| File name: | emBridge.exe |
| Full analysis: | https://app.any.run/tasks/235faba6-2069-4644-9514-730951b934fb |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2025, 12:35:05 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | 404ECFAF5FF950E83D1E2C1228CCB926 |
| SHA1: | 770233F622038C64748528530DA9E607100A429B |
| SHA256: | E50A3EEEB5601C6A3CFD03DEA99753E68BAFE309E8DBC1FB7713CF392D534E2D |
| SSDEEP: | 98304:3+cD4dnJOK7ScFCdqzLnTrwZLM8EMCgekFyxeT3j8chAGBjJXnZUYKtIhYQRrlyG:Q2FMzPOieJ |
MALICIOUS
Create files in the Startup directory
- emBridge.tmp (PID: 7256)
SUSPICIOUS
Reads security settings of Internet Explorer
- emBridge.tmp (PID: 6668)
- emBridge.exe (PID: 4428)
Executable content was dropped or overwritten
- emBridge.exe (PID: 7224)
- emBridge.exe (PID: 5680)
- emBridge.tmp (PID: 7256)
Reads the Windows owner or organization settings
- emBridge.tmp (PID: 7256)
Modifies hosts file to alter network resolution
- emBridge.tmp (PID: 7256)
Process drops legitimate windows executable
- emBridge.tmp (PID: 7256)
Starts CMD.EXE for commands execution
- emBridge.tmp (PID: 7256)
- emBridge.exe (PID: 4428)
Executing commands from a ".bat" file
- emBridge.tmp (PID: 7256)
Creates or modifies Windows services
- emBridge.exe (PID: 8072)
Executes as Windows Service
- emBridge.exe (PID: 4428)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 5416)
- cmd.exe (PID: 4740)
- cmd.exe (PID: 7484)
- cmd.exe (PID: 2616)
- cmd.exe (PID: 6752)
- cmd.exe (PID: 7468)
Adds/modifies Windows certificates
- emBridge.exe (PID: 4428)
INFO
Checks supported languages
- emBridge.tmp (PID: 6668)
- emBridge.exe (PID: 7224)
- emBridge.tmp (PID: 7256)
- emBridge.exe (PID: 5680)
- emBridge.exe (PID: 8072)
- emBridge.exe (PID: 4428)
- emBridge.exe (PID: 8144)
Reads the computer name
- emBridge.tmp (PID: 6668)
- emBridge.tmp (PID: 7256)
- emBridge.exe (PID: 8072)
- emBridge.exe (PID: 8144)
- emBridge.exe (PID: 4428)
Process checks computer location settings
- emBridge.tmp (PID: 6668)
Create files in a temporary directory
- emBridge.exe (PID: 5680)
- emBridge.tmp (PID: 7256)
- emBridge.exe (PID: 7224)
Compiled with Borland Delphi (YARA)
- emBridge.exe (PID: 5680)
- emBridge.tmp (PID: 6668)
- emBridge.exe (PID: 7224)
- emBridge.tmp (PID: 7256)
Detects InnoSetup installer (YARA)
- emBridge.exe (PID: 5680)
- emBridge.tmp (PID: 6668)
- emBridge.tmp (PID: 7256)
- emBridge.exe (PID: 7224)
The sample compiled with english language support
- emBridge.tmp (PID: 7256)
Creates files in the program directory
- emBridge.exe (PID: 4428)
- emBridge.exe (PID: 8072)
- emBridge.tmp (PID: 7256)
Reads the machine GUID from the registry
- emBridge.exe (PID: 8144)
- emBridge.exe (PID: 8072)
- emBridge.exe (PID: 4428)
Disables trace logs
- emBridge.exe (PID: 4428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (51.8) |
|---|---|---|
| .exe | | | InstallShield setup (20.3) |
| .exe | | | Win32 EXE PECompact compressed (generic) (19.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.1) |
| .exe | | | Win32 Executable (generic) (2.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 38400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.9.1.3 |
| ProductVersionNumber: | 5.9.1.3 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | eMudhra Limited |
| FileDescription: | emBridge Setup |
| FileVersion: | 5.9.1.3 |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | emBridge |
| ProductVersion: | 5.9.1.3 |
Total processes
165
Monitored processes
35
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1240 | netsh http add sslcert ipport=0.0.0.0:26770 appid= {a38aa4bd-f42d-44fa-a9c9-da61f74ca666} certhash="3fa603462da4d313af958c5ab2dc7c4bd5137784" | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | netsh http dele sslcert ipport=0.0.0.0:26770 | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2560 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2616 | "C:\Windows\System32\cmd.exe" /C netsh http dele sslcert ipport=0.0.0.0:26770 | C:\Windows\SysWOW64\cmd.exe | — | emBridge.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3100 | netsh http add urlacl url=https://+:26769/ user=Everyone | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | "C:\Windows\System32\cmd.exe" /C CheckNetIsolation LoopbackExempt -a -n=Microsoft.MicrosoftEdge_8wekyb3d8bbwe | C:\Windows\SysWOW64\cmd.exe | — | emBridge.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4272 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4428 | "C:\Program Files (x86)\eMudhra\emBridge\emBridge.exe" -displayname "emBridge Service" -servicename "emBridge" | C:\Program Files (x86)\eMudhra\emBridge\emBridge.exe | services.exe | ||||||||||||
User: SYSTEM Company: eMudhra Limited Integrity Level: SYSTEM Description: emBridge Version: 5.9.1.3 Modules
| |||||||||||||||
| 4740 | "C:\Windows\System32\cmd.exe" /C netsh http dele sslcert ipport=0.0.0.0:26769 | C:\Windows\SysWOW64\cmd.exe | — | emBridge.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5008 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 272
Read events
11 222
Write events
46
Delete events
4
Modification events
| (PID) Process: | (7256) emBridge.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{a38aa4bd-f42d-44fa-a9c9-da61f74ca666}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.2 | |||
| (PID) Process: | (7256) emBridge.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{a38aa4bd-f42d-44fa-a9c9-da61f74ca666}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
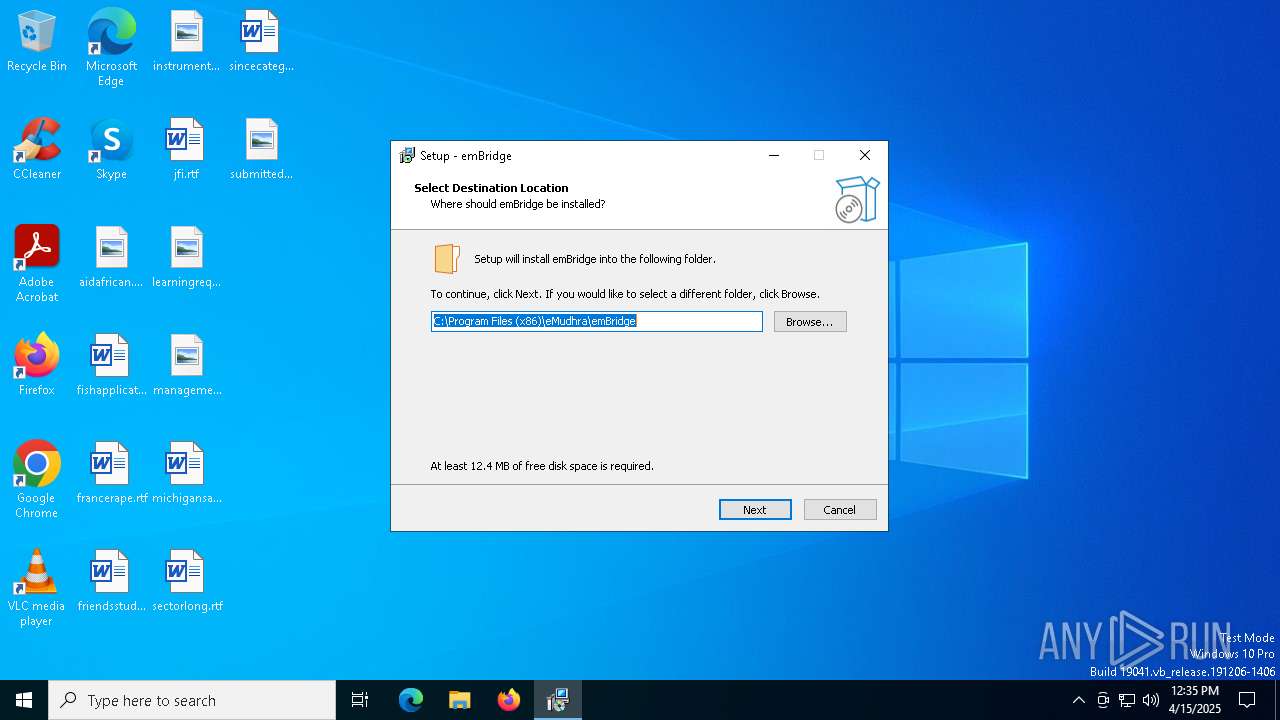
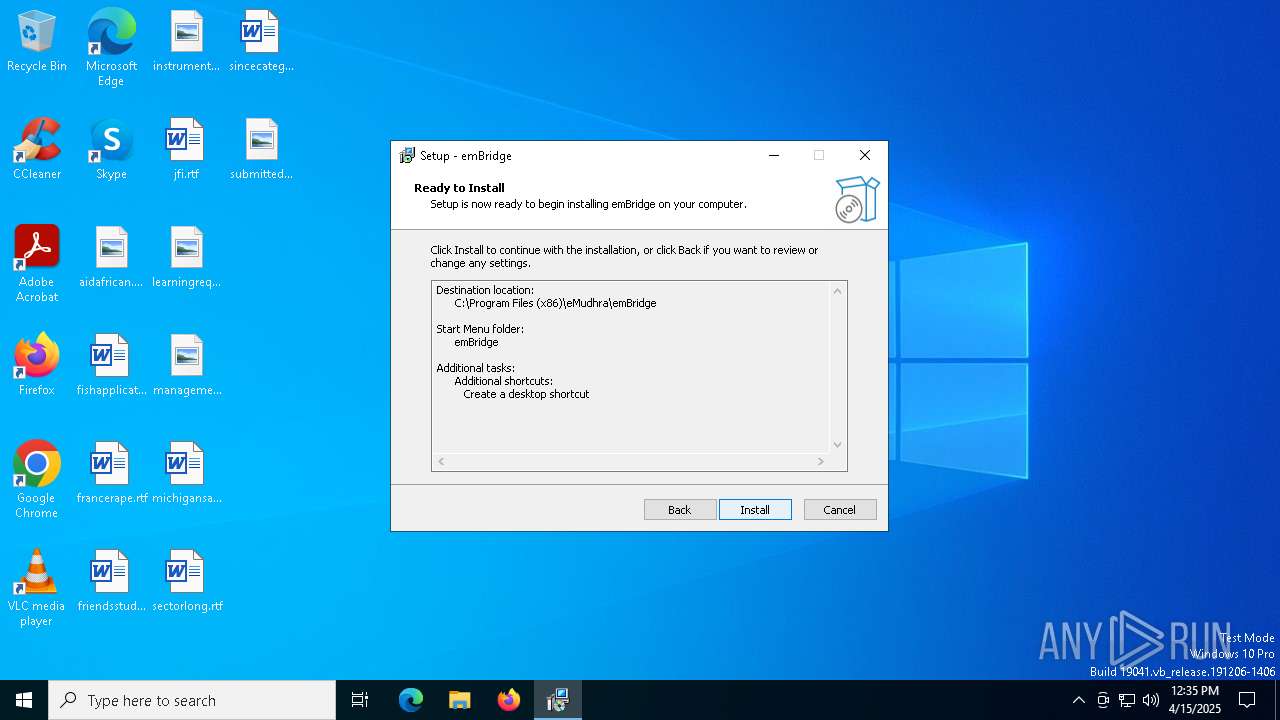
Value: C:\Program Files (x86)\eMudhra\emBridge | |||
| (PID) Process: | (7256) emBridge.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{a38aa4bd-f42d-44fa-a9c9-da61f74ca666}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\eMudhra\emBridge\ | |||
| (PID) Process: | (7256) emBridge.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{a38aa4bd-f42d-44fa-a9c9-da61f74ca666}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: emBridge | |||
| (PID) Process: | (7256) emBridge.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{a38aa4bd-f42d-44fa-a9c9-da61f74ca666}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (7256) emBridge.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{a38aa4bd-f42d-44fa-a9c9-da61f74ca666}_is1 |
| Operation: | write | Name: | Inno Setup: Selected Tasks |
Value: desktopicon | |||
| (PID) Process: | (7256) emBridge.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{a38aa4bd-f42d-44fa-a9c9-da61f74ca666}_is1 |
| Operation: | write | Name: | Inno Setup: Deselected Tasks |
Value: win7reg | |||
| (PID) Process: | (7256) emBridge.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{a38aa4bd-f42d-44fa-a9c9-da61f74ca666}_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: english | |||
| (PID) Process: | (7256) emBridge.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{a38aa4bd-f42d-44fa-a9c9-da61f74ca666}_is1 |
| Operation: | write | Name: | DisplayName |
Value: emBridge | |||
| (PID) Process: | (7256) emBridge.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{a38aa4bd-f42d-44fa-a9c9-da61f74ca666}_is1 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\eMudhra\emBridge\emBridge.exe | |||
Executable files
29
Suspicious files
12
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7256 | emBridge.tmp | C:\Users\admin\AppData\Local\Temp\is-TT39M.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 7256 | emBridge.tmp | C:\Program Files (x86)\eMudhra\emBridge\is-K7AMJ.tmp | executable | |
MD5:3DD7F96C27E65B8F567EE3673E42EB7F | SHA256:D65325AA76F8997F151D58AD3DABA76AAAE987C5DB1114223A239B849722189C | |||
| 7256 | emBridge.tmp | C:\Program Files (x86)\eMudhra\emBridge\is-A1VHC.tmp | executable | |
MD5:BDC52F53AE7BBD99D60CDC2156F27BD3 | SHA256:EA4C2C88771AD1FAB8C1772B75FC9B16162AFD94596FF92905D9741047F75C9B | |||
| 7256 | emBridge.tmp | C:\Program Files (x86)\eMudhra\emBridge\Newtonsoft.Json.dll | executable | |
MD5:C724ACF1B7F9D029C35F80315D3E340A | SHA256:EC2C36C86514579E8E960724C9D5FDE2793F4FD68BED503B62F2C580B96D863C | |||
| 7256 | emBridge.tmp | C:\Program Files (x86)\eMudhra\emBridge\is-IM4PL.tmp | executable | |
MD5:C724ACF1B7F9D029C35F80315D3E340A | SHA256:EC2C36C86514579E8E960724C9D5FDE2793F4FD68BED503B62F2C580B96D863C | |||
| 7256 | emBridge.tmp | C:\Program Files (x86)\eMudhra\emBridge\is-29B9K.tmp | executable | |
MD5:261D3C739FA4EB69830D7A077CB23BB1 | SHA256:EBDA5089E0E304ADADAE3A7463146436C33CA23257A2EDAD2DE8032C73804D2E | |||
| 7256 | emBridge.tmp | C:\Program Files (x86)\eMudhra\emBridge\emBridge.exe | executable | |
MD5:3DD7F96C27E65B8F567EE3673E42EB7F | SHA256:D65325AA76F8997F151D58AD3DABA76AAAE987C5DB1114223A239B849722189C | |||
| 7256 | emBridge.tmp | C:\Program Files (x86)\eMudhra\emBridge\is-8GIHC.tmp | executable | |
MD5:A16A0AE73197C99125266C81599DA511 | SHA256:152EF62B614CA2B746283BC7FD008655408B3BAB763CA20B77AC83A316670519 | |||
| 7224 | emBridge.exe | C:\Users\admin\AppData\Local\Temp\is-H1QBK.tmp\emBridge.tmp | executable | |
MD5:C74092BE958A2081B459F4E816C00D58 | SHA256:7ECA41250586118B758396C82947213E5DD448B5611D907BD473271149318DF7 | |||
| 7256 | emBridge.tmp | C:\Program Files (x86)\eMudhra\emBridge\unins000.exe | executable | |
MD5:261D3C739FA4EB69830D7A077CB23BB1 | SHA256:EBDA5089E0E304ADADAE3A7463146436C33CA23257A2EDAD2DE8032C73804D2E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
18
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7804 | SIHClient.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7804 | SIHClient.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.18.244.216:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4428 | emBridge.exe | GET | 200 | 13.234.51.255:80 | http://resources.emudhra.com/hs/updates.xml | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.18.244.216:80 | crl.microsoft.com | Akamai International B.V. | FR | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7804 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7804 | SIHClient.exe | 104.85.1.163:80 | www.microsoft.com | AKAMAI-AS | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
resources.emudhra.com |
| whitelisted |
Threats
Process | Message |
|---|---|
emBridge.exe | Configuration Result:
[Success] Name emBridge
[Success] DisplayName emBridge Service
[Success] Description emBridge Service.
[Success] ServiceName emBridge
|
emBridge.exe | Topshelf.HostFactory Information: 0 : |
emBridge.exe | Topshelf.HostConfigurators.HostConfiguratorImpl Information: 0 : |
emBridge.exe | Topshelf v3.3.154.0, .NET Framework v4.0.30319.42000
|
emBridge.exe | Topshelf.Runtime.Windows.WindowsServiceHost Information: 0 : |
emBridge.exe | Starting as a Windows service
|
emBridge.exe | Topshelf.Runtime.Windows.WindowsServiceHost Information: 0 : |
emBridge.exe | [Topshelf] Starting
|
emBridge.exe | [Topshelf] Started
|
emBridge.exe | Topshelf.Runtime.Windows.WindowsServiceHost Information: 0 : |