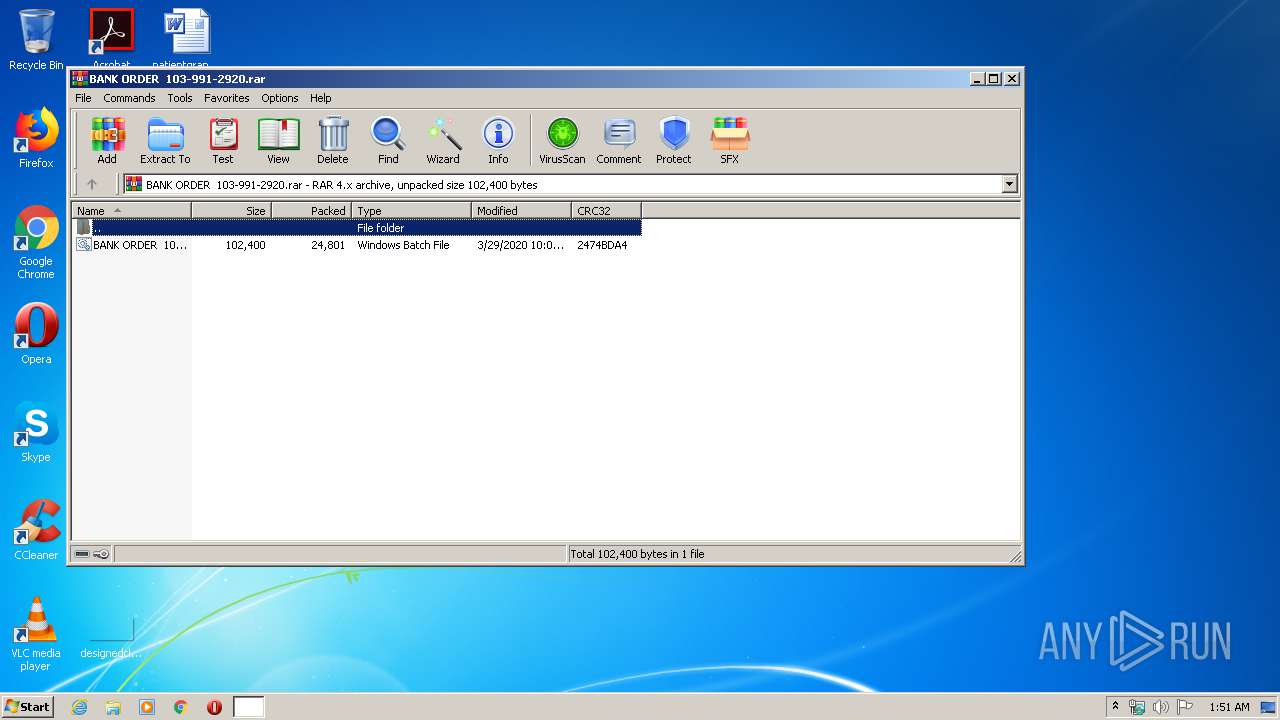
| File name: | BANK ORDER 103-991-2920.rar |
| Full analysis: | https://app.any.run/tasks/ffdd051a-479d-47a7-b03e-ea806926abb5 |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2020, 00:51:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 4088AA700B9AAB0EA9A58188542AB0A5 |
| SHA1: | 00CF014FC4087DA6E203DD9E224C6EFFB07A365F |
| SHA256: | E584D5ABD2319076D8FD4D7BB7AC09F52723CD0C2E58990EECA2C0A8F9CABC5B |
| SSDEEP: | 768:AxQrSTG3LLeOgpD0lLmKLZm3ieIyLrYgXMo:4QrR+103VmyshXMo |
MALICIOUS
Application was dropped or rewritten from another process
- BANK ORDER 103-991-2920.bat (PID: 564)
- BANK ORDER 103-991-2920.bat (PID: 3980)
Changes settings of System certificates
- BANK ORDER 103-991-2920.bat (PID: 3980)
SUSPICIOUS
Suspicious files were dropped or overwritten
- WinRAR.exe (PID: 3092)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3092)
Starts application with an unusual extension
- WinRAR.exe (PID: 3092)
- BANK ORDER 103-991-2920.bat (PID: 564)
Application launched itself
- BANK ORDER 103-991-2920.bat (PID: 564)
Reads Internet Cache Settings
- BANK ORDER 103-991-2920.bat (PID: 3980)
Creates files in the user directory
- BANK ORDER 103-991-2920.bat (PID: 3980)
Adds / modifies Windows certificates
- BANK ORDER 103-991-2920.bat (PID: 3980)
INFO
Reads settings of System Certificates
- BANK ORDER 103-991-2920.bat (PID: 3980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 24855 |
|---|---|
| UncompressedSize: | 102400 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2020:03:29 22:04:04 |
| PackingMethod: | Normal |
| ArchivedFileName: | BANK ORDER 103-991-2920.bat |
Total processes
37
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 564 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa3092.21532\BANK ORDER 103-991-2920.bat" | C:\Users\admin\AppData\Local\Temp\Rar$DIa3092.21532\BANK ORDER 103-991-2920.bat | — | WinRAR.exe | |||||||||||
User: admin Company: WONderware Integrity Level: MEDIUM Description: term Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 3092 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\BANK ORDER 103-991-2920.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3980 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa3092.21532\BANK ORDER 103-991-2920.bat" | C:\Users\admin\AppData\Local\Temp\Rar$DIa3092.21532\BANK ORDER 103-991-2920.bat | BANK ORDER 103-991-2920.bat | ||||||||||||
User: admin Company: WONderware Integrity Level: MEDIUM Description: term Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
4 024
Read events
454
Write events
2 383
Delete events
1 187
Modification events
| (PID) Process: | (3092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3092) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\BANK ORDER 103-991-2920.rar | |||
| (PID) Process: | (3092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3092) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (3092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
1
Suspicious files
4
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3980 | BANK ORDER 103-991-2920.bat | C:\Users\admin\AppData\Local\Temp\CabD6E0.tmp | — | |
MD5:— | SHA256:— | |||
| 3980 | BANK ORDER 103-991-2920.bat | C:\Users\admin\AppData\Local\Temp\TarD6E1.tmp | — | |
MD5:— | SHA256:— | |||
| 3980 | BANK ORDER 103-991-2920.bat | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CFE86DBBE02D859DC92F1E17E0574EE8_46766FC45507C0B9E264E4C18BC7288B | der | |
MD5:— | SHA256:— | |||
| 3092 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3092.21532\BANK ORDER 103-991-2920.bat | executable | |
MD5:— | SHA256:— | |||
| 3980 | BANK ORDER 103-991-2920.bat | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BE8B021F9E811DFC8C8A28572A17C05A_0B97942EE72A6E3F514E8E84F294CC72 | binary | |
MD5:— | SHA256:— | |||
| 3980 | BANK ORDER 103-991-2920.bat | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BE8B021F9E811DFC8C8A28572A17C05A_0B97942EE72A6E3F514E8E84F294CC72 | der | |
MD5:— | SHA256:— | |||
| 3980 | BANK ORDER 103-991-2920.bat | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CFE86DBBE02D859DC92F1E17E0574EE8_46766FC45507C0B9E264E4C18BC7288B | binary | |
MD5:— | SHA256:— | |||
| 3980 | BANK ORDER 103-991-2920.bat | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\U2815OK4.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3980 | BANK ORDER 103-991-2920.bat | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDL%2FQslYWVuogIAAAAAXGdc | US | der | 472 b | whitelisted |
3980 | BANK ORDER 103-991-2920.bat | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3980 | BANK ORDER 103-991-2920.bat | 172.217.21.206:443 | drive.google.com | Google Inc. | US | whitelisted |
3980 | BANK ORDER 103-991-2920.bat | 172.217.16.195:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
drive.google.com |
| shared |
ocsp.pki.goog |
| whitelisted |