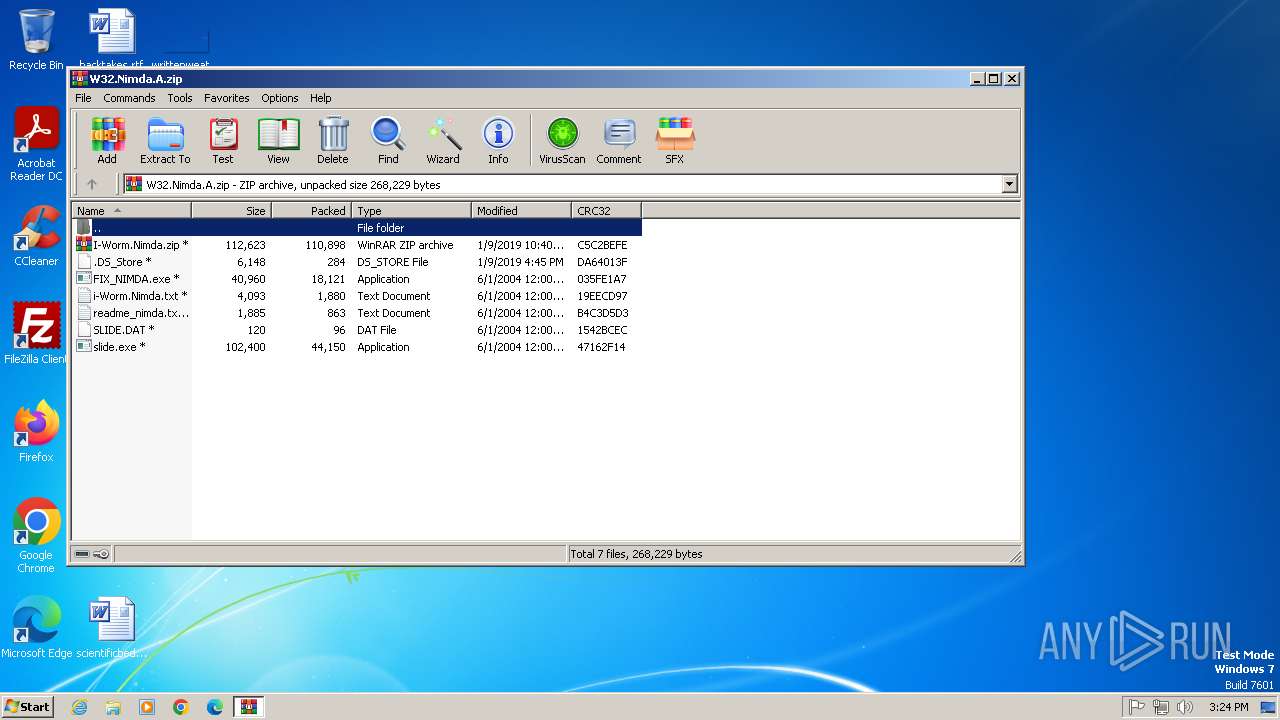
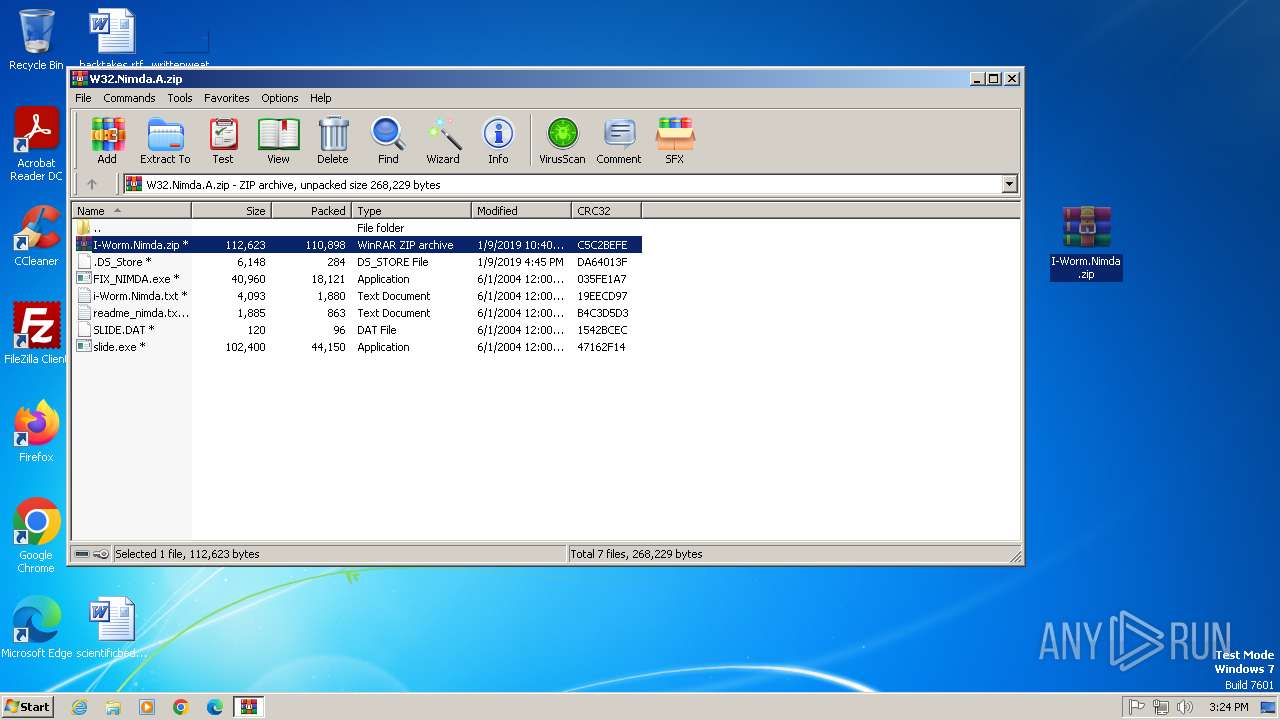
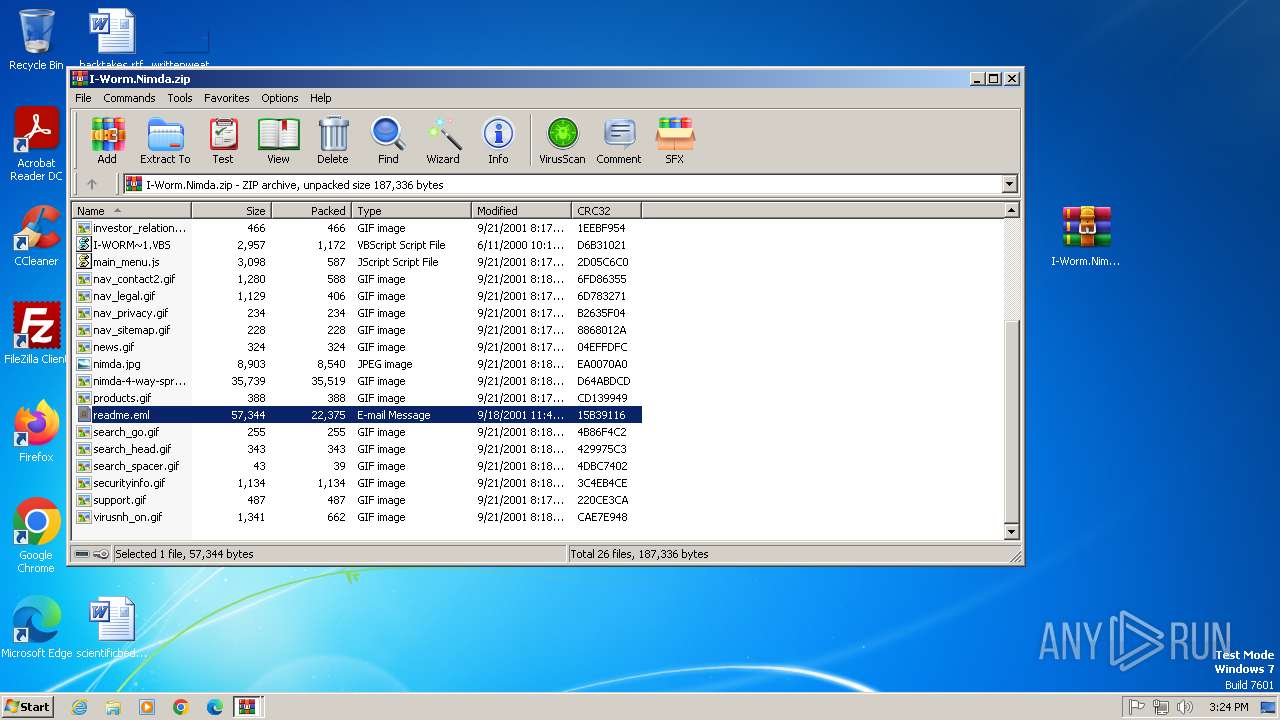
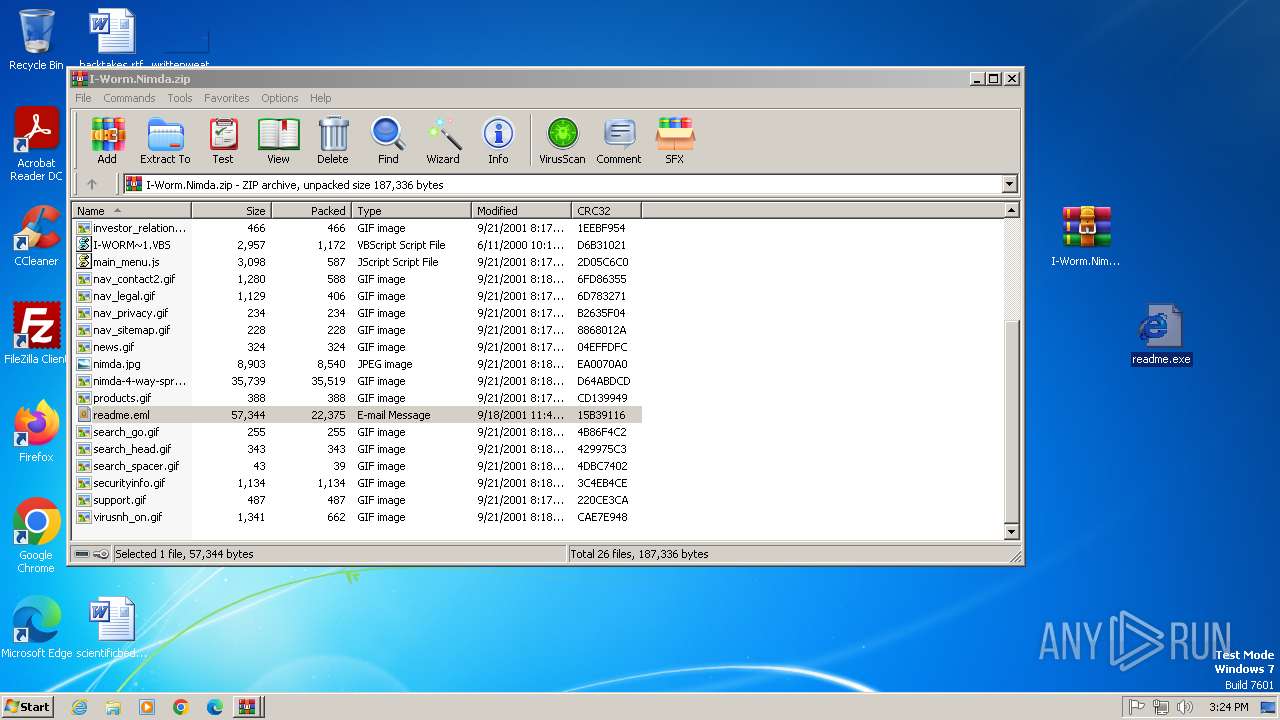
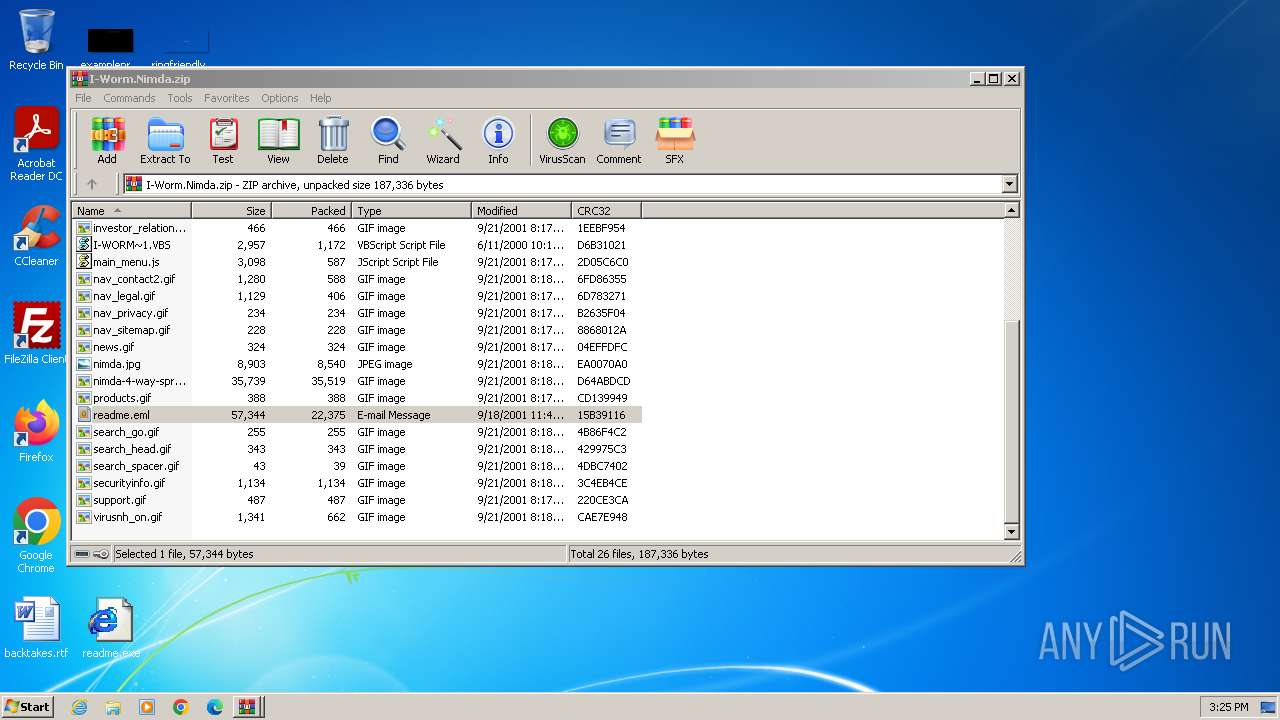
| File name: | W32.Nimda.A.zip |
| Full analysis: | https://app.any.run/tasks/37eacba8-348a-43e6-b73f-1a4cf1482d7d |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2025, 14:24:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | B62632C8E6AAFA05A07CAD52B2E25AA5 |
| SHA1: | 35C626A3513F8866095F891F69C593DE6D87EBD2 |
| SHA256: | E56E79F9DC8752E11B66C3DEA5282E835EF280A46A2B5D98AF19222D11B72767 |
| SSDEEP: | 6144:F5+YTd3QOMgyjGyrQb+MU5opgJcvd7JEZ:F5+YhogyjGK4ZqWgZ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2784)
Application was injected by another process
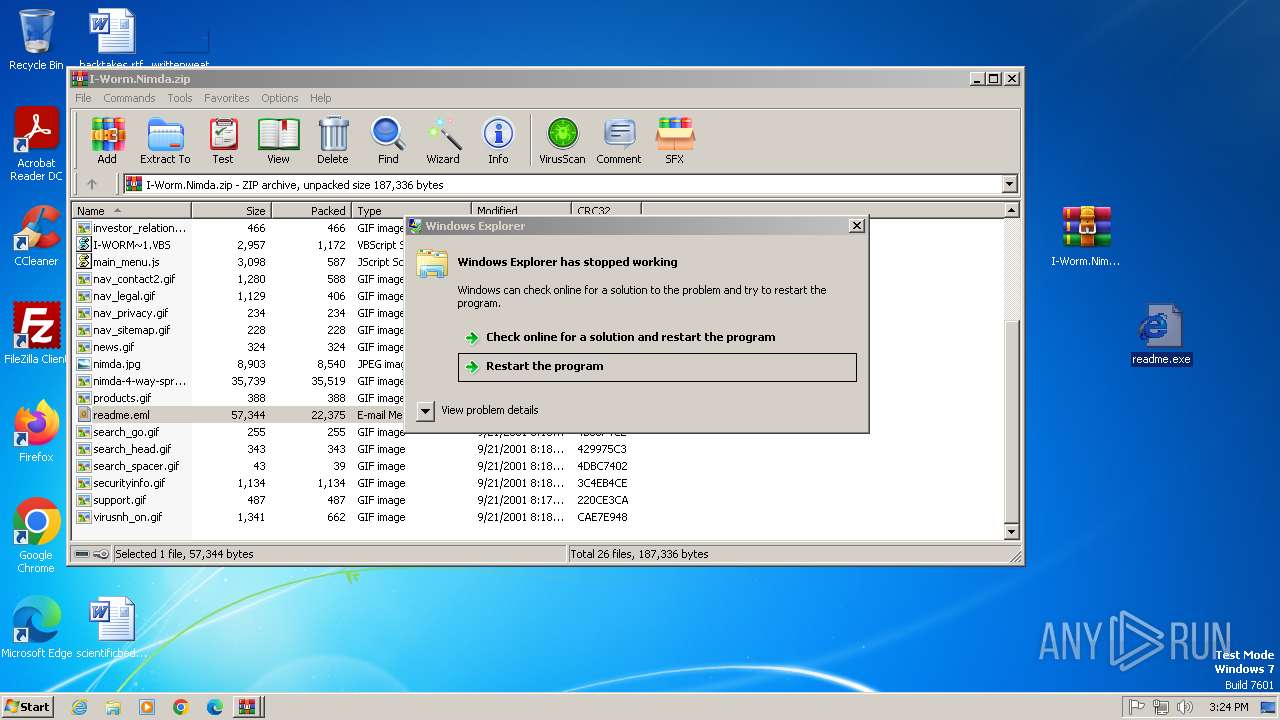
- explorer.exe (PID: 1452)
Runs injected code in another process
- mepBFC1.tmp.exe (PID: 2816)
SUSPICIOUS
Detected use of alternative data streams (AltDS)
- readme.exe (PID: 3464)
- mepBFC1.tmp.exe (PID: 2816)
Starts itself from another location
- readme.exe (PID: 3464)
Executable content was dropped or overwritten
- readme.exe (PID: 3464)
- explorer.exe (PID: 1452)
- mepBFC1.tmp.exe (PID: 2816)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 1452)
Manual execution by a user
- WinRAR.exe (PID: 3184)
- readme.exe (PID: 3464)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3184)
Reads the Internet Settings
- explorer.exe (PID: 1452)
Create files in a temporary directory
- readme.exe (PID: 3464)
- mepBFC1.tmp.exe (PID: 2816)
Checks supported languages
- readme.exe (PID: 3464)
- mepBFC1.tmp.exe (PID: 2816)
Reads the computer name
- mepBFC1.tmp.exe (PID: 2816)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:01:09 16:45:30 |
| ZipCRC: | 0xda64013f |
| ZipCompressedSize: | 284 |
| ZipUncompressedSize: | 6148 |
| ZipFileName: | .DS_Store |
Total processes
43
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1452 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 255 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2784 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\W32.Nimda.A.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2816 | C:\Users\admin\AppData\Local\Temp\mepBFC1.tmp.exe -dontrunold | C:\Users\admin\AppData\Local\Temp\mepBFC1.tmp.exe | readme.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3184 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\I-Worm.Nimda.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3464 | "C:\Users\admin\Desktop\readme.exe" | C:\Users\admin\Desktop\readme.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
8 819
Read events
8 750
Write events
69
Delete events
0
Modification events
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1452) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000A1A559CD5EBA54449F9B23534AC7F42F00000000020000000000106600000001000020000000588A5629DB60DA02DB7614987AF6435DDFE1957D2742BD90EECEAC977DD2B03F000000000E80000000020000200000009941A314A30B183B1EC0A19BA61A4CAC71F3635D9825732B9844DE4CAB874E3A30000000ABE84BCB32942F90785226CA38B56EAEED99D70C759DB91F3FAFFFD04CCE06736084862E6B8C4D1BE4E0EDF59F25526140000000807FD493B989A57428858FAF1C988FF6F5676514663945DF6A3FF4A82D67419536A79935C4CB57EBC703294EF51E7842DC6CC401C8813018AFE9CA12C26DDD7F | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\W32.Nimda.A.zip | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
10
Suspicious files
5
Text files
1
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2784 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2784.37415\I-Worm.Nimda.zip | compressed | |
MD5:844855B2EC58F20718CFF30D874AB43E | SHA256:70E37EA05B1D89E37E04B1C2CE98731E65B6C37CF718DC72A109D862CA36CC2A | |||
| 1452 | explorer.exe | C:\Users\admin\Desktop\I-Worm.Nimda.zip | compressed | |
MD5:844855B2EC58F20718CFF30D874AB43E | SHA256:70E37EA05B1D89E37E04B1C2CE98731E65B6C37CF718DC72A109D862CA36CC2A | |||
| 1452 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | automaticdestinations-ms | |
MD5:71CC3C9F04AD2CD0E6BB210979300765 | SHA256:7718E46C8E78C29BB8AC33B44DD0922033522F55F13B7A61EA7D573FF0640D50 | |||
| 2816 | mepBFC1.tmp.exe | C:\Users\admin\AppData\Local\Temp\mepBFF0.tmp.exe:OECustomProperty | binary | |
MD5:8243E382810CB1DF88D17BB47C998B8E | SHA256:7DFD2BAAA67EE5473604683461E100D6EAD5702581728D211516CD95CC17345B | |||
| 1452 | explorer.exe | C:\Users\admin\Desktop\readme.exe | executable | |
MD5:7A9527AFDDA4179B10E5465E93D0F3AA | SHA256:C4A60096AD81F6E4CE7412F4873465DE408EAB69D7AC35B9AF9B0B1A4CCD3EEA | |||
| 3464 | readme.exe | C:\Users\admin\AppData\Local\Temp\mepBFC1.tmp.exe | executable | |
MD5:7A9527AFDDA4179B10E5465E93D0F3AA | SHA256:C4A60096AD81F6E4CE7412F4873465DE408EAB69D7AC35B9AF9B0B1A4CCD3EEA | |||
| 2816 | mepBFC1.tmp.exe | C:\Users\admin\AppData\Local\Temp\mepBFF0.tmp.exe | executable | |
MD5:7A9527AFDDA4179B10E5465E93D0F3AA | SHA256:C4A60096AD81F6E4CE7412F4873465DE408EAB69D7AC35B9AF9B0B1A4CCD3EEA | |||
| 2816 | mepBFC1.tmp.exe | C:\Users\admin\AppData\Local\Temp\RCXC041.tmp | executable | |
MD5:23F13762CAE2CA663CB2E7B7E826D442 | SHA256:2AF33645C69509801CBF53636F0DD5C076EDB7F1672795B49F67AD6BA3D2A71B | |||
| 2816 | mepBFC1.tmp.exe | C:\Users\admin\AppData\Local\Temp\mepC030.tmp:OECustomProperty | binary | |
MD5:8243E382810CB1DF88D17BB47C998B8E | SHA256:7DFD2BAAA67EE5473604683461E100D6EAD5702581728D211516CD95CC17345B | |||
| 1452 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | automaticdestinations-ms | |
MD5:AC72932B9CA09087C1448B04B35287AC | SHA256:7A5B6BFDFE0CF3E5771E6EE853AB6358E8C2766B2484DDDCB0925CE2E1A32AF8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |