisted |
2724 | iexplore.exe | GET | 200 | 216.58.210.3:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEDdE1cf4Gvu%2FAgAAAABzzNg%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2724 | iexplore.exe | 172.217.22.110:443 | docs.google.com | Google Inc. | US | whitelisted |
2724 | iexplore.exe | 216.58.207.74:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2724 | iexplore.exe | 172.217.21.195:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2724 | iexplore.exe | 172.217.23.99:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2288 | iexplore.exe | 172.217.23.99:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2288 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2288 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2288 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2732 | iexplore.exe | 172.217.16.164:443 | www.google.com | Google Inc. | US | whitelisted |
2288 | iexplore.exe | 172.217.16.164:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
docs.google.com |
| shared |
ocsp.pki.goog |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.pki.goog |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |