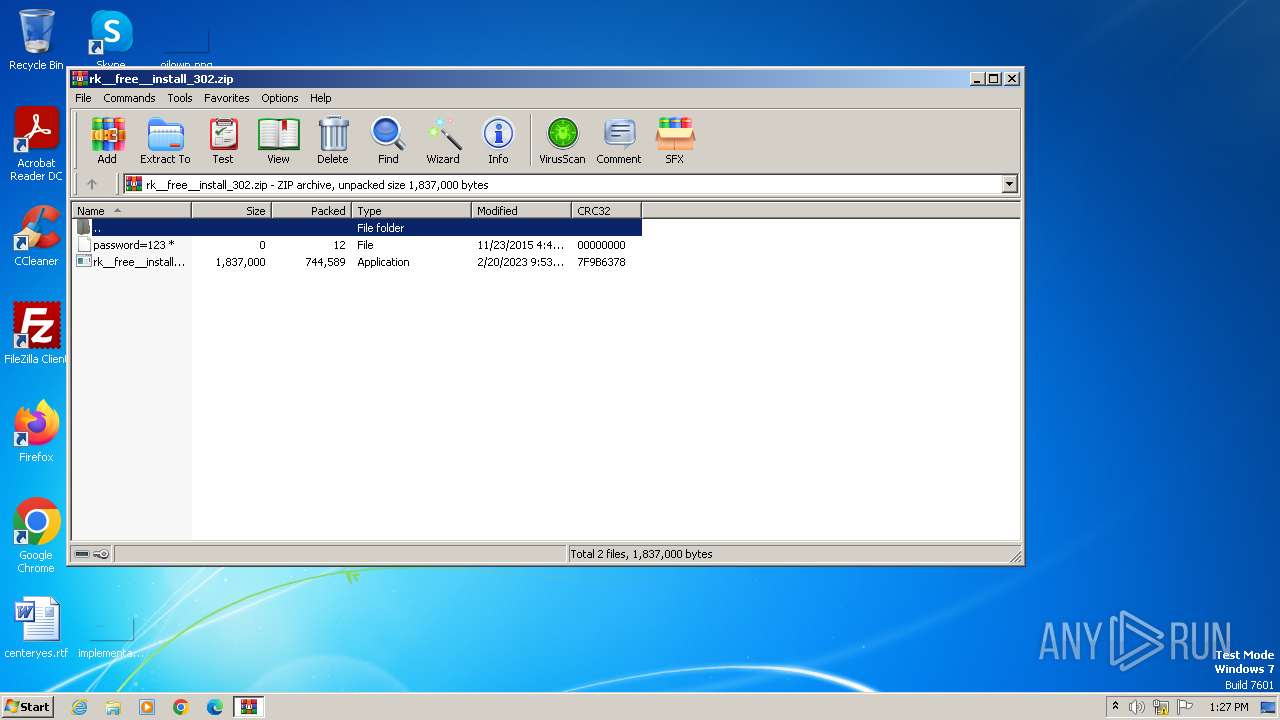
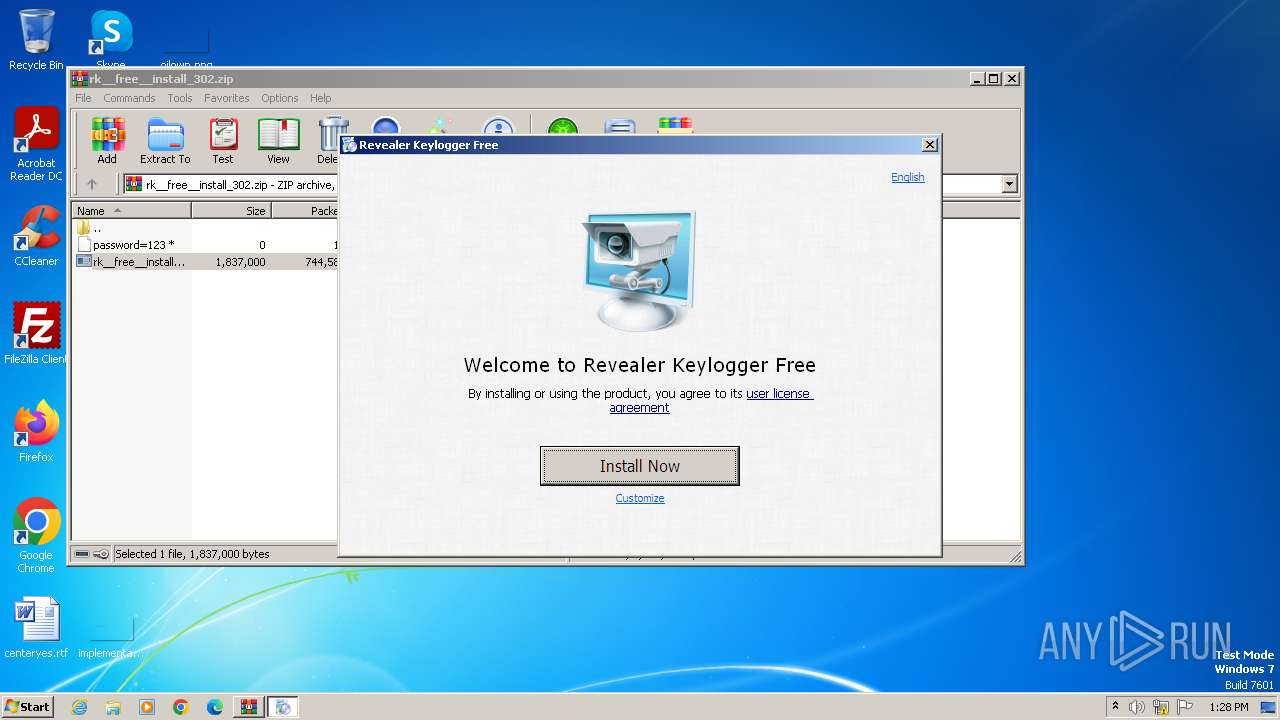
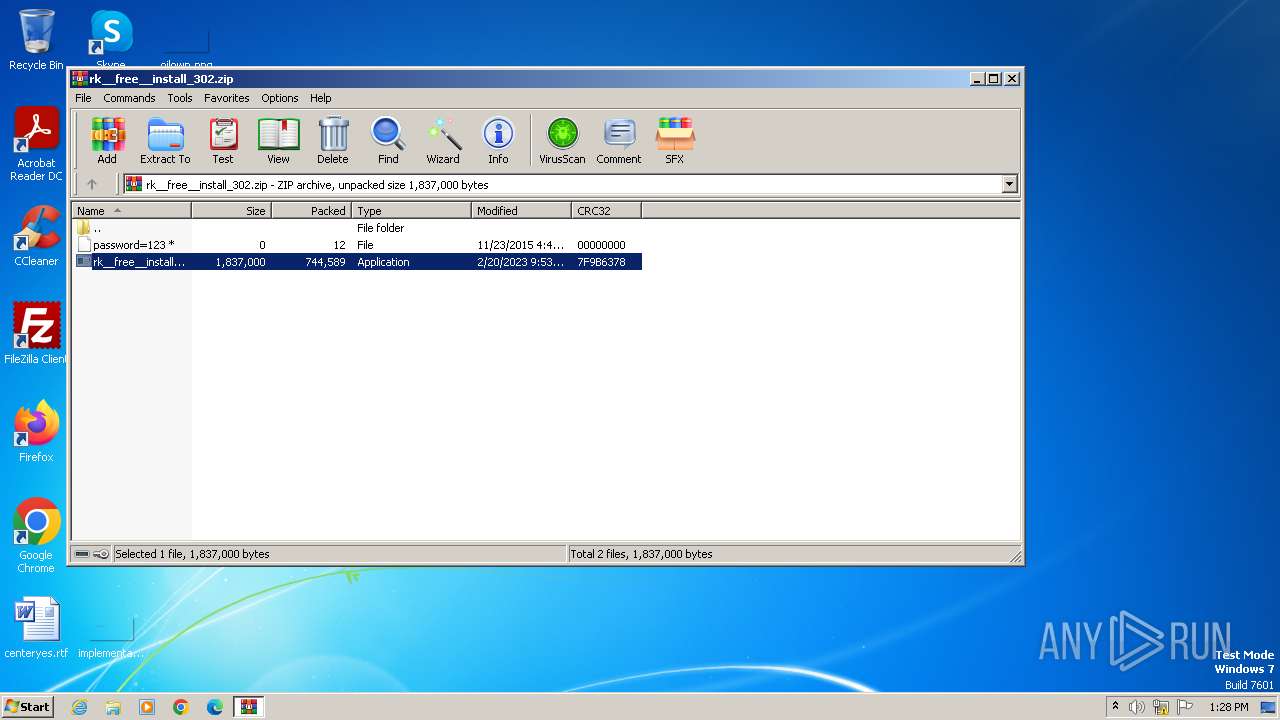
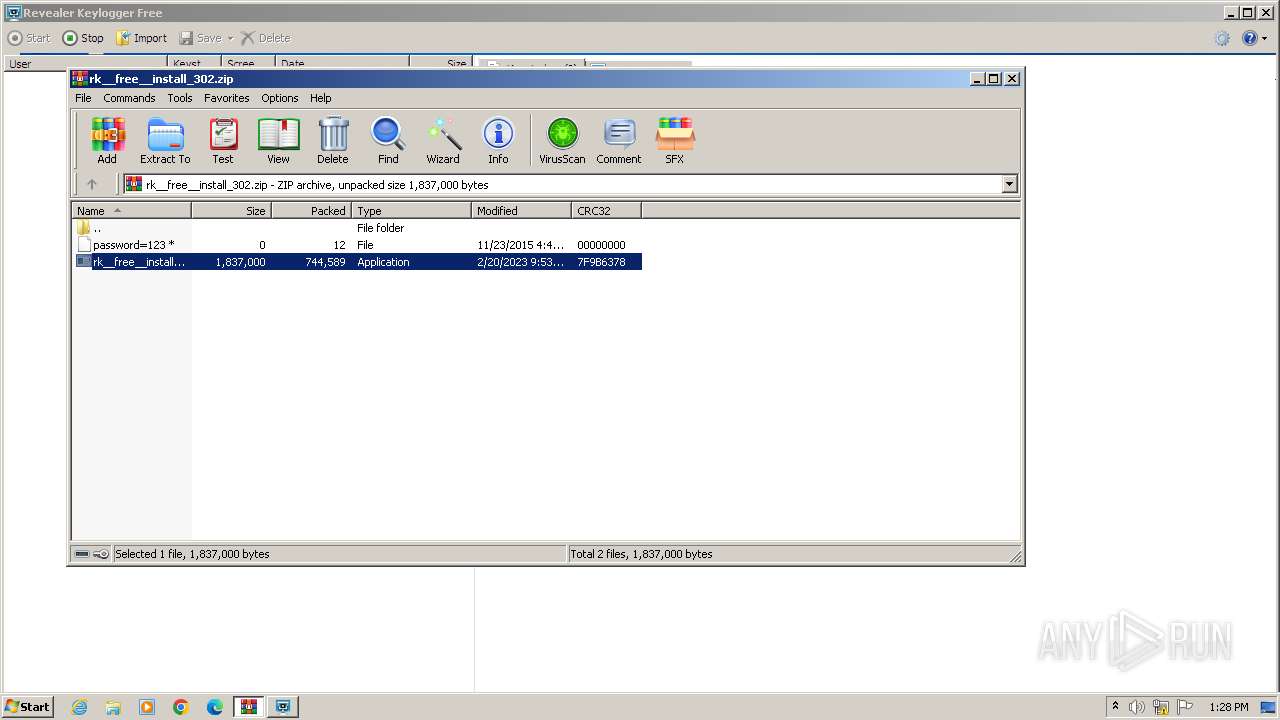
| File name: | rk__free__install_302.zip |
| Full analysis: | https://app.any.run/tasks/c47635aa-8a20-4f0c-b69f-f6d18b6cd296 |
| Verdict: | Malicious activity |
| Analysis date: | June 06, 2024, 12:27:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | F0DADC01E7B2ADFE5E15595DF558D4BE |
| SHA1: | E50D194AA19424BE71E563B456AB19DA53841E0E |
| SHA256: | E52FB474CFDBFA3A213B603E51D52BC767F11DB16998EDB1B2D3FC809ADDF2F9 |
| SSDEEP: | 24576:pSQMQ3Uh2Ca1GXkRZEvl6NOlWxpO7e0MiT1+ZOzVbRifS4rBKRfptb55UXJeRDAE:pSQMQ3Uh2Ca1GXkRZEvl6NOlWxpO7e01 |
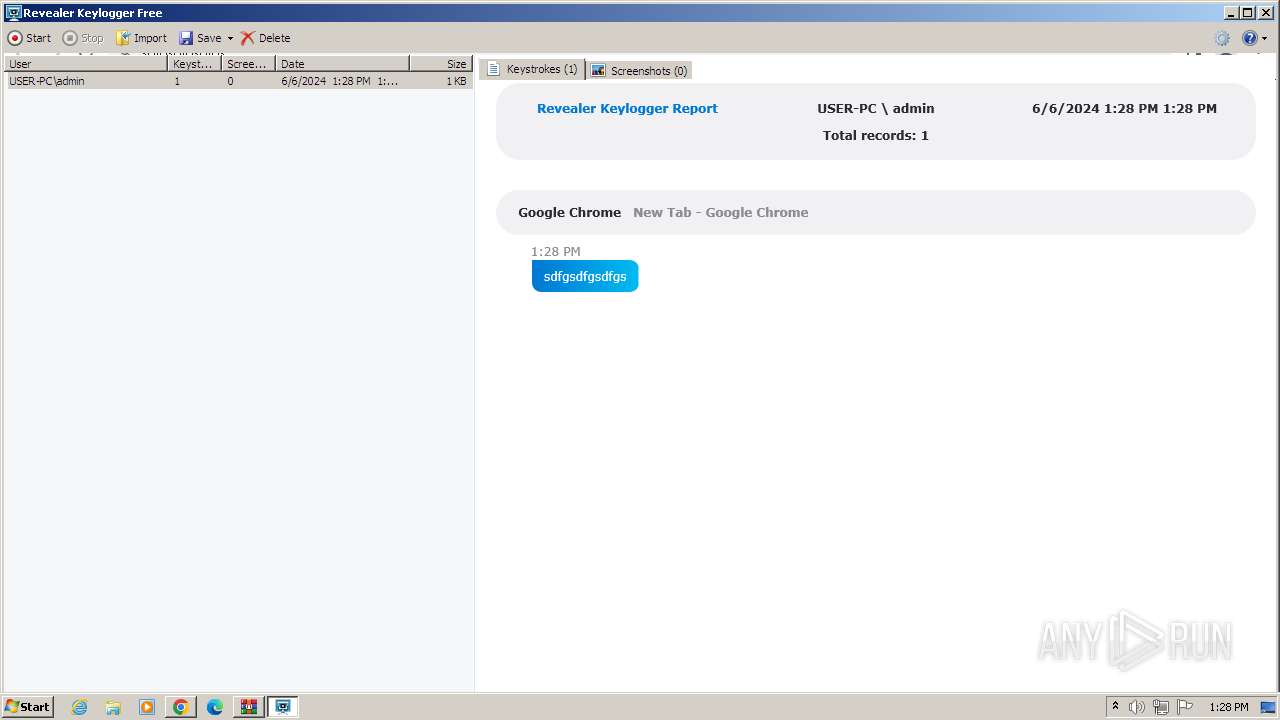
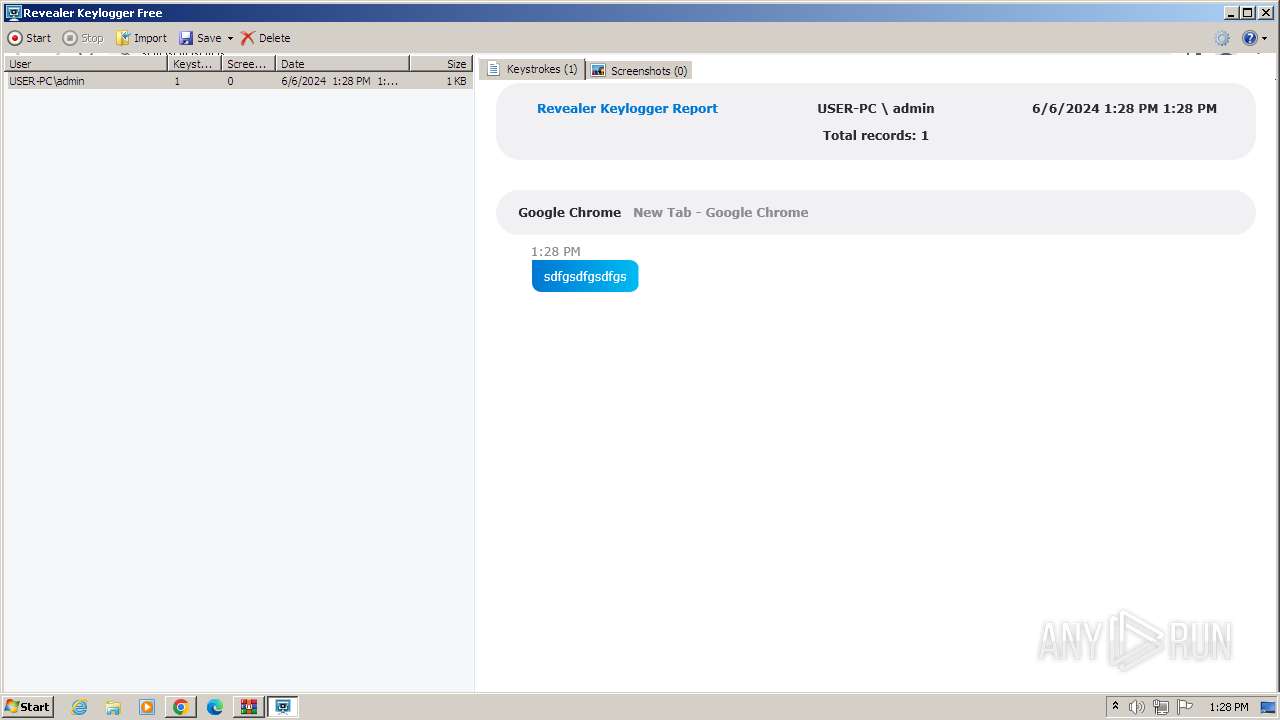
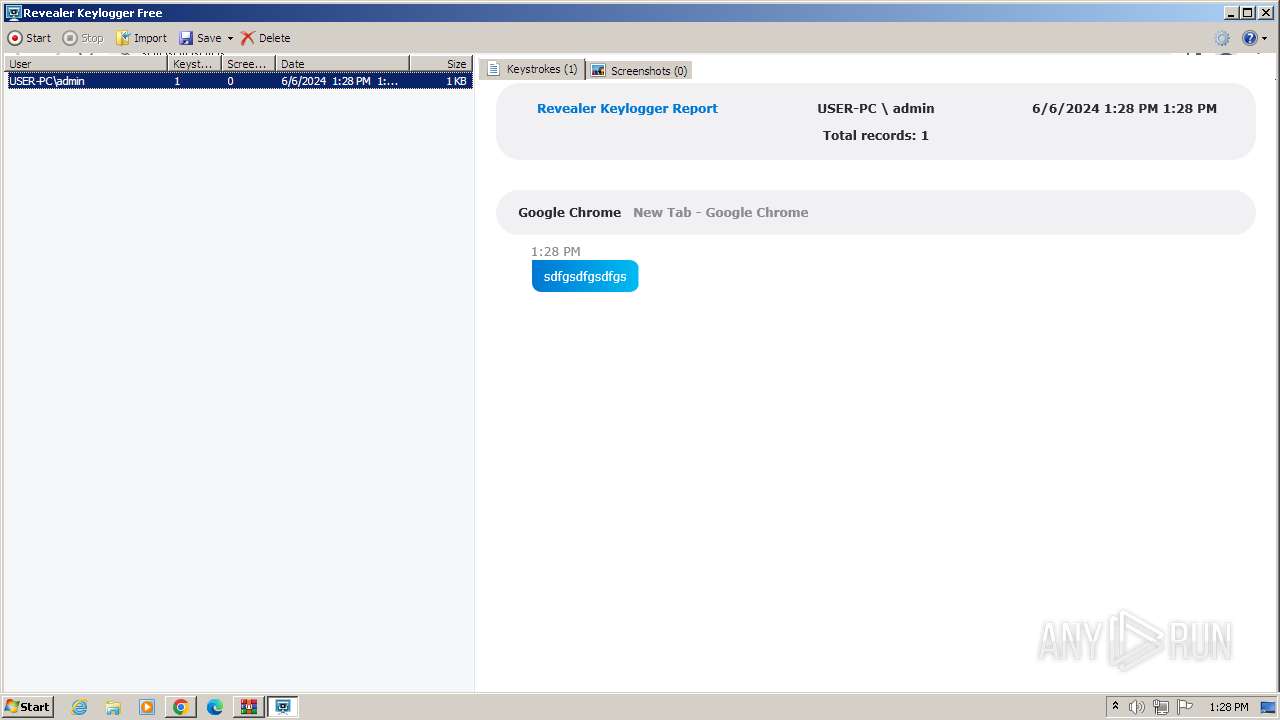
MALICIOUS
Drops the executable file immediately after the start
- rk__free__install_302.exe (PID: 864)
Modifies exclusions in Windows Defender
- rk__free__install_302.exe (PID: 864)
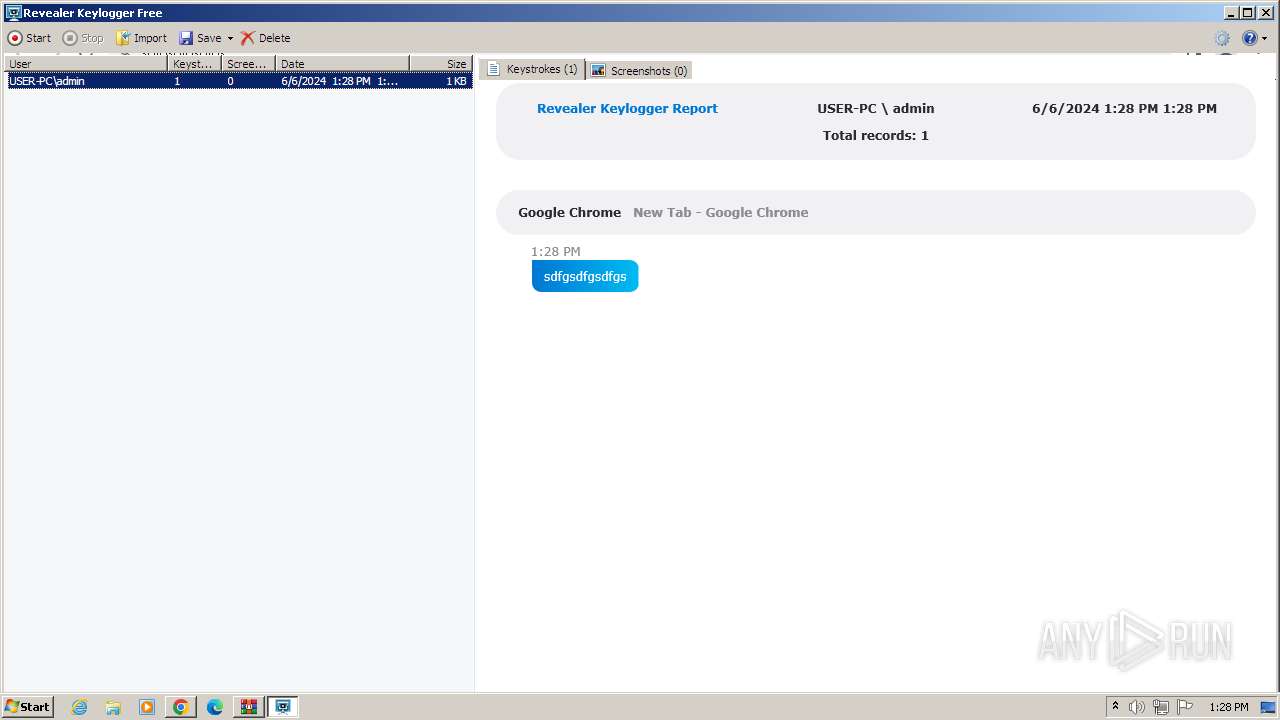
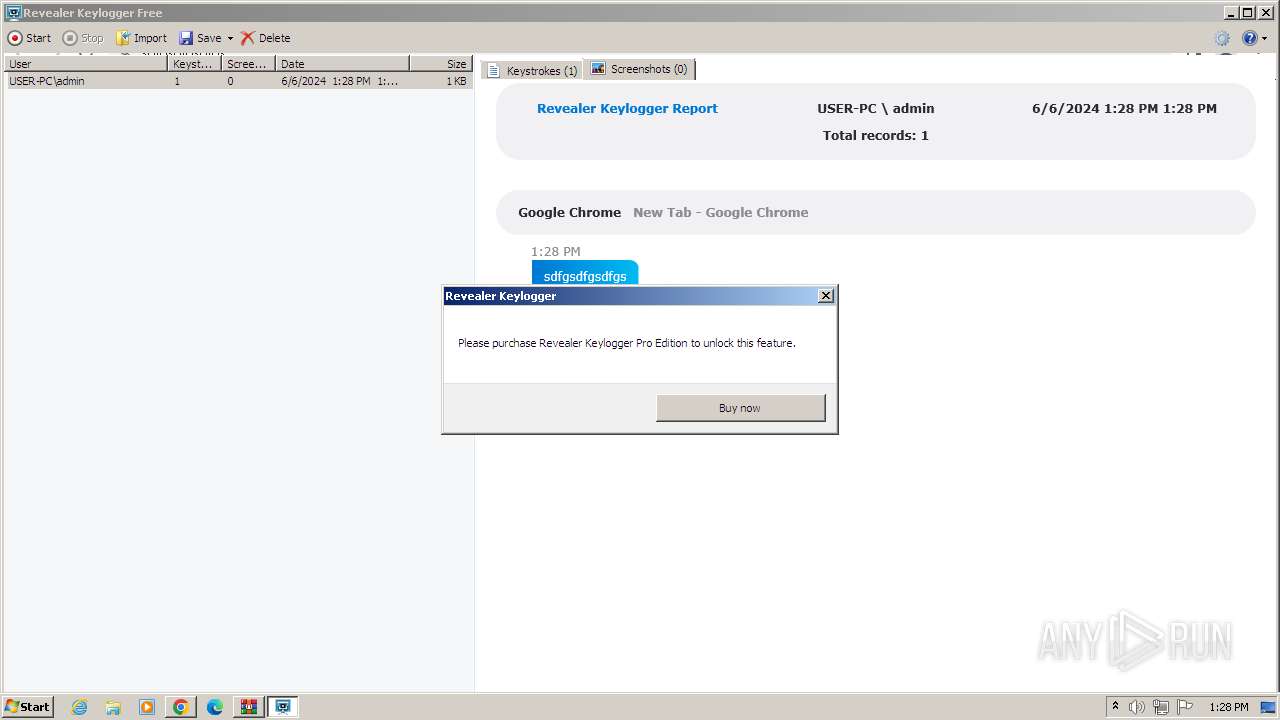
Create files in the Startup directory
- rvlkl.exe (PID: 328)
Creates a writable file in the system directory
- rk__free__install_302.exe (PID: 864)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3976)
- rk__free__install_302.exe (PID: 864)
- rvlkl.exe (PID: 1652)
Detected use of alternative data streams (AltDS)
- rk__free__install_302.exe (PID: 864)
Executable content was dropped or overwritten
- rk__free__install_302.exe (PID: 864)
Reads the Internet Settings
- rk__free__install_302.exe (PID: 864)
- rvlkl.exe (PID: 1652)
Reads Microsoft Outlook installation path
- rvlkl.exe (PID: 1652)
Reads Internet Explorer settings
- rvlkl.exe (PID: 1652)
INFO
Checks supported languages
- rk__free__install_302.exe (PID: 864)
- rvlkl.exe (PID: 328)
- rvlkl.exe (PID: 1652)
- wmpnscfg.exe (PID: 2412)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3976)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3976)
Reads the machine GUID from the registry
- rk__free__install_302.exe (PID: 864)
- rvlkl.exe (PID: 328)
- rvlkl.exe (PID: 1652)
Reads the computer name
- rk__free__install_302.exe (PID: 864)
- rvlkl.exe (PID: 328)
- rvlkl.exe (PID: 1652)
- wmpnscfg.exe (PID: 2412)
Creates files in the program directory
- rvlkl.exe (PID: 328)
- rvlkl.exe (PID: 1652)
- rk__free__install_302.exe (PID: 864)
Manual execution by a user
- rvlkl.exe (PID: 304)
- chrome.exe (PID: 768)
- wmpnscfg.exe (PID: 2412)
- rvlkl.exe (PID: 1652)
Application launched itself
- chrome.exe (PID: 768)
Checks proxy server information
- rvlkl.exe (PID: 1652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
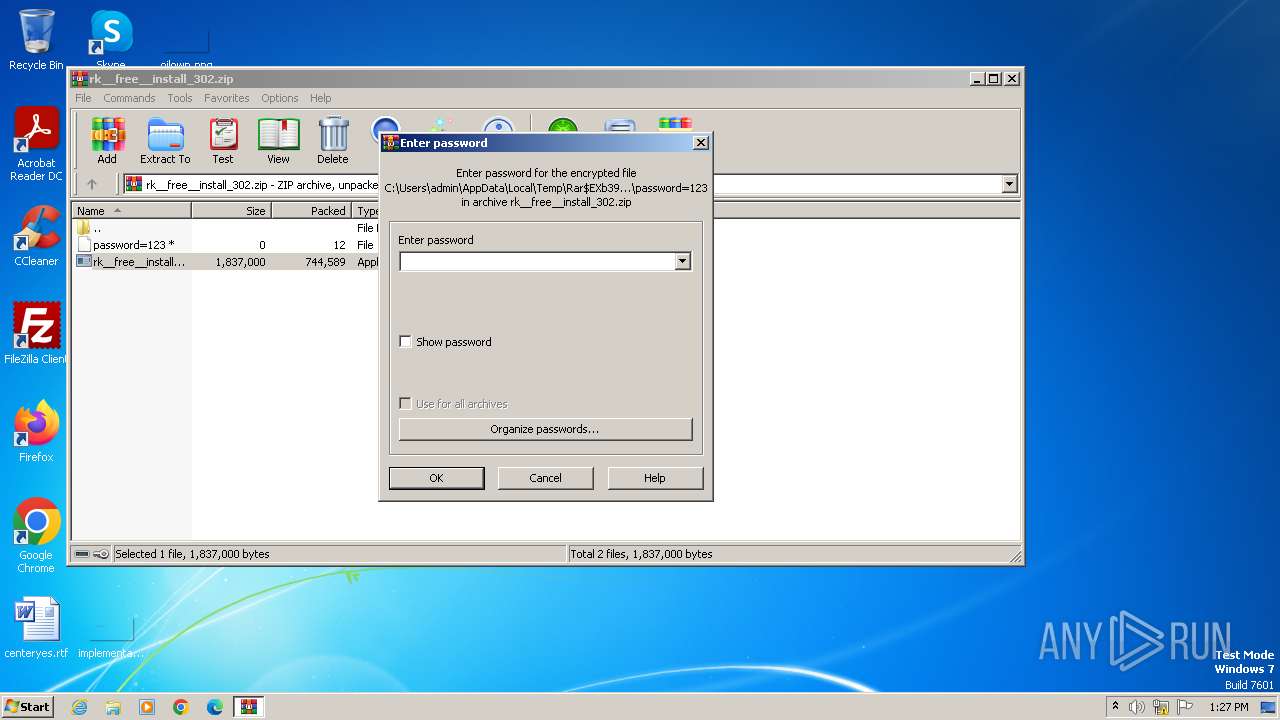
| ZipBitFlag: | 0x0001 |
| ZipCompression: | None |
| ZipModifyDate: | 2015:11:23 17:45:06 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 12 |
| ZipUncompressedSize: | 12 |
| ZipFileName: | password=123 |
Total processes
57
Monitored processes
19
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Windows\system32\rvlkl.exe" | C:\Windows\System32\rvlkl.exe | — | explorer.exe | |||||||||||
User: admin Company: Logixoft Integrity Level: MEDIUM Description: Revealer Free Exit code: 3221226540 Version: 3.0.2.0 Modules
| |||||||||||||||
| 328 | "C:\Windows\system32\rvlkl.exe" -install -lang 9 | C:\Windows\System32\rvlkl.exe | rk__free__install_302.exe | ||||||||||||
User: admin Company: Logixoft Integrity Level: HIGH Description: Revealer Free Exit code: 0 Version: 3.0.2.0 Modules
| |||||||||||||||
| 600 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2448 --field-trial-handle=1172,i,11424370500928894952,10081737348788126968,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 768 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 864 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3976.18819\rk__free__install_302.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3976.18819\rk__free__install_302.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1064 | "C:\Windows\system32\rvlkl.exe" -install -lang 9 | C:\Windows\System32\rvlkl.exe | — | rk__free__install_302.exe | |||||||||||
User: admin Company: Logixoft Integrity Level: HIGH Description: Revealer Free Exit code: 3221226540 Version: 3.0.2.0 Modules
| |||||||||||||||
| 1080 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6e058b38,0x6e058b48,0x6e058b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1280 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3420 --field-trial-handle=1172,i,11424370500928894952,10081737348788126968,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1652 | "C:\Windows\system32\rvlkl.exe" | C:\Windows\System32\rvlkl.exe | explorer.exe | ||||||||||||
User: admin Company: Logixoft Integrity Level: HIGH Description: Revealer Free Version: 3.0.2.0 Modules
| |||||||||||||||
| 1868 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1528 --field-trial-handle=1172,i,11424370500928894952,10081737348788126968,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
12 372
Read events
12 268
Write events
99
Delete events
5
Modification events
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\rk__free__install_302.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
3
Suspicious files
25
Text files
24
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 768 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF109f30.TMP | — | |
MD5:— | SHA256:— | |||
| 768 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 328 | rvlkl.exe | C:\ProgramData\rvlkl\conf_ | text | |
MD5:408695590448CD5FD80A51DFB52AC978 | SHA256:AA70F21F439B0A6DB84BACF2C00A79903B7BC23EC43A19388325665A7CA5DFAF | |||
| 768 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:FF6BABA737D50E515029C3F3A1305BBC | SHA256:670EED15EAA8E3F1A4F8612B229654EB0C64107AEAF0B1017E4BD45E3F7EED83 | |||
| 768 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 864 | rk__free__install_302.exe | C:\ProgramData\rvlkl\log.css | text | |
MD5:A35BD6E012B609D94A076699C5372657 | SHA256:6EF8CFC8307115A02E5B60AF549867DC79BDF3018EB95A9417E8E6C3632EABB5 | |||
| 864 | rk__free__install_302.exe | C:\Windows\system32\rvlkl.exe | executable | |
MD5:9CDBF1530AE67E0D457BE21D3587329B | SHA256:D924B0CD61A2FCCF0F97574FB0FB230F583BEBE655E0B5D181E975174A276C1C | |||
| 1652 | rvlkl.exe | C:\ProgramData\rvlkl\conf_ | text | |
MD5:58A98F529EE661B5237ACC2E301716BE | SHA256:CCB8B502C9F8EADF132A8C76A518B12F272DC1A4DA8904EBFF868644D4F9E4C2 | |||
| 328 | rvlkl.exe | C:\ProgramData\rvlkl\conf | text | |
MD5:F029B85E498793E0CB73175040B0E24B | SHA256:438084D39D670AC7EC780D9DF98DC9CD57B3008A3923706A4BB7DFE91BB0E2BD | |||
| 768 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF10a162.TMP | text | |
MD5:AD0DB8476493577A67FA94A162B646C4 | SHA256:304FB5B4FD83D4A9FF1EF4CF20232A1783169C148297BFE37ED24A1D22A74F2B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
13
DNS requests
12
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
768 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
2348 | chrome.exe | 216.58.212.163:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2348 | chrome.exe | 173.194.69.84:443 | accounts.google.com | GOOGLE | US | unknown |
2348 | chrome.exe | 142.250.185.100:443 | www.google.com | GOOGLE | US | unknown |
2348 | chrome.exe | 142.250.185.174:443 | encrypted-tbn0.gstatic.com | GOOGLE | US | whitelisted |
2348 | chrome.exe | 142.250.186.163:443 | update.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
update.googleapis.com |
| unknown |
www.googleapis.com |
| whitelisted |