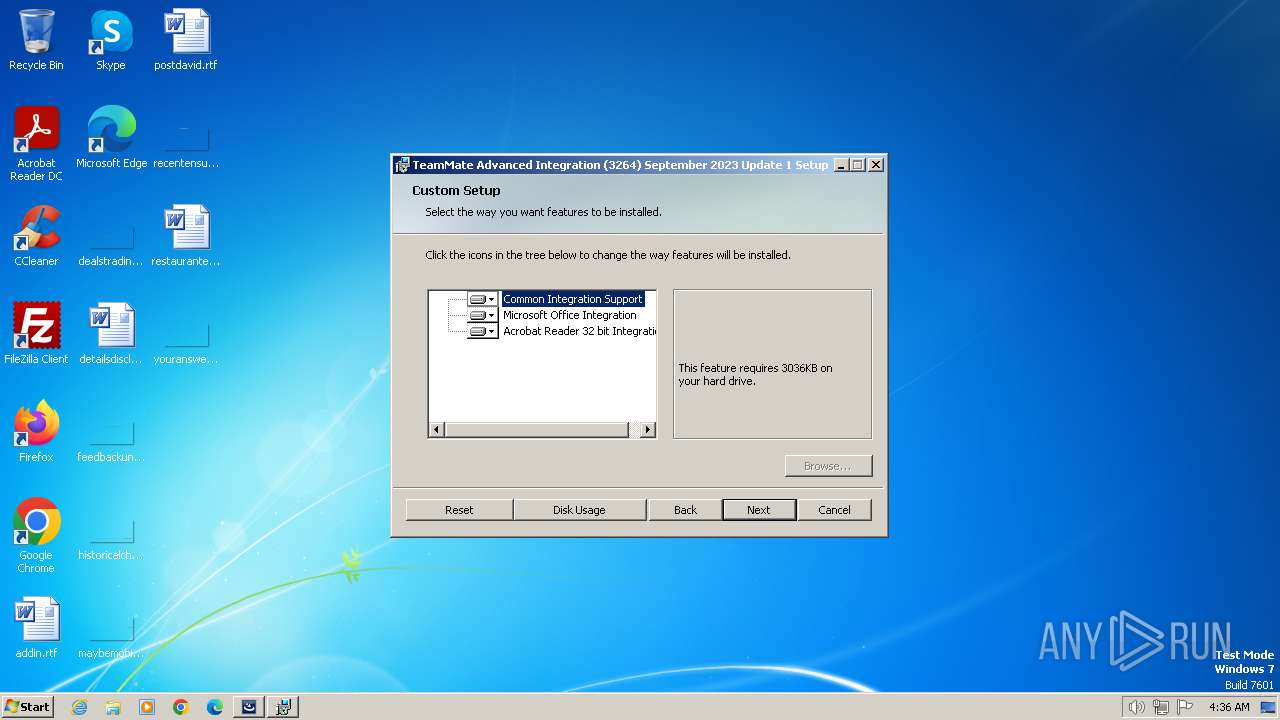
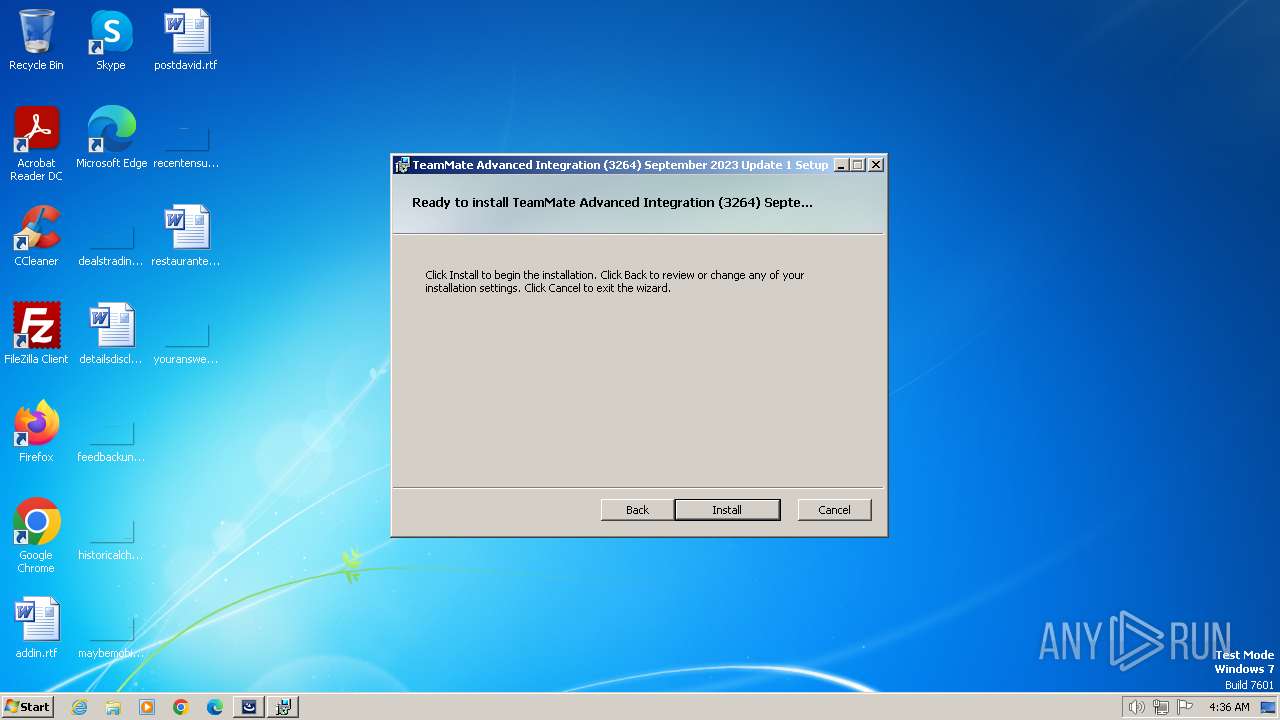
| File name: | TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe |
| Full analysis: | https://app.any.run/tasks/060a846f-7a02-4dab-93ab-94c76eb0a0af |
| Verdict: | Malicious activity |
| Analysis date: | December 22, 2023, 04:35:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 58B05149E1BA3AE4BFE8181A2B5C958B |
| SHA1: | 118D2ADC33D7D3853DA15E8C1E68E66A00822231 |
| SHA256: | E51FB228BD5C2649EBE0A359DE308EC2A8A21C38A008CCCC81008DB382C329BD |
| SSDEEP: | 98304:BLbkHLWqniKHqvsfK/nHPqH5lTy0wi28oqExu2xN2LjaHDXrPRRljmeB5rb60c2c:toPGHq40xn |
MALICIOUS
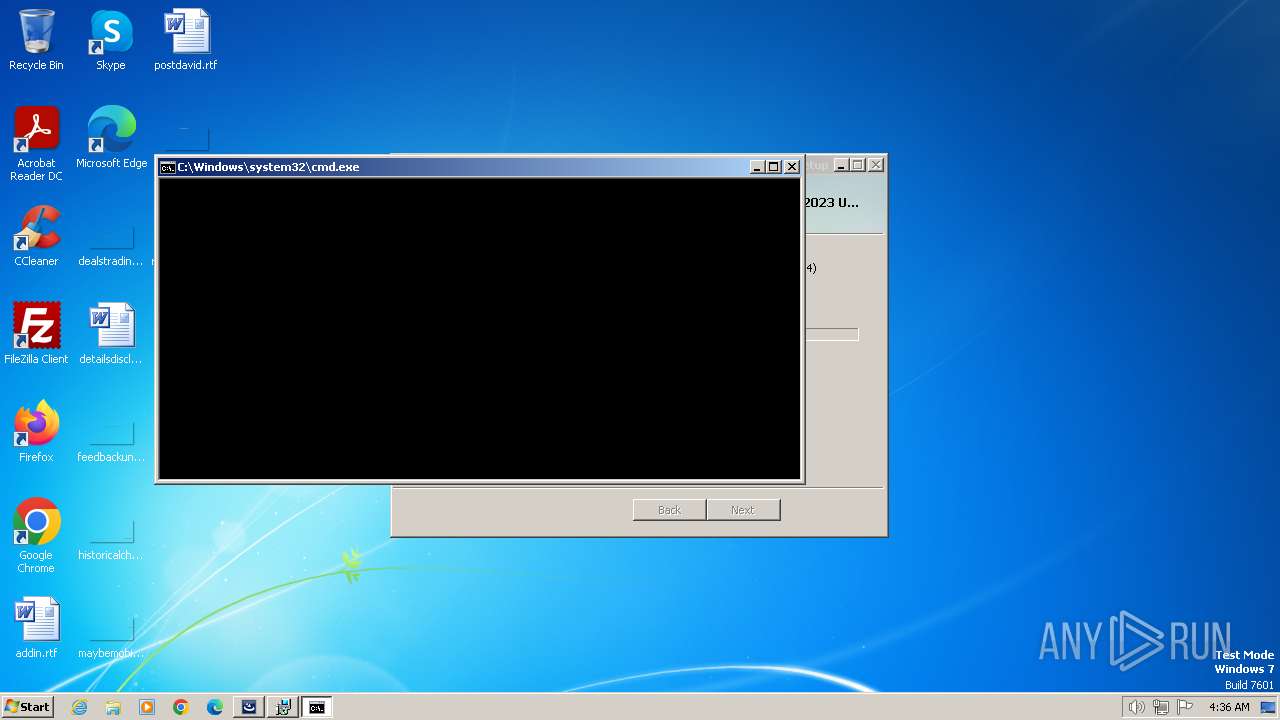
Starts NET.EXE for service management
- cmd.exe (PID: 2584)
- net.exe (PID: 2396)
SUSPICIOUS
The process creates files with name similar to system file names
- TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe (PID: 1072)
Searches for installed software
- OfficeAddIn.Setup3264.Bootstrapper_x32.exe (PID: 1504)
- TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe (PID: 1072)
Reads the Internet Settings
- TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe (PID: 1072)
Adds/modifies Windows certificates
- OfficeAddIn.Setup3264.Bootstrapper_x32.exe (PID: 1504)
Reads the Windows owner or organization settings
- OfficeAddIn.Setup3264.Bootstrapper_x32.exe (PID: 1504)
Reads security settings of Internet Explorer
- OfficeAddIn.Setup3264.Bootstrapper_x32.exe (PID: 1504)
Checks Windows Trust Settings
- msiexec.exe (PID: 2028)
- OfficeAddIn.Setup3264.Bootstrapper_x32.exe (PID: 1504)
Reads settings of System Certificates
- OfficeAddIn.Setup3264.Bootstrapper_x32.exe (PID: 1504)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 2028)
Creates a software uninstall entry
- OfficeAddIn.Setup3264.Bootstrapper_x32.exe (PID: 1504)
Starts SC.EXE for service management
- cmd.exe (PID: 2468)
INFO
Checks supported languages
- TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe (PID: 128)
- TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe (PID: 1072)
- OfficeAddIn.Setup3264.Bootstrapper_x32.exe (PID: 1504)
- msiexec.exe (PID: 2028)
Drops the executable file immediately after the start
- TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe (PID: 128)
- TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe (PID: 1072)
- OfficeAddIn.Setup3264.Bootstrapper_x32.exe (PID: 1504)
- msiexec.exe (PID: 2028)
Create files in a temporary directory
- TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe (PID: 128)
- TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe (PID: 1072)
- OfficeAddIn.Setup3264.Bootstrapper_x32.exe (PID: 1504)
- msiexec.exe (PID: 2028)
Reads the machine GUID from the registry
- OfficeAddIn.Setup3264.Bootstrapper_x32.exe (PID: 1504)
- TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe (PID: 1072)
- msiexec.exe (PID: 2028)
Executes as Windows Service
- VSSVC.exe (PID: 1780)
Creates files in the program directory
- OfficeAddIn.Setup3264.Bootstrapper_x32.exe (PID: 1504)
Reads the computer name
- TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe (PID: 1072)
- OfficeAddIn.Setup3264.Bootstrapper_x32.exe (PID: 1504)
- msiexec.exe (PID: 2028)
Starts itself from another location
- TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe (PID: 1072)
Process drops legitimate windows executable
- msiexec.exe (PID: 2028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:09:17 07:33:38+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit, Removable run from swap, Net run from swap |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 299008 |
| InitializedDataSize: | 186880 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2df71 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 42.1.15.0 |
| ProductVersionNumber: | 42.1.15.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | TeamMate, a Wolters Kluwer company |
| FileDescription: | TeamMate Advanced Integration (3264) September 2023 Update 1 |
| FileVersion: | 42.1.15.0 |
| InternalName: | setup |
| LegalCopyright: | Copyright (c) 2023 TeamMate Licensing B.V. All rights reserved. |
| OriginalFileName: | OfficeAddIn.Setup3264.Bootstrapper_x32.exe |
| ProductName: | TeamMate Advanced Integration (3264) September 2023 Update 1 |
| ProductVersion: | 42.1.15.0 |
Total processes
48
Monitored processes
10
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Users\admin\AppData\Local\Temp\TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe" | C:\Users\admin\AppData\Local\Temp\TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | — | explorer.exe | |||||||||||
User: admin Company: TeamMate, a Wolters Kluwer company Integrity Level: MEDIUM Description: TeamMate Advanced Integration (3264) September 2023 Update 1 Exit code: 0 Version: 42.1.15.0 Modules
| |||||||||||||||
| 1072 | "C:\Users\admin\AppData\Local\Temp\{256BBD72-B38E-4A02-8DBF-9E627329732D}\.cr\TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe" -burn.clean.room="C:\Users\admin\AppData\Local\Temp\TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe" -burn.filehandle.attached=152 -burn.filehandle.self=160 | C:\Users\admin\AppData\Local\Temp\{256BBD72-B38E-4A02-8DBF-9E627329732D}\.cr\TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | — | TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | |||||||||||
User: admin Company: TeamMate, a Wolters Kluwer company Integrity Level: MEDIUM Description: TeamMate Advanced Integration (3264) September 2023 Update 1 Exit code: 0 Version: 42.1.15.0 Modules
| |||||||||||||||
| 1504 | "C:\Users\admin\AppData\Local\Temp\{6BCF5CEB-B270-477F-8D33-3F7AEBD6B5FD}\.be\OfficeAddIn.Setup3264.Bootstrapper_x32.exe" -q -burn.elevated BurnPipe.{B59E300D-94C0-4C22-9F64-3A6F4D633B1C} {FEE73889-8D6E-4B35-9FA5-B6CD7B9E52F1} 1072 | C:\Users\admin\AppData\Local\Temp\{6BCF5CEB-B270-477F-8D33-3F7AEBD6B5FD}\.be\OfficeAddIn.Setup3264.Bootstrapper_x32.exe | TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | ||||||||||||
User: admin Company: TeamMate, a Wolters Kluwer company Integrity Level: HIGH Description: TeamMate Advanced Integration (3264) September 2023 Update 1 Exit code: 0 Version: 42.1.15.0 Modules
| |||||||||||||||
| 1600 | sc config webclient start=auto | C:\Windows\System32\sc.exe | cmd.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 1639 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1780 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2028 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2396 | net start webclient | C:\Windows\System32\net.exe | cmd.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2468 | cmd.exe /c "sc config webclient start=auto" | C:\Windows\System32\cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1639 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2584 | cmd.exe /c "net start webclient" | C:\Windows\System32\cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2808 | C:\Windows\system32\net1 start webclient | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
10 808
Read events
10 744
Write events
52
Delete events
12
Modification events
| (PID) Process: | (1072) TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (1072) TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1072) TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1072) TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1072) TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1504) OfficeAddIn.Setup3264.Bootstrapper_x32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000009F5A7BD72FB0D90164030000840D0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1504) OfficeAddIn.Setup3264.Bootstrapper_x32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 40000000000000009F5A7BD72FB0D90164030000840D0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1504) OfficeAddIn.Setup3264.Bootstrapper_x32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 73 | |||
| (PID) Process: | (1504) OfficeAddIn.Setup3264.Bootstrapper_x32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008543C5D72FB0D90164030000840D0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1504) OfficeAddIn.Setup3264.Bootstrapper_x32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 4000000000000000D1ABF1D82FB0D90164030000840D0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
66
Suspicious files
12
Text files
49
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1072 | TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | C:\Users\admin\AppData\Local\Temp\{6BCF5CEB-B270-477F-8D33-3F7AEBD6B5FD}\.ba\BootstrapperCore.dll | executable | |
MD5:1197872FA5DBF0A9D8C742558812DDE8 | SHA256:C1232F304EC8B3CE1626569AC28C6D1EEEA2EB891FC52D39E56F0D6102AC3D7E | |||
| 128 | TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | C:\Users\admin\AppData\Local\Temp\{256BBD72-B38E-4A02-8DBF-9E627329732D}\.cr\TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | executable | |
MD5:CDD9AF677DEB995E370C80A466D0E3BB | SHA256:B54C5CC5BD8F56E8C057523BA527ADA988F281AABEC891F7991BB41B3E771F51 | |||
| 1072 | TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | C:\Users\admin\AppData\Local\Temp\{6BCF5CEB-B270-477F-8D33-3F7AEBD6B5FD}\.ba\1028\mbapreq.wxl | xml | |
MD5:1D4B831F77EFEC96FFBC70BC4B59B8B5 | SHA256:1B93556F07C35AC0564D57E0743CCBA231950962C6506C8D4A74A31CD66FD04C | |||
| 1072 | TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | C:\Users\admin\AppData\Local\Temp\{6BCF5CEB-B270-477F-8D33-3F7AEBD6B5FD}\.ba\mbapreq.dll | executable | |
MD5:FE7E0BD53F52E6630473C31299A49FDD | SHA256:2BEA14D70943A42D344E09B7C9DE5562FA7E109946E1C615DD584DA30D06CC80 | |||
| 1072 | TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | C:\Users\admin\AppData\Local\Temp\{6BCF5CEB-B270-477F-8D33-3F7AEBD6B5FD}\.ba\mbapreq.wxl | xml | |
MD5:9B058AFD9185EBB4E7B93D58999EBFBA | SHA256:4F6D257CB03C0C57B16F1FEAC4D90A611BA9D0CAFFE9CE917E4D14A8F6CFB789 | |||
| 1072 | TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | C:\Users\admin\AppData\Local\Temp\{6BCF5CEB-B270-477F-8D33-3F7AEBD6B5FD}\.ba\eula.rtf | text | |
MD5:85BED13090AF7404DBFCCAC7DFFA96DB | SHA256:5B757D784DAA37607832999EDFB496F59AC0637C3CE36AB0FB98144C98673C67 | |||
| 1072 | TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | C:\Users\admin\AppData\Local\Temp\{6BCF5CEB-B270-477F-8D33-3F7AEBD6B5FD}\.ba\1040\mbapreq.wxl | xml | |
MD5:50261379B89457B1980FF19CFABE6A08 | SHA256:A40C94EB33F8841C79E9F6958433AFFD517F97B4570F731666AF572E63178BB7 | |||
| 1072 | TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | C:\Users\admin\AppData\Local\Temp\{6BCF5CEB-B270-477F-8D33-3F7AEBD6B5FD}\.ba\1030\mbapreq.wxl | xml | |
MD5:7C6E4CE87870B3B5E71D3EF4555500F8 | SHA256:CAC263E0E90A4087446A290055257B1C39F17E11F065598CB2286DF4332C7696 | |||
| 1072 | TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | C:\Users\admin\AppData\Local\Temp\{6BCF5CEB-B270-477F-8D33-3F7AEBD6B5FD}\.ba\mbapreq.thm | xml | |
MD5:4D9386E0154D2A3607D77241C36292CC | SHA256:141749F1752331E90E30B1421953776DDB75DF29A6164D048A08ED3E7B772C7C | |||
| 1072 | TeamMate_Advanced_Integration_3264_September_2023_Update_1_,jssl.teammatehosting.com,.exe | C:\Users\admin\AppData\Local\Temp\{6BCF5CEB-B270-477F-8D33-3F7AEBD6B5FD}\.ba\1036\mbapreq.wxl | xml | |
MD5:AA32A059AADD42431F7837CB1BE7257F | SHA256:88E7DDACD6B714D94D5322876BD50051479B7A0C686DC2E9EB06B3B7A0BC06C9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |