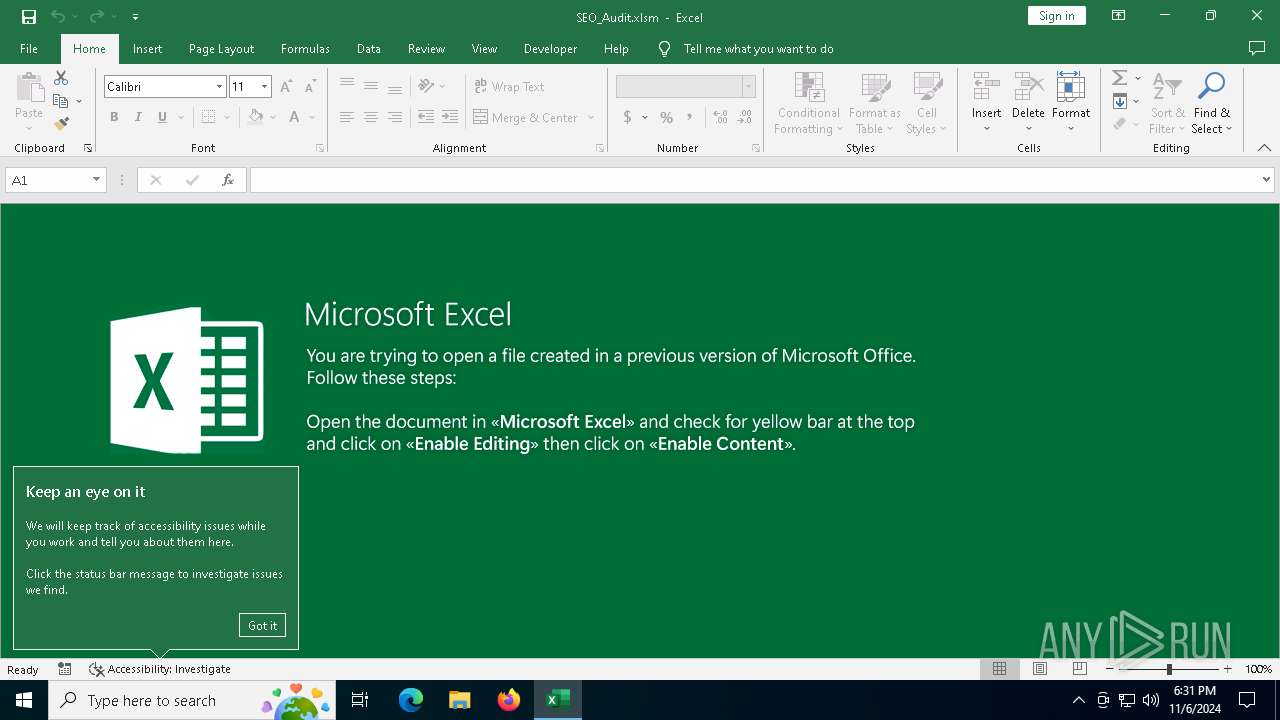
| File name: | SEO_Audit.xlsm |
| Full analysis: | https://app.any.run/tasks/da5b76cc-107d-4189-8162-5463465256f9 |
| Verdict: | Malicious activity |
| Analysis date: | November 06, 2024, 18:31:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | 9064815FCEE9A3331C62D8518E021A1B |
| SHA1: | D566580664D4E44F43692A7AF2697BEBE75D4EE4 |
| SHA256: | E5A49AC33BA1B3566DF1640B0890E00E0AB0A3F3C734273F4CF4F815F4222A47 |
| SSDEEP: | 3072:reRE9kogCeZ6JkjTRPnNGh2XYgiyxWPqw2:a8YvZ/lNfXYgQO |
MALICIOUS
No malicious indicators.SUSPICIOUS
Connects to the server without a host name
- DSAWcfProxy.exe (PID: 6240)
INFO
Executable content was dropped or overwritten
- msiexec.exe (PID: 4308)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlsm | | | Excel Microsoft Office Open XML Format document (with Macro) (50.8) |
|---|---|---|
| .xlsx | | | Excel Microsoft Office Open XML Format document (30) |
| .zip | | | Open Packaging Conventions container (15.4) |
| .zip | | | ZIP compressed archive (3.5) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x9cc0ec29 |
| ZipCompressedSize: | 394 |
| ZipUncompressedSize: | 1257 |
| ZipFileName: | [Content_Types].xml |
XMP
| Creator: | User |
|---|
XML
| LastModifiedBy: | PCs |
|---|---|
| CreateDate: | 2015:06:05 18:17:20Z |
| ModifyDate: | 2024:11:06 04:28:27Z |
| Application: | Microsoft Excel |
| DocSecurity: | None |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | Sheet 1 |
| Company: | - |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16.03 |
Total processes
130
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4308 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6240 | "C:\Persistent\DSAWcfProxy.exe" | C:\Persistent\DSAWcfProxy.exe | msiexec.exe | ||||||||||||
User: admin Company: AutoHotkey Foundation LLC Integrity Level: MEDIUM Description: AutoHotkey Unicode 32-bit Version: 1.1.37.02 Modules
| |||||||||||||||
| 6680 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" C:\Users\admin\AppData\Local\Temp\SEO_Audit.xlsm | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
9 813
Read events
9 539
Write events
247
Delete events
27
Modification events
| (PID) Process: | (6680) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (6680) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\EXCEL\6680 |
| Operation: | write | Name: | 0 |
Value: 0B0E1075EB285067E42044A52061191060D50323004696D8DDEFA18FCCED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5119834D2120965007800630065006C002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6680) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6680) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6680) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6680) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6680) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6680) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6680) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6680) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
2
Suspicious files
22
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6680 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\2865FAF8-5727-433C-86F5-47CD27924D70 | xml | |
MD5:AFB348DBC745C385309E1A4C5796971C | SHA256:7E4A245DE7E67DAE95809D6E4C99EFE70E1DD4E7E8BE2A34E520E5821BC8388B | |||
| 4308 | msiexec.exe | C:\Windows\Temp\~DF23E82B9A52DD89CE.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 6680 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:8D686E50CE51E769ED99A22F97AEBC6E | SHA256:7D48EADABAE6053BF6C863AA6E50A7E896DCAE1FBA3C5ED6BCA323EE35FD0384 | |||
| 4308 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:17663C0BD1F75117415A0A90163A8475 | SHA256:D2E701623D041D05188B658FA73DBDFDE2D091E48BB9B67FA5A1E623B6FA6DA7 | |||
| 4308 | msiexec.exe | C:\Windows\Installer\MSIF537.tmp | binary | |
MD5:CDD19EA7E60E2B70971F932B53ACAD98 | SHA256:F04C659B786266039179C68F78A68E498C3B6E99B4FC29D033CD7EEC1BB4CB46 | |||
| 6680 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | binary | |
MD5:EE5E65449CDEC4B203AF4378805DD629 | SHA256:3010E531FD62AB1323570B5DE164571BCC43D1EB20564BFE81821124B5478723 | |||
| 4308 | msiexec.exe | C:\Windows\Temp\~DFC25EE7BFA43CAC22.TMP | binary | |
MD5:17663C0BD1F75117415A0A90163A8475 | SHA256:D2E701623D041D05188B658FA73DBDFDE2D091E48BB9B67FA5A1E623B6FA6DA7 | |||
| 4308 | msiexec.exe | C:\Windows\Temp\~DF2BC60D2DA4BE8D58.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 4308 | msiexec.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\DSAWcfProxy.lnk | binary | |
MD5:2894736AE1C37C7F6FB80230DE42D6FB | SHA256:FDA708E2C453041900628457B9B8234FC5F1578E187D576948B1A5338DC9FA3D | |||
| 4308 | msiexec.exe | C:\Windows\Temp\~DF2AE88362B13BA091.TMP | binary | |
MD5:80AED0523F261D1A68FBA1153D3055AD | SHA256:5A9368A01B85779A414FCCCD9421F698E8A9FC617246311AC7CCF57DFA50125D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
27
DNS requests
13
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.23.94.24:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.23.94.24:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6240 | DSAWcfProxy.exe | GET | 404 | 66.23.227.33:80 | http://66.23.227.33/649566714-SEO | unknown | — | — | malicious |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6240 | DSAWcfProxy.exe | GET | 404 | 66.23.227.33:80 | http://66.23.227.33/649566714-SEO | unknown | — | — | malicious |
6680 | EXCEL.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6240 | DSAWcfProxy.exe | GET | 404 | 66.23.227.33:80 | http://66.23.227.33/649566714-SEO | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.23.94.24:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.23.94.24:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.200.189.225:80 | www.microsoft.com | Moratelindo Internet Exchange Point | ID | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.200.189.225:80 | www.microsoft.com | Moratelindo Internet Exchange Point | ID | whitelisted |
— | — | 2.22.240.211:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 2.22.240.211:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
alradifoods.com |
| unknown |
messaging.lifecycle.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6240 | DSAWcfProxy.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (AutoHotkey) |
6240 | DSAWcfProxy.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (AutoHotkey) |