| File name: | RVTools4.4.5.exe |
| Full analysis: | https://app.any.run/tasks/a37f3d7a-b313-4547-8d96-b1747d9723de |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2023, 21:44:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 7EA554EB25CC70969B6FB68A8E6E2523 |
| SHA1: | 9200E4D5A277A8932D8FF4BA3F50A8A326BECF7E |
| SHA256: | E5750BA72164E3EB1E4052D3F1A20EA333A4E9A9CC796F1FE7D1151D01BF018E |
| SSDEEP: | 98304:5lZ4zuzwgxwR42IlR8kQWraC+oXDL1RyUr5R+nGF0qvsijt70/Bx1vT/DY940vXo:Z0L7rjUbYYLkL |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 2336)
SUSPICIOUS
Checks Windows Trust Settings
- msiexec.exe (PID: 2336)
Process drops legitimate windows executable
- msiexec.exe (PID: 2532)
- msiexec.exe (PID: 2336)
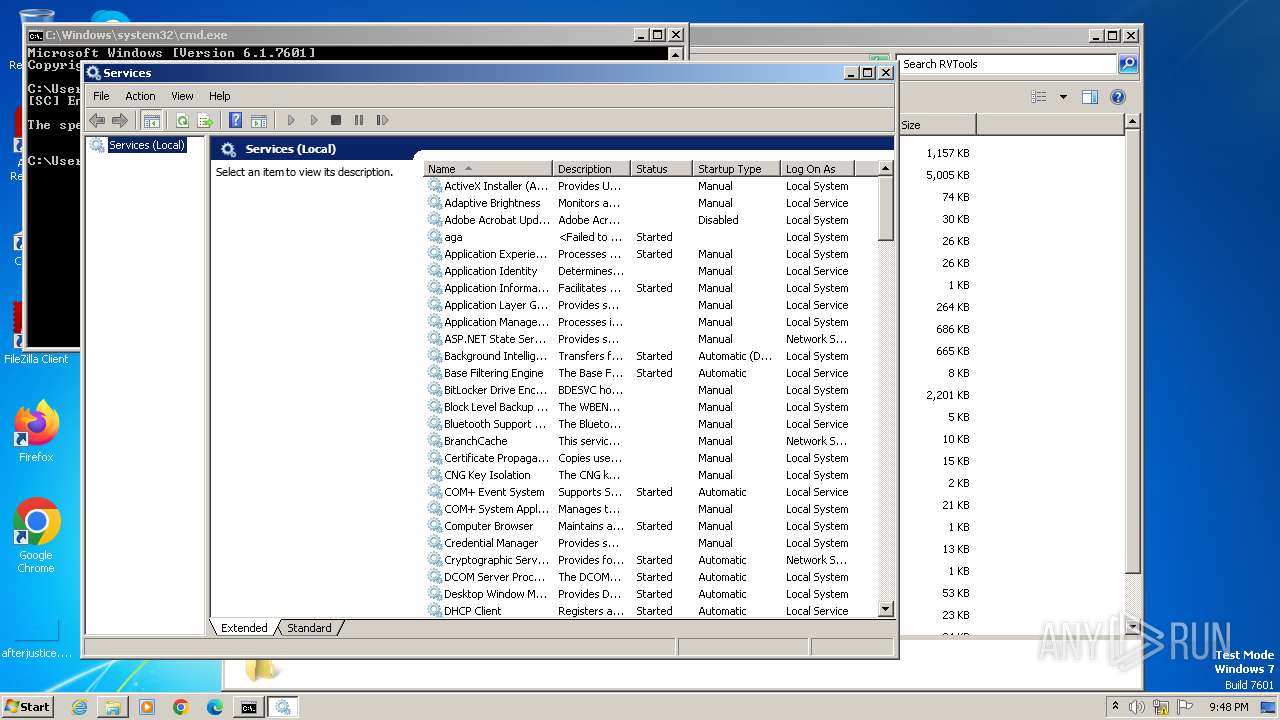
Executes as Windows Service
- VSSVC.exe (PID: 2716)
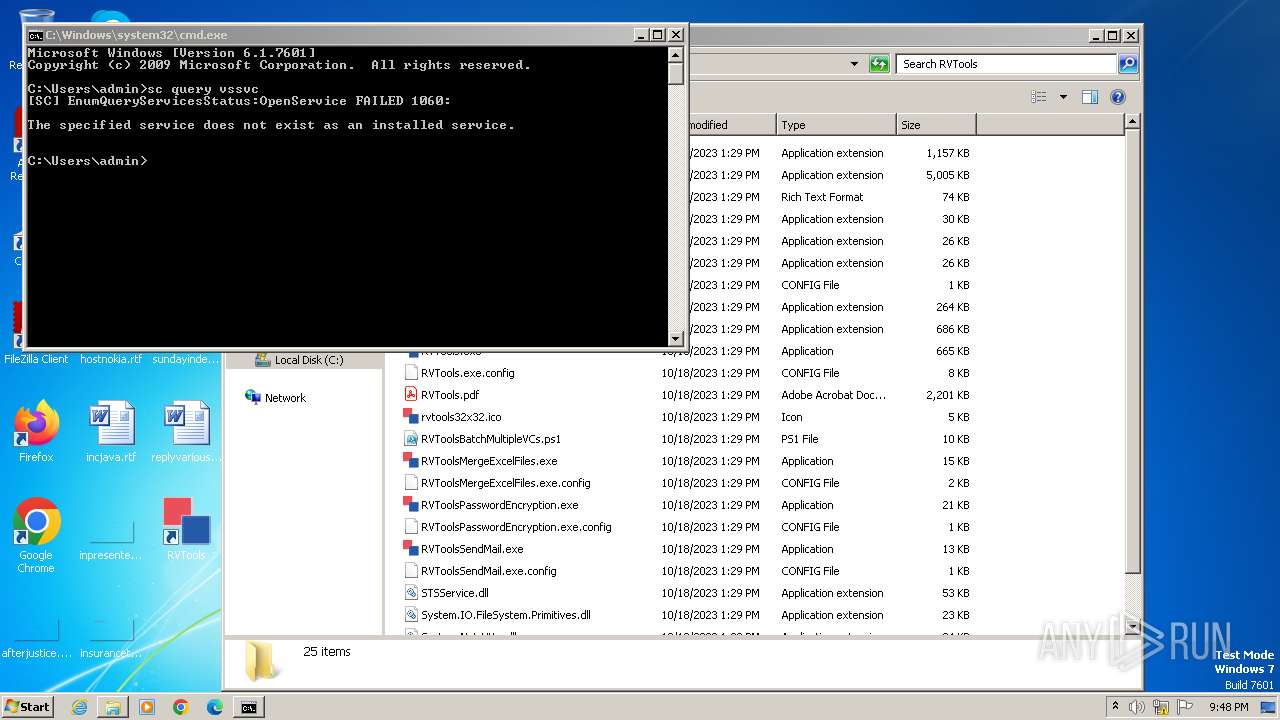
Starts SC.EXE for service management
- cmd.exe (PID: 1660)
Reads Microsoft Outlook installation path
- mmc.exe (PID: 2480)
Reads the Internet Settings
- mmc.exe (PID: 2480)
Adds/modifies Windows certificates
- msiexec.exe (PID: 2532)
Reads Internet Explorer settings
- mmc.exe (PID: 2480)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 2464)
- RVTools4.4.5.exe (PID: 1152)
- msiexec.exe (PID: 3304)
- msiexec.exe (PID: 1860)
- msiexec.exe (PID: 2336)
Checks supported languages
- RVTools4.4.5.exe (PID: 1152)
- wmpnscfg.exe (PID: 2464)
- msiexec.exe (PID: 3304)
- msiexec.exe (PID: 1860)
- msiexec.exe (PID: 2336)
Creates files in the program directory
- RVTools4.4.5.exe (PID: 1152)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2336)
- msiexec.exe (PID: 1860)
- msiexec.exe (PID: 3304)
Application launched itself
- msiexec.exe (PID: 2336)
Drops the executable file immediately after the start
- msiexec.exe (PID: 2532)
Create files in a temporary directory
- msiexec.exe (PID: 1860)
- msiexec.exe (PID: 3304)
- msiexec.exe (PID: 2336)
Manual execution by a user
- cmd.exe (PID: 1660)
- explorer.exe (PID: 3660)
- mmc.exe (PID: 2512)
- mmc.exe (PID: 2480)
Checks proxy server information
- mmc.exe (PID: 2480)
Creates files or folders in the user directory
- mmc.exe (PID: 2480)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 23:57:46+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 186880 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x352d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.4.5.0 |
| ProductVersionNumber: | 4.4.5.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | RVTools |
| FileDescription: | RVTools 4.4.5.0 |
| FileVersion: | 4.4.5.0 |
| InternalName: | RVTools 4.4.5.0.msi |
| LegalCopyright: | RVTools |
| OriginalFileName: | RVTools 4.4.5.0.msi |
| ProductName: | RVTools 4.4.5.0 |
| ProductVersion: | 4.4.5.0 |
Total processes
60
Monitored processes
13
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1152 | "C:\Users\admin\AppData\Local\Temp\RVTools4.4.5.exe" | C:\Users\admin\AppData\Local\Temp\RVTools4.4.5.exe | explorer.exe | ||||||||||||
User: admin Company: RVTools Integrity Level: HIGH Description: RVTools 4.4.5.0 Exit code: 0 Version: 4.4.5.0 Modules
| |||||||||||||||
| 1660 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1860 | C:\Windows\system32\MsiExec.exe -Embedding 381BDEFCDD49B69F3286B6F3A75FD0A7 C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1996 | "C:\Users\admin\AppData\Local\Temp\RVTools4.4.5.exe" | C:\Users\admin\AppData\Local\Temp\RVTools4.4.5.exe | — | explorer.exe | |||||||||||
User: admin Company: RVTools Integrity Level: MEDIUM Description: RVTools 4.4.5.0 Exit code: 3221226540 Version: 4.4.5.0 Modules
| |||||||||||||||
| 2040 | sc query vssvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2336 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2464 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2480 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\services.msc" | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2512 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\services.msc" | C:\Windows\System32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2532 | msiexec /i "C:\ProgramData\Microsoft\NodejsToolsVsix\RVTools.msi" | C:\Windows\System32\msiexec.exe | — | RVTools4.4.5.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
12 414
Read events
12 349
Write events
55
Delete events
10
Modification events
| (PID) Process: | (2532) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2532) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\503006091D97D4F5AE39F7CBE7927D7D652D3431 |
| Operation: | write | Name: | Blob |
Value: 7E000000010000000800000000C001B39667D601530000000100000041000000303F3020060A6086480186FA6C0A010230123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C019000000010000001000000091FAD483F14848A8A69B18B805CDBB3A6200000001000000200000006DC47172E01CBCB0BF62580D895FE2B8AC9AD4F873801E0C10B9C837D21EB1770B000000010000001E00000045006E00740072007500730074002000280032003000340038002900000014000000010000001400000055E481D11180BED889B908A331F9A1240916B9701D0000000100000010000000E871723E266F38AF5D49CDA2A502669C030000000100000014000000503006091D97D4F5AE39F7CBE7927D7D652D34310F0000000100000014000000327FC447408DE9BF596F83D4B2FA4B8E3E7097D8090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703087F000000010000002C000000302A060A2B0601040182370A030406082B0601050507030506082B0601050507030606082B0601050507030720000000010000002E0400003082042A30820312A00302010202043863DEF8300D06092A864886F70D01010505003081B431143012060355040A130B456E74727573742E6E65743140303E060355040B14377777772E656E74727573742E6E65742F4350535F3230343820696E636F72702E206279207265662E20286C696D697473206C6961622E2931253023060355040B131C286329203139393920456E74727573742E6E6574204C696D69746564313330310603550403132A456E74727573742E6E65742043657274696669636174696F6E20417574686F7269747920283230343829301E170D3939313232343137353035315A170D3239303732343134313531325A3081B431143012060355040A130B456E74727573742E6E65743140303E060355040B14377777772E656E74727573742E6E65742F4350535F3230343820696E636F72702E206279207265662E20286C696D697473206C6961622E2931253023060355040B131C286329203139393920456E74727573742E6E6574204C696D69746564313330310603550403132A456E74727573742E6E65742043657274696669636174696F6E20417574686F726974792028323034382930820122300D06092A864886F70D01010105000382010F003082010A0282010100AD4D4BA91286B2EAA320071516642A2B4BD1BF0B4A4D8EED8076A567B77840C07342C868C0DB532BDD5EB8769835938B1A9D7C133A0E1F5BB71ECFE524141EB181A98D7DB8CC6B4B03F1020CDCABA54024007F7494A19D0829B3880BF587779D55CDE4C37ED76A64AB851486955B9732506F3DC8BA660CE3FCBDB849C176894919FDC0A8BD89A3672FC69FBC711960B82DE92CC99076667B94E2AF78D665535D3CD69CB2CF2903F92FA450B2D448CE0532558AFDB2644C0EE4980775DB7FDFB9085560853029F97B48A46986E3353F1E865D7A7A15BDEF008E1522541700902693BC0E496891BFF847D39D9542C10E4DDF6F26CFC3182162664370D6D5C007E10203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E0416041455E481D11180BED889B908A331F9A1240916B970300D06092A864886F70D010105050003820101003B9B8F569B30E753997C7A79A74D97D7199590FB061FCA337C46638F966624FA401B2127CAE67273F24FFE3199FDC80C4C6853C680821398FAB6ADDA5D3DF1CE6EF6151194820CEE3F95AF11AB0FD72FDE1F038F572C1EC9BB9A1A4495EB184FA61FCD7D57102F9B04095A84B56ED81D3AE1D69ED16C795E791C14C5E3D04C933B653CEDDF3DBEA6E5951AC3B519C3BD5E5BBBFF23EF6819CB1293275C032D6F30D01EB61AACDE5AF7D1AAA827A6FE7981C479993357BA12B0A9E0426C93CA56DEFE6D840B088B7E8DEAD79821C6F3E73C792F5E9CD14C158DE1EC2237CC9A430B97DC80908DB3679B6F48081556CFBFF12B7C5E9A76E95990C57C8335116551 | |||
| (PID) Process: | (2532) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\503006091D97D4F5AE39F7CBE7927D7D652D3431 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000EE2931BC327E9AE6E8B5F751B43471907F000000010000002C000000302A060A2B0601040182370A030406082B0601050507030506082B0601050507030606082B06010505070307090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F0000000100000014000000327FC447408DE9BF596F83D4B2FA4B8E3E7097D8030000000100000014000000503006091D97D4F5AE39F7CBE7927D7D652D34311D0000000100000010000000E871723E266F38AF5D49CDA2A502669C14000000010000001400000055E481D11180BED889B908A331F9A1240916B9700B000000010000001E00000045006E0074007200750073007400200028003200300034003800290000006200000001000000200000006DC47172E01CBCB0BF62580D895FE2B8AC9AD4F873801E0C10B9C837D21EB17719000000010000001000000091FAD483F14848A8A69B18B805CDBB3A530000000100000041000000303F3020060A6086480186FA6C0A010230123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C07E000000010000000800000000C001B39667D60120000000010000002E0400003082042A30820312A00302010202043863DEF8300D06092A864886F70D01010505003081B431143012060355040A130B456E74727573742E6E65743140303E060355040B14377777772E656E74727573742E6E65742F4350535F3230343820696E636F72702E206279207265662E20286C696D697473206C6961622E2931253023060355040B131C286329203139393920456E74727573742E6E6574204C696D69746564313330310603550403132A456E74727573742E6E65742043657274696669636174696F6E20417574686F7269747920283230343829301E170D3939313232343137353035315A170D3239303732343134313531325A3081B431143012060355040A130B456E74727573742E6E65743140303E060355040B14377777772E656E74727573742E6E65742F4350535F3230343820696E636F72702E206279207265662E20286C696D697473206C6961622E2931253023060355040B131C286329203139393920456E74727573742E6E6574204C696D69746564313330310603550403132A456E74727573742E6E65742043657274696669636174696F6E20417574686F726974792028323034382930820122300D06092A864886F70D01010105000382010F003082010A0282010100AD4D4BA91286B2EAA320071516642A2B4BD1BF0B4A4D8EED8076A567B77840C07342C868C0DB532BDD5EB8769835938B1A9D7C133A0E1F5BB71ECFE524141EB181A98D7DB8CC6B4B03F1020CDCABA54024007F7494A19D0829B3880BF587779D55CDE4C37ED76A64AB851486955B9732506F3DC8BA660CE3FCBDB849C176894919FDC0A8BD89A3672FC69FBC711960B82DE92CC99076667B94E2AF78D665535D3CD69CB2CF2903F92FA450B2D448CE0532558AFDB2644C0EE4980775DB7FDFB9085560853029F97B48A46986E3353F1E865D7A7A15BDEF008E1522541700902693BC0E496891BFF847D39D9542C10E4DDF6F26CFC3182162664370D6D5C007E10203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E0416041455E481D11180BED889B908A331F9A1240916B970300D06092A864886F70D010105050003820101003B9B8F569B30E753997C7A79A74D97D7199590FB061FCA337C46638F966624FA401B2127CAE67273F24FFE3199FDC80C4C6853C680821398FAB6ADDA5D3DF1CE6EF6151194820CEE3F95AF11AB0FD72FDE1F038F572C1EC9BB9A1A4495EB184FA61FCD7D57102F9B04095A84B56ED81D3AE1D69ED16C795E791C14C5E3D04C933B653CEDDF3DBEA6E5951AC3B519C3BD5E5BBBFF23EF6819CB1293275C032D6F30D01EB61AACDE5AF7D1AAA827A6FE7981C479993357BA12B0A9E0426C93CA56DEFE6D840B088B7E8DEAD79821C6F3E73C792F5E9CD14C158DE1EC2237CC9A430B97DC80908DB3679B6F48081556CFBFF12B7C5E9A76E95990C57C8335116551 | |||
| (PID) Process: | (2532) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\8CF427FD790C3AD166068DE81E57EFBB932272D4 |
| Operation: | write | Name: | Blob |
Value: 7E000000010000000800000000C001B39667D601530000000100000041000000303F3020060A6086480186FA6C0A010230123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0190000000100000010000000FA46CE7CBB85CFB4310075313A09EE0562000000010000002000000043DF5774B03E7FEF5FE40D931A7BEDF1BB2E6B42738C4E6D3841103D3AA7F3390B000000010000001800000045006E00740072007500730074002E006E006500740000001400000001000000140000006A72267AD01EEF7DE73B6951D46C8D9F901266AB1D0000000100000010000000521B5F4582C1DCAAE381B05E37CA2D340300000001000000140000008CF427FD790C3AD166068DE81E57EFBB932272D40F0000000100000020000000FDE5F2D9CE2026E1E10064C0A468C9F355B90ACF85BAF5CE6F52D4016837FD94090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703087F000000010000002C000000302A060A2B0601040182370A030406082B0601050507030506082B0601050507030606082B060105050703072000000001000000420400003082043E30820326A00302010202044A538C28300D06092A864886F70D01010B05003081BE310B300906035504061302555331163014060355040A130D456E74727573742C20496E632E31283026060355040B131F536565207777772E656E74727573742E6E65742F6C6567616C2D7465726D7331393037060355040B1330286329203230303920456E74727573742C20496E632E202D20666F7220617574686F72697A656420757365206F6E6C793132303006035504031329456E747275737420526F6F742043657274696669636174696F6E20417574686F72697479202D204732301E170D3039303730373137323535345A170D3330313230373137353535345A3081BE310B300906035504061302555331163014060355040A130D456E74727573742C20496E632E31283026060355040B131F536565207777772E656E74727573742E6E65742F6C6567616C2D7465726D7331393037060355040B1330286329203230303920456E74727573742C20496E632E202D20666F7220617574686F72697A656420757365206F6E6C793132303006035504031329456E747275737420526F6F742043657274696669636174696F6E20417574686F72697479202D20473230820122300D06092A864886F70D01010105000382010F003082010A0282010100BA84B672DB9E0C6BE299E93001A776EA32B895411AC9DA614E5872CFFEF68279BF7361060AA527D8B35FD3454E1C72D64E32F2728A0FF78319D06A808000451EB0C7E79ABF1257271CA3682F0A87BD6A6B0E5E65F31C77D5D4858D7021B4B332E78BA2D5863902B1B8D247CEE4C949C43BA7DEFB547D57BEF0E86EC279B23A0B55E250981632135C2F7856C1C294B3F25AE4279A9F24D7C6ECD09B2582E3CCC2C445C58C977A066B2A119FA90A6E483B6FDBD4111942F78F07BFF5535F9C3EF4172CE669AC4E324C6277EAB7E8E5BB34BC198BAE9C51E7B77EB553B13322E56DCF703C1AFAE29B67B683F48DA5AF624C4DE058AC64341203F8B68D946324A4710203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604146A72267AD01EEF7DE73B6951D46C8D9F901266AB300D06092A864886F70D01010B05000382010100799F1D96C6B6793F228D87D3870304606A6B9A2E59897311AC43D1F513FF8D392BC0F2BD4F708CA92FEA17C40B549ED41B9698333CA8AD62A20076AB59696E061D7EC4B9448D98AF12D461DB0A194647F3EBF763C1400540A5D2B7F4B59A36BFA98876880455042B9C877F1A373C7E2DA51AD8D4895ECABDAC3D6CD86DAFD5F3760FCD3B8838229D6C939AC43DBF821B653FA60F5DAAFCE5B215CAB5ADC6BC3DD084E8EA0672B04D393278BF3E119C0BA49D9A21F3F09B0B3078DBC1DC8743FEBC639ACAC5C21CC9C78DFF3B125808E6B63DEC7A2C4EFB8396CE0C3C69875473A473C293FF5110AC155401D8FC05B189A17F74839A49D7DC4E7B8A486F8B45F6 | |||
| (PID) Process: | (2532) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\8CF427FD790C3AD166068DE81E57EFBB932272D4 |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000004BE2C99196650CF40E5A9392A00AFEB27F000000010000002C000000302A060A2B0601040182370A030406082B0601050507030506082B0601050507030606082B06010505070307090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F0000000100000020000000FDE5F2D9CE2026E1E10064C0A468C9F355B90ACF85BAF5CE6F52D4016837FD940300000001000000140000008CF427FD790C3AD166068DE81E57EFBB932272D41D0000000100000010000000521B5F4582C1DCAAE381B05E37CA2D341400000001000000140000006A72267AD01EEF7DE73B6951D46C8D9F901266AB0B000000010000001800000045006E00740072007500730074002E006E0065007400000062000000010000002000000043DF5774B03E7FEF5FE40D931A7BEDF1BB2E6B42738C4E6D3841103D3AA7F339190000000100000010000000FA46CE7CBB85CFB4310075313A09EE05530000000100000041000000303F3020060A6086480186FA6C0A010230123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C07E000000010000000800000000C001B39667D6012000000001000000420400003082043E30820326A00302010202044A538C28300D06092A864886F70D01010B05003081BE310B300906035504061302555331163014060355040A130D456E74727573742C20496E632E31283026060355040B131F536565207777772E656E74727573742E6E65742F6C6567616C2D7465726D7331393037060355040B1330286329203230303920456E74727573742C20496E632E202D20666F7220617574686F72697A656420757365206F6E6C793132303006035504031329456E747275737420526F6F742043657274696669636174696F6E20417574686F72697479202D204732301E170D3039303730373137323535345A170D3330313230373137353535345A3081BE310B300906035504061302555331163014060355040A130D456E74727573742C20496E632E31283026060355040B131F536565207777772E656E74727573742E6E65742F6C6567616C2D7465726D7331393037060355040B1330286329203230303920456E74727573742C20496E632E202D20666F7220617574686F72697A656420757365206F6E6C793132303006035504031329456E747275737420526F6F742043657274696669636174696F6E20417574686F72697479202D20473230820122300D06092A864886F70D01010105000382010F003082010A0282010100BA84B672DB9E0C6BE299E93001A776EA32B895411AC9DA614E5872CFFEF68279BF7361060AA527D8B35FD3454E1C72D64E32F2728A0FF78319D06A808000451EB0C7E79ABF1257271CA3682F0A87BD6A6B0E5E65F31C77D5D4858D7021B4B332E78BA2D5863902B1B8D247CEE4C949C43BA7DEFB547D57BEF0E86EC279B23A0B55E250981632135C2F7856C1C294B3F25AE4279A9F24D7C6ECD09B2582E3CCC2C445C58C977A066B2A119FA90A6E483B6FDBD4111942F78F07BFF5535F9C3EF4172CE669AC4E324C6277EAB7E8E5BB34BC198BAE9C51E7B77EB553B13322E56DCF703C1AFAE29B67B683F48DA5AF624C4DE058AC64341203F8B68D946324A4710203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604146A72267AD01EEF7DE73B6951D46C8D9F901266AB300D06092A864886F70D01010B05000382010100799F1D96C6B6793F228D87D3870304606A6B9A2E59897311AC43D1F513FF8D392BC0F2BD4F708CA92FEA17C40B549ED41B9698333CA8AD62A20076AB59696E061D7EC4B9448D98AF12D461DB0A194647F3EBF763C1400540A5D2B7F4B59A36BFA98876880455042B9C877F1A373C7E2DA51AD8D4895ECABDAC3D6CD86DAFD5F3760FCD3B8838229D6C939AC43DBF821B653FA60F5DAAFCE5B215CAB5ADC6BC3DD084E8EA0672B04D393278BF3E119C0BA49D9A21F3F09B0B3078DBC1DC8743FEBC639ACAC5C21CC9C78DFF3B125808E6B63DEC7A2C4EFB8396CE0C3C69875473A473C293FF5110AC155401D8FC05B189A17F74839A49D7DC4E7B8A486F8B45F6 | |||
| (PID) Process: | (2336) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2336) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2336) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 72 | |||
| (PID) Process: | (2336) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008C62D6BA16B0D901C80700002C0A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2336) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 400000000000000064514ABC16B0D901C80700002C0A0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
20
Suspicious files
11
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1152 | RVTools4.4.5.exe | C:\ProgramData\Microsoft\NodejsToolsVsix\RVTools.msi | — | |
MD5:— | SHA256:— | |||
| 2336 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2336 | msiexec.exe | C:\Windows\Installer\216e1b.msi | — | |
MD5:— | SHA256:— | |||
| 2532 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIA40.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 2532 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIA9F.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 2336 | msiexec.exe | C:\Windows\Installer\MSI6F92.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 1860 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CFGA8E.tmp | xml | |
MD5:C0D6E4A03F64551DEC4FB14D43A77763 | SHA256:53E7665DB8CDCF73BA27509B89B0BA2AB70AAA483FD2A211B2BBAEE69A593278 | |||
| 2336 | msiexec.exe | C:\Windows\Installer\216e1c.ipi | binary | |
MD5:3C9C456B49AB95663FC8A1686F23489E | SHA256:F5D14655C7C3C1D399906570AEF5533AAE621A9EF5F58E696DE7644F82583CBD | |||
| 2336 | msiexec.exe | C:\Program Files\Dell\RVTools\RVToolsPasswordEncryption.exe | executable | |
MD5:E5C227A189F08B44885808FEB27E278E | SHA256:C05360E8F3333BB66CD79D30C80FF4E08170990563B50A3156C24329F255C19C | |||
| 3304 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CFG6FEF.tmp | xml | |
MD5:C0D6E4A03F64551DEC4FB14D43A77763 | SHA256:53E7665DB8CDCF73BA27509B89B0BA2AB70AAA483FD2A211B2BBAEE69A593278 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |