| File name: | de4dot - 21 deobfuscator modules loaded!.rar |
| Full analysis: | https://app.any.run/tasks/fc194337-2aee-4cb7-8d88-4eca5899eea1 |
| Verdict: | Malicious activity |
| Analysis date: | January 16, 2024, 02:30:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 309B0AB91EB0D999D18E5D4967B5AF94 |
| SHA1: | 10697A88D4BAFE248867D4BF1C48061CF341A862 |
| SHA256: | E55879294A2E1BD00B26E9F10AF2DD6C38CE8BA423A0BF47F04B8DCC295EF1A6 |
| SSDEEP: | 49152:74gRYkJMV/NDnOpr/4UpM0GovuUmrMKhtTsz3Vat0cmiTkxMPcvjmevyoWLnbuqB:8gRYkCNc7lHGomBntkq0cmykgcSevy33 |
MALICIOUS
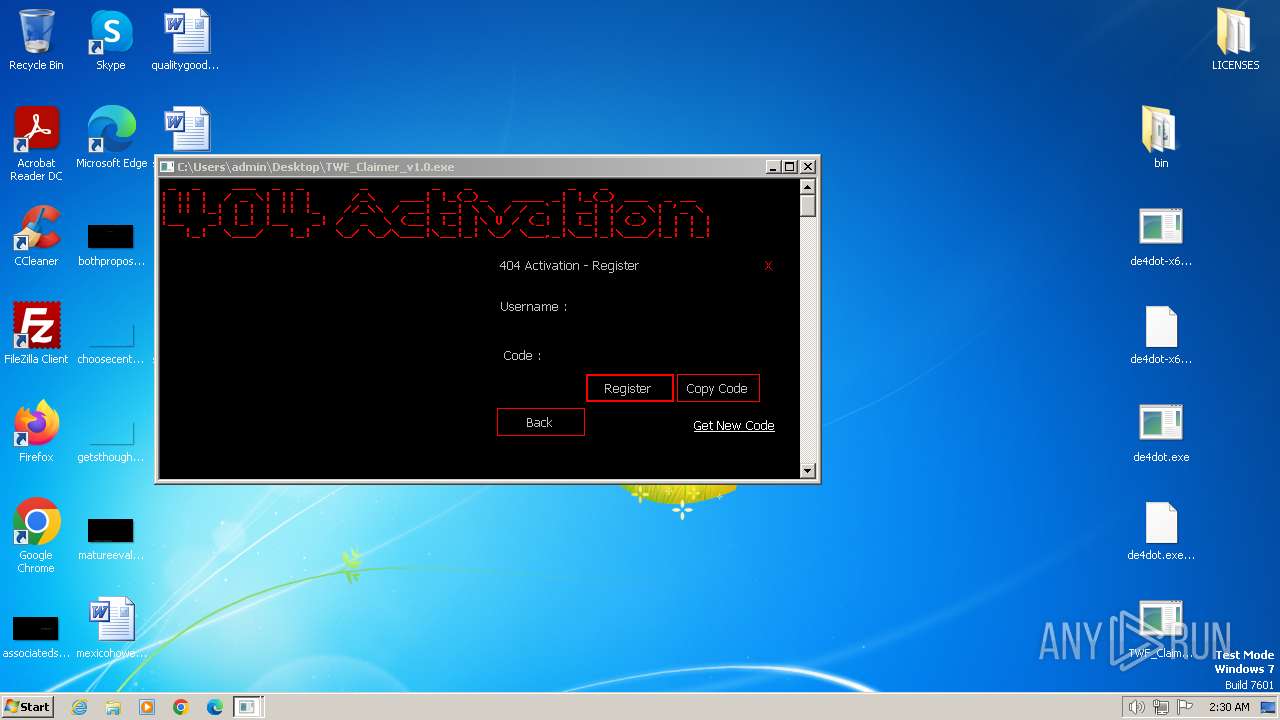
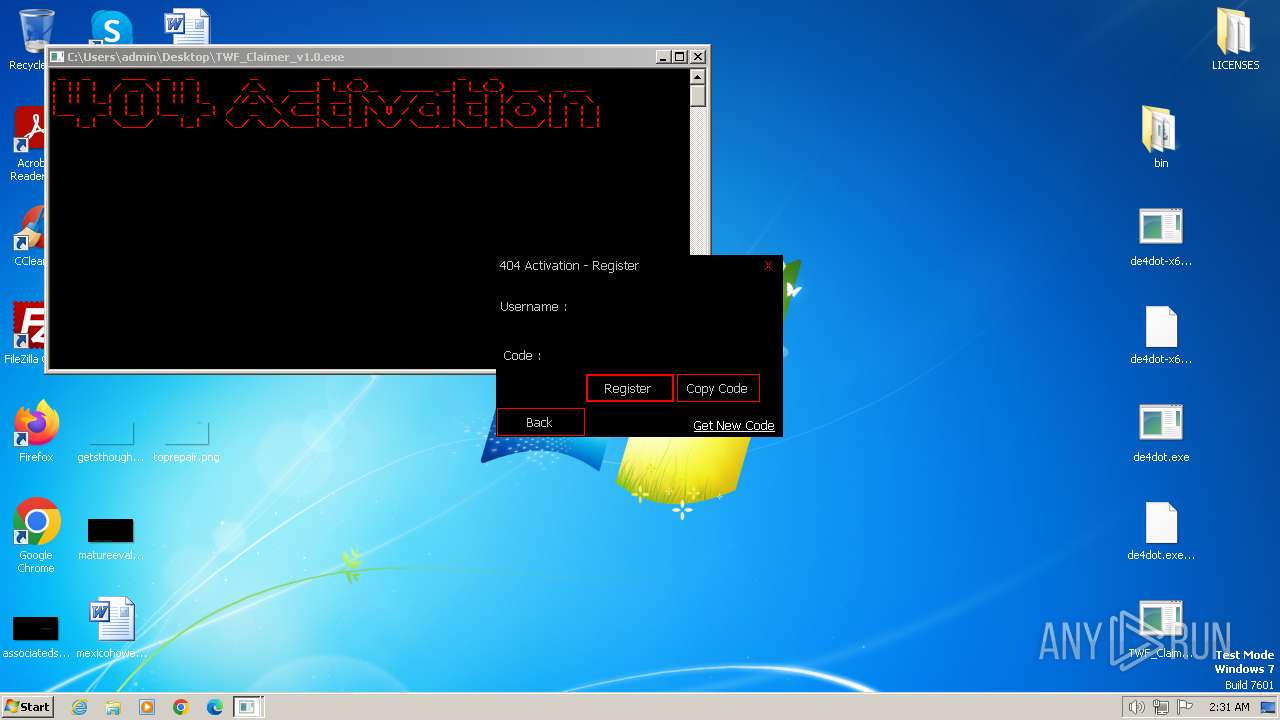
Drops the executable file immediately after the start
- WinRAR.exe (PID: 116)
- TWF_Claimer_v1.0.exe (PID: 2020)
SUSPICIOUS
Executable content was dropped or overwritten
- TWF_Claimer_v1.0.exe (PID: 2020)
Reads the Internet Settings
- TWF_Claimer_v1.0.exe (PID: 1820)
- TWF_Claimer_v1.0.exe (PID: 2020)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 116)
Reads the computer name
- TWF_Claimer_v1.0.exe (PID: 2020)
- de4dot.exe (PID: 1608)
- de4dot.exe (PID: 1536)
- TWF_Claimer_v1.0.exe (PID: 1820)
Create files in a temporary directory
- TWF_Claimer_v1.0.exe (PID: 2020)
Checks supported languages
- TWF_Claimer_v1.0.exe (PID: 2020)
- de4dot.exe (PID: 1608)
- de4dot.exe (PID: 1536)
- TWF_Claimer_v1.0.exe (PID: 1820)
Manual execution by a user
- TWF_Claimer_v1.0.exe (PID: 2020)
- de4dot.exe (PID: 1608)
- TWF_Claimer_v1.0.exe (PID: 1820)
- de4dot.exe (PID: 1536)
Reads the machine GUID from the registry
- TWF_Claimer_v1.0.exe (PID: 2020)
- de4dot.exe (PID: 1536)
- de4dot.exe (PID: 1608)
- TWF_Claimer_v1.0.exe (PID: 1820)
Reads Environment values
- TWF_Claimer_v1.0.exe (PID: 1820)
- TWF_Claimer_v1.0.exe (PID: 2020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
43
Monitored processes
5
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\de4dot - 21 deobfuscator modules loaded!.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
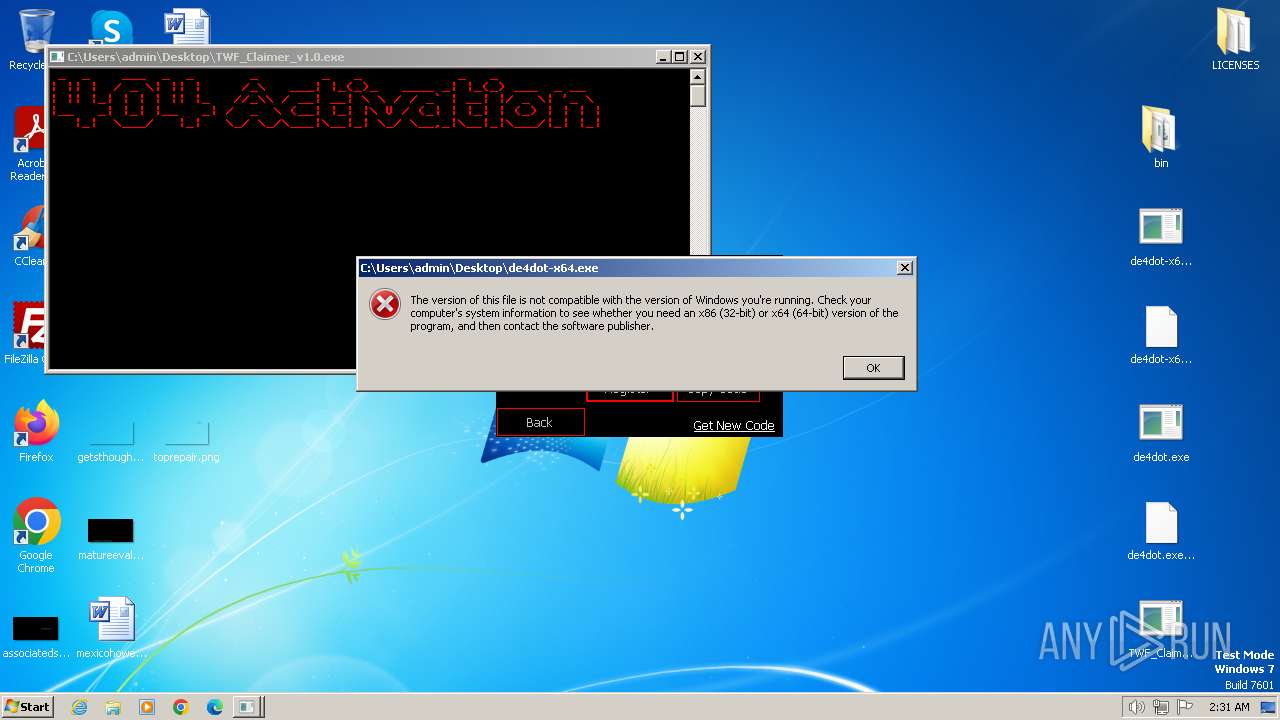
| 1536 | "C:\Users\admin\Desktop\de4dot.exe" | C:\Users\admin\Desktop\de4dot.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: de4dot Exit code: 4294967295 Version: 3.1.41592.3405 Modules
| |||||||||||||||
| 1608 | "C:\Users\admin\Desktop\de4dot.exe" | C:\Users\admin\Desktop\de4dot.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: de4dot Exit code: 4294967295 Version: 3.1.41592.3405 Modules
| |||||||||||||||
| 1820 | "C:\Users\admin\Desktop\TWF_Claimer_v1.0.exe" | C:\Users\admin\Desktop\TWF_Claimer_v1.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: TWF_Claimer Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2020 | "C:\Users\admin\Desktop\TWF_Claimer_v1.0.exe" | C:\Users\admin\Desktop\TWF_Claimer_v1.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: TWF_Claimer Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
2 466
Read events
2 446
Write events
20
Delete events
0
Modification events
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
16
Suspicious files
0
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.22614\bin\AssemblyServer-CLR20-x64.exe | executable | |
MD5:ACEB8FF95E1B9275CD64948E9F6CD68E | SHA256:81DF538F60002615017DC1566886C6C5B3ED0FC233375B3E1D8702DC325FF53D | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.22614\bin\AssemblyServer-CLR40.exe | executable | |
MD5:02C118E766712D8BD0ED56396874B4AE | SHA256:165ED3F0DCBC7ABB5630EE42DBB092BB13E200CDE86CE7DF945294D7886A2BD2 | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.22614\bin\AssemblyData.dll | executable | |
MD5:C589009470C50169B013631F1576DE7C | SHA256:99DC2B58DCD7C43EFB55D8EBD7B151025F1527B358310492C1D5A01D86CBE1D9 | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.22614\bin\AssemblyServer-CLR20.exe.config | xml | |
MD5:773D62E07CB2526F2D7D0DFE7232976E | SHA256:BF82081F1A62C82B196367D76F401533C53CDF9B53D2E8DFE4CE06CBF8F7D939 | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.22614\bin\AssemblyServer-CLR20.exe | executable | |
MD5:EDE2A03A52ABDD55B88057A8CBF4B721 | SHA256:A1222481607559D09FD3AA91C6A159157B165659D74055CEDB63E52A58517B68 | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.22614\bin\AssemblyServer-CLR20-x64.exe.config | xml | |
MD5:773D62E07CB2526F2D7D0DFE7232976E | SHA256:BF82081F1A62C82B196367D76F401533C53CDF9B53D2E8DFE4CE06CBF8F7D939 | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.22614\bin\AssemblyServer-x64.exe | executable | |
MD5:19F40521EB262308684E388C46CB571F | SHA256:C19C13FB0DFF9CB45D8FB269A1A4D9459F12A02727A9C44115ADB7B5F322EC6A | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.22614\bin\AssemblyServer-CLR40-x64.exe.config | xml | |
MD5:D7D253E396E0FDF9530366D9AC6E6DD3 | SHA256:54277782ECD7D3503E66B4D86493FAC0649AD3B8C9D2493AC28F4C948968A6E9 | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.22614\bin\AssemblyServer-x64.exe.config | xml | |
MD5:88A956F4FCA5481B2311AFE28566092E | SHA256:AED6224C24F14853F35CD6077E68B3721BF5055B43D64724437E8164ADA025B7 | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.22614\bin\AssemblyServer.exe | executable | |
MD5:1FCB4298B400C1E37DC6D004650482B1 | SHA256:CC23F4877CE501521F700CC2789D354ECB0B4DDCF576CB5E9718BAEF9BF92411 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
1
Threats
3
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2020 | TWF_Claimer_v1.0.exe | 64.185.227.156:443 | api.ipify.org | WEBNX | US | unknown |
1820 | TWF_Claimer_v1.0.exe | 64.185.227.156:443 | api.ipify.org | WEBNX | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.ipify.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
2020 | TWF_Claimer_v1.0.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
1820 | TWF_Claimer_v1.0.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |