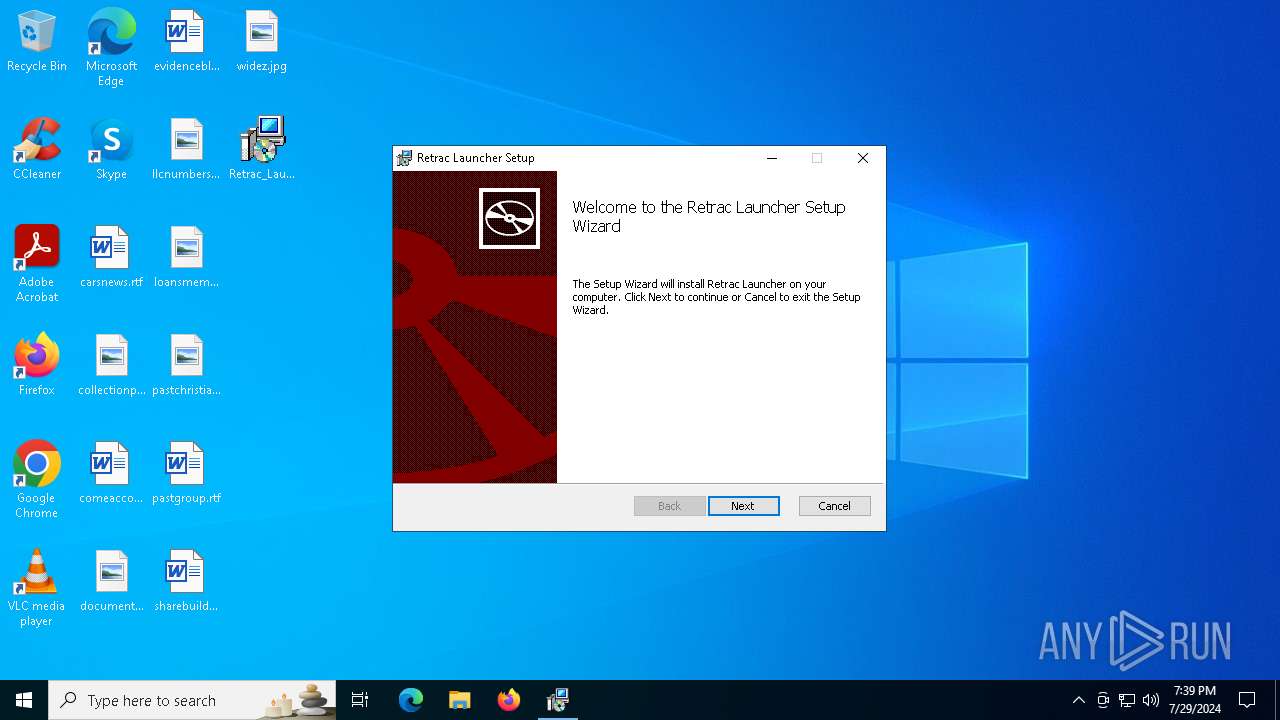
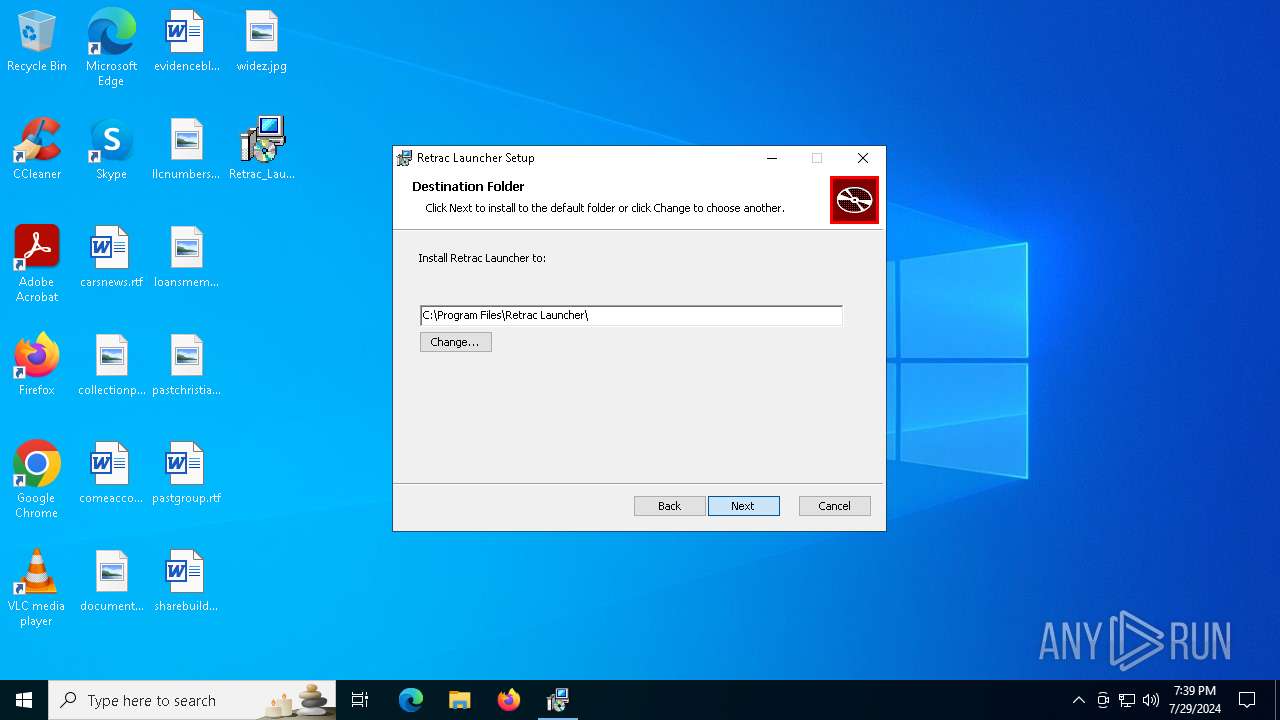
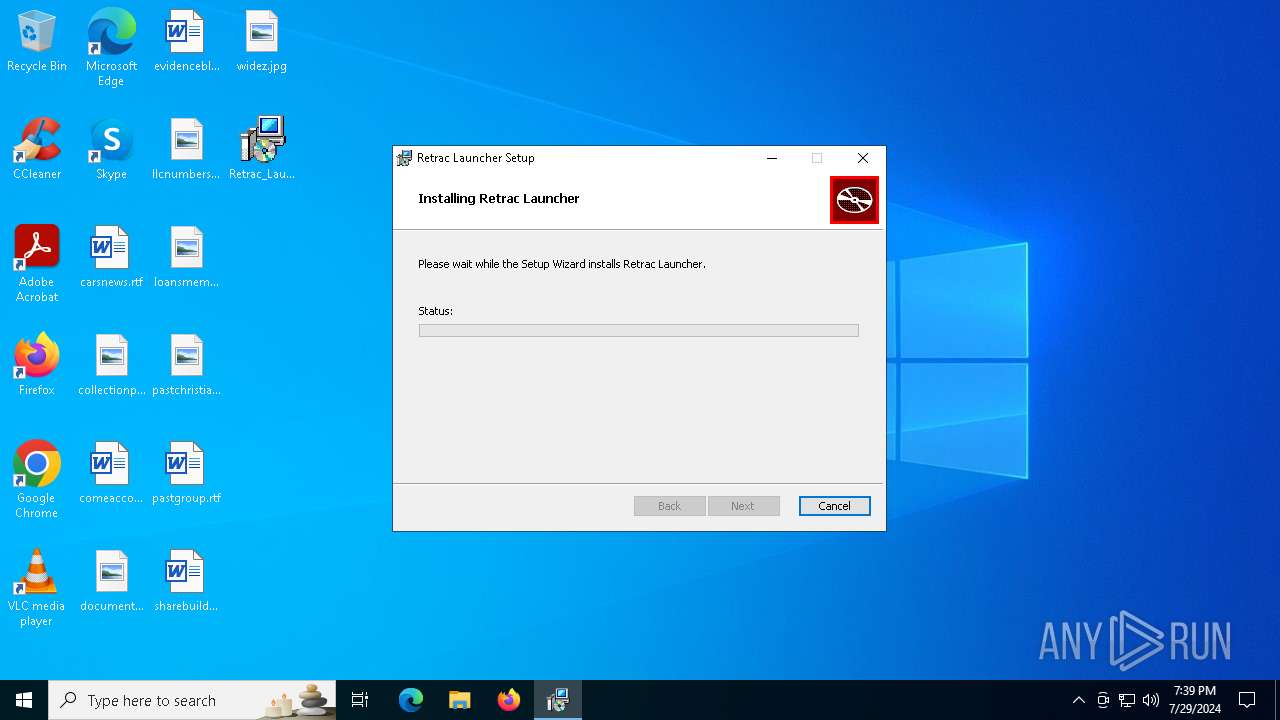
| File name: | Retrac_Launcher_1.0.9_x64_en-US.msi |
| Full analysis: | https://app.any.run/tasks/cac1b606-2e37-4eab-abab-b0d328259e3a |
| Verdict: | Malicious activity |
| Analysis date: | July 29, 2024, 19:38:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Retrac Launcher, Author: retrac, Keywords: Installer, Comments: This installer database contains the logic and data required to install Retrac Launcher., Template: x64;0, Revision Number: {40B8E828-9C76-48B1-A498-F10EA833B7D1}, Create Time/Date: Sat Jul 13 22:10:24 2024, Last Saved Time/Date: Sat Jul 13 22:10:24 2024, Number of Pages: 450, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | 79A3EF34FB61355DF68B7931C56F08F5 |
| SHA1: | F945151E501116AA5D2FBE3698CD55FF9B766691 |
| SHA256: | E54675FDCD9D66F78F122B7DD4B61F2ACD77951DCDD32914AF8ACE2FF71FD18C |
| SSDEEP: | 98304:rOQkEhQW6Lq6aYfYO75qRmL5w55IP4IDU2rn/W3JWALJgBVJolNBDYLUA5ts7pF4:PQOfn3FP81 |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 5624)
- msiexec.exe (PID: 2332)
Run PowerShell with an invisible window
- powershell.exe (PID: 7788)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 5616)
Powershell scripting: start process
- msiexec.exe (PID: 2332)
Request a resource from the Internet using PowerShell's cmdlet
- msiexec.exe (PID: 2332)
Downloads file from URI
- powershell.exe (PID: 7788)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 2332)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 2332)
INFO
Checks supported languages
- msiexec.exe (PID: 3124)
- msiexec.exe (PID: 2332)
Checks proxy server information
- slui.exe (PID: 1712)
Reads the computer name
- msiexec.exe (PID: 3124)
- msiexec.exe (PID: 2332)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5624)
- msiexec.exe (PID: 2332)
Reads the software policy settings
- slui.exe (PID: 1712)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Retrac Launcher |
| Author: | retrac |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Retrac Launcher. |
| Template: | x64;0 |
| RevisionNumber: | {40B8E828-9C76-48B1-A498-F10EA833B7D1} |
| CreateDate: | 2024:07:13 22:10:24 |
| ModifyDate: | 2024:07:13 22:10:24 |
| Pages: | 450 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
150
Monitored processes
10
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1712 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2332 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3124 | C:\Windows\syswow64\MsiExec.exe -Embedding 4300F08BBA2C33280C9CC5E49C69938F C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3188 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5616 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5624 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\Desktop\Retrac_Launcher_1.0.9_x64_en-US.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7656 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 7668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 7788 | powershell.exe -NoProfile -windowstyle hidden try { [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 } catch {}; Invoke-WebRequest -Uri "https://go.microsoft.com/fwlink/p/?LinkId=2124703" -OutFile "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" ; Start-Process -FilePath "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" -ArgumentList ('/silent', '/install') -Wait | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 7796 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
3 204
Read events
3 157
Write events
37
Delete events
10
Modification events
| (PID) Process: | (2332) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000E0BE5AFEEEE1DA011C090000B8190000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2332) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000E0BE5AFEEEE1DA011C090000B8190000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2332) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000047EFB2FEEEE1DA011C090000B8190000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2332) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000047EFB2FEEEE1DA011C090000B8190000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2332) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000CEB8B7FEEEE1DA011C090000B8190000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2332) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000007E6DBCFEEEE1DA011C090000B8190000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2332) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (2332) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 480000000000000028018B00EFE1DA011C090000B8190000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2332) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000035658D00EFE1DA011C09000000120000E8030000010000000000000000000000A8B732351B0373468D89EF4138CB080100000000000000000000000000000000 | |||
| (PID) Process: | (5616) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000060AD9B00EFE1DA01F015000050190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
2
Suspicious files
6
Text files
3
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2332 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2332 | msiexec.exe | C:\Windows\Installer\1c9041.msi | — | |
MD5:— | SHA256:— | |||
| 2332 | msiexec.exe | C:\Windows\Installer\1c9043.msi | — | |
MD5:— | SHA256:— | |||
| 2332 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:6503CFC3E8D4E5FA0274FC4A07E6F93E | SHA256:A51E9B4FAB9587E449913E0EC59044705C54F745C859CE856EB16A31B13BF411 | |||
| 5624 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI290B.tmp | executable | |
MD5:4FDD16752561CF585FED1506914D73E0 | SHA256:AECD2D2FE766F6D439ACC2BBF1346930ECC535012CF5AD7B3273D2875237B7E7 | |||
| 2332 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{3532b7a8-031b-4673-8d89-ef4138cb0801}_OnDiskSnapshotProp | binary | |
MD5:6503CFC3E8D4E5FA0274FC4A07E6F93E | SHA256:A51E9B4FAB9587E449913E0EC59044705C54F745C859CE856EB16A31B13BF411 | |||
| 2332 | msiexec.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Retrac Launcher\~etrac Launcher.tmp | lnk | |
MD5:62BCBFCAC1FEA9CE3A09CFB0EF3179C5 | SHA256:60646A90B19B7DEDD32E59F9902EDC95EA657AA182B3A962B34D48C91A3C3B18 | |||
| 2332 | msiexec.exe | C:\Windows\Temp\~DF7CFE933E89F94E1A.TMP | binary | |
MD5:54699D9613B03204E7334495C34F5FA6 | SHA256:61BCC73C493D3BC1D7F6A0F709B971E703CB2B268E23276BD0284A3097B624A8 | |||
| 2332 | msiexec.exe | C:\Users\Public\Desktop\Retrac Launcher.lnk | binary | |
MD5:4F32297065E273EA82972E1B6995F323 | SHA256:6A1A8AE686F02DF751544E2977D3E30E9A2FBB8A531BB9260F62BE7E3C3B2179 | |||
| 2332 | msiexec.exe | C:\Windows\Installer\{7DD522F6-E5CD-4B2E-9A9D-A445D8FF8695}\ProductIcon | image | |
MD5:B57F2765879042B033B21C525C289D80 | SHA256:B9F884956C9D614CCE40B8E362F814C279AC9C93BBFBA75601587BCD6B7CD117 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
53
DNS requests
31
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1248 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2348 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1712 | slui.exe | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4424 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |