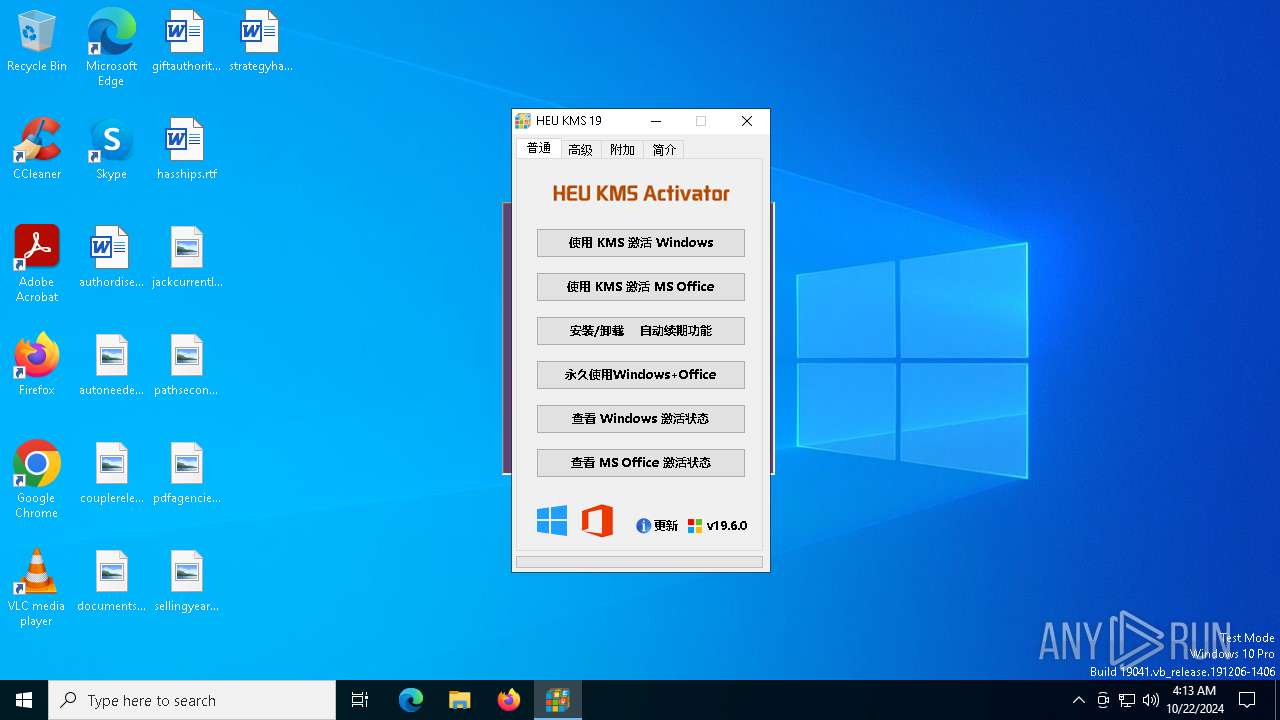
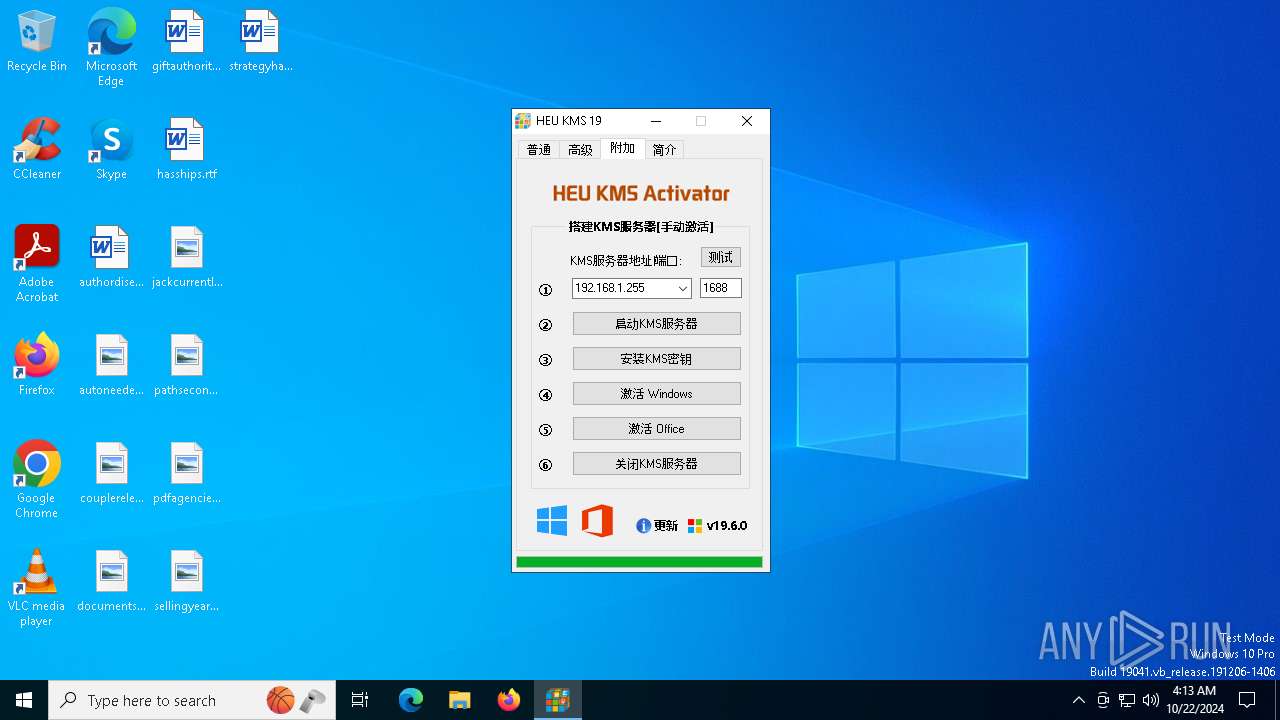
| File name: | KMS.exe |
| Full analysis: | https://app.any.run/tasks/9b87e45e-9eae-4d6f-a21a-9e38e6fec23d |
| Verdict: | Malicious activity |
| Analysis date: | October 22, 2024, 04:12:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D180B08E2FB015EE41DD58D35698363B |
| SHA1: | F8486313B90100E7B7B21E6A798F620D26F047BE |
| SHA256: | E55907FEAD6EE99F2F70EC671C43B4712ABB1D92B8CB71D9EEDB423F7F1AE93C |
| SSDEEP: | 98304:6Wbp/GNeOUNsuxRxTxvQtiLdNZyYcPwudHi4ZkPqsNpLMixC21CHLtqYl6g8cfjU:BiQ8RplMAiJ |
MALICIOUS
Changes the autorun value in the registry
- KMS.exe (PID: 2360)
Connects to the CnC server
- Synaptics.exe (PID: 3600)
Starts NET.EXE for service management
- net.exe (PID: 1184)
- cmd.exe (PID: 1172)
- net.exe (PID: 4308)
- cmd.exe (PID: 6360)
- net.exe (PID: 1748)
- cmd.exe (PID: 6696)
- net.exe (PID: 7052)
- net.exe (PID: 6956)
- cmd.exe (PID: 6724)
- cmd.exe (PID: 3028)
SUSPICIOUS
Executable content was dropped or overwritten
- KMS.exe (PID: 1396)
- KMS.exe (PID: 5004)
- KMS.exe (PID: 2360)
- 7Z.EXE (PID: 3076)
- ._cache_KMS.exe (PID: 6224)
- kms_x64.exe (PID: 1176)
Starts itself from another location
- KMS.exe (PID: 1396)
Reads security settings of Internet Explorer
- KMS.exe (PID: 2360)
- ._cache_KMS.exe (PID: 6224)
Detected use of alternative data streams (AltDS)
- ._cache_KMS.exe (PID: 6224)
Reads Microsoft Outlook installation path
- ._cache_KMS.exe (PID: 6224)
Starts CMD.EXE for commands execution
- ._cache_KMS.exe (PID: 6224)
- kms_x64.exe (PID: 1176)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 5952)
- cmd.exe (PID: 4232)
- cmd.exe (PID: 5912)
- cmd.exe (PID: 6800)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 7100)
- cmd.exe (PID: 6952)
Reads Internet Explorer settings
- ._cache_KMS.exe (PID: 6224)
Drops 7-zip archiver for unpacking
- ._cache_KMS.exe (PID: 6224)
Process drops legitimate windows executable
- ._cache_KMS.exe (PID: 6224)
- 7Z.EXE (PID: 3076)
There is functionality for taking screenshot (YARA)
- Synaptics.exe (PID: 3600)
There is functionality for communication over UDP network (YARA)
- Synaptics.exe (PID: 3600)
There is functionality for communication dyndns network (YARA)
- Synaptics.exe (PID: 3600)
The process drops C-runtime libraries
- 7Z.EXE (PID: 3076)
Drops a system driver (possible attempt to evade defenses)
- 7Z.EXE (PID: 3076)
Contacting a server suspected of hosting an CnC
- Synaptics.exe (PID: 3600)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 1768)
- cmd.exe (PID: 6364)
- cmd.exe (PID: 6324)
Starts application with an unusual extension
- cmd.exe (PID: 1584)
- cmd.exe (PID: 6340)
- cmd.exe (PID: 6320)
- cmd.exe (PID: 948)
- cmd.exe (PID: 864)
- cmd.exe (PID: 1584)
The process executes VB scripts
- cmd.exe (PID: 1440)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 6340)
- cmd.exe (PID: 1584)
- cmd.exe (PID: 4808)
- cmd.exe (PID: 1584)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6320)
- cmd.exe (PID: 948)
- cmd.exe (PID: 864)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 6852)
Starts SC.EXE for service management
- cmd.exe (PID: 6852)
INFO
Checks supported languages
- KMS.exe (PID: 1396)
- KMS.exe (PID: 5004)
- KMS.exe (PID: 2360)
- ._cache_KMS.exe (PID: 6224)
Creates files or folders in the user directory
- KMS.exe (PID: 1396)
Reads the computer name
- KMS.exe (PID: 5004)
- KMS.exe (PID: 2360)
- ._cache_KMS.exe (PID: 6224)
- KMS.exe (PID: 1396)
Create files in a temporary directory
- KMS.exe (PID: 5004)
- KMS.exe (PID: 2360)
- ._cache_KMS.exe (PID: 6224)
The process uses the downloaded file
- KMS.exe (PID: 2360)
- ._cache_KMS.exe (PID: 6224)
Reads mouse settings
- ._cache_KMS.exe (PID: 6224)
Process checks computer location settings
- KMS.exe (PID: 2360)
Creates files in the program directory
- KMS.exe (PID: 2360)
Reads Environment values
- ._cache_KMS.exe (PID: 6224)
Checks proxy server information
- ._cache_KMS.exe (PID: 6224)
The process uses AutoIt
- ._cache_KMS.exe (PID: 6224)
Changes the display of characters in the console
- cmd.exe (PID: 6340)
- cmd.exe (PID: 6320)
- cmd.exe (PID: 1584)
- cmd.exe (PID: 948)
- cmd.exe (PID: 1584)
- cmd.exe (PID: 864)
Deletes a route via ROUTE.EXE
- ROUTE.EXE (PID: 4692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:08:10 00:51:29+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 89600 |
| InitializedDataSize: | 6292480 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9b4a |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.4 |
| ProductVersionNumber: | 1.0.0.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Turkish |
| CharacterSet: | Windows, Turkish |
| CompanyName: | Synaptics |
| FileDescription: | Synaptics Pointing Device Driver |
| FileVersion: | 1.0.0.4 |
| InternalName: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | Synaptics Pointing Device Driver |
| ProductVersion: | 1.0.0.0 |
| Comments: | - |
Total processes
246
Monitored processes
117
Malicious processes
6
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | wmic path SoftwareLicensingProduct where ID='2de67392-b7a7-462a-b1ca-108dd189f588' call Activate | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 860 | C:\WINDOWS\system32\net1 stop sppsvc /y | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | C:\WINDOWS\system32\cmd.exe /c set "Path=%SystemRoot%;%SystemRoot%\system32;%SystemRoot%\System32\Wbem;%SYSTEMROOT%\System32\WindowsPowerShell\v1.0\;" & chcp 437 & wmic path SoftwareLicensingProduct where ID='2de67392-b7a7-462a-b1ca-108dd189f588' call Activate > %windir%\HeuKmsLog\ActivateWindows.log | C:\Windows\System32\cmd.exe | — | kms_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 948 | C:\WINDOWS\system32\cmd.exe /c set "Path=%SystemRoot%;%SystemRoot%\system32;%SystemRoot%\System32\Wbem;%SYSTEMROOT%\System32\WindowsPowerShell\v1.0\;" & chcp 437 & wmic path SoftwareLicensingProduct where ID='2de67392-b7a7-462a-b1ca-108dd189f588' call ClearKeyManagementServicePort >> %windir%\HeuKmsLog\KMSSet.log | C:\Windows\System32\cmd.exe | — | kms_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | C:\WINDOWS\system32\net1 stop sppsvc /y | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1156 | C:\WINDOWS\system32\cmd.exe /c echo Temp=_temp10220412585481 >>%windir%\ScriptTemp.ini | C:\Windows\SysWOW64\cmd.exe | — | ._cache_KMS.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1172 | C:\WINDOWS\system32\cmd.exe /c set "Path=%SystemRoot%;%SystemRoot%\system32;%SystemRoot%\System32\Wbem;%SYSTEMROOT%\System32\WindowsPowerShell\v1.0\;" & net stop sppsvc /y | C:\Windows\System32\cmd.exe | — | kms_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1176 | C:\WINDOWS\_temp10220412585481\kms_x64.exe | C:\Windows\_temp10220412585481\kms_x64.exe | ._cache_KMS.exe | ||||||||||||
User: admin Company: 知彼而知己 Integrity Level: HIGH Description: HEU KMS Activator™ Version: 19.6.0.0 Modules
| |||||||||||||||
| 1184 | net stop osppsvc /y | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 128
Read events
7 114
Write events
11
Delete events
3
Modification events
| (PID) Process: | (2360) KMS.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (2360) KMS.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Synaptics Pointing Device Driver |
Value: C:\ProgramData\Synaptics\Synaptics.exe | |||
| (PID) Process: | (2360) KMS.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 4B26176700000000 | |||
| (PID) Process: | (6224) ._cache_KMS.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6224) ._cache_KMS.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6224) ._cache_KMS.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6224) ._cache_KMS.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (6224) ._cache_KMS.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (1176) kms_x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.exe |
| Operation: | write | Name: | Debugger |
Value: rundll32.exe SECOPatcher.dll,PatcherMain | |||
| (PID) Process: | (1176) kms_x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\CurrentVersion\Software Protection Platform |
| Operation: | write | Name: | NoGenTicket |
Value: 1 | |||
Executable files
35
Suspicious files
19
Text files
113
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2360 | KMS.exe | C:\ProgramData\Synaptics\RCXBF03.tmp | executable | |
MD5:0A39C009FBCE68B687B7D2E2FC3F936A | SHA256:5632327523B34F50681B33D39B8942D64FECE16F0EBA563BBCC792385DCE4BDC | |||
| 2360 | KMS.exe | C:\Users\admin\AppData\Local\Temp\._cache_KMS.exe | executable | |
MD5:4D6A189B7B3F5A33F2658C9D5B15BF12 | SHA256:0077F12EF2689EE5E8F53B426C33950BEE7E81AFE698E91377F22A9469346FA8 | |||
| 1396 | KMS.exe | C:\Users\admin\AppData\Roaming\KMS.exe | executable | |
MD5:D180B08E2FB015EE41DD58D35698363B | SHA256:E55907FEAD6EE99F2F70EC671C43B4712ABB1D92B8CB71D9EEDB423F7F1AE93C | |||
| 6224 | ._cache_KMS.exe | C:\Windows\_temp10220412585481\cert.7z | compressed | |
MD5:10A8C081F96DC74DACA5F0BA91045B36 | SHA256:1E1B06B1BDA8D90232F1B96C116603001C9F56EBCF28F2790533B5825BC475DD | |||
| 6224 | ._cache_KMS.exe | C:\Windows\_temp10220412585481\digital.7z | compressed | |
MD5:69D31717AEF163434058C80209C376EA | SHA256:0F3DD4702B9AE22A9B6D3A1E16B96C9C4FD5F11EE7A01D73AF82505A6A03435C | |||
| 3076 | 7Z.EXE | C:\Windows\_temp10220412585481\OEM\gr1dr1 | binary | |
MD5:AE65783C284AD725317A38DFF0599537 | SHA256:8475795A455E8EA210F6A32280CFBE76F998E7A081A8FB0519AE0408D9F2D54C | |||
| 2360 | KMS.exe | C:\ProgramData\Synaptics\Synaptics.exe | executable | |
MD5:C5246F6FB99924879F3FA014D6D535EB | SHA256:F6C227B33508B7482137B3992C2255D5E5B2116977A854D1572212F930272CB7 | |||
| 6224 | ._cache_KMS.exe | C:\Users\admin\AppData\Local\Temp\autC713.tmp | compressed | |
MD5:19D6252765EB66809BEC9AC0BA8B02E8 | SHA256:F3B4E65E959B0A7E7F9CB926740699D74FCC07BCFDF9667526D2BD3A3D9D08F8 | |||
| 6224 | ._cache_KMS.exe | C:\Windows\splashlogo.gif | image | |
MD5:95CCF61C6AB8C98CD9C6F33AB8D4108F | SHA256:E91A4F80813094EF53A0408D91679E7757E4F71C4ACC9E942E8ACA630BE0DF45 | |||
| 6224 | ._cache_KMS.exe | C:\Windows\HeuKmsRenewal\HEU_KMS_Activator.exe | executable | |
MD5:4D6A189B7B3F5A33F2658C9D5B15BF12 | SHA256:0077F12EF2689EE5E8F53B426C33950BEE7E81AFE698E91377F22A9469346FA8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
56
DNS requests
22
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3648 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4004 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3600 | Synaptics.exe | GET | 200 | 69.42.215.252:80 | http://freedns.afraid.org/api/?action=getdyndns&sha=a30fa98efc092684e8d1c5cff797bcc613562978 | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.164.51:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.51:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4360 | SearchApp.exe | 2.23.209.179:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
xred.mooo.com |
| whitelisted |
freedns.afraid.org |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to Abused Domain *.mooo.com |
3 ETPRO signatures available at the full report