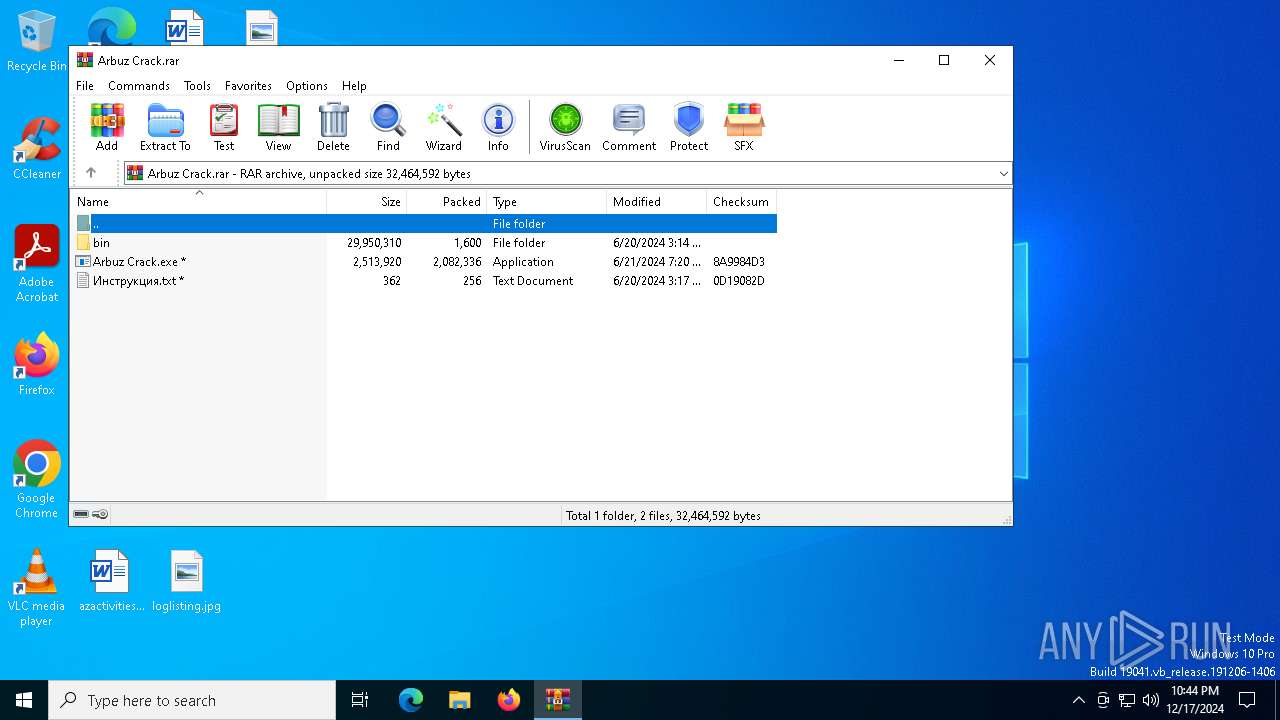
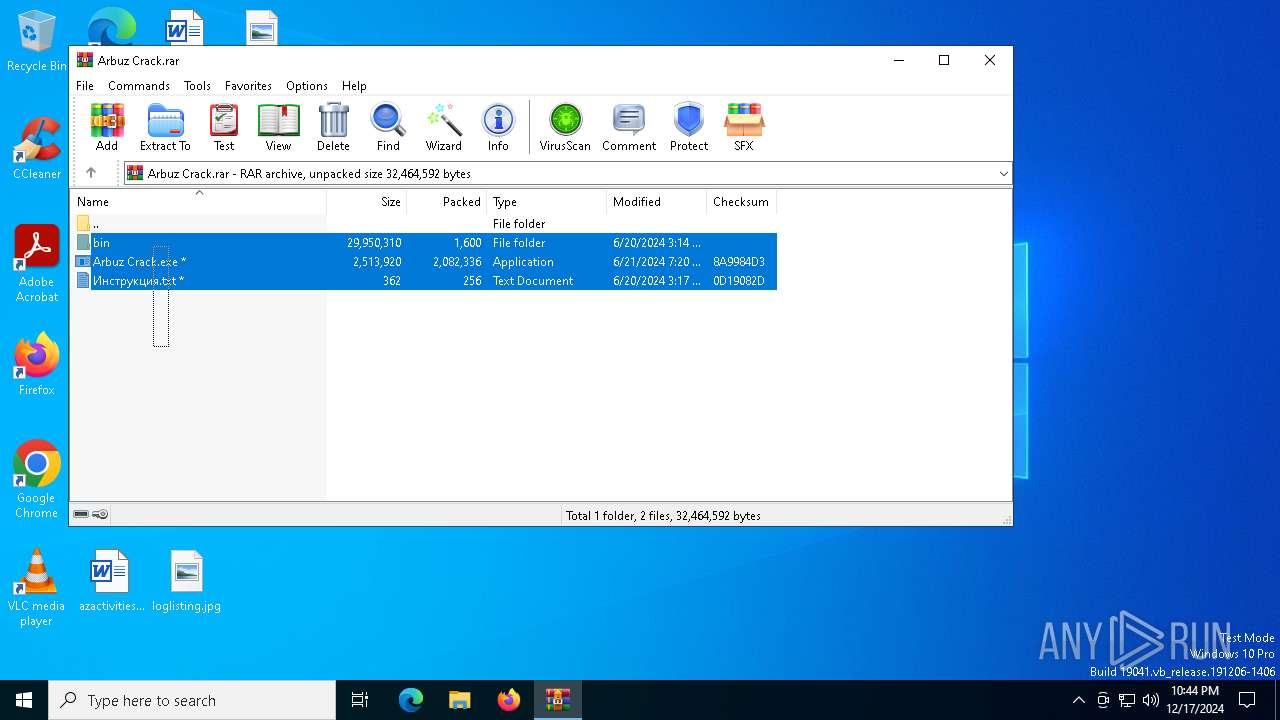
| File name: | Arbuz Crack.rar |
| Full analysis: | https://app.any.run/tasks/2cdeb169-de19-4ac9-b020-b9c0deb320f3 |
| Verdict: | Malicious activity |
| Analysis date: | December 17, 2024, 22:44:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 1424FA2CB5E27148F8928B85DEB6CD16 |
| SHA1: | 57821FD9A2937B2C5D56589D7A5ECB3391B007B8 |
| SHA256: | E5D9461E71D17FB701B871F3AC5522E1E08697EAB73724CFC522F800AD02DC17 |
| SSDEEP: | 98304:1O7kUBDkdv1aVgbuqB1nvo9dhRQpZ4tjyTSxROdXDj4oMO5z5axeYPcLuYRxpTPn:JCGL |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 7160)
- wscript.exe (PID: 6212)
- wscript.exe (PID: 1328)
SUSPICIOUS
Executable content was dropped or overwritten
- Arbuz Crack.exe (PID: 6976)
- crackarbuz.exe (PID: 7032)
- hypercom.exe (PID: 5536)
- Arbuz Crack.exe (PID: 6984)
- hypercom.exe (PID: 7160)
- Arbuz Crack.exe (PID: 1224)
- hypercom.exe (PID: 1356)
Executing commands from a ".bat" file
- Arbuz Crack.exe (PID: 7060)
- wscript.exe (PID: 7160)
- Arbuz Crack.exe (PID: 6996)
- hypercom.exe (PID: 7160)
- Arbuz Crack.exe (PID: 5628)
- wscript.exe (PID: 6212)
- hypercom.exe (PID: 1356)
- wscript.exe (PID: 1328)
Reads security settings of Internet Explorer
- Arbuz Crack.exe (PID: 6976)
- crackarbuz.exe (PID: 7032)
- Arbuz Crack.exe (PID: 6984)
- Arbuz Crack.exe (PID: 1224)
Starts CMD.EXE for commands execution
- Arbuz Crack.exe (PID: 7060)
- wscript.exe (PID: 7160)
- wscript.exe (PID: 6212)
- Arbuz Crack.exe (PID: 6996)
- hypercom.exe (PID: 7160)
- Arbuz Crack.exe (PID: 5628)
- wscript.exe (PID: 1328)
- hypercom.exe (PID: 1356)
The executable file from the user directory is run by the CMD process
- hypercom.exe (PID: 5536)
- hypercom.exe (PID: 7160)
- hypercom.exe (PID: 1356)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7160)
- wscript.exe (PID: 6212)
- wscript.exe (PID: 1328)
The process executes VB scripts
- cmd.exe (PID: 7128)
- cmd.exe (PID: 6180)
Checks for external IP
- svchost.exe (PID: 2192)
- hypercom.exe (PID: 5536)
- Registry.exe (PID: 3080)
- hypercom.exe (PID: 7160)
- dllhost.exe (PID: 4228)
- hypercom.exe (PID: 1356)
The process creates files with name similar to system file names
- hypercom.exe (PID: 5536)
Executed via WMI
- schtasks.exe (PID: 5460)
- schtasks.exe (PID: 3420)
- schtasks.exe (PID: 4980)
- schtasks.exe (PID: 936)
- schtasks.exe (PID: 6012)
- schtasks.exe (PID: 5544)
- schtasks.exe (PID: 6368)
- schtasks.exe (PID: 1540)
- schtasks.exe (PID: 6640)
- schtasks.exe (PID: 6740)
- schtasks.exe (PID: 6660)
- schtasks.exe (PID: 6756)
- schtasks.exe (PID: 6324)
- schtasks.exe (PID: 2076)
- schtasks.exe (PID: 6952)
- schtasks.exe (PID: 6736)
- schtasks.exe (PID: 6772)
- schtasks.exe (PID: 5392)
- schtasks.exe (PID: 6996)
- schtasks.exe (PID: 7052)
- schtasks.exe (PID: 7072)
- schtasks.exe (PID: 7004)
- schtasks.exe (PID: 7032)
- schtasks.exe (PID: 7152)
- schtasks.exe (PID: 6972)
- schtasks.exe (PID: 7160)
- schtasks.exe (PID: 3732)
- schtasks.exe (PID: 4716)
- schtasks.exe (PID: 5792)
- schtasks.exe (PID: 640)
- schtasks.exe (PID: 556)
- schtasks.exe (PID: 4428)
- schtasks.exe (PID: 3524)
- schtasks.exe (PID: 3992)
- schtasks.exe (PID: 1804)
- schtasks.exe (PID: 5588)
- schtasks.exe (PID: 5460)
- schtasks.exe (PID: 5252)
- schtasks.exe (PID: 4128)
- schtasks.exe (PID: 5572)
- schtasks.exe (PID: 5092)
- schtasks.exe (PID: 6700)
- schtasks.exe (PID: 6200)
- schtasks.exe (PID: 1804)
- schtasks.exe (PID: 3840)
- schtasks.exe (PID: 3140)
- schtasks.exe (PID: 4244)
- schtasks.exe (PID: 5040)
- schtasks.exe (PID: 5720)
- schtasks.exe (PID: 4980)
- schtasks.exe (PID: 5340)
- schtasks.exe (PID: 5728)
- schtasks.exe (PID: 4668)
- schtasks.exe (PID: 5604)
- schtasks.exe (PID: 3812)
- schtasks.exe (PID: 936)
- schtasks.exe (PID: 4932)
- schtasks.exe (PID: 6088)
- schtasks.exe (PID: 5616)
- schtasks.exe (PID: 3288)
- schtasks.exe (PID: 6200)
- schtasks.exe (PID: 836)
- schtasks.exe (PID: 536)
- schtasks.exe (PID: 6032)
- schtasks.exe (PID: 4244)
- schtasks.exe (PID: 5460)
- schtasks.exe (PID: 3820)
- schtasks.exe (PID: 6068)
- schtasks.exe (PID: 2928)
- schtasks.exe (PID: 5752)
- schtasks.exe (PID: 3208)
- schtasks.exe (PID: 6284)
- schtasks.exe (PID: 3560)
- schtasks.exe (PID: 4724)
- schtasks.exe (PID: 204)
- schtasks.exe (PID: 5592)
- schtasks.exe (PID: 4008)
- schtasks.exe (PID: 6156)
- schtasks.exe (PID: 7132)
- schtasks.exe (PID: 5432)
- schtasks.exe (PID: 6696)
- schtasks.exe (PID: 6648)
- schtasks.exe (PID: 2624)
- schtasks.exe (PID: 6332)
- schtasks.exe (PID: 6700)
- schtasks.exe (PID: 4468)
- schtasks.exe (PID: 6204)
- schtasks.exe (PID: 6768)
- schtasks.exe (PID: 6340)
- schtasks.exe (PID: 3140)
Likely accesses (executes) a file from the Public directory
- schtasks.exe (PID: 936)
- schtasks.exe (PID: 6012)
- schtasks.exe (PID: 5544)
- schtasks.exe (PID: 6740)
- schtasks.exe (PID: 6660)
- schtasks.exe (PID: 6700)
- schtasks.exe (PID: 6756)
- schtasks.exe (PID: 6324)
- schtasks.exe (PID: 6736)
- schtasks.exe (PID: 6772)
- schtasks.exe (PID: 2076)
- schtasks.exe (PID: 5392)
- schtasks.exe (PID: 7052)
- schtasks.exe (PID: 7004)
- schtasks.exe (PID: 6972)
- schtasks.exe (PID: 7032)
- schtasks.exe (PID: 3732)
- schtasks.exe (PID: 4244)
- schtasks.exe (PID: 5040)
- schtasks.exe (PID: 936)
- schtasks.exe (PID: 4980)
- schtasks.exe (PID: 5604)
- schtasks.exe (PID: 5340)
- schtasks.exe (PID: 6952)
- dllhost.exe (PID: 4228)
- schtasks.exe (PID: 6200)
- schtasks.exe (PID: 6032)
- schtasks.exe (PID: 6648)
- schtasks.exe (PID: 6156)
- schtasks.exe (PID: 6696)
- schtasks.exe (PID: 3288)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 6744)
- cmd.exe (PID: 7128)
Starts itself from another location
- hypercom.exe (PID: 5536)
Reads the date of Windows installation
- hypercom.exe (PID: 1356)
INFO
Manual execution by a user
- Arbuz Crack.exe (PID: 6976)
- Arbuz Crack.exe (PID: 6984)
- Arbuz Crack.exe (PID: 1224)
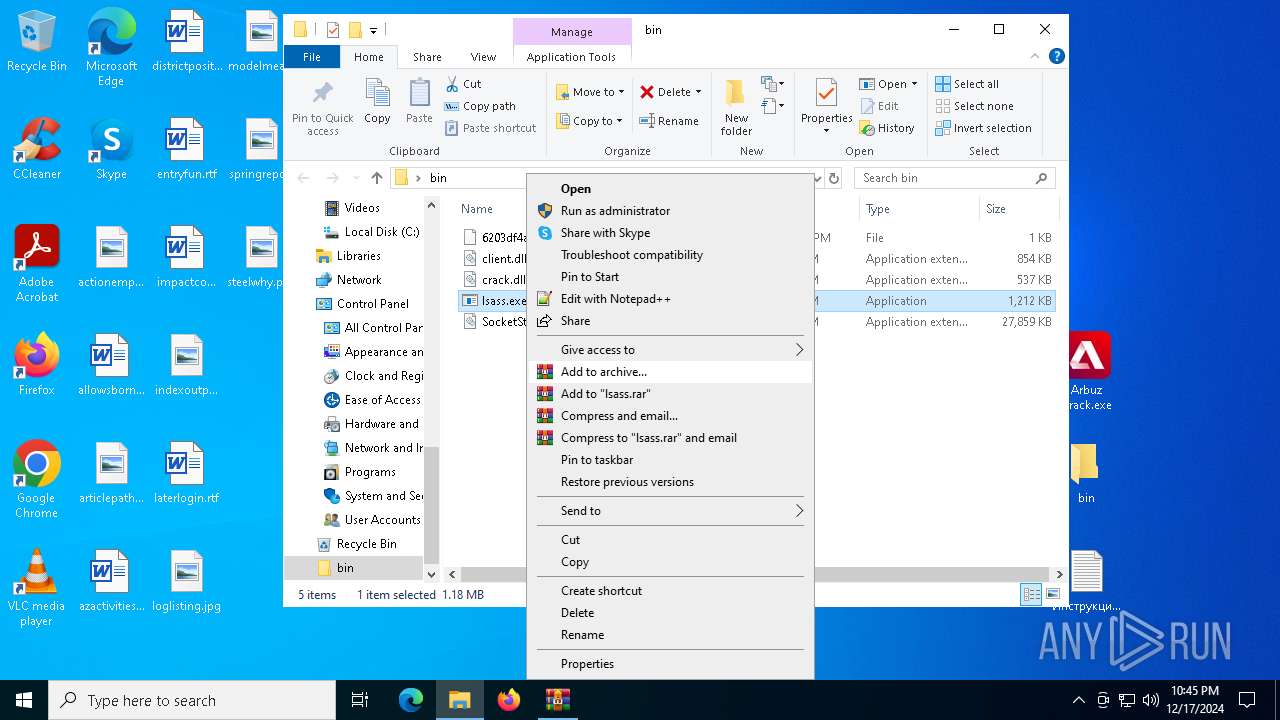
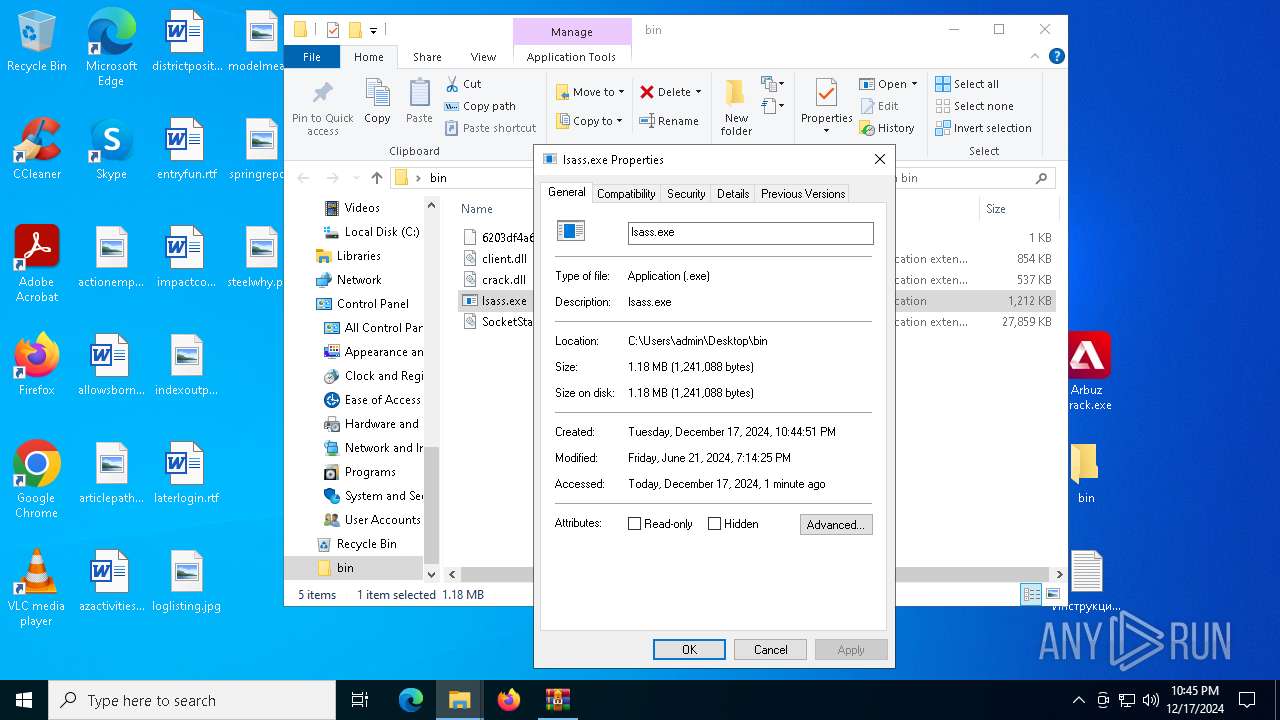
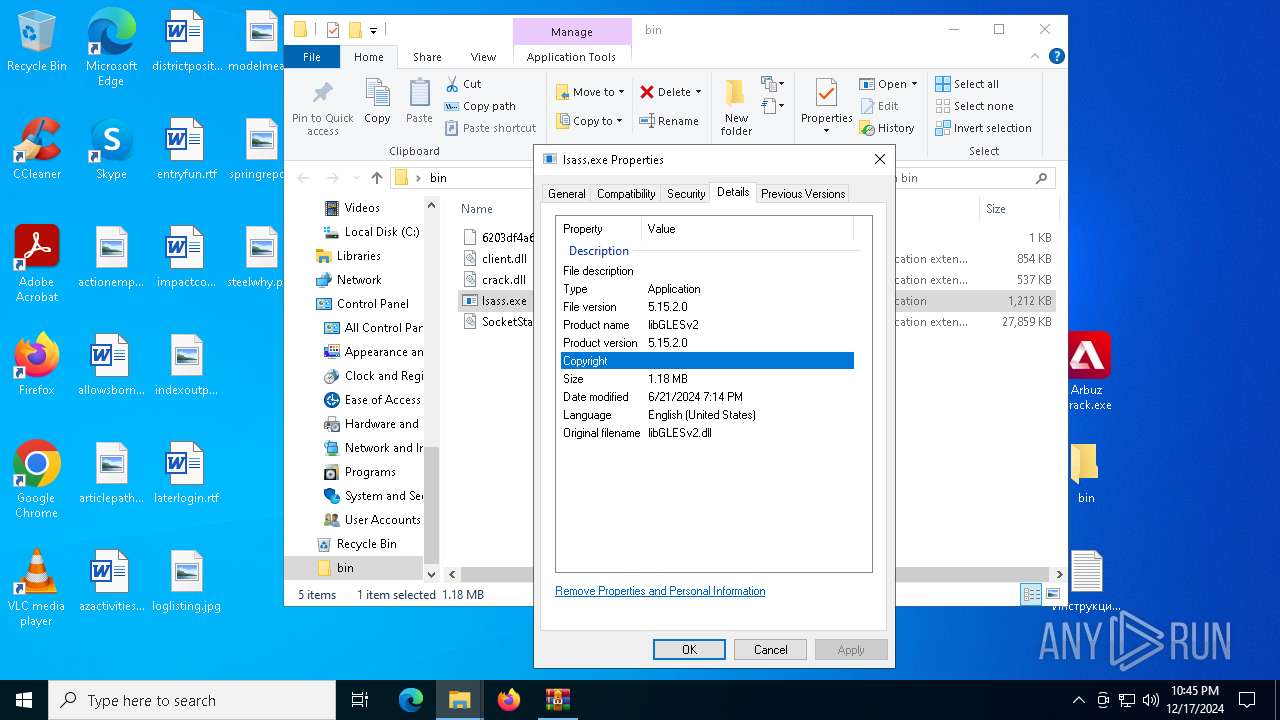
- lsass.exe (PID: 540)
- lsass.exe (PID: 3816)
- lsass.exe (PID: 3640)
Checks supported languages
- Arbuz Crack.exe (PID: 6976)
- Arbuz Crack.exe (PID: 7060)
- crackarbuz.exe (PID: 7032)
- hypercom.exe (PID: 5536)
- Arbuz Crack.exe (PID: 6996)
- Arbuz Crack.exe (PID: 1224)
- dllhost.exe (PID: 4228)
- hypercom.exe (PID: 1356)
- lsass.exe (PID: 3640)
- backgroundTaskHost.exe (PID: 6772)
Process checks computer location settings
- Arbuz Crack.exe (PID: 6976)
- crackarbuz.exe (PID: 7032)
- Arbuz Crack.exe (PID: 1224)
- hypercom.exe (PID: 1356)
The process uses the downloaded file
- WinRAR.exe (PID: 6372)
- Arbuz Crack.exe (PID: 6976)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6372)
Reads the computer name
- Arbuz Crack.exe (PID: 6976)
- crackarbuz.exe (PID: 7032)
- hypercom.exe (PID: 5536)
- Arbuz Crack.exe (PID: 1224)
- hypercom.exe (PID: 1356)
- backgroundTaskHost.exe (PID: 6772)
Drops encrypted VBS script (Microsoft Script Encoder)
- wscript.exe (PID: 7160)
The sample compiled with english language support
- crackarbuz.exe (PID: 7032)
- hypercom.exe (PID: 7160)
- hypercom.exe (PID: 5536)
- hypercom.exe (PID: 1356)
Disables trace logs
- hypercom.exe (PID: 5536)
Reads the machine GUID from the registry
- hypercom.exe (PID: 5536)
- dllhost.exe (PID: 4228)
- hypercom.exe (PID: 1356)
Reads Environment values
- Registry.exe (PID: 3080)
- hypercom.exe (PID: 5536)
- lsass.exe (PID: 540)
- hypercom.exe (PID: 7160)
Checks proxy server information
- hypercom.exe (PID: 7160)
Reads security settings of Internet Explorer
- cscript.exe (PID: 6332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 256 |
| UncompressedSize: | 362 |
| OperatingSystem: | Win32 |
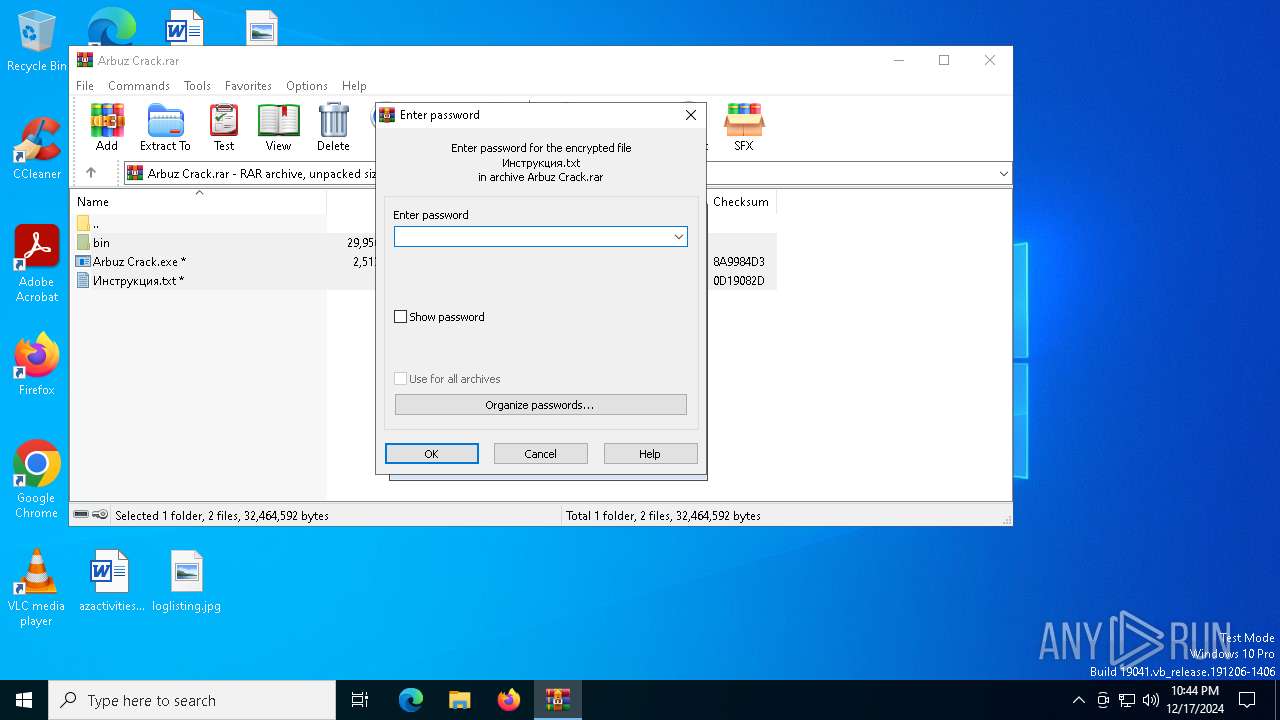
| ArchivedFileName: | Инструкция.txt |
Total processes
260
Monitored processes
134
Malicious processes
10
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Users\admin\AppData\Local\Temp\crackarbuz.exe" | C:\Users\admin\AppData\Local\Temp\crackarbuz.exe | — | Arbuz Crack.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 10 Modules
| |||||||||||||||
| 204 | schtasks.exe /create /tn "csrssc" /sc MINUTE /mo 10 /tr "'C:\Windows\Registration\CRMLog\csrss.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | cscript msgbox.vbs | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 536 | schtasks.exe /create /tn "SystemSettingsS" /sc MINUTE /mo 9 /tr "'C:\Users\admin\.ms-ad\SystemSettings.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | "C:\Users\admin\Desktop\bin\lsass.exe" | C:\Users\admin\Desktop\bin\lsass.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 556 | schtasks.exe /create /tn "RuntimeBroker" /sc ONLOGON /tr "'C:\Users\Default\Downloads\RuntimeBroker.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | schtasks.exe /create /tn "backgroundTaskHostb" /sc MINUTE /mo 11 /tr "'C:\Users\admin\OneDrive\backgroundTaskHost.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 836 | schtasks.exe /create /tn "SystemSettings" /sc ONLOGON /tr "'C:\Users\admin\.ms-ad\SystemSettings.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | schtasks.exe /create /tn "fontdrvhostf" /sc MINUTE /mo 7 /tr "'C:\Users\Public\Downloads\fontdrvhost.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | schtasks.exe /create /tn "RuntimeBrokerR" /sc MINUTE /mo 12 /tr "'C:\Users\Public\Videos\RuntimeBroker.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 060
Read events
19 999
Write events
61
Delete events
0
Modification events
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Arbuz Crack.rar | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6976) Arbuz Crack.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
Executable files
37
Suspicious files
1
Text files
42
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
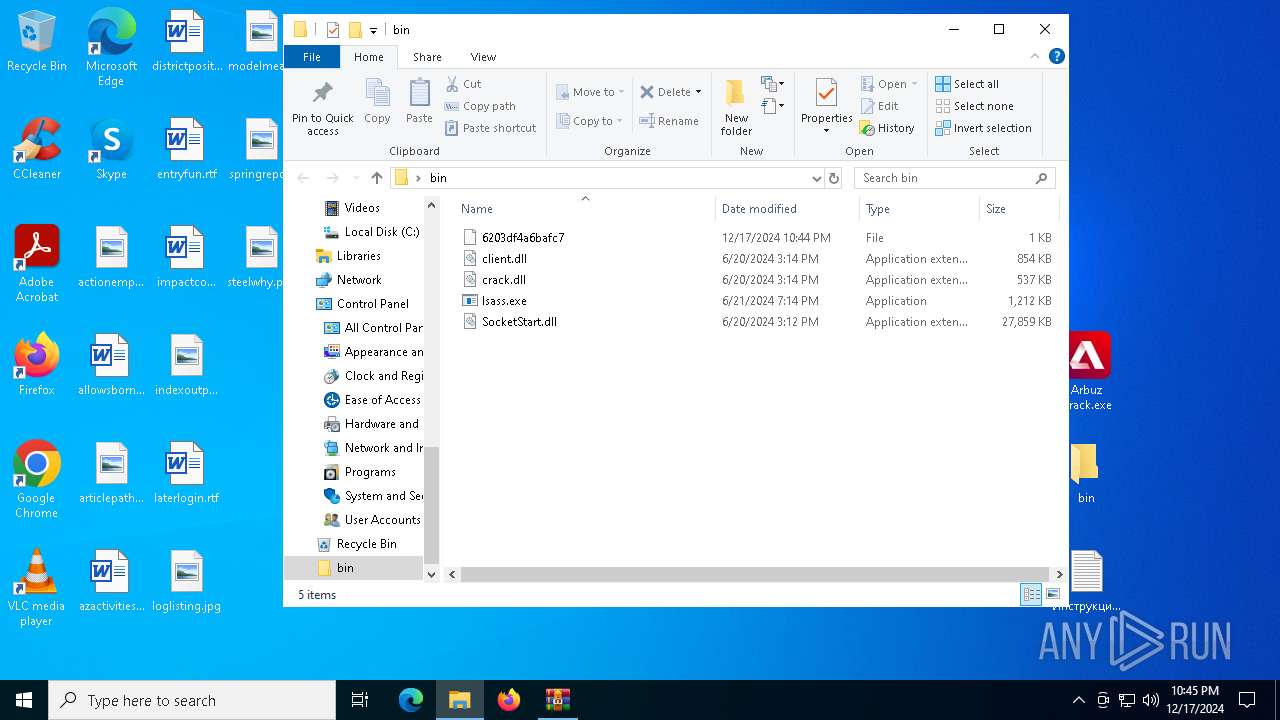
| 6372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6372.27080\bin\SocketStart.dll | — | |
MD5:— | SHA256:— | |||
| 6372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6372.27080\bin\client.dll | text | |
MD5:143FE4754478E1683A1C07F3AC172C58 | SHA256:DC18263FE54120CE926EDC80CFEB1F91B92195089805C74E7770A5EA5E633432 | |||
| 7032 | crackarbuz.exe | C:\Users\admin\AppData\Roaming\comcontainerComponentWinnet\vIEM9XUNGMaUbDtMx1GwS.vbe | vbe | |
MD5:73BB0981A4A659DD6E9A28CBDD83E7D7 | SHA256:B3154D694AF513BC75EB45BE582E260F5562E3FF5D20A6AFB89F5F7D9A1BB527 | |||
| 6976 | Arbuz Crack.exe | C:\Users\admin\AppData\Local\Temp\crackarbuz.exe | executable | |
MD5:E9FD04B3D31EB351AFABD6D33D8A5EC0 | SHA256:F29B77B47AB380EE2B677363C4BBBDB804371B1118A879289236C41F61E5AF98 | |||
| 6372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6372.27080\Инструкция.txt | text | |
MD5:0B66E24306DF19DC96E3293914BA62E8 | SHA256:663501242C04E6DADDB173B0F21A003039A2782D58C70C09AB2A13D4A557C563 | |||
| 6372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6372.27080\bin\crack.dll | text | |
MD5:61F5338CB909C8A1BF15AF306AF8BC9F | SHA256:5C1029BFF5B4FDCE53C66F1701F5D50E9AB8F8527E463FDBCEF40CEA9937A95D | |||
| 6372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6372.27080\Arbuz Crack.exe | executable | |
MD5:17EC33022F441D1988C519881AFF364F | SHA256:9B7739BAB52B1A8757AA22AA1F876370D870E7A5E9FFBE909079A8854C82ECD6 | |||
| 5536 | hypercom.exe | C:\Users\Default\Links\886983d96e3d3e | text | |
MD5:27AC50F8F672A5060755873AF1750950 | SHA256:25F44EBCF3B9974183D1A3C379C2EF2944C783D99D6D09F9DD88B740F0C8FC87 | |||
| 5536 | hypercom.exe | C:\Users\Default\Links\csrss.exe | executable | |
MD5:D0F2C7B9C27C4A6AD43296D52CDA8F52 | SHA256:B47E3C1183E2840D6A24B97048750B8520552F3A83C29045C207EA8520137D22 | |||
| 5536 | hypercom.exe | C:\Users\Public\Downloads\fontdrvhost.exe | executable | |
MD5:D0F2C7B9C27C4A6AD43296D52CDA8F52 | SHA256:B47E3C1183E2840D6A24B97048750B8520552F3A83C29045C207EA8520137D22 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
41
DNS requests
20
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5536 | hypercom.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6552 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6764 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6764 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1356 | hypercom.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
7160 | hypercom.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
3080 | Registry.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1016 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 104.126.37.144:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ip-api.com |
| shared |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2192 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
5536 | hypercom.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
5536 | hypercom.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
3080 | Registry.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
3080 | Registry.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
7160 | hypercom.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
7160 | hypercom.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
4228 | dllhost.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
4228 | dllhost.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |